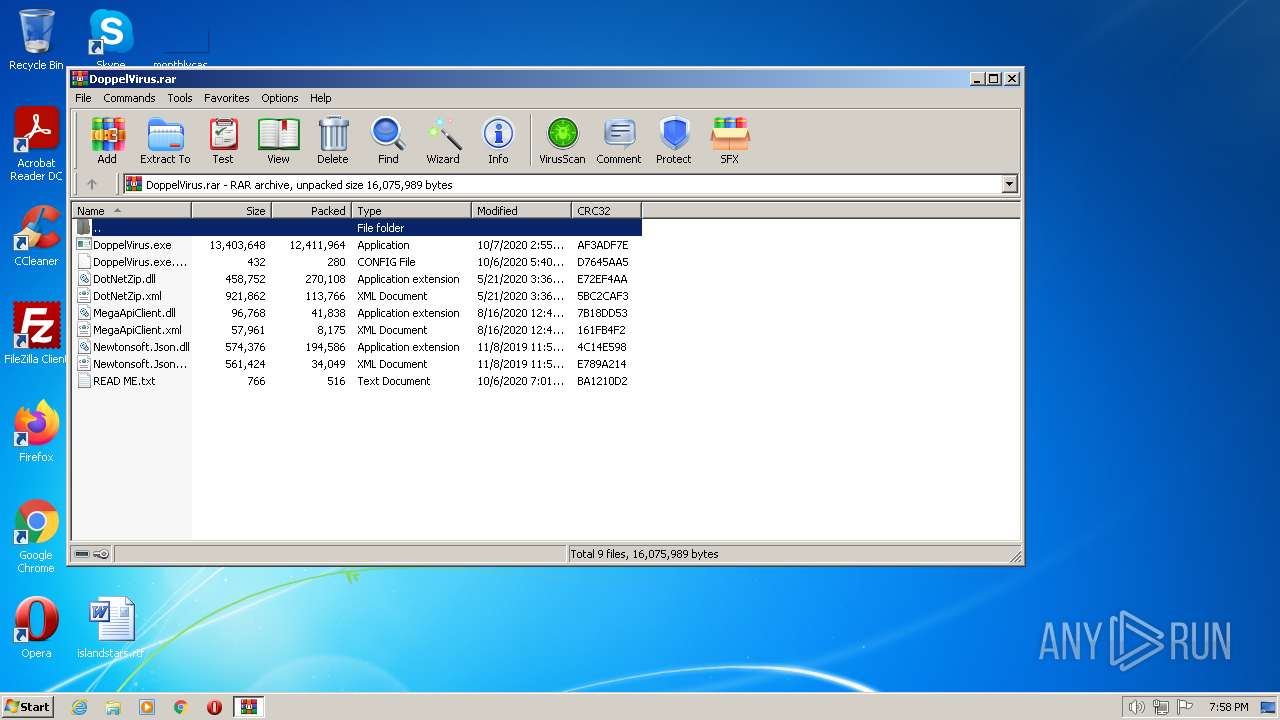
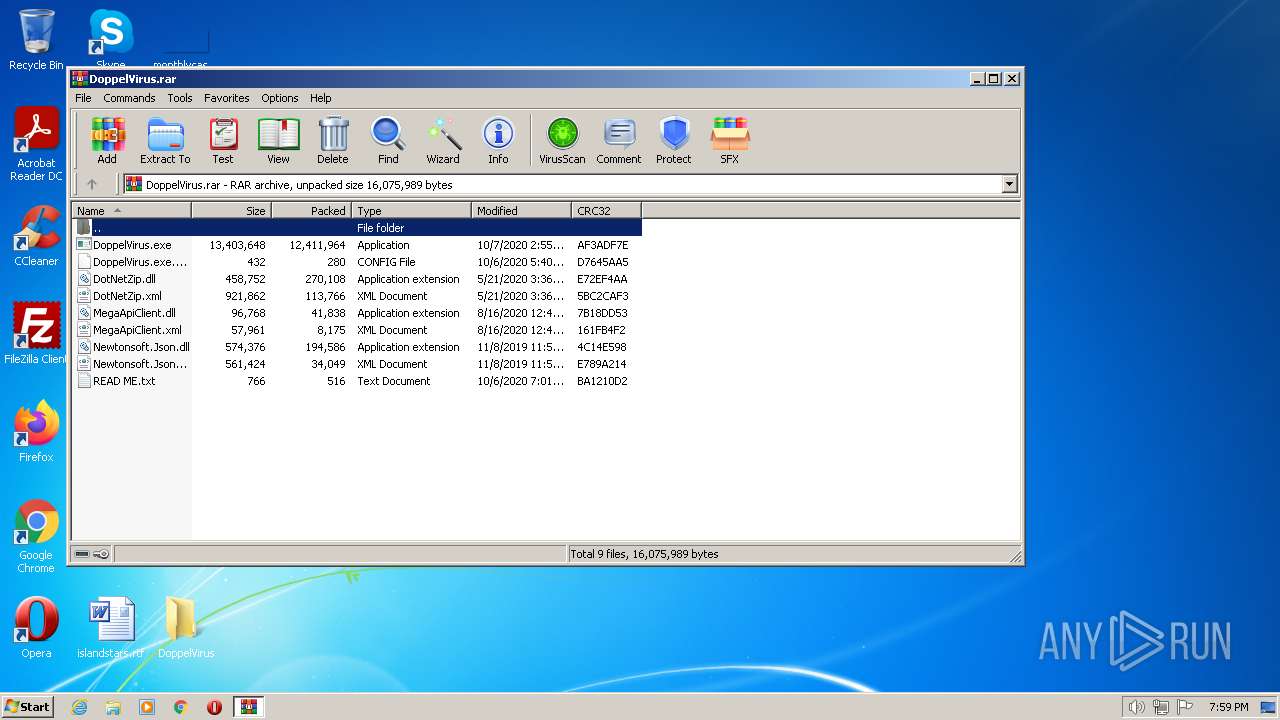
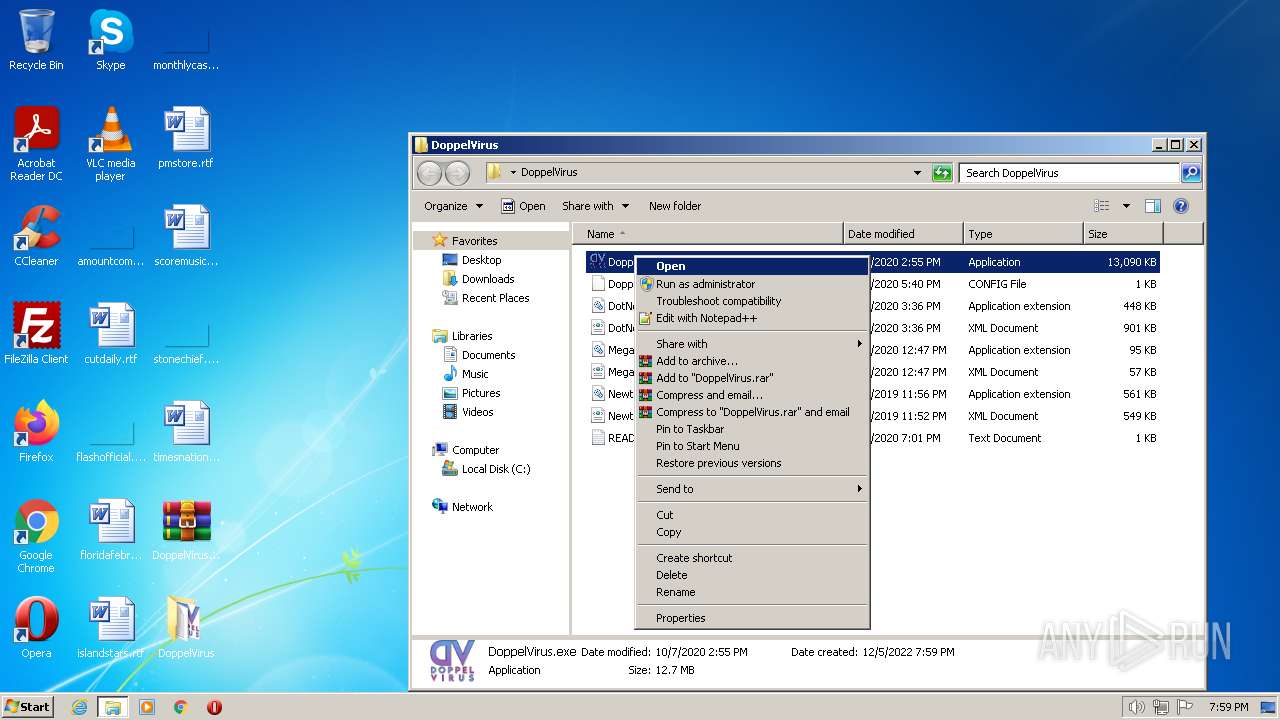
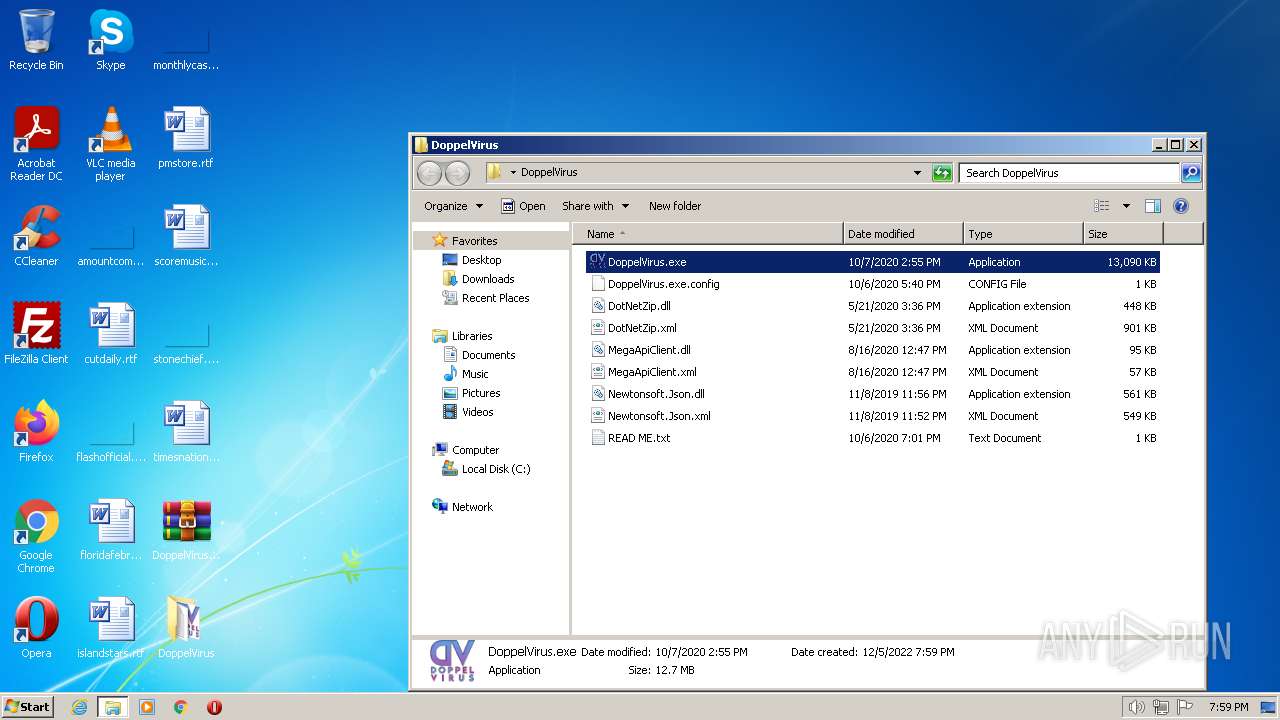
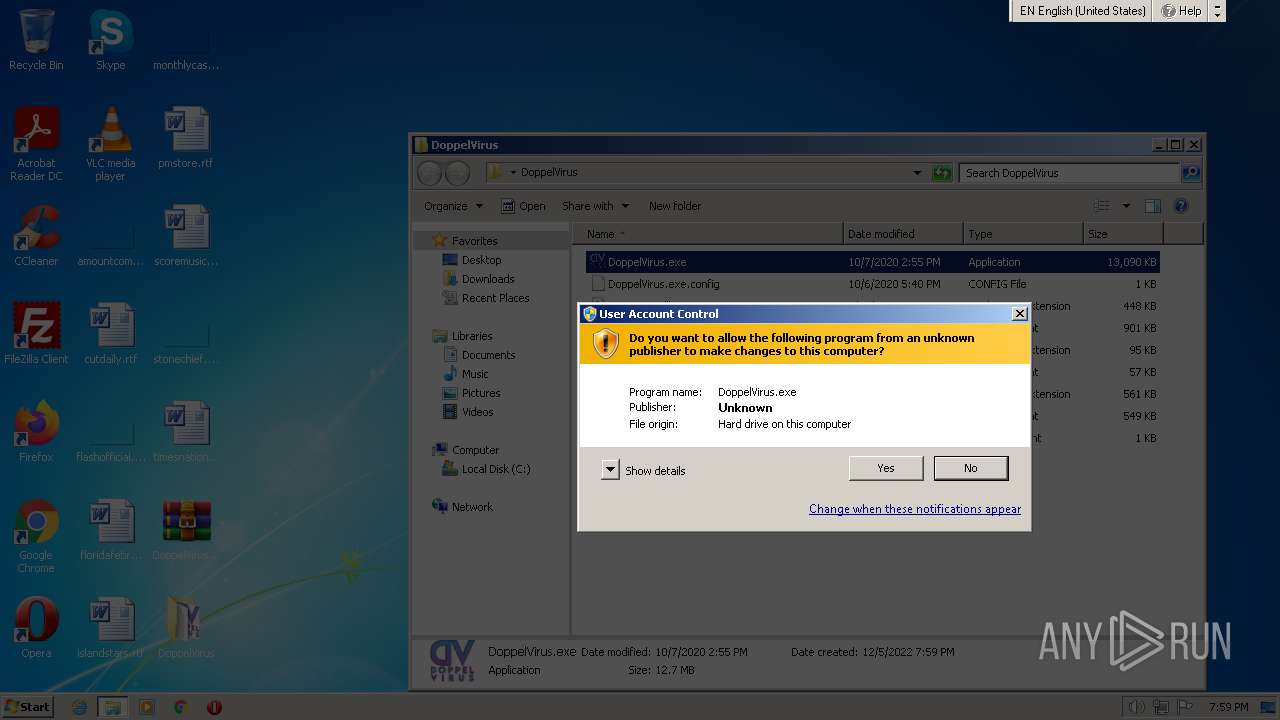
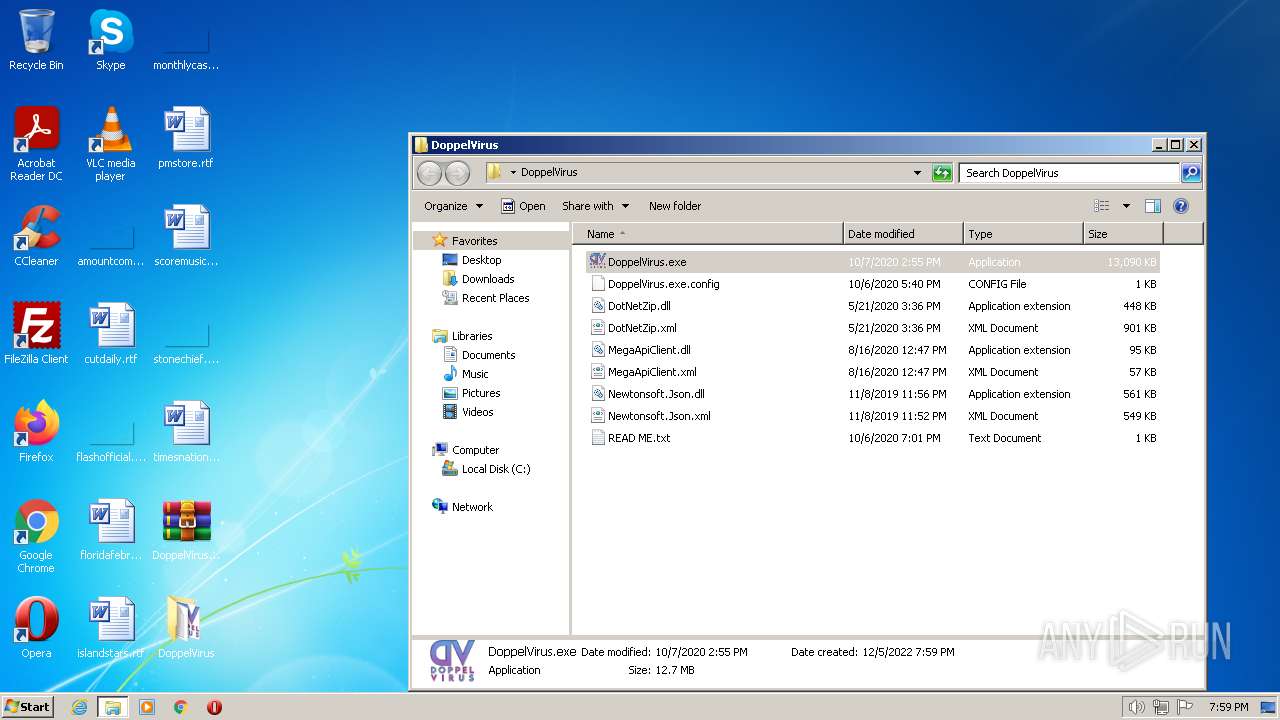
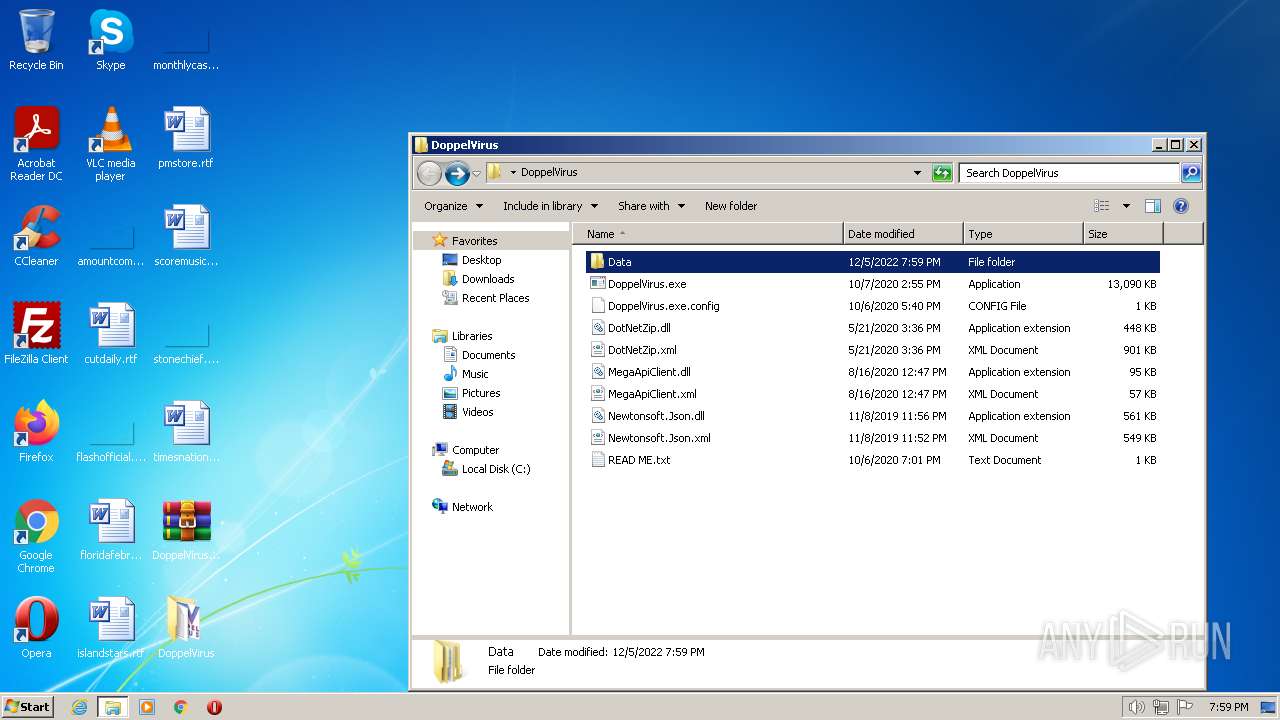
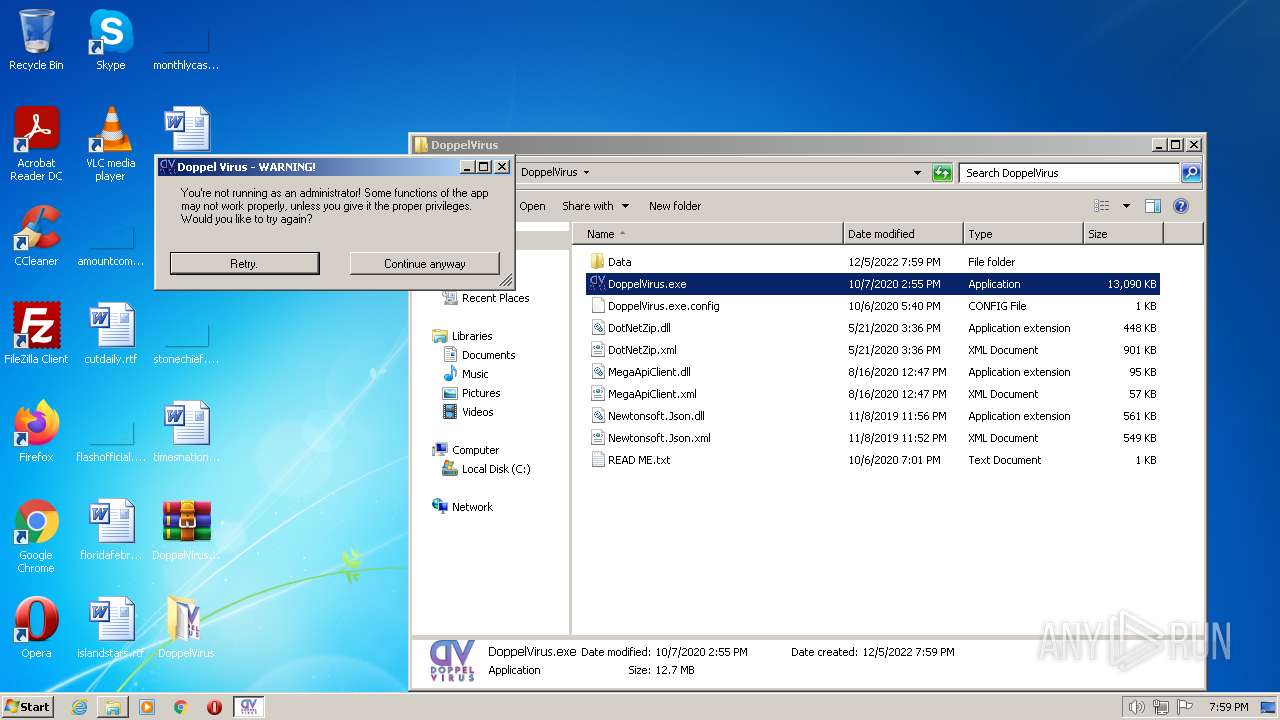
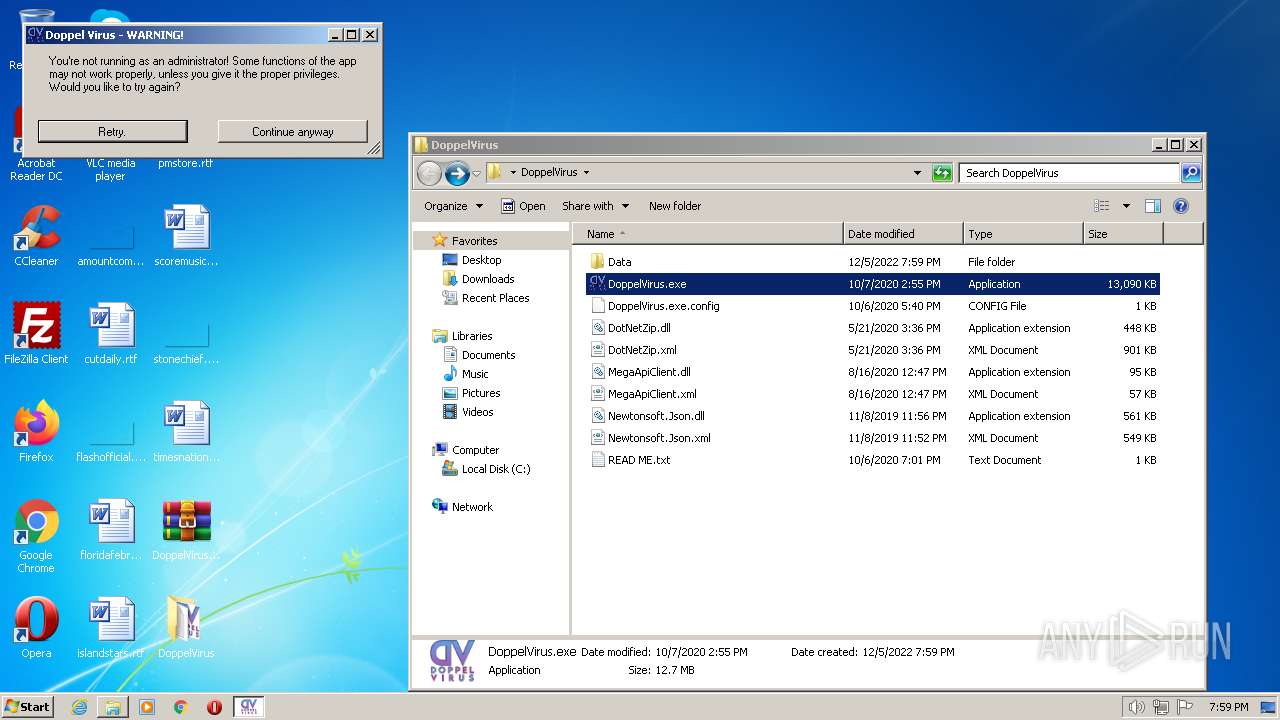
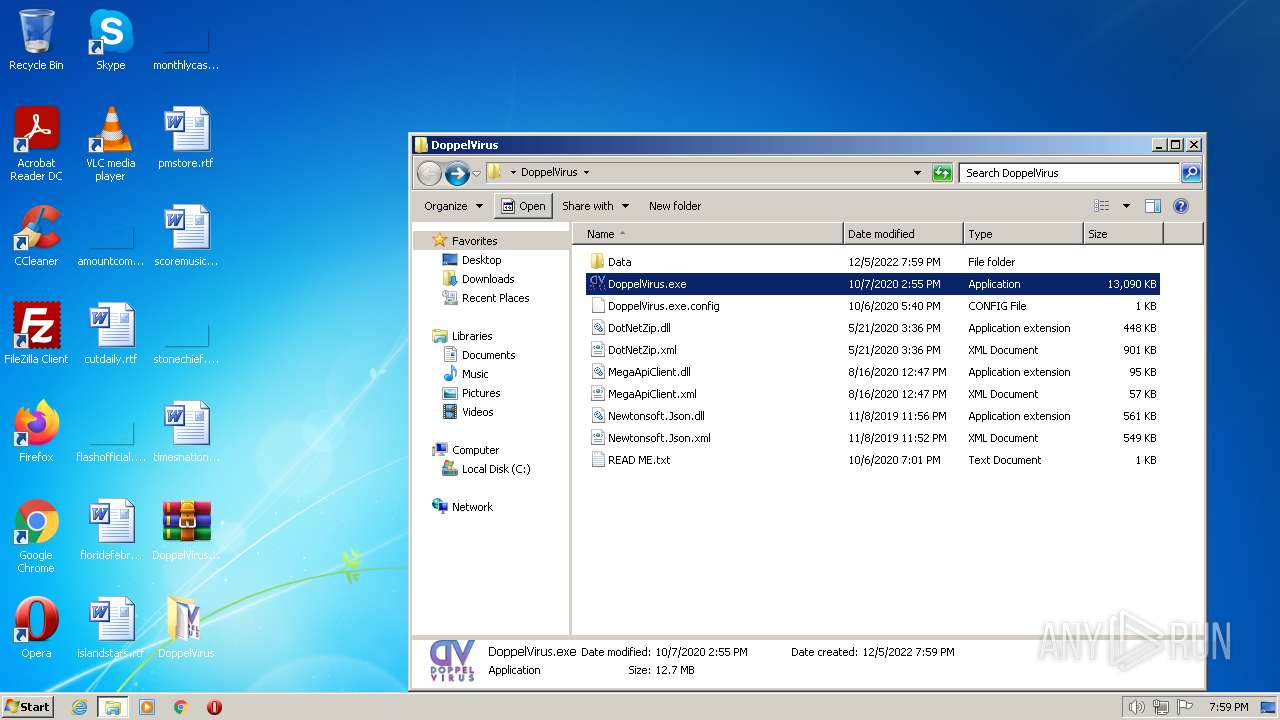
| File name: | DoppelVirus.rar |
| Full analysis: | https://app.any.run/tasks/6f5fd91f-5d87-4af5-8c5f-d65651b2da34 |
| Verdict: | Malicious activity |
| Analysis date: | December 05, 2022, 19:58:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | F8046215A13324EDCD05E8638576749E |
| SHA1: | A1B1D740116899756922AD50AFC384CCCF8AD176 |
| SHA256: | 3124B4A081A85FA01FFDB0037E0BF3D1969228B12DDC9CCC939F59A2D9FE947C |
| SSDEEP: | 393216:wvPlvD+Hz+fZGA5sHsFqg95dKGvQS9GtjAkrYnale:wlqTxsFq89vQYSjAkrYale |
MALICIOUS
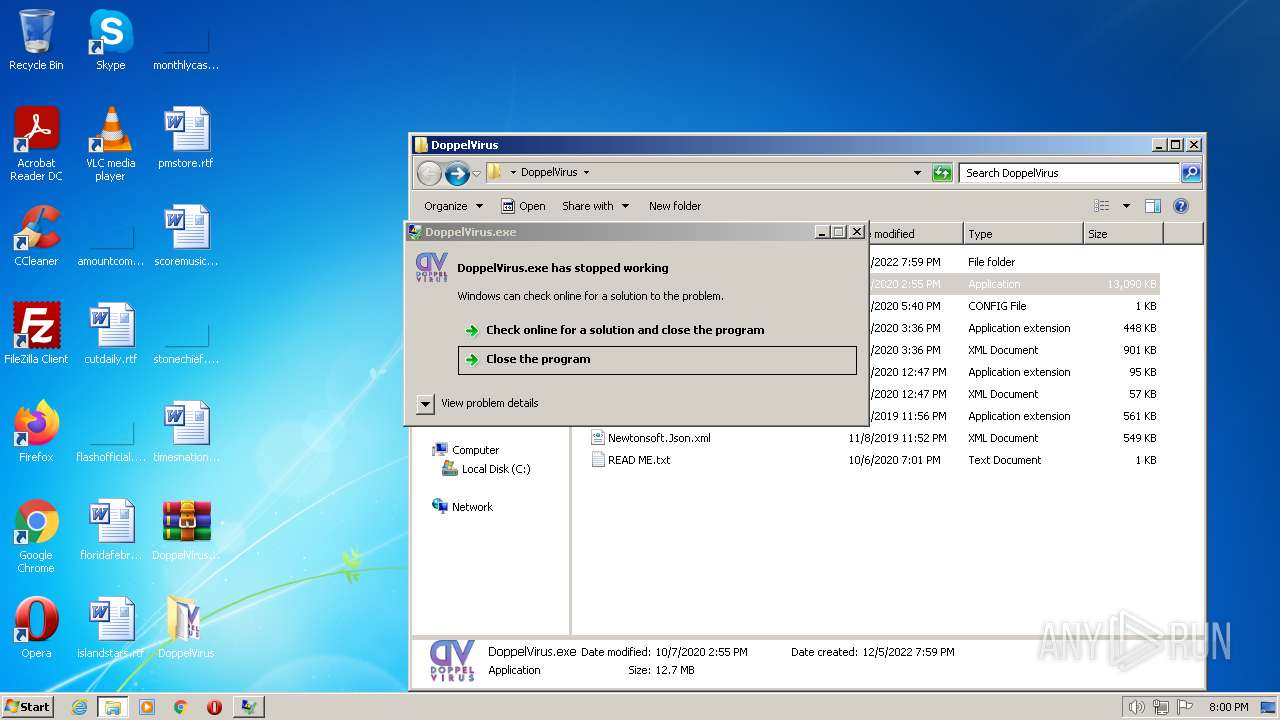
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2648)
- DoppelVirus.exe (PID: 3172)
- DoppelVirus.exe (PID: 2280)
- DoppelVirus.exe (PID: 3272)
- DoppelVirus.exe (PID: 1832)
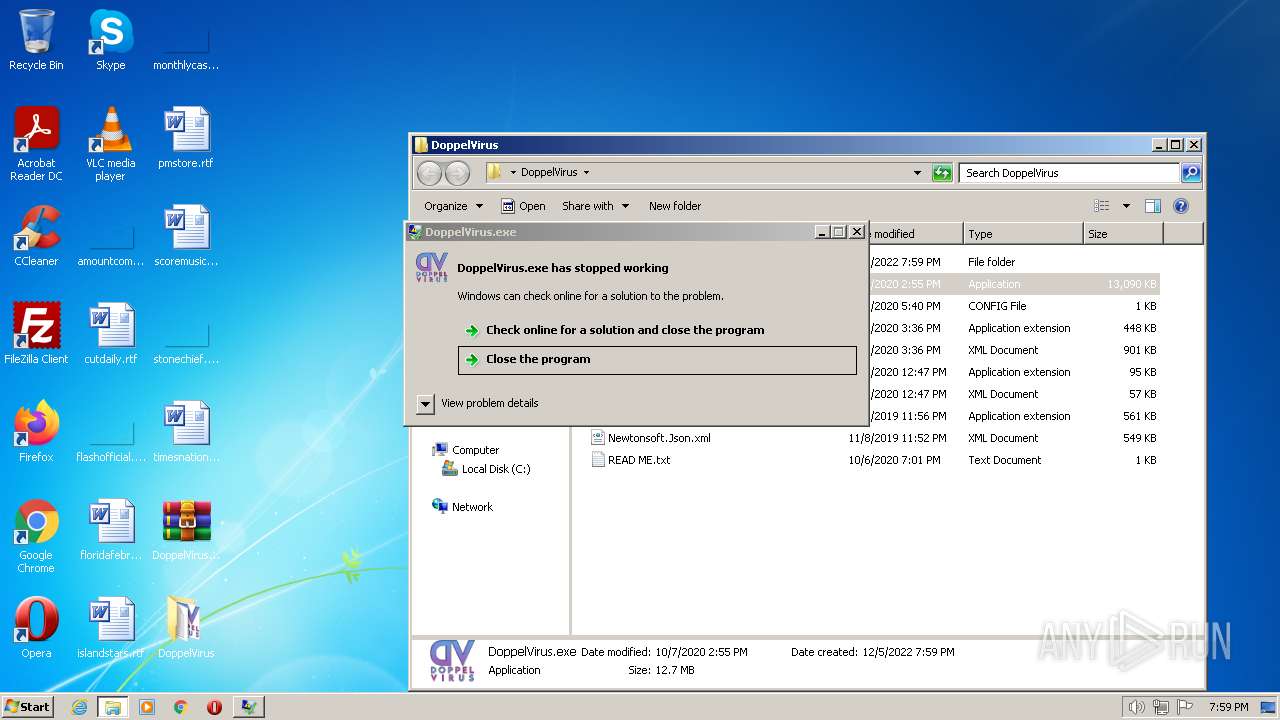
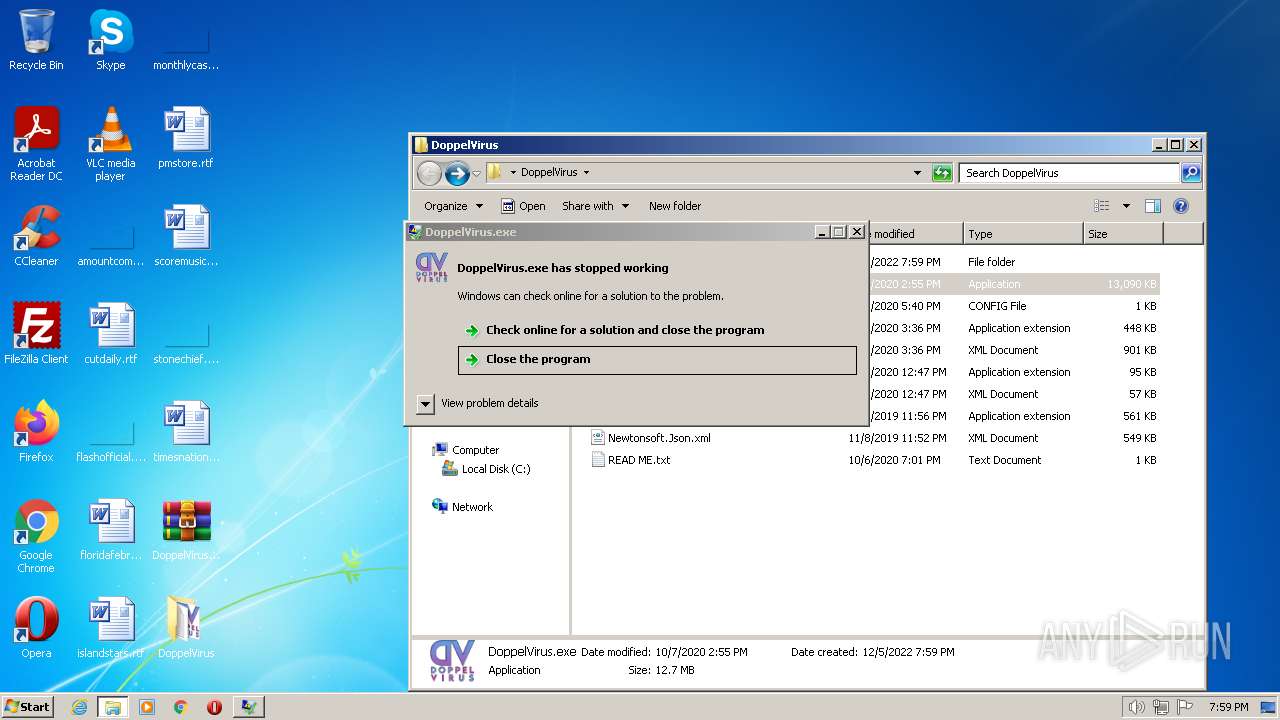
- WerFault.exe (PID: 2924)
- DoppelVirus.exe (PID: 3184)
- DoppelVirus.exe (PID: 1588)
Application was dropped or rewritten from another process
- DoppelVirus.exe (PID: 3172)
- DoppelVirus.exe (PID: 2280)
- DoppelVirus.exe (PID: 3272)
- DoppelVirus.exe (PID: 1832)
- DoppelVirus.exe (PID: 3184)
- DoppelVirus.exe (PID: 1588)
SUSPICIOUS
Reads the Internet Settings
- DoppelVirus.exe (PID: 3172)
- DoppelVirus.exe (PID: 2280)
- DoppelVirus.exe (PID: 1832)
- DoppelVirus.exe (PID: 1588)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1636)
Reads the computer name
- DoppelVirus.exe (PID: 3172)
- DoppelVirus.exe (PID: 2280)
- DoppelVirus.exe (PID: 3272)
- DoppelVirus.exe (PID: 1832)
- DoppelVirus.exe (PID: 3184)
- DoppelVirus.exe (PID: 1588)
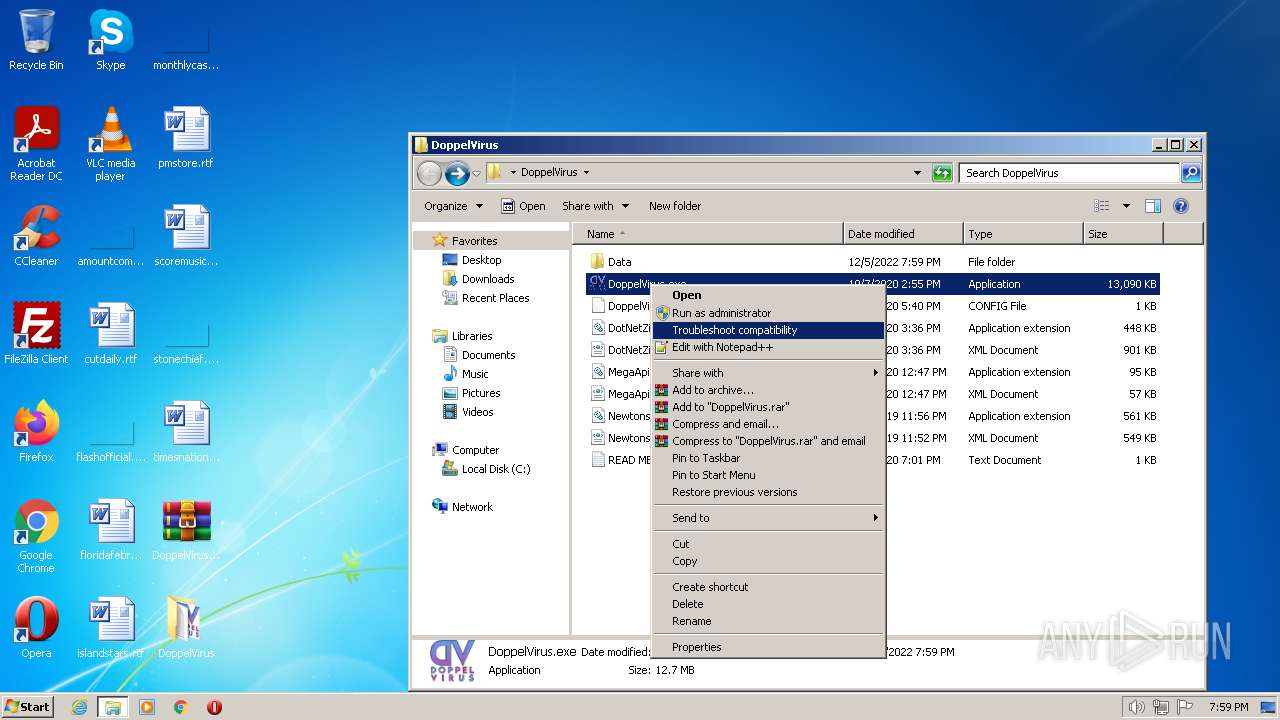
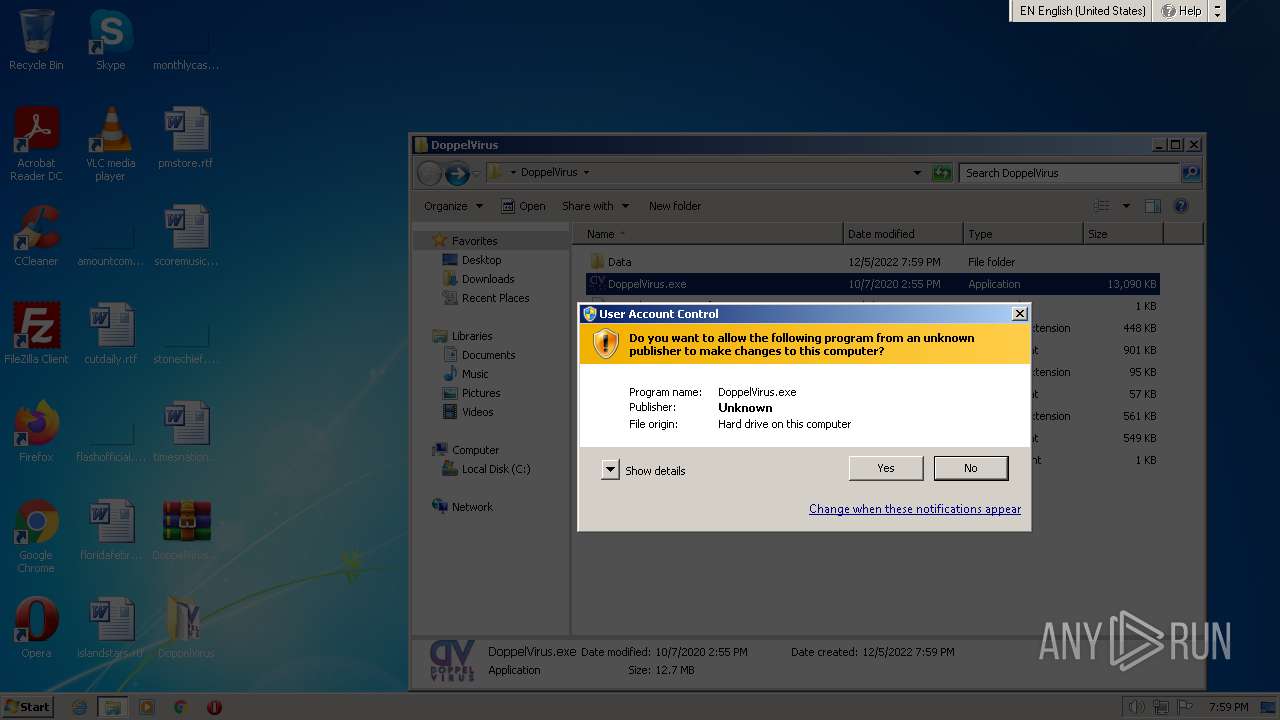
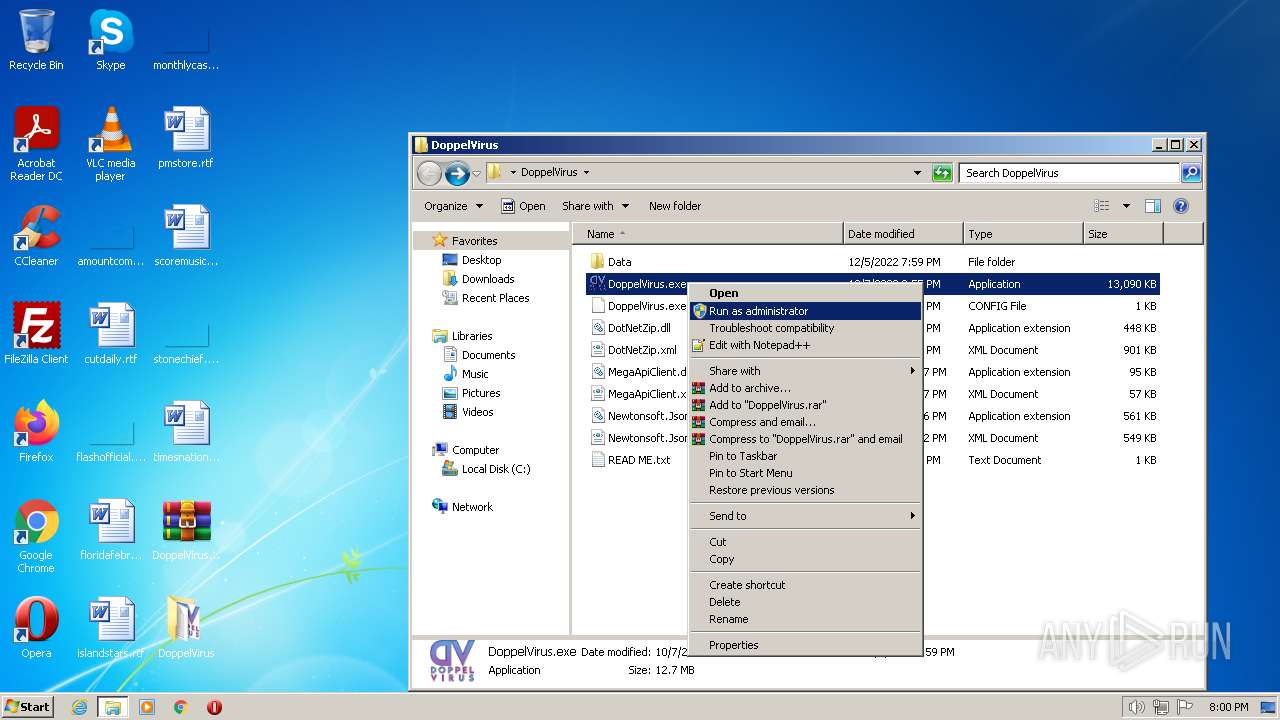
Manual execution by a user
- DoppelVirus.exe (PID: 3172)
- DoppelVirus.exe (PID: 2280)
- DoppelVirus.exe (PID: 3272)
- DoppelVirus.exe (PID: 1832)
- NOTEPAD.EXE (PID: 3952)
- DoppelVirus.exe (PID: 3184)
- DoppelVirus.exe (PID: 1588)
Checks supported languages
- DoppelVirus.exe (PID: 3172)
- DoppelVirus.exe (PID: 2280)
- DoppelVirus.exe (PID: 3272)
- DoppelVirus.exe (PID: 1832)
- DoppelVirus.exe (PID: 3184)
- DoppelVirus.exe (PID: 1588)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 1636)
Reads Environment values
- DoppelVirus.exe (PID: 3172)
- DoppelVirus.exe (PID: 2280)
- DoppelVirus.exe (PID: 1832)
- DoppelVirus.exe (PID: 1588)
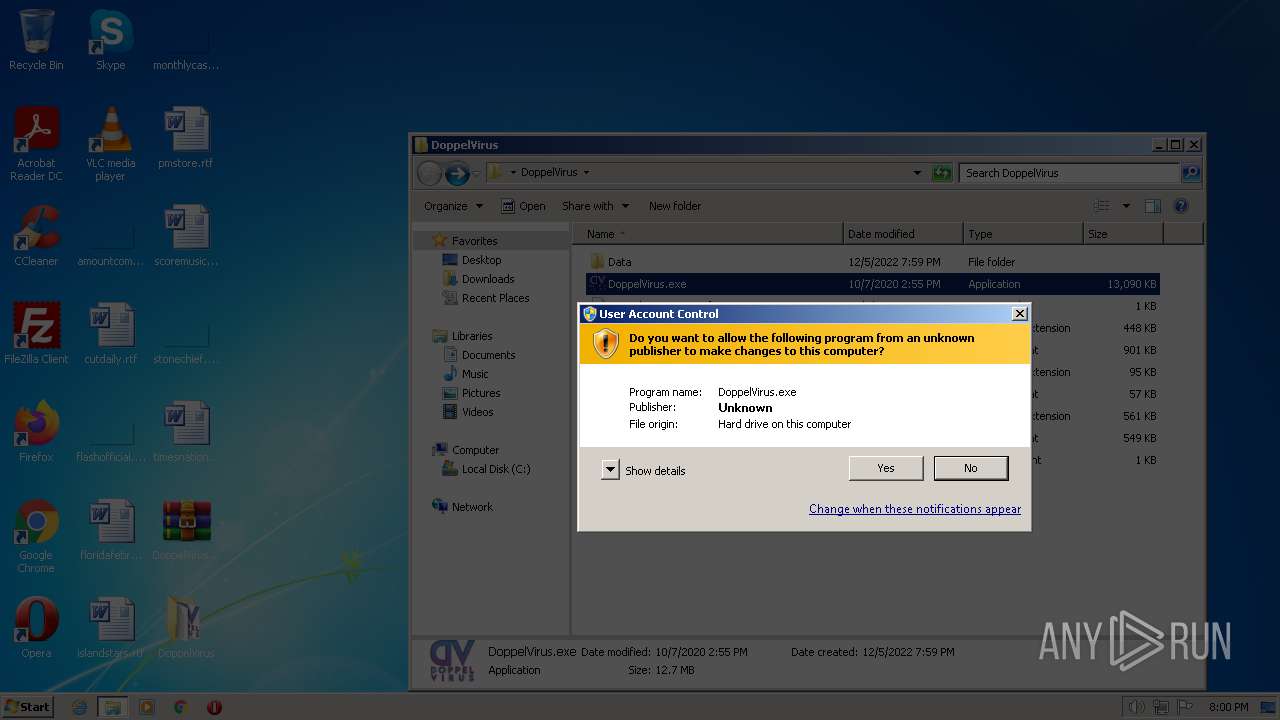
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1636)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
57
Monitored processes
10
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1588 | "C:\Users\admin\Desktop\DoppelVirus\DoppelVirus.exe" | C:\Users\admin\Desktop\DoppelVirus\DoppelVirus.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.7417.41804 Modules
| |||||||||||||||
| 1636 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\DoppelVirus.rar" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1832 | "C:\Users\admin\Desktop\DoppelVirus\DoppelVirus.exe" | C:\Users\admin\Desktop\DoppelVirus\DoppelVirus.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.7417.41804 Modules
| |||||||||||||||
| 2280 | "C:\Users\admin\Desktop\DoppelVirus\DoppelVirus.exe" | C:\Users\admin\Desktop\DoppelVirus\DoppelVirus.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.7417.41804 Modules
| |||||||||||||||
| 2648 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 2924 | C:\Windows\system32\WerFault.exe -u -p 1832 -s 1140 | C:\Windows\system32\WerFault.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3172 | "C:\Users\admin\Desktop\DoppelVirus\DoppelVirus.exe" | C:\Users\admin\Desktop\DoppelVirus\DoppelVirus.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3762504530 Version: 1.0.7417.41804 Modules
| |||||||||||||||
| 3184 | "C:\Users\admin\Desktop\DoppelVirus\DoppelVirus.exe" | C:\Users\admin\Desktop\DoppelVirus\DoppelVirus.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.7417.41804 Modules
| |||||||||||||||
| 3272 | "C:\Users\admin\Desktop\DoppelVirus\DoppelVirus.exe" | C:\Users\admin\Desktop\DoppelVirus\DoppelVirus.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.7417.41804 Modules
| |||||||||||||||
| 3952 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\DoppelVirus\READ ME.txt | C:\Windows\system32\NOTEPAD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 706
Read events
3 656
Write events
50
Delete events
0
Modification events
| (PID) Process: | (1636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1636) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\DoppelVirus.rar | |||
| (PID) Process: | (1636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1636) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
4
Suspicious files
0
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2924 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WERBCEA.tmp.hdmp | — | |
MD5:— | SHA256:— | |||
| 2924 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WERD390.tmp.mdmp | — | |
MD5:— | SHA256:— | |||
| 2924 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_DoppelVirus.exe_2dd80bc77e54f52a15d31ef57a54f43a3dc084_cab_0a6bd4f4\WERBCEA.tmp.hdmp | — | |
MD5:— | SHA256:— | |||
| 2924 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_DoppelVirus.exe_2dd80bc77e54f52a15d31ef57a54f43a3dc084_cab_0a6bd4f4\WERD390.tmp.mdmp | — | |
MD5:— | SHA256:— | |||
| 2924 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_DoppelVirus.exe_2dd80bc77e54f52a15d31ef57a54f43a3dc084_cab_0a6bd4f4\Report.wer | — | |
MD5:— | SHA256:— | |||
| 2924 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\DoppelVirus.exe.1832.dmp | — | |
MD5:— | SHA256:— | |||
| 1636 | WinRAR.exe | C:\Users\admin\Desktop\DoppelVirus\MegaApiClient.xml | xml | |
MD5:D68C609E8FE32DEDBC977F2DB8666803 | SHA256:452E3C2C8F461D0D12660DDBCD55413B422309C34DD4DE8C59F6003F43178AA5 | |||
| 1636 | WinRAR.exe | C:\Users\admin\Desktop\DoppelVirus\DotNetZip.xml | xml | |
MD5:AFFC560C09C60B437D6ABE245691CDC8 | SHA256:A55C1ACD3FE400A5CA2B988D838E3EBFA3C561B7657ADB6D994E27636369E5D1 | |||
| 2924 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WERA2A9.tmp.WERInternalMetadata.xml | xml | |
MD5:— | SHA256:— | |||
| 2924 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WERBCC9.tmp.appcompat.txt | xml | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
11
DNS requests
3
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2924 | WerFault.exe | 104.208.16.93:443 | watson.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | suspicious |
2280 | DoppelVirus.exe | 66.203.125.15:443 | g.api.mega.co.nz | Datacenter Luxembourg S.A. | LU | unknown |
2280 | DoppelVirus.exe | 66.203.125.13:443 | g.api.mega.co.nz | Datacenter Luxembourg S.A. | LU | unknown |
2280 | DoppelVirus.exe | 66.203.125.14:443 | g.api.mega.co.nz | Datacenter Luxembourg S.A. | LU | unknown |
— | — | 66.203.125.11:443 | g.api.mega.co.nz | Datacenter Luxembourg S.A. | LU | unknown |
1832 | DoppelVirus.exe | 66.203.125.11:443 | g.api.mega.co.nz | Datacenter Luxembourg S.A. | LU | unknown |
1588 | DoppelVirus.exe | 66.203.125.11:443 | g.api.mega.co.nz | Datacenter Luxembourg S.A. | LU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
g.api.mega.co.nz |
| shared |
watson.microsoft.com |
| whitelisted |
dns.msftncsi.com |
| shared |