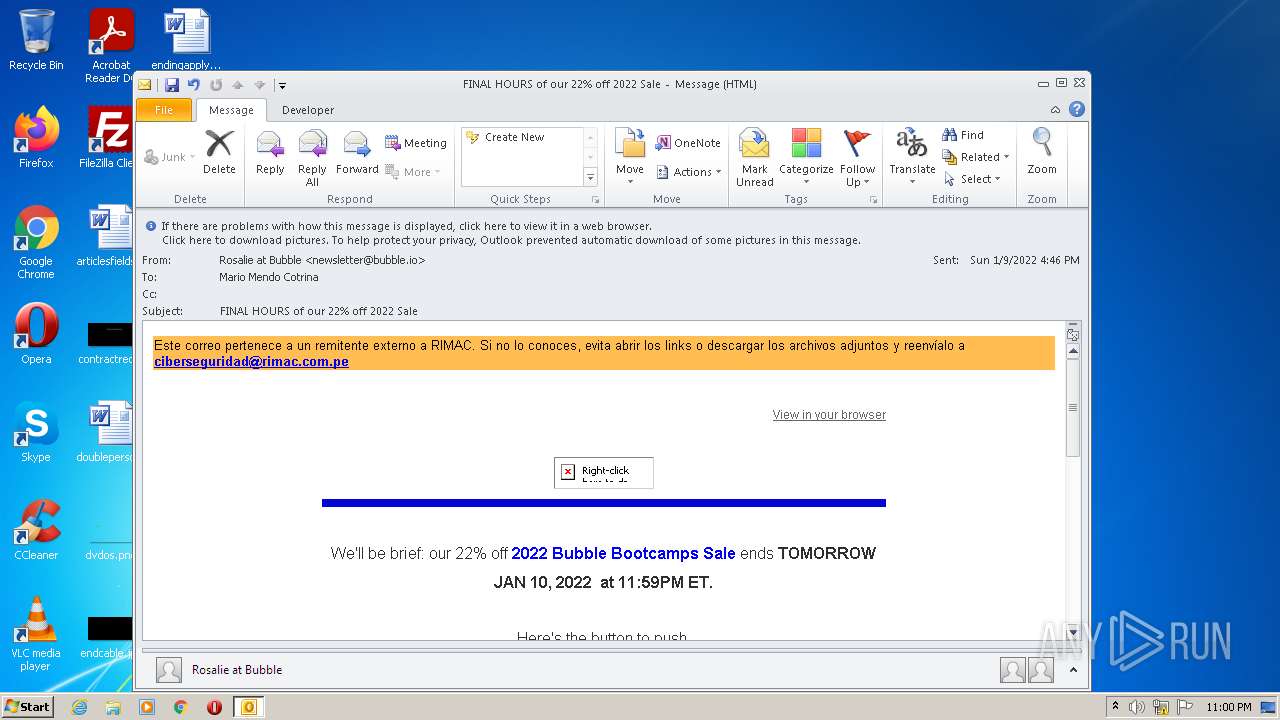
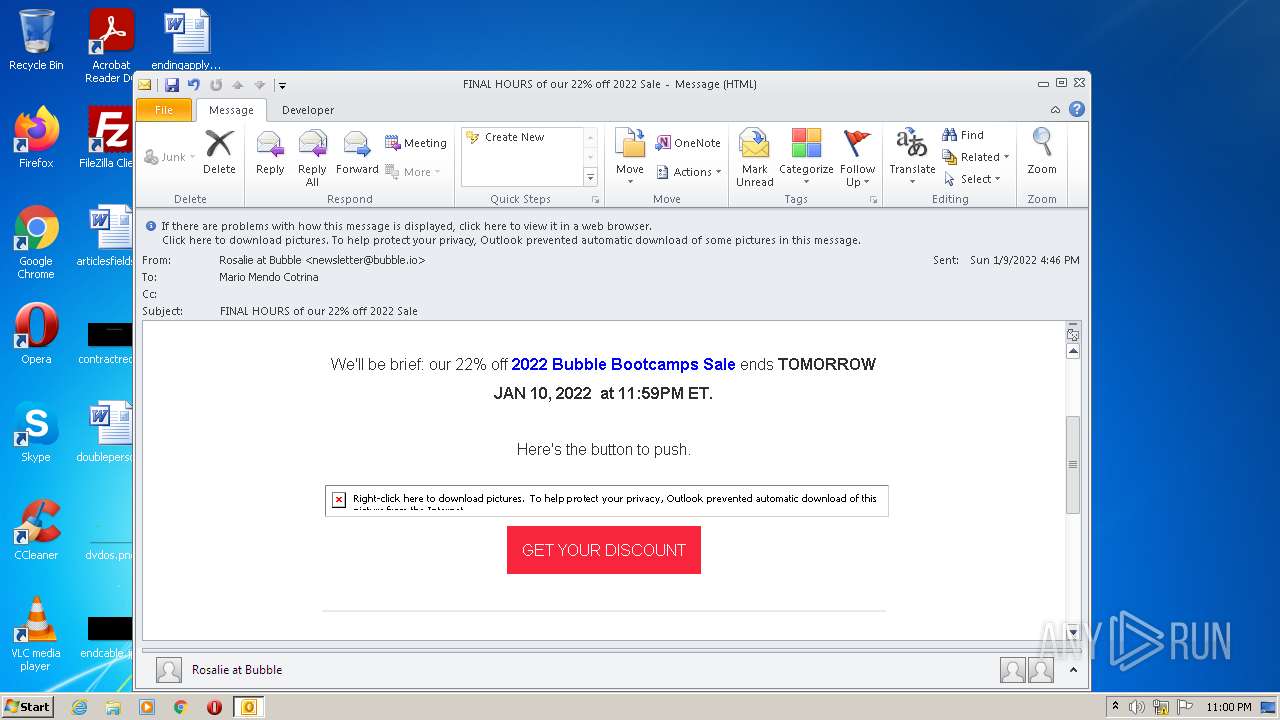
| File name: | FINAL HOURS of our 22% off 2022 Sale.eml |
| Full analysis: | https://app.any.run/tasks/d81897f7-2869-4285-8f45-0def9ee9a35b |
| Verdict: | Malicious activity |
| Analysis date: | January 14, 2022, 23:00:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 6DCEF5B82C42C0295B132D8FB98CBC18 |
| SHA1: | E940D021D3A2C28849C1910DF3A51B8DF9D8CAE1 |
| SHA256: | 311C252ADA0587FFD4BB04B7988295EE33FCDEF7E6F3DEED6EEF29EBA21D6634 |
| SSDEEP: | 1536:lu0giGbohXE/UholbThaKxSZbchPN8NkcAbHuo0Ki96:zGkhXE/UhoJThaKxSFchPN8NkcAbHuoJ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the computer name
- OUTLOOK.EXE (PID: 1188)
Starts Internet Explorer
- OUTLOOK.EXE (PID: 1188)
Checks supported languages
- OUTLOOK.EXE (PID: 1188)
Searches for installed software
- OUTLOOK.EXE (PID: 1188)
Creates files in the user directory
- OUTLOOK.EXE (PID: 1188)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 4076)
INFO
Reads the computer name
- iexplore.exe (PID: 3412)
- iexplore.exe (PID: 4076)
Changes internet zones settings
- iexplore.exe (PID: 3412)
Reads settings of System Certificates
- iexplore.exe (PID: 4076)
- iexplore.exe (PID: 3412)
Checks Windows Trust Settings
- iexplore.exe (PID: 3412)
- iexplore.exe (PID: 4076)
Application launched itself
- iexplore.exe (PID: 3412)
Checks supported languages
- iexplore.exe (PID: 3412)
- iexplore.exe (PID: 4076)
Creates files in the user directory
- iexplore.exe (PID: 4076)
Reads internet explorer settings
- iexplore.exe (PID: 4076)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 1188)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
41
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1188 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\21a8fd30-27fa-484b-a9a4-ca456ddac426.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
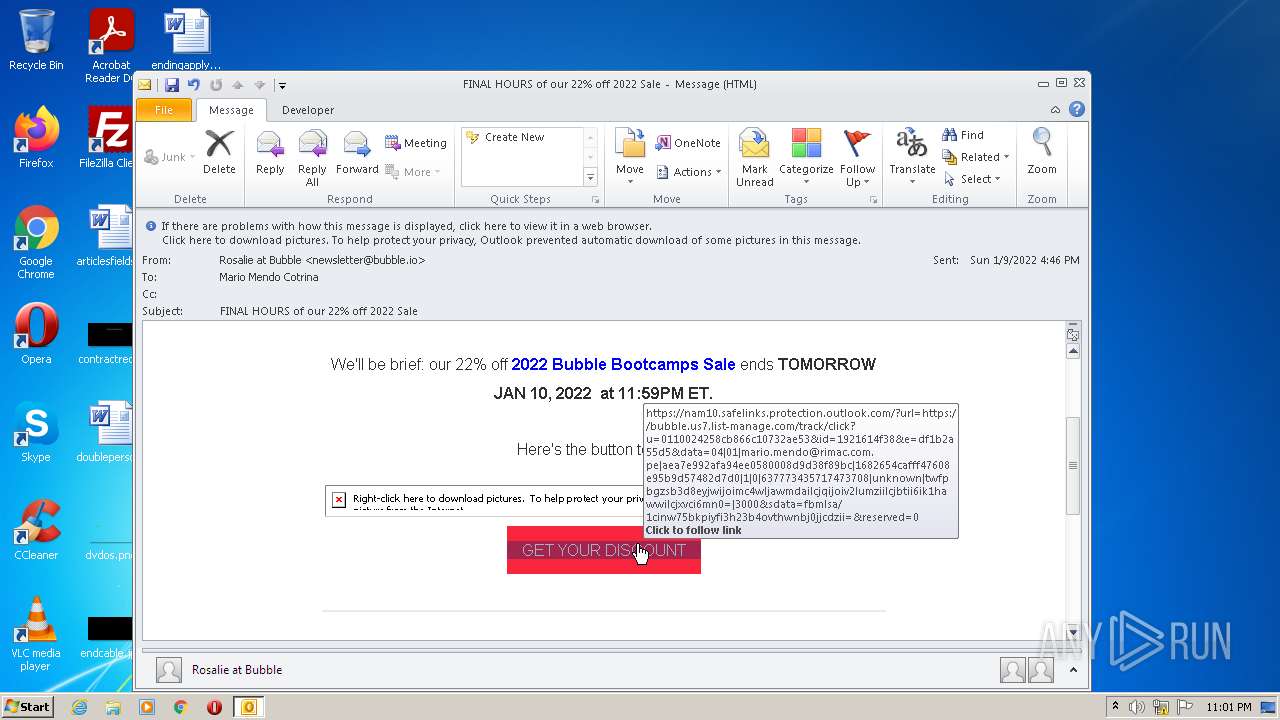
| 3412 | "C:\Program Files\Internet Explorer\iexplore.exe" https://nam10.safelinks.protection.outlook.com/?url=https%3A%2F%2Fbubble.us7.list-manage.com%2Ftrack%2Fclick%3Fu%3D0110024258cb866c10732ae53%26id%3D1921614f38%26e%3Ddf1b2a55d5&data=04%7C01%7Cmario.mendo%40rimac.com.pe%7Caea7e992afa94ee0580008d9d38f89bc%7C1682654cafff47608e95b9d57482d7d0%7C1%7C0%7C637773435717473708%7CUnknown%7CTWFpbGZsb3d8eyJWIjoiMC4wLjAwMDAiLCJQIjoiV2luMzIiLCJBTiI6Ik1haWwiLCJXVCI6Mn0%3D%7C3000&sdata=FBMLsa%2F1CiNw75bkPiYFi3H23B4oVtHWnbj0JJcDZII%3D&reserved=0 | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 4076 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3412 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
30 876
Read events
29 963
Write events
892
Delete events
21
Modification events
| (PID) Process: | (1188) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1188) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1188) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1188) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1188) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1188) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1188) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1188) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1188) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (1188) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
40
Text files
137
Unknown types
43
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1188 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR2AD4.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1188 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 4076 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\2F23D0F5E4D72862517E1CB26A329742_F6FACC49395CFA949BCE851E73323C49 | binary | |
MD5:— | SHA256:— | |||
| 4076 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_D975BBA8033175C8D112023D8A7A8AD6 | binary | |
MD5:— | SHA256:— | |||
| 1188 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_Calendar_2_9AB6CE356ED4A849AD17D402309518E8.dat | xml | |
MD5:B21ED3BD946332FF6EBC41A87776C6BB | SHA256:B1AAC4E817CD10670B785EF8E5523C4A883F44138E50486987DC73054A46F6F4 | |||
| 4076 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\IKHD7V4G.txt | text | |
MD5:— | SHA256:— | |||
| 1188 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_AvailabilityOptions_2_4CED281D80777C40AD893DB2427D16EF.dat | xml | |
MD5:EEAA832C12F20DE6AAAA9C7B77626E72 | SHA256:C4C9A90F2C961D9EE79CF08FBEE647ED7DE0202288E876C7BAAD00F4CA29CA16 | |||
| 1188 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 1188 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_RssRule_2_D0C295BAC69CA34CBDCAAD1D5F7D8928.dat | xml | |
MD5:D8B37ED0410FB241C283F72B76987F18 | SHA256:31E68049F6B7F21511E70CD7F2D95B9CF1354CF54603E8F47C1FC40F40B7A114 | |||
| 4076 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_D975BBA8033175C8D112023D8A7A8AD6 | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
41
TCP/UDP connections
135
DNS requests
57
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4076 | iexplore.exe | GET | 200 | 18.66.92.73:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
4076 | iexplore.exe | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
4076 | iexplore.exe | GET | 200 | 104.18.31.182:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
4076 | iexplore.exe | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEGmSmALa8169CgAAAAEn3NM%3D | US | der | 471 b | whitelisted |
4076 | iexplore.exe | GET | 200 | 52.222.250.185:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
4076 | iexplore.exe | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
3412 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
4076 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
4076 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAGewca9P1l7sgwzOOVR2Hc%3D | US | der | 471 b | whitelisted |
4076 | iexplore.exe | GET | 200 | 52.222.250.112:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4076 | iexplore.exe | 104.47.70.28:443 | nam10.safelinks.protection.outlook.com | Microsoft Corporation | US | suspicious |
1188 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
4076 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
4076 | iexplore.exe | 18.66.121.131:443 | dhtiece9044ep.cloudfront.net | Massachusetts Institute of Technology | US | unknown |
4076 | iexplore.exe | 18.66.92.73:80 | o.ss2.us | Massachusetts Institute of Technology | US | unknown |
4076 | iexplore.exe | 18.66.92.97:443 | dd7tel2830j4w.cloudfront.net | Massachusetts Institute of Technology | US | unknown |
3412 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3412 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
4076 | iexplore.exe | 142.250.184.202:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
4076 | iexplore.exe | 104.19.241.93:443 | bubble.io | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
nam10.safelinks.protection.outlook.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
bubble.us7.list-manage.com |
| suspicious |
bubble.io |
| malicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
dhtiece9044ep.cloudfront.net |
| whitelisted |
dd7tel2830j4w.cloudfront.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4076 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
4076 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
4076 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
4076 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |