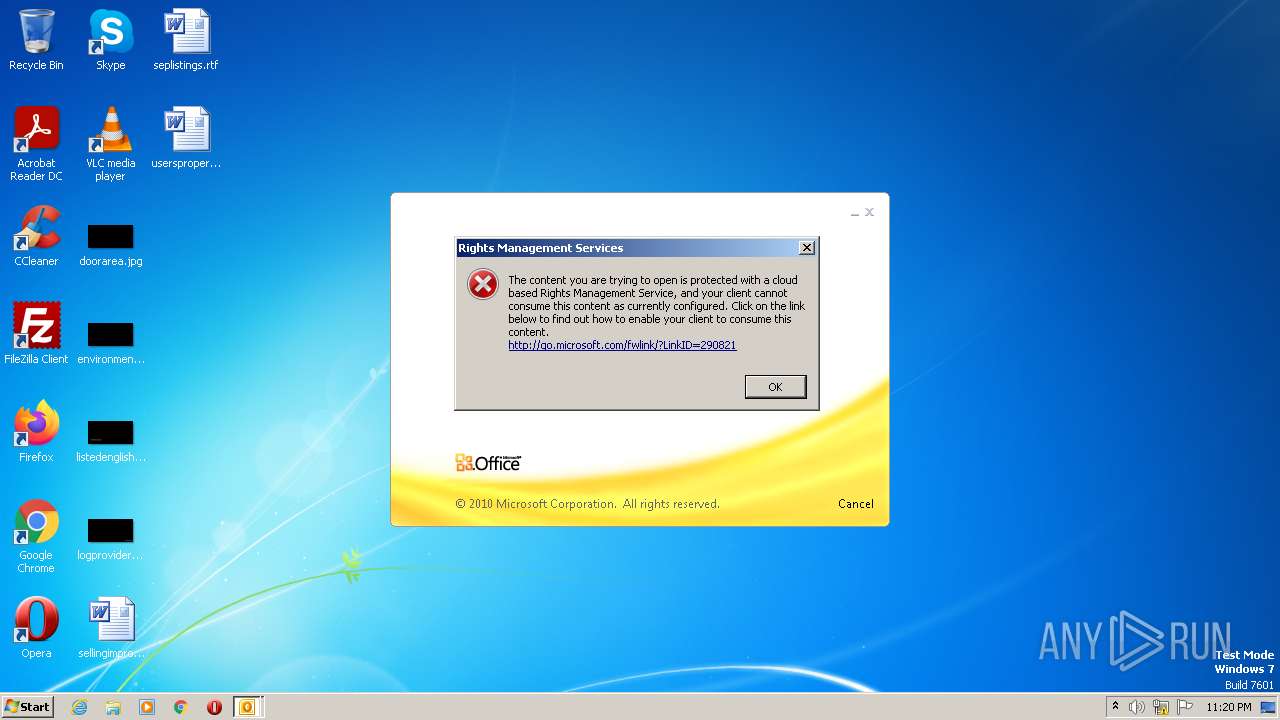
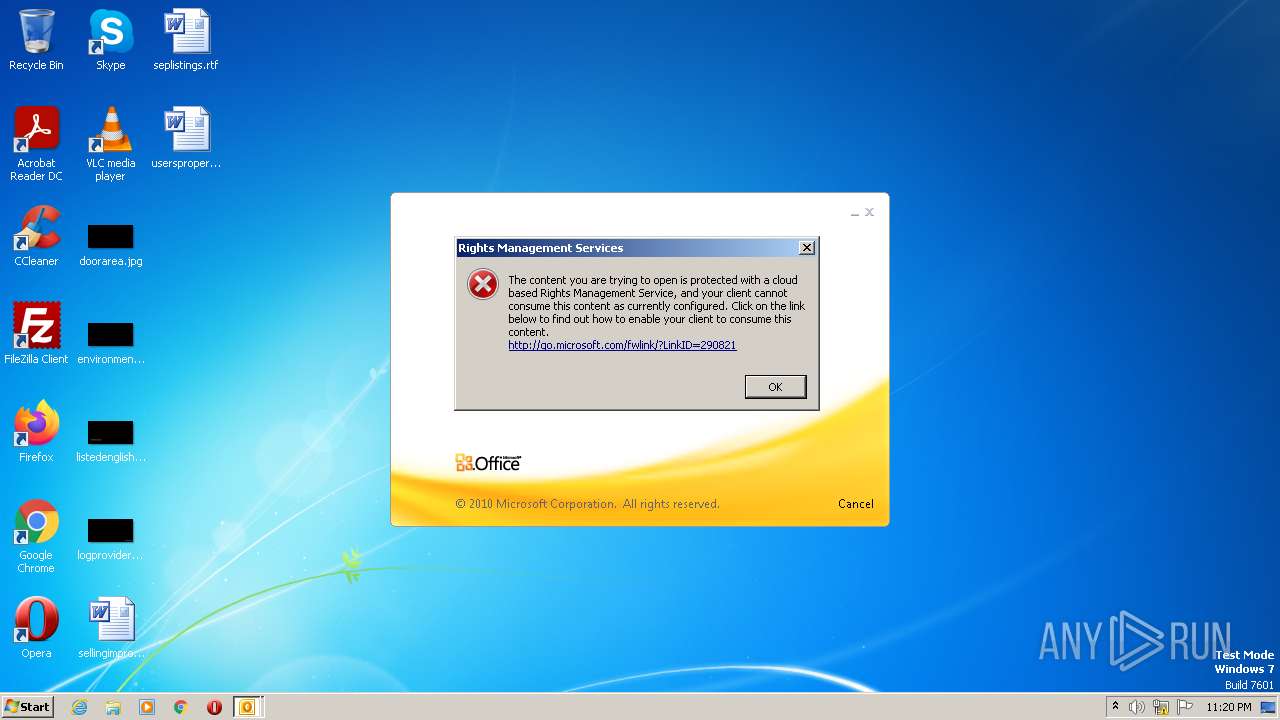
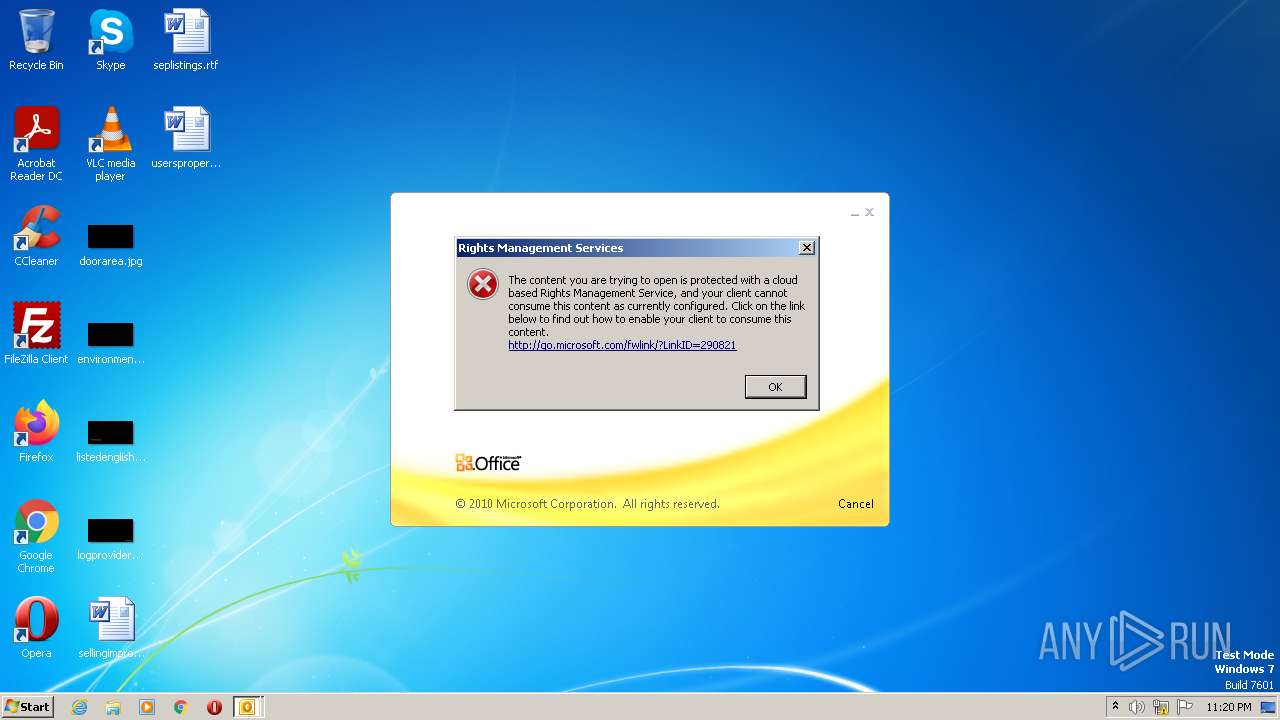
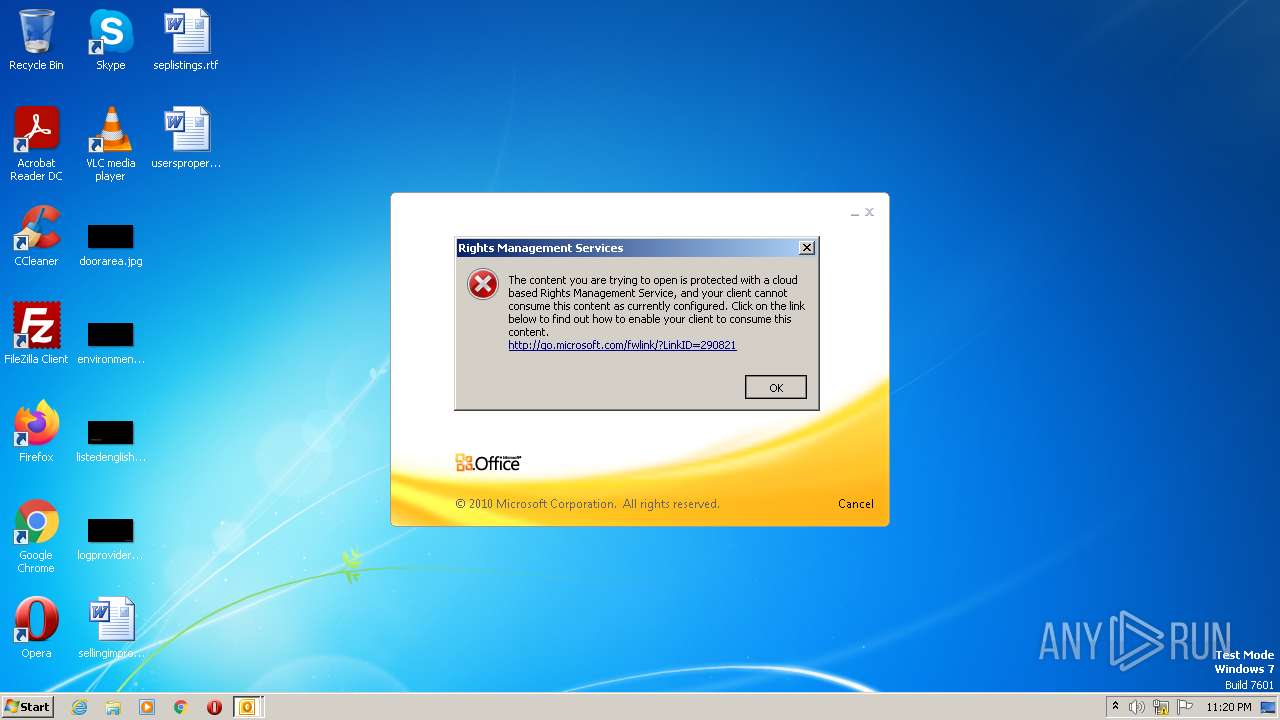
| File name: | Alerta _ correo sospechoso- .msg |
| Full analysis: | https://app.any.run/tasks/d3401dd4-aac0-4c44-8d28-4402d6ec27fb |
| Verdict: | Malicious activity |
| Analysis date: | March 31, 2023, 22:20:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 2D2ABA48D03B5BA0F18E7ED28A58B4C1 |
| SHA1: | D82B45582CF6C8292F9F8607821C22D7FD34280C |
| SHA256: | 316DFAD597A764B5A6348A150A18B309E125A90A8F81D7BF1CEF6EE712DB53B0 |
| SSDEEP: | 6144:3emO88cYhmZ/ddeI4c8Q50PMyqnCyUeP3RzeeuziBijB9TU:7X8dhmZWI4cppChePReeuaiP4 |
MALICIOUS
Unusual execution from MS Office
- OUTLOOK.EXE (PID: 2696)
SUSPICIOUS
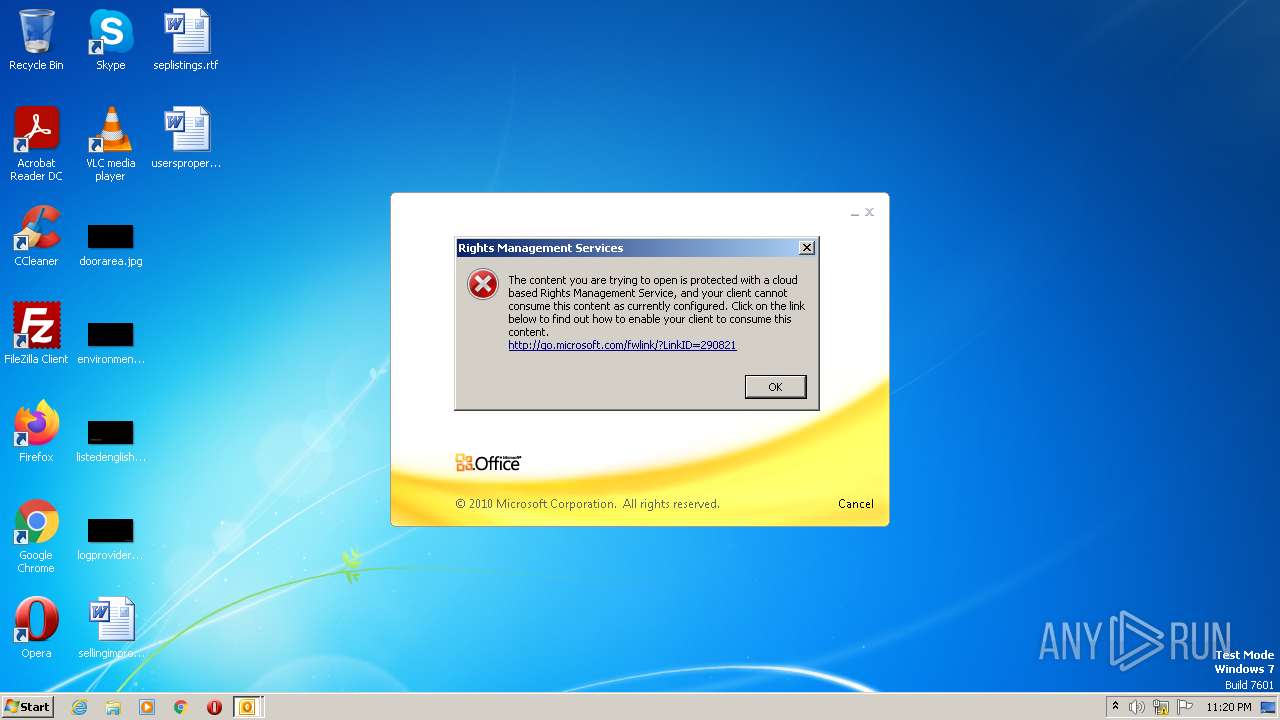
Reads the Internet Settings
- rmactivate.exe (PID: 3688)
Reads security settings of Internet Explorer
- rmactivate.exe (PID: 3688)
Reads settings of System Certificates
- rmactivate.exe (PID: 3688)
INFO
The process uses the downloaded file
- OUTLOOK.EXE (PID: 2696)
The process checks LSA protection
- rmactivate.exe (PID: 3688)
Creates files or folders in the user directory
- rmactivate.exe (PID: 3688)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
37
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
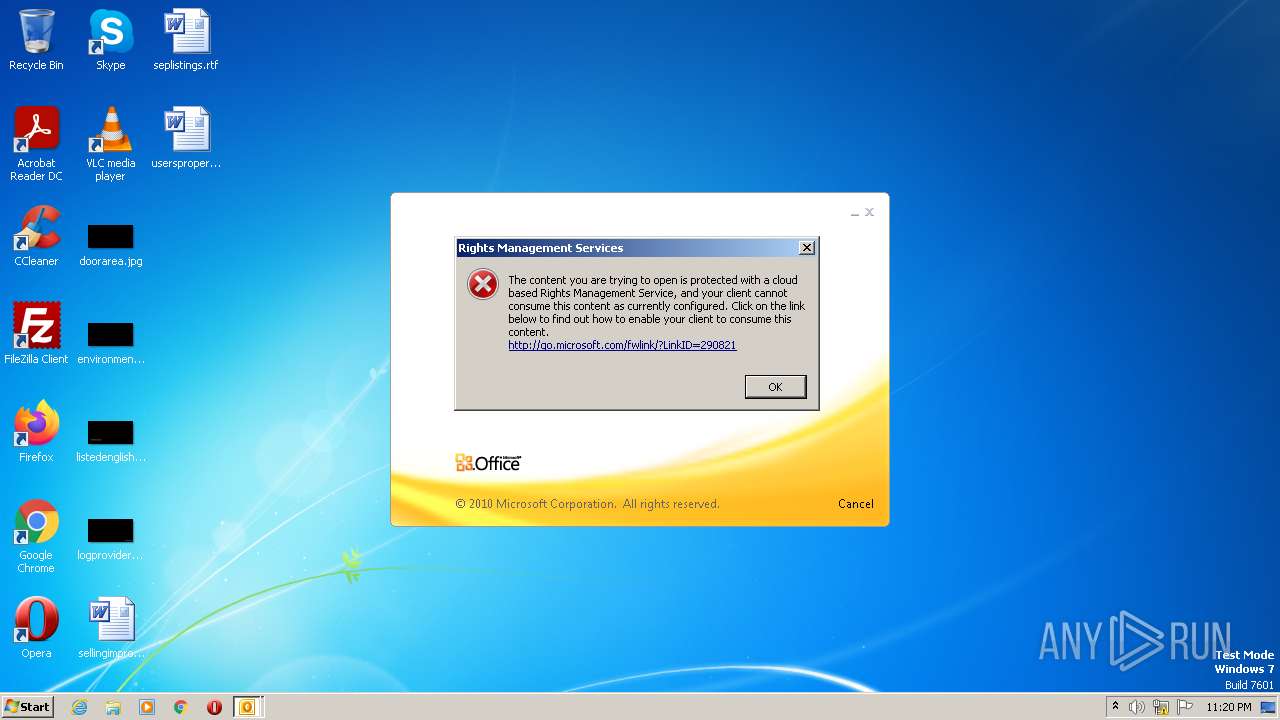
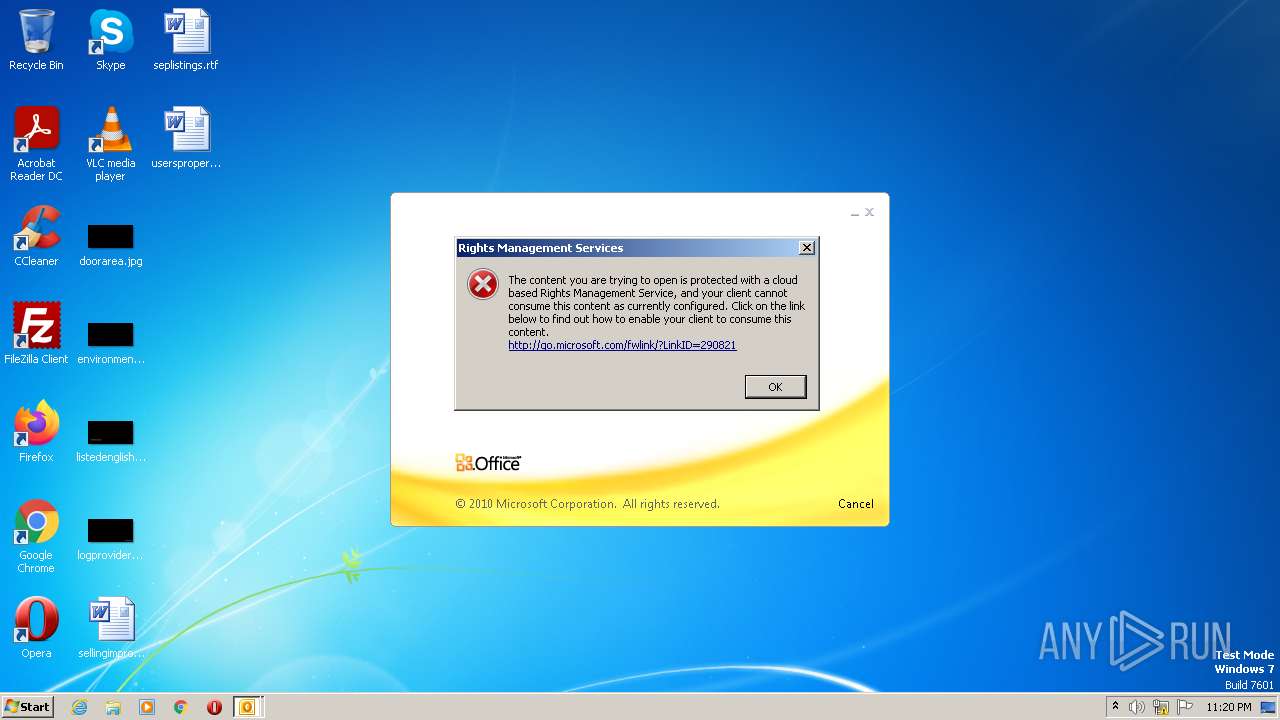
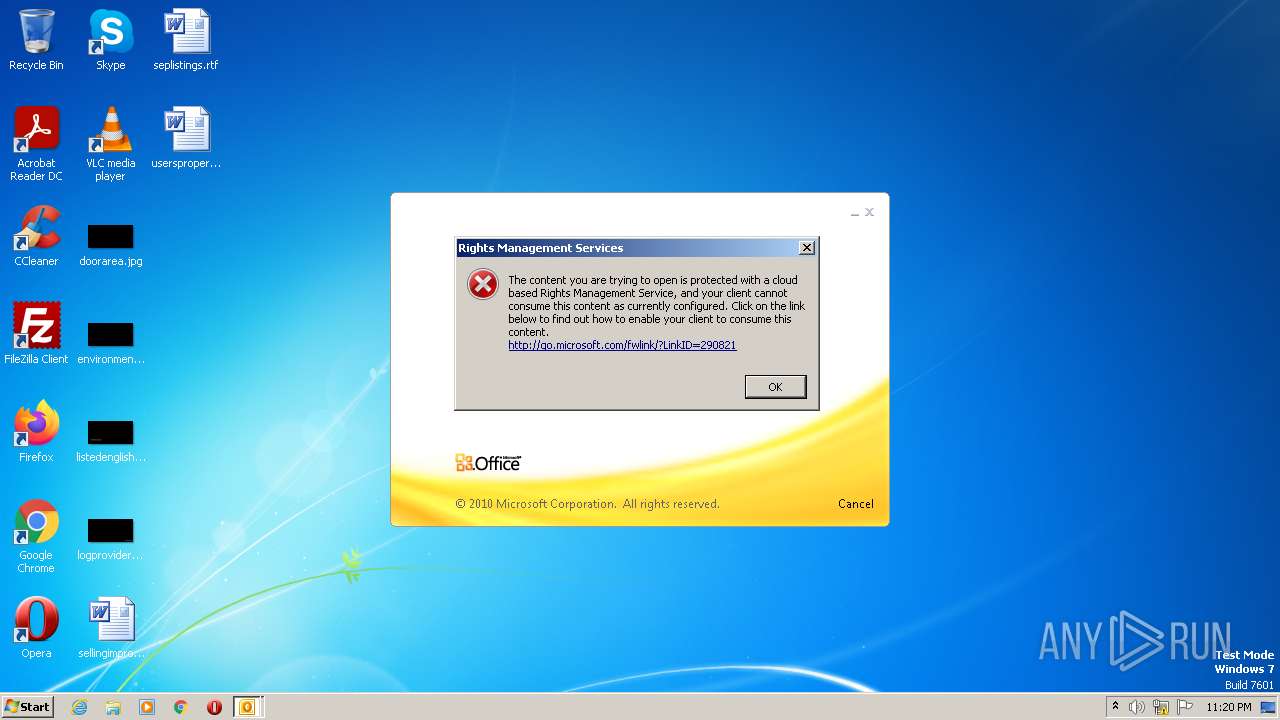
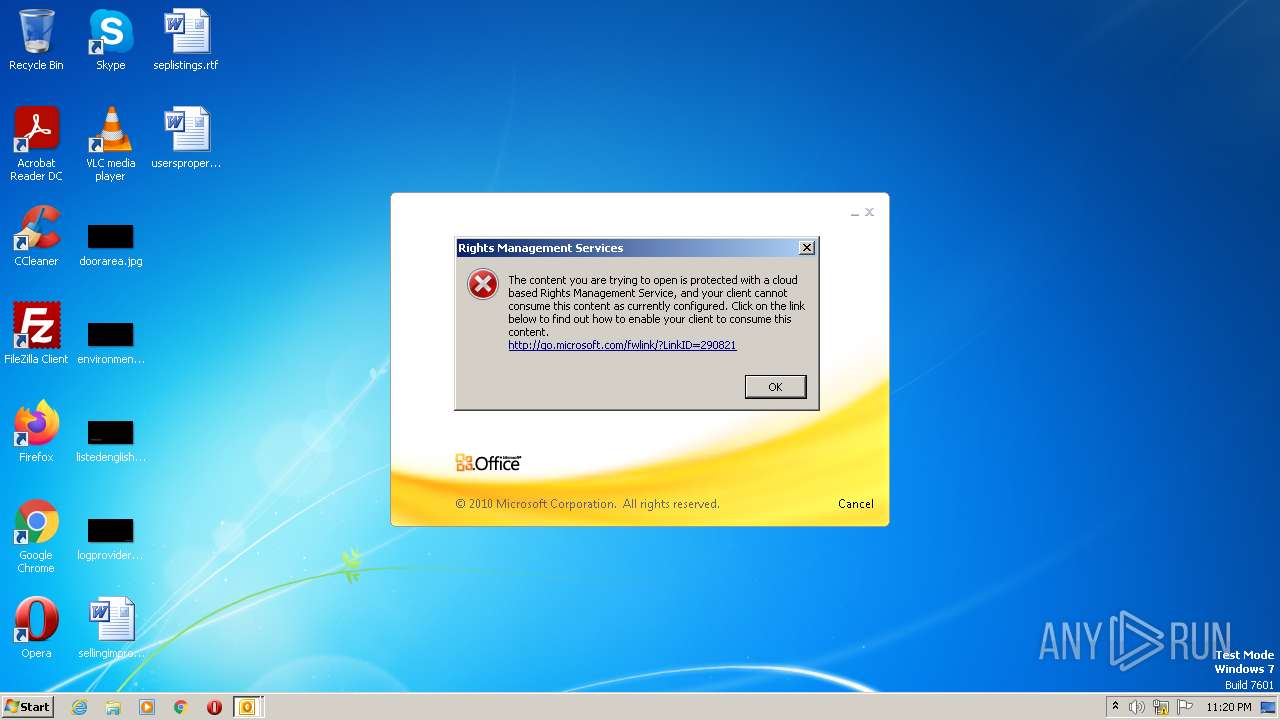
| 2696 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\Alerta _ correo sospechoso- .msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3688 | "C:\Windows\system32\rmactivate.exe" | C:\Windows\System32\rmactivate.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Rights Management Services Activation for Desktop Security Processor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
15 058
Read events
14 916
Write events
136
Delete events
6
Modification events
| (PID) Process: | (2696) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2696) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (2696) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (2696) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (2696) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (2696) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (2696) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (2696) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (2696) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
| (PID) Process: | (2696) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: On | |||
Executable files
0
Suspicious files
22
Text files
6
Unknown types
18
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2696 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRF463.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2696 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 2696 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\4JNI4J8S\message.rpmsg | rpmsg | |
MD5:— | SHA256:— | |||
| 3688 | rmactivate.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3688 | rmactivate.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A583E2A51BFBDC1E492A57B7C8325850 | binary | |
MD5:— | SHA256:— | |||
| 3688 | rmactivate.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\2CD1F910DD5DC23C234E99A91DE345C0 | binary | |
MD5:— | SHA256:— | |||
| 3688 | rmactivate.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\4C7F163ED126D5C3CB9457F68EC64E9E | binary | |
MD5:— | SHA256:— | |||
| 3688 | rmactivate.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\696F3DE637E6DE85B458996D49D759AD | binary | |
MD5:— | SHA256:— | |||
| 2696 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 2696 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\4JNI4J8S\message.rpmsg:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
5
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2696 | OUTLOOK.EXE | GET | 302 | 95.100.53.90:80 | http://go.microsoft.com/fwlink/?LinkId=5998&LANGID=1033 | CH | — | — | whitelisted |
3688 | rmactivate.exe | GET | 200 | 2.18.233.62:80 | http://www.microsoft.com/pkiops/crl/MicWinProPCA2011_2011-10-19.crl | unknown | der | 564 b | whitelisted |
3688 | rmactivate.exe | GET | 200 | 2.21.20.137:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | DE | der | 555 b | whitelisted |
3688 | rmactivate.exe | GET | 200 | 2.21.20.137:80 | http://crl.microsoft.com/pki/crl/products/WinPCA.crl | DE | der | 530 b | whitelisted |
3688 | rmactivate.exe | GET | 200 | 2.21.20.137:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | DE | der | 767 b | whitelisted |
3688 | rmactivate.exe | GET | 200 | 2.21.20.137:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | DE | der | 519 b | whitelisted |
3688 | rmactivate.exe | GET | 200 | 2.21.20.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | DE | der | 824 b | whitelisted |
3688 | rmactivate.exe | GET | 200 | 67.27.233.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a6d436515f926847 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2696 | OUTLOOK.EXE | 65.55.61.29:443 | certification.drm.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3688 | rmactivate.exe | 67.27.233.126:80 | ctldl.windowsupdate.com | LEVEL3 | US | suspicious |
3688 | rmactivate.exe | 2.21.20.137:80 | crl.microsoft.com | Akamai International B.V. | DE | suspicious |
3688 | rmactivate.exe | 2.18.233.62:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2696 | OUTLOOK.EXE | 95.100.53.90:80 | go.microsoft.com | AKAMAI-AS | CH | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
certification.drm.microsoft.com |
| whitelisted |