| File name: | Launcher.exe |
| Full analysis: | https://app.any.run/tasks/45adc264-2bda-427a-91c8-a4a7518af205 |
| Verdict: | Malicious activity |
| Analysis date: | October 30, 2024, 02:34:35 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, 7 sections |
| MD5: | 455AF626AFE9B6231D94ADAD883B7F43 |
| SHA1: | A2F2E1CB2F73DA7F2048F03E696CE93841226317 |
| SHA256: | 31649AE73D27007030BD175521FD52EB5332460DE68004C9CFC3277489E75AD3 |
| SSDEEP: | 98304:ebr76E9HgQY2PMdm99YH+VfNJV2IH2u9/XAMGytLP8XOEqFXbpl9D+kOPECd0tI8:uQSN |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the BIOS version
- Launcher.exe (PID: 3648)
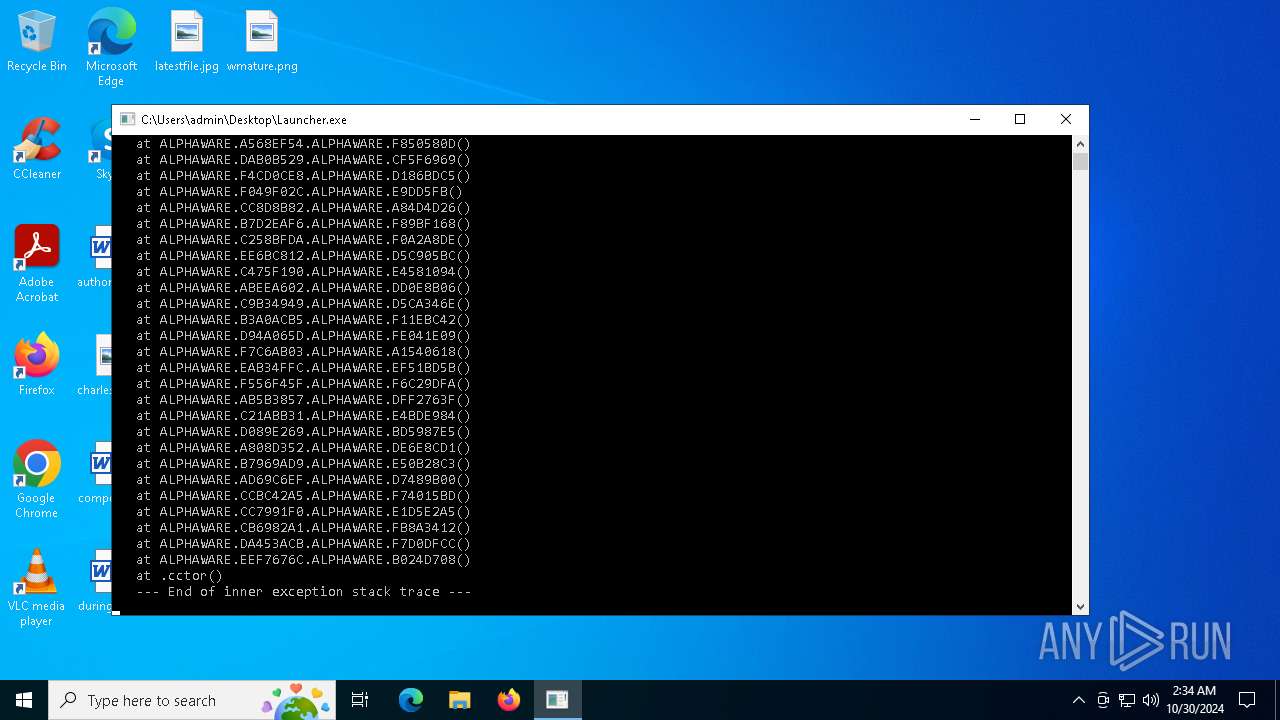
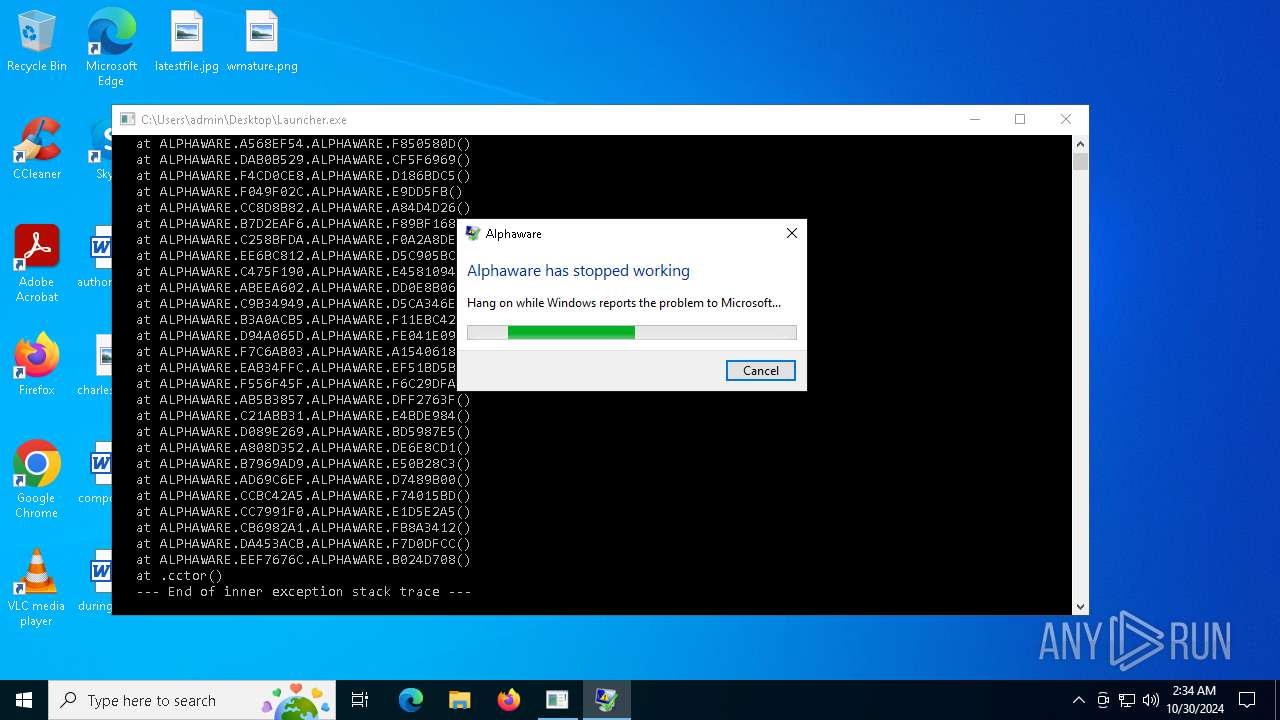
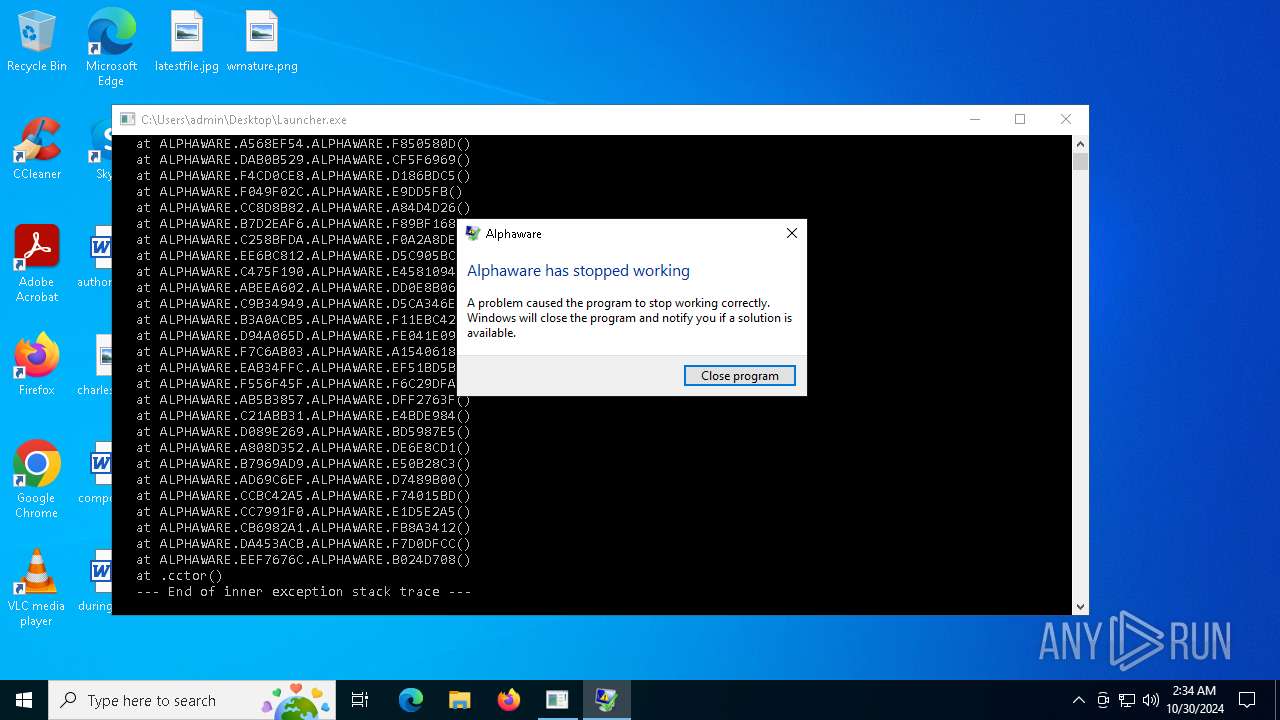
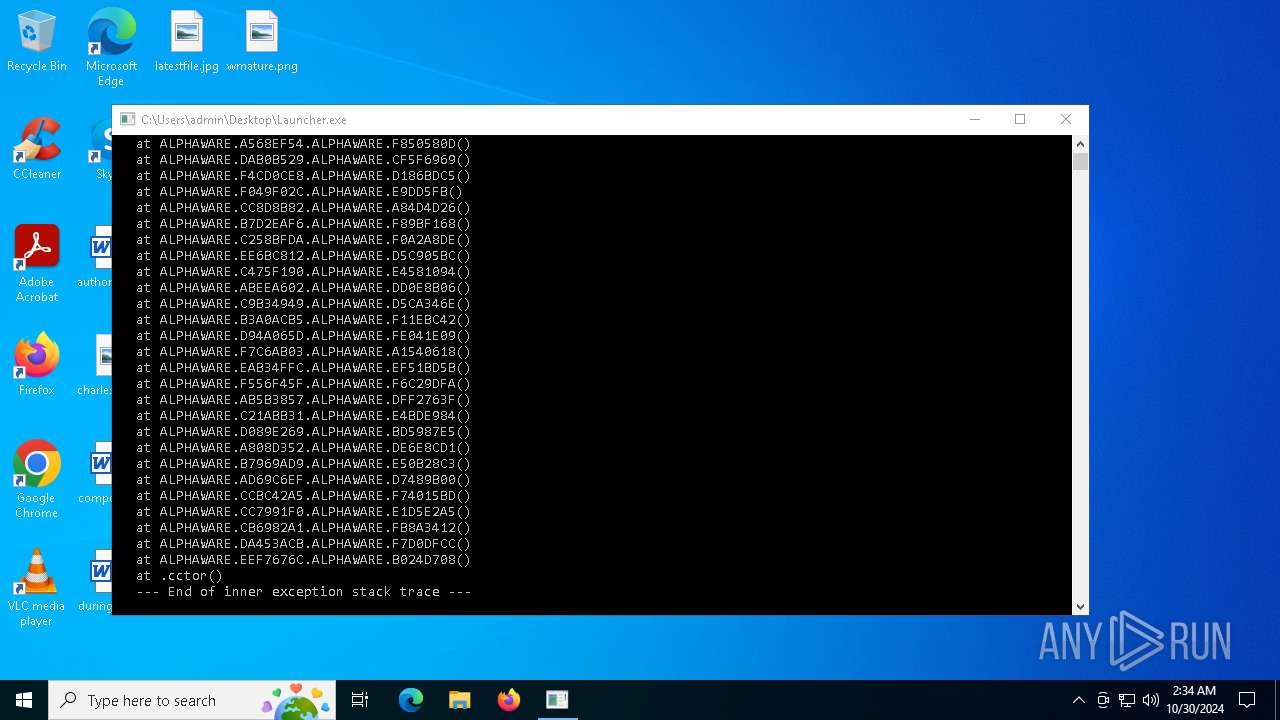
Executes application which crashes
- Launcher.exe (PID: 3648)
Possible usage of Discord/Telegram API has been detected (YARA)
- Launcher.exe (PID: 3648)
INFO
Process checks whether UAC notifications are on
- Launcher.exe (PID: 3648)
Checks supported languages
- Launcher.exe (PID: 3648)
Reads the computer name
- Launcher.exe (PID: 3648)
Themida protector has been detected
- Launcher.exe (PID: 3648)
Checks proxy server information
- WerFault.exe (PID: 6792)
Reads the software policy settings
- WerFault.exe (PID: 6792)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(3648) Launcher.exe
Discord-Webhook-Tokens (1)1287537468308197427/5JyV9B35am3kYCrGxn7gzMY-Obvux88L4FIQfXt93VK60o7KnM5mPstf8skpEKIwM4kn
Discord-Info-Links
1287537468308197427/5JyV9B35am3kYCrGxn7gzMY-Obvux88L4FIQfXt93VK60o7KnM5mPstf8skpEKIwM4kn
Get Webhook Infohttps://discord.com/api/webhooks/1287537468308197427/5JyV9B35am3kYCrGxn7gzMY-Obvux88L4FIQfXt93VK60o7KnM5mPstf8skpEKIwM4kn
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2073:08:14 04:38:57+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 1746432 |
| InitializedDataSize: | 5120 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6ca058 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Alphaware |
| CompanyName: | Alphaware |
| FileDescription: | Alphaware |
| FileVersion: | 1.0.0.0 |
| InternalName: | Alphaware.exe |
| LegalCopyright: | Alphaware |
| LegalTrademarks: | Alphaware |
| OriginalFileName: | Alphaware.exe |
| ProductName: | Alphaware |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
131
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2620 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Launcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2708 | "C:\Users\admin\Desktop\Launcher.exe" | C:\Users\admin\Desktop\Launcher.exe | — | explorer.exe | |||||||||||
User: admin Company: Alphaware Integrity Level: MEDIUM Description: Alphaware Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3648 | "C:\Users\admin\Desktop\Launcher.exe" | C:\Users\admin\Desktop\Launcher.exe | explorer.exe | ||||||||||||
User: admin Company: Alphaware Integrity Level: HIGH Description: Alphaware Exit code: 3762504530 Version: 1.0.0.0 Modules
ims-api(PID) Process(3648) Launcher.exe Discord-Webhook-Tokens (1)1287537468308197427/5JyV9B35am3kYCrGxn7gzMY-Obvux88L4FIQfXt93VK60o7KnM5mPstf8skpEKIwM4kn Discord-Info-Links 1287537468308197427/5JyV9B35am3kYCrGxn7gzMY-Obvux88L4FIQfXt93VK60o7KnM5mPstf8skpEKIwM4kn Get Webhook Infohttps://discord.com/api/webhooks/1287537468308197427/5JyV9B35am3kYCrGxn7gzMY-Obvux88L4FIQfXt93VK60o7KnM5mPstf8skpEKIwM4kn | |||||||||||||||
| 6792 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 3648 -s 1000 | C:\Windows\SysWOW64\WerFault.exe | Launcher.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 629
Read events
6 621
Write events
5
Delete events
3
Modification events
| (PID) Process: | (6792) WerFault.exe | Key: | \REGISTRY\A\{8b85718a-b811-b9f8-e39f-3395038bd4ab}\Root\InventoryApplicationFile |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (6792) WerFault.exe | Key: | \REGISTRY\A\{8b85718a-b811-b9f8-e39f-3395038bd4ab}\Root\InventoryApplicationFile\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6792) WerFault.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\IdentityCRL\ClockData |
| Operation: | write | Name: | ClockTimeSeconds |
Value: 469B216700000000 | |||
| (PID) Process: | (6792) WerFault.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\IdentityCRL\ClockData |
| Operation: | write | Name: | TickCount |
Value: 56C6080000000000 | |||
Executable files
0
Suspicious files
2
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6792 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_Launcher.exe_Alp_96f4cb505de92ac97c2ee73689b12ee2903295a0_439d963c_2921212c-4f33-4312-bb58-fd73d3b0a478\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6792 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\Launcher.exe.3648.dmp | — | |
