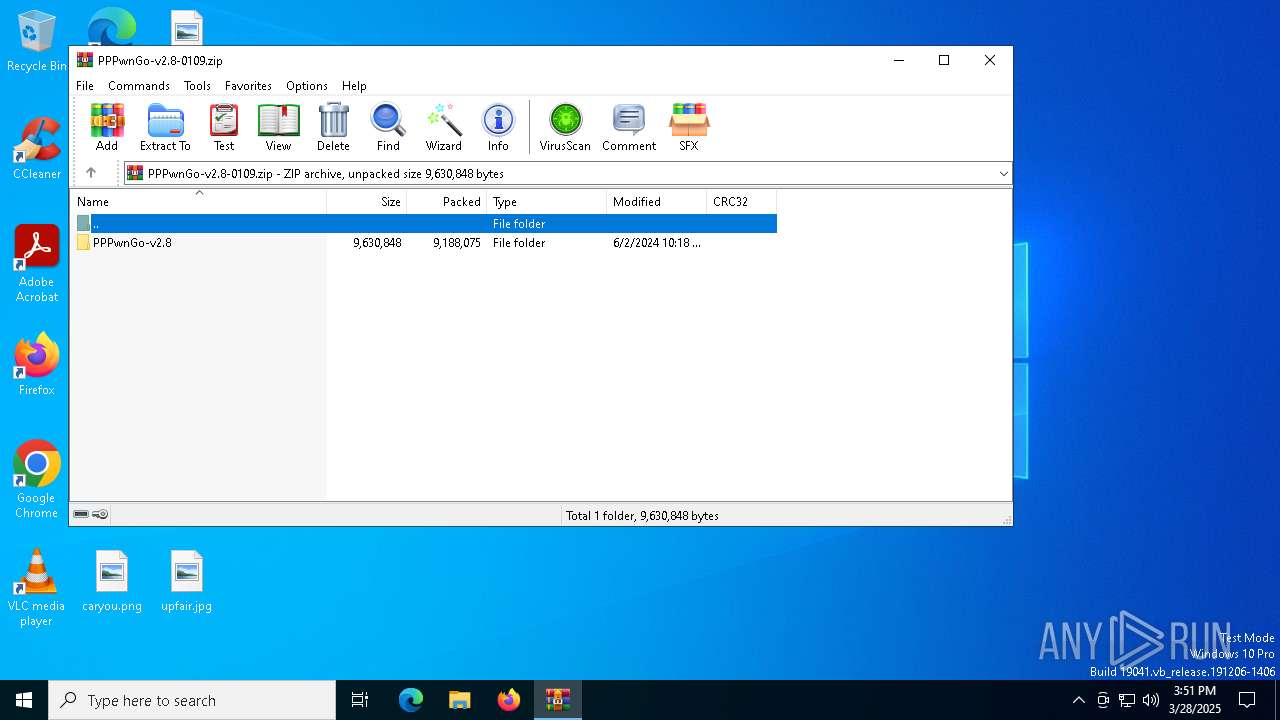
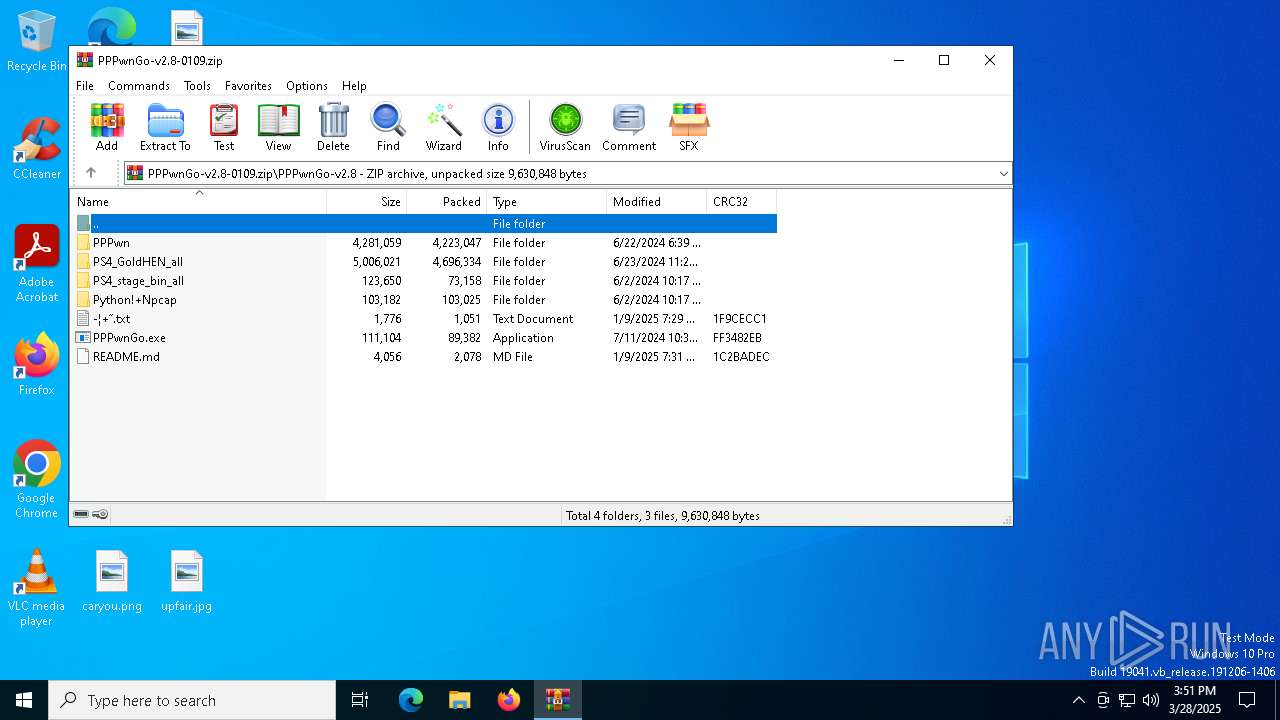
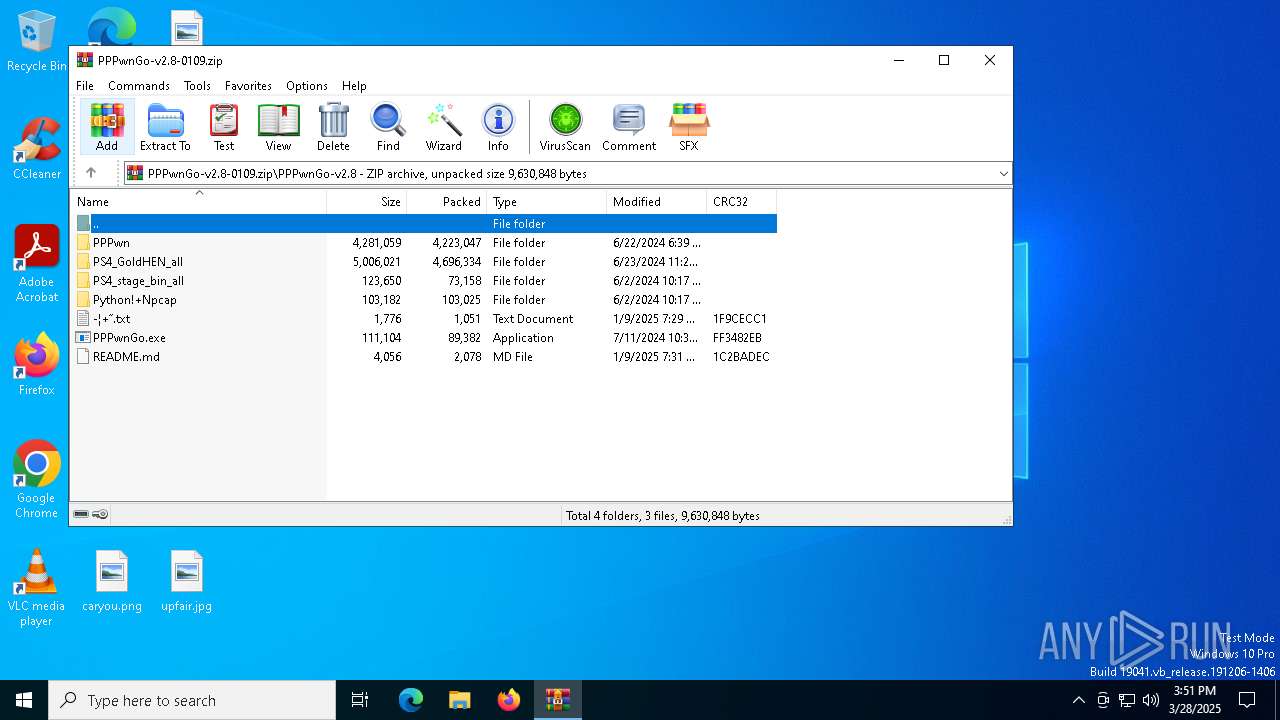
| download: | /PSGO/PPPwnGo/releases/download/v2.8-20250109/PPPwnGo-v2.8-0109.zip |
| Full analysis: | https://app.any.run/tasks/6c3b9936-f5a0-4677-a338-c36a134a85e4 |
| Verdict: | Malicious activity |
| Analysis date: | March 28, 2025, 15:51:17 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 4AC3233D138F47E255F57B900A078789 |
| SHA1: | 3FCF987492D775618116C047BA2F4D9E3196A890 |
| SHA256: | 310583FBB1EFA90CF3CA4F499251496F59F43E3F1425C7ECF814E06F437BAD1E |
| SSDEEP: | 98304:Uc8Wi0/pIhwQsKVgcc8Wi0/pIhgQsKVdPUQsKVCc8Wi0/pIhqQsKVCc8Wi0/pIh8:uJP4FWuFtzRcuhj+pZ0 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 732)
SUSPICIOUS
Starts CMD.EXE for commands execution
- PPPwnGo.exe (PID: 3300)
Suspicious use of NETSH.EXE
- cmd.exe (PID: 2772)
- cmd.exe (PID: 5328)
INFO
Manual execution by a user
- PPPwnGo.exe (PID: 1052)
- PPPwnGo.exe (PID: 3300)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 732)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:01:09 15:31:44 |
| ZipCRC: | 0x1c2badec |
| ZipCompressedSize: | 2078 |
| ZipUncompressedSize: | 4056 |
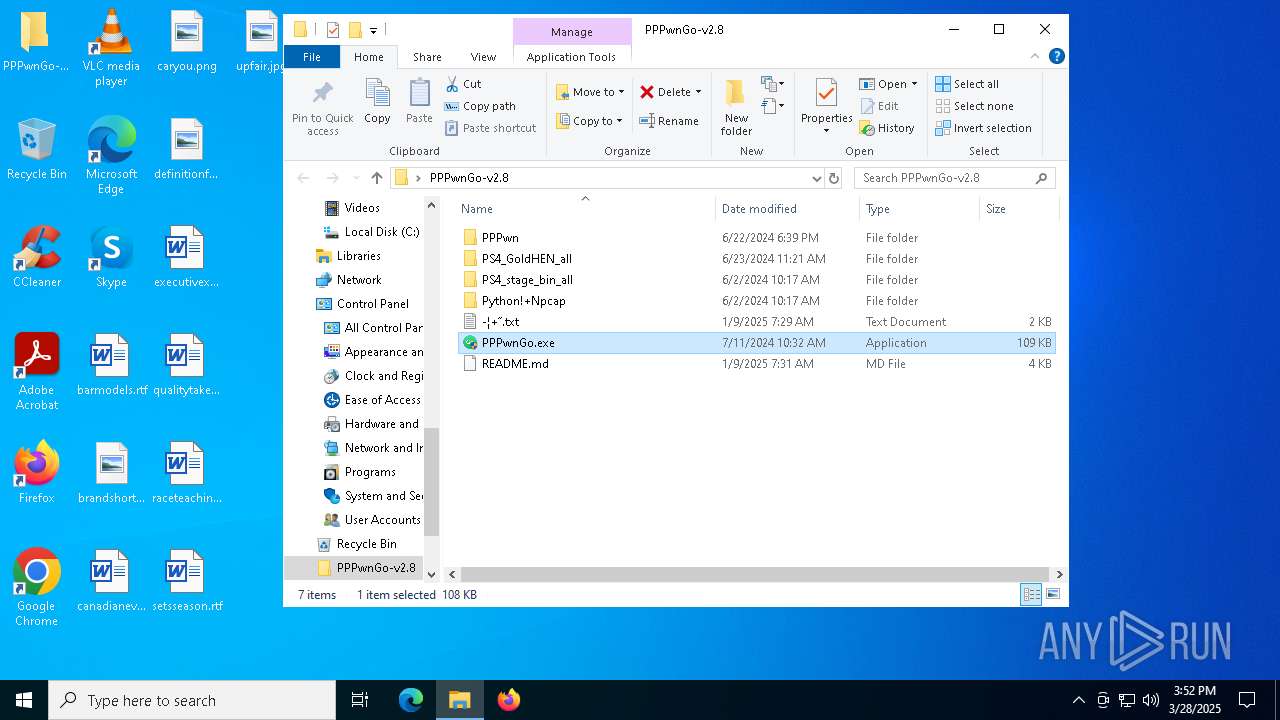
| ZipFileName: | PPPwnGo-v2.8/README.md |
Total processes
147
Monitored processes
15
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\PPPwnGo-v2.8-0109.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
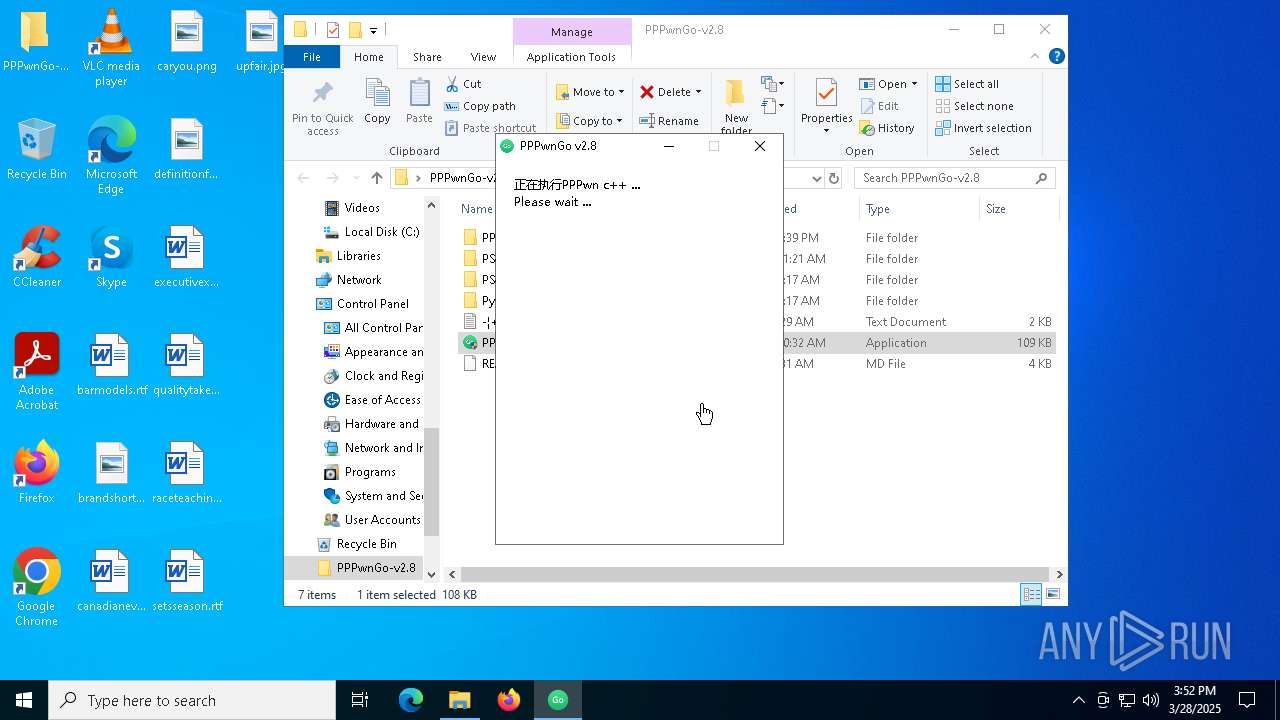
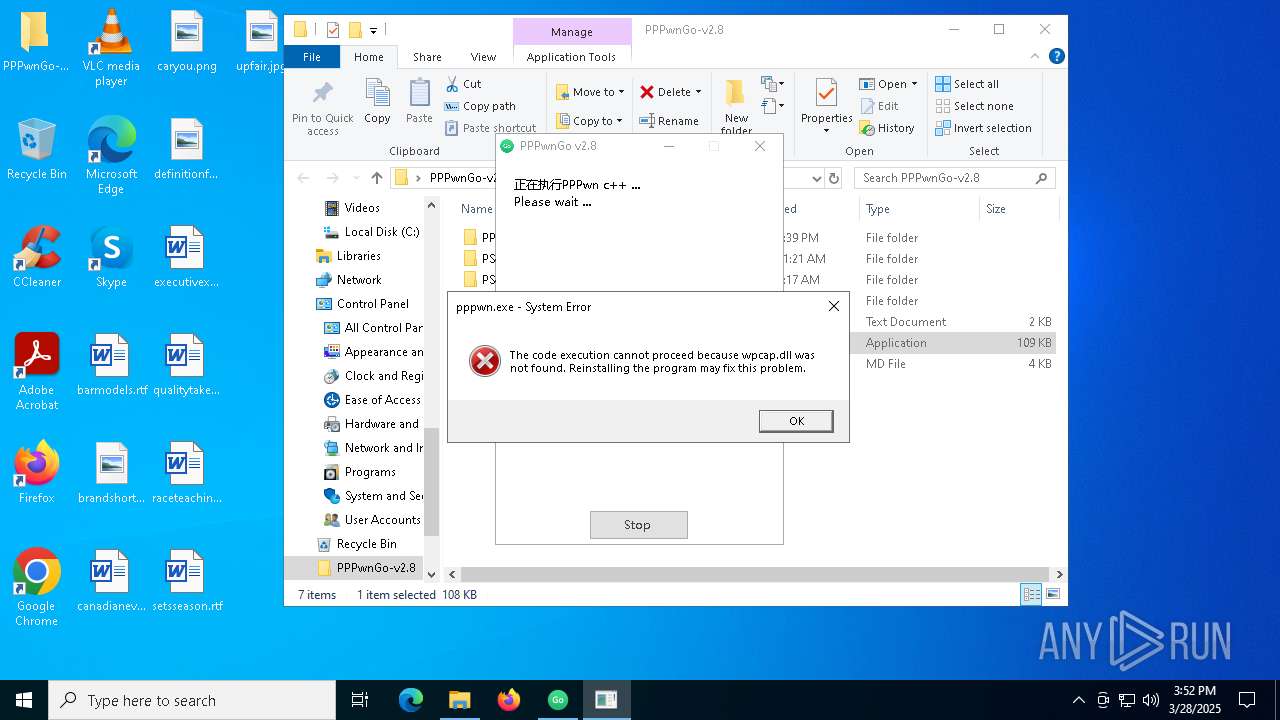
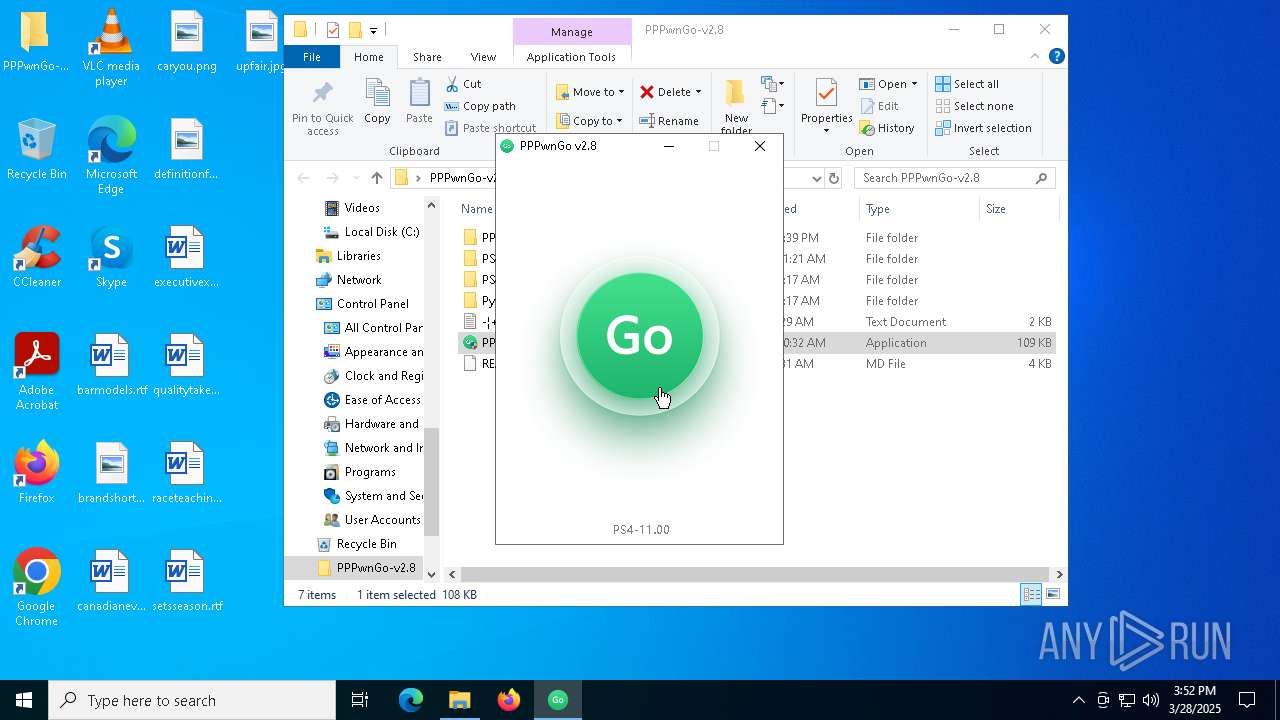
| 1052 | "C:\Users\admin\Desktop\PPPwnGo-v2.8\PPPwnGo.exe" | C:\Users\admin\Desktop\PPPwnGo-v2.8\PPPwnGo.exe | — | explorer.exe | |||||||||||
User: admin Company: PSGO Integrity Level: MEDIUM Description: PPPwnGo Exit code: 3221226540 Version: 2.7.0.0 Modules
| |||||||||||||||
| 2420 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2516 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2772 | "cmd.exe" /c netsh interface set interface "Connection" admin=disable | C:\Windows\System32\cmd.exe | — | PPPwnGo.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
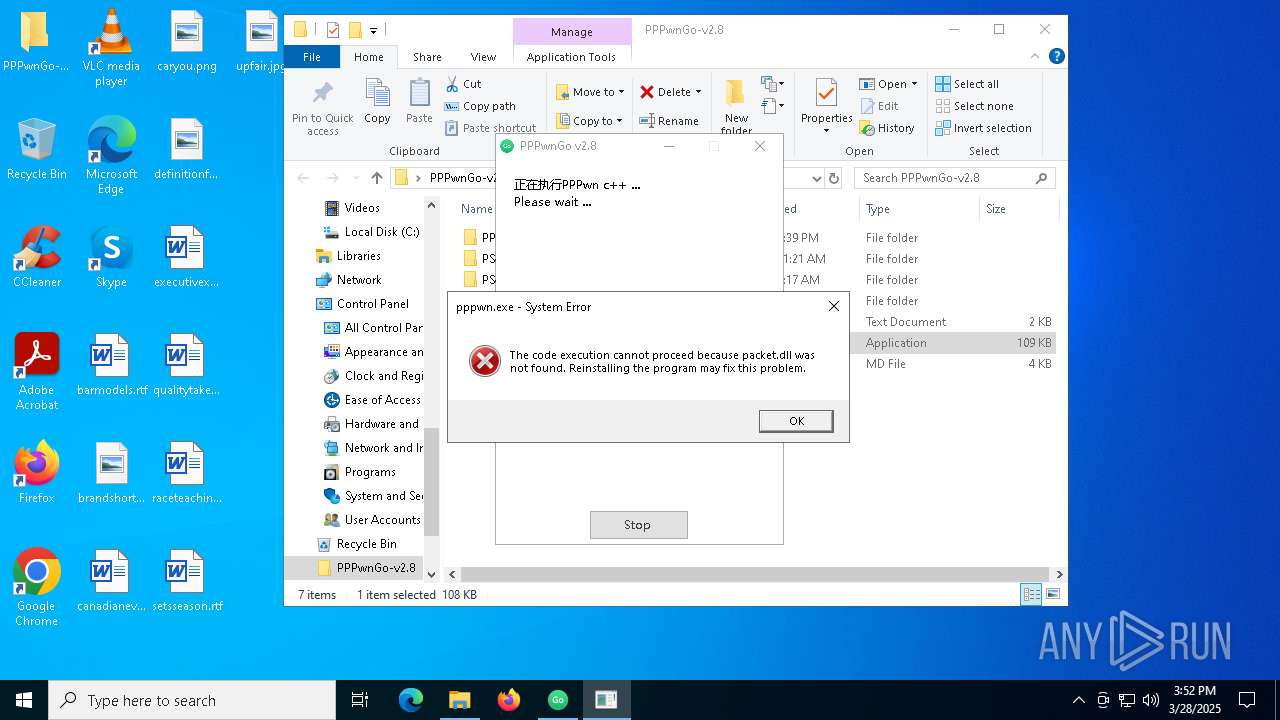
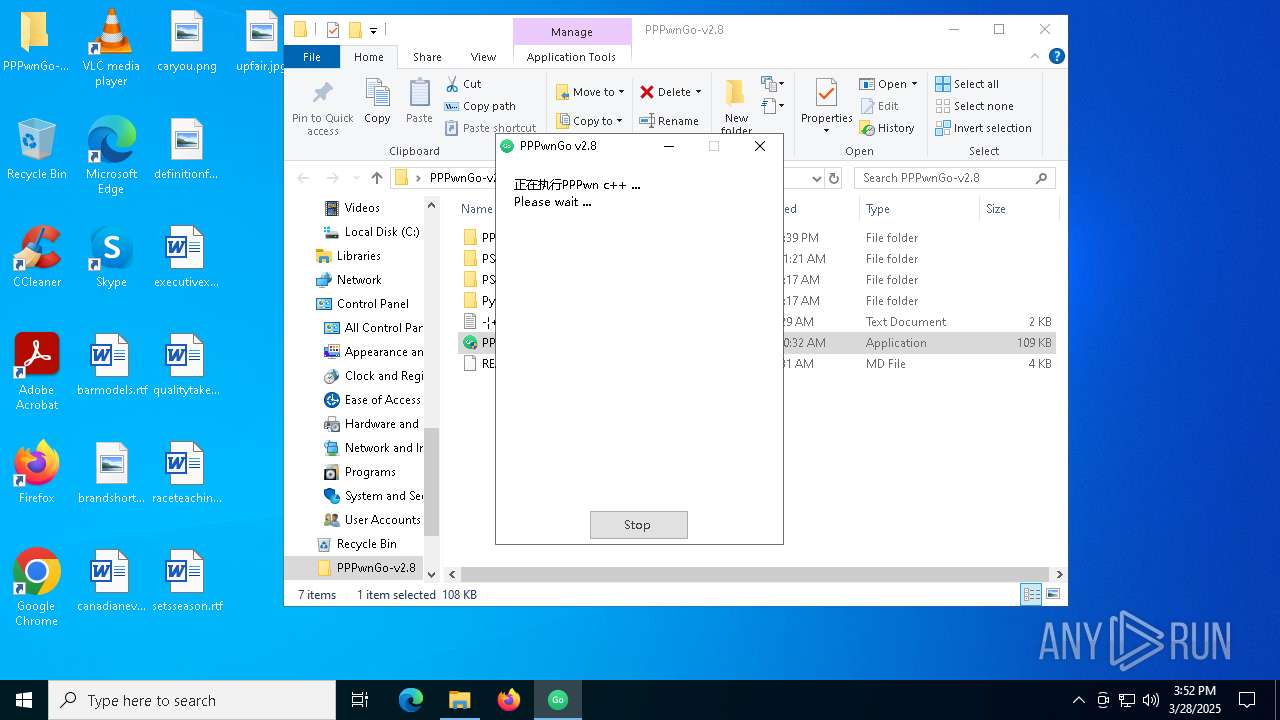
| 3300 | "C:\Users\admin\Desktop\PPPwnGo-v2.8\PPPwnGo.exe" | C:\Users\admin\Desktop\PPPwnGo-v2.8\PPPwnGo.exe | explorer.exe | ||||||||||||
User: admin Company: PSGO Integrity Level: HIGH Description: PPPwnGo Exit code: 0 Version: 2.7.0.0 Modules
| |||||||||||||||
| 3896 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4300 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | pppwn.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5024 | "C:\Users\admin\Desktop\PPPwnGo-v2.8\PPPwn\CPP\pppwn.exe" --interface \Device\NPF_{D950CA8D-448E-4CA2-89DE-A65A1AC2B2A6} --fw 1100 --stage1 PS4_stage_bin_all/PS4-11.00/stage1/stage1.bin --stage2 PS4_stage_bin_all/PS4-11.00/stage2/stage2.bin --timeout 0 --wait-after-pin 1 --groom-delay 4 --buffer-size 0 --auto-retry --url 0.0.0.0:7796 | C:\Users\admin\Desktop\PPPwnGo-v2.8\PPPwn\CPP\pppwn.exe | — | PPPwnGo.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225781 Modules
| |||||||||||||||
Total events
6 009
Read events
5 975
Write events
21
Delete events
13
Modification events
| (PID) Process: | (732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\PPPwnGo-v2.8-0109.zip | |||
| (PID) Process: | (732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\ext | |||
| (PID) Process: | (732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
Executable files
5
Suspicious files
80
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 732 | WinRAR.exe | C:\Users\admin\Desktop\PPPwnGo-v2.8\-¦+˜.txt | text | |
MD5:ED975688CA3AFDB197C3BADFC78AD2A1 | SHA256:6135EF146214F3DCEFB2B3B43D04BAD92C0A41E37F5E770333E60CA95E643B00 | |||
| 732 | WinRAR.exe | C:\Users\admin\Desktop\PPPwnGo-v2.8\PS4_GoldHEN_all\PS4-9.04(VTX)\payload.bin | binary | |
MD5:4C6F0CCC08E5C7D6399D24E7817B7E3F | SHA256:8464315FBFC78ED156815C61764562B7F9188ED982142214B1E3E4511F6AC57D | |||
| 732 | WinRAR.exe | C:\Users\admin\Desktop\PPPwnGo-v2.8\PS4_GoldHEN_all\PS4-9.60\GoldHENv2.4b18\goldhen.bin | binary | |
MD5:78C655DB47C395434715FCE94FA86743 | SHA256:C64FFEFDFEC184E87F48C79100206F13D8D786FA8BDC1E611DFC0713E713358A | |||
| 732 | WinRAR.exe | C:\Users\admin\Desktop\PPPwnGo-v2.8\PS4_GoldHEN_all\Payload-¦+˜readme.txt | text | |
MD5:56812B74F96D715F779FECC5399862FE | SHA256:5B5A57A4EFA88D28E00D889A27571F68418F068CAA25F654EE998D6425D472BD | |||
| 732 | WinRAR.exe | C:\Users\admin\Desktop\PPPwnGo-v2.8\PS4_GoldHEN_all\PS4-9.00\GoldHENv2.4b18.2\goldhen.bin | binary | |
MD5:9CAEB9AFA1E26D80D0E293ADE0446B10 | SHA256:76D9A67E79B3363385DF202BC102760BFA3051444D0101DB90A9BDD5C2F728FB | |||
| 732 | WinRAR.exe | C:\Users\admin\Desktop\PPPwnGo-v2.8\PS4_GoldHEN_all\PS4-9.03(VTX)\payload.bin | binary | |
MD5:7BC8B565A82EDDF7FE70B34311BE86AC | SHA256:60B2444F66F9976A3AB3FDC9F15BA7B83099462850F2D64FBED1FD23AA2E0067 | |||
| 732 | WinRAR.exe | C:\Users\admin\Desktop\PPPwnGo-v2.8\PS4_GoldHEN_all\PS4-10.00\GoldHENv2.4b18\goldhen.bin | binary | |
MD5:78C655DB47C395434715FCE94FA86743 | SHA256:C64FFEFDFEC184E87F48C79100206F13D8D786FA8BDC1E611DFC0713E713358A | |||
| 732 | WinRAR.exe | C:\Users\admin\Desktop\PPPwnGo-v2.8\PS4_GoldHEN_all\GoldHEN vs VTX.png | image | |
MD5:5FABBFF85DB7895BEB2018B66D4C2E5A | SHA256:D5DA308FFE4EF8792792A503192C3E283D27F7B1886F063A705493BD261DC24A | |||
| 732 | WinRAR.exe | C:\Users\admin\Desktop\PPPwnGo-v2.8\PS4_GoldHEN_all\PS4-9.00\GoldHENv2.4b18\goldhen.bin | binary | |
MD5:78C655DB47C395434715FCE94FA86743 | SHA256:C64FFEFDFEC184E87F48C79100206F13D8D786FA8BDC1E611DFC0713E713358A | |||
| 732 | WinRAR.exe | C:\Users\admin\Desktop\PPPwnGo-v2.8\PS4_GoldHEN_all\PS4-10.00\GoldHENv2.4b18.2\goldhen.bin | binary | |
MD5:9CAEB9AFA1E26D80D0E293ADE0446B10 | SHA256:76D9A67E79B3363385DF202BC102760BFA3051444D0101DB90A9BDD5C2F728FB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
23
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4040 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4040 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5728 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3216 | svchost.exe | 172.172.255.218:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5728 | backgroundTaskHost.exe | 20.223.36.55:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |