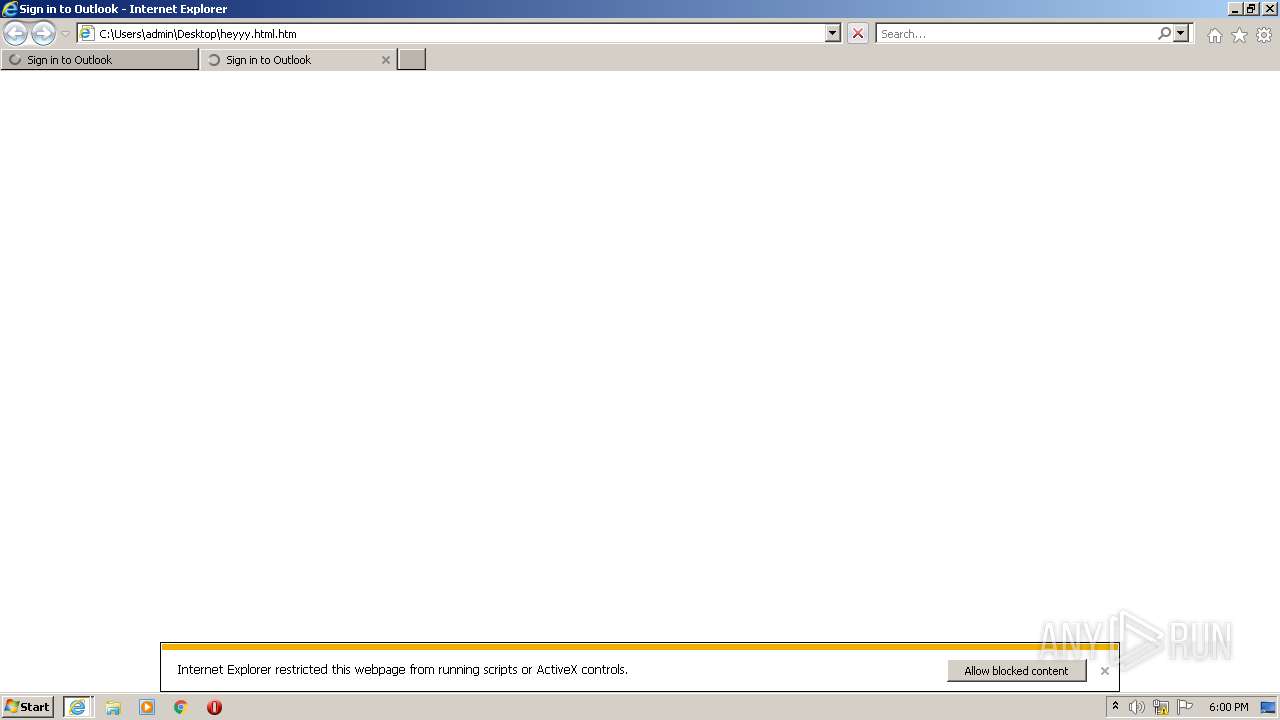
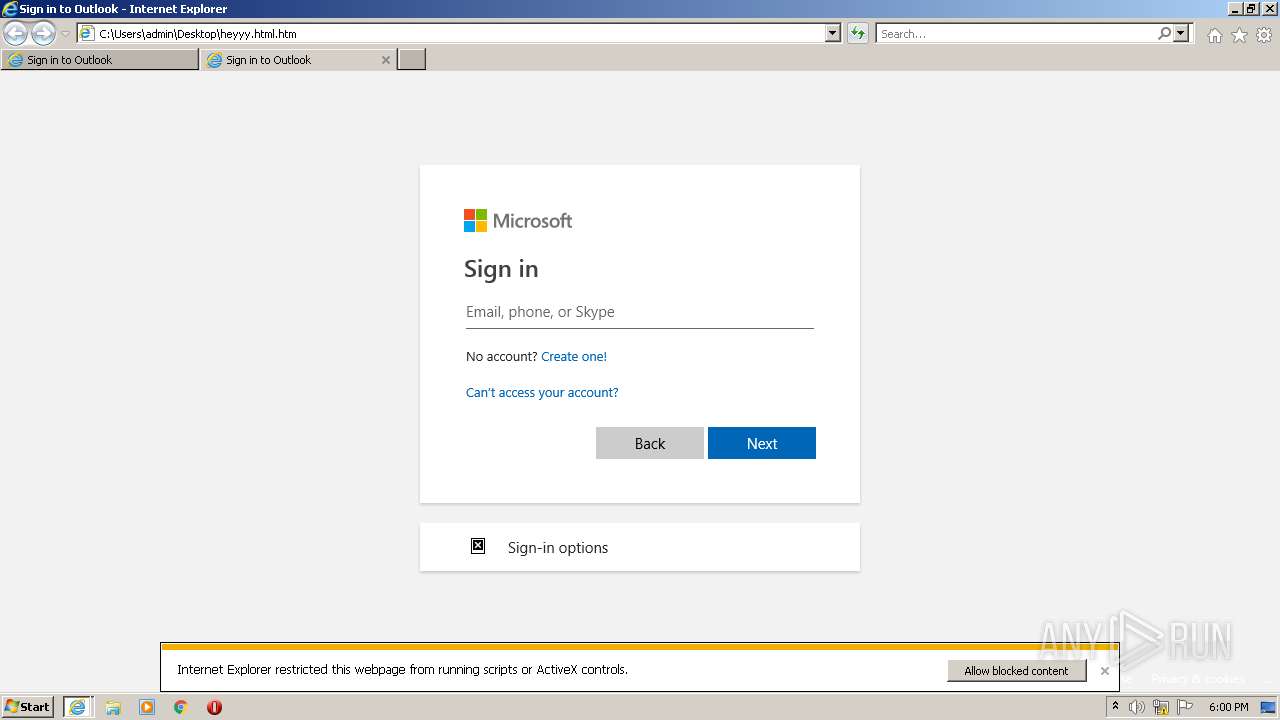
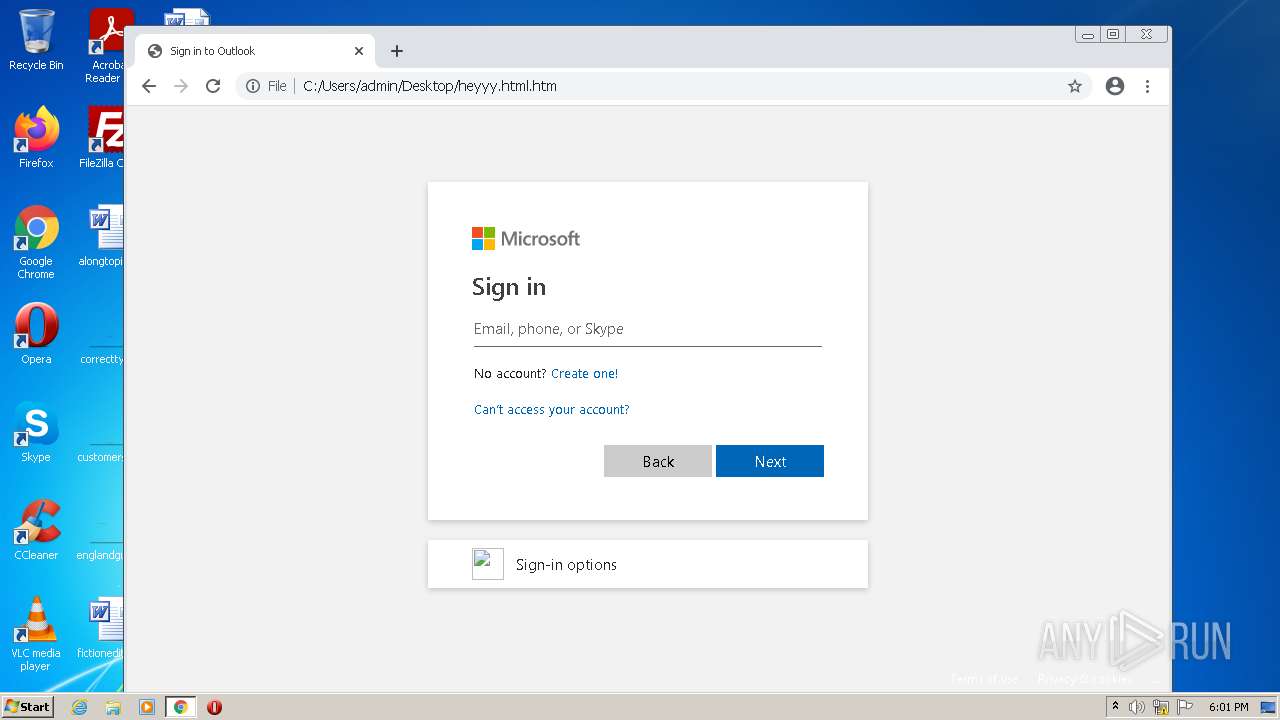
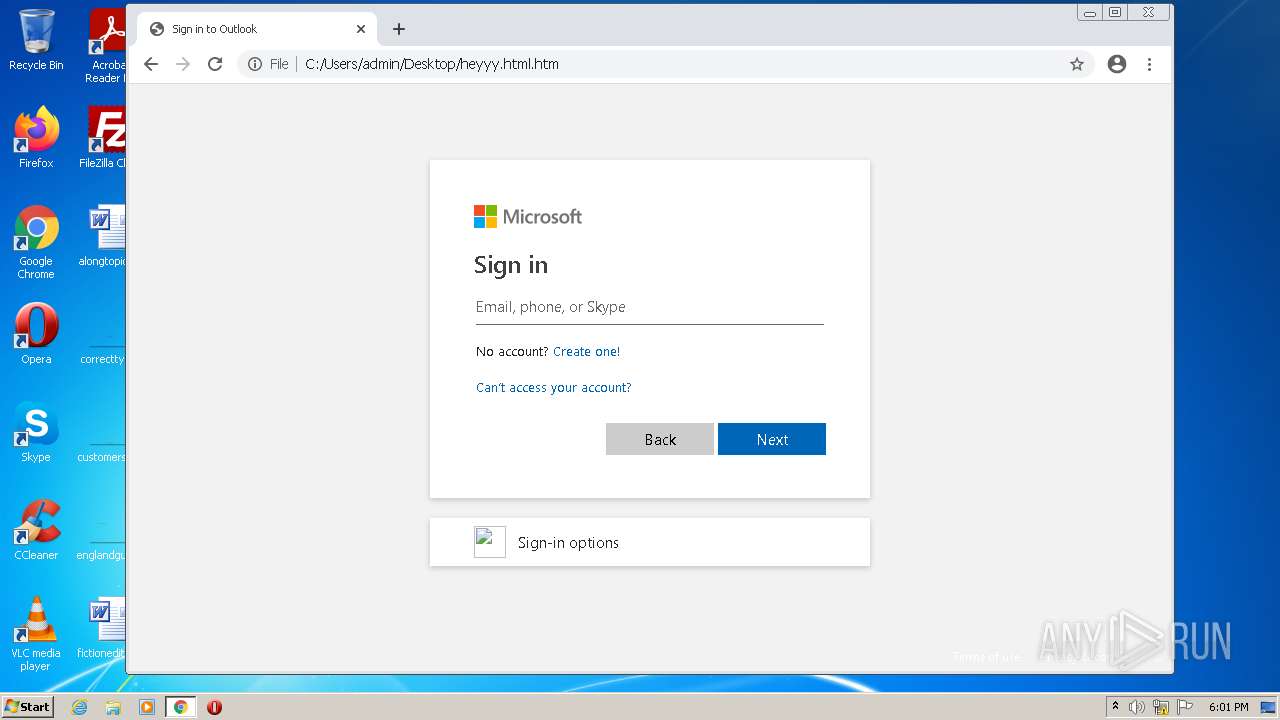
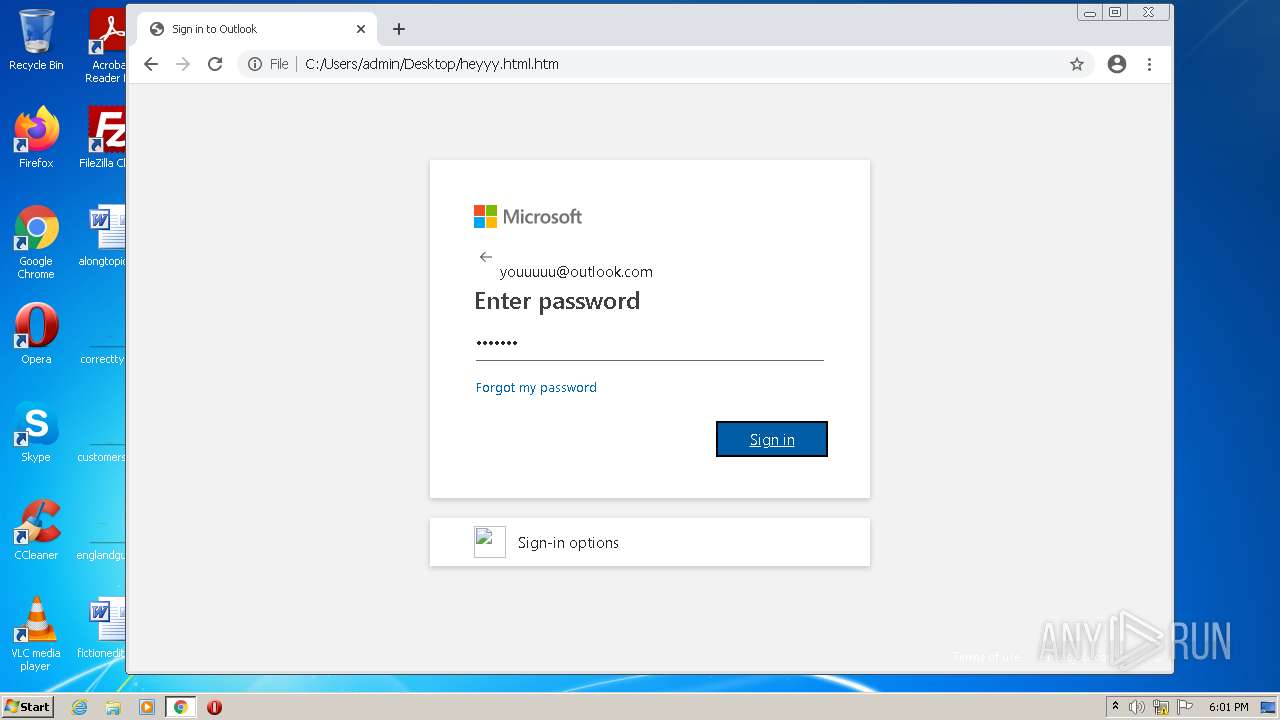
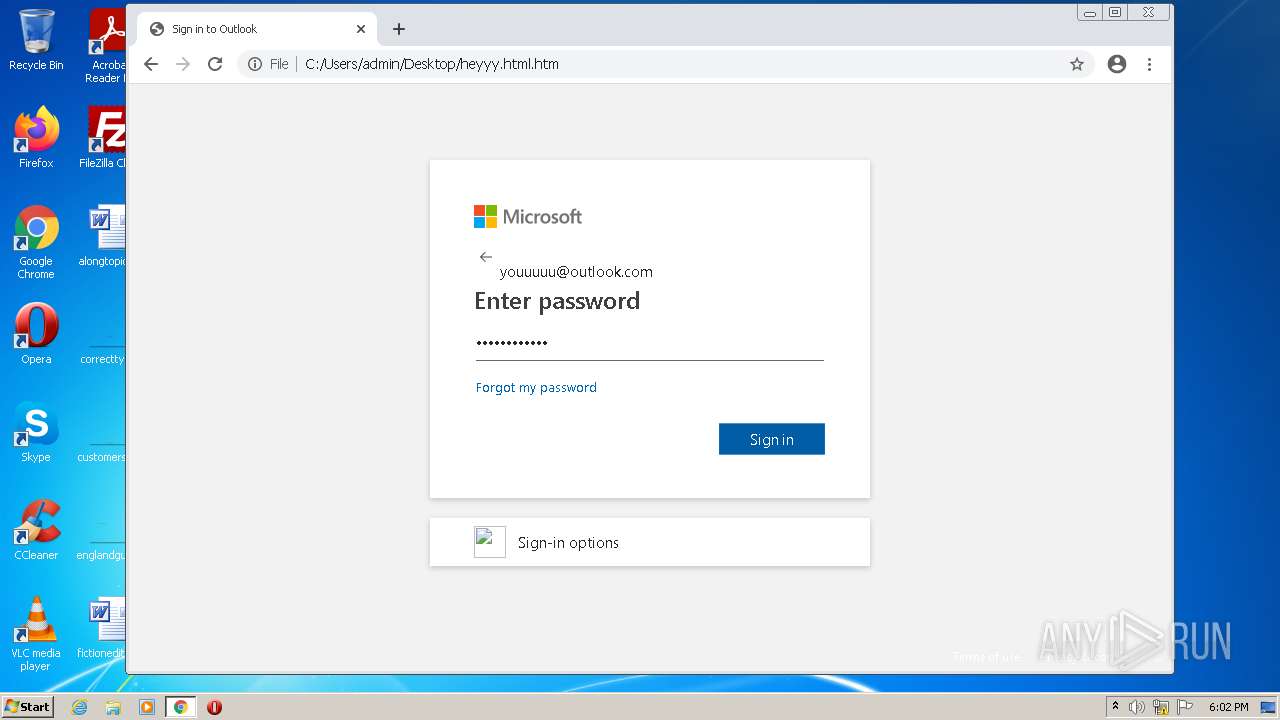
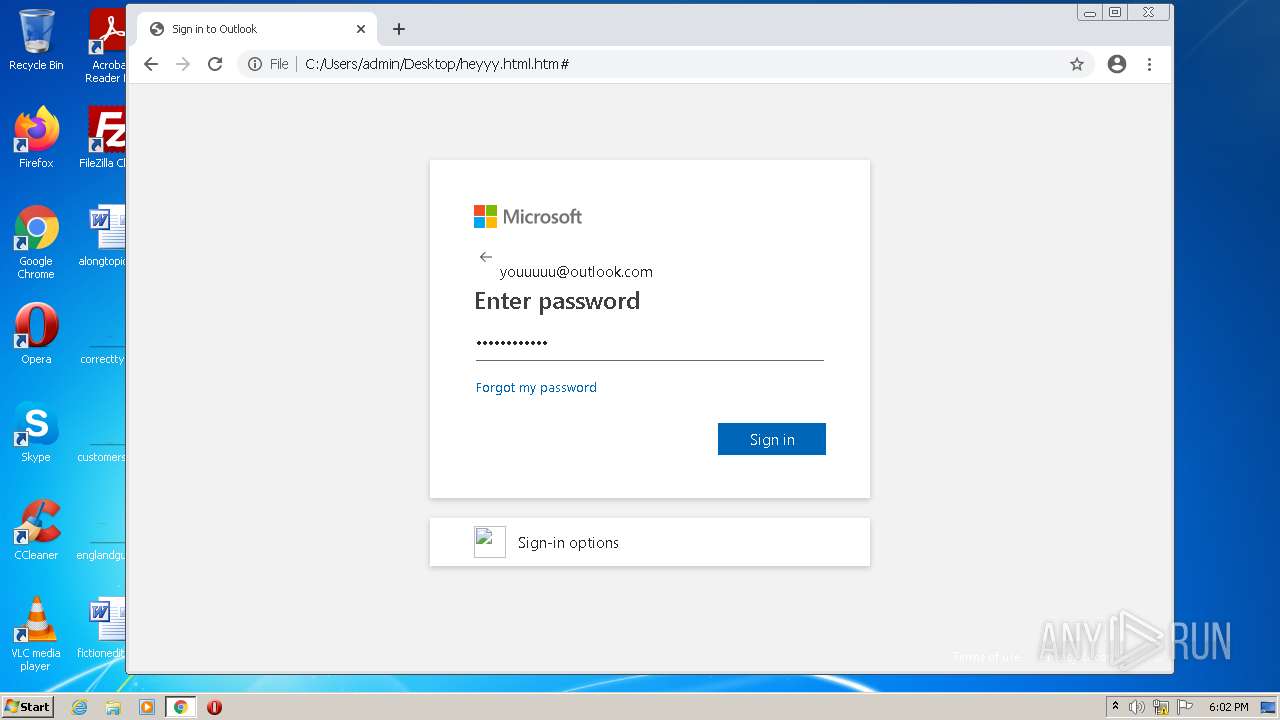
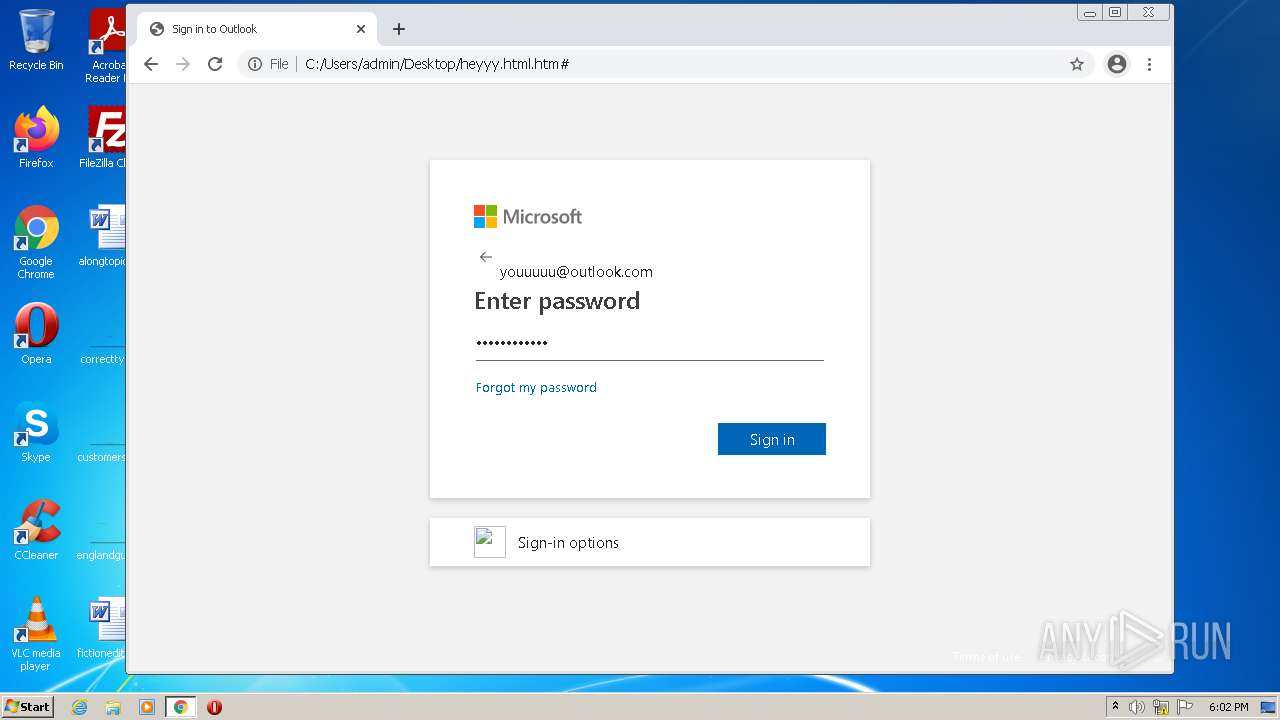
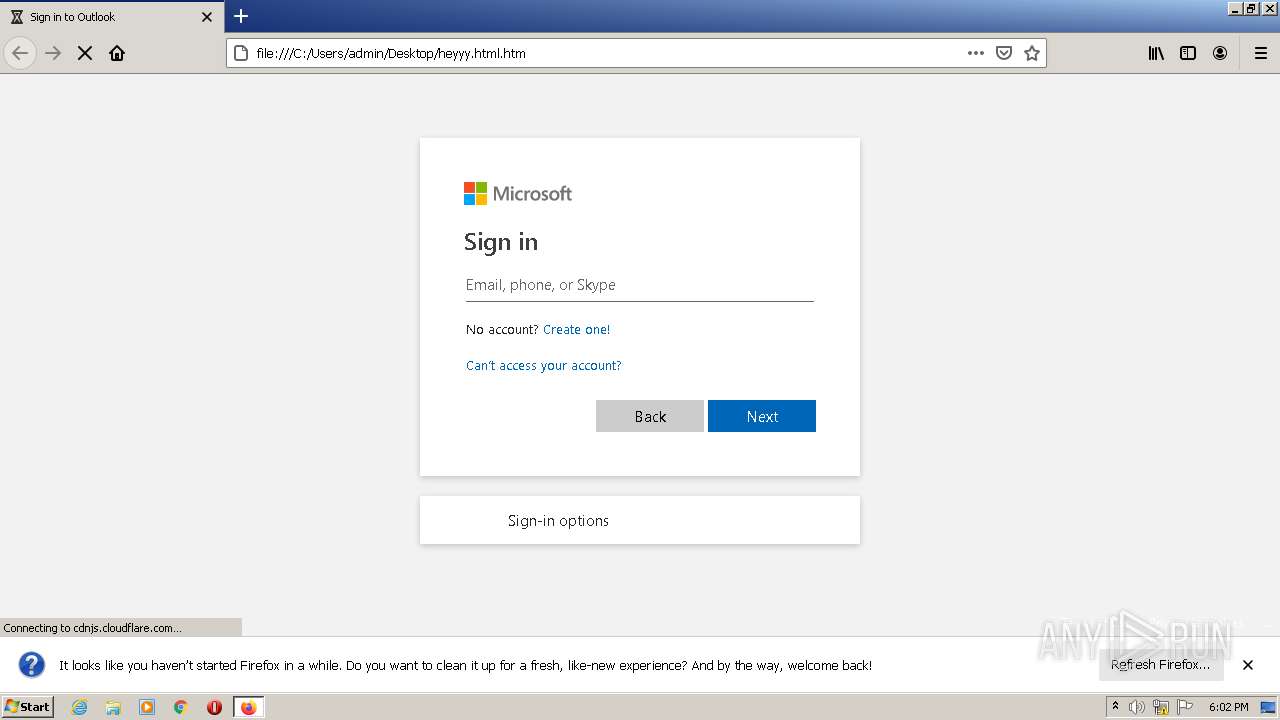
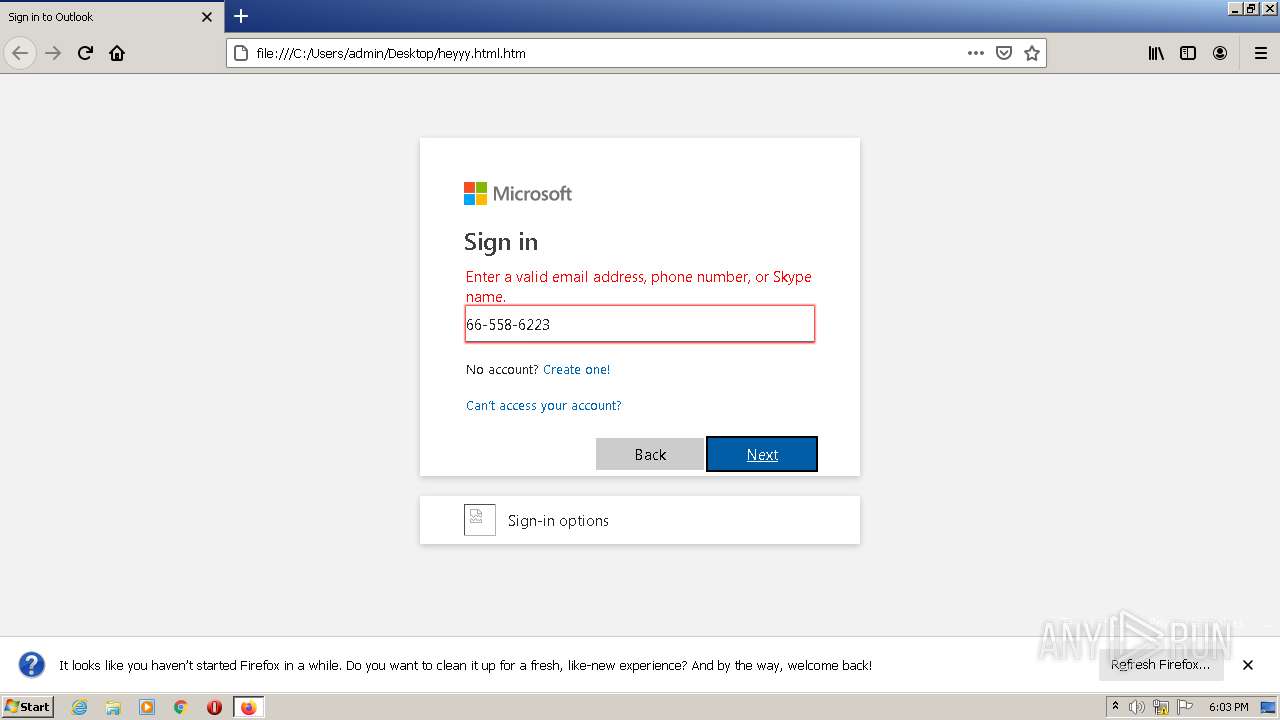
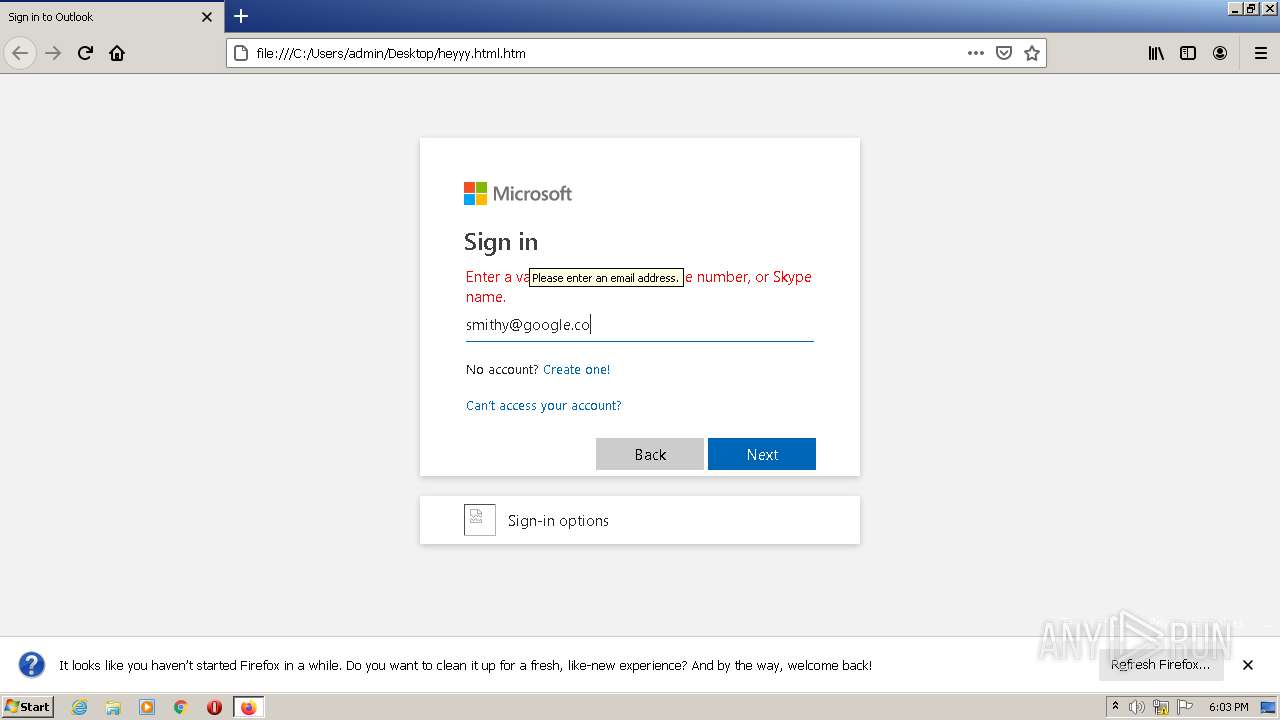
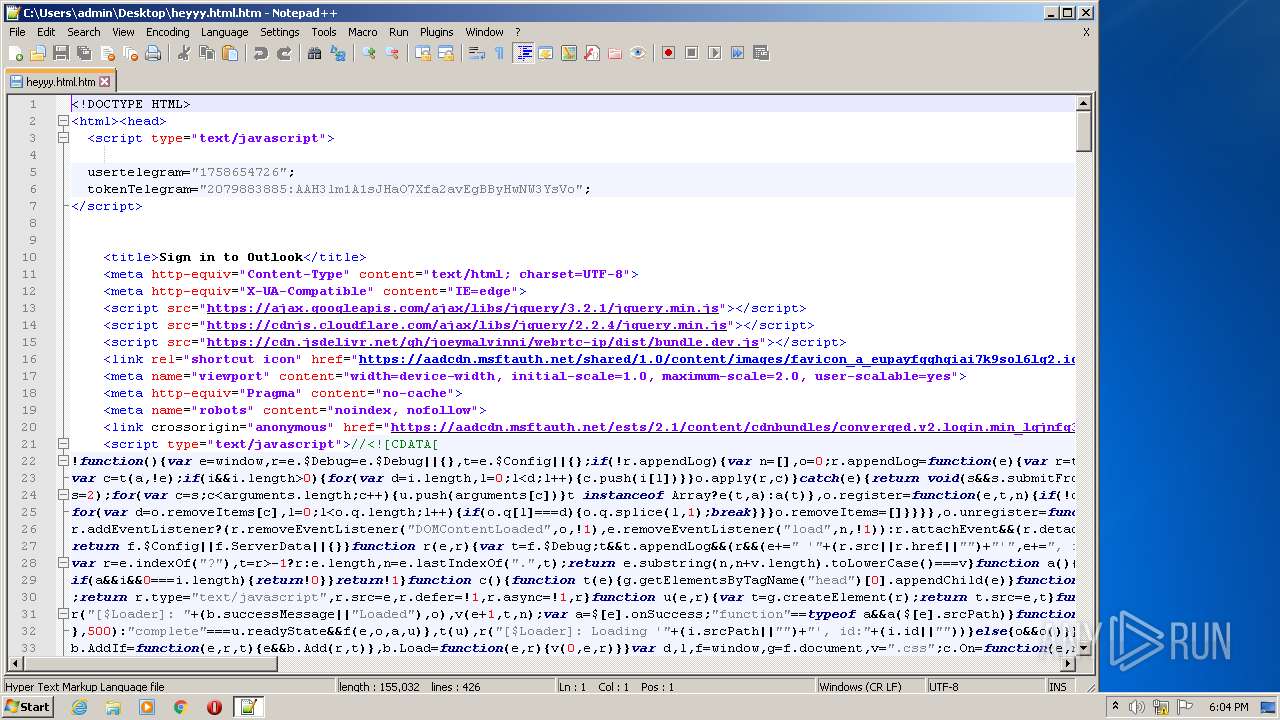
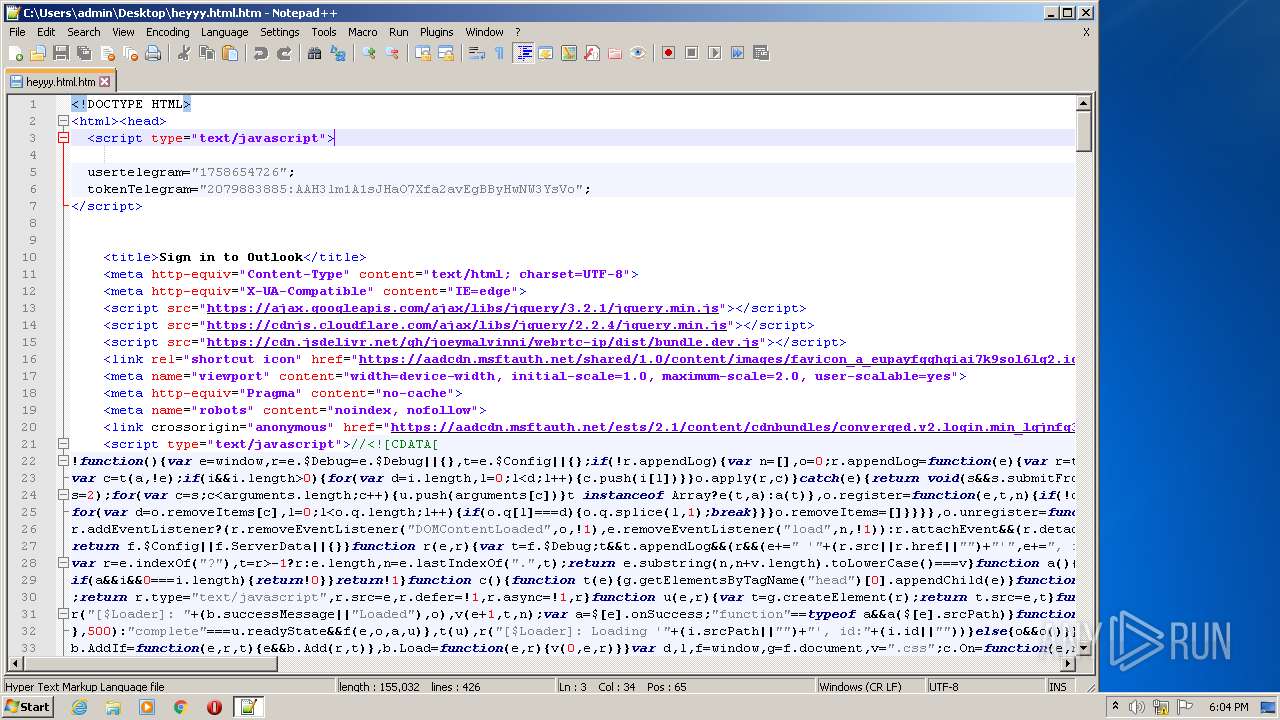
| File name: | heyyy.html |
| Full analysis: | https://app.any.run/tasks/a29b9f57-7521-47b3-a987-809ee0f88f63 |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 18:00:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with very long lines, with CRLF line terminators |
| MD5: | 09BFEC2FF940DEAC8CDFC0EFE2EFAC9B |
| SHA1: | 02E3DA2A9683F0CD13F404B775C16A6CF87B83DE |
| SHA256: | 3179F925294771977304BCB7936C03EC31C38A9FBAE8CD80A59150702C06B11F |
| SSDEEP: | 1536:WsFv6eBoRbjQHuhw+E3mazA/PWrF7qvEAFiQcpm8tpHzyJRT9UEpdm3BPdBF:UxpQBDbyJ3UEpdmRN |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3160)
- iexplore.exe (PID: 3060)
Checks supported languages
- notepad++.exe (PID: 4012)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2368)
Checks supported languages
- iexplore.exe (PID: 2368)
- iexplore.exe (PID: 3160)
- iexplore.exe (PID: 3060)
- chrome.exe (PID: 3640)
- chrome.exe (PID: 712)
- chrome.exe (PID: 2452)
- iexplore.exe (PID: 3204)
- chrome.exe (PID: 3224)
- chrome.exe (PID: 964)
- chrome.exe (PID: 2848)
- chrome.exe (PID: 356)
- chrome.exe (PID: 2076)
- chrome.exe (PID: 2244)
- chrome.exe (PID: 3980)
- chrome.exe (PID: 2480)
- chrome.exe (PID: 1088)
- chrome.exe (PID: 3580)
- chrome.exe (PID: 4004)
- firefox.exe (PID: 2152)
- firefox.exe (PID: 3608)
- firefox.exe (PID: 1508)
- firefox.exe (PID: 2964)
- firefox.exe (PID: 3276)
- firefox.exe (PID: 2804)
- firefox.exe (PID: 2948)
Reads the computer name
- iexplore.exe (PID: 3160)
- iexplore.exe (PID: 2368)
- chrome.exe (PID: 3640)
- iexplore.exe (PID: 3060)
- iexplore.exe (PID: 3204)
- chrome.exe (PID: 3224)
- chrome.exe (PID: 2452)
- chrome.exe (PID: 2076)
- chrome.exe (PID: 2244)
- chrome.exe (PID: 1088)
- chrome.exe (PID: 2480)
- chrome.exe (PID: 4004)
- firefox.exe (PID: 2152)
- firefox.exe (PID: 1508)
- firefox.exe (PID: 2964)
- firefox.exe (PID: 3276)
- firefox.exe (PID: 2804)
- firefox.exe (PID: 2948)
Application launched itself
- iexplore.exe (PID: 2368)
- chrome.exe (PID: 3640)
- iexplore.exe (PID: 3160)
- firefox.exe (PID: 3608)
- firefox.exe (PID: 2152)
Manual execution by user
- chrome.exe (PID: 3640)
- firefox.exe (PID: 3608)
- notepad++.exe (PID: 4012)
Reads the hosts file
- chrome.exe (PID: 3640)
- chrome.exe (PID: 3224)
Reads internet explorer settings
- iexplore.exe (PID: 3160)
- iexplore.exe (PID: 3060)
Reads the date of Windows installation
- iexplore.exe (PID: 2368)
- chrome.exe (PID: 4004)
- firefox.exe (PID: 2152)
Reads CPU info
- firefox.exe (PID: 2152)
Creates files in the user directory
- firefox.exe (PID: 2152)
Creates files in the program directory
- firefox.exe (PID: 2152)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .htm/html | | | HyperText Markup Language with DOCTYPE (80.6) |
|---|---|---|
| .html | | | HyperText Markup Language (19.3) |
EXIF
HTML
| Robots: | noindex, nofollow |
|---|---|
| Pragma: | no-cache |
| viewport: | width=device-width, initial-scale=1.0, maximum-scale=2.0, user-scalable=yes |
| HTTPEquivXUACompatible: | IE=edge |
| ContentType: | text/html; charset=UTF-8 |
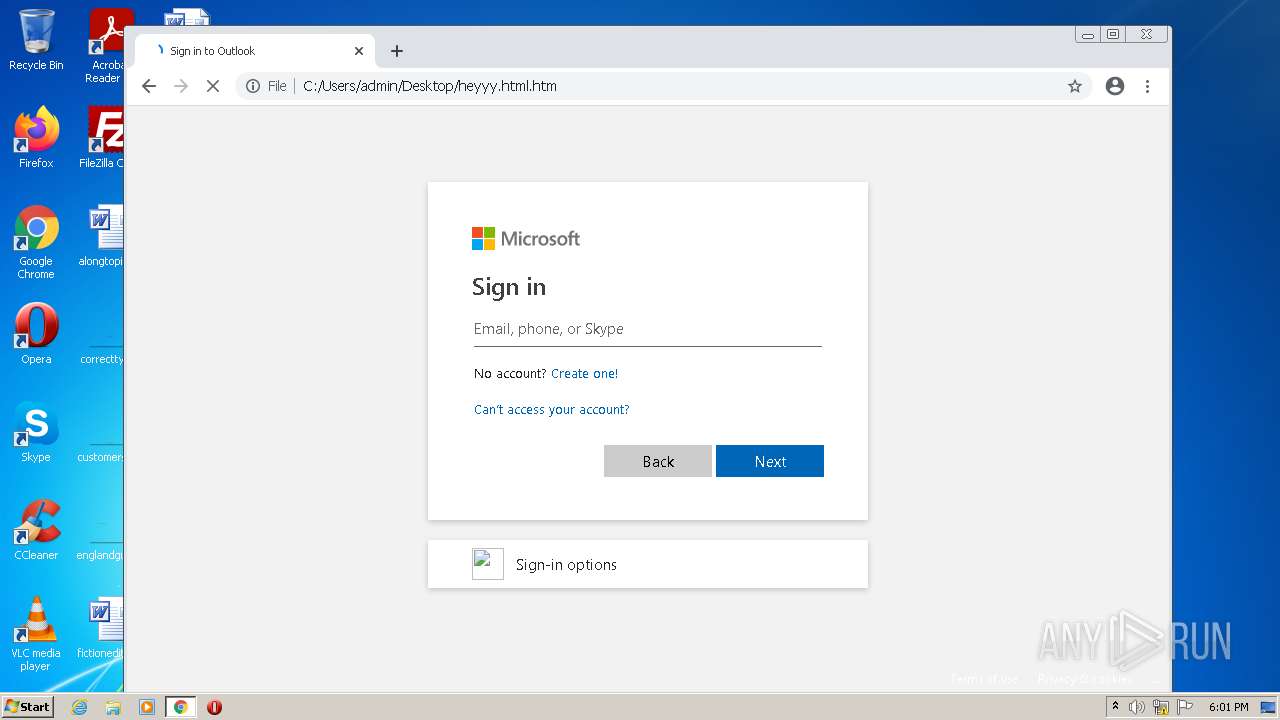
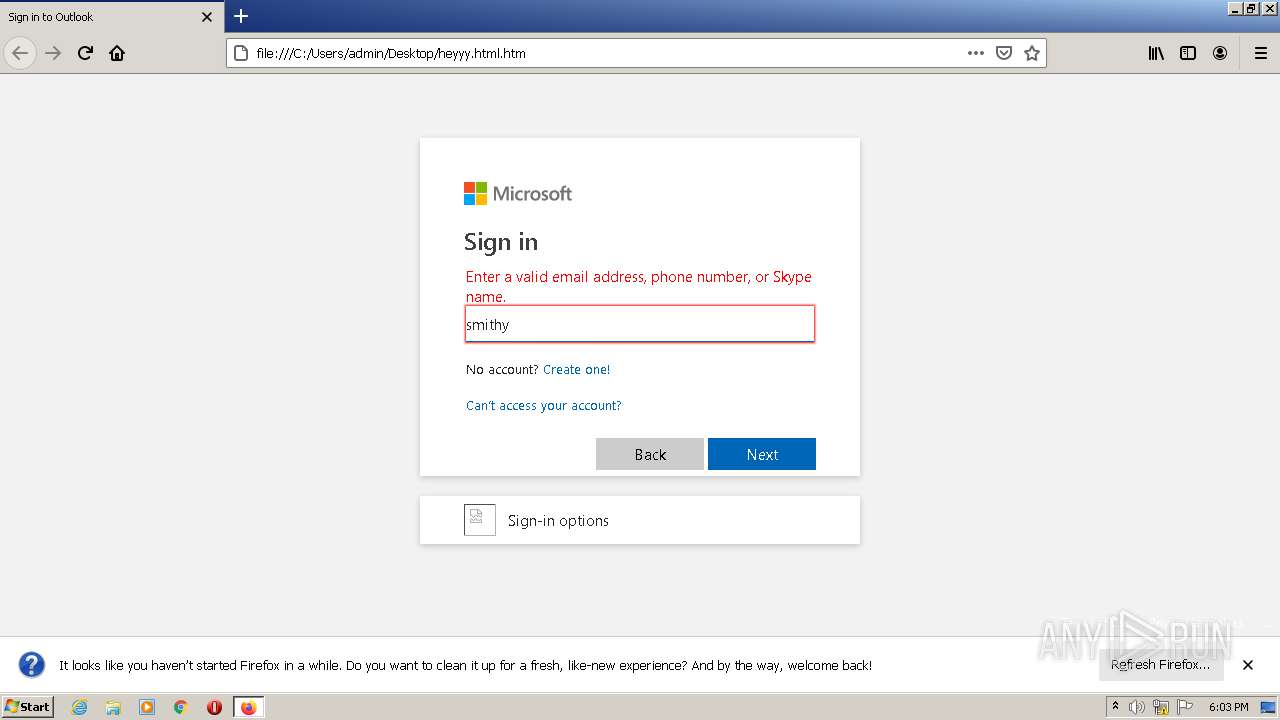
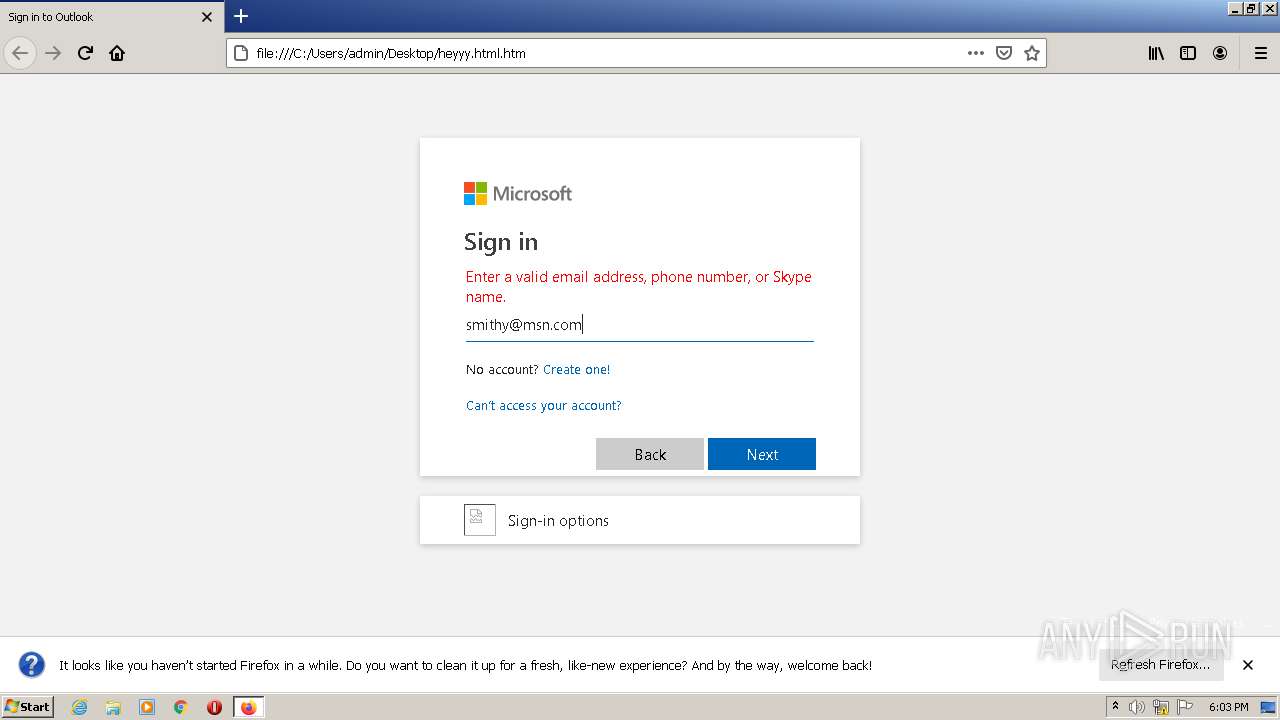
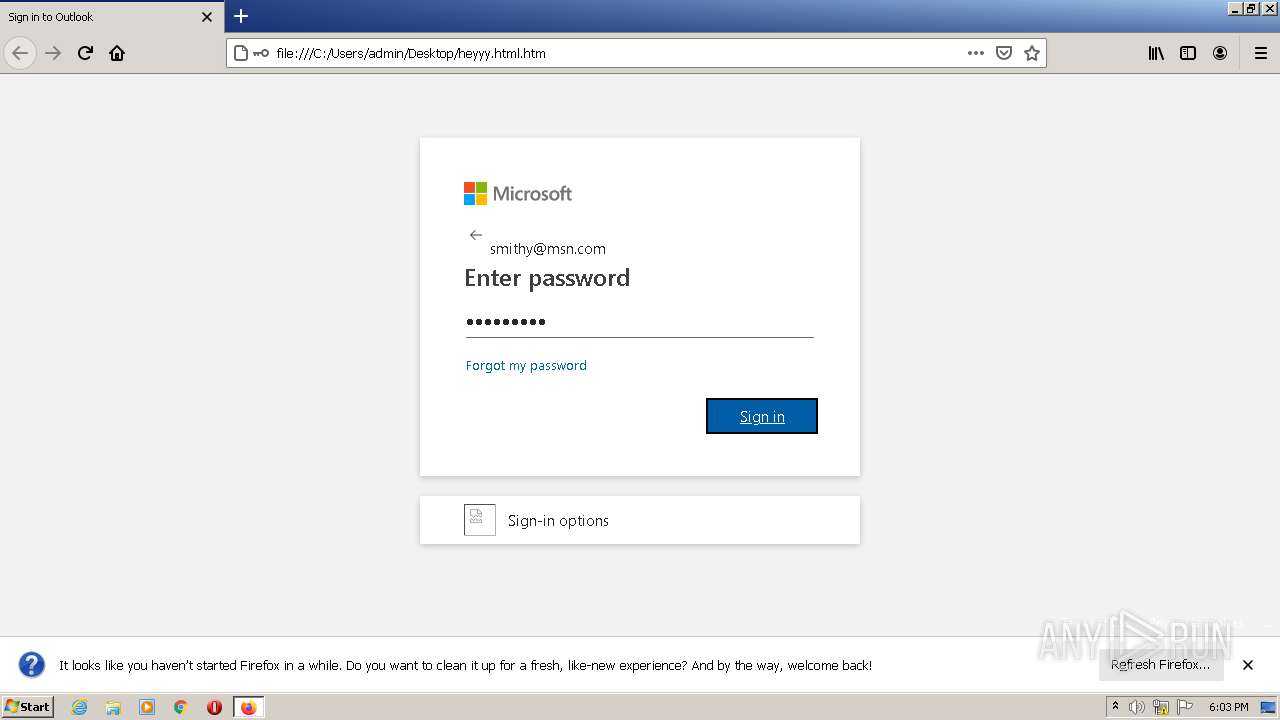
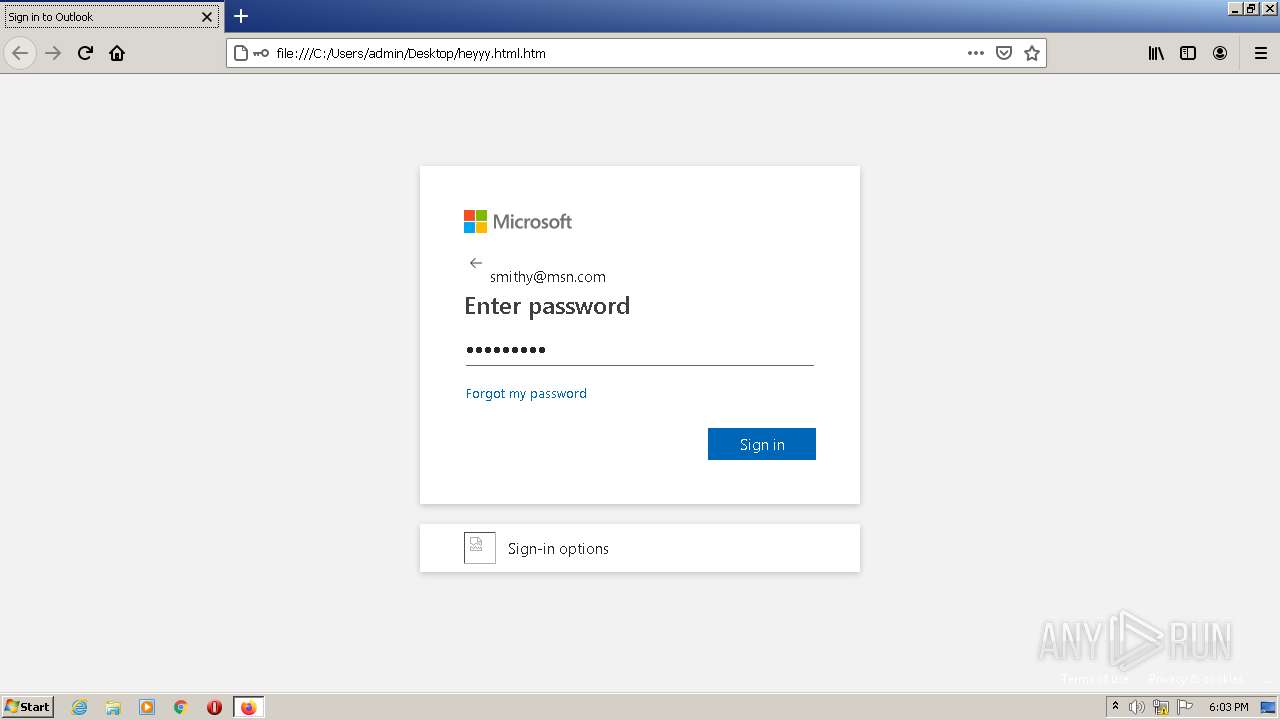
| Title: | Sign in to Outlook |
Total processes
66
Monitored processes
26
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 356 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,13926743966547259465,3235879204782857800,131072 --enable-features=PasswordImport --lang=en-US --instant-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1948 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 712 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=86.0.4240.198 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x7188d988,0x7188d998,0x7188d9a4 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 964 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,13926743966547259465,3235879204782857800,131072 --enable-features=PasswordImport --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1840 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1088 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1032,13926743966547259465,3235879204782857800,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2448 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1508 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2152.0.1416038064\1207752363" -parentBuildID 20201112153044 -prefsHandle 1120 -prefMapHandle 1112 -prefsLen 1 -prefMapSize 238726 -appdir "C:\Program Files\Mozilla Firefox\browser" - 2152 "\\.\pipe\gecko-crash-server-pipe.2152" 1208 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 1 Version: 83.0 Modules
| |||||||||||||||
| 2076 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1032,13926743966547259465,3235879204782857800,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --use-gl=swiftshader-webgl --mojo-platform-channel-handle=1040 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2152 | "C:\Program Files\Mozilla Firefox\firefox.exe" -url C:\Users\admin\Desktop\heyyy.html.htm | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 2244 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1032,13926743966547259465,3235879204782857800,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3344 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2368 | "C:\Program Files\Internet Explorer\iexplore.exe" "C:\Users\admin\Desktop\heyyy.html.htm" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2452 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1032,13926743966547259465,3235879204782857800,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1060 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
13 135
Read events
12 813
Write events
316
Delete events
6
Modification events
| (PID) Process: | (2368) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2368) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2368) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30937420 | |||
| (PID) Process: | (2368) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2368) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30937420 | |||
| (PID) Process: | (2368) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2368) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2368) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2368) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2368) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
87
Text files
104
Unknown types
47
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3640 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-61EEE951-E38.pma | — | |
MD5:— | SHA256:— | |||
| 2368 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\{8D59E254-7D3F-11EC-A20C-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 2368 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF74AF3793A9F9B841.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2368 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF24DCF568C3FFBB45.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2368 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFE8430BFD50AE8211.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2368 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{868646A5-7D3F-11EC-A20C-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 2368 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\RecoveryStore.{42C873D0-1D90-11EB-BA2C-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 2368 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{868646A6-7D3F-11EC-A20C-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 2368 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFECF6F6193E9EA056.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2368 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{868646A7-7D3F-11EC-A20C-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
1 169
DNS requests
113
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2152 | firefox.exe | GET | 404 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt | US | xml | 341 b | whitelisted |
3224 | chrome.exe | POST | 404 | 142.250.185.99:80 | http://update.googleapis.com/service/update2/json?cup2key=10:2768986104&cup2hreq=68b36c83d079cc58b94e7524c7eb8092d67c6d8aca70f3ef048585cb360ce3d9 | US | xml | 341 b | whitelisted |
2152 | firefox.exe | GET | 404 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt | US | xml | 341 b | whitelisted |
2152 | firefox.exe | GET | 404 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt | US | xml | 341 b | whitelisted |
2152 | firefox.exe | GET | 404 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt | US | xml | 341 b | whitelisted |
2152 | firefox.exe | GET | 404 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt | US | xml | 341 b | whitelisted |
2152 | firefox.exe | GET | 404 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt | US | xml | 341 b | whitelisted |
2152 | firefox.exe | GET | 404 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt | US | xml | 341 b | whitelisted |
2152 | firefox.exe | GET | 404 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt | US | xml | 341 b | whitelisted |
2152 | firefox.exe | GET | 404 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt | US | xml | 341 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3160 | iexplore.exe | 104.16.19.94:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | suspicious |
3160 | iexplore.exe | 104.16.87.20:443 | cdn.jsdelivr.net | Cloudflare Inc | US | shared |
3160 | iexplore.exe | 152.199.23.37:443 | aadcdn.msftauth.net | MCI Communications Services, Inc. d/b/a Verizon Business | US | suspicious |
3160 | iexplore.exe | 216.58.212.138:443 | ajax.googleapis.com | Google Inc. | US | whitelisted |
3060 | iexplore.exe | 104.16.87.20:443 | cdn.jsdelivr.net | Cloudflare Inc | US | shared |
3060 | iexplore.exe | 152.199.23.37:443 | aadcdn.msftauth.net | MCI Communications Services, Inc. d/b/a Verizon Business | US | suspicious |
3060 | iexplore.exe | 104.16.19.94:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | suspicious |
3060 | iexplore.exe | 216.58.212.138:443 | ajax.googleapis.com | Google Inc. | US | whitelisted |
— | — | 104.16.19.94:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | suspicious |
3160 | iexplore.exe | 104.16.18.94:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cdnjs.cloudflare.com |
| whitelisted |
ajax.googleapis.com |
| whitelisted |
aadcdn.msftauth.net |
| whitelisted |
cdn.jsdelivr.net |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
clients2.google.com |
| whitelisted |
www.google.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2152 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2152 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2152 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2152 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2152 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2152 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2152 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2152 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2152 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2152 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\plugins\Config\nppPluginList.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|