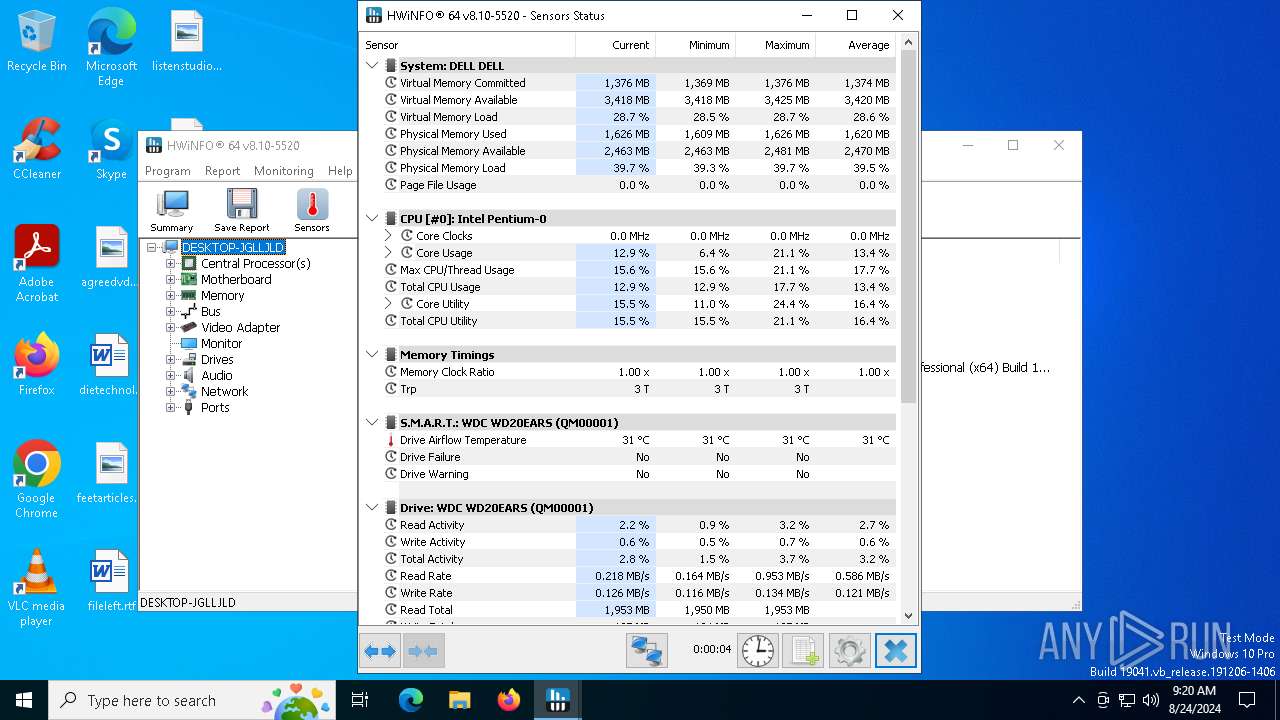
| File name: | HWiNFO64.exe |
| Full analysis: | https://app.any.run/tasks/4010128f-e3bd-401d-b401-1d147f04bb30 |
| Verdict: | Malicious activity |
| Analysis date: | August 24, 2024, 09:20:03 |
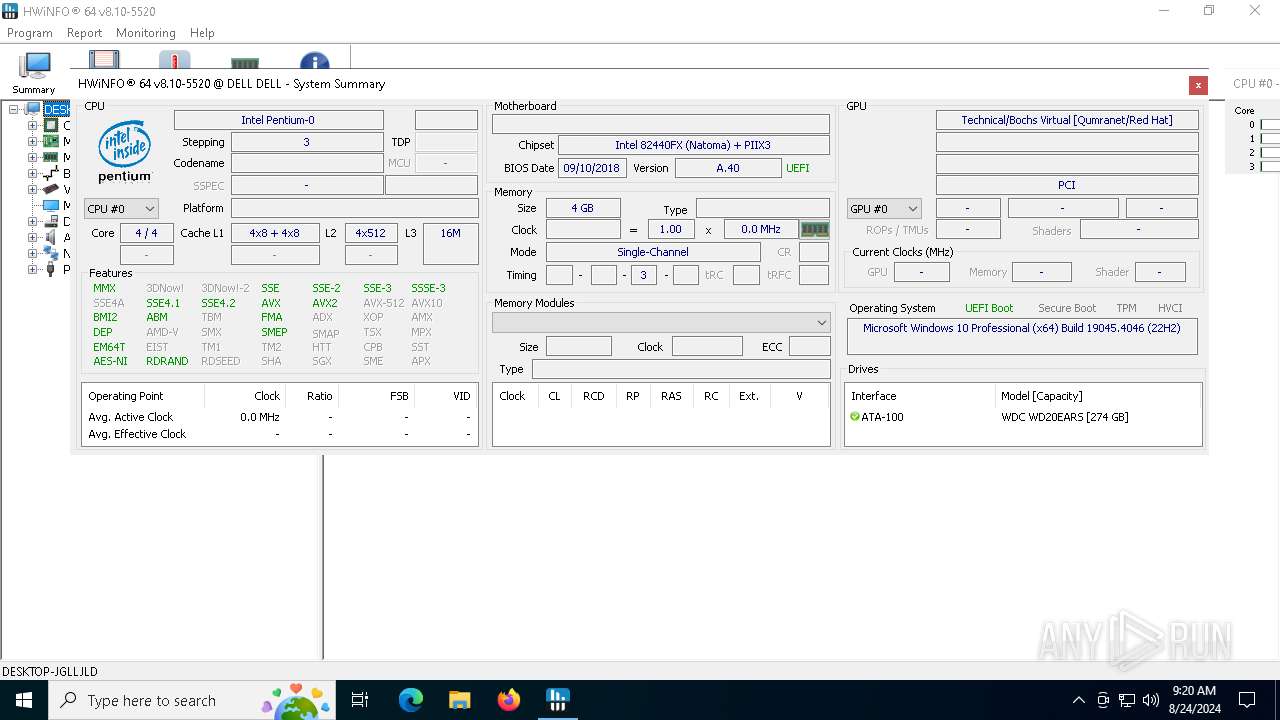
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | 6432D4D9A2242765E663FC8E69DFD205 |
| SHA1: | DBA583B6A8F1281DE8870C3335B32228CA71CC3C |
| SHA256: | 317FCCF2E5F208F23269BEAAC9D16A10B8A5217ECC713088902B36B9B0643582 |
| SSDEEP: | 98304:1LtUMWNZscXpuC4+q6Yp1b5fRql+xsK2TIER6879N09HRFiNMoFbMfzNRvUYSEOS:0QX6bQJPln+haG |
MALICIOUS
No malicious indicators.SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- HWiNFO64.exe (PID: 6760)
Drops the executable file immediately after the start
- HWiNFO64.exe (PID: 6760)
Executable content was dropped or overwritten
- HWiNFO64.exe (PID: 6760)
The process checks if it is being run in the virtual environment
- HWiNFO64.exe (PID: 6760)
Reads the BIOS version
- HWiNFO64.exe (PID: 6760)
Reads security settings of Internet Explorer
- HWiNFO64.exe (PID: 6760)
Checks Windows Trust Settings
- HWiNFO64.exe (PID: 6760)
There is functionality for VM detection (antiVM strings)
- HWiNFO64.exe (PID: 6760)
INFO
Checks supported languages
- HWiNFO64.exe (PID: 6760)
Reads the computer name
- HWiNFO64.exe (PID: 6760)
Create files in a temporary directory
- HWiNFO64.exe (PID: 6760)
Reads CPU info
- HWiNFO64.exe (PID: 6760)
Checks proxy server information
- HWiNFO64.exe (PID: 6760)
Reads the software policy settings
- HWiNFO64.exe (PID: 6760)
Reads the machine GUID from the registry
- HWiNFO64.exe (PID: 6760)
Creates files or folders in the user directory
- HWiNFO64.exe (PID: 6760)
UPX packer has been detected
- HWiNFO64.exe (PID: 6760)
Reads the time zone
- HWiNFO64.exe (PID: 6760)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (47) |
|---|---|---|
| .exe | | | UPX compressed Win32 Executable (46.1) |
| .exe | | | Generic Win/DOS Executable (3.4) |
| .exe | | | DOS Executable Generic (3.4) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:08:20 10:43:58+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.29 |
| CodeSize: | 9342976 |
| InitializedDataSize: | 114688 |
| UninitializedDataSize: | 19431424 |
| EntryPoint: | 0x1b70920 |
| OSVersion: | 6.1 |
| ImageVersion: | - |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 8.10.5520.0 |
| ProductVersionNumber: | 8.10.5520.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | REALiX s.r.o. |
| FileVersion: | 8.10-5520 |
| ProductVersion: | 8.10-5520 |
| LegalCopyright: | Copyright (c)1999-2024 Martin Malik, REALiX s.r.o. |
| InternalName: | HWiNFO® 64 |
| FileDescription: | HWiNFO® 64 (x64) |
| OriginalFileName: | HWiNFO64.EXE |
| ProductName: | Hardware Info Program for x64 (HWiNFO® 64) |
Total processes
126
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6712 | "C:\Users\admin\AppData\Local\Temp\HWiNFO64.exe" | C:\Users\admin\AppData\Local\Temp\HWiNFO64.exe | — | explorer.exe | |||||||||||
User: admin Company: REALiX s.r.o. Integrity Level: MEDIUM Description: HWiNFO® 64 (x64) Exit code: 3221226540 Version: 8.10-5520 Modules
| |||||||||||||||
| 6760 | "C:\Users\admin\AppData\Local\Temp\HWiNFO64.exe" | C:\Users\admin\AppData\Local\Temp\HWiNFO64.exe | explorer.exe | ||||||||||||
User: admin Company: REALiX s.r.o. Integrity Level: HIGH Description: HWiNFO® 64 (x64) Version: 8.10-5520 Modules
| |||||||||||||||
Total events
6 962
Read events
4 743
Write events
48
Delete events
2 171
Modification events
| (PID) Process: | (6760) HWiNFO64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6760) HWiNFO64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6760) HWiNFO64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6760) HWiNFO64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6760) HWiNFO64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\HWiNFO64\Summary\Clocks |
| Operation: | write | Name: | WndTopX |
Value: 1217 | |||
| (PID) Process: | (6760) HWiNFO64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\HWiNFO64\Summary\Clocks |
| Operation: | write | Name: | WndTopY |
Value: 68 | |||
| (PID) Process: | (6760) HWiNFO64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\HWiNFO64\Summary\Clocks |
| Operation: | write | Name: | WndBottomX |
Value: 1480 | |||
| (PID) Process: | (6760) HWiNFO64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\HWiNFO64\Summary\Clocks |
| Operation: | write | Name: | WndBottomY |
Value: 182 | |||
| (PID) Process: | (6760) HWiNFO64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\HWiNFO64\Summary\Clocks |
| Operation: | write | Name: | WndStyle |
Value: | |||
| (PID) Process: | (6760) HWiNFO64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\HWiNFO64\Summary\Clocks |
| Operation: | write | Name: | Scaling |
Value: 100 | |||
Executable files
1
Suspicious files
9
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6760 | HWiNFO64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:7FB5FA1534DCF77F2125B2403B30A0EE | SHA256:33A39E9EC2133230533A686EC43760026E014A3828C703707ACBC150FE40FD6F | |||
| 6760 | HWiNFO64.exe | C:\Users\admin\AppData\Local\Temp\HWiNFO_x64_202.sys | executable | |
MD5:45C0EABA8CA43D50F461A0B64D01F4FF | SHA256:EA48FDB863B52E1A2BA8C001C8C5393B51C2BE349CD0FC3DEEEA50C452E87203 | |||
| 6760 | HWiNFO64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:E42DB58BE10174EFA0F190909E6A3822 | SHA256:17666AF1633F028B961266442C02BAC19CFA537699CF4492FEAF11A50632BB6F | |||
| 6760 | HWiNFO64.exe | C:\Windows\INF\basicrender.PNF | binary | |
MD5:8567F128605CC616A38D0870D077D165 | SHA256:7B2D28D317F49EED7BC242241E54EB3FFFB512C5FB6F719C4F5E9395E6B1F533 | |||
| 6760 | HWiNFO64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:5FBCEA6829DE9B908696DFD5038CA449 | SHA256:B5403DF169DDDC41D5001EA2CE770A1EC5D3BA1F70F10F823943A72162DF9C9E | |||
| 6760 | HWiNFO64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | der | |
MD5:971C514F84BBA0785F80AA1C23EDFD79 | SHA256:F157ED17FCAF8837FA82F8B69973848C9B10A02636848F995698212A08F31895 | |||
| 6760 | HWiNFO64.exe | C:\Windows\INF\basicdisplay.PNF | binary | |
MD5:914DCB989709A0CE3F4B24A4CD147F1A | SHA256:C2FEE0EAD23C7B3B509FDDE94DDD6A549F999F364C5CA9D09AC084F22BC0ECB4 | |||
| 6760 | HWiNFO64.exe | C:\Users\admin\AppData\Local\Temp\HWiNFO64.INI | text | |
MD5:31EA0D720B02F5BE9A0A8C843FA525B6 | SHA256:2B52116A161DB87EAD7FBA5329E113610A39EC5183D713A9D9A7222FE657C949 | |||
| 6760 | HWiNFO64.exe | C:\Windows\INF\machine.PNF | binary | |
MD5:2832AC38B3F7C5EAE6490E5DB414B98E | SHA256:DFE57032C2FC69400AD3CA6D96566387B4336FD19A363F4F32041EC81E35F12B | |||
| 6760 | HWiNFO64.exe | C:\Windows\INF\display.PNF | binary | |
MD5:AA07E83C9A138E09DE7F06CE574BA4A4 | SHA256:E67D1A09E66448F2E3C0862851AC1C61ED90CB6D45AFBD675FB854F7CA9844BA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
23
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6760 | HWiNFO64.exe | GET | 200 | 172.217.16.195:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
6760 | HWiNFO64.exe | GET | 200 | 172.217.16.195:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
5468 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6612 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
5284 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3840 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5284 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6760 | HWiNFO64.exe | 172.67.205.235:443 | www.hwinfo.com | CLOUDFLARENET | US | unknown |
6760 | HWiNFO64.exe | 172.217.16.195:80 | c.pki.goog | GOOGLE | US | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.hwinfo.com |
| whitelisted |
c.pki.goog |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |