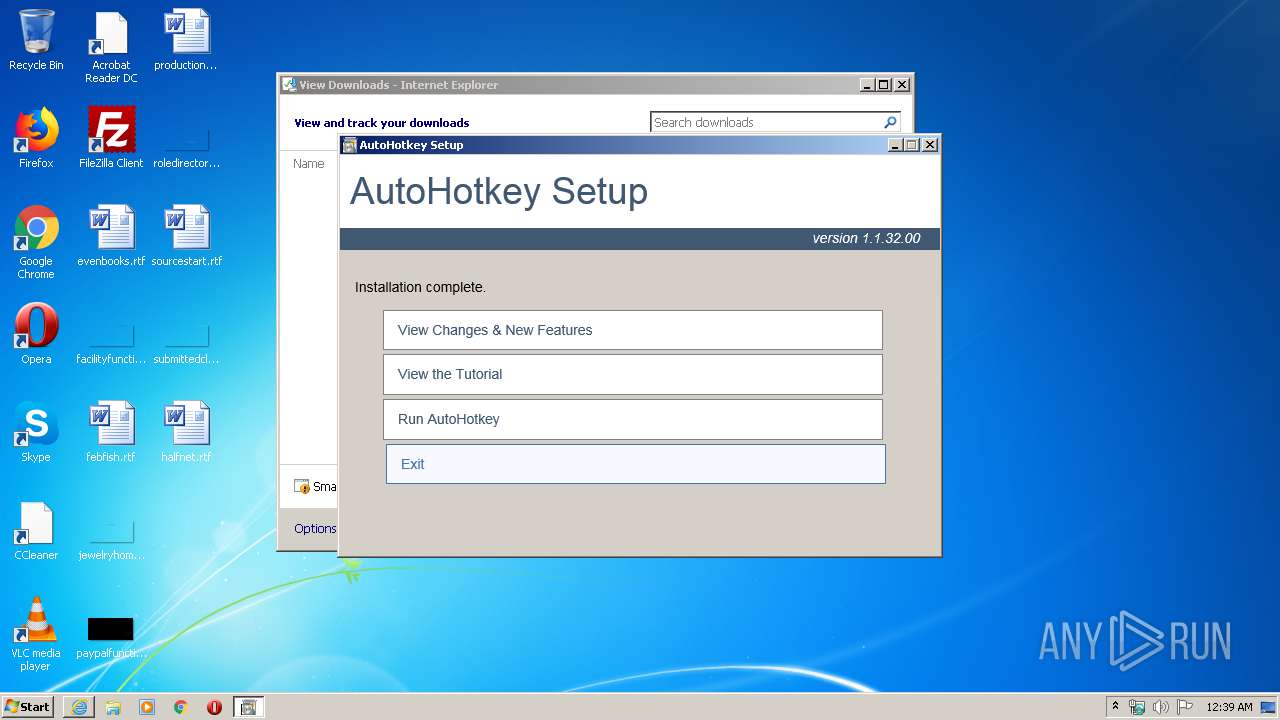
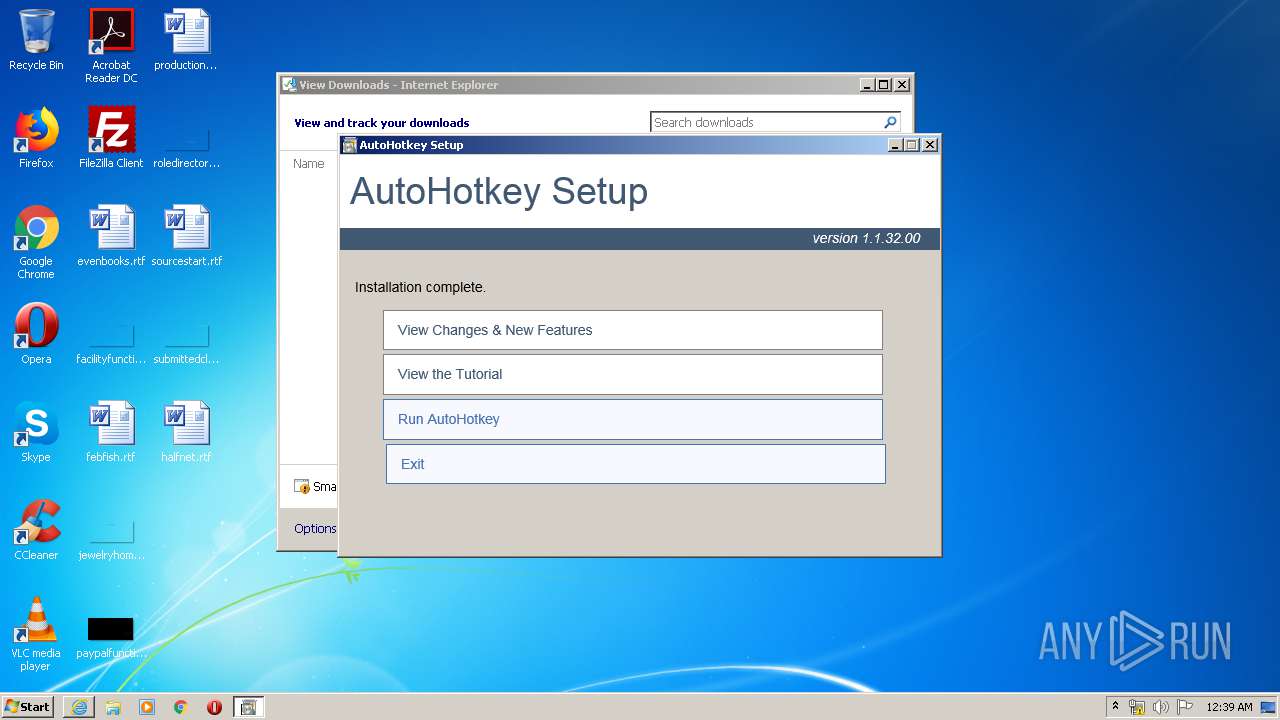
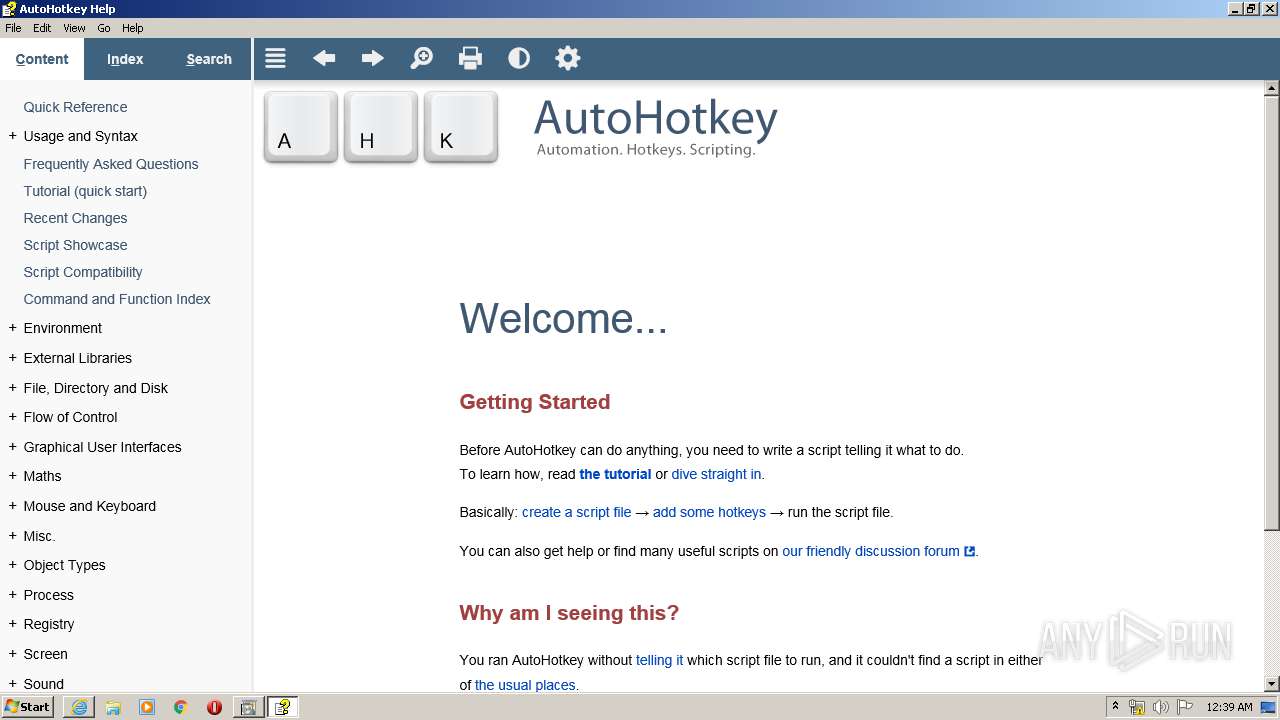
| URL: | https://www.autohotkey.com/download/ahk-install.exe |
| Full analysis: | https://app.any.run/tasks/ae4e451b-cac3-4384-a59b-9476b95cc5d9 |
| Verdict: | Malicious activity |
| Analysis date: | March 01, 2020, 00:38:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 2CDC74790EE4C21384B03F10F6041900 |
| SHA1: | 18C1714002FCF04D82C0053DF8C84192E7BBC578 |
| SHA256: | 31DFE1DD5B9281A0908752C44DF02D525F3D884C50E41FD24311E05D83273A96 |
| SSDEEP: | 3:N8DSLKwLknNRKN:2OLKwUDe |
MALICIOUS
Application was dropped or rewritten from another process
- AutoHotkey_1.1.32.00_setup.exe (PID: 2696)
- AutoHotkey_1.1.32.00_setup.exe (PID: 3172)
- setup.exe (PID: 3888)
- AutoHotkey.exe (PID: 564)
- AutoHotkey.exe (PID: 2928)
SUSPICIOUS
Executable content was dropped or overwritten
- iexplore.exe (PID: 3328)
- iexplore.exe (PID: 3436)
- AutoHotkey_1.1.32.00_setup.exe (PID: 2696)
- setup.exe (PID: 3888)
Reads internet explorer settings
- setup.exe (PID: 3888)
- hh.exe (PID: 540)
Creates files in the program directory
- setup.exe (PID: 3888)
Creates files in the Windows directory
- setup.exe (PID: 3888)
Modifies the open verb of a shell class
- setup.exe (PID: 3888)
Creates a software uninstall entry
- setup.exe (PID: 3888)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 3328)
- iexplore.exe (PID: 3436)
Changes internet zones settings
- iexplore.exe (PID: 3328)
Creates files in the user directory
- iexplore.exe (PID: 3436)
- iexplore.exe (PID: 3328)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3328)
Reads settings of System Certificates
- iexplore.exe (PID: 3328)
- iexplore.exe (PID: 3436)
Manual execution by user
- AutoHotkey.exe (PID: 564)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3328)
Changes settings of System certificates
- iexplore.exe (PID: 3328)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
46
Monitored processes
8
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 540 | "C:\Windows\hh.exe" "ms-its:C:\Program Files\AutoHotkey\AutoHotkey.chm::/docs/Welcome.htm" | C:\Windows\hh.exe | — | AutoHotkey.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® HTML Help Executable Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 564 | "C:\Program Files\AutoHotkey\AutoHotkey.exe" "C:\Program Files\AutoHotkey\Installer.ahk" /exec runahk | C:\Program Files\AutoHotkey\AutoHotkey.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: AutoHotkey Unicode 32-bit Exit code: 0 Version: 1.1.32.00 Modules
| |||||||||||||||
| 2696 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\AutoHotkey_1.1.32.00_setup.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\AutoHotkey_1.1.32.00_setup.exe | iexplore.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: AutoHotkey Setup Exit code: 0 Version: 1.1.32.00 Modules
| |||||||||||||||
| 2928 | AutoHotkey.exe | C:\Program Files\AutoHotkey\AutoHotkey.exe | — | AutoHotkey.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: AutoHotkey Unicode 32-bit Exit code: 2 Version: 1.1.32.00 Modules
| |||||||||||||||
| 3172 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\AutoHotkey_1.1.32.00_setup.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\AutoHotkey_1.1.32.00_setup.exe | — | iexplore.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: AutoHotkey Setup Exit code: 3221226540 Version: 1.1.32.00 Modules
| |||||||||||||||
| 3328 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.autohotkey.com/download/ahk-install.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3436 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3328 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3888 | C:\Users\admin\AppData\Local\Temp\7z6FE8AA88\setup.exe | C:\Users\admin\AppData\Local\Temp\7z6FE8AA88\setup.exe | AutoHotkey_1.1.32.00_setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.1.32.00 Modules
| |||||||||||||||
Total events
4 718
Read events
1 065
Write events
2 465
Delete events
1 188
Modification events
| (PID) Process: | (3328) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 3480296160 | |||
| (PID) Process: | (3328) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30797665 | |||
| (PID) Process: | (3328) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3328) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3328) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3328) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3328) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3328) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3328) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3328) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
19
Suspicious files
10
Text files
23
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3436 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab70F2.tmp | — | |
MD5:— | SHA256:— | |||
| 3436 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar70F3.tmp | — | |
MD5:— | SHA256:— | |||
| 3328 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF6BBABE61ABD5C1E5.TMP | — | |
MD5:— | SHA256:— | |||
| 3328 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\AutoHotkey_1.1.32.00_setup.exe.qcw5v5x.partial:Zone.Identifier | — | |
MD5:— | SHA256:— | |||
| 3436 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_74167E25E5476CCA2A5946AAA61BF9E1 | der | |
MD5:— | SHA256:— | |||
| 3436 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\8QU1CQCK.txt | text | |
MD5:— | SHA256:— | |||
| 3436 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_74167E25E5476CCA2A5946AAA61BF9E1 | binary | |
MD5:— | SHA256:— | |||
| 3328 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\AutoHotkey_1.1.32.00_setup.exe:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 3328 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{FB3017FB-5B54-11EA-972D-5254004A04AF}.dat | binary | |
MD5:— | SHA256:— | |||
| 3436 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\AutoHotkey_1.1.32.00_setup.exe.qcw5v5x.partial | executable | |
MD5:818105AB8672979AA12542EBC90C4518 | SHA256:CE505D272F8D36C5599AC81F005E1D2D586EEAAA778C779AD858E44FDADFDB0D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
11
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3436 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2Fz5hY5qj0aEmX0H4s05bY%3D | US | der | 1.47 Kb | whitelisted |
3328 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
3328 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3436 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3328 | iexplore.exe | 72.21.81.200:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3328 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3328 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
— | — | 204.79.197.200:443 | ieonline.microsoft.com | Microsoft Corporation | US | whitelisted |
3436 | iexplore.exe | 104.18.45.93:443 | www.autohotkey.com | Cloudflare Inc | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.autohotkey.com |
| suspicious |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |