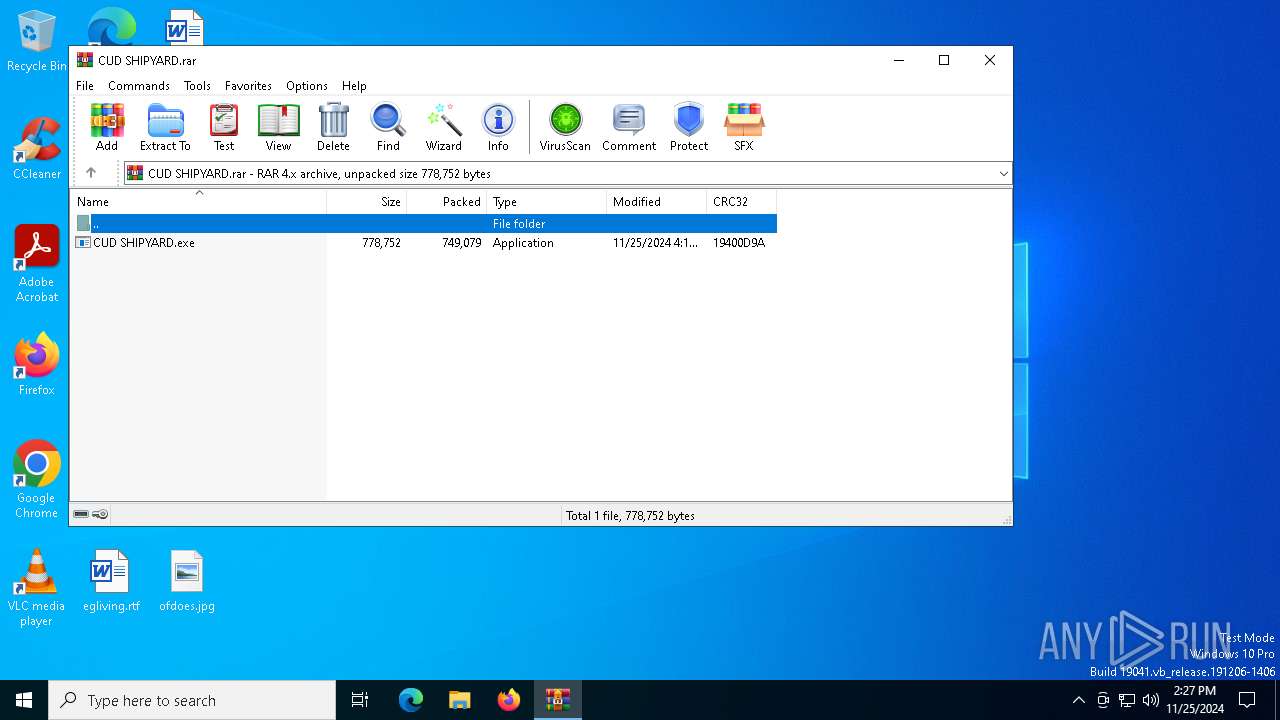
| File name: | CUD SHIPYARD.rar |
| Full analysis: | https://app.any.run/tasks/17c49013-850e-4afa-a754-3680684da527 |
| Verdict: | Malicious activity |
| Analysis date: | November 25, 2024, 14:26:59 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 6A07AE4BADB638C4DAEE3993FBF8E860 |
| SHA1: | 0CD213871A85D41D550B517FAB0C7DFEC20BDC24 |
| SHA256: | 31E03D626C4ED64DB5B43EA55B347CE0472E9F448477EBDD2973B852B47119A0 |
| SSDEEP: | 24576:b/WzjsqSvdB1HaDwEOVrfFMJwMT0v0V+tTz3nmod17LTLzvpDBFd2rXhyT+AWqlM:b/WzjNSvdB16DwRVrfFMJwMT0v4+tTze |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6440)
SUSPICIOUS
Application launched itself
- CUD SHIPYARD.exe (PID: 6332)
- CUD SHIPYARD.exe (PID: 6232)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6440)
Manual execution by a user
- CUD SHIPYARD.exe (PID: 6332)
- CUD SHIPYARD.exe (PID: 6232)
- WINWORD.EXE (PID: 6964)
- WINWORD.EXE (PID: 4840)
.NET Reactor protector has been detected
- CUD SHIPYARD.exe (PID: 6232)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| FileVersion: | RAR v4 |
|---|---|
| CompressedSize: | 749121 |
| UncompressedSize: | 778752 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2024:11:25 04:12:42 |
| PackingMethod: | Normal |
| ArchivedFileName: | CUD SHIPYARD.exe |
Total processes
147
Monitored processes
9
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4504 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "5C23B2CF-9F2B-45E4-B828-F49ED8E933D4" "AF800C69-5751-4269-8D9E-8FE7AC00CA9E" "6964" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 3221225547 Version: 0.12.2.0 Modules
| |||||||||||||||
| 4840 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\historybox.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 5244 | "C:\Users\admin\Desktop\CUD SHIPYARD.exe" | C:\Users\admin\Desktop\CUD SHIPYARD.exe | — | CUD SHIPYARD.exe | |||||||||||
User: admin Company: DCC Integrity Level: MEDIUM Description: DynamicFormLoading Exit code: 0 Version: 1.1.0.0 Modules
| |||||||||||||||
| 6188 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "BF3309C3-38DD-45D6-945D-A3F7ADA21AF6" "2122C9A1-1098-4FBE-A484-A4DD3B6F6E6C" "4840" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 6232 | "C:\Users\admin\Desktop\CUD SHIPYARD.exe" | C:\Users\admin\Desktop\CUD SHIPYARD.exe | explorer.exe | ||||||||||||
User: admin Company: DCC Integrity Level: HIGH Description: DynamicFormLoading Exit code: 0 Version: 1.1.0.0 Modules
| |||||||||||||||
| 6304 | "C:\Users\admin\Desktop\CUD SHIPYARD.exe" | C:\Users\admin\Desktop\CUD SHIPYARD.exe | — | CUD SHIPYARD.exe | |||||||||||
User: admin Company: DCC Integrity Level: HIGH Description: DynamicFormLoading Exit code: 0 Version: 1.1.0.0 Modules
| |||||||||||||||
| 6332 | "C:\Users\admin\Desktop\CUD SHIPYARD.exe" | C:\Users\admin\Desktop\CUD SHIPYARD.exe | — | explorer.exe | |||||||||||
User: admin Company: DCC Integrity Level: MEDIUM Description: DynamicFormLoading Exit code: 0 Version: 1.1.0.0 Modules
| |||||||||||||||
| 6440 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\CUD SHIPYARD.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6964 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\davidjuly.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
18 100
Read events
16 925
Write events
1 062
Delete events
113
Modification events
| (PID) Process: | (6440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\CUD SHIPYARD.rar | |||
| (PID) Process: | (6440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (6964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\6964 |
| Operation: | write | Name: | 0 |
Value: 0B0E100F498E6A6D11DA49846D84A8A4846B82230046E4E3DDAFE7E8CFED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511B436D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
Executable files
2
Suspicious files
49
Text files
7
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6964 | WINWORD.EXE | C:\Users\admin\Desktop\~$vidjuly.rtf | binary | |
MD5:24C8C9BA11AA9FD1032180399C286589 | SHA256:BD30F45BDC27DF427CFD5471CB28D62B1447F65DE4362BAADCF4BC6411616FDF | |||
| 6964 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 6964 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | der | |
MD5:99BA6B7F0F3EC8D66A8B6A80669C7B3D | SHA256:D3B813690DFC256C53B3AF9FC4015F5AA3344ABB4416CE0D79BC2CE6603D299B | |||
| 6964 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:8EAC9F5D241B0D7F01D515AFF353CB2F | SHA256:13D00DC7AC72C75A144174B2E99056439786DAFCBCB911076ACCC34AD010D299 | |||
| 6964 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:D911100AE52142539AF0A0F0D2B6377D | SHA256:D149BB48E4766DFDAE41B666503CFE414C4C27F7C8E5C11168C4FA03D7E42BDE | |||
| 6964 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json | binary | |
MD5:13FA31CEB462F0E61565D0D39D8643F8 | SHA256:DCECE5ADF943A8C8321D37661396A124D4531FC84D754CAB7FB5063FC779FA86 | |||
| 6964 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:8B54E230309B238BAFDF840E8F204560 | SHA256:C9C490E3ED204CA75E80849309693CC90F422AC2E09B740C1C878EE2A451FC91 | |||
| 6964 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json.tmp | binary | |
MD5:13FA31CEB462F0E61565D0D39D8643F8 | SHA256:DCECE5ADF943A8C8321D37661396A124D4531FC84D754CAB7FB5063FC779FA86 | |||
| 6440 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6440.14178\CUD SHIPYARD.exe | executable | |
MD5:637A1E173D014C0D112909398E136207 | SHA256:882751E8B0F45890EA932235EBAC16147EE1130833EDABF20C43DE18DF3995B8 | |||
| 6964 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:522AB61E2FC5B55EDDEB21478BAFF530 | SHA256:895F196FF49EF049221105C23BD7EC122E7AC59C44C123BBA7DF7399518E785C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
51
DNS requests
34
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
132 | svchost.exe | GET | 200 | 23.48.23.161:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.161:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1864 | RUXIMICS.exe | GET | 200 | 23.48.23.161:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
132 | svchost.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3620 | SIHClient.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3620 | SIHClient.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6964 | WINWORD.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 2.16.204.135:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
132 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.161:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
132 | svchost.exe | 23.48.23.161:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1864 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1864 | RUXIMICS.exe | 23.48.23.161:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|