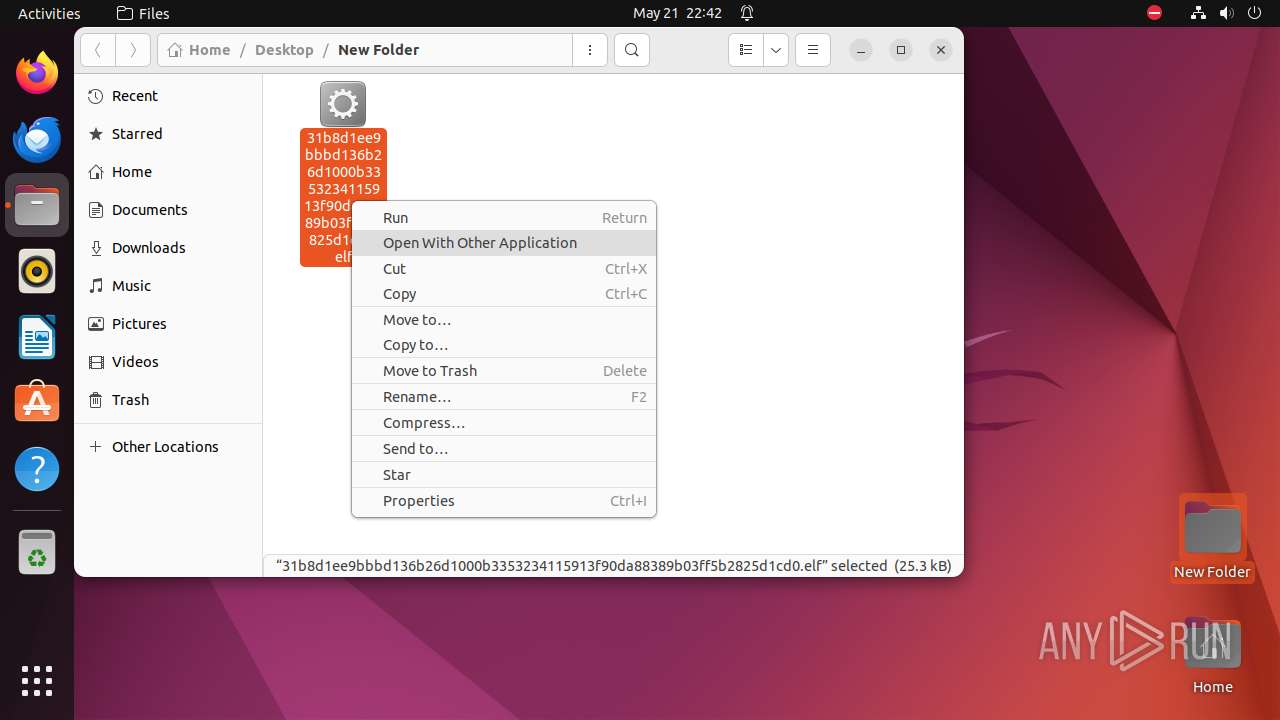
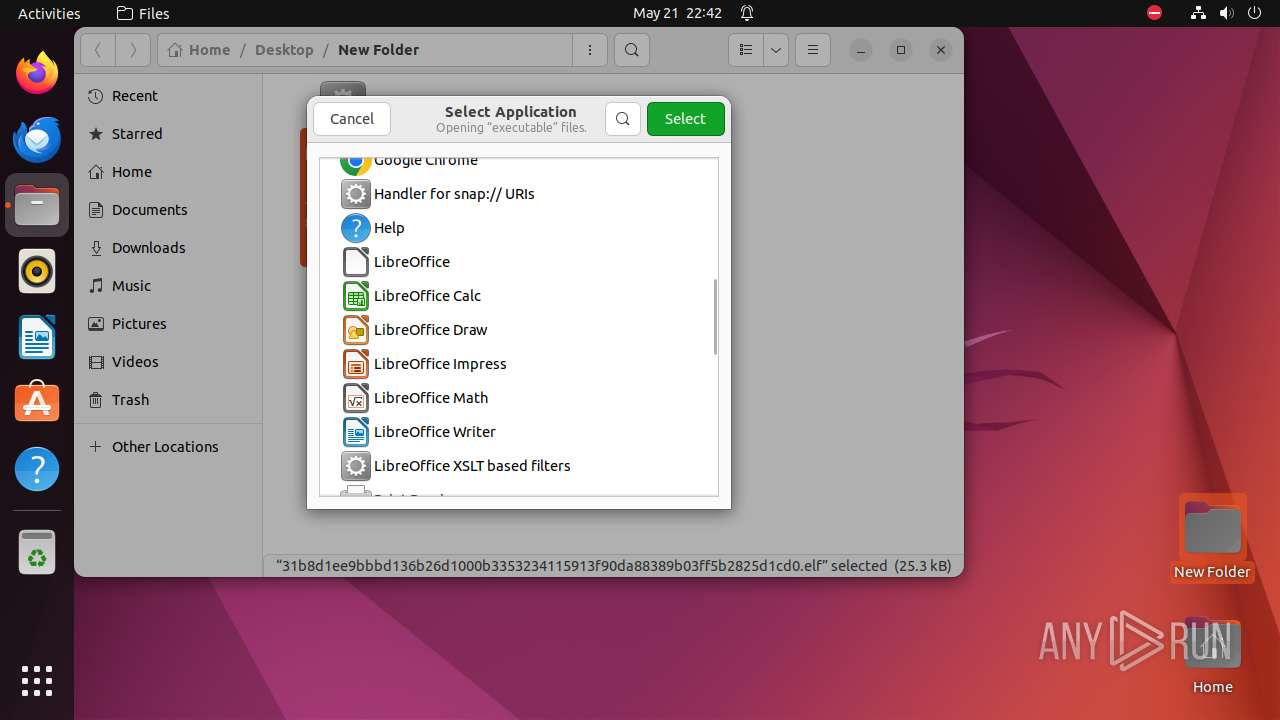
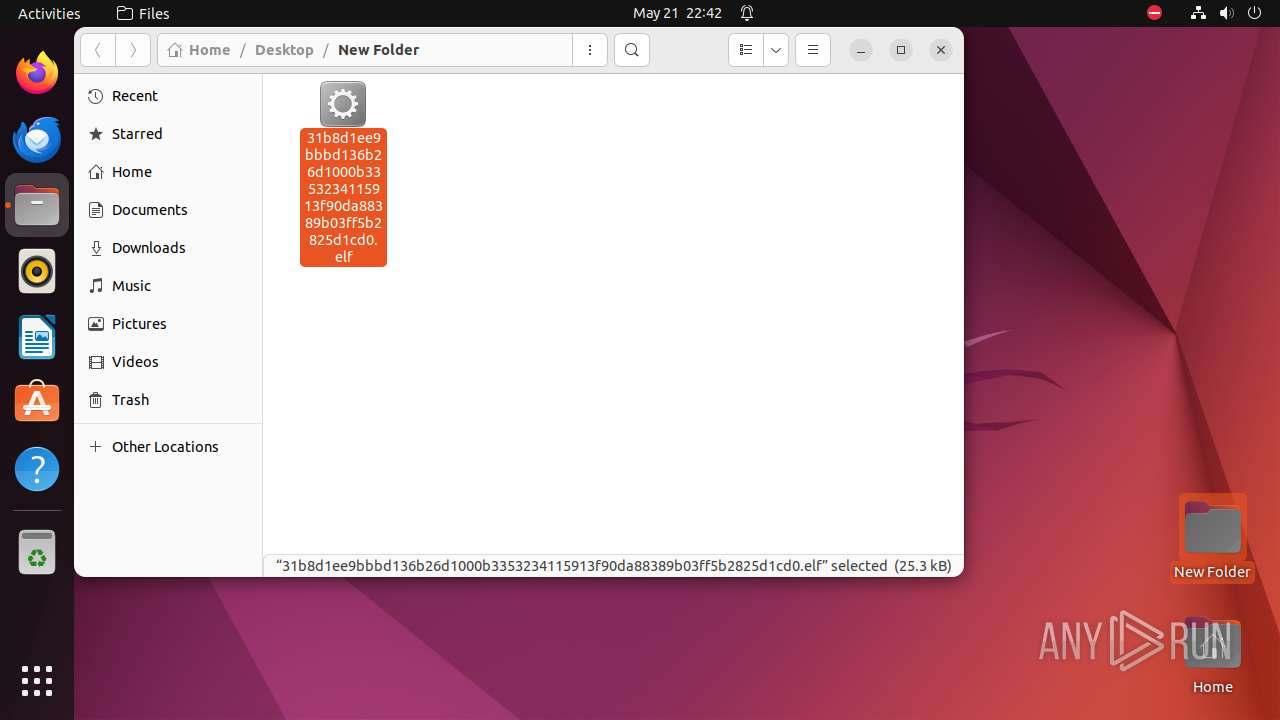
| File name: | 31b8d1ee9bbbd136b26d1000b3353234115913f90da88389b03ff5b2825d1cd0.elf |
| Full analysis: | https://app.any.run/tasks/d79d41e9-4b26-484e-8eb8-cd08357c547a |
| Verdict: | Malicious activity |
| Analysis date: | May 21, 2024, 21:41:36 |
| OS: | Ubuntu 22.04.2 |
| MIME: | application/x-executable |
| File info: | ELF 64-bit LSB executable, x86-64, version 1 (SYSV), statically linked, no section header |
| MD5: | C36198CF6A51D72798E6CC13F0C4609F |
| SHA1: | E7B264AFD633F6EBC5EE9D11B21DA74195F008D1 |
| SHA256: | 31B8D1EE9BBBD136B26D1000B3353234115913F90DA88389B03FF5B2825D1CD0 |
| SSDEEP: | 768:Qi4qgCeMKB8jxO4nLBSbO+tFe0UMFPFTuMqtYYftRs:/4mJKB8jxplSbt40UWMMqhf8 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks DMI information (probably VM detection)
- systemd-hostnamed (PID: 6221)
Executes commands using command-line interpreter
- bash (PID: 6187)
- sudo (PID: 6184)
Modifies file or directory owner
- sudo (PID: 6181)
Connects to unusual port
- 31b8d1ee9bbbd136b26d1000b3353234115913f90da88389b03ff5b2825d1cd0.elf (PID: 6282)
- 31b8d1ee9bbbd136b26d1000b3353234115913f90da88389b03ff5b2825d1cd0.elf (PID: 6194)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .o | | | ELF Executable and Linkable format (generic) (100) |
|---|
EXIF
EXE
| CPUArchitecture: | 64 bit |
|---|---|
| CPUByteOrder: | Little endian |
| ObjectFileType: | Executable file |
| CPUType: | AMD x86-64 |
Total processes
251
Monitored processes
34
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 6180 | /bin/sh -c "sudo chown user /home/user/Desktop/31b8d1ee9bbbd136b26d1000b3353234115913f90da88389b03ff5b2825d1cd0\.elf && chmod +x /home/user/Desktop/31b8d1ee9bbbd136b26d1000b3353234115913f90da88389b03ff5b2825d1cd0\.elf && DISPLAY=:0 sudo -i /home/user/Desktop/31b8d1ee9bbbd136b26d1000b3353234115913f90da88389b03ff5b2825d1cd0\.elf " | /bin/sh | — | any-guest-agent |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 6181 | sudo chown user /home/user/Desktop/31b8d1ee9bbbd136b26d1000b3353234115913f90da88389b03ff5b2825d1cd0.elf | /usr/bin/sudo | — | sh |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 6182 | chown user /home/user/Desktop/31b8d1ee9bbbd136b26d1000b3353234115913f90da88389b03ff5b2825d1cd0.elf | /usr/bin/chown | — | sudo |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 6183 | chmod +x /home/user/Desktop/31b8d1ee9bbbd136b26d1000b3353234115913f90da88389b03ff5b2825d1cd0.elf | /usr/bin/chmod | — | sh |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 6184 | sudo -i /home/user/Desktop/31b8d1ee9bbbd136b26d1000b3353234115913f90da88389b03ff5b2825d1cd0.elf | /usr/bin/sudo | — | sh |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 6185 | /home/user/Desktop/31b8d1ee9bbbd136b26d1000b3353234115913f90da88389b03ff5b2825d1cd0.elf | /home/user/Desktop/31b8d1ee9bbbd136b26d1000b3353234115913f90da88389b03ff5b2825d1cd0.elf | — | sudo |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 6186 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | 31b8d1ee9bbbd136b26d1000b3353234115913f90da88389b03ff5b2825d1cd0.elf |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 6187 | -bash --login -c \/home\/user\/Desktop\/31b8d1ee9bbbd136b26d1000b3353234115913f90da88389b03ff5b2825d1cd0\.elf | /usr/bin/bash | — | 31b8d1ee9bbbd136b26d1000b3353234115913f90da88389b03ff5b2825d1cd0.elf |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 6188 | sh -c "cat /usr/etc/debuginfod/*\.urls 2>/dev/null" | /usr/bin/sh | — | bash |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 6189 | tr \n " " | /usr/bin/tr | — | bash |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6250 | nautilus | /home/user/.local/share/nautilus/tags/meta.db-wal | — | |
MD5:— | SHA256:— | |||
| 6250 | nautilus | /home/user/.local/share/nautilus/tags/meta.db-shm | — | |
MD5:— | SHA256:— | |||
| 6250 | nautilus | /home/user/.local/share/nautilus/tags/.meta.isrunning | — | |
MD5:— | SHA256:— | |||
| 6203 | file-roller | /home/user/.local/share/recently-used.xbel.ZYV0N2 | — | |
MD5:— | SHA256:— | |||
| 6250 | nautilus | /home/user/.config/mimeapps.list.W1M4N2 | — | |
MD5:— | SHA256:— | |||
| 6250 | nautilus | /home/user/.local/share/recently-used.xbel.XUWYN2 | — | |
MD5:— | SHA256:— | |||
| 6250 | nautilus | /home/user/.config/mimeapps.list.B0P3N2 | — | |
MD5:— | SHA256:— | |||
| 6250 | nautilus | /home/user/.local/share/recently-used.xbel.XDQ0N2 | — | |
MD5:— | SHA256:— | |||
| 6318 | gedit | /home/user/.config/enchant/en.dic | — | |
MD5:— | SHA256:— | |||
| 6318 | gedit | /home/user/.config/enchant/en.exc | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
19
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 185.125.190.48:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
470 | avahi-daemon | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 185.125.190.48:80 | — | Canonical Group Limited | GB | unknown |
— | — | 185.125.188.54:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
— | — | 185.125.188.59:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
— | — | 185.125.188.55:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
6194 | 31b8d1ee9bbbd136b26d1000b3353234115913f90da88389b03ff5b2825d1cd0.elf | 141.11.92.115:3778 | — | ServiHosting Networks S.L. | US | malicious |
6229 | gvfsd-smb-browse | 192.168.100.255:137 | — | — | — | whitelisted |
6282 | 31b8d1ee9bbbd136b26d1000b3353234115913f90da88389b03ff5b2825d1cd0.elf | 141.11.92.115:3778 | — | ServiHosting Networks S.L. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.snapcraft.io |
| unknown |
134.100.168.192.in-addr.arpa |
| unknown |
connectivity-check.ubuntu.com |
| unknown |