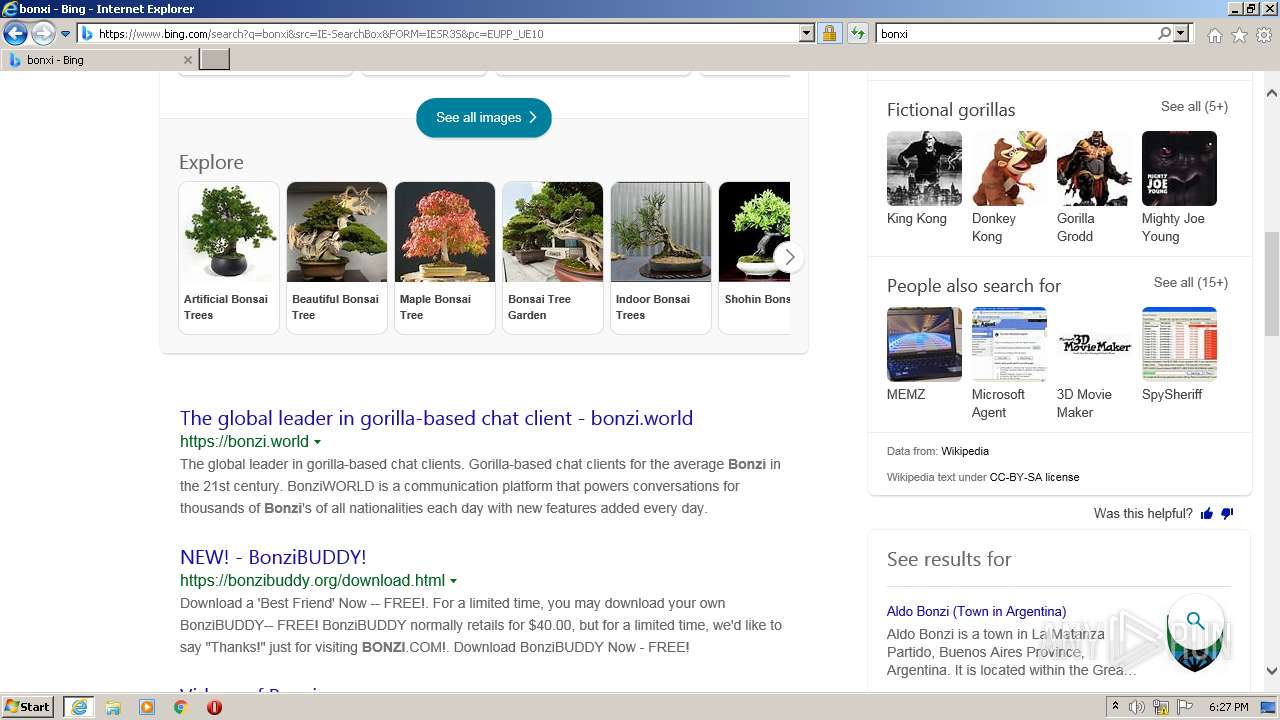
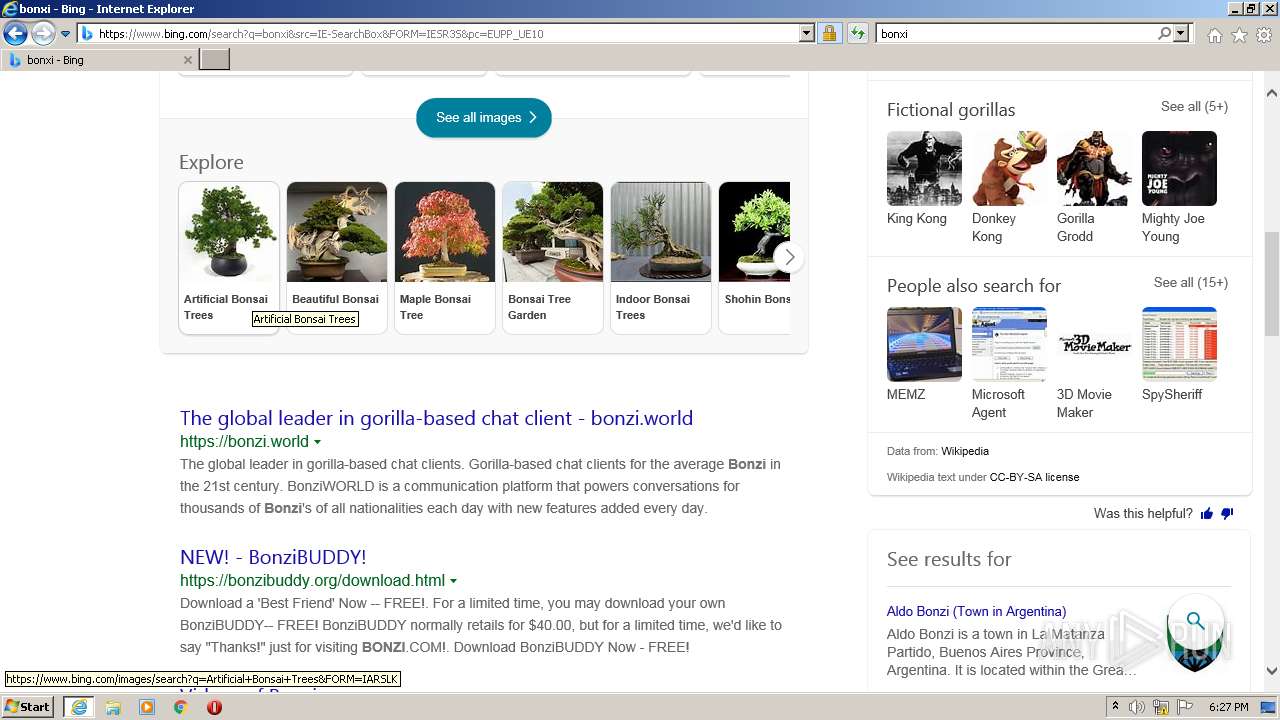
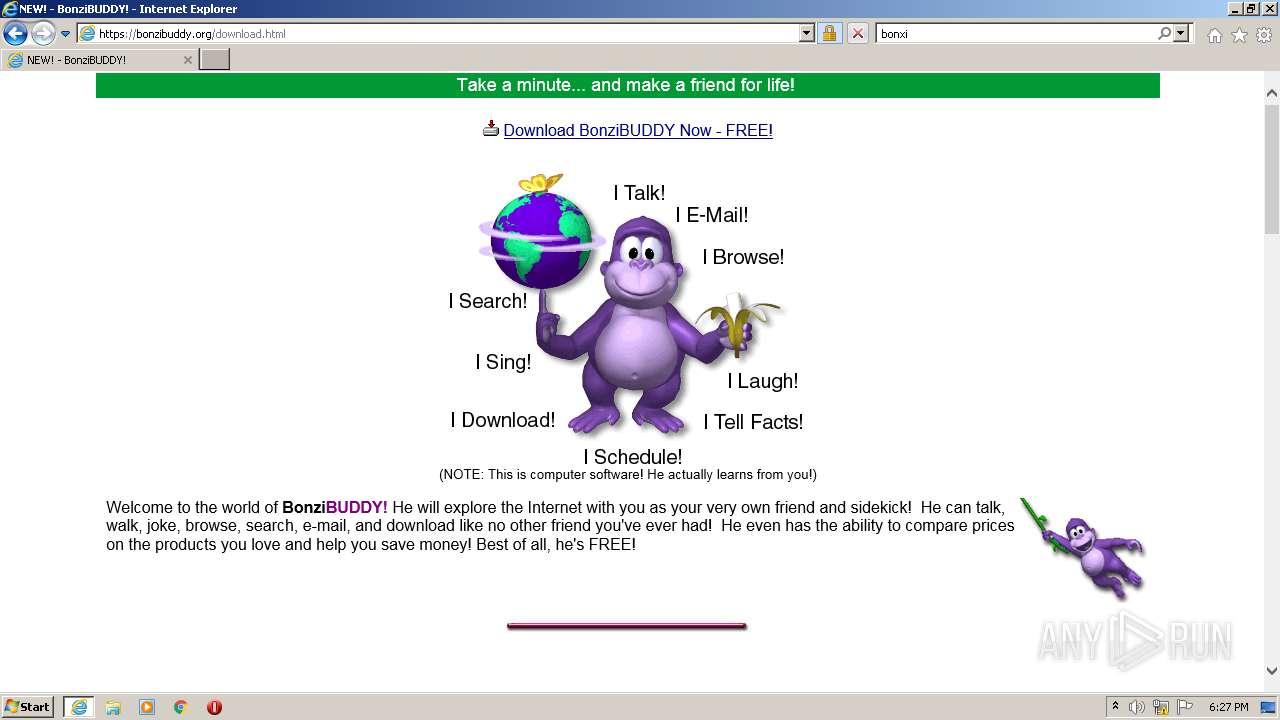
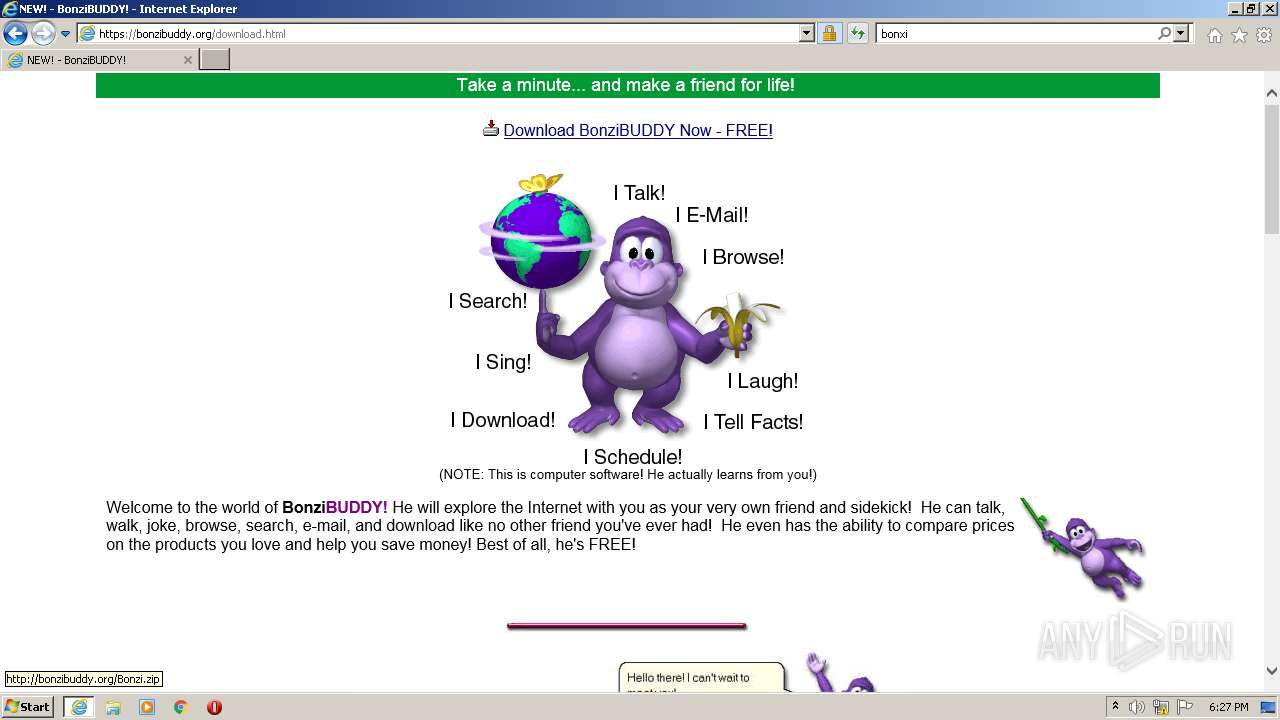
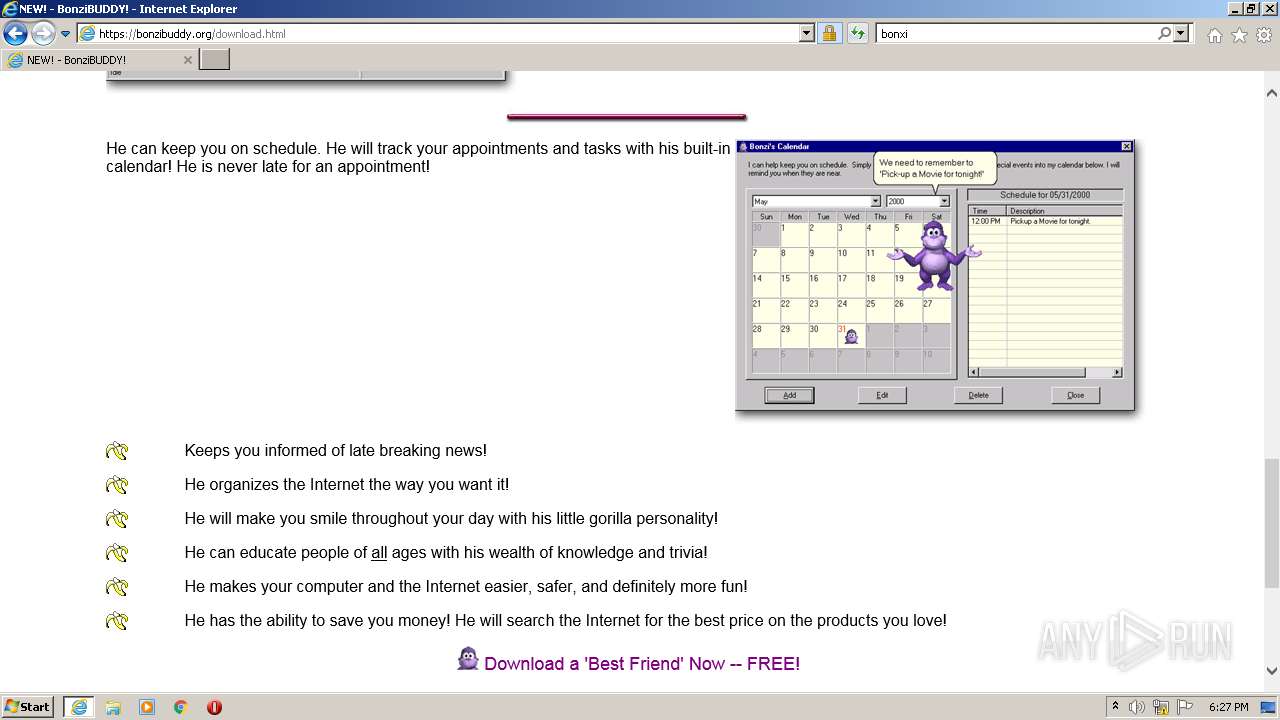
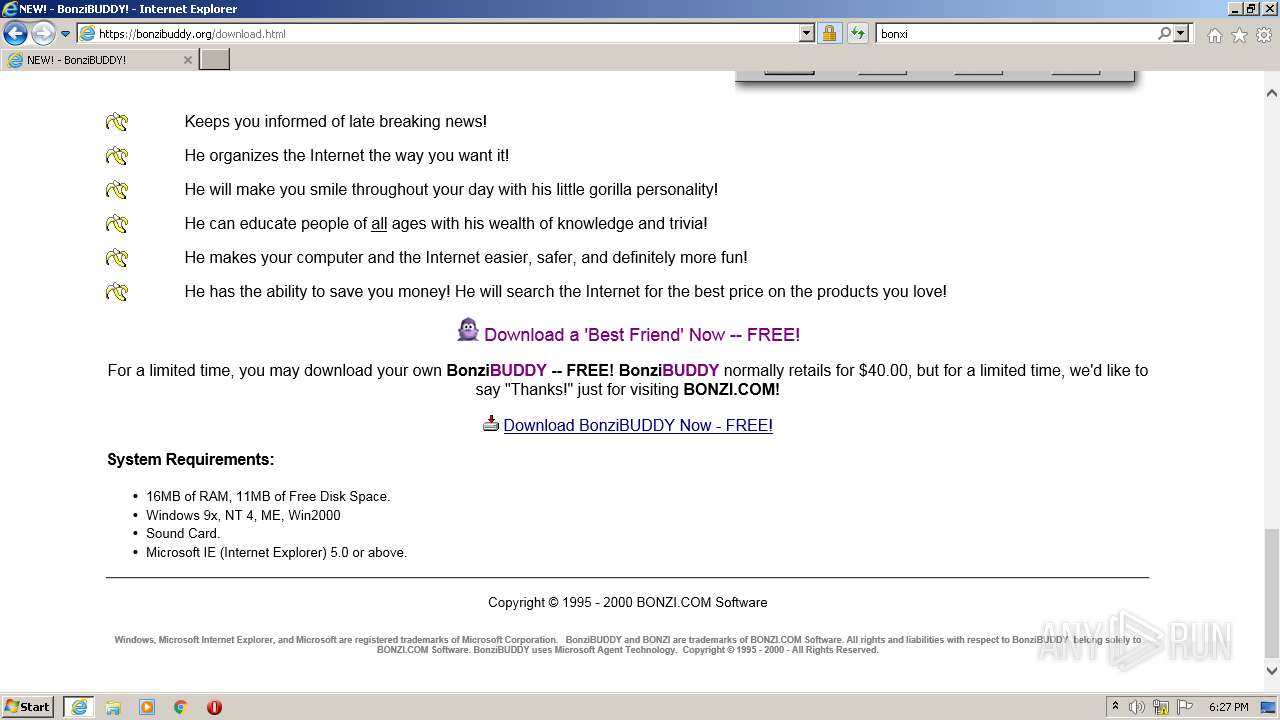
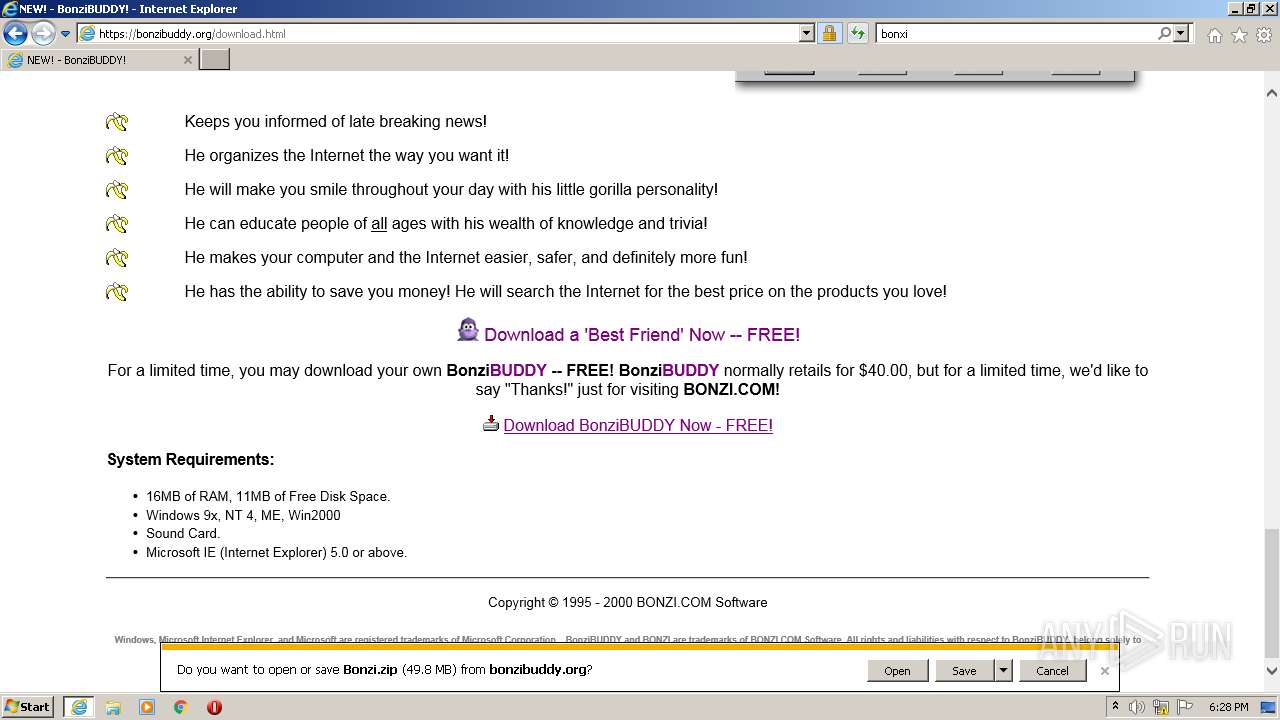
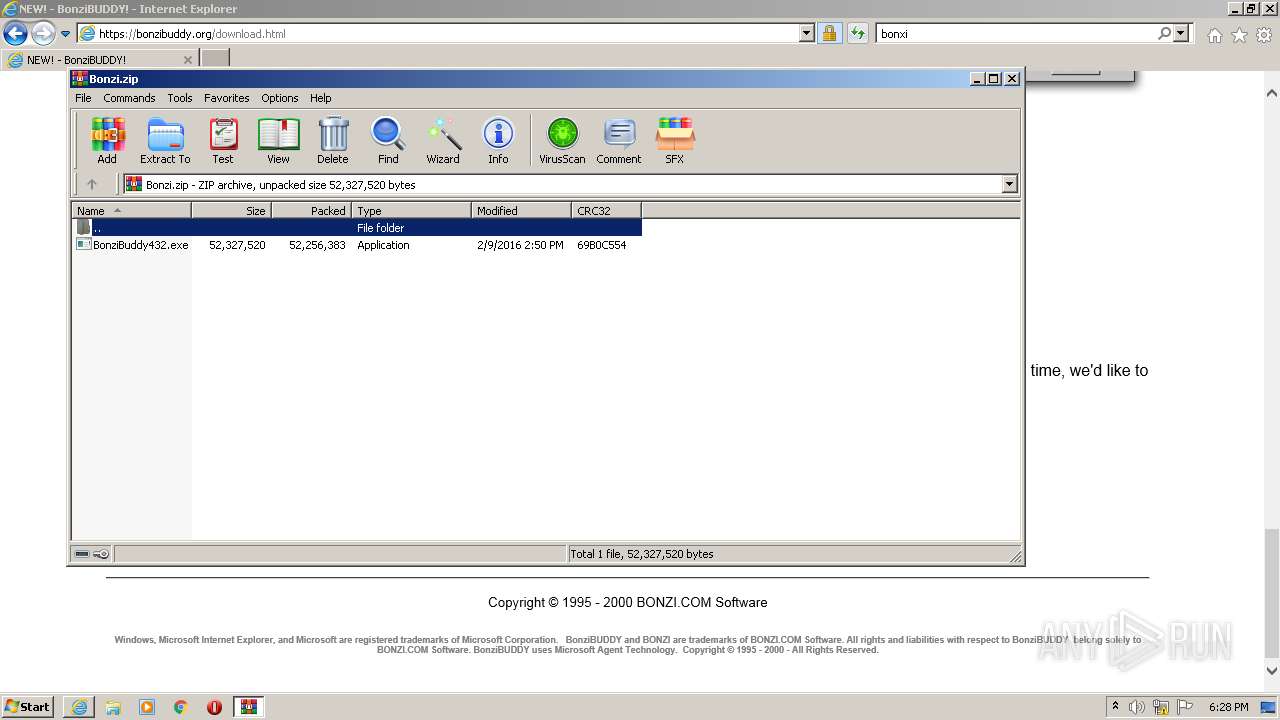
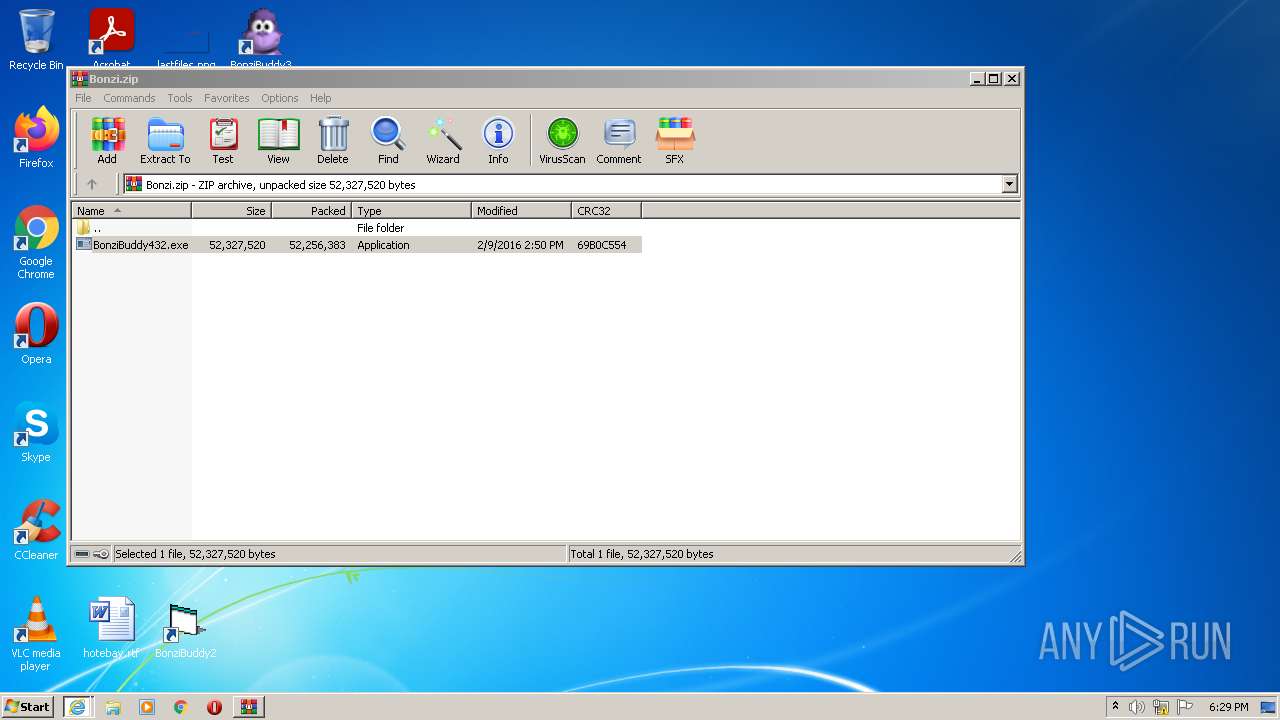
| URL: | https://bonzi.link/Bon.zip |
| Full analysis: | https://app.any.run/tasks/4dbe0d69-4e14-48f0-b424-89f1e6c5bca9 |
| Verdict: | Malicious activity |
| Analysis date: | January 05, 2022, 18:26:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | DF77A555F167492F438E1D4E60DF9C7F |
| SHA1: | 14F0AFE9AF532DF4745FE5A09723B3EE2B7F9A8D |
| SHA256: | 3134AB5CDFEC221D0170C93FE4FA1940237128C281DDEF5FD52262CF58A81767 |
| SSDEEP: | 3:N898KL4:298Kk |
MALICIOUS
Loads dropped or rewritten executable
- BonziBuddy432.exe (PID: 628)
- regsvr32.exe (PID: 4068)
- regsvr32.exe (PID: 3176)
- regsvr32.exe (PID: 1088)
- regsvr32.exe (PID: 3300)
- MSAGENT.EXE (PID: 4020)
- regsvr32.exe (PID: 1288)
- tv_enua.exe (PID: 3740)
- BonziBDY_35.EXE (PID: 2112)
- regsvr32.exe (PID: 824)
- regsvr32.exe (PID: 1256)
- AgentSvr.exe (PID: 688)
Application was dropped or rewritten from another process
- tv_enua.exe (PID: 3740)
- MSAGENT.EXE (PID: 4020)
- AgentSvr.exe (PID: 2824)
- BonziBDY_35.EXE (PID: 2112)
- AgentSvr.exe (PID: 688)
Registers / Runs the DLL via REGSVR32.EXE
- MSAGENT.EXE (PID: 4020)
- tv_enua.exe (PID: 3740)
Changes the autorun value in the registry
- tv_enua.exe (PID: 3740)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3648)
- iexplore.exe (PID: 3488)
- iexplore.exe (PID: 1240)
- iexplore.exe (PID: 1332)
- iexplore.exe (PID: 2824)
Reads the computer name
- WinRAR.exe (PID: 1536)
- BonziBuddy432.exe (PID: 628)
- MSAGENT.EXE (PID: 4020)
- tv_enua.exe (PID: 3740)
- BonziBDY_35.EXE (PID: 2112)
- AgentSvr.exe (PID: 688)
Checks supported languages
- WinRAR.exe (PID: 1536)
- BonziBuddy432.exe (PID: 628)
- cmd.exe (PID: 2548)
- MSAGENT.EXE (PID: 4020)
- tv_enua.exe (PID: 3740)
- AgentSvr.exe (PID: 2824)
- BonziBDY_35.EXE (PID: 2112)
- AgentSvr.exe (PID: 688)
Executable content was dropped or overwritten
- BonziBuddy432.exe (PID: 628)
- MSAGENT.EXE (PID: 4020)
- tv_enua.exe (PID: 3740)
Drops a file that was compiled in debug mode
- BonziBuddy432.exe (PID: 628)
- MSAGENT.EXE (PID: 4020)
- tv_enua.exe (PID: 3740)
Reads mouse settings
- BonziBuddy432.exe (PID: 628)
- BonziBDY_35.EXE (PID: 2112)
Starts CMD.EXE for commands execution
- BonziBuddy432.exe (PID: 628)
Drops a file with too old compile date
- BonziBuddy432.exe (PID: 628)
- MSAGENT.EXE (PID: 4020)
- tv_enua.exe (PID: 3740)
Creates files in the user directory
- BonziBuddy432.exe (PID: 628)
Creates files in the program directory
- BonziBuddy432.exe (PID: 628)
- BonziBDY_35.EXE (PID: 2112)
Creates files in the Windows directory
- MSAGENT.EXE (PID: 4020)
- BonziBuddy432.exe (PID: 628)
- tv_enua.exe (PID: 3740)
Removes files from Windows directory
- MSAGENT.EXE (PID: 4020)
- tv_enua.exe (PID: 3740)
Drops a file with a compile date too recent
- MSAGENT.EXE (PID: 4020)
- tv_enua.exe (PID: 3740)
Creates a directory in Program Files
- BonziBuddy432.exe (PID: 628)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 688)
- regsvr32.exe (PID: 4068)
- regsvr32.exe (PID: 3244)
- regsvr32.exe (PID: 3300)
- regsvr32.exe (PID: 3176)
- regsvr32.exe (PID: 1288)
- regsvr32.exe (PID: 1088)
- regsvr32.exe (PID: 824)
- regsvr32.exe (PID: 1256)
Creates a software uninstall entry
- tv_enua.exe (PID: 3740)
- BonziBuddy432.exe (PID: 628)
Executed via COM
- AgentSvr.exe (PID: 688)
- iexplore.exe (PID: 2844)
INFO
Checks supported languages
- iexplore.exe (PID: 3488)
- iexplore.exe (PID: 3648)
- iexplore.exe (PID: 1240)
- regsvr32.exe (PID: 4068)
- regsvr32.exe (PID: 3244)
- regsvr32.exe (PID: 688)
- regsvr32.exe (PID: 1288)
- regsvr32.exe (PID: 3300)
- regsvr32.exe (PID: 3176)
- regsvr32.exe (PID: 1088)
- grpconv.exe (PID: 1340)
- regsvr32.exe (PID: 1256)
- regsvr32.exe (PID: 824)
- grpconv.exe (PID: 964)
- iexplore.exe (PID: 1332)
- iexplore.exe (PID: 2844)
- iexplore.exe (PID: 2824)
Changes internet zones settings
- iexplore.exe (PID: 3488)
- iexplore.exe (PID: 2844)
Reads the computer name
- iexplore.exe (PID: 3488)
- iexplore.exe (PID: 3648)
- iexplore.exe (PID: 1240)
- iexplore.exe (PID: 2844)
- iexplore.exe (PID: 1332)
- iexplore.exe (PID: 2824)
Application launched itself
- iexplore.exe (PID: 3488)
- iexplore.exe (PID: 2844)
Reads settings of System Certificates
- iexplore.exe (PID: 3648)
- iexplore.exe (PID: 3488)
- iexplore.exe (PID: 1240)
Reads internet explorer settings
- iexplore.exe (PID: 3648)
- iexplore.exe (PID: 1240)
Checks Windows Trust Settings
- iexplore.exe (PID: 3648)
- iexplore.exe (PID: 3488)
- iexplore.exe (PID: 1240)
Creates files in the user directory
- iexplore.exe (PID: 3488)
- iexplore.exe (PID: 3648)
- iexplore.exe (PID: 1240)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3488)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3488)
Changes settings of System certificates
- iexplore.exe (PID: 3488)
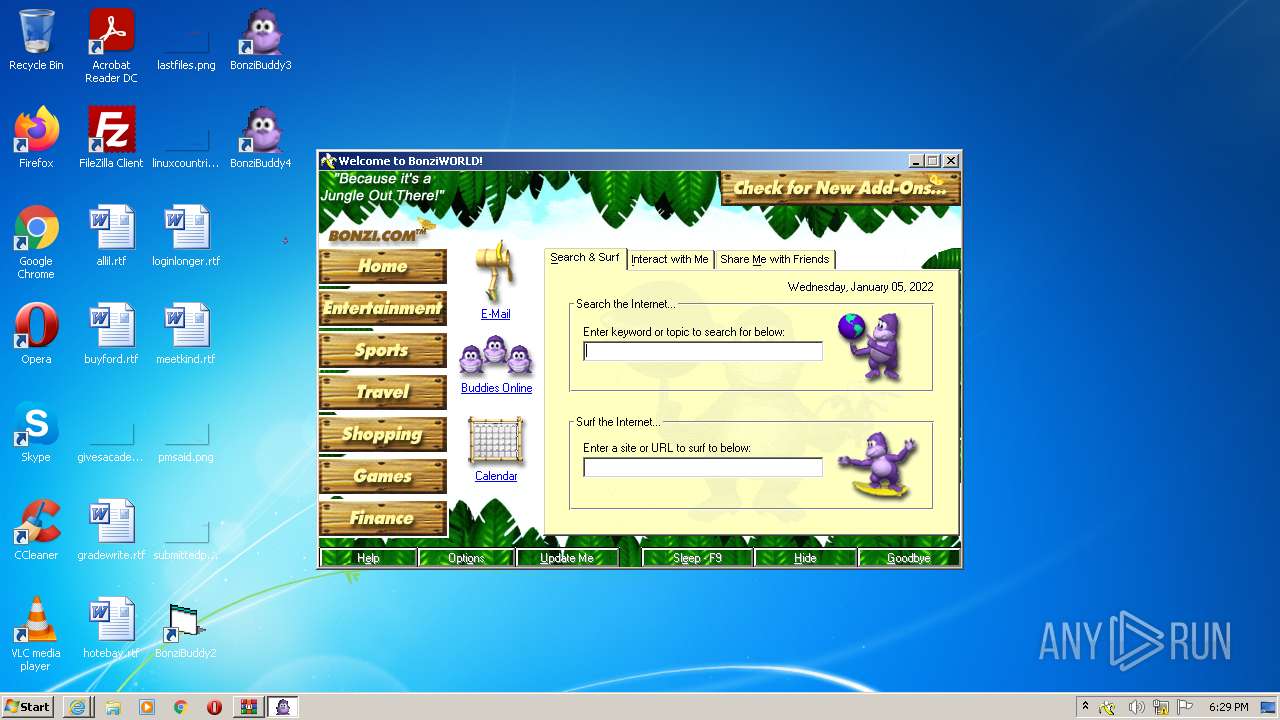
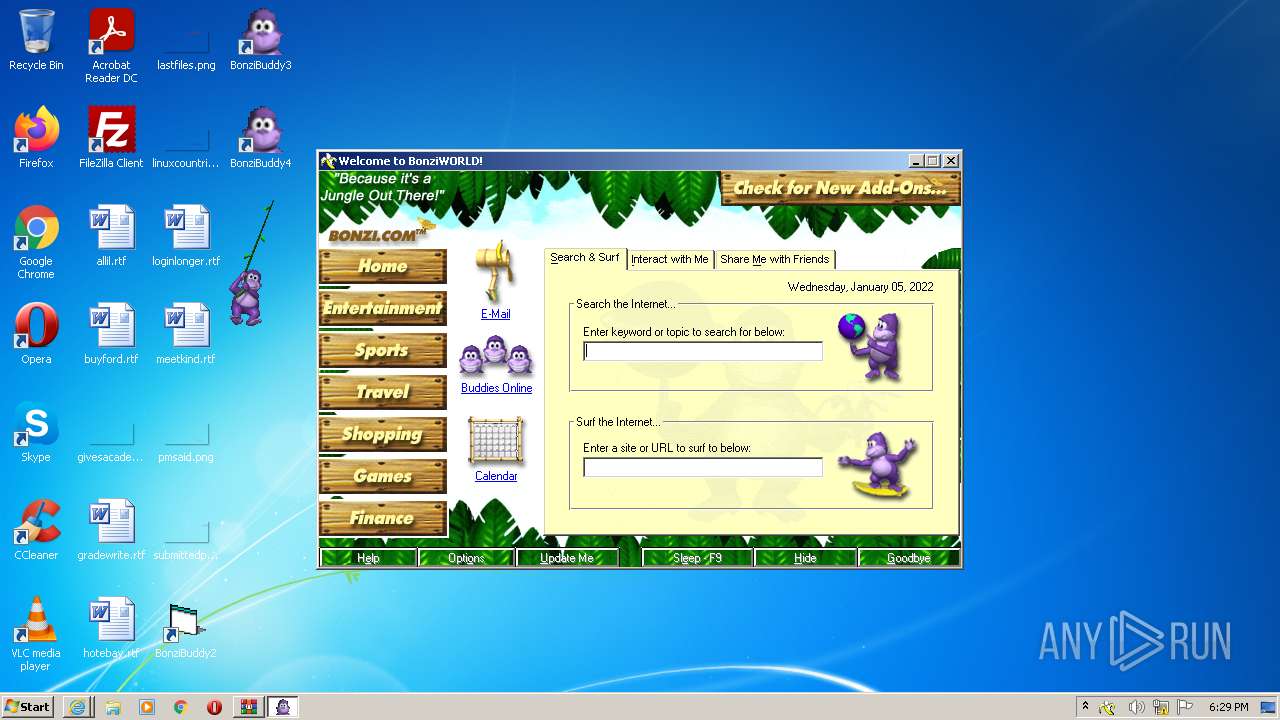
Manual execution by user
- BonziBDY_35.EXE (PID: 2112)
Reads Microsoft Office registry keys
- BonziBDY_35.EXE (PID: 2112)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
72
Monitored processes
26
Malicious processes
6
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
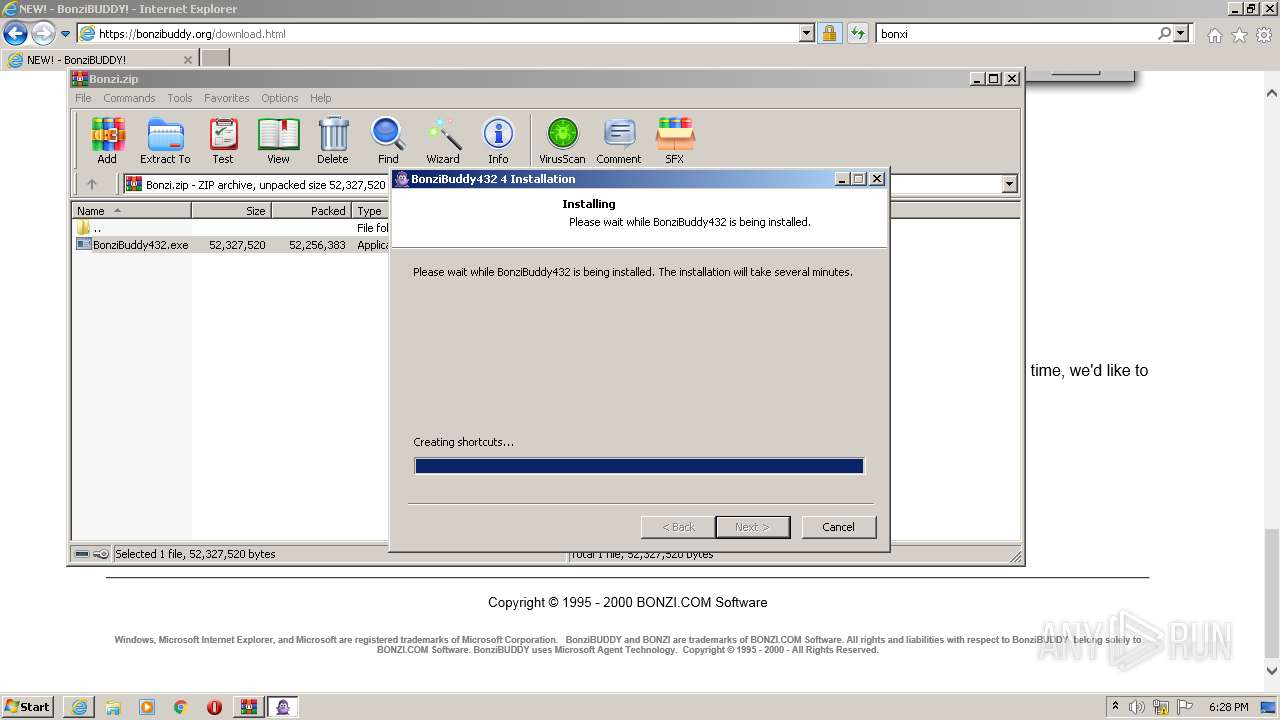
| 628 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1536.48486\BonziBuddy432.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1536.48486\BonziBuddy432.exe | WinRAR.exe | |
User: admin Company: Bonzi Software Integrity Level: HIGH Description: BonziBuddy432 4 Installation Exit code: 3221225547 Version: 4 | ||||
| 688 | regsvr32 /s "C:\Windows\msagent\AgentDPv.dll" | C:\Windows\system32\regsvr32.exe | — | MSAGENT.EXE |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 688 | C:\Windows\msagent\AgentSvr.exe -Embedding | C:\Windows\msagent\AgentSvr.exe | svchost.exe | |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Agent Server Exit code: 0 Version: 2.00.0.2202 | ||||
| 824 | regsvr32 /s C:\Windows\lhsp\tv\tvenuax.dll | C:\Windows\system32\regsvr32.exe | — | tv_enua.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 964 | grpconv.exe -o | C:\Windows\system32\grpconv.exe | — | tv_enua.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Progman Group Converter Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 1088 | regsvr32 /s "C:\Windows\msagent\AgentPsh.dll" | C:\Windows\system32\regsvr32.exe | — | MSAGENT.EXE |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 1240 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3488 CREDAT:2102559 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | |
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) | ||||
| 1256 | regsvr32 /s C:\Windows\lhsp\tv\tv_enua.dll | C:\Windows\system32\regsvr32.exe | — | tv_enua.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 1288 | regsvr32 /s "C:\Windows\msagent\AgentSR.dll" | C:\Windows\system32\regsvr32.exe | — | MSAGENT.EXE |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 1332 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2844 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
83
Suspicious files
59
Text files
331
Unknown types
39
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3648 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\E1FY6BST.txt | text | |
MD5:— | SHA256:— | |||
| 3648 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\92GUONXX.txt | text | |
MD5:— | SHA256:— | |||
| 3648 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\2WWK1G2F.txt | text | |
MD5:— | SHA256:— | |||
| 3648 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\HW9CJGEW.txt | text | |
MD5:— | SHA256:— | |||
| 3648 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\qsml[1].htm | xml | |
MD5:— | SHA256:— | |||
| 3648 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3648 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\ZEEF7I3U.txt | text | |
MD5:— | SHA256:— | |||
| 3648 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\9YBO7SV0.txt | text | |
MD5:— | SHA256:— | |||
| 3488 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3648 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
68
DNS requests
33
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3648 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
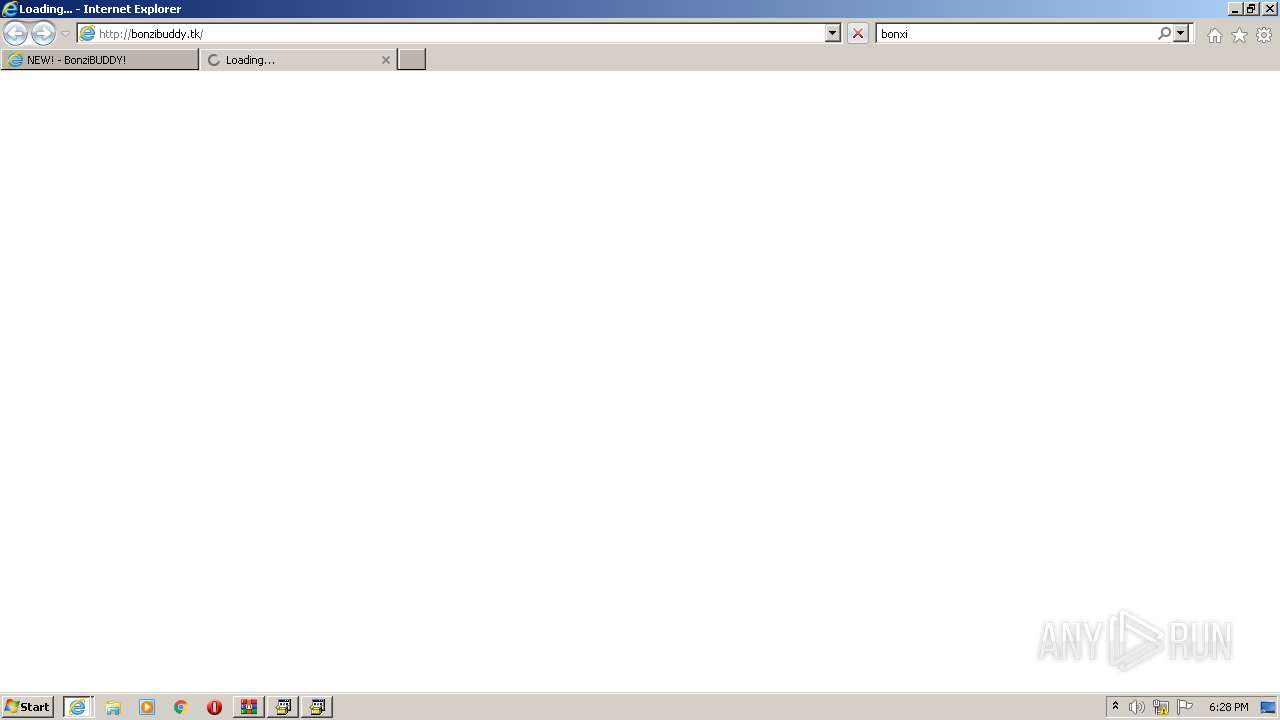
1240 | iexplore.exe | GET | 200 | 185.199.220.34:80 | http://bonzibuddy.tk/ | GB | compressed | 762 b | malicious |
1240 | iexplore.exe | GET | — | 185.199.220.34:80 | http://bonzibuddy.tk/survive.mp3 | GB | — | — | malicious |
3648 | iexplore.exe | GET | 200 | 104.18.31.182:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
3648 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3648 | iexplore.exe | GET | 200 | 104.18.31.182:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQCVMZfnVSS75TyCF2MLr2ij | US | der | 472 b | whitelisted |
1240 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCECHMNwkPtKJCCgAAAAEl%2FQo%3D | US | der | 471 b | whitelisted |
3488 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | US | der | 471 b | whitelisted |
3648 | iexplore.exe | GET | 200 | 104.18.30.182:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
1240 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCECiWvl1%2BUB7cCgAAAAEl%2F%2BI%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3648 | iexplore.exe | 149.56.78.29:443 | bonzi.link | OVH SAS | CA | suspicious |
— | — | 131.253.33.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3648 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3488 | iexplore.exe | 13.107.22.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3648 | iexplore.exe | 13.107.5.80:443 | api.bing.com | Microsoft Corporation | US | whitelisted |
— | — | 40.126.31.1:443 | login.live.com | Microsoft Corporation | US | whitelisted |
3648 | iexplore.exe | 131.253.33.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3648 | iexplore.exe | 13.107.21.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3648 | iexplore.exe | 40.126.31.135:443 | login.live.com | Microsoft Corporation | US | suspicious |
3648 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
bonzi.link |
| suspicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.microsoftonline.com |
| whitelisted |
login.live.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
www2.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |
1240 | iexplore.exe | Potentially Bad Traffic | ET POLICY HTTP Request to a *.tk domain |
1240 | iexplore.exe | Potentially Bad Traffic | ET POLICY HTTP Request to a *.tk domain |
1240 | iexplore.exe | Potentially Bad Traffic | ET POLICY HTTP Request to a *.tk domain |
1240 | iexplore.exe | Potentially Bad Traffic | ET POLICY HTTP Request to a *.tk domain |
1240 | iexplore.exe | Potentially Bad Traffic | ET POLICY HTTP Request to a *.tk domain |
3488 | iexplore.exe | Potentially Bad Traffic | ET POLICY HTTP Request to a *.tk domain |
Process | Message |
|---|---|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|