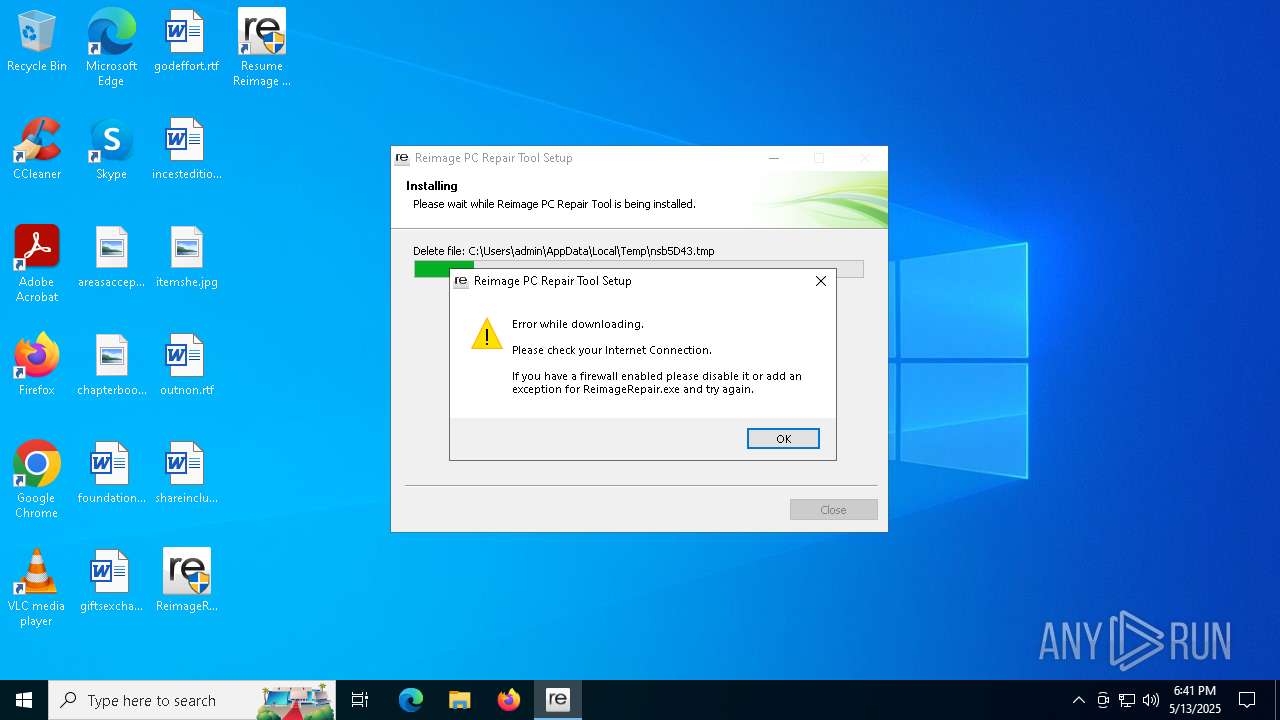
| download: | /web/20180603082928/http://cdnrep.reimageplus.com/rqc/ny/ReimageRepair.exe |
| Full analysis: | https://app.any.run/tasks/ef2589fe-cce9-4748-80f0-060d56877522 |
| Verdict: | Malicious activity |
| Analysis date: | May 13, 2025, 18:39:32 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 20C7E0396DE12D823E8B1660650AD999 |
| SHA1: | A6D7AF8CE2AE317D2FE637D0ACA5FD971315CB7B |
| SHA256: | 315609F7D22AA3CA237AFA9B33AAC5F3BC7C44A07C5A6022F06FE653794F577F |
| SSDEEP: | 12288:nER9hWUGXEcfpxILsSwD31renxA2s8NJ0X4O:na9oE6pxUuhexrsmQ4O |
MALICIOUS
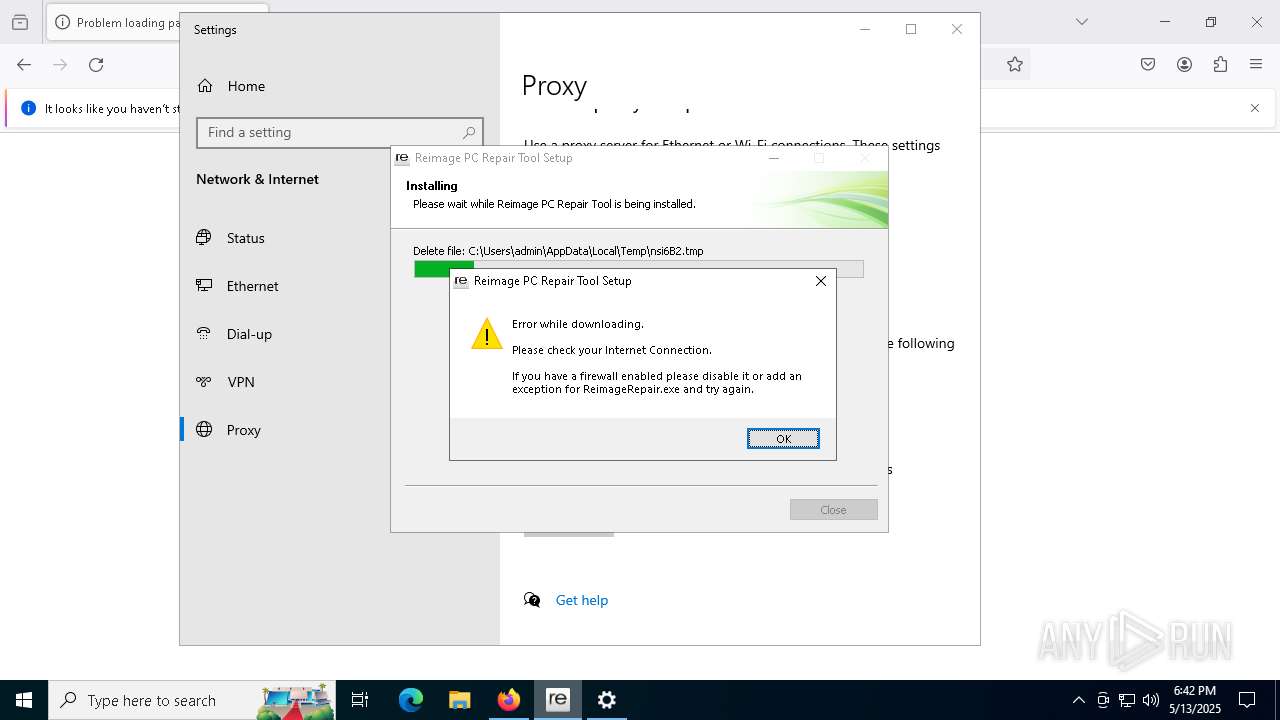
Executing a file with an untrusted certificate
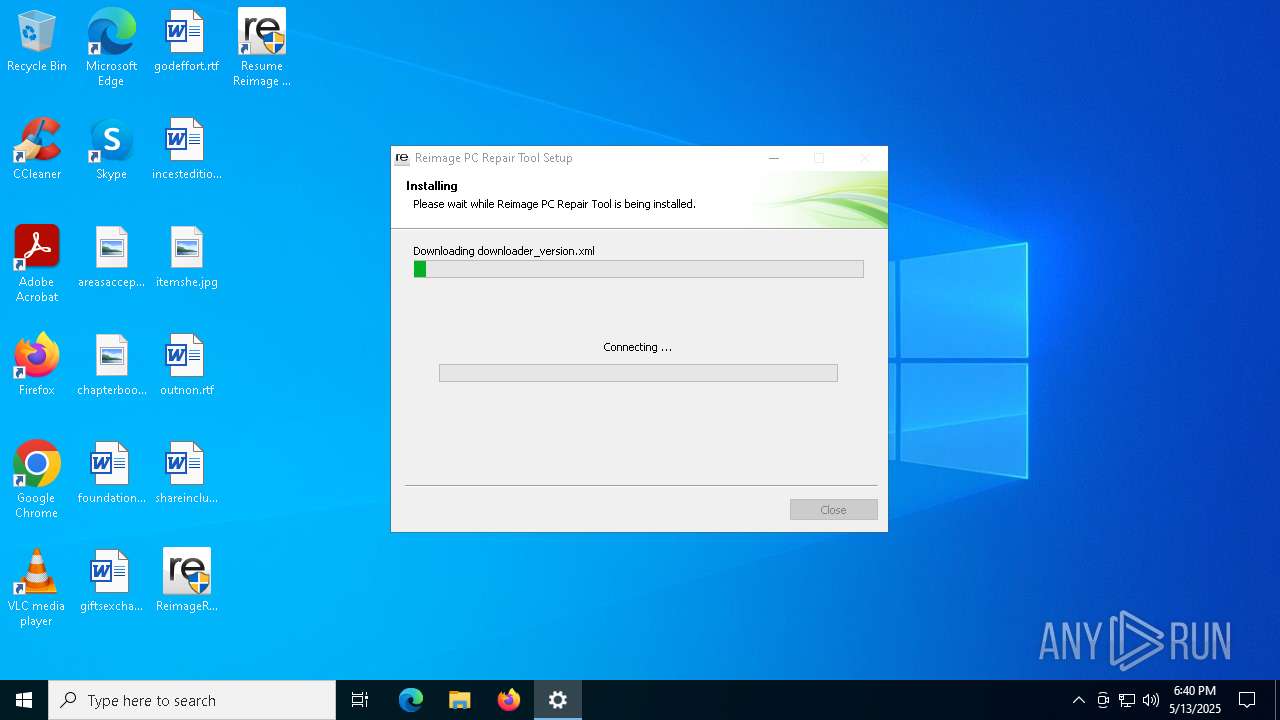
- ReimageRepair.exe (PID: 7332)
- ReimageRepair.exe (PID: 4008)
- ReimageRepair.exe (PID: 5380)
Registers / Runs the DLL via REGSVR32.EXE
- ReimageRepair.exe (PID: 7448)
- ReimageRepair.exe (PID: 5380)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- ReimageRepair.exe (PID: 7448)
- ReimageRepair.exe (PID: 5380)
The process creates files with name similar to system file names
- ReimageRepair.exe (PID: 7448)
- ReimageRepair.exe (PID: 5380)
Executing commands from a ".bat" file
- ReimageRepair.exe (PID: 7448)
- ReimageRepair.exe (PID: 5380)
Starts CMD.EXE for commands execution
- ReimageRepair.exe (PID: 7448)
- ReimageRepair.exe (PID: 5380)
The executable file from the user directory is run by the CMD process
- sqlite3.exe (PID: 7568)
- sqlite3.exe (PID: 7664)
- sqlite3.exe (PID: 7748)
- sqlite3.exe (PID: 4488)
- sqlite3.exe (PID: 7280)
- sqlite3.exe (PID: 2244)
Reads security settings of Internet Explorer
- ReimageRepair.exe (PID: 7448)
- ReimageRepair.exe (PID: 5380)
Executable content was dropped or overwritten
- ReimageRepair.exe (PID: 7448)
- ReimageRepair.exe (PID: 5380)
Get information on the list of running processes
- cmd.exe (PID: 7772)
- ReimageRepair.exe (PID: 7448)
- cmd.exe (PID: 8060)
- ReimageRepair.exe (PID: 5380)
- cmd.exe (PID: 5680)
- cmd.exe (PID: 7240)
There is functionality for taking screenshot (YARA)
- ReimageRepair.exe (PID: 7448)
- ReimageRepair.exe (PID: 5380)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 7576)
- regsvr32.exe (PID: 2288)
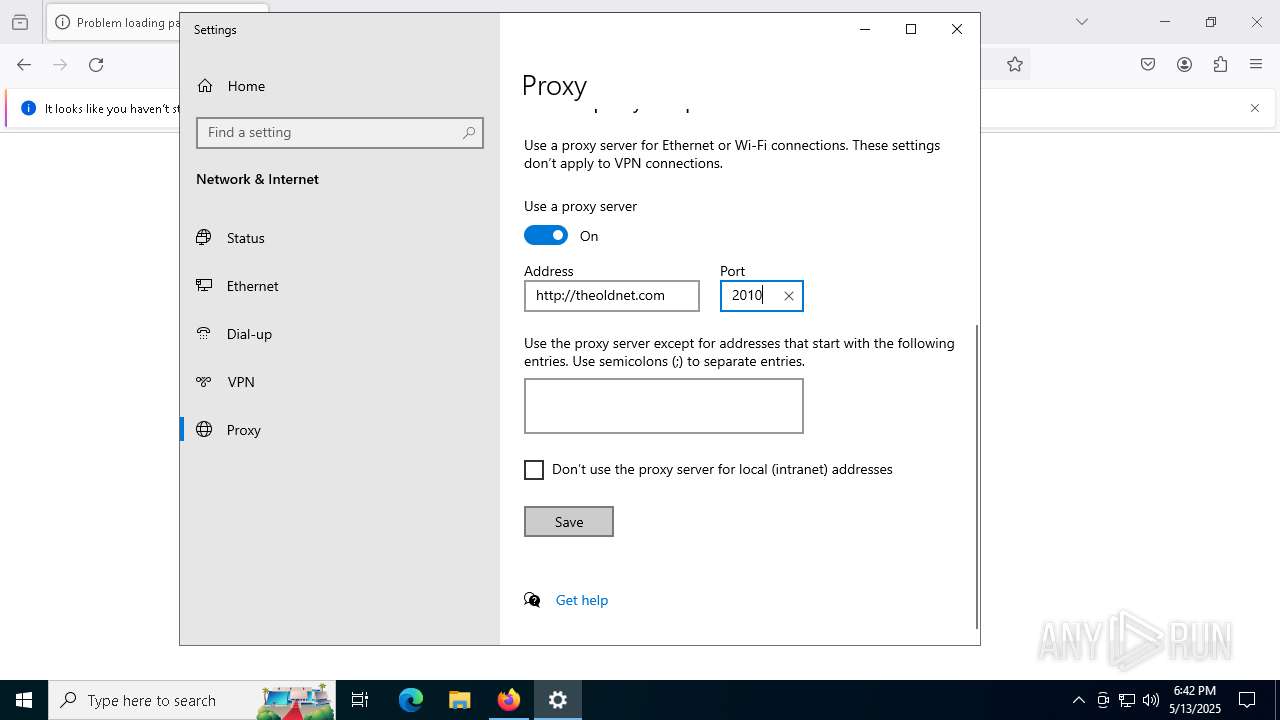
Connects to unusual port
- ReimageRepair.exe (PID: 7448)
- ReimageRepair.exe (PID: 5380)
- slui.exe (PID: 1348)
- SystemSettings.exe (PID: 7396)
Uses NSLOOKUP.EXE to check DNS info
- ReimageRepair.exe (PID: 7448)
- ReimageRepair.exe (PID: 5380)
INFO
Checks supported languages
- ReimageRepair.exe (PID: 7448)
- sqlite3.exe (PID: 7568)
- sqlite3.exe (PID: 7664)
- sqlite3.exe (PID: 7748)
- ReimageRepair.exe (PID: 5380)
- sqlite3.exe (PID: 4488)
- sqlite3.exe (PID: 7280)
- sqlite3.exe (PID: 2244)
Reads the computer name
- ReimageRepair.exe (PID: 7448)
- ReimageRepair.exe (PID: 5380)
Create files in a temporary directory
- ReimageRepair.exe (PID: 7448)
- ReimageRepair.exe (PID: 5380)
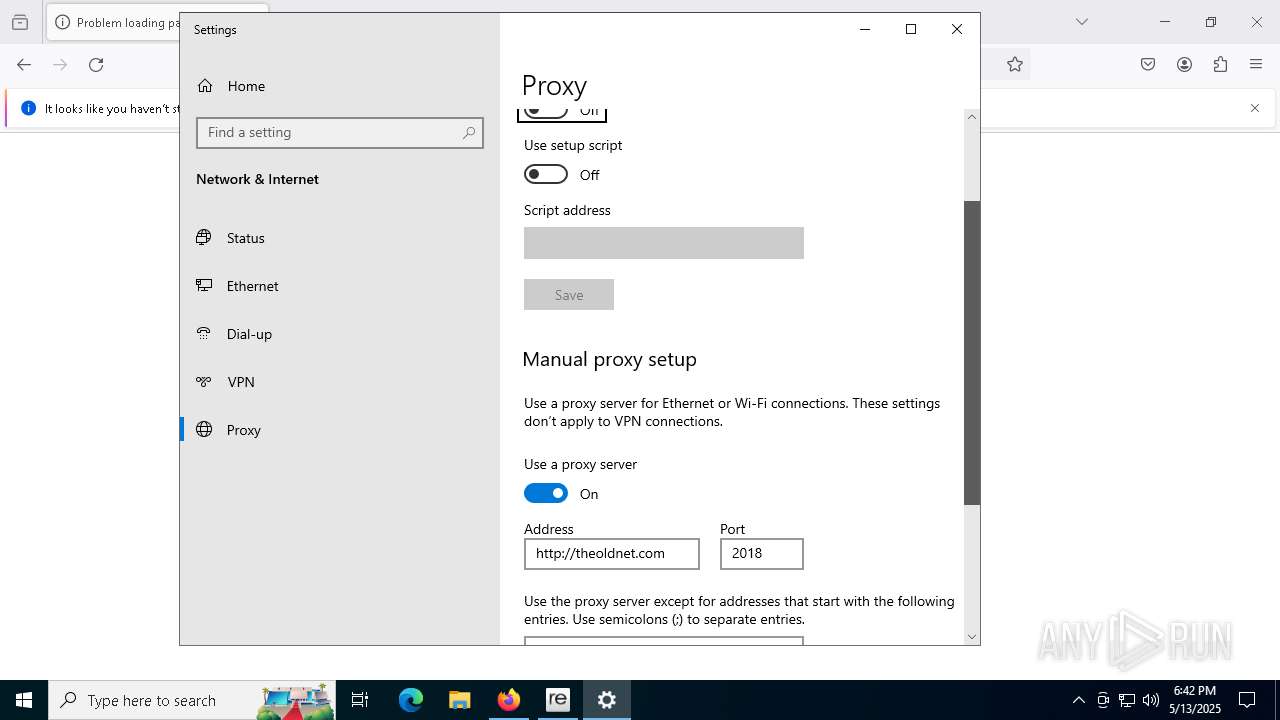
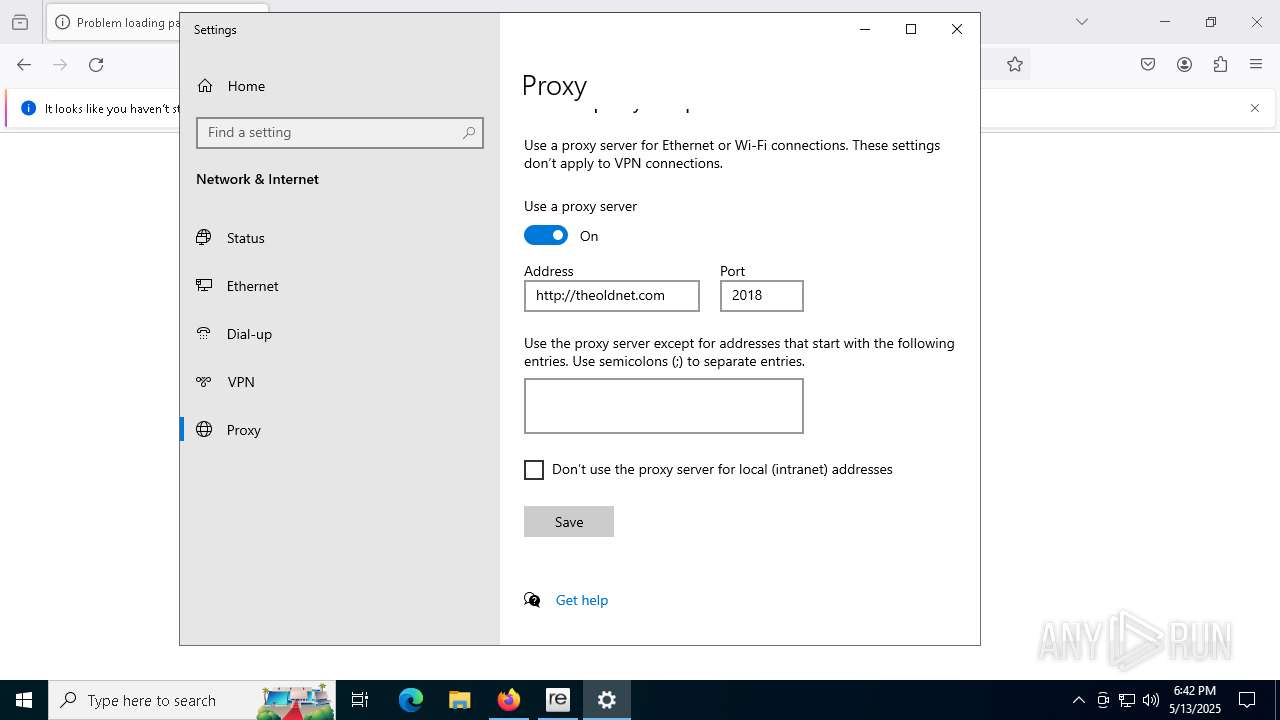
Checks proxy server information
- ReimageRepair.exe (PID: 7448)
- ReimageRepair.exe (PID: 5380)
- slui.exe (PID: 1348)
Manual execution by a user
- ReimageRepair.exe (PID: 5380)
- ReimageRepair.exe (PID: 4008)
- firefox.exe (PID: 7652)
Reads the software policy settings
- slui.exe (PID: 7912)
Connects to unusual port
- firefox.exe (PID: 7636)
Application launched itself
- firefox.exe (PID: 7652)
- firefox.exe (PID: 7636)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:02:24 19:19:59+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 28672 |
| InitializedDataSize: | 446976 |
| UninitializedDataSize: | 16896 |
| EntryPoint: | 0x39e3 |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.5.4.2 |
| ProductVersionNumber: | 1.5.4.2 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | Reimage |
| FileDescription: | Reimage Downloader |
| FileVersion: | 1.542 |
| InternalName: | Reimage Downloader |
| LegalCopyright: | © Reimage 2017 |
| LegalTrademarks: | Reimage |
| ProductName: | Reimage Repair |
| ProductVersion: | 1.542 |
Total processes
203
Monitored processes
67
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2252 -childID 2 -isForBrowser -prefsHandle 3576 -prefMapHandle 3624 -prefsLen 36588 -prefMapSize 244583 -jsInitHandle 1444 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {5db53c2b-2d2e-45e3-aba0-0f880aa925b7} 7636 "\\.\pipe\gecko-crash-server-pipe.7636" 182b7c6e690 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1020 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | nslookup.exe cdnrep.reimage.com | C:\Windows\SysWOW64\nslookup.exe | ReimageRepair.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: nslookup Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1348 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2092 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2612 -childID 1 -isForBrowser -prefsHandle 2792 -prefMapHandle 2780 -prefsLen 31447 -prefMapSize 244583 -jsInitHandle 1444 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {afdd7bbc-e082-4d78-8f8a-a0b7395eb62f} 7636 "\\.\pipe\gecko-crash-server-pipe.7636" 182b603ef50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 2244 | "C:\Users\admin\AppData\Local\Temp\sqlite3.exe" "C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite" "select value, expiry from moz_cookies where baseDomain like 'reimageplus.com' and name='_campaign';" | C:\Users\admin\AppData\Local\Temp\sqlite3.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 2288 | regsvr32 /s "C:\WINDOWS\system32\jscript.dll" | C:\Windows\System32\regsvr32.exe | — | ReimageRepair.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2456 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4444 -childID 7 -isForBrowser -prefsHandle 4068 -prefMapHandle 5668 -prefsLen 31248 -prefMapSize 244583 -jsInitHandle 1444 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {f85b7cf6-779f-45da-8540-4af61764d394} 7636 "\\.\pipe\gecko-crash-server-pipe.7636" 182b4e754d0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 2772 | "tasklist.exe" | C:\Windows\SysWOW64\tasklist.exe | — | ReimageRepair.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
22 115
Read events
21 952
Write events
14
Delete events
149
Modification events
| (PID) Process: | (7448) ReimageRepair.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Reimage\Reimage Repair |
| Operation: | write | Name: | Installer Language |
Value: 1033 | |||
| (PID) Process: | (7576) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{f414c260-6ac0-11cf-b6d1-00aa00bbbb58}\ProgID |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7576) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{f414c260-6ac0-11cf-b6d1-00aa00bbbb58}\OLEScript |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7576) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{f414c260-6ac0-11cf-b6d1-00aa00bbbb58}\Implemented Categories |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7576) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{f414c260-6ac0-11cf-b6d1-00aa00bbbb58}\InprocServer32 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7576) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{f414c260-6ac0-11cf-b6d1-00aa00bbbb58} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7576) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{f414c260-6ac0-11cf-b6d1-00aa00bbbb58}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Both | |||
| (PID) Process: | (7576) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{f414c261-6ac0-11cf-b6d1-00aa00bbbb58}\Implemented Categories\{0AEE2A92-BCBB-11D0-8C72-00C04FC2B085} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7576) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\JScript Author\CLSID |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7576) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\JScript Author\OLEScript |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
22
Suspicious files
100
Text files
41
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7448 | ReimageRepair.exe | C:\Windows\Reimage.ini | text | |
MD5:B880452B210C5DA32A477B42B7F8B692 | SHA256:66F36F5BC02D7215BEADD5948900B7EF3C1A956227269D22DD614E72C5945A79 | |||
| 7448 | ReimageRepair.exe | C:\Users\admin\AppData\Local\Temp\nsuC1FC.tmp\LogEx.dll | executable | |
MD5:0F96D9EB959AD4E8FD205E6D58CF01B8 | SHA256:57EDE354532937E38C4AE9DA3710EE295705EA9770C402DFB3A5C56A32FD4314 | |||
| 7448 | ReimageRepair.exe | C:\Users\admin\AppData\Local\Temp\nsuC1FC.tmp\System.dll | executable | |
MD5:BF712F32249029466FA86756F5546950 | SHA256:7851CB12FA4131F1FEE5DE390D650EF65CAC561279F1CFE70AD16CC9780210AF | |||
| 7448 | ReimageRepair.exe | C:\Users\admin\AppData\Local\Temp\nsuC1FC.tmp\nsExec.dll | executable | |
MD5:132E6153717A7F9710DCEA4536F364CD | SHA256:D29AFCE2588D8DD7BB94C00CA91CAC0E85B80FFA6B221F5FFCB83A2497228EB2 | |||
| 7448 | ReimageRepair.exe | C:\Users\admin\AppData\Local\Temp\nsuC1FC.tmp\modern-header.bmp | image | |
MD5:BBCA00F87A00AE8BDB3927D5C93D08CF | SHA256:D451E423EED515713117E53BD733A7333E64F2A0C7C5D695C6750AD919E70EC3 | |||
| 7448 | ReimageRepair.exe | C:\Users\admin\AppData\Local\Temp\nsfC374.tmp | text | |
MD5:B8E635EB01CAB0F0B09DF3F903DFCD8F | SHA256:389C3CCE5E24354CB2CCD139CE2C58352A45B61D6D3F4133C9A7C1E279EFC8D4 | |||
| 7448 | ReimageRepair.exe | C:\Users\admin\AppData\Local\Temp\FF.bat | text | |
MD5:B8E635EB01CAB0F0B09DF3F903DFCD8F | SHA256:389C3CCE5E24354CB2CCD139CE2C58352A45B61D6D3F4133C9A7C1E279EFC8D4 | |||
| 7568 | sqlite3.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7448 | ReimageRepair.exe | C:\Users\admin\AppData\Local\Temp\sqlite3.exe | executable | |
MD5:91CDCEA4BE94624E198D3012F5442584 | SHA256:CA4C0F1EC0CCBC9988EA3F43FF73FE84228FFB4D76BADDC386051DFFE7DDD8C2 | |||
| 7448 | ReimageRepair.exe | C:\Users\admin\AppData\Local\Temp\nsuC1FC.tmp\UserInfo.dll | executable | |
MD5:C7CE0E47C83525983FD2C4C9566B4AAD | SHA256:6293408A5FA6D0F55F0A4D01528EB5B807EE9447A75A28B5986267475EBCD3AE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
427
TCP/UDP connections
1 279
DNS requests
61
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7400 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.60:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7636 | firefox.exe | CONNECT | — | 159.203.14.9:2010 | http://firefox.settings.services.mozilla.com:443 | unknown | — | — | whitelisted |
7636 | firefox.exe | CONNECT | — | 159.203.14.9:2010 | http://firefox.settings.services.mozilla.com:443 | unknown | — | — | whitelisted |
7636 | firefox.exe | CONNECT | — | 159.203.14.9:2010 | http://firefox.settings.services.mozilla.com:443 | unknown | — | — | whitelisted |
7636 | firefox.exe | GET | — | 159.203.14.9:2010 | http://google.com/ | unknown | — | — | whitelisted |
7636 | firefox.exe | CONNECT | — | 159.203.14.9:2010 | http://firefox.settings.services.mozilla.com:443 | unknown | — | — | whitelisted |
7636 | firefox.exe | CONNECT | — | 159.203.14.9:2010 | http://firefox.settings.services.mozilla.com:443 | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1616 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.60:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7448 | ReimageRepair.exe | 161.47.7.14:80 | www.reimageplus.com | RACKSPACE | US | suspicious |
6544 | svchost.exe | 20.190.160.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.reimageplus.com |
| unknown |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |