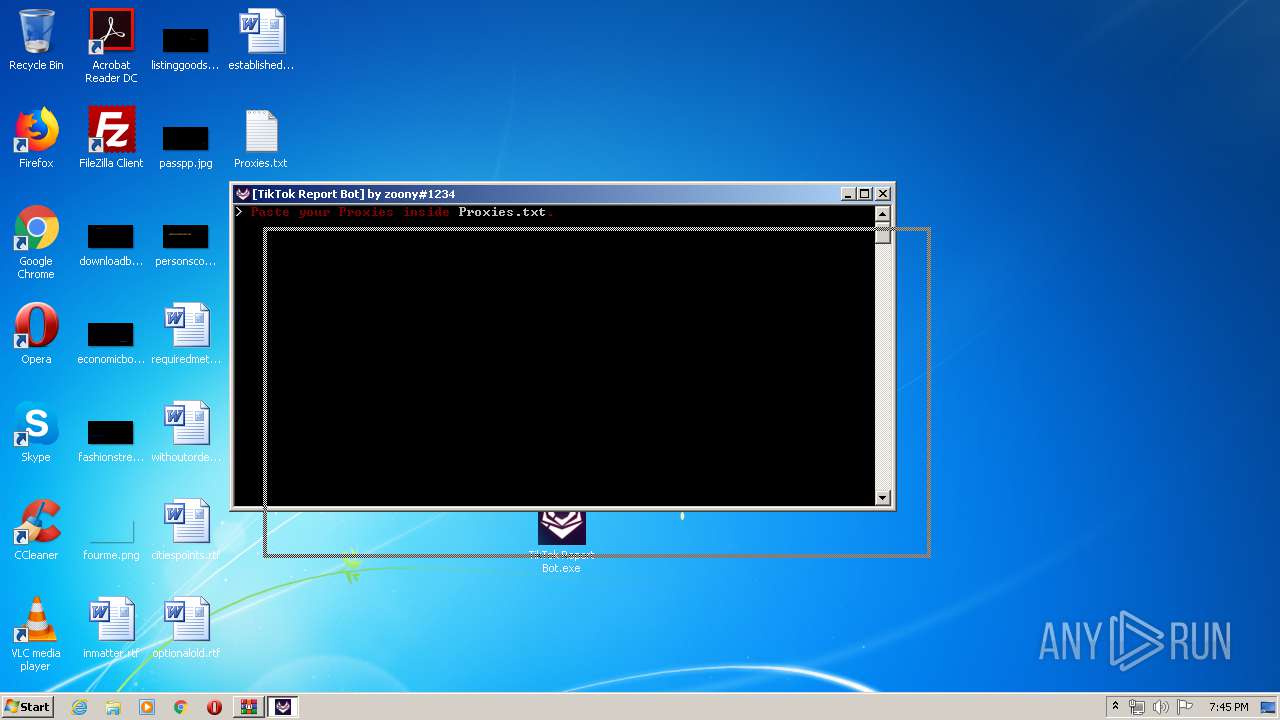
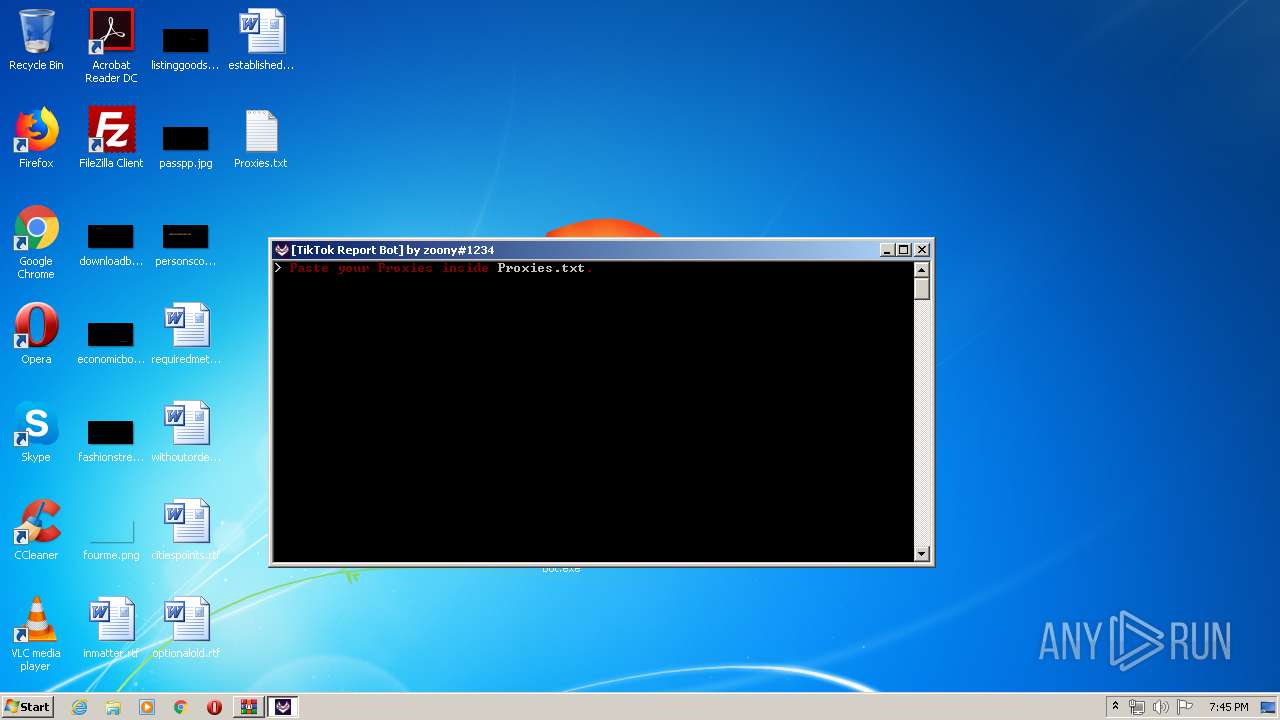
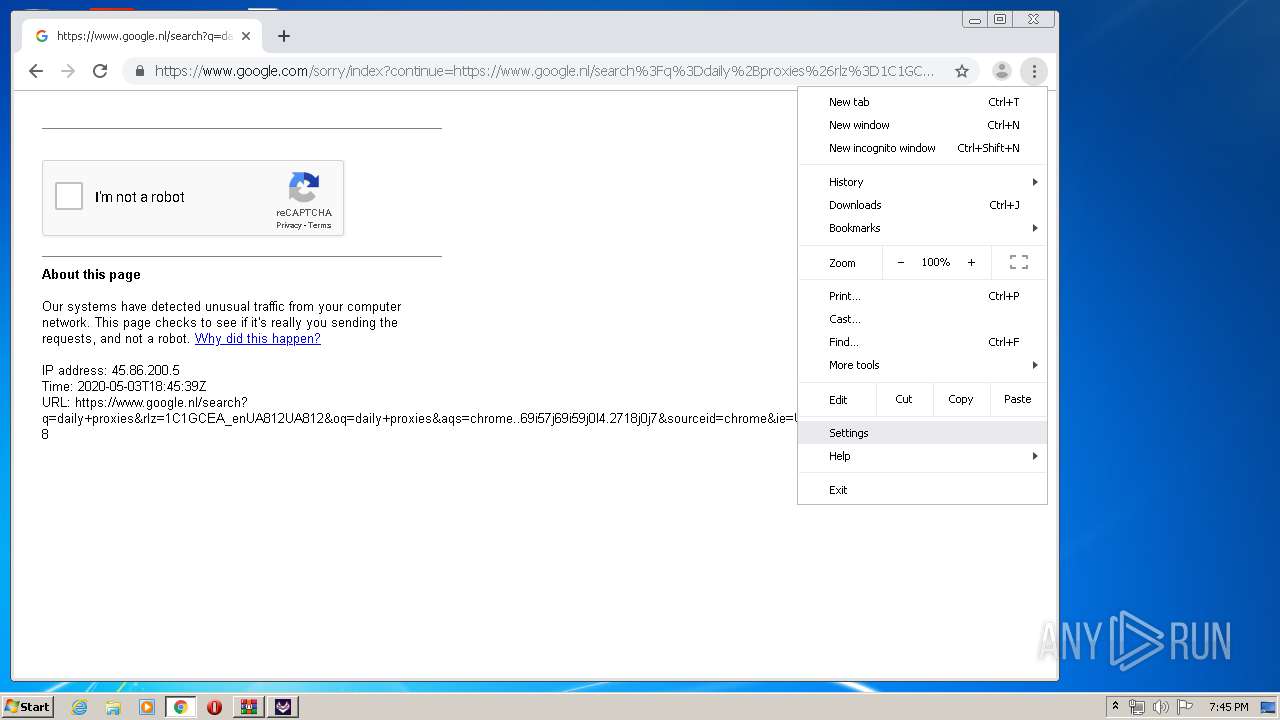
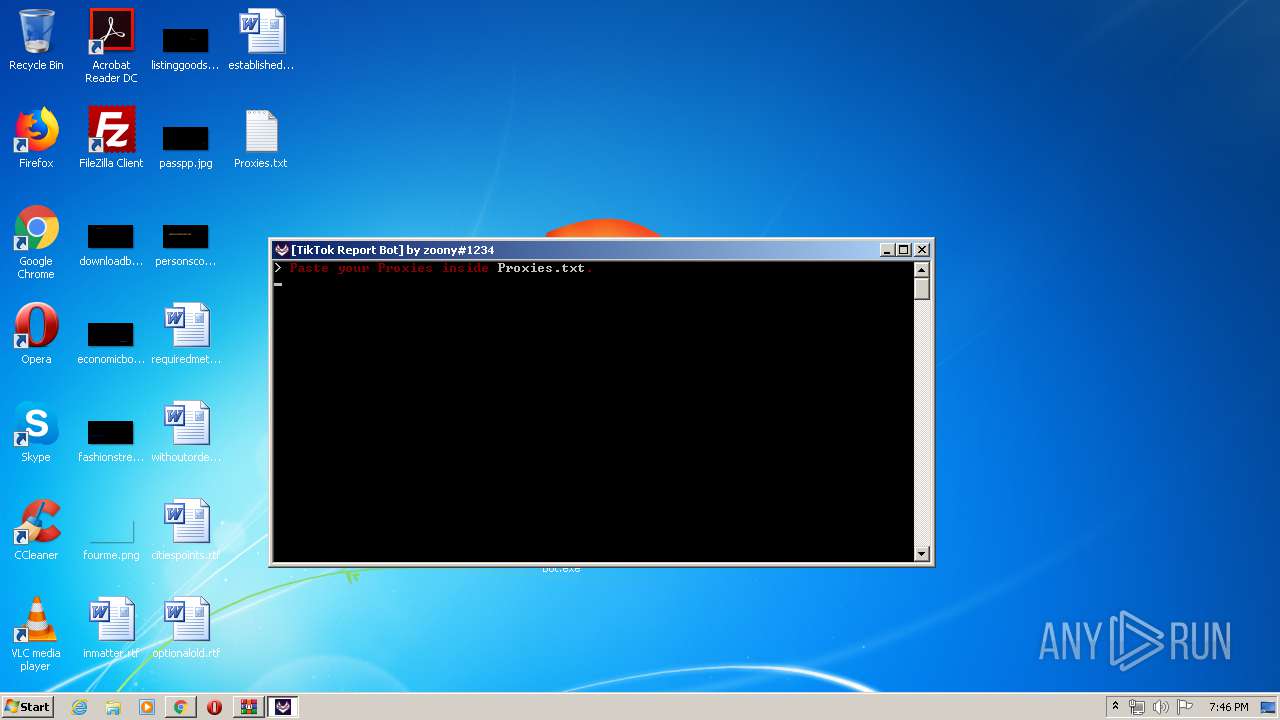
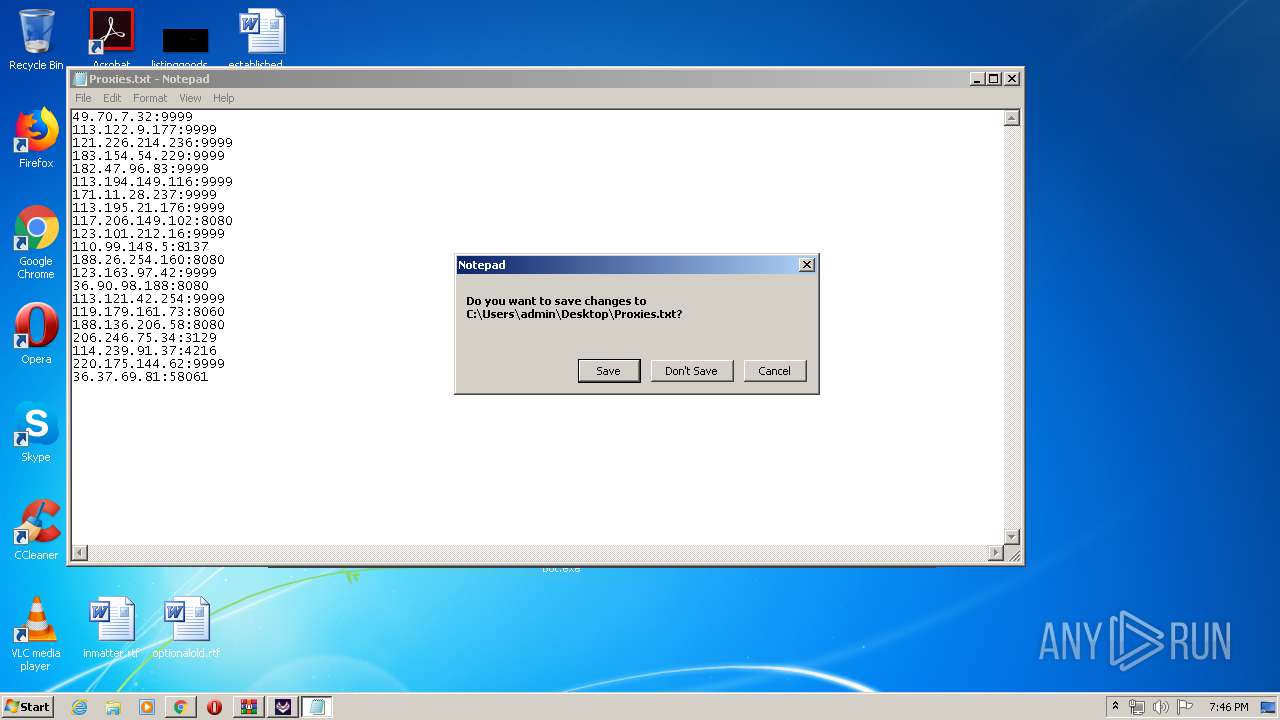
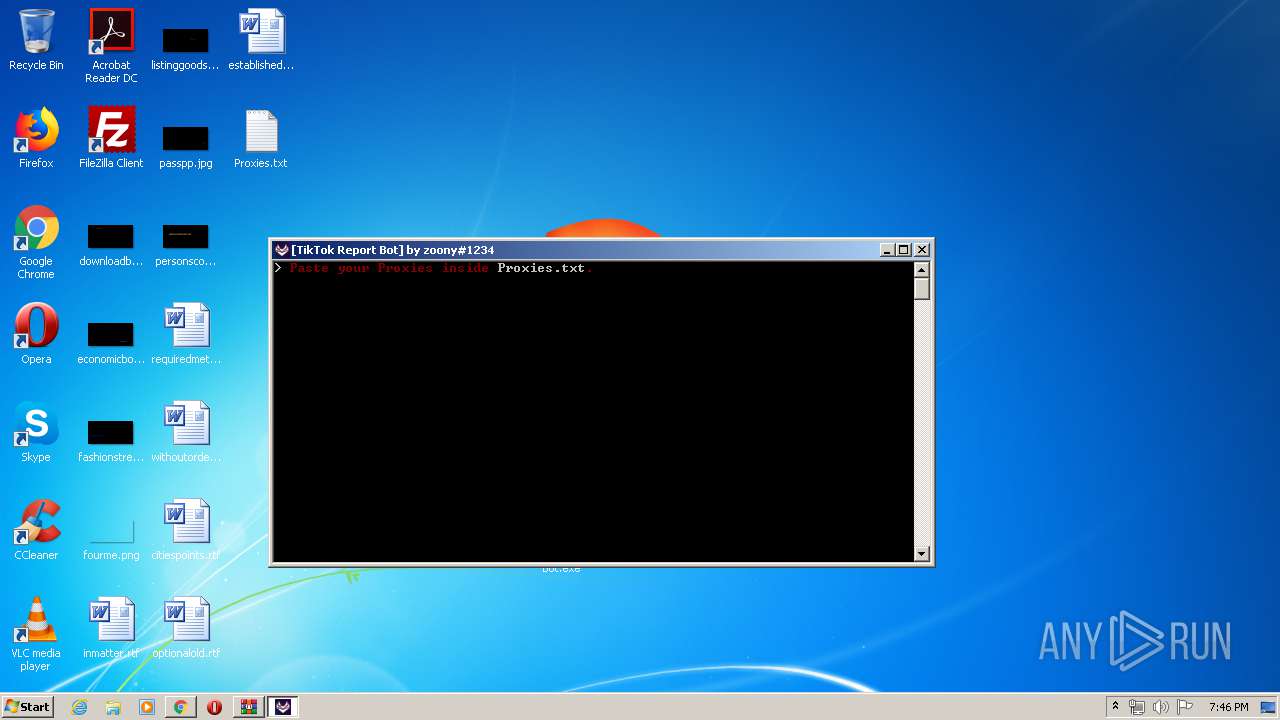
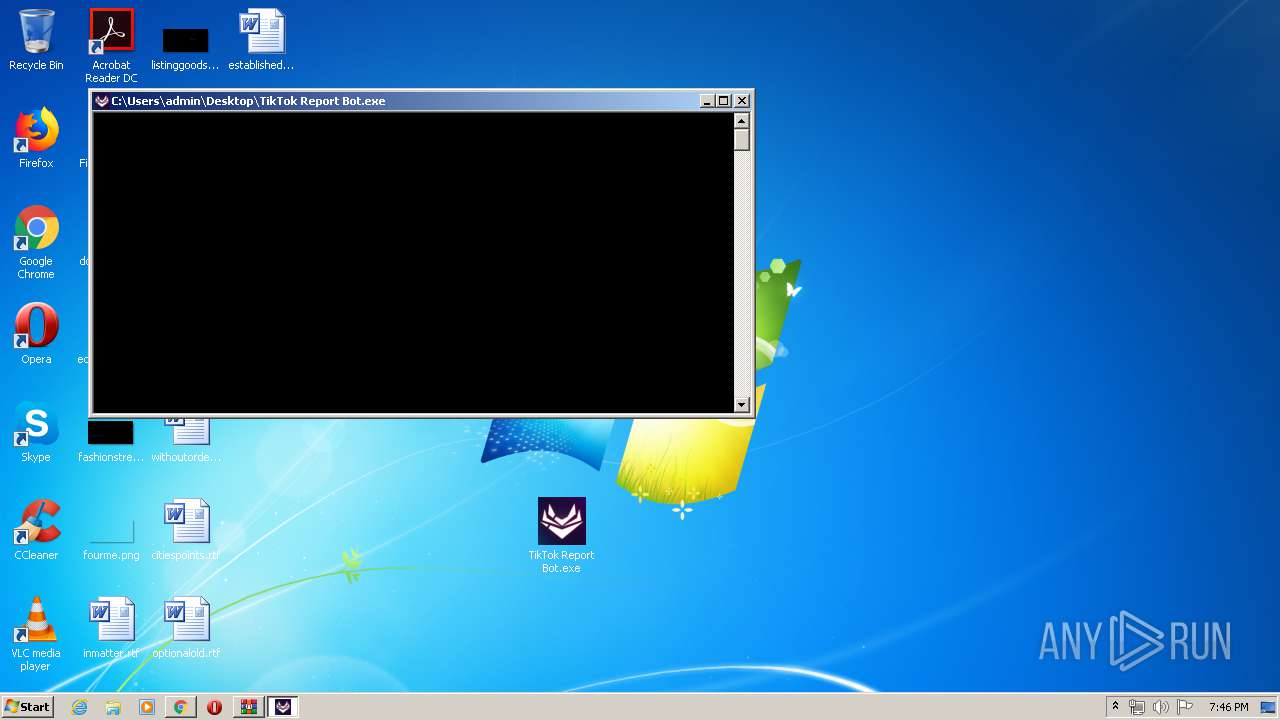
| File name: | TikTok Report Bot.rar |
| Full analysis: | https://app.any.run/tasks/1d62da50-5582-433d-a7be-880a6751ed43 |
| Verdict: | Malicious activity |
| Analysis date: | May 03, 2020, 18:44:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 86D6CC7A6E8DDC89104B0F88634598F6 |
| SHA1: | 44B8528AB490F2DDAEA8E5F20554BEC7C2362004 |
| SHA256: | 313E223EA7EB40FFA1DDE078408467284E5623BEEC6CCBBA8D1B0022EEF0A2A0 |
| SSDEEP: | 393216:YjYil9jrZxJTsnLpoSjK+O9kyKzkLtQHieR:YEilFJQowK+OHKzxR |
MALICIOUS
Application was dropped or rewritten from another process
- TikTok Report Bot.exe (PID: 2600)
- TikTok Report Bot.exe (PID: 4060)
- TikTok Report Bot.exe (PID: 3572)
- TikTok Report Bot.exe (PID: 2160)
Loads dropped or rewritten executable
- TikTok Report Bot.exe (PID: 4060)
- TikTok Report Bot.exe (PID: 2160)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1524)
- TikTok Report Bot.exe (PID: 2600)
- TikTok Report Bot.exe (PID: 3572)
Uses WMIC.EXE to obtain a system information
- TikTok Report Bot.exe (PID: 4060)
- TikTok Report Bot.exe (PID: 2160)
Loads Python modules
- TikTok Report Bot.exe (PID: 4060)
- TikTok Report Bot.exe (PID: 2160)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2928)
INFO
Manual execution by user
- TikTok Report Bot.exe (PID: 2600)
- chrome.exe (PID: 2928)
- NOTEPAD.EXE (PID: 2680)
- TikTok Report Bot.exe (PID: 3572)
Reads settings of System Certificates
- TikTok Report Bot.exe (PID: 4060)
- TikTok Report Bot.exe (PID: 2160)
- chrome.exe (PID: 2936)
Dropped object may contain Bitcoin addresses
- TikTok Report Bot.exe (PID: 2600)
- chrome.exe (PID: 2928)
- TikTok Report Bot.exe (PID: 3572)
Application launched itself
- chrome.exe (PID: 2928)
Reads the hosts file
- chrome.exe (PID: 2936)
- chrome.exe (PID: 2928)
Dropped object may contain TOR URL's
- chrome.exe (PID: 2928)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
101
Monitored processes
56
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 280 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,57534624273335631,2671761655600428602,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7147367885830768754 --renderer-client-id=10 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3560 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 304 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=996,57534624273335631,2671761655600428602,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=3640325108558514034 --mojo-platform-channel-handle=4648 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 588 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=996,57534624273335631,2671761655600428602,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=1184260094536423074 --mojo-platform-channel-handle=3320 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 620 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=996,57534624273335631,2671761655600428602,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=16579278426307066792 --mojo-platform-channel-handle=4160 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 680 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,57534624273335631,2671761655600428602,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7280641956156467347 --renderer-client-id=24 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4756 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 772 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,57534624273335631,2671761655600428602,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=146194410448140694 --renderer-client-id=30 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4636 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 880 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,57534624273335631,2671761655600428602,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=13525939835607698522 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2432 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1092 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,57534624273335631,2671761655600428602,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=12862329599646883960 --renderer-client-id=42 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4244 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1348 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6982a9d0,0x6982a9e0,0x6982a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1352 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=996,57534624273335631,2671761655600428602,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=14124930678192351123 --mojo-platform-channel-handle=4340 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
1 426
Read events
1 295
Write events
123
Delete events
8
Modification events
| (PID) Process: | (1524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1524) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\TikTok Report Bot.rar | |||
| (PID) Process: | (1524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2928) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2928) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
Executable files
133
Suspicious files
107
Text files
334
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2600 | TikTok Report Bot.exe | C:\Users\admin\AppData\Local\Temp\_MEI26002\Crypto\Cipher\_raw_ctr.cp37-win32.pyd | executable | |
MD5:1ED1FA9D2CA368AFF1AE133E6DB469C2 | SHA256:D8A5300EB9E1CC717036C9B47EDEED3B41405BCC2FCAE0E4CDBD1A676934D137 | |||
| 2600 | TikTok Report Bot.exe | C:\Users\admin\AppData\Local\Temp\_MEI26002\Crypto\Cipher\_raw_arc2.cp37-win32.pyd | executable | |
MD5:2FABA6133AEAE941D47AD5545151B6C6 | SHA256:C2FDF4302D4062ABFB966E0EF47F47D8305930D08C9467D087311F661D8C6EB0 | |||
| 2600 | TikTok Report Bot.exe | C:\Users\admin\AppData\Local\Temp\_MEI26002\Crypto\Cipher\_raw_blowfish.cp37-win32.pyd | executable | |
MD5:BDF2E776C9344B811D3B211CA0AAE84B | SHA256:2465B1FD959A8DF6B9C46ADBD01DD089951E54334759B3FC49C3BFDCFECD53BE | |||
| 2600 | TikTok Report Bot.exe | C:\Users\admin\AppData\Local\Temp\_MEI26002\Crypto\Cipher\_raw_aesni.cp37-win32.pyd | executable | |
MD5:6E2246CF80FB80BBBF4EF4EC427F1551 | SHA256:1CE466D147637C7DDD906854506D01A07FCFF807146A73E4F7B54AC7DD74977E | |||
| 2600 | TikTok Report Bot.exe | C:\Users\admin\AppData\Local\Temp\_MEI26002\Crypto\Cipher\_raw_des.cp37-win32.pyd | executable | |
MD5:170848C9DD3554E62B2959FA4DCA485E | SHA256:99D4A0D313B1A46110313F7A7FC05E075855BA37B78BFC63492C6373DF0C2E07 | |||
| 2600 | TikTok Report Bot.exe | C:\Users\admin\AppData\Local\Temp\_MEI26002\Crypto\Cipher\_raw_cast.cp37-win32.pyd | executable | |
MD5:8FF66E96E39F44056B1C0E49F5D6F15C | SHA256:4BEDBE1230EB95949D9B5F20A50E51CBD4910C0589BC679B9D3D97F3720C8A2E | |||
| 2600 | TikTok Report Bot.exe | C:\Users\admin\AppData\Local\Temp\_MEI26002\Crypto\Cipher\_raw_ocb.cp37-win32.pyd | executable | |
MD5:D8B06F7A097CA90ABE1A6A7A4E302F87 | SHA256:4CD47357A2FF25A21CA64F093D5FFA59AA73E25666C4DAE921614F7EA9FC2E3E | |||
| 2600 | TikTok Report Bot.exe | C:\Users\admin\AppData\Local\Temp\_MEI26002\Crypto\Hash\_BLAKE2b.cp37-win32.pyd | executable | |
MD5:76463845DDA31656F8A7E015DFB8F989 | SHA256:546803EB742F36B694AE6329329E4BB36FA3B4A17173DFA623ED1F8AD120DD59 | |||
| 2600 | TikTok Report Bot.exe | C:\Users\admin\AppData\Local\Temp\_MEI26002\Crypto\Cipher\_raw_cfb.cp37-win32.pyd | executable | |
MD5:E92E8E711ECB30CFF67014C39176E180 | SHA256:E9C7E46571D11977D7A5D57B9D8420B8413DCFC0F4897C3AFAE21EC457976181 | |||
| 2600 | TikTok Report Bot.exe | C:\Users\admin\AppData\Local\Temp\_MEI26002\Crypto\Cipher\_raw_des3.cp37-win32.pyd | executable | |
MD5:708B780DFB8ED59111B988A42330D0E7 | SHA256:265DFFF8267CBE91C83AD3AC42D5728E273D5B52DB2B53C0691D4CD53E94D175 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
136
DNS requests
74
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
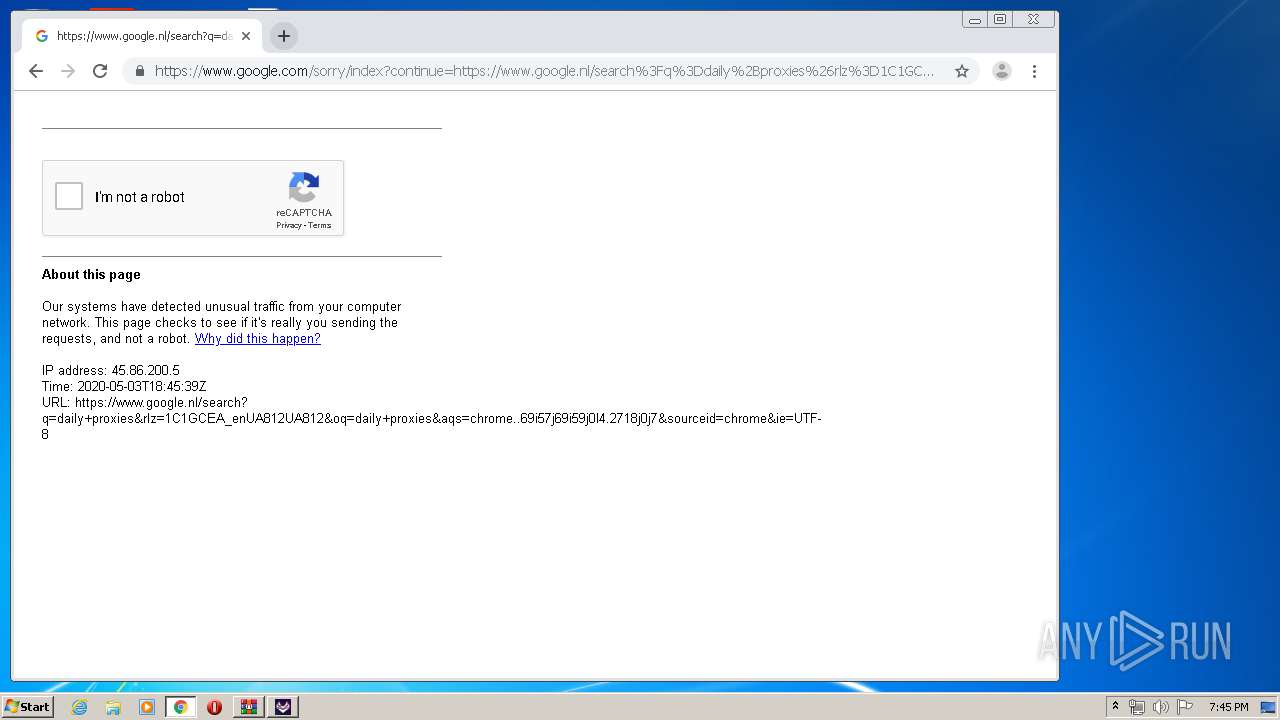
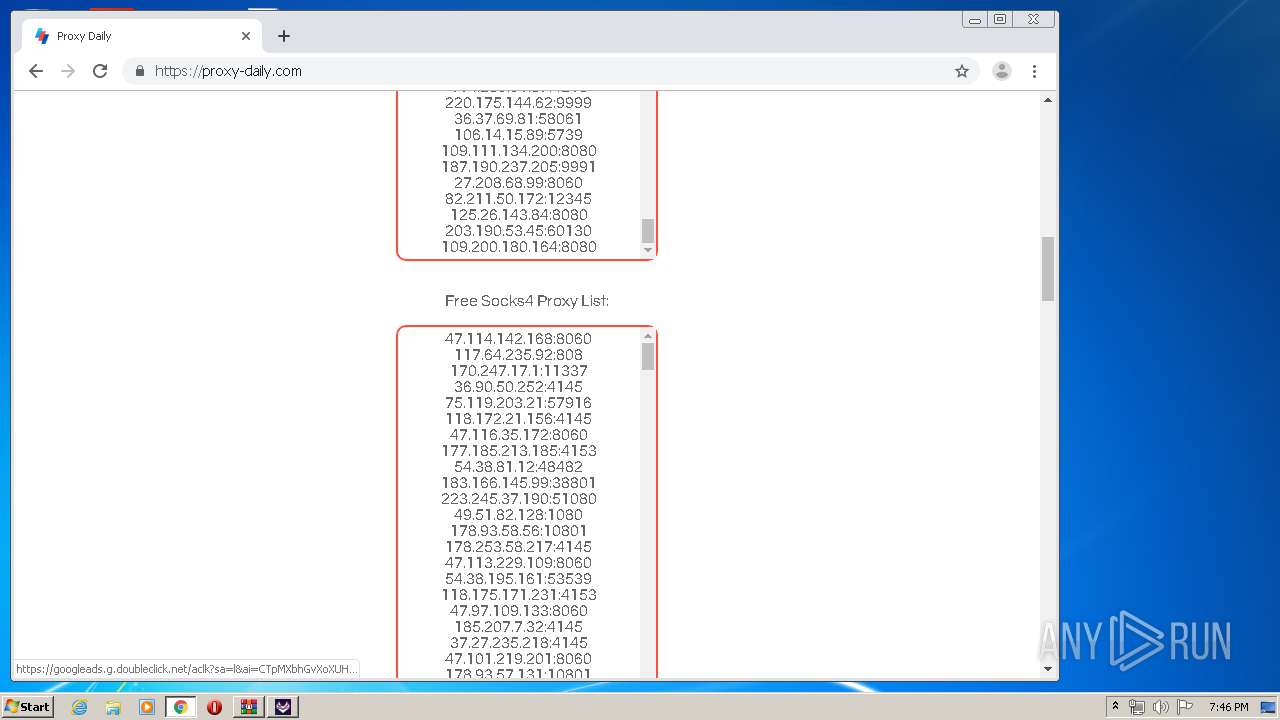
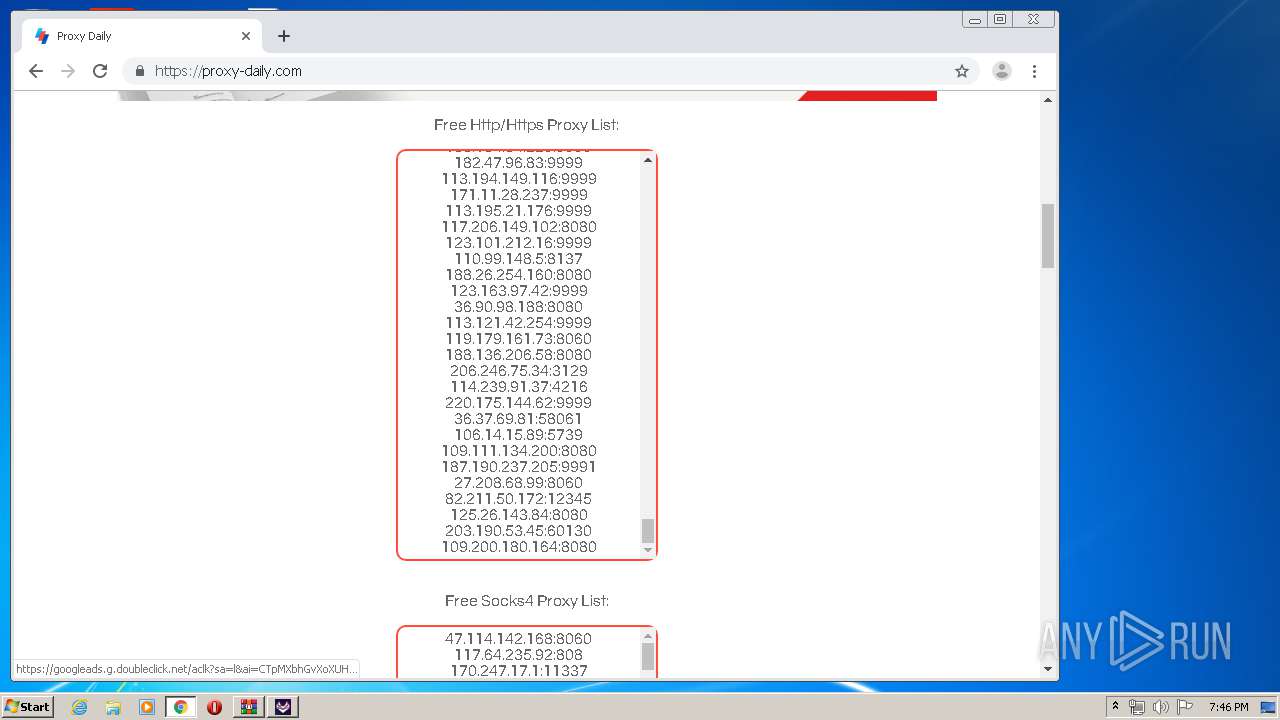
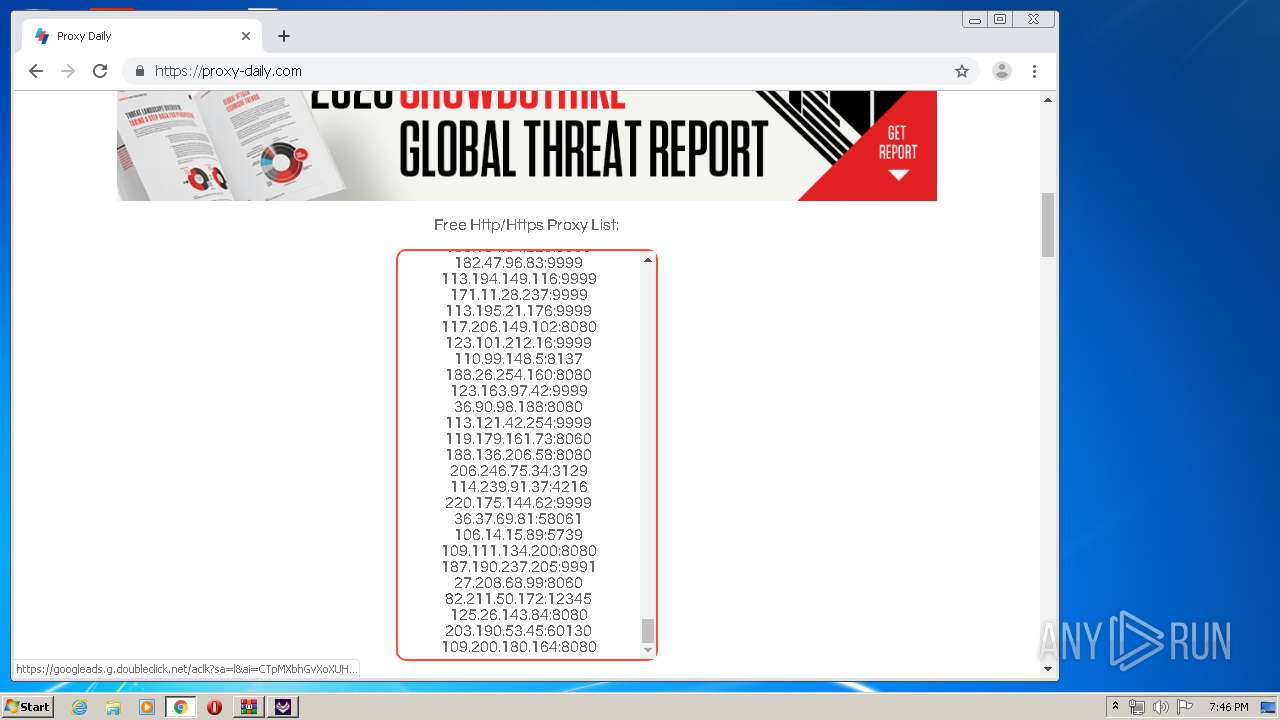
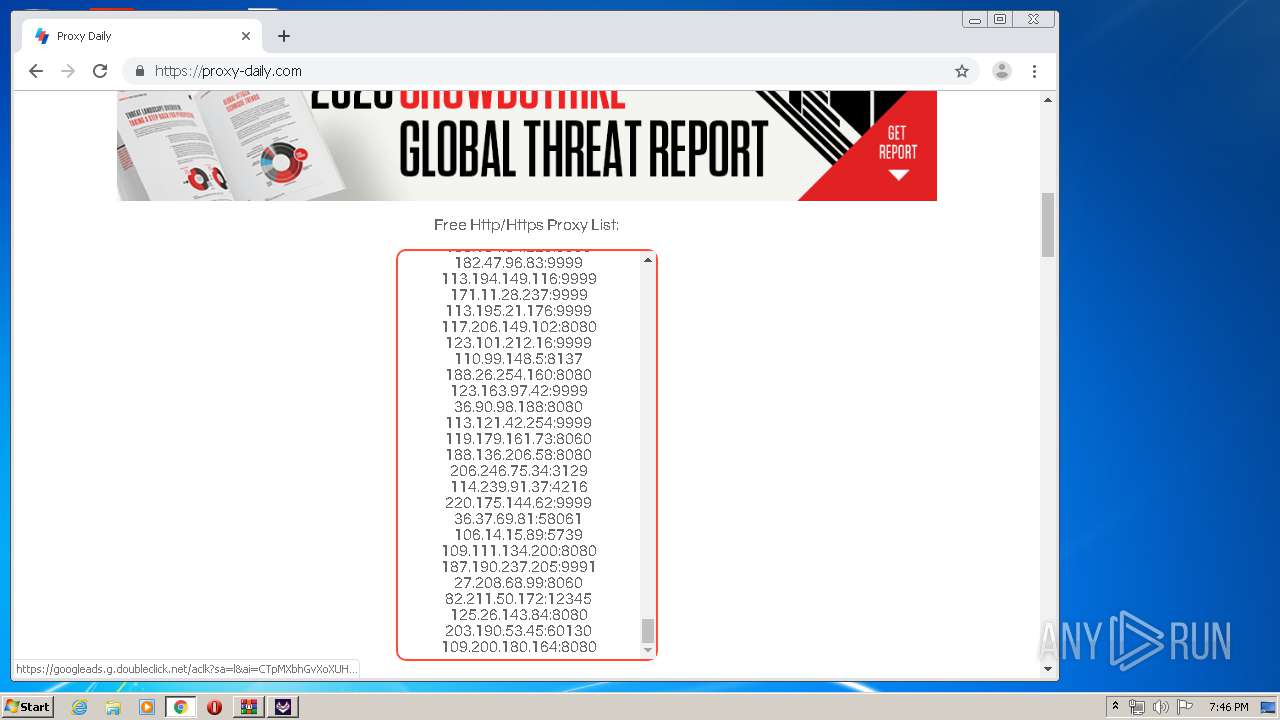
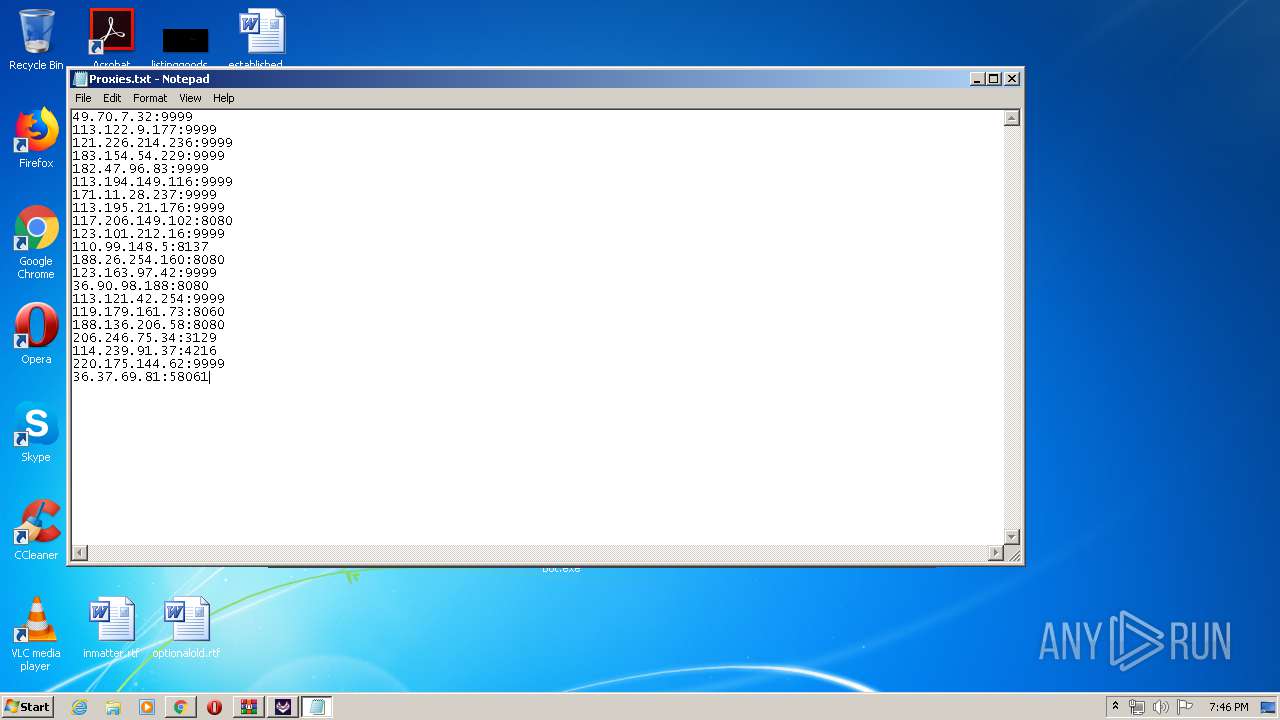
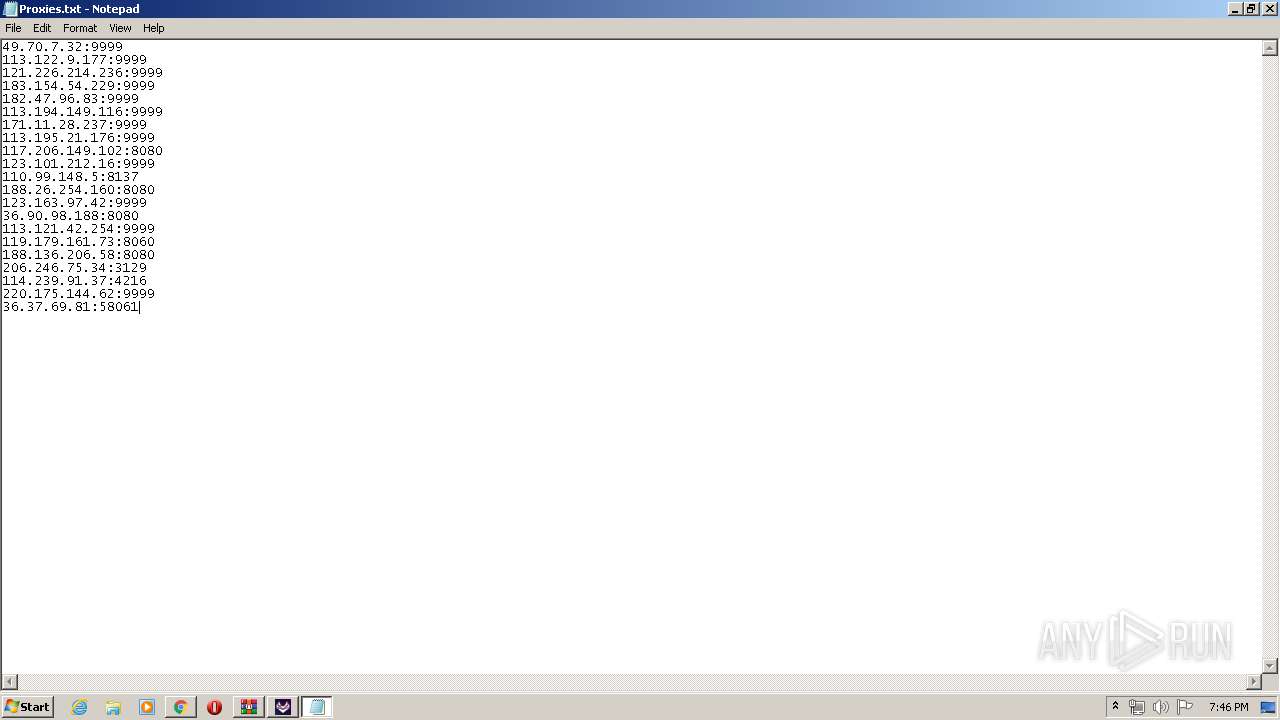
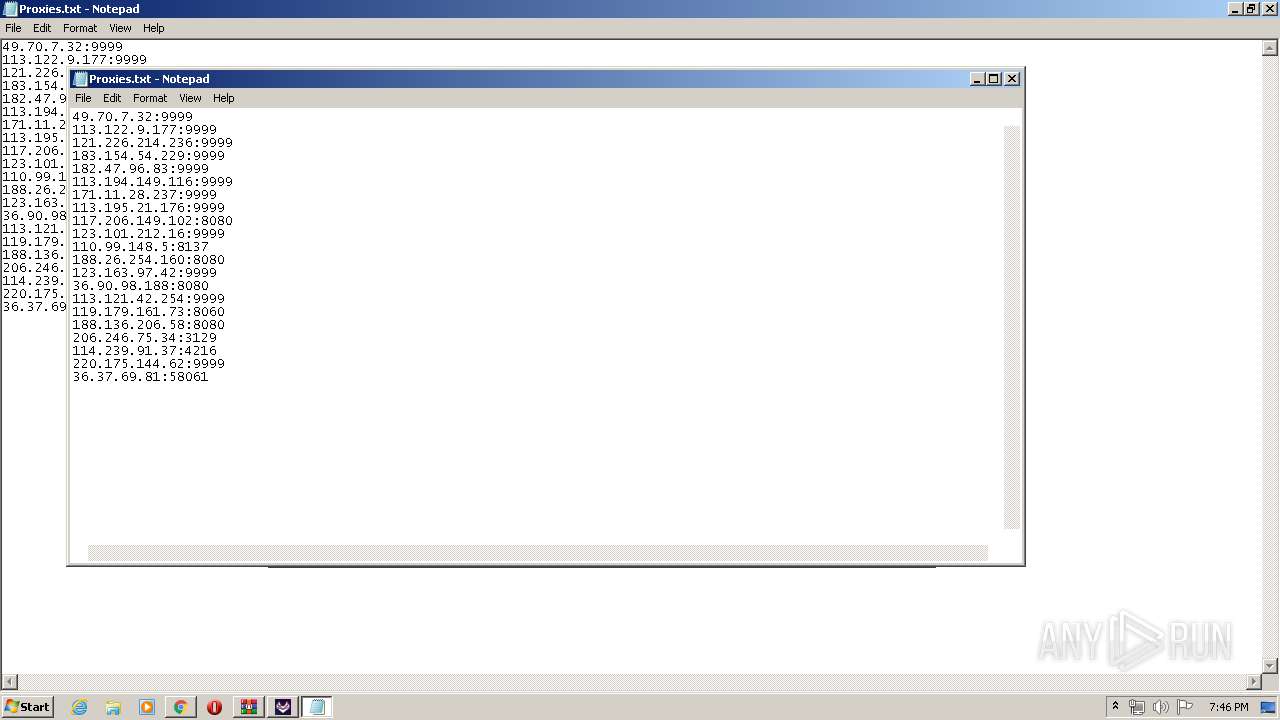
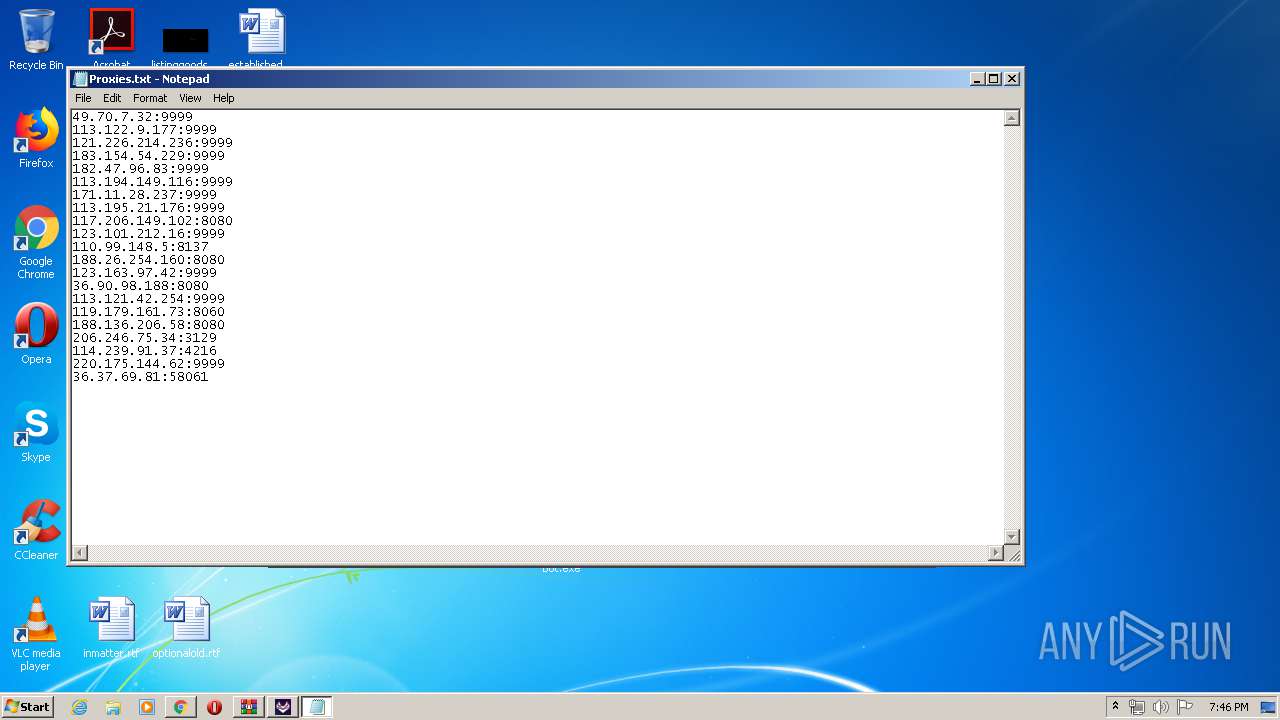
2160 | TikTok Report Bot.exe | CONNECT | — | 188.26.254.160:8080 | http://188.26.254.160:8080www.tiktok.com:443 | RO | — | — | unknown |
2160 | TikTok Report Bot.exe | CONNECT | — | 188.26.254.160:8080 | http://188.26.254.160:8080www.tiktok.com:443 | RO | — | — | unknown |
2160 | TikTok Report Bot.exe | CONNECT | — | 117.206.149.102:8080 | http://117.206.149.102:8080www.tiktok.com:443 | IN | — | — | unknown |
2160 | TikTok Report Bot.exe | CONNECT | — | 117.206.149.102:8080 | http://117.206.149.102:8080www.tiktok.com:443 | IN | — | — | unknown |
2160 | TikTok Report Bot.exe | CONNECT | — | 117.206.149.102:8080 | http://117.206.149.102:8080www.tiktok.com:443 | IN | — | — | unknown |
2160 | TikTok Report Bot.exe | CONNECT | — | 188.26.254.160:8080 | http://188.26.254.160:8080www.tiktok.com:443 | RO | — | — | unknown |
2936 | chrome.exe | GET | 200 | 173.194.150.231:80 | http://r1---sn-2gb7sn7s.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjY5QUFXTEQwc2RPVXhRY3picjhxblh1dw/7619.603.0.2_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mh=Qx&mip=45.86.200.5&mm=28&mn=sn-2gb7sn7s&ms=nvh&mt=1588531456&mv=m&mvi=0&pl=25&shardbypass=yes | US | crx | 816 Kb | whitelisted |
2936 | chrome.exe | GET | 302 | 172.217.23.110:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 517 b | whitelisted |
2936 | chrome.exe | GET | 302 | 172.217.23.110:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjY5QUFXTEQwc2RPVXhRY3picjhxblh1dw/7619.603.0.2_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 522 b | whitelisted |
2160 | TikTok Report Bot.exe | CONNECT | — | 36.90.98.188:8080 | http://36.90.98.188:8080www.tiktok.com:443 | ID | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4060 | TikTok Report Bot.exe | 104.23.98.190:443 | pastebin.com | Cloudflare Inc | US | malicious |
2936 | chrome.exe | 172.217.22.77:443 | accounts.google.com | Google Inc. | US | whitelisted |
4060 | TikTok Report Bot.exe | 3.125.110.76:27017 | zoony-shard-00-01-kn0um.mongodb.net | — | US | unknown |
2936 | chrome.exe | 172.217.23.99:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2936 | chrome.exe | 216.58.210.10:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2936 | chrome.exe | 216.58.212.131:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2936 | chrome.exe | 172.217.22.46:443 | ogs.google.com.ua | Google Inc. | US | whitelisted |
2936 | chrome.exe | 172.217.23.110:443 | apis.google.com | Google Inc. | US | whitelisted |
2936 | chrome.exe | 172.217.23.100:443 | www.google.com | Google Inc. | US | whitelisted |
— | — | 172.217.22.46:443 | ogs.google.com.ua | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| malicious |
_mongodb._tcp.zoony-kn0um.mongodb.net |
| unknown |
zoony-kn0um.mongodb.net |
| unknown |
zoony-shard-00-01-kn0um.mongodb.net |
| unknown |
zoony-shard-00-02-kn0um.mongodb.net |
| unknown |
zoony-shard-00-00-kn0um.mongodb.net |
| unknown |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com.ua |
| whitelisted |
fonts.googleapis.com |
| whitelisted |