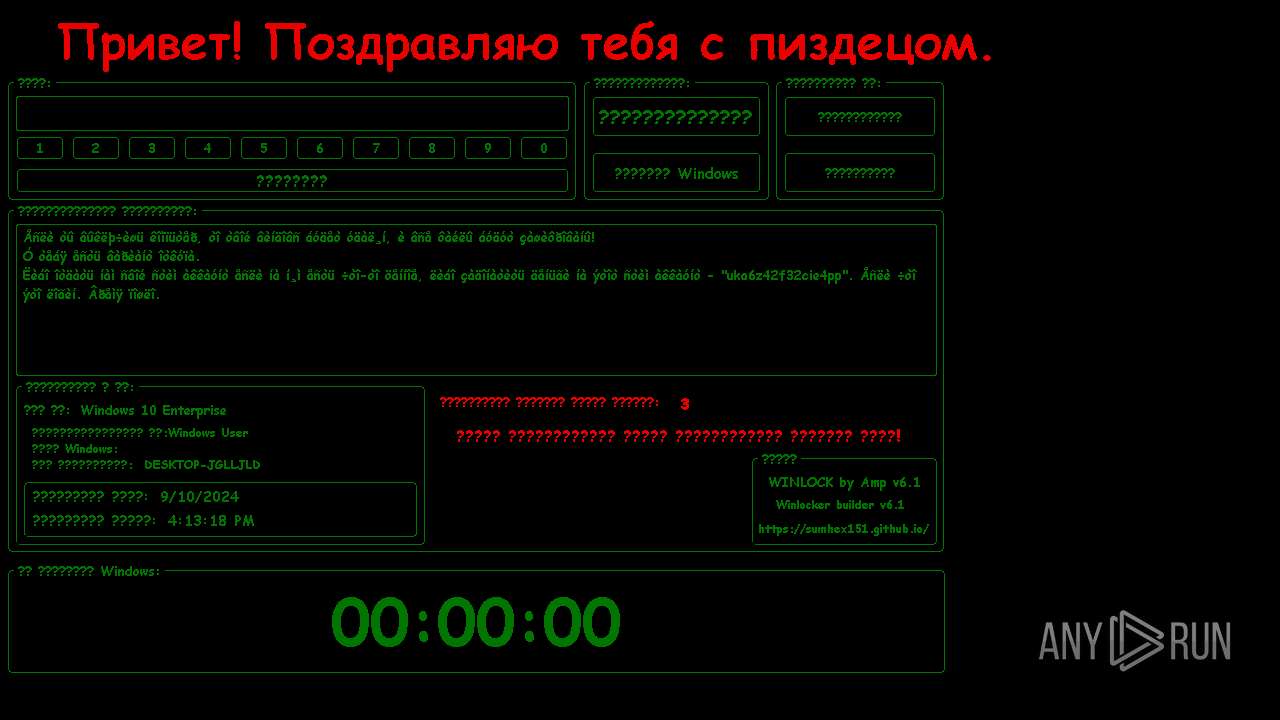
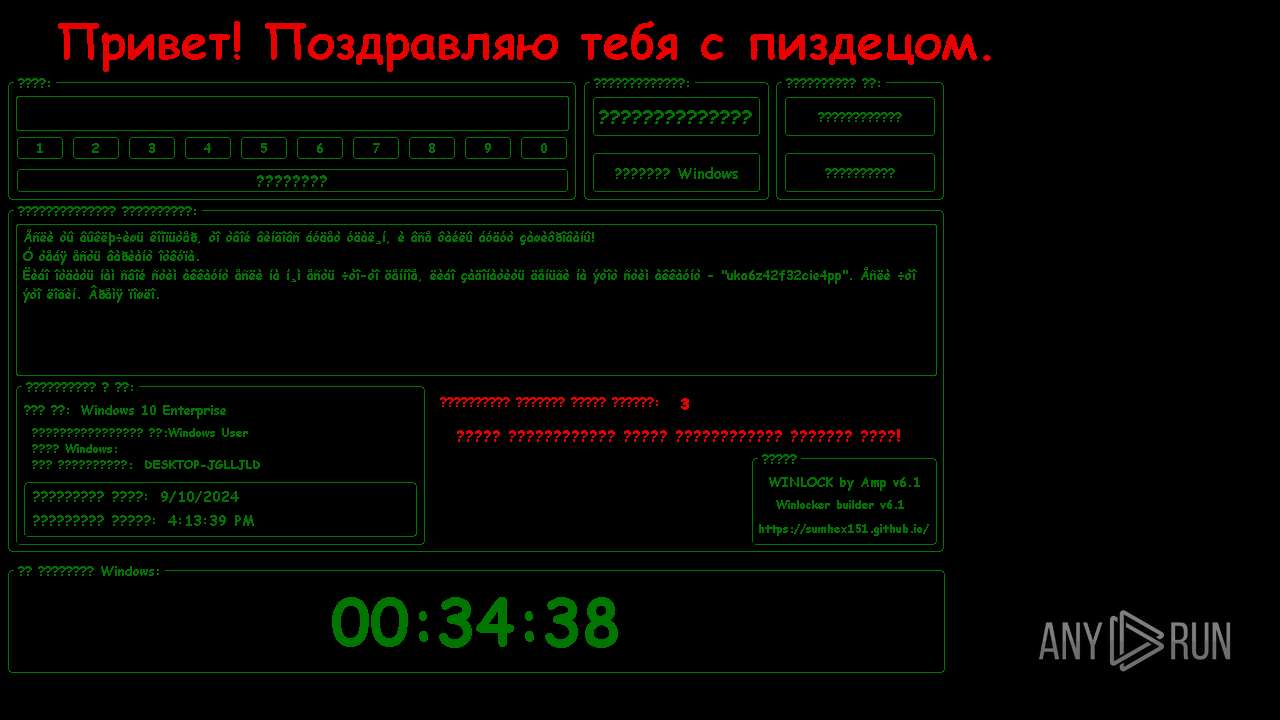
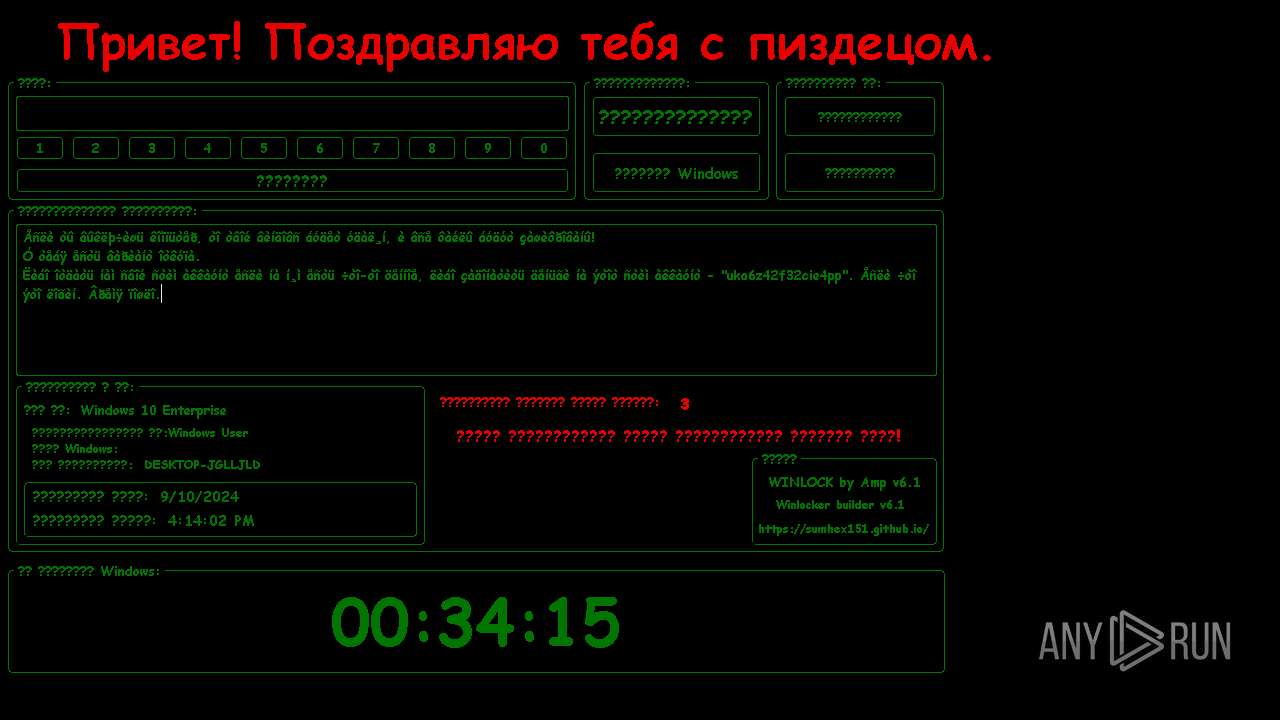
| File name: | WinLocker.exe |
| Full analysis: | https://app.any.run/tasks/06b1b8f8-1d4d-4002-addc-c86c7d081d64 |
| Verdict: | Malicious activity |
| Analysis date: | September 10, 2024, 16:13:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 1C620A1B027E461248279C7E081A71A3 |
| SHA1: | 7655DF116CC0810D368B1EFE743002F87AE52661 |
| SHA256: | 314C03E98209EDBBA09788406922FA27A117D93AB6651B2AA0F43FE5778646D8 |
| SSDEEP: | 98304:9cCyub1kqAzajfr/qSRmkgT2908yj2fBRhdLfCdat6zcMlU3UJfdA48X6GM+V:Guf |
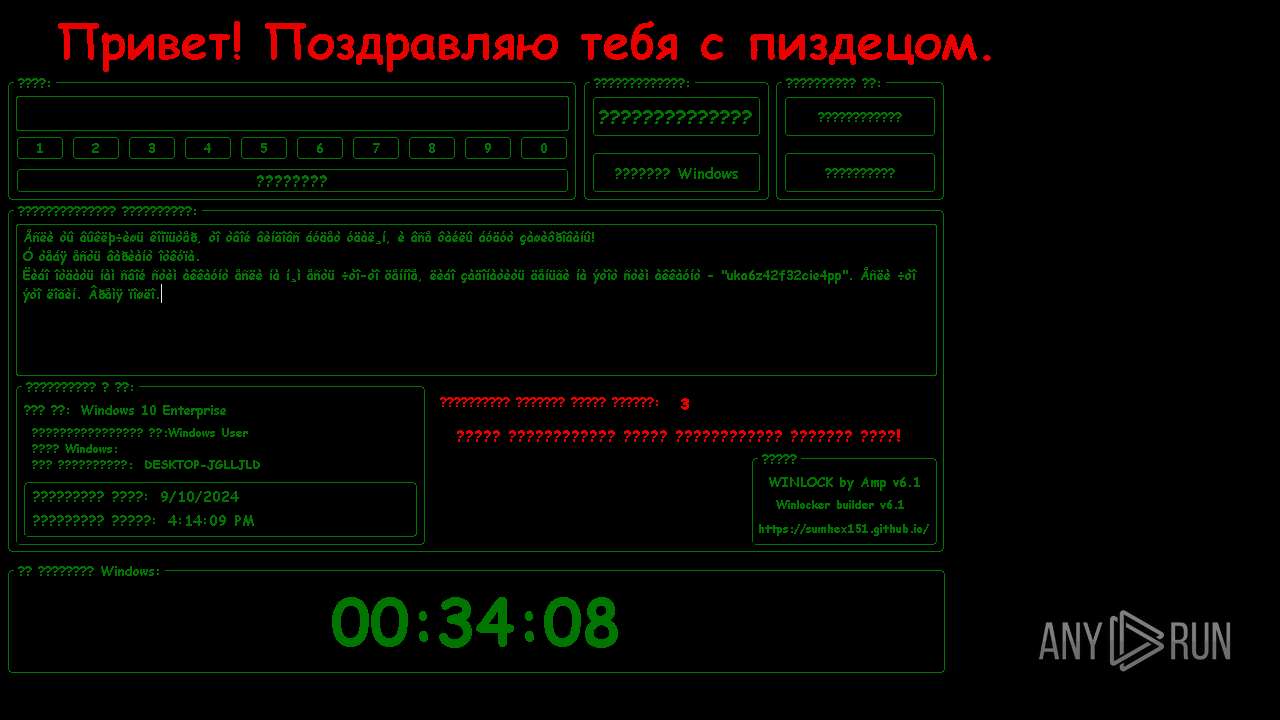
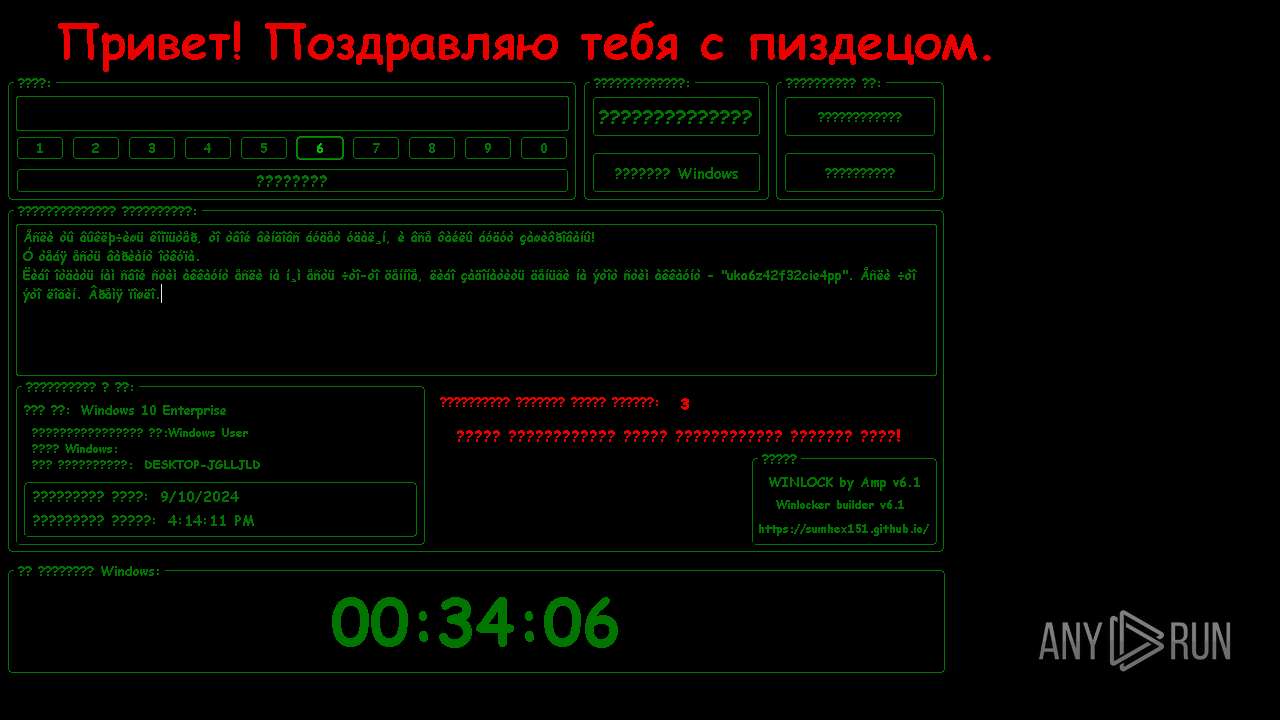
MALICIOUS
Disables the Shutdown in the Start menu
- WinLocker.exe (PID: 4440)
Changes the autorun value in the registry
- WinLocker.exe (PID: 4440)
UAC/LUA settings modification
- WinLocker.exe (PID: 4440)
Disables the Run the Start menu
- WinLocker.exe (PID: 4440)
Changes image file execution options
- WinLocker.exe (PID: 4440)
Disables the Find the Start menu
- WinLocker.exe (PID: 4440)
Disables the LogOff the Start menu
- WinLocker.exe (PID: 4440)
SUSPICIOUS
Creates file in the systems drive root
- WinLocker.exe (PID: 4440)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 5548)
There is functionality for taking screenshot (YARA)
- WinLocker.exe (PID: 4440)
INFO
Checks supported languages
- WinLocker.exe (PID: 4440)
- ShellExperienceHost.exe (PID: 5548)
Reads the computer name
- WinLocker.exe (PID: 4440)
- ShellExperienceHost.exe (PID: 5548)
Create files in a temporary directory
- WinLocker.exe (PID: 4440)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Borland Delphi 7 (94.6) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (2) |
| .scr | | | Windows screen saver (1.8) |
| .exe | | | Win32 Executable (generic) (0.6) |
| .exe | | | Win16/32 Executable Delphi generic (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 1146368 |
| InitializedDataSize: | 1500160 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x118d94 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
130
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4440 | "C:\Users\admin\AppData\Local\Temp\WinLocker.exe" | C:\Users\admin\AppData\Local\Temp\WinLocker.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 5548 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6288 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Exit code: 2147945463 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6676 | "C:\Users\admin\AppData\Local\Temp\WinLocker.exe" | C:\Users\admin\AppData\Local\Temp\WinLocker.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
538
Read events
510
Write events
28
Delete events
0
Modification events
| (PID) Process: | (4440) WinLocker.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\Windows\System |
| Operation: | write | Name: | DisableCMD |
Value: 2 | |||
| (PID) Process: | (4440) WinLocker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (4440) WinLocker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Java |
Value: C:\Users\admin\AppData\Local\Temp\WinLocker.exe | |||
| (PID) Process: | (4440) WinLocker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\explorer.exe |
| Operation: | write | Name: | Debugger |
Value: C:\Users\admin\AppData\Local\Temp\WinLocker.exe | |||
| (PID) Process: | (4440) WinLocker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\taskmgr.exe |
| Operation: | write | Name: | Debugger |
Value: C:\Users\admin\AppData\Local\Temp\WinLocker.exe | |||
| (PID) Process: | (4440) WinLocker.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Uninstall |
| Operation: | write | Name: | NoAddRemovePrograms |
Value: 1 | |||
| (PID) Process: | (4440) WinLocker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | HideFastUserSwitching |
Value: 1 | |||
| (PID) Process: | (4440) WinLocker.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Advanced |
| Operation: | write | Name: | NoClose |
Value: 1 | |||
| (PID) Process: | (4440) WinLocker.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableLockWorkstation |
Value: 1 | |||
| (PID) Process: | (4440) WinLocker.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableChangePassword |
Value: 1 | |||
Executable files
0
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4440 | WinLocker.exe | \Device\Harddisk0\DR0 | — | |
MD5:— | SHA256:— | |||
| 4440 | WinLocker.exe | C:\Users\admin\AppData\Local\Temp\Time.ini | text | |
MD5:EB13B7EAF7F30D348E471F0907B31AAC | SHA256:94BA214735774FB4E68BE906C3E181D29C71DBBCD10540E70BA7021FCF5EA3AA | |||
| 4440 | WinLocker.exe | C:\MBR.bin | binary | |
MD5:0DA182957D5B2BD11A50DA7293ACEB77 | SHA256:4EAE113930004A304FCAB258B075265F9E934A46D9CA09665258ACCDA77F87D2 | |||
| 4440 | WinLocker.exe | C:\Users\admin\AppData\Local\Temp\Time2.ini | text | |
MD5:33498F44B01748F2C22885625AE03B7B | SHA256:882DA845177022E108A6C468625A168EE19FCD523C56F1FF3993E8F101FBFD19 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
30
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6020 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1496 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5044 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5044 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6020 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1332 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6020 | svchost.exe | 52.167.249.196:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6020 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.106.86.13:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1496 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1496 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |