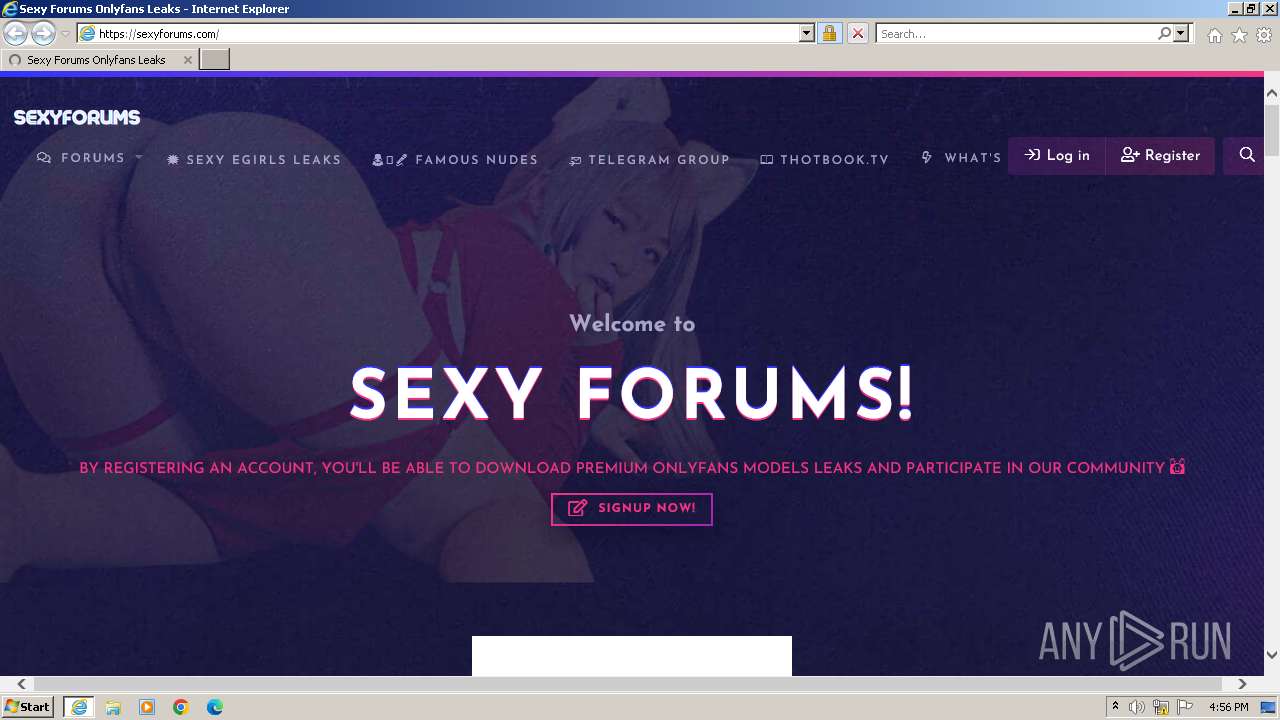
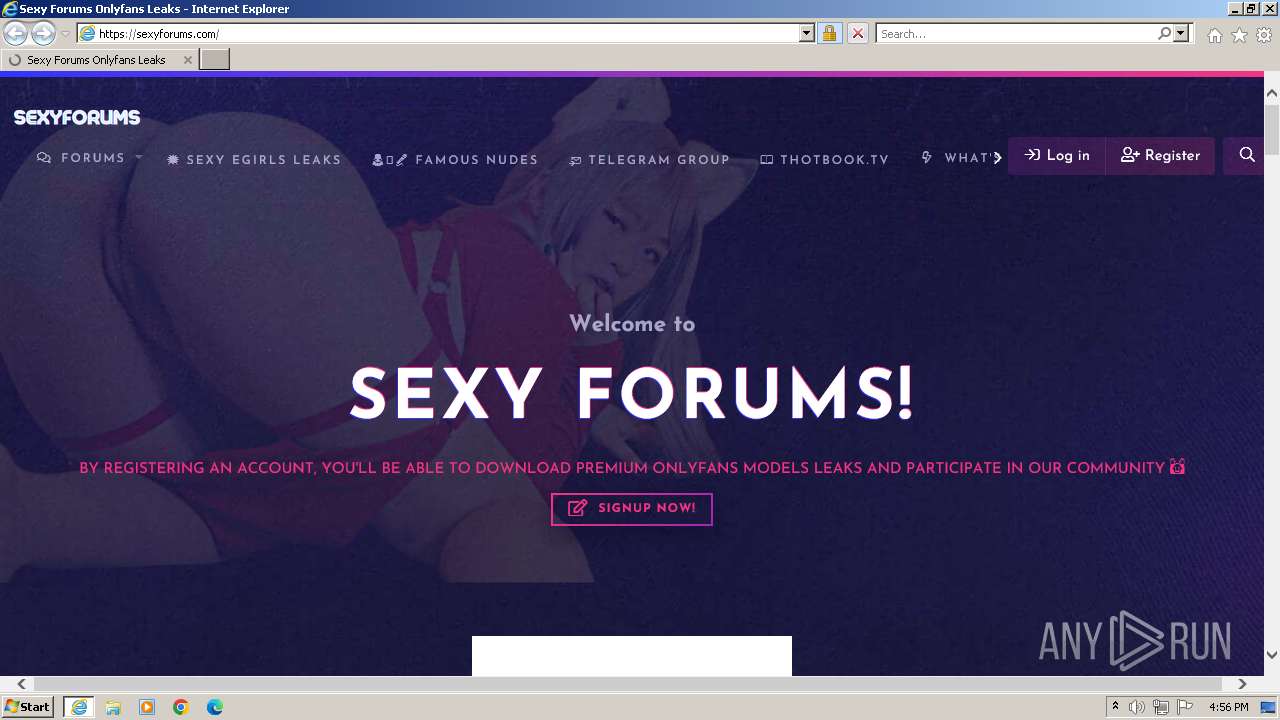
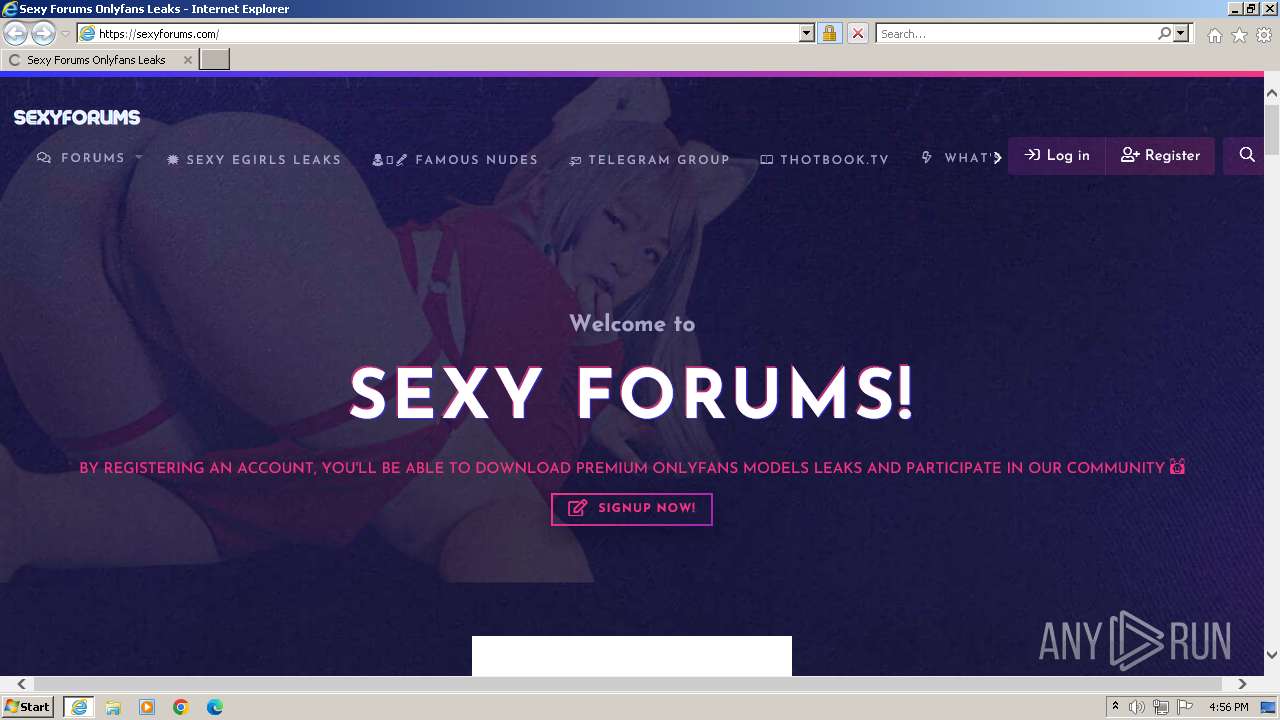
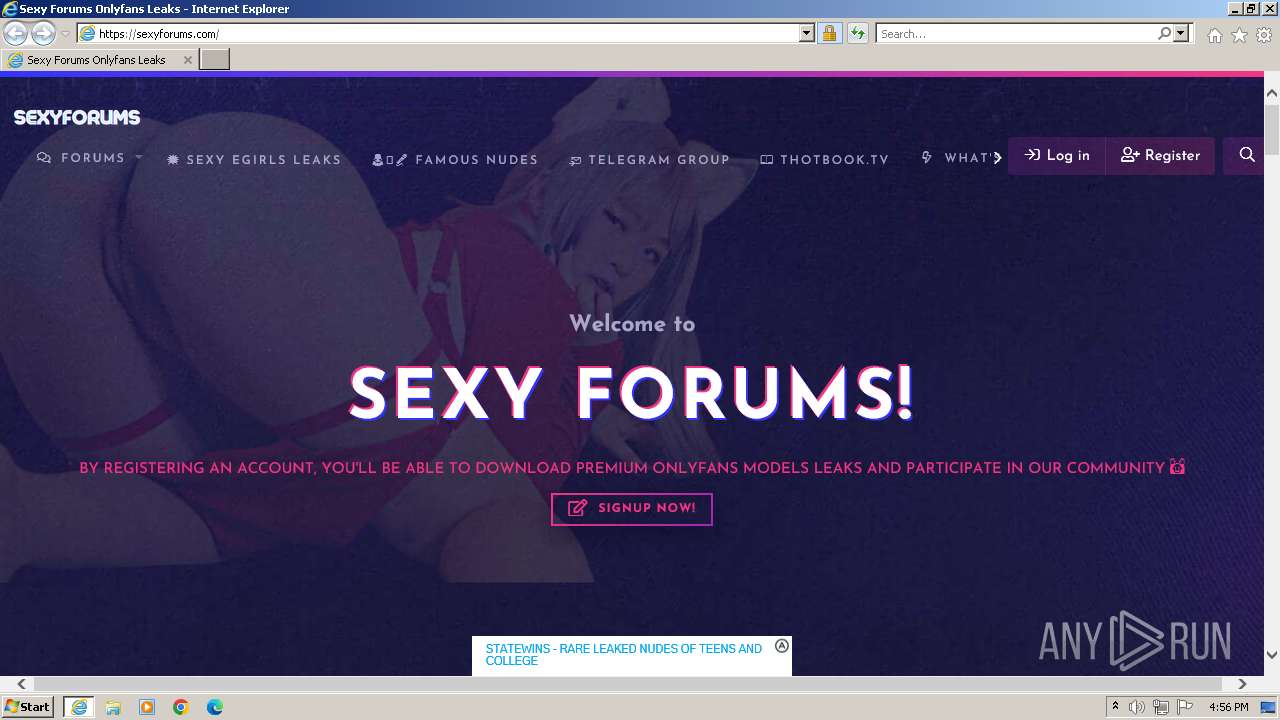
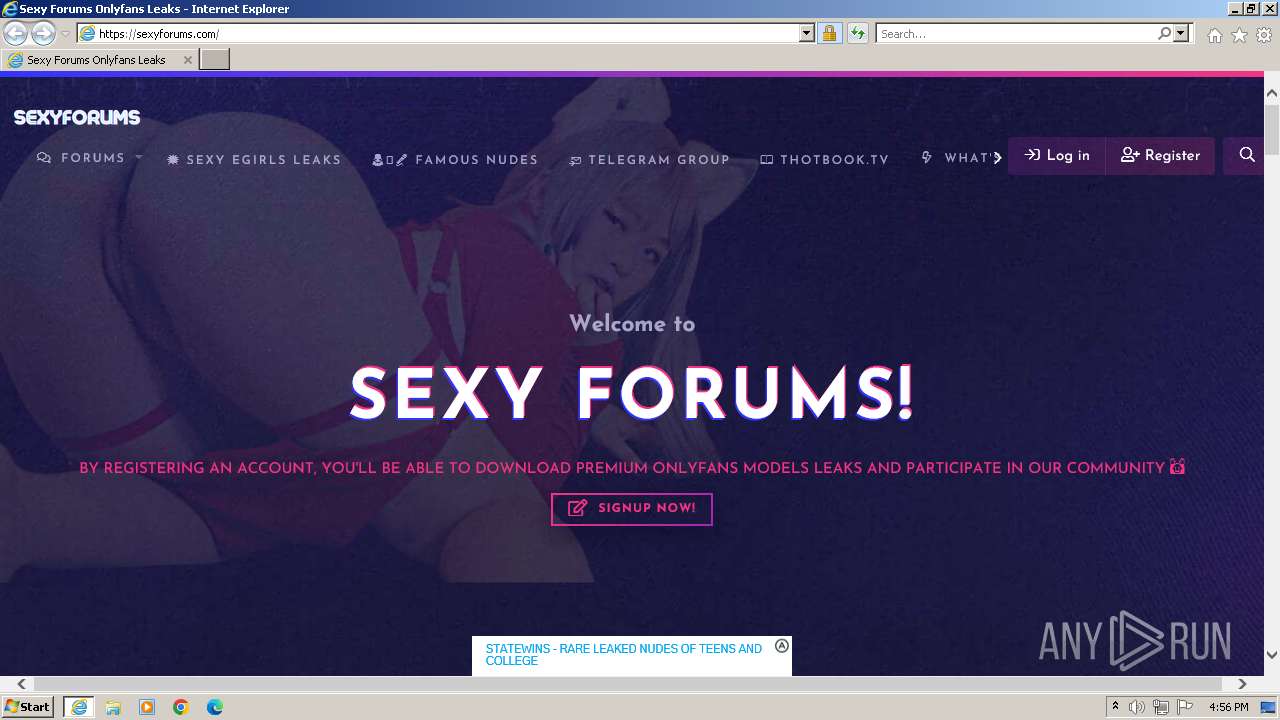
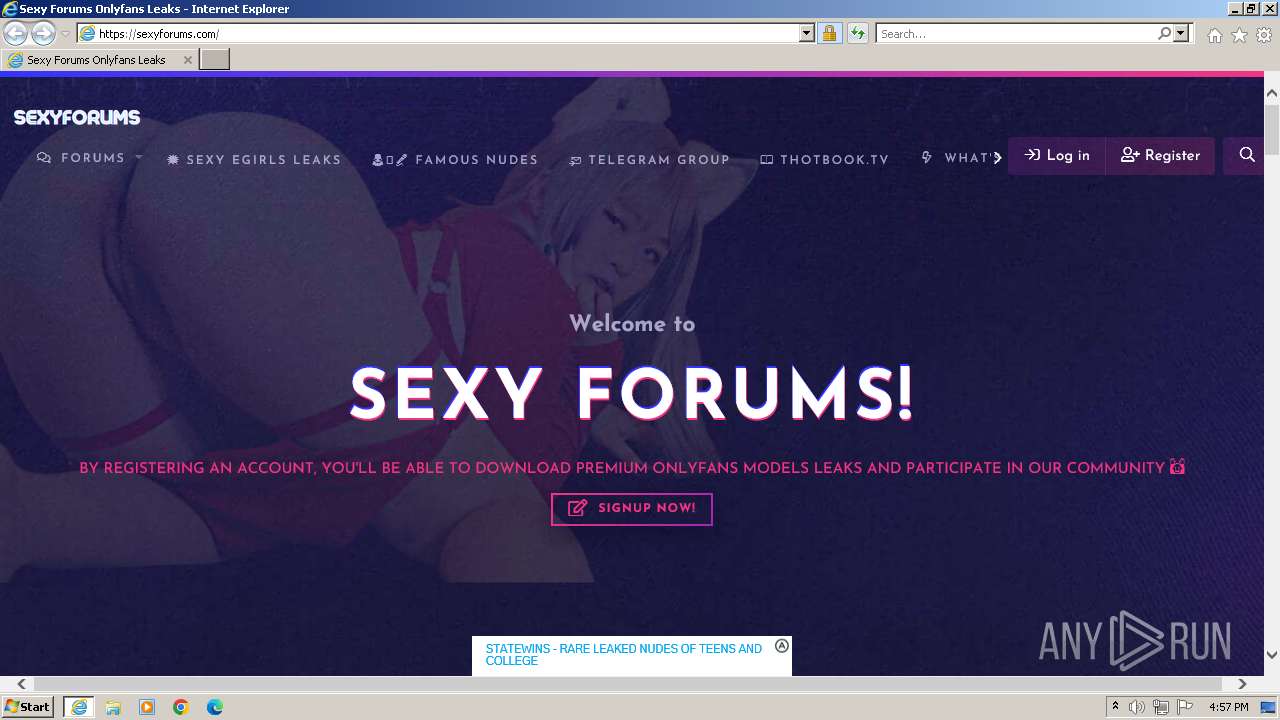
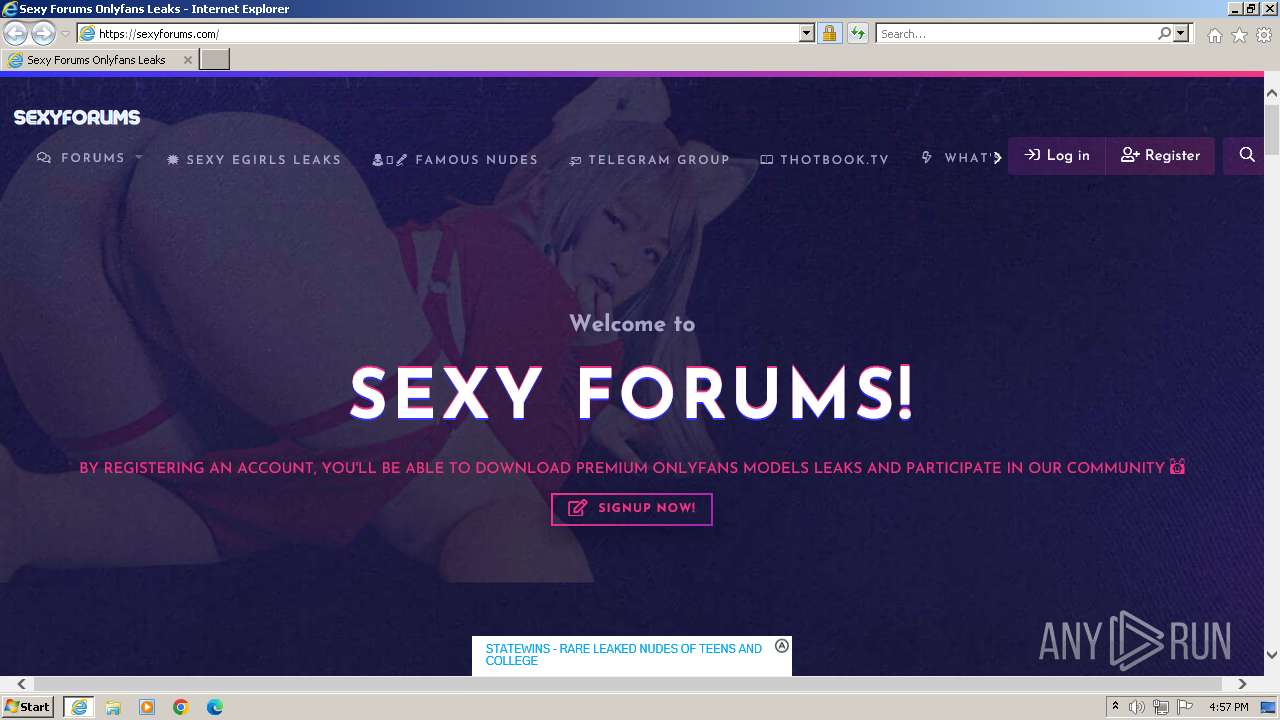
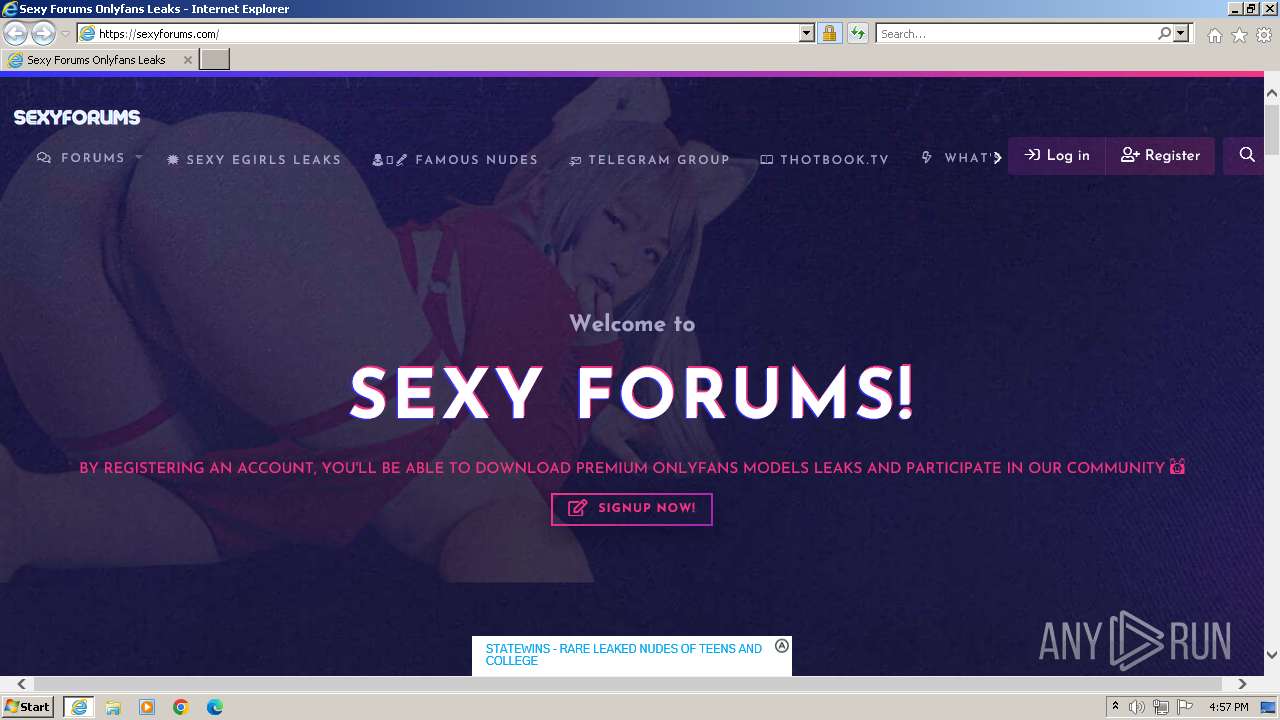
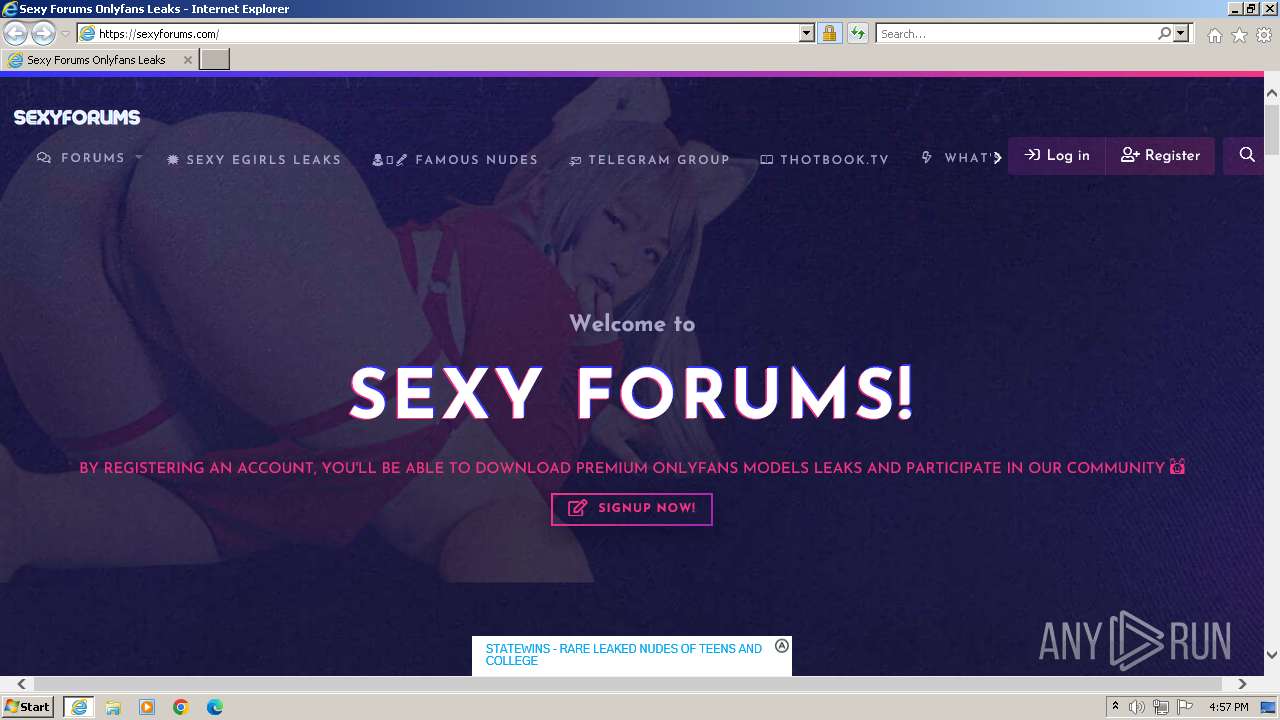
| URL: | Sexyforums.com |
| Full analysis: | https://app.any.run/tasks/1c66efd0-0772-4f97-abfb-2c4d2a760f46 |
| Verdict: | Malicious activity |
| Analysis date: | June 13, 2024, 15:56:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | B65FB19BF3345346C639178E7C1C29DC |
| SHA1: | C56F79AB0C86BB44C047181DA13313F6F3E0ACB3 |
| SHA256: | 3108E8CD19AFADCAC3D54778F283112B072734A31025AAD9F416FEBB6895940D |
| SSDEEP: | 3:eFuTn:cyn |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 3984)
Reads the computer name
- wmpnscfg.exe (PID: 1284)
Checks supported languages
- wmpnscfg.exe (PID: 1284)
Manual execution by a user
- wmpnscfg.exe (PID: 1284)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
35
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1284 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3984 | "C:\Program Files\Internet Explorer\iexplore.exe" "Sexyforums.com" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 4040 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3984 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
19 950
Read events
19 829
Write events
87
Delete events
34
Modification events
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31112618 | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31112618 | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
54
Text files
53
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4040 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\preamble.min[1].js | binary | |
MD5:387F790DF3B04817B3B499539218A32F | SHA256:F8F0D5E29E4408E8ECDCCEE5E73A185566774F71C7F440CC50AD5C647B127CE3 | |||
| 4040 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\OBR40UQO.htm | html | |
MD5:FF6BDB6F50B37FC2855BDC0812659A5A | SHA256:4BCCE45E2B45958244DBC6C5EE197BD9D95234C588586974CD6A33FEED361A99 | |||
| 4040 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\defaultReaction.min[1].js | text | |
MD5:296FC1FA3117230953F66EC6F13773C9 | SHA256:2E4B29279885FE7563561F27B9DA11AC677061A51B27C9DC5CF1A380373A6CAF | |||
| 4040 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\core.min[1].js | binary | |
MD5:1F593C87A1B48503E6A52B91A1CD5A5C | SHA256:688DD33ED28D8089F3B559839052791CADFCE9FA46F15DC39D8AFBF0F5F4EB57 | |||
| 4040 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\nut[1].png | image | |
MD5:DB6430974BD713C3FAC129210ADC72A2 | SHA256:A67CEB00D317A65E35EE5AA01886DB67FE2AE72D7A3B9F0FE30DA3A7F32A4A63 | |||
| 4040 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\TYX336G5.htm | html | |
MD5:0104C301C5E02BD6148B8703D19B3A73 | SHA256:446A6087825FA73EADB045E5A2E9E2ADF7DF241B571228187728191D961DDA1F | |||
| 4040 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\SexyForums1[1].png | image | |
MD5:7159195DAEED044A5D9D2950D72B1C70 | SHA256:475AAEE454A0DB0DA98F3060D49C1CCE03677462CFA2494C5840EA205F902A60 | |||
| 4040 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:6D6832E66C2159BFE39E615B5B37A39E | SHA256:D0D21D56F77DEA927B2814ECFC1536A00A5D72D353A2AD559037FF7942EC7821 | |||
| 4040 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\1000041735[1].jpg | image | |
MD5:8A5640562D4B8DD64461A014B95316C2 | SHA256:9A4E61038713D6697B59DCBE33FC608087BD0BCE172764C4D91078B5B7F57F79 | |||
| 4040 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\css[1].css | text | |
MD5:E7344EC406E3020FBB5695D0F89CFC4D | SHA256:8B2EF27C8F7B6AD4927ECBB0618911D47B4AF2424B91935EDDDB8129442BA1CD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
88
DNS requests
42
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4040 | iexplore.exe | GET | 301 | 172.67.138.143:80 | http://sexyforums.com/ | unknown | — | — | unknown |
4040 | iexplore.exe | GET | 304 | 2.19.126.137:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0eb42db1385d6a0b | unknown | — | — | unknown |
4040 | iexplore.exe | GET | 200 | 2.19.126.137:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?9061d5aa6d0ed04e | unknown | — | — | unknown |
4040 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | — | — | unknown |
4040 | iexplore.exe | GET | 200 | 216.58.212.163:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | unknown |
4040 | iexplore.exe | GET | 200 | 2.19.126.163:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?0950bbb8847fa8c4 | unknown | — | — | unknown |
4040 | iexplore.exe | GET | 200 | 2.19.105.18:80 | http://x1.c.lencr.org/ | unknown | — | — | unknown |
4040 | iexplore.exe | GET | 200 | 216.58.212.163:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | — | — | unknown |
4040 | iexplore.exe | GET | 200 | 216.58.212.163:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | unknown |
4040 | iexplore.exe | GET | 200 | 2.16.241.8:80 | http://r10.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRpD%2BQVZ%2B1vf7U0RGQGBm8JZwdxcgQUdKR2KRcYVIUxN75n5gZYwLzFBXICEgMcfLVQc1c929GWjgQVi4cb5w%3D%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4040 | iexplore.exe | 172.67.138.143:80 | sexyforums.com | CLOUDFLARENET | US | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4040 | iexplore.exe | 172.67.138.143:443 | sexyforums.com | CLOUDFLARENET | US | unknown |
4040 | iexplore.exe | 2.19.126.137:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
4040 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4040 | iexplore.exe | 142.250.186.74:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
4040 | iexplore.exe | 104.21.5.179:443 | ip1.imgporn.to | CLOUDFLARENET | — | unknown |
4040 | iexplore.exe | 88.208.22.2:443 | bobabillydirect.org | DataWeb Global Group B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
sexyforums.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
ip1.imgporn.to |
| unknown |
bobabillydirect.org |
| unknown |
cdn.tsyndicate.com |
| unknown |
linktr.ee |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |