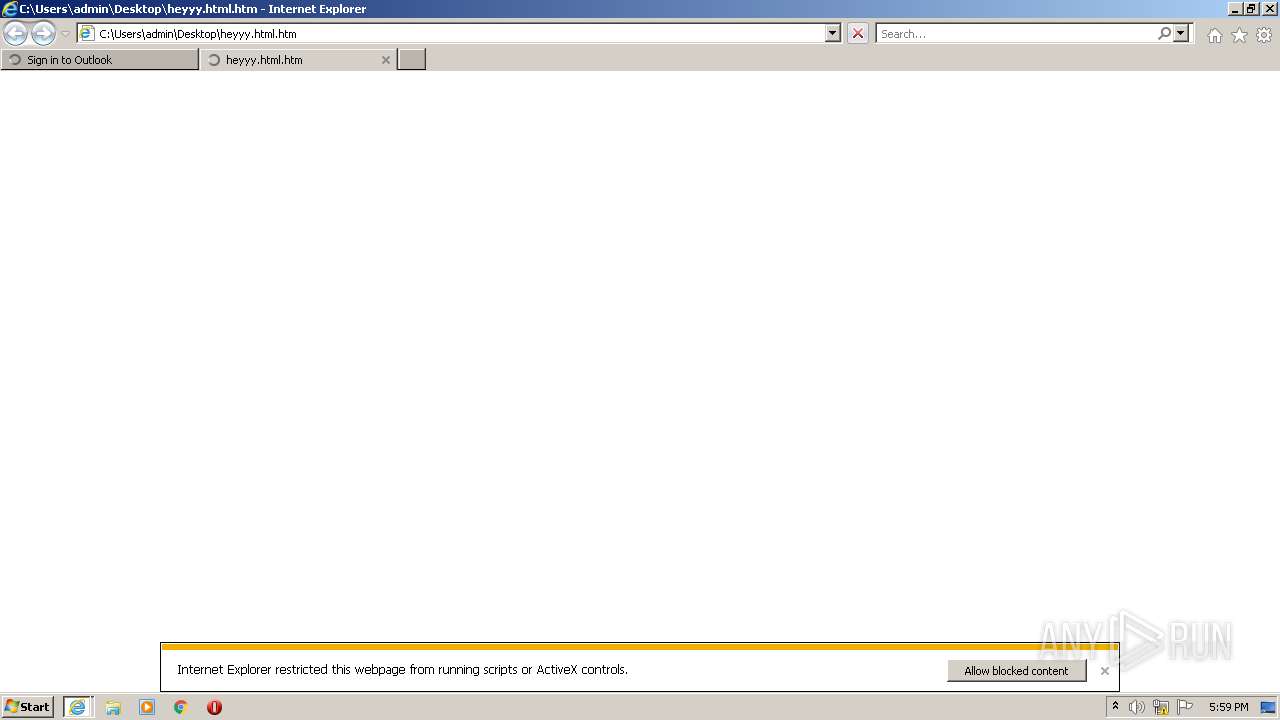
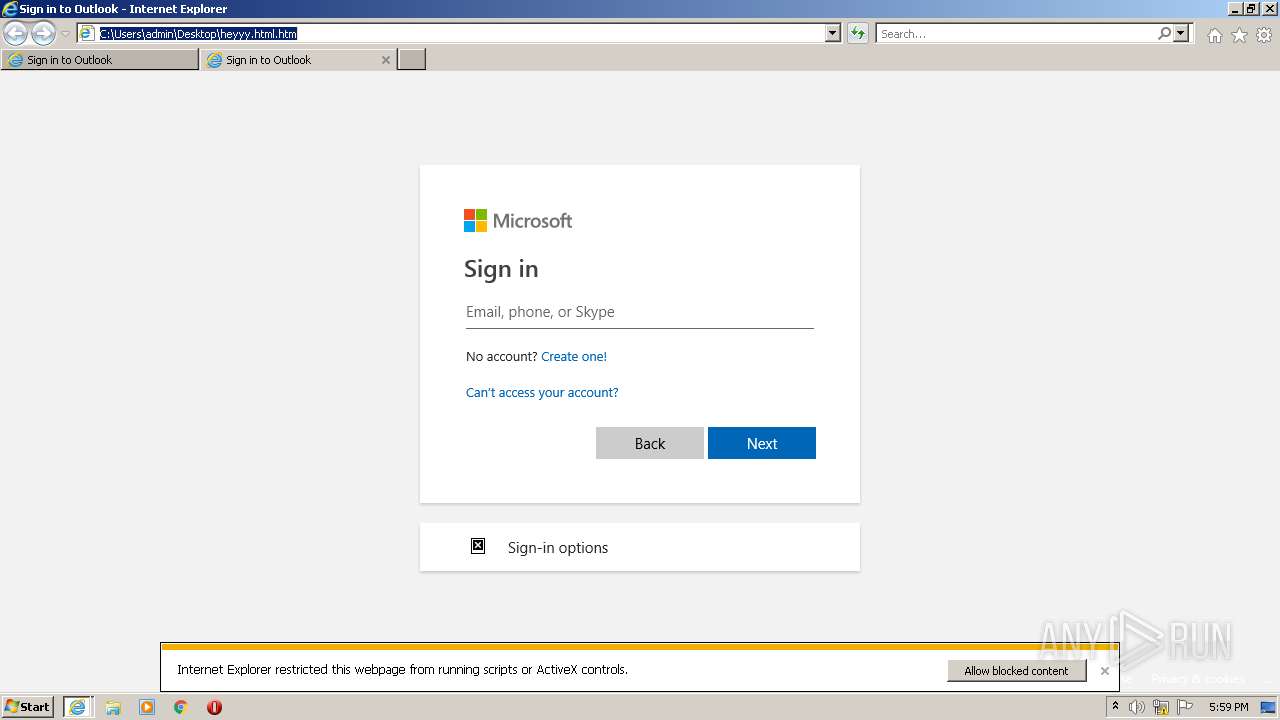
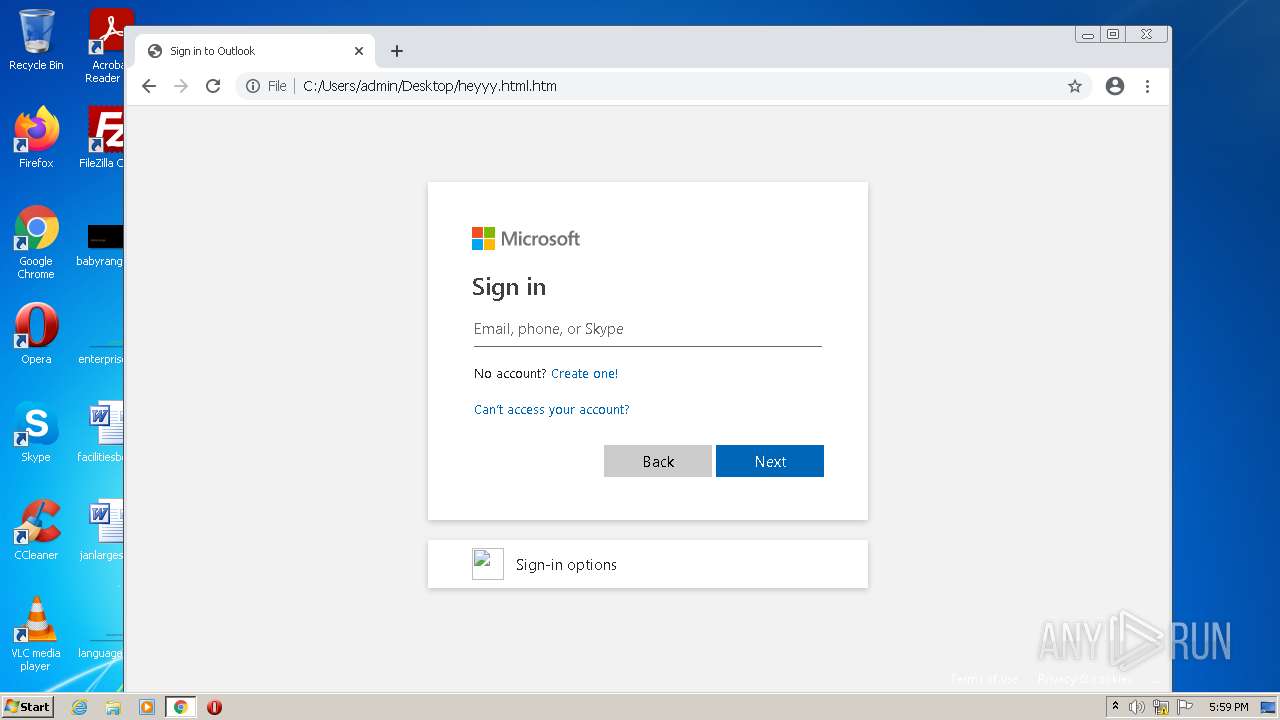
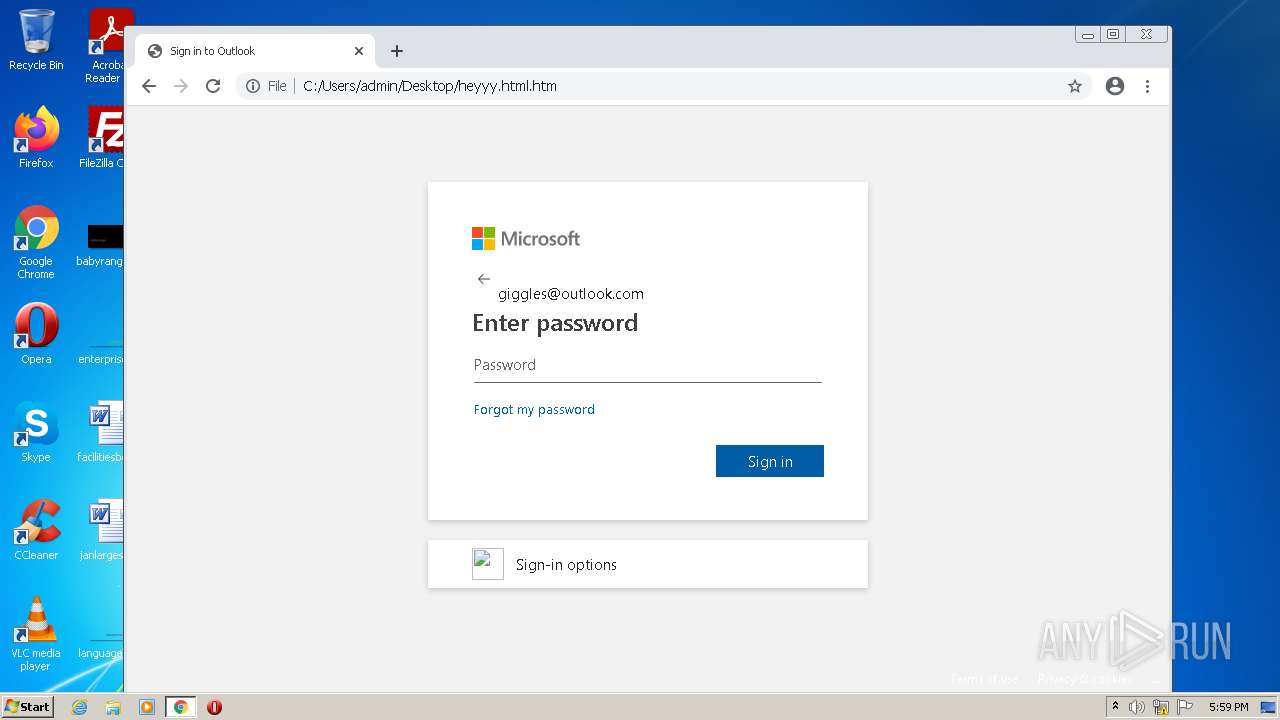
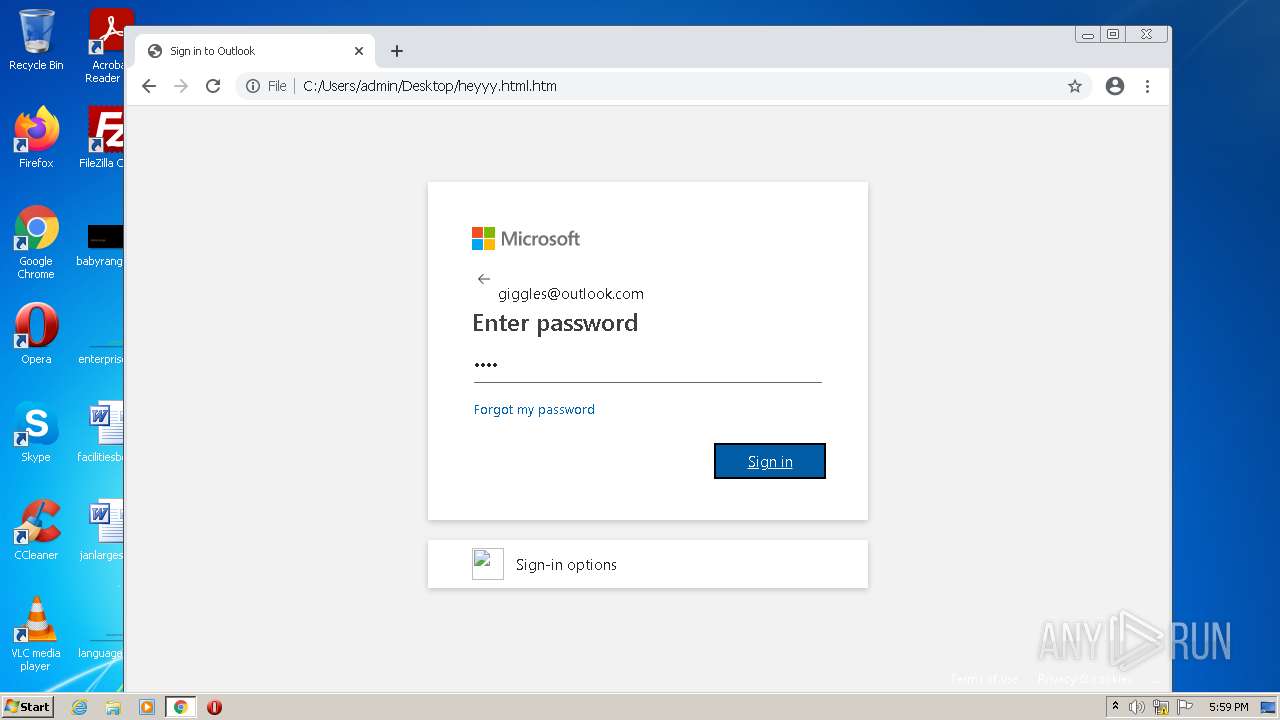
| File name: | heyyy.html |
| Full analysis: | https://app.any.run/tasks/70baf449-3e87-44af-92a3-da143c396f34 |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 17:58:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with very long lines, with CRLF line terminators |
| MD5: | 09BFEC2FF940DEAC8CDFC0EFE2EFAC9B |
| SHA1: | 02E3DA2A9683F0CD13F404B775C16A6CF87B83DE |
| SHA256: | 3179F925294771977304BCB7936C03EC31C38A9FBAE8CD80A59150702C06B11F |
| SSDEEP: | 1536:WsFv6eBoRbjQHuhw+E3mazA/PWrF7qvEAFiQcpm8tpHzyJRT9UEpdm3BPdBF:UxpQBDbyJ3UEpdmRN |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3340)
- iexplore.exe (PID: 368)
INFO
Reads the computer name
- iexplore.exe (PID: 120)
- iexplore.exe (PID: 3340)
- iexplore.exe (PID: 368)
- iexplore.exe (PID: 3160)
- chrome.exe (PID: 4068)
- chrome.exe (PID: 1780)
- chrome.exe (PID: 3820)
- chrome.exe (PID: 1972)
- chrome.exe (PID: 3356)
- chrome.exe (PID: 2664)
- chrome.exe (PID: 2768)
Checks supported languages
- iexplore.exe (PID: 120)
- iexplore.exe (PID: 3340)
- iexplore.exe (PID: 368)
- iexplore.exe (PID: 3160)
- chrome.exe (PID: 4068)
- chrome.exe (PID: 1780)
- chrome.exe (PID: 2436)
- chrome.exe (PID: 2160)
- chrome.exe (PID: 2064)
- chrome.exe (PID: 2752)
- chrome.exe (PID: 1060)
- chrome.exe (PID: 1972)
- chrome.exe (PID: 3820)
- chrome.exe (PID: 3356)
- chrome.exe (PID: 3152)
- chrome.exe (PID: 2664)
- chrome.exe (PID: 2768)
Application launched itself
- iexplore.exe (PID: 120)
- iexplore.exe (PID: 368)
- chrome.exe (PID: 4068)
Changes internet zones settings
- iexplore.exe (PID: 120)
Reads internet explorer settings
- iexplore.exe (PID: 3340)
- iexplore.exe (PID: 368)
Checks Windows Trust Settings
- iexplore.exe (PID: 3340)
- iexplore.exe (PID: 368)
- iexplore.exe (PID: 120)
Reads settings of System Certificates
- iexplore.exe (PID: 3340)
- iexplore.exe (PID: 368)
- iexplore.exe (PID: 120)
- chrome.exe (PID: 1780)
Reads the date of Windows installation
- iexplore.exe (PID: 120)
- chrome.exe (PID: 2768)
Manual execution by user
- chrome.exe (PID: 4068)
Reads the hosts file
- chrome.exe (PID: 4068)
- chrome.exe (PID: 1780)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .htm/html | | | HyperText Markup Language with DOCTYPE (80.6) |
|---|---|---|
| .html | | | HyperText Markup Language (19.3) |
EXIF
HTML
| Robots: | noindex, nofollow |
|---|---|
| Pragma: | no-cache |
| viewport: | width=device-width, initial-scale=1.0, maximum-scale=2.0, user-scalable=yes |
| HTTPEquivXUACompatible: | IE=edge |
| ContentType: | text/html; charset=UTF-8 |
| Title: | Sign in to Outlook |
Total processes
54
Monitored processes
17
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Program Files\Internet Explorer\iexplore.exe" "C:\Users\admin\Desktop\heyyy.html.htm" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 368 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:120 CREDAT:406532 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1060 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=86.0.4240.198 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6e86d988,0x6e86d998,0x6e86d9a4 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1780 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1032,4641437190046048356,14805396612407770826,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1344 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1972 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1032,4641437190046048356,14805396612407770826,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1048 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2064 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,4641437190046048356,14805396612407770826,131072 --enable-features=PasswordImport --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1908 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2160 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,4641437190046048356,14805396612407770826,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1928 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2436 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,4641437190046048356,14805396612407770826,131072 --enable-features=PasswordImport --lang=en-US --instant-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1928 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2664 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1032,4641437190046048356,14805396612407770826,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=920 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2752 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,4641437190046048356,14805396612407770826,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3432 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
56 170
Read events
55 941
Write events
228
Delete events
1
Modification events
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 294033680 | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30937420 | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 594038133 | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30937420 | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
20
Text files
52
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4068 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-61EEE8EF-FE4.pma | — | |
MD5:— | SHA256:— | |||
| 120 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\{4F29ACED-7D3F-11EC-976C-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 120 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFA8378B7669231636.TMP | gmc | |
MD5:— | SHA256:— | |||
| 120 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF969597321E74F317.TMP | gmc | |
MD5:— | SHA256:— | |||
| 120 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFB5829529F29F3AE9.TMP | gmc | |
MD5:— | SHA256:— | |||
| 120 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF260C2B0750B33968.TMP | gmc | |
MD5:— | SHA256:— | |||
| 120 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{4F29ACEA-7D3F-11EC-976C-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 120 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFDB812211382E55B4.TMP | gmc | |
MD5:— | SHA256:— | |||
| 120 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\RecoveryStore.{42C873D0-1D90-11EB-BA2C-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 120 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\{4F29ACEC-7D3F-11EC-976C-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
75
DNS requests
29
Threats
25
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3340 | iexplore.exe | GET | 404 | 8.241.78.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b98edd2916e29a2d | US | xml | 341 b | whitelisted |
368 | iexplore.exe | GET | 404 | 8.241.78.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c9b6ea68158807b5 | US | xml | 341 b | whitelisted |
368 | iexplore.exe | GET | 404 | 8.241.78.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?363ddf8c9791bb0b | US | xml | 341 b | whitelisted |
3340 | iexplore.exe | GET | 404 | 8.241.78.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c2594ff8a3b52262 | US | xml | 341 b | whitelisted |
3340 | iexplore.exe | GET | 404 | 8.241.78.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?56b2116e06b06f89 | US | xml | 341 b | whitelisted |
368 | iexplore.exe | GET | 404 | 8.241.78.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a20c072532264222 | US | xml | 341 b | whitelisted |
368 | iexplore.exe | GET | 404 | 8.241.78.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4446b18fed3acfde | US | xml | 341 b | whitelisted |
3340 | iexplore.exe | GET | 404 | 8.241.78.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?17fa8e0e0a2bb62c | US | xml | 341 b | whitelisted |
368 | iexplore.exe | GET | 404 | 8.241.78.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?08181ea0b9be165d | US | xml | 341 b | whitelisted |
368 | iexplore.exe | GET | 404 | 8.241.78.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?932a618d0a8b0047 | US | xml | 341 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3340 | iexplore.exe | 104.16.87.20:443 | cdn.jsdelivr.net | Cloudflare Inc | US | shared |
3340 | iexplore.exe | 142.250.185.138:443 | ajax.googleapis.com | Google Inc. | US | whitelisted |
368 | iexplore.exe | 104.16.87.20:443 | cdn.jsdelivr.net | Cloudflare Inc | US | shared |
3340 | iexplore.exe | 152.199.23.37:443 | aadcdn.msftauth.net | MCI Communications Services, Inc. d/b/a Verizon Business | US | suspicious |
3340 | iexplore.exe | 104.16.19.94:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | suspicious |
368 | iexplore.exe | 104.16.19.94:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | suspicious |
120 | iexplore.exe | 8.241.78.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
368 | iexplore.exe | 8.241.78.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
1780 | chrome.exe | 142.250.185.164:443 | www.google.com | Google Inc. | US | whitelisted |
120 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ajax.googleapis.com |
| whitelisted |
cdn.jsdelivr.net |
| whitelisted |
aadcdn.msftauth.net |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
clients2.google.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
Threats
25 ETPRO signatures available at the full report