MD5:— | SHA256:— | |||
| 6792 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERC416.tmp.xml | xml | |
MD5:34E5A9FC968D33B3A6BE5D5383896756 | SHA256:58EB219737579238EA7D957449113FE529C321A3F2421D538A59F5043DC93F27 | |||
| 6792 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERC2BC.tmp.dmp | binary | |
MD5:15817747110AF1468DE10BBB7CA5C9CE | SHA256:83FB8D16397B73A24994CEA6AA4E7CFDE6A8EB2C073D21935DB7A2B23B5BA2BE | |||
| 6792 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERC3D6.tmp.WERInternalMetadata.xml | xml | |
MD5:82F3432103A90B1DB34A5AFA66C0A9B8 | SHA256:F7FE95095B9BA01779124082D11C3612F764259A66F00BADFD83E6E38AEBF036 | |||
| 6792 | WerFault.exe | C:\Windows\appcompat\Programs\Amcache.hve | binary | |
MD5:48A955F86B74F8C926ED496B12B35304 | SHA256:BAA5D8FD01EFF69EE2D1C7E8BAFEB510BD34376C37913E178B45470CD9B2DC4F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
26
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5640 | RUXIMICS.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5640 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5640 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.23.209.187:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
6792 | WerFault.exe | 52.168.117.173:443 | watson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5640 | RUXIMICS.exe | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |