analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
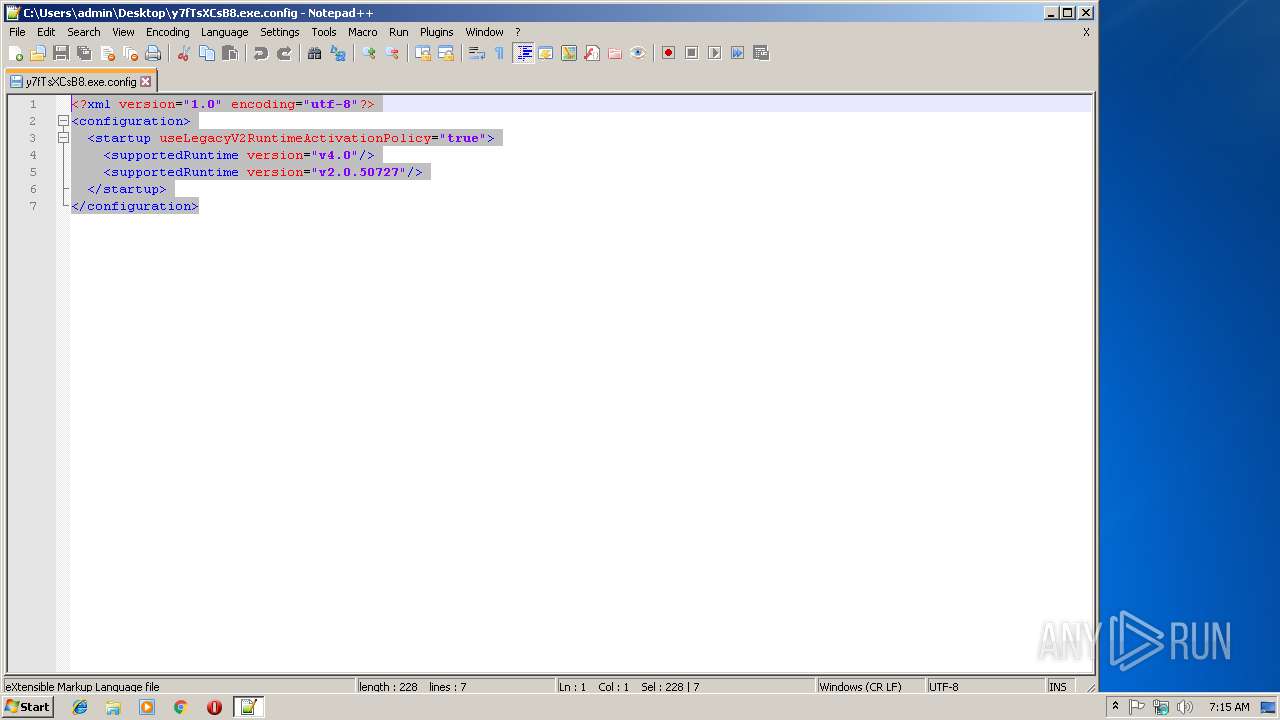
| File name: | y7fTsXCsB8.exe |
| Full analysis: | https://app.any.run/tasks/55c9e793-20ac-44fa-810b-b58490abd2d5 |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | March 14, 2019, 07:15:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | DF3199FAB02297E100AEE844DF0CA11E |
| SHA1: | 13017EE41075BBA9925D254EDA44B0162E4CC826 |
| SHA256: | 3121427D2D782F32BB8FC9383A27E7C1DB7F61D67ED1F57A619BB6ED4DA662FE |
| SSDEEP: | 24576:46WQsv3mfmkMY2GIEs/cdnAbdMDJZmNRDBU:Cr/lYnBSs |
MALICIOUS
Loads dropped or rewritten executable
- y7fTsXCsB8.exe (PID: 3668)
- Cookiesmr0dw.exe (PID: 4072)
Connects to CnC server
- explorer.exe (PID: 284)
FORMBOOK was detected
- explorer.exe (PID: 284)
Actions looks like stealing of personal data
- nbtstat.exe (PID: 2116)
Formbook was detected
- Firefox.exe (PID: 2276)
- nbtstat.exe (PID: 2116)
Changes the autorun value in the registry
- nbtstat.exe (PID: 2116)
Stealing of credential data
- nbtstat.exe (PID: 2116)
SUSPICIOUS
Creates files in the user directory
- notepad++.exe (PID: 2688)
- nbtstat.exe (PID: 2116)
Executable content was dropped or overwritten
- y7fTsXCsB8.exe (PID: 3668)
- explorer.exe (PID: 284)
- Cookiesmr0dw.exe (PID: 4072)
- DllHost.exe (PID: 2140)
Application launched itself
- y7fTsXCsB8.exe (PID: 3668)
- Cookiesmr0dw.exe (PID: 4072)
Starts CMD.EXE for commands execution
- nbtstat.exe (PID: 2116)
Loads DLL from Mozilla Firefox
- nbtstat.exe (PID: 2116)
Uses NETSTAT.EXE to discover network connections
- explorer.exe (PID: 284)
Creates files in the program directory
- DllHost.exe (PID: 2140)
INFO
Creates files in the user directory
- Firefox.exe (PID: 2276)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| ProductName: | Exeinfo PE by A.S.L |
|---|---|
| LegalTrademarks: | ( c ) A.S.L. Soft |
| LegalCopyright: | A.S.L. |
| FileVersion: | 2.3.0.6 |
| FileDescription: | ExEinfo PE |
| CompanyName: | A.S.L Software |
| Comments: | www.exeinfo.xwp.pl |
| CharacterSet: | Windows, Latin1 |
| LanguageCode: | English (U.S.) |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x0000 |
| ProductVersionNumber: | 2.3.0.6 |
| FileVersionNumber: | 2.3.0.6 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 4 |
| ImageVersion: | 6 |
| OSVersion: | 4 |
| EntryPoint: | 0x3489 |
| UninitializedDataSize: | 2048 |
| InitializedDataSize: | 141824 |
| CodeSize: | 25600 |
| LinkerVersion: | 6 |
| PEType: | PE32 |
| TimeStamp: | 2017:08:01 02:33:59+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 01-Aug-2017 00:33:59 |
| Detected languages: |
|
| Comments: | www.exeinfo.xwp.pl |
| CompanyName: | A.S.L Software |
| FileDescription: | ExEinfo PE |
| FileVersion: | 2.3.0.6 |
| LegalCopyright: | A.S.L. |
| LegalTrademarks: | ( c ) A.S.L. Soft |
| ProductName: | Exeinfo PE by A.S.L |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 01-Aug-2017 00:33:59 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000063D1 | 0x00006400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.47945 |
.rdata | 0x00008000 | 0x0000138E | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.14383 |
.data | 0x0000A000 | 0x00020358 | 0x00000600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.00074 |
.ndata | 0x0002B000 | 0x00010000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x0003B000 | 0x0000DE28 | 0x0000E000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.19818 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.30178 | 832 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 4.79746 | 9640 | UNKNOWN | English - United States | RT_ICON |
3 | 5.16809 | 4264 | UNKNOWN | English - United States | RT_ICON |
4 | 5.503 | 2440 | UNKNOWN | English - United States | RT_ICON |
5 | 5.92267 | 1128 | UNKNOWN | English - United States | RT_ICON |
103 | 2.64638 | 76 | UNKNOWN | English - United States | RT_GROUP_ICON |
105 | 2.66174 | 256 | UNKNOWN | English - United States | RT_DIALOG |
106 | 2.88094 | 284 | UNKNOWN | English - United States | RT_DIALOG |
111 | 2.48825 | 96 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
46
Monitored processes
14
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3668 | "C:\Users\admin\Desktop\y7fTsXCsB8.exe" | C:\Users\admin\Desktop\y7fTsXCsB8.exe | explorer.exe | ||||||||||||
User: admin Company: A.S.L Software Integrity Level: MEDIUM Description: ExEinfo PE Exit code: 0 Version: 2.3.0.6 Modules
| |||||||||||||||
| 2688 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\y7fTsXCsB8.exe.config" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO [email protected] Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.51 Modules
| |||||||||||||||
| 3580 | "C:\Program Files\Notepad++\updater\gup.exe" -v7.51 | C:\Program Files\Notepad++\updater\gup.exe | notepad++.exe | ||||||||||||
User: admin Company: Don HO [email protected] Integrity Level: MEDIUM Description: GUP : a free (LGPL) Generic Updater Exit code: 0 Version: 4.1 Modules
| |||||||||||||||
| 3276 | C:\Users\admin\Desktop\y7fTsXCsB8.exe | C:\Users\admin\Desktop\y7fTsXCsB8.exe | — | y7fTsXCsB8.exe | |||||||||||
User: admin Company: A.S.L Software Integrity Level: MEDIUM Description: ExEinfo PE Exit code: 0 Version: 2.3.0.6 Modules
| |||||||||||||||
| 2116 | "C:\Windows\System32\nbtstat.exe" | C:\Windows\System32\nbtstat.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP NetBios Information Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2832 | /c del "C:\Users\admin\Desktop\y7fTsXCsB8.exe" | C:\Windows\System32\cmd.exe | — | nbtstat.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 284 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2276 | "C:\Program Files\Mozilla Firefox\Firefox.exe" | C:\Program Files\Mozilla Firefox\Firefox.exe | nbtstat.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 61.0.2 Modules
| |||||||||||||||
| 2140 | C:\Windows\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\system32\DllHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4072 | "C:\Program Files\Kut-d\Cookiesmr0dw.exe" | C:\Program Files\Kut-d\Cookiesmr0dw.exe | explorer.exe | ||||||||||||
User: admin Company: A.S.L Software Integrity Level: MEDIUM Description: ExEinfo PE Exit code: 0 Version: 2.3.0.6 Modules
| |||||||||||||||
Total events
1 956
Read events
1 920
Write events
36
Delete events
0
Modification events
| (PID) Process: | (284) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2688) notepad++.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2688) notepad++.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2688) notepad++.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (284) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | {7P5N40RS-N0SO-4OSP-874N-P0S2R0O9SN8R}\Abgrcnq++\abgrcnq++.rkr |
Value: 0000000000000000000000001D030000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF000000000000000000000000 | |||
| (PID) Process: | (284) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 000000002D0000003D000000D04E1500090000000B000000DCC402007B00370043003500410034003000450046002D0041003000460042002D0034004200460043002D0038003700340041002D004300300046003200450030004200390046004100380045007D005C00410064006F00620065005C004100630072006F0062006100740020005200650061006400650072002000440043005C005200650061006400650072005C004100630072006F0052006400330032002E0065007800650000000000D09866060000000034E82802C05D5A740200000002000000000C00940F000000E8E82802010000000400000001000000010000006B001001D098660605000000D098660602020000E20101AE2B51EA0088E7280239B58D76E20101AE24E82802130000000400000030000000120000001D000000130000001D0000000E00000012000000020000003200000014000000E387EE7A38E82802F3AE5B7400574100E20101AE010000000000000011000000F0443500E8443500A14A52740000000020E800001F51EA7AD0E728028291917520E828028CD800006B51EA7AE4E72802B69C917590D8D4035C0000000401000084F2280244F228026B4E317411000000F0443500E8443500A8EAD403FA4F31740000000074E80000AB5EEA7A24E828028291917574E8280228E8280227959175000000008CD8D40350E82802CD9491758CD8D403FCE8280200D4D403E19491750000000000D4D403FCE8280258E82802000000000F000000E21705007B00440036003500320033003100420030002D0042003200460031002D0034003800350037002D0041003400430045002D004100380045003700430036004500410037004400320037007D005C007400610073006B006D00670072002E006500780065000000D201B0E536027CE43602A532DC75BCE4360294E5360200000000B432DC75F4E536020145DC756A00CA028C00CA02B8ACCA0278E336020001000101000000000100000000000028FCA802C8E53602E0E2BF02A4E53602CAFEBF02A0E33602D4E536026000CA022B0000006A00CA0228FCA802000000008C00CA025CE536020A00CA020000000005000500A823D3016601CA022B0000000F000000F4E53602BCE5360228FCA8021000000074FFA802050017004E1ED301BCE436021600000002000000B8ACCA020400360228FCA80203000000000000000909090009090909000911110000000011000000B8452700B04527000000000000000000000000000000000000000000000000001CE400005A743083D0E336028291F5751CE43602CCB700002E743083E4E33602B69CF575D0B7DD024C060000FCE3360240B3DD0208E43602789CF57511000000B8452700B045270060B3DD026CE40000E67330831CE436028291F5756CE4360220E436022795F57500000000CCB7DD0248E43602CD94F575CCB7DD02F4E4360240B3DD02E194F5750000000040B3DD02F4E4360250E43602090000000B000000DCC402007B00370043003500410034003000450046002D0041003000460042002D0034004200460043002D0038003700340041002D004300300046003200450030004200390046004100380045007D005C00410064006F00620065005C004100630072006F0062006100740020005200650061006400650072002000440043005C005200650061006400650072005C004100630072006F0052006400330032002E0065007800650000000000D09866060000000034E82802C05D5A740200000002000000000C00940F000000E8E82802010000000400000001000000010000006B001001D098660605000000D098660602020000E20101AE2B51EA0088E7280239B58D76E20101AE24E82802130000000400000030000000120000001D000000130000001D0000000E00000012000000020000003200000014000000E387EE7A38E82802F3AE5B7400574100E20101AE010000000000000011000000F0443500E8443500A14A52740000000020E800001F51EA7AD0E728028291917520E828028CD800006B51EA7AE4E72802B69C917590D8D4035C0000000401000084F2280244F228026B4E317411000000F0443500E8443500A8EAD403FA4F31740000000074E80000AB5EEA7A24E828028291917574E8280228E8280227959175000000008CD8D40350E82802CD9491758CD8D403FCE8280200D4D403E19491750000000000D4D403FCE8280258E82802 | |||
| (PID) Process: | (284) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | {7P5N40RS-N0SO-4OSP-874N-P0S2R0O9SN8R}\Abgrcnq++\hcqngre\THC.rkr |
Value: 000000000000000000000000420F0000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF000000000000000000000000 | |||
| (PID) Process: | (284) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 000000002D0000003D000000125E1500090000000B000000DCC402007B00370043003500410034003000450046002D0041003000460042002D0034004200460043002D0038003700340041002D004300300046003200450030004200390046004100380045007D005C00410064006F00620065005C004100630072006F0062006100740020005200650061006400650072002000440043005C005200650061006400650072005C004100630072006F0052006400330032002E0065007800650000000000D09866060000000034E82802C05D5A740200000002000000000C00940F000000E8E82802010000000400000001000000010000006B001001D098660605000000D098660602020000E20101AE2B51EA0088E7280239B58D76E20101AE24E82802130000000400000030000000120000001D000000130000001D0000000E00000012000000020000003200000014000000E387EE7A38E82802F3AE5B7400574100E20101AE010000000000000011000000F0443500E8443500A14A52740000000020E800001F51EA7AD0E728028291917520E828028CD800006B51EA7AE4E72802B69C917590D8D4035C0000000401000084F2280244F228026B4E317411000000F0443500E8443500A8EAD403FA4F31740000000074E80000AB5EEA7A24E828028291917574E8280228E8280227959175000000008CD8D40350E82802CD9491758CD8D403FCE8280200D4D403E19491750000000000D4D403FCE8280258E82802000000000F000000E21705007B00440036003500320033003100420030002D0042003200460031002D0034003800350037002D0041003400430045002D004100380045003700430036004500410037004400320037007D005C007400610073006B006D00670072002E006500780065000000D201B0E536027CE43602A532DC75BCE4360294E5360200000000B432DC75F4E536020145DC756A00CA028C00CA02B8ACCA0278E336020001000101000000000100000000000028FCA802C8E53602E0E2BF02A4E53602CAFEBF02A0E33602D4E536026000CA022B0000006A00CA0228FCA802000000008C00CA025CE536020A00CA020000000005000500A823D3016601CA022B0000000F000000F4E53602BCE5360228FCA8021000000074FFA802050017004E1ED301BCE436021600000002000000B8ACCA020400360228FCA80203000000000000000909090009090909000911110000000011000000B8452700B04527000000000000000000000000000000000000000000000000001CE400005A743083D0E336028291F5751CE43602CCB700002E743083E4E33602B69CF575D0B7DD024C060000FCE3360240B3DD0208E43602789CF57511000000B8452700B045270060B3DD026CE40000E67330831CE436028291F5756CE4360220E436022795F57500000000CCB7DD0248E43602CD94F575CCB7DD02F4E4360240B3DD02E194F5750000000040B3DD02F4E4360250E43602090000000B000000DCC402007B00370043003500410034003000450046002D0041003000460042002D0034004200460043002D0038003700340041002D004300300046003200450030004200390046004100380045007D005C00410064006F00620065005C004100630072006F0062006100740020005200650061006400650072002000440043005C005200650061006400650072005C004100630072006F0052006400330032002E0065007800650000000000D09866060000000034E82802C05D5A740200000002000000000C00940F000000E8E82802010000000400000001000000010000006B001001D098660605000000D098660602020000E20101AE2B51EA0088E7280239B58D76E20101AE24E82802130000000400000030000000120000001D000000130000001D0000000E00000012000000020000003200000014000000E387EE7A38E82802F3AE5B7400574100E20101AE010000000000000011000000F0443500E8443500A14A52740000000020E800001F51EA7AD0E728028291917520E828028CD800006B51EA7AE4E72802B69C917590D8D4035C0000000401000084F2280244F228026B4E317411000000F0443500E8443500A8EAD403FA4F31740000000074E80000AB5EEA7A24E828028291917574E8280228E8280227959175000000008CD8D40350E82802CD9491758CD8D403FCE8280200D4D403E19491750000000000D4D403FCE8280258E82802 | |||
| (PID) Process: | (284) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | {7P5N40RS-N0SO-4OSP-874N-P0S2R0O9SN8R}\Abgrcnq++\abgrcnq++.rkr |
Value: 0000000000000000010000001D030000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF000000000000000000000000 | |||
| (PID) Process: | (284) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 000000002D0000003E000000125E1500090000000B000000DCC402007B00370043003500410034003000450046002D0041003000460042002D0034004200460043002D0038003700340041002D004300300046003200450030004200390046004100380045007D005C00410064006F00620065005C004100630072006F0062006100740020005200650061006400650072002000440043005C005200650061006400650072005C004100630072006F0052006400330032002E0065007800650000000000D09866060000000034E82802C05D5A740200000002000000000C00940F000000E8E82802010000000400000001000000010000006B001001D098660605000000D098660602020000E20101AE2B51EA0088E7280239B58D76E20101AE24E82802130000000400000030000000120000001D000000130000001D0000000E00000012000000020000003200000014000000E387EE7A38E82802F3AE5B7400574100E20101AE010000000000000011000000F0443500E8443500A14A52740000000020E800001F51EA7AD0E728028291917520E828028CD800006B51EA7AE4E72802B69C917590D8D4035C0000000401000084F2280244F228026B4E317411000000F0443500E8443500A8EAD403FA4F31740000000074E80000AB5EEA7A24E828028291917574E8280228E8280227959175000000008CD8D40350E82802CD9491758CD8D403FCE8280200D4D403E19491750000000000D4D403FCE8280258E82802000000000F000000E21705007B00440036003500320033003100420030002D0042003200460031002D0034003800350037002D0041003400430045002D004100380045003700430036004500410037004400320037007D005C007400610073006B006D00670072002E006500780065000000D201B0E536027CE43602A532DC75BCE4360294E5360200000000B432DC75F4E536020145DC756A00CA028C00CA02B8ACCA0278E336020001000101000000000100000000000028FCA802C8E53602E0E2BF02A4E53602CAFEBF02A0E33602D4E536026000CA022B0000006A00CA0228FCA802000000008C00CA025CE536020A00CA020000000005000500A823D3016601CA022B0000000F000000F4E53602BCE5360228FCA8021000000074FFA802050017004E1ED301BCE436021600000002000000B8ACCA020400360228FCA80203000000000000000909090009090909000911110000000011000000B8452700B04527000000000000000000000000000000000000000000000000001CE400005A743083D0E336028291F5751CE43602CCB700002E743083E4E33602B69CF575D0B7DD024C060000FCE3360240B3DD0208E43602789CF57511000000B8452700B045270060B3DD026CE40000E67330831CE436028291F5756CE4360220E436022795F57500000000CCB7DD0248E43602CD94F575CCB7DD02F4E4360240B3DD02E194F5750000000040B3DD02F4E4360250E43602090000000B000000DCC402007B00370043003500410034003000450046002D0041003000460042002D0034004200460043002D0038003700340041002D004300300046003200450030004200390046004100380045007D005C00410064006F00620065005C004100630072006F0062006100740020005200650061006400650072002000440043005C005200650061006400650072005C004100630072006F0052006400330032002E0065007800650000000000D09866060000000034E82802C05D5A740200000002000000000C00940F000000E8E82802010000000400000001000000010000006B001001D098660605000000D098660602020000E20101AE2B51EA0088E7280239B58D76E20101AE24E82802130000000400000030000000120000001D000000130000001D0000000E00000012000000020000003200000014000000E387EE7A38E82802F3AE5B7400574100E20101AE010000000000000011000000F0443500E8443500A14A52740000000020E800001F51EA7AD0E728028291917520E828028CD800006B51EA7AE4E72802B69C917590D8D4035C0000000401000084F2280244F228026B4E317411000000F0443500E8443500A8EAD403FA4F31740000000074E80000AB5EEA7A24E828028291917574E8280228E8280227959175000000008CD8D40350E82802CD9491758CD8D403FCE8280200D4D403E19491750000000000D4D403FCE8280258E82802 | |||
Executable files
8
Suspicious files
73
Text files
16
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3668 | y7fTsXCsB8.exe | C:\Users\admin\AppData\Local\Temp\nsyDE1E.tmp\sYqEVzUD.txt | text | |
MD5:BD8F783D4904011C332957BE852ECB46 | SHA256:F5ECC0750D2CA6CE50B5DED4B77C7743892E66187C24A33C962FEF6B853F7C99 | |||
| 2688 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\session.xml | text | |
MD5:F13B22C0EF49863E9BAF782AFE2562AC | SHA256:4DC3EBB0D0B525CDDF7E39E1FCECE6097576FECEF84AE83B49D98A44E01AB3B3 | |||
| 3668 | y7fTsXCsB8.exe | C:\Users\admin\Desktop\y7fTsXCsB8.exe.config | xml | |
MD5:4F27F5EB21BDA1863AE582832B495911 | SHA256:D96AD73B2F1668ADE39462F1E2044D55B74D1A6090A5C15F4E2F5820E6D5EF4A | |||
| 2688 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\config.xml | xml | |
MD5:9DF7B16A4983447B8551763B94247114 | SHA256:CA28004A172C2D7874119BD4847A32A8048CAC9E9E05B78DEB70762CE8B45B2A | |||
| 3668 | y7fTsXCsB8.exe | C:\Users\admin\AppData\Local\Temp\nsyDE1E.tmp\Stavka-3.mp3 | mp3 | |
MD5:405756B3F7C5F92E11096039B62E61F4 | SHA256:B32B971793858F8B9CC0C2CD21E6ED2C981FE6866A3FE934F4F6CA8C03D93F84 | |||
| 3668 | y7fTsXCsB8.exe | C:\Users\admin\AppData\Local\Temp\nsyDE1E.tmp\2isewpqt.3lj | image | |
MD5:890D08E62212F1FBF0F4A225D3ED5B82 | SHA256:796C4ED3F5390F74B7973C6AACFA82FA8A9D7E584676FB48404F1CD5BAEA0B1A | |||
| 3668 | y7fTsXCsB8.exe | C:\Users\admin\AppData\Local\Temp\nsyDE1E.tmp\IdYVOb7yYryuIL4t.dll | executable | |
MD5:A54E0AE94D3D6234F9DBBC10F6CE500A | SHA256:AC5CCACBB1B72ADA90BE11477FB97CD332CC2A33A83427675D377C9D63C08BB5 | |||
| 3668 | y7fTsXCsB8.exe | C:\Users\admin\AppData\Local\Temp\nsyDE1E.tmp\cpcbrgxf.d1z | image | |
MD5:898A5D672A626D39D6536A1EBEF96EE4 | SHA256:9D61B8C315587A0872DDA8515E08C9FADDAD17454DEBA1D0166BC301D956B3EB | |||
| 2116 | nbtstat.exe | C:\Users\admin\AppData\Roaming\L789231B\L78logrc.ini | binary | |
MD5:2855A82ECDD565B4D957EC2EE05AED26 | SHA256:88E38DA5B12DD96AFD9DC90C79929EC31D8604B1AFDEBDD5A02B19249C08C939 | |||
| 3668 | y7fTsXCsB8.exe | C:\Users\admin\AppData\Local\Temp\nsyDE1E.tmp\Icon Dollar 01.png | image | |
MD5:F5A151367A19533E4112893C183D8F72 | SHA256:29B078AEED620C40E8F3C60F2C112FE217FFF4E87AAEE40AF46957ABF458D504 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
19
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
284 | explorer.exe | GET | — | 172.217.16.147:80 | http://www.mantuidaman.com/m24/?yVftqxDh=febP4Wjw8AQDU/aQrEfEfcs+CuAQ4VWjGG6DgO1MeZWQTbd2N9s8U6k2Z9EkzXTfCkx6PA==&1b0=L6QliPVP6V4PlVqP&sql=1 | US | — | — | malicious |
284 | explorer.exe | GET | — | 47.105.157.66:80 | http://www.zongpuw.com/m24/?yVftqxDh=LOm2yhEldEMRRSyscaC0GryXsCD5UyssDwr9A8r/bgtERWqQOMCdTPhCTU+F5/FLjityJg==&1b0=L6QliPVP6V4PlVqP | CN | — | — | malicious |
284 | explorer.exe | GET | — | 198.199.79.56:80 | http://www.ajdove.com/m24/?yVftqxDh=kn7NtWSCuCtcLsk5OKq9WXv/0VP3QoS4v54i+2snUve+uqiNE4paWFrC7VF2HwJ+b2EWJw==&1b0=L6QliPVP6V4PlVqP&sql=1 | US | — | — | malicious |
— | — | GET | 200 | 195.138.255.16:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCEBPqKHBb9OztDDZjCYBhQzY%3D | DE | der | 471 b | whitelisted |
284 | explorer.exe | POST | — | 172.217.16.147:80 | http://www.mantuidaman.com/m24/ | US | — | — | malicious |
284 | explorer.exe | POST | — | 172.217.16.147:80 | http://www.mantuidaman.com/m24/ | US | — | — | malicious |
284 | explorer.exe | GET | — | 198.54.117.212:80 | http://www.airbnb-online-booking.com/m24/?yVftqxDh=63gdm11q20rcc0M3hUwQxD1645nWnGcXIN2ZKMDF02itVUZAP8FMya6sAKxkJKU9QuzA6w==&1b0=L6QliPVP6V4PlVqP&sql=1 | US | — | — | malicious |
284 | explorer.exe | GET | — | 108.187.106.76:80 | http://www.jljxwd.com/m24/?yVftqxDh=e5iTx40M2VdgWF4cEfYIM536j4/hCIhpKCB/aZCupY3LhDvdI/iSOy+RdwR0CLObtlUeaw==&1b0=L6QliPVP6V4PlVqP&sql=1 | US | — | — | malicious |
— | — | GET | 200 | 195.138.255.16:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEAXk3DuUOKs7hZfLpqGYUOM%3D | DE | der | 727 b | whitelisted |
284 | explorer.exe | POST | — | 198.199.79.56:80 | http://www.ajdove.com/m24/ | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3580 | gup.exe | 37.59.28.236:443 | notepad-plus-plus.org | OVH SAS | FR | whitelisted |
284 | explorer.exe | 172.217.16.147:80 | www.mantuidaman.com | Google Inc. | US | malicious |
284 | explorer.exe | 198.54.117.212:80 | www.airbnb-online-booking.com | Namecheap, Inc. | US | malicious |
284 | explorer.exe | 108.187.106.76:80 | www.jljxwd.com | Nobis Technology Group, LLC | US | malicious |
— | — | 195.138.255.16:80 | ocsp.usertrust.com | AS33891 Netzbetrieb GmbH | DE | suspicious |
284 | explorer.exe | 47.105.157.66:80 | www.zongpuw.com | Hangzhou Alibaba Advertising Co.,Ltd. | CN | malicious |
284 | explorer.exe | 198.199.79.56:80 | www.ajdove.com | Digital Ocean, Inc. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
notepad-plus-plus.org |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
www.zongpuw.com |
| malicious |
www.mantuidaman.com |
| malicious |
www.ajdove.com |
| malicious |
www.ofb8lsim.site |
| unknown |
www.airbnb-online-booking.com |
| malicious |
www.jljxwd.com |
| malicious |
www.barfashion.tech |
| suspicious |
www.webcube.studio |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
284 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
284 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
284 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
284 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
284 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (POST) |
284 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
284 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
284 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (POST) |
284 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (POST) |
284 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
13 ETPRO signatures available at the full report
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|