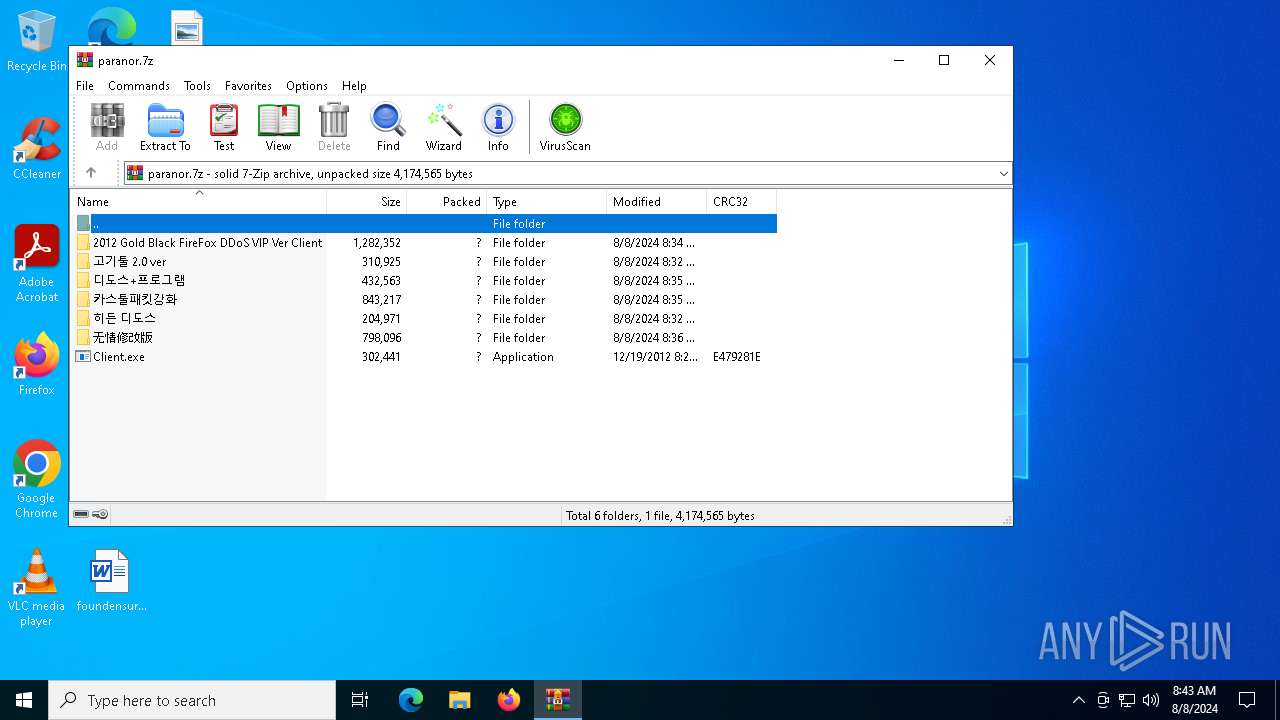
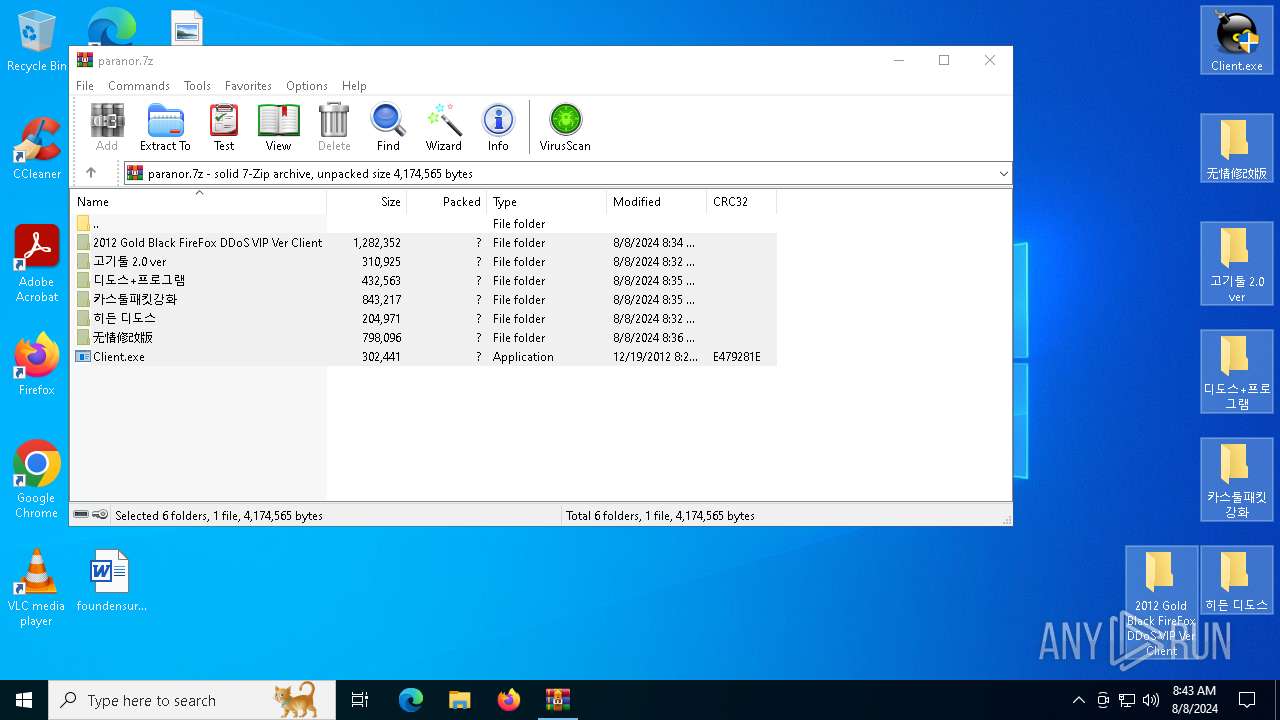
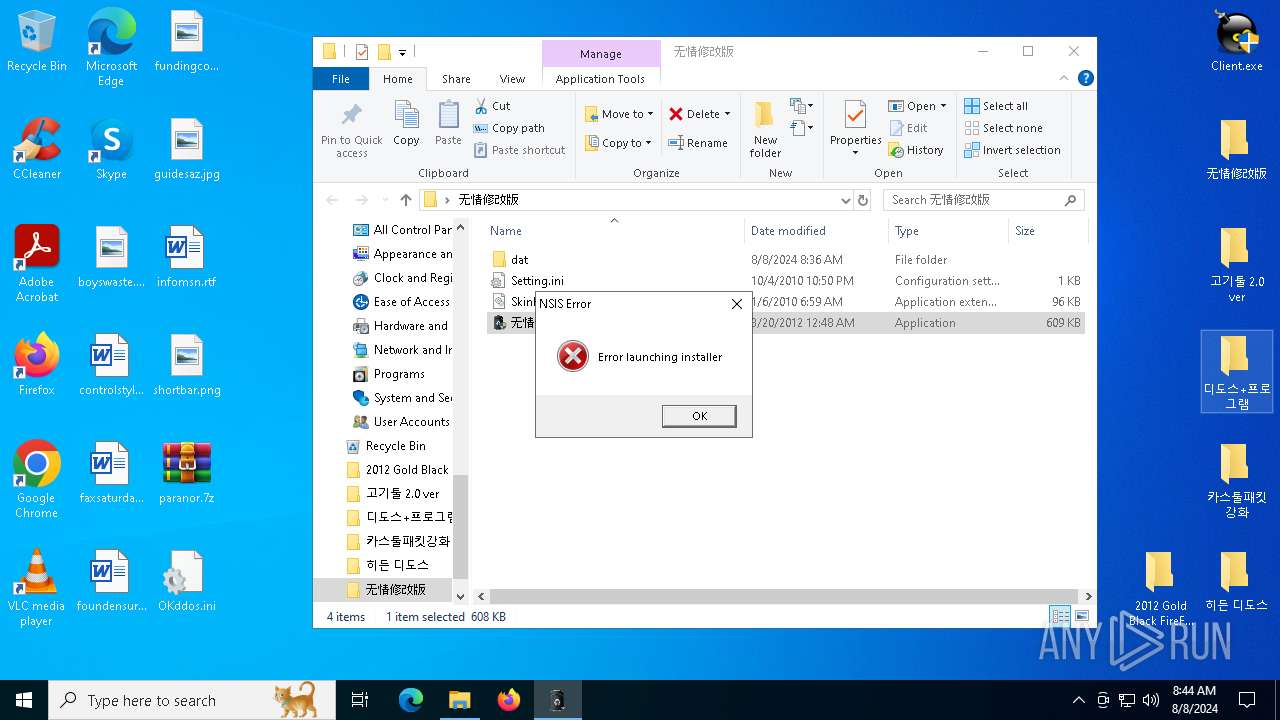
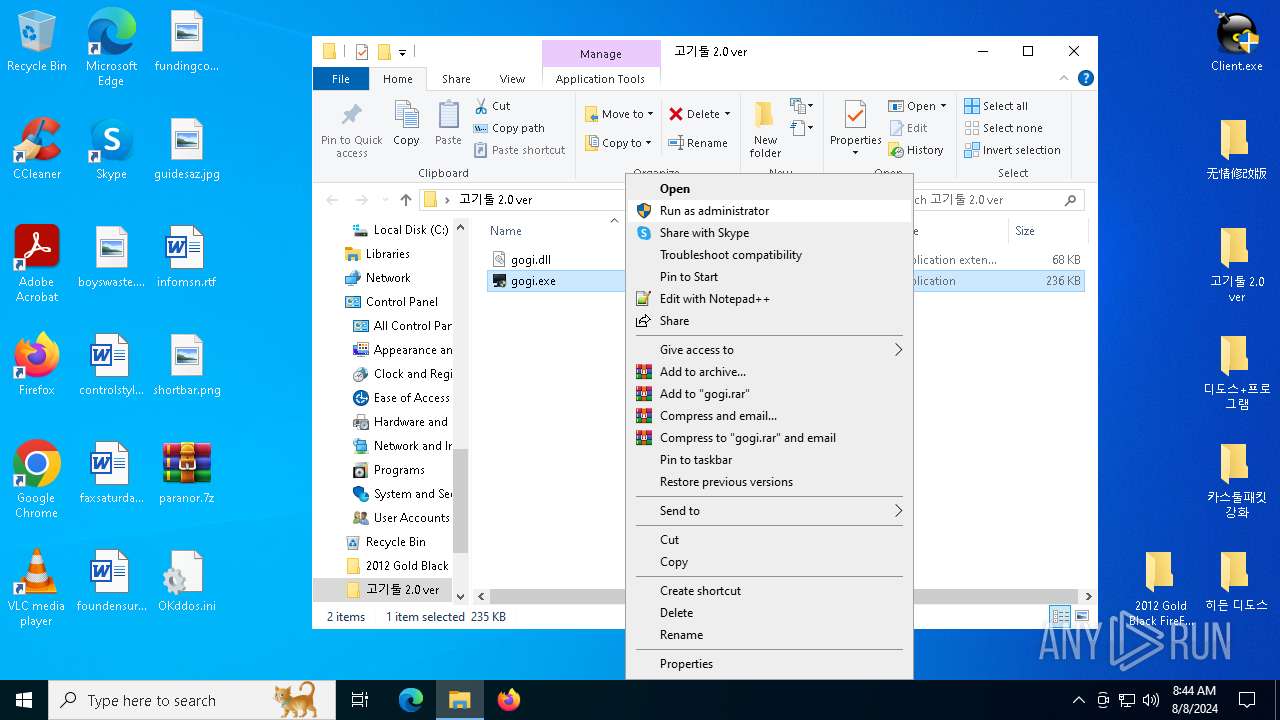
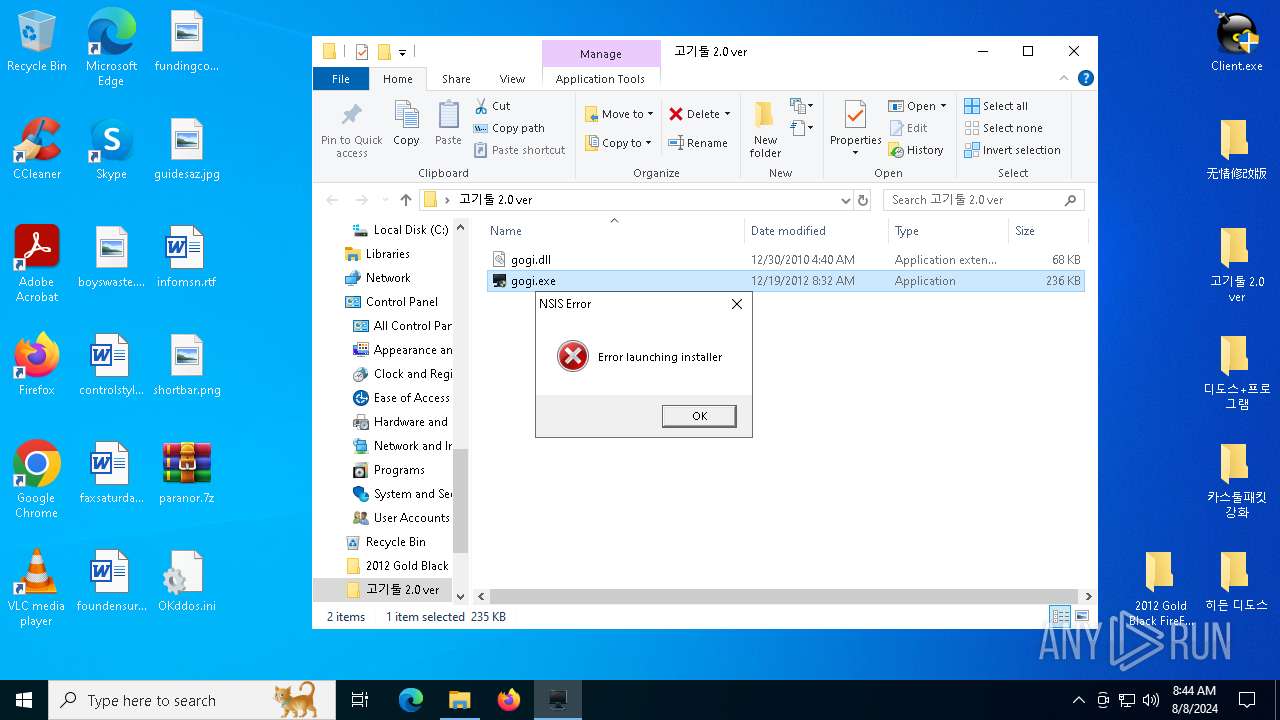
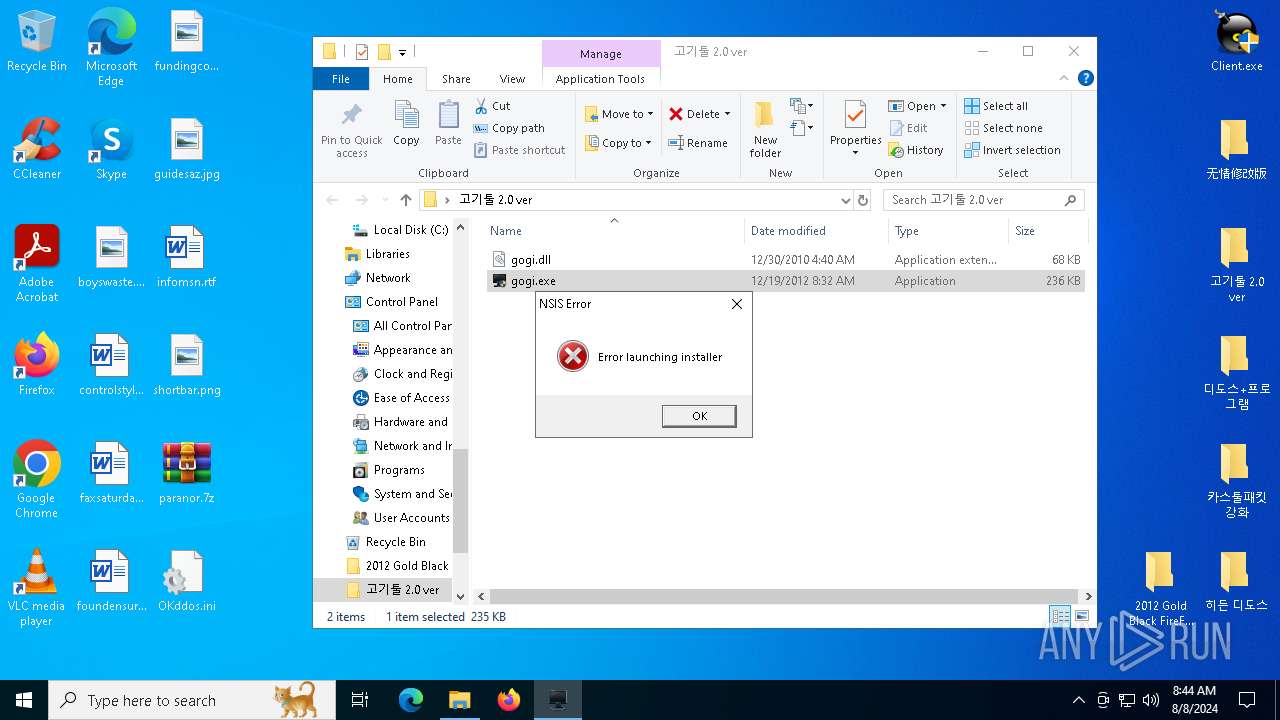
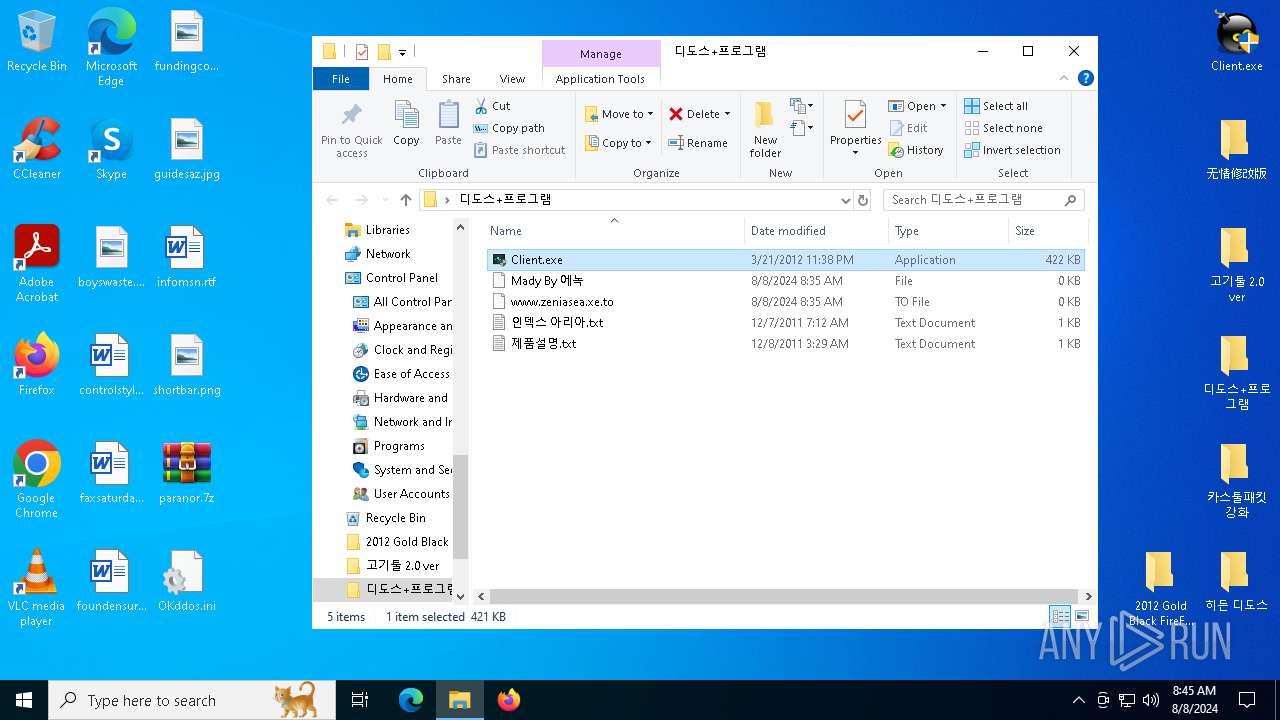
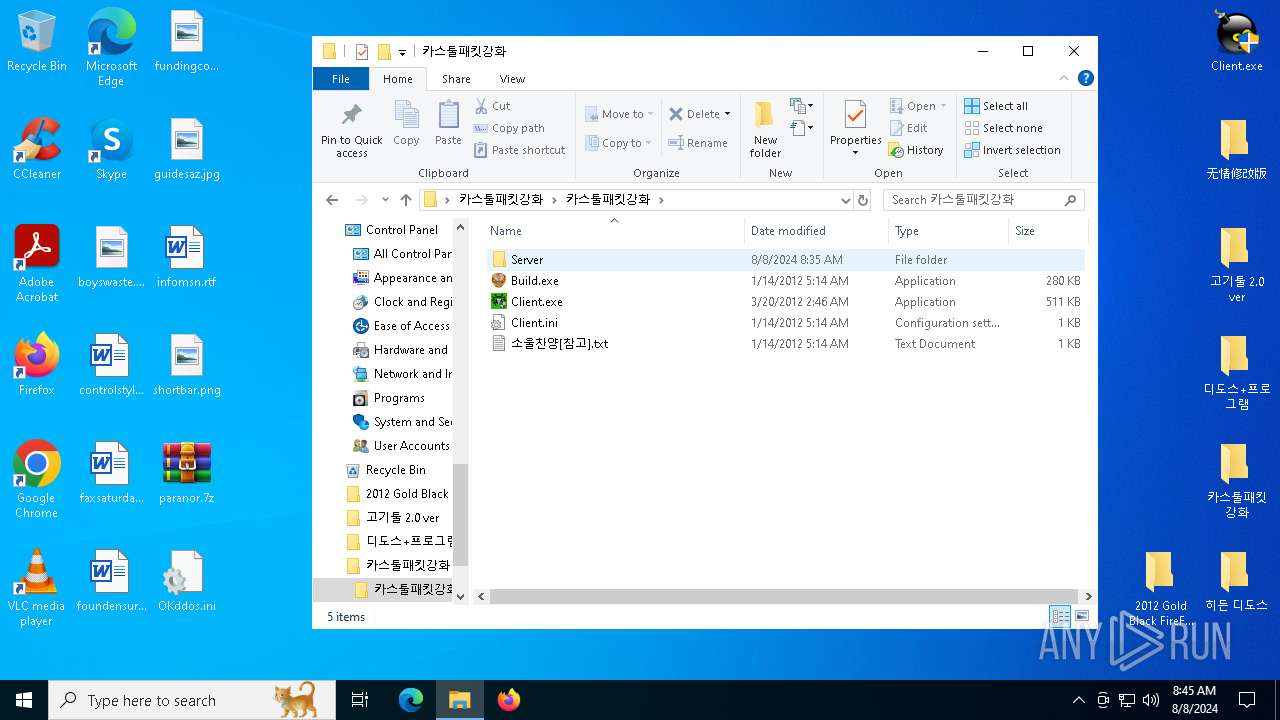
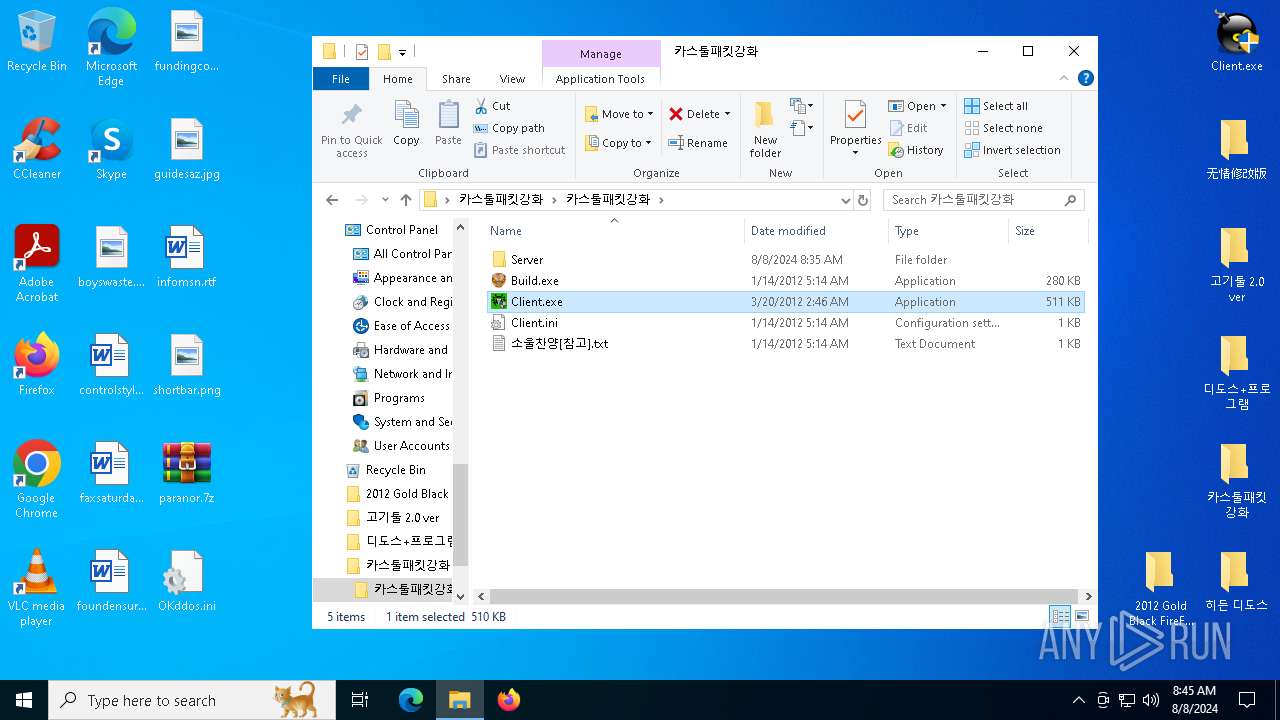
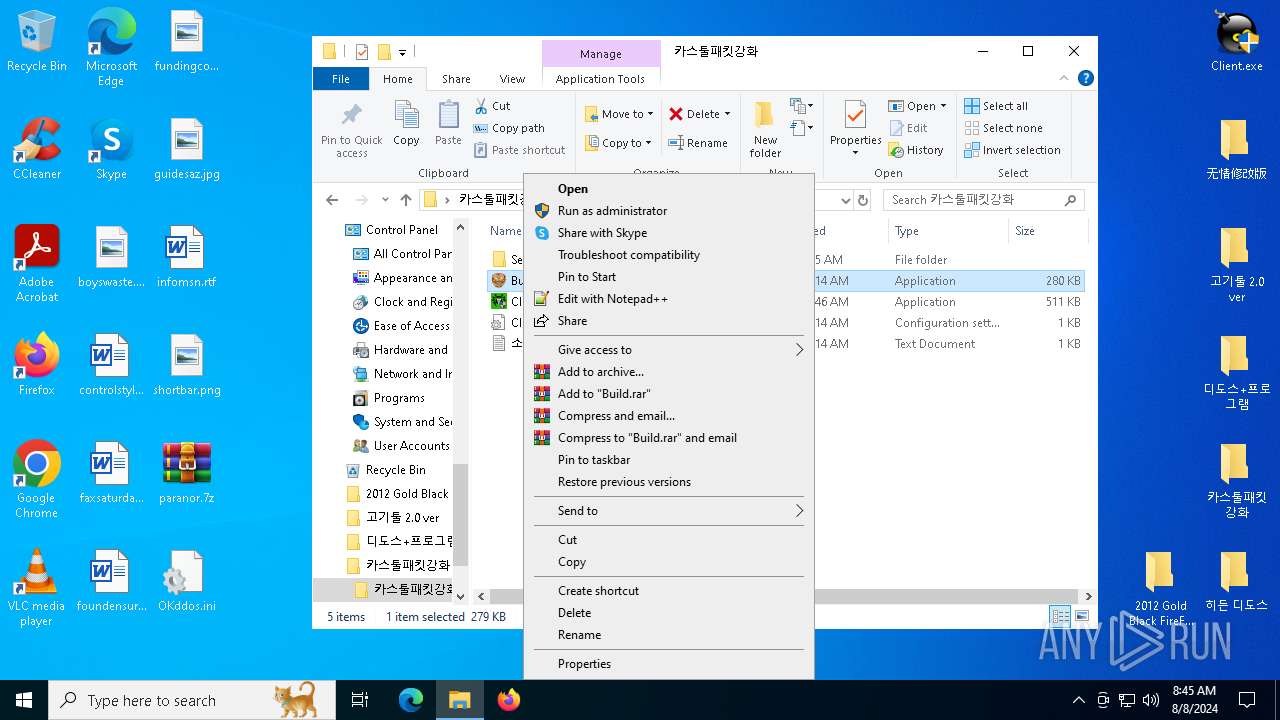
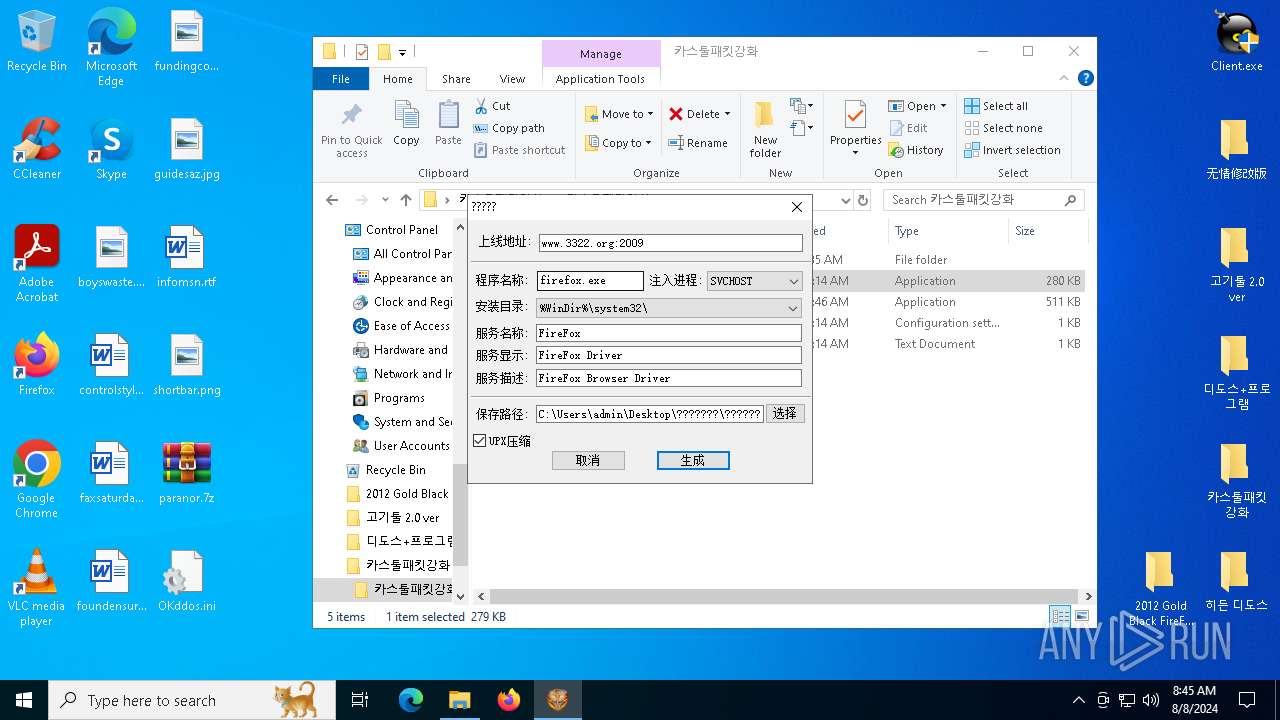
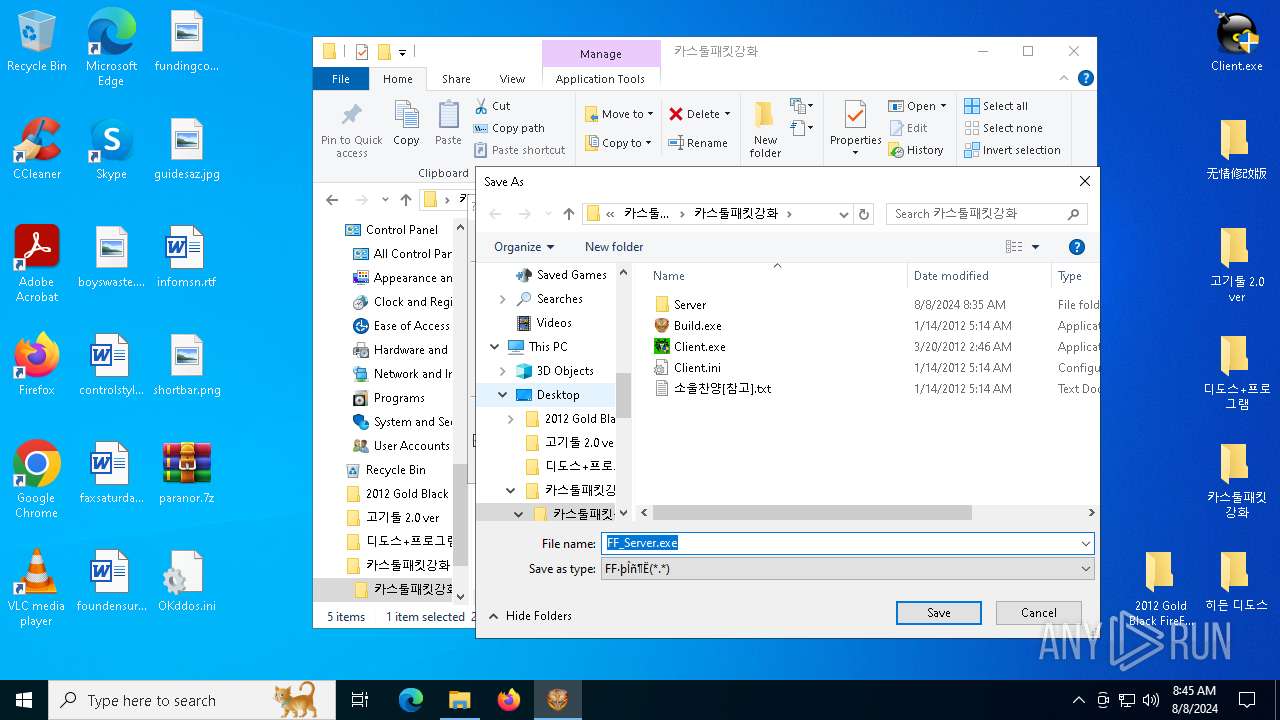
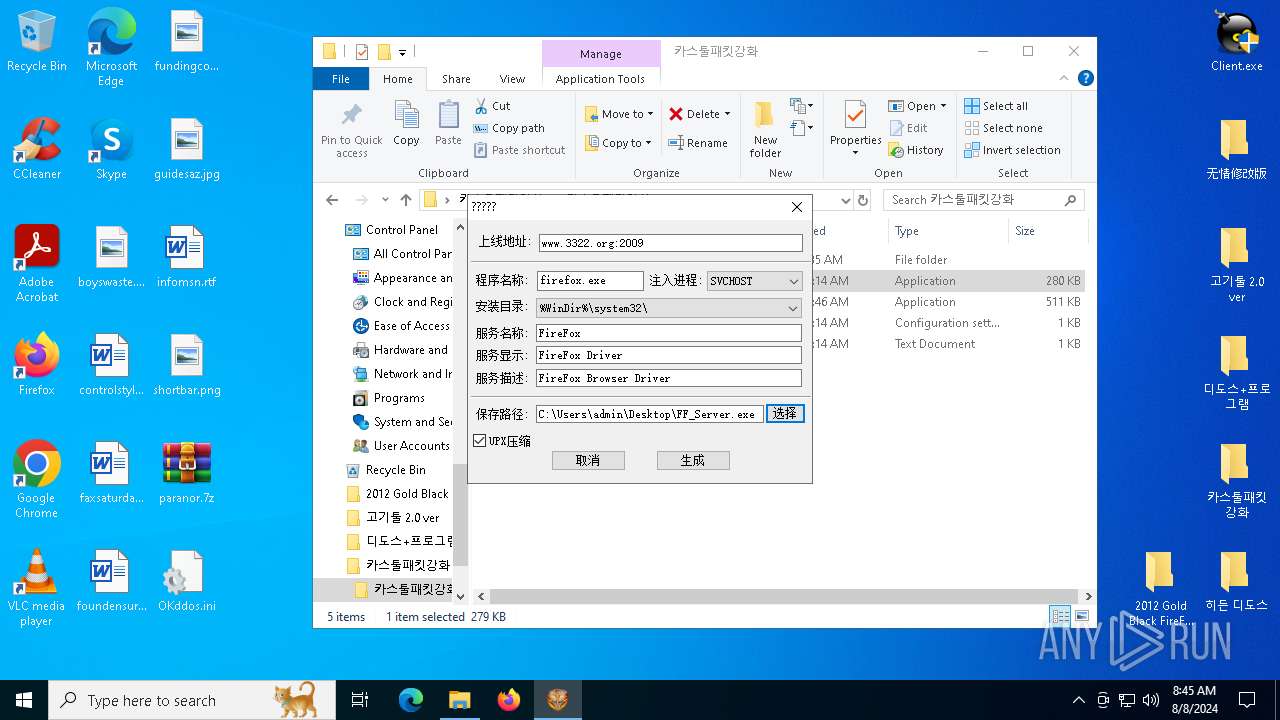
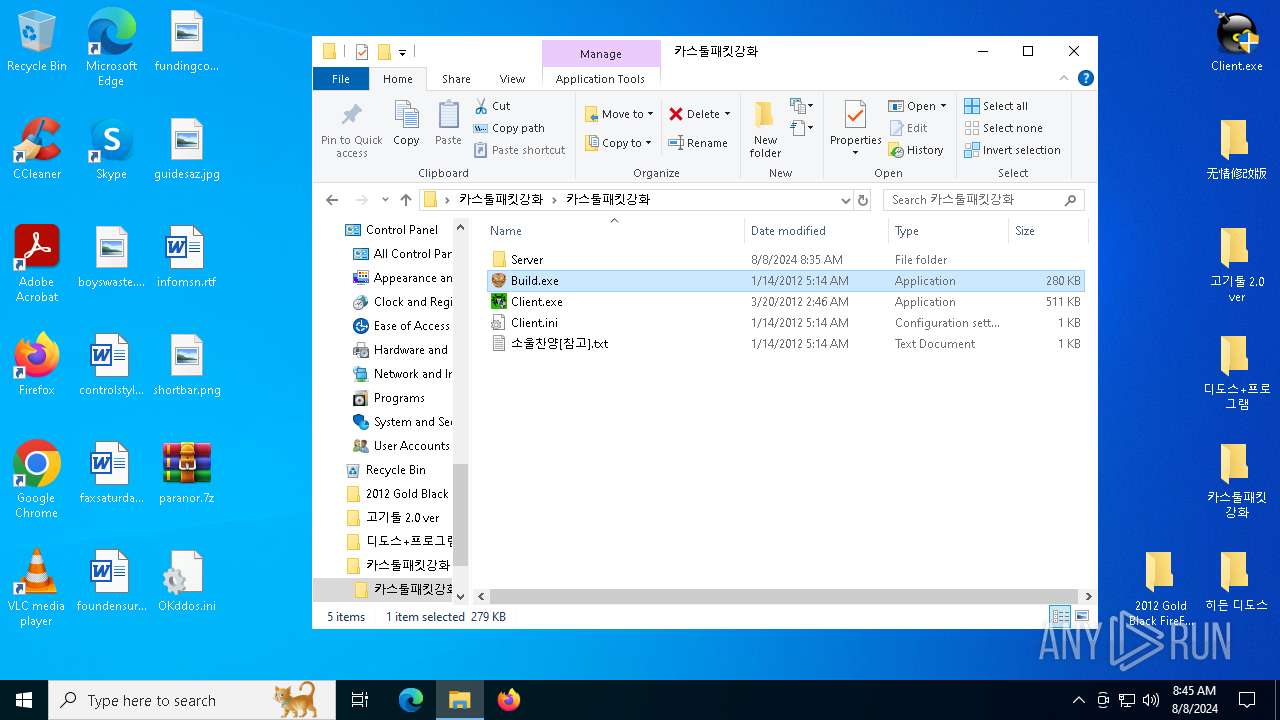
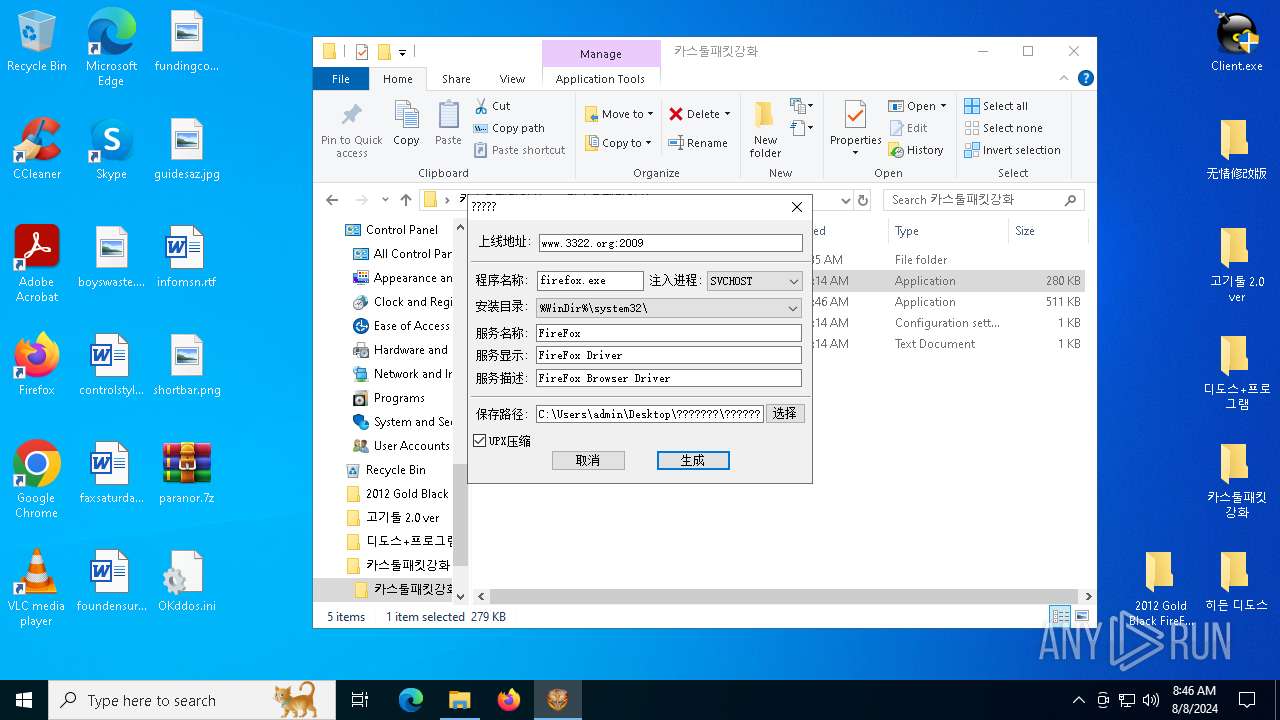
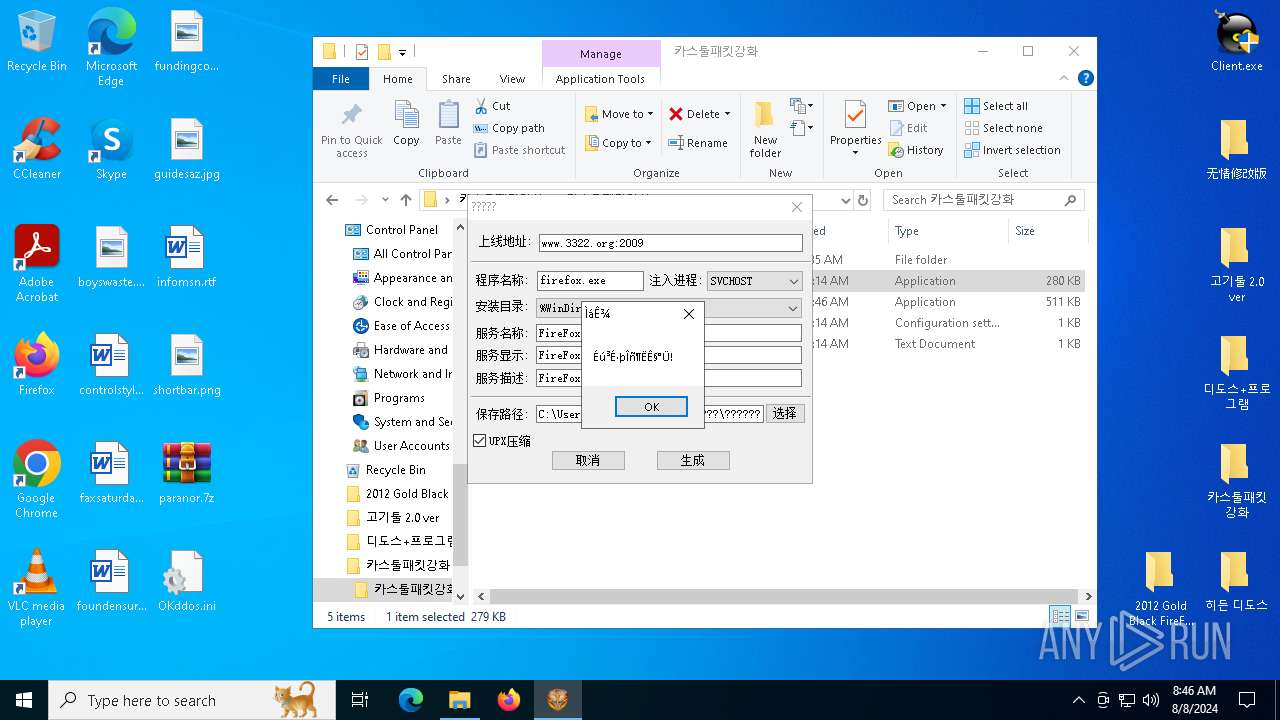
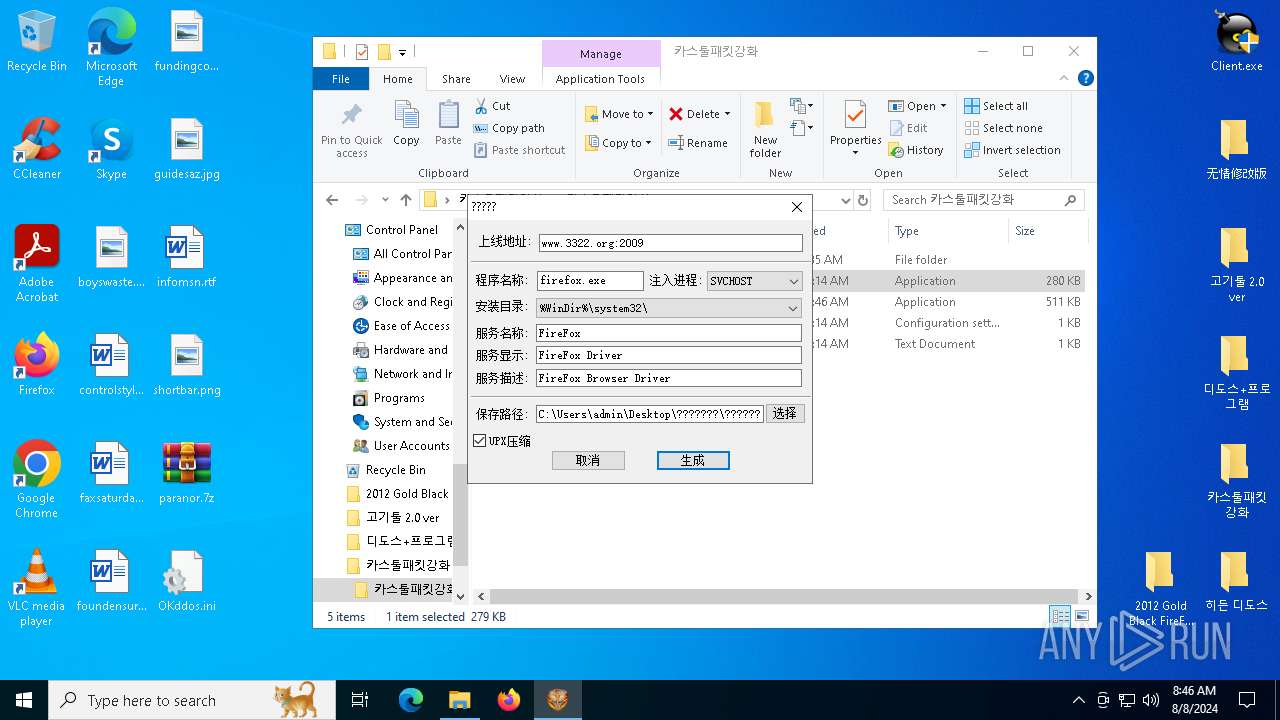
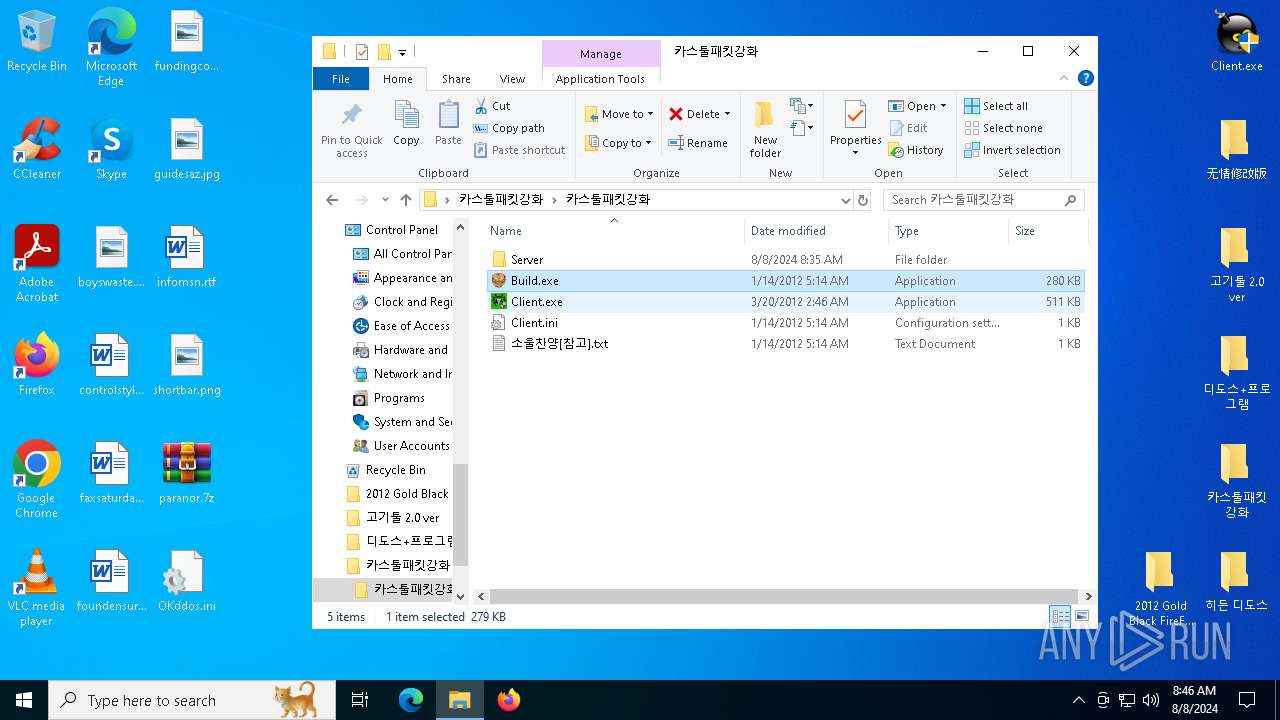
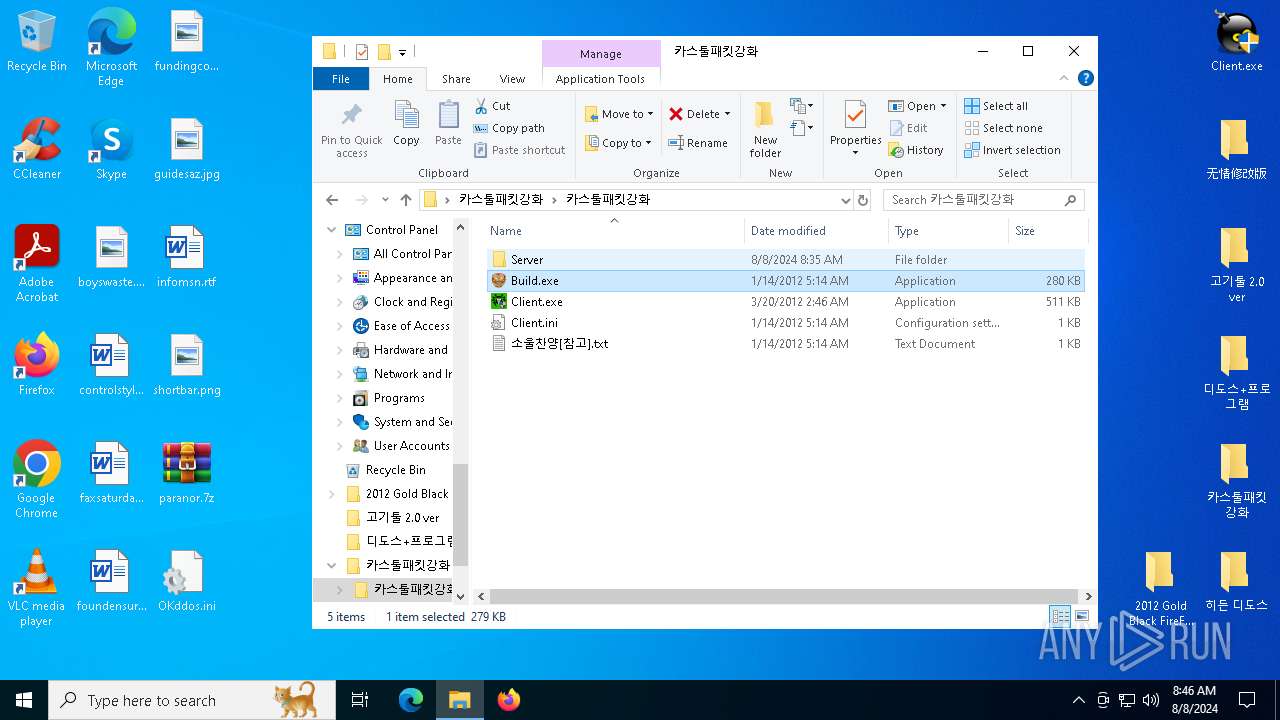
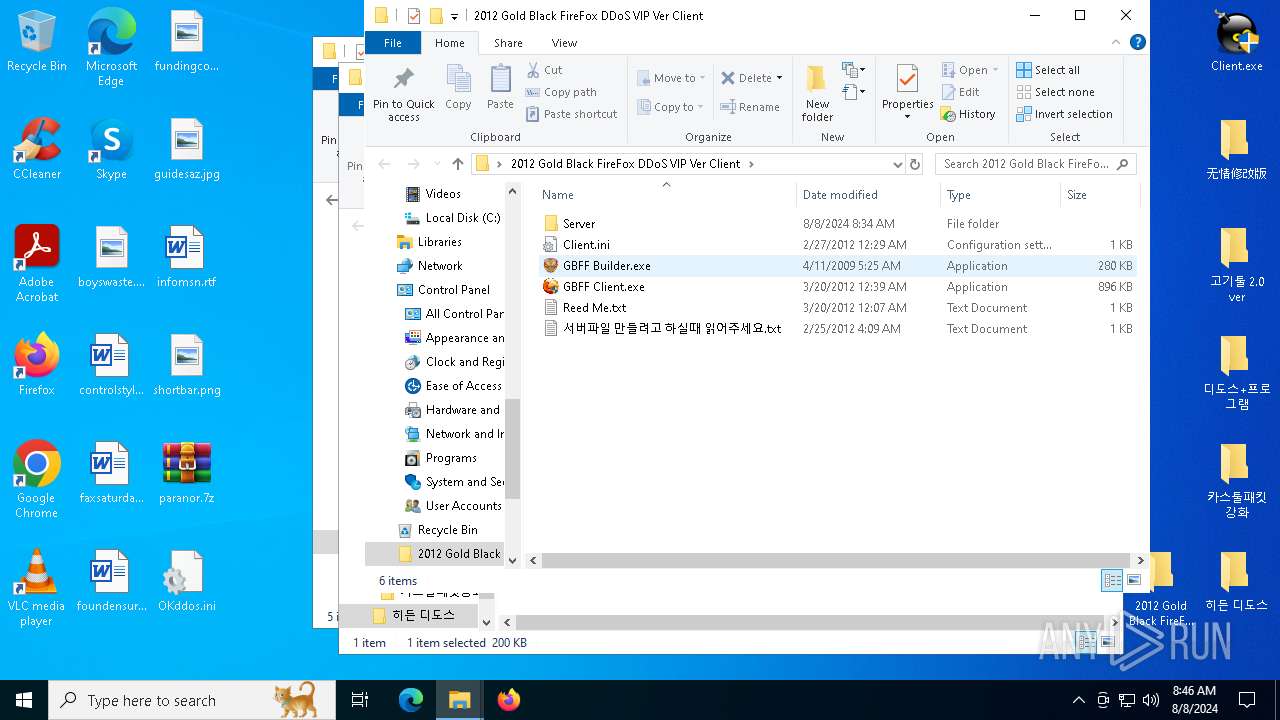
