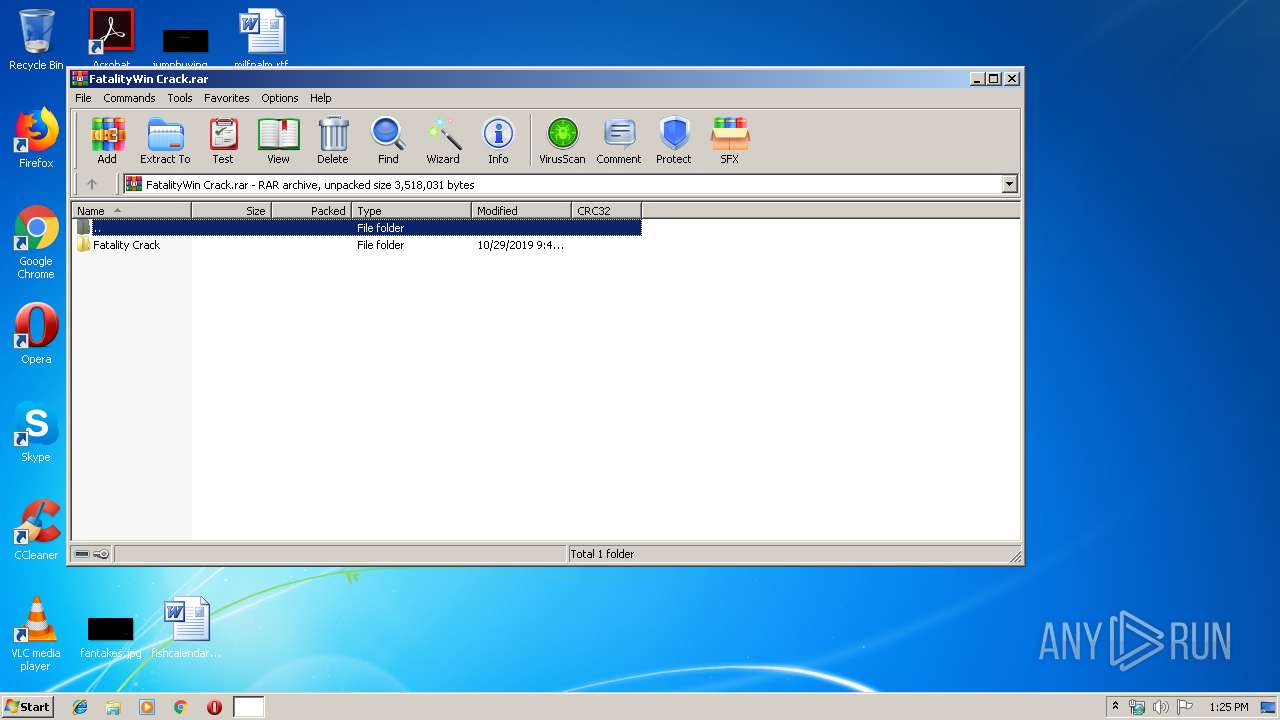
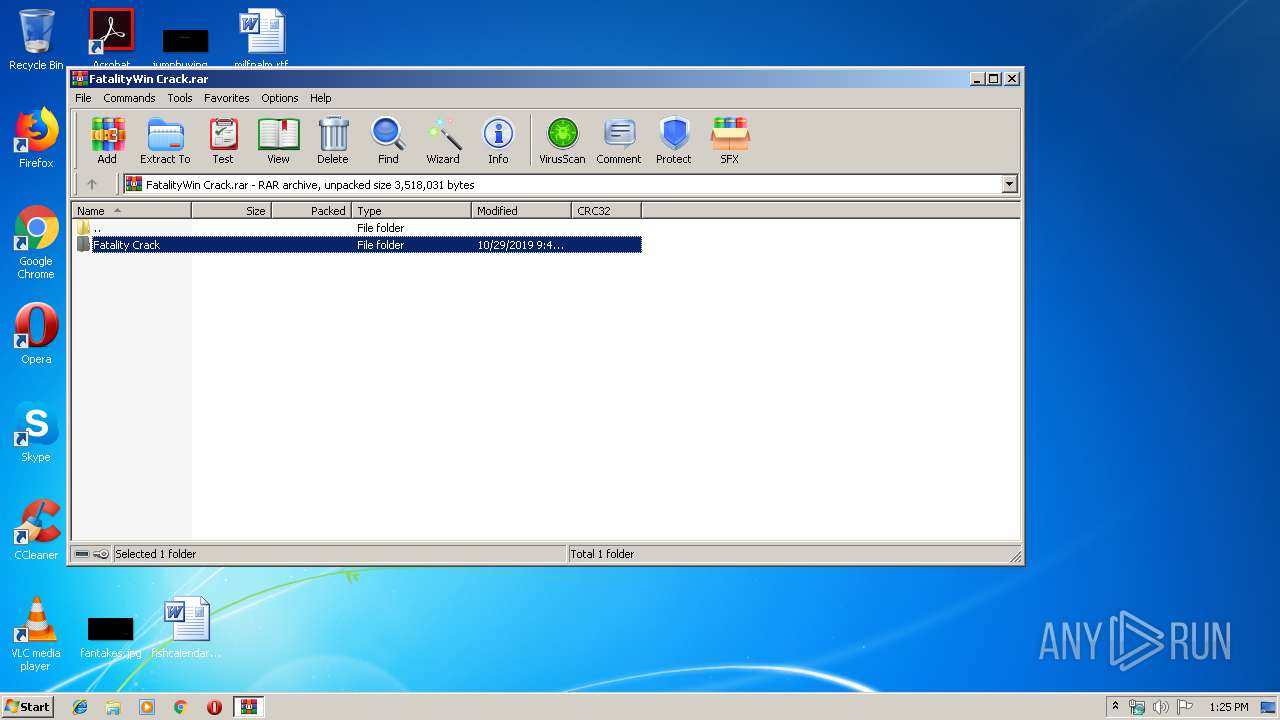
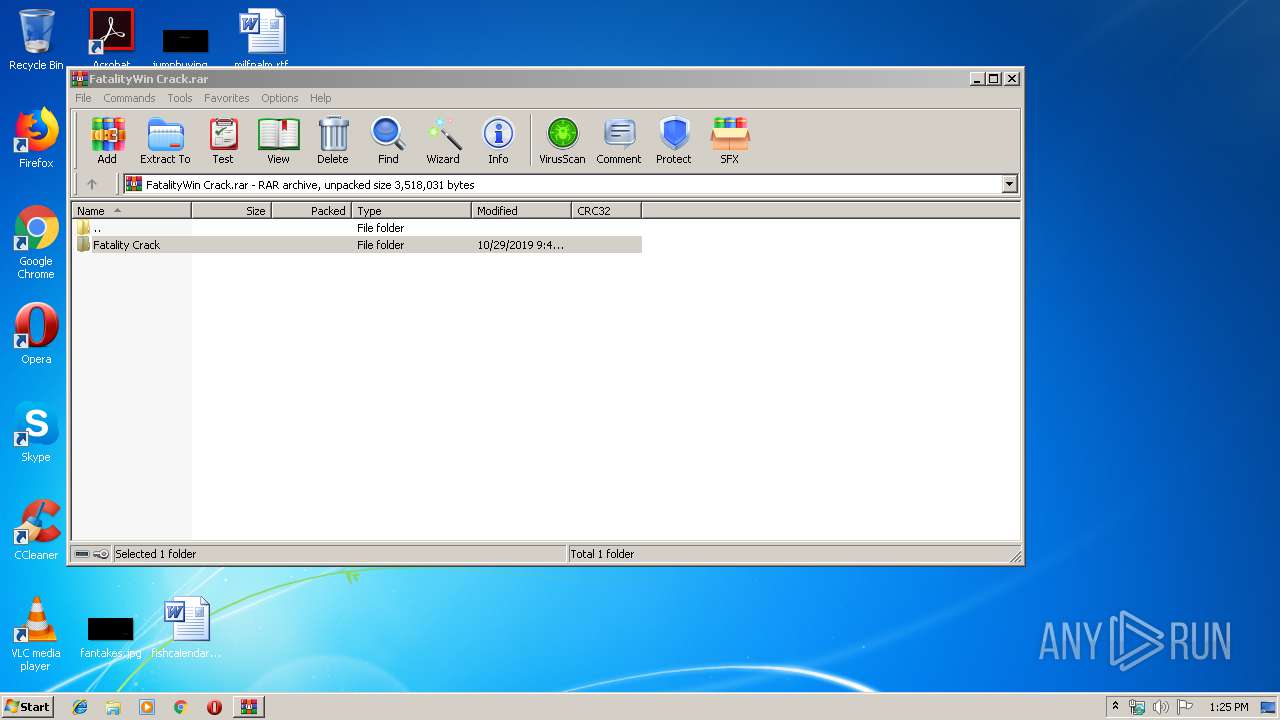
| File name: | FatalityWin Crack.rar |
| Full analysis: | https://app.any.run/tasks/c495da88-4131-4112-9aab-dace39c319f4 |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | November 16, 2019, 13:25:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | E5A0E16F0A81ED7ED51F888E15F4ECE3 |
| SHA1: | 8B3AC9DC70E2FEFC0F80C444B5FF340BB24E55CE |
| SHA256: | 31943CC119C9AEB5C0B23B329FA33CABEEAB10E5E9D845441D7CD5CF24719513 |
| SSDEEP: | 24576:yiPBhsv1ohPnfdTVO5I2Qm/S0jsUC0zweObR2qgU0wTEpIuiN:yiPE1oXQINprUC0n0R2qgJPpIuiN |
MALICIOUS
Stealing of credential data
- fatalityLauncher.exe (PID: 332)
SUSPICIOUS
Application launched itself
- fatalityLauncher.exe (PID: 2368)
Creates files in the program directory
- fatalityLauncher.exe (PID: 332)
Reads Environment values
- fatalityLauncher.exe (PID: 332)
Reads the cookies of Google Chrome
- fatalityLauncher.exe (PID: 332)
Starts CMD.EXE for commands execution
- fatalityLauncher.exe (PID: 332)
Starts CHOICE.EXE (used to create a delay)
- cmd.exe (PID: 3080)
INFO
Manual execution by user
- fatalityLauncher.exe (PID: 2368)
- rundll32.exe (PID: 3876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
45
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 332 | "C:\Users\admin\Desktop\Fatality Crack\fatalityLauncher.exe" | C:\Users\admin\Desktop\Fatality Crack\fatalityLauncher.exe | fatalityLauncher.exe | ||||||||||||
User: admin Company: 5pp1Zs5xUzqK1sすBLこBzHかBrLpW9JoBuRKo2Ys元tvvs91s気OWoHvvWB5SR4tKtYBQK Integrity Level: MEDIUM Description: 1v3SDvx68K9K7tXnで47o2H8YntAoに2OかQXZYsOHKで92CQ4YS5K6urは2tzWXVDzzHP8 Exit code: 0 Version: 5.1.5.2 Modules
| |||||||||||||||
| 640 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\FatalityWin Crack.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2368 | "C:\Users\admin\Desktop\Fatality Crack\fatalityLauncher.exe" | C:\Users\admin\Desktop\Fatality Crack\fatalityLauncher.exe | — | explorer.exe | |||||||||||
User: admin Company: 5pp1Zs5xUzqK1sすBLこBzHかBrLpW9JoBuRKo2Ys元tvvs91s気OWoHvvWB5SR4tKtYBQK Integrity Level: MEDIUM Description: 1v3SDvx68K9K7tXnで47o2H8YntAoに2OかQXZYsOHKで92CQ4YS5K6urは2tzWXVDzzHP8 Exit code: 0 Version: 5.1.5.2 Modules
| |||||||||||||||
| 2912 | choice /C Y /N /D Y /T | C:\Windows\system32\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Offers the user a choice Exit code: 255 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3080 | "C:\Windows\System32\cmd.exe" /C choice /C Y /N /D Y /T & Del "fatalityLauncher.exe" | C:\Windows\System32\cmd.exe | — | fatalityLauncher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3876 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\GDIPFONTCACHEV1.DAT | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
565
Read events
526
Write events
39
Delete events
0
Modification events
| (PID) Process: | (640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (640) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\FatalityWin Crack.rar | |||
| (PID) Process: | (640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (640) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (332) fatalityLauncher.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\fatalityLauncher_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (332) fatalityLauncher.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\fatalityLauncher_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
0
Suspicious files
2
Text files
8
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 640 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa640.25963\Fatality Crack\fatalityLauncher.exe | — | |
MD5:— | SHA256:— | |||
| 640 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa640.25963\Fatality Crack\gui-57.dll | — | |
MD5:— | SHA256:— | |||
| 640 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa640.25963\Fatality Crack\icuuc.dll | — | |
MD5:— | SHA256:— | |||
| 640 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa640.25963\Fatality Crack\ReadMe.txt | — | |
MD5:— | SHA256:— | |||
| 332 | fatalityLauncher.exe | C:\Users\admin\AppData\Local\Temp\s4dgdtadpgu.fv | — | |
MD5:— | SHA256:— | |||
| 332 | fatalityLauncher.exe | C:\Users\admin\AppData\Local\Temp\v5y1puhfa5j.fv | — | |
MD5:— | SHA256:— | |||
| 332 | fatalityLauncher.exe | C:\Users\admin\AppData\Local\U3LZDGVTLKNOYXJBXQ\FuckTheWorld\Misc\ReadMe.txt | — | |
MD5:— | SHA256:— | |||
| 332 | fatalityLauncher.exe | C:\Users\admin\AppData\Local\U3LZDGVTLKNOYXJBXQ\FuckTheWorld\Browsers\AutoFill.txt | text | |
MD5:— | SHA256:— | |||
| 332 | fatalityLauncher.exe | C:\Users\admin\AppData\Local\U3LZDGVTLKNOYXJBXQ\FuckTheWorld\image.png | image | |
MD5:— | SHA256:— | |||
| 332 | fatalityLauncher.exe | C:\ProgramData\debug.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
332 | fatalityLauncher.exe | GET | 200 | 31.131.30.43:80 | http://hokage.ru/antivirus.php | US | text | 31 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
332 | fatalityLauncher.exe | 31.131.30.43:80 | hokage.ru | PE Skurykhin Mukola Volodumurovuch | US | malicious |
332 | fatalityLauncher.exe | 176.10.124.134:443 | soranoproject.com | SOFTplus Entwicklungen GmbH | CH | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
hokage.ru |
| malicious |
soranoproject.com |
| suspicious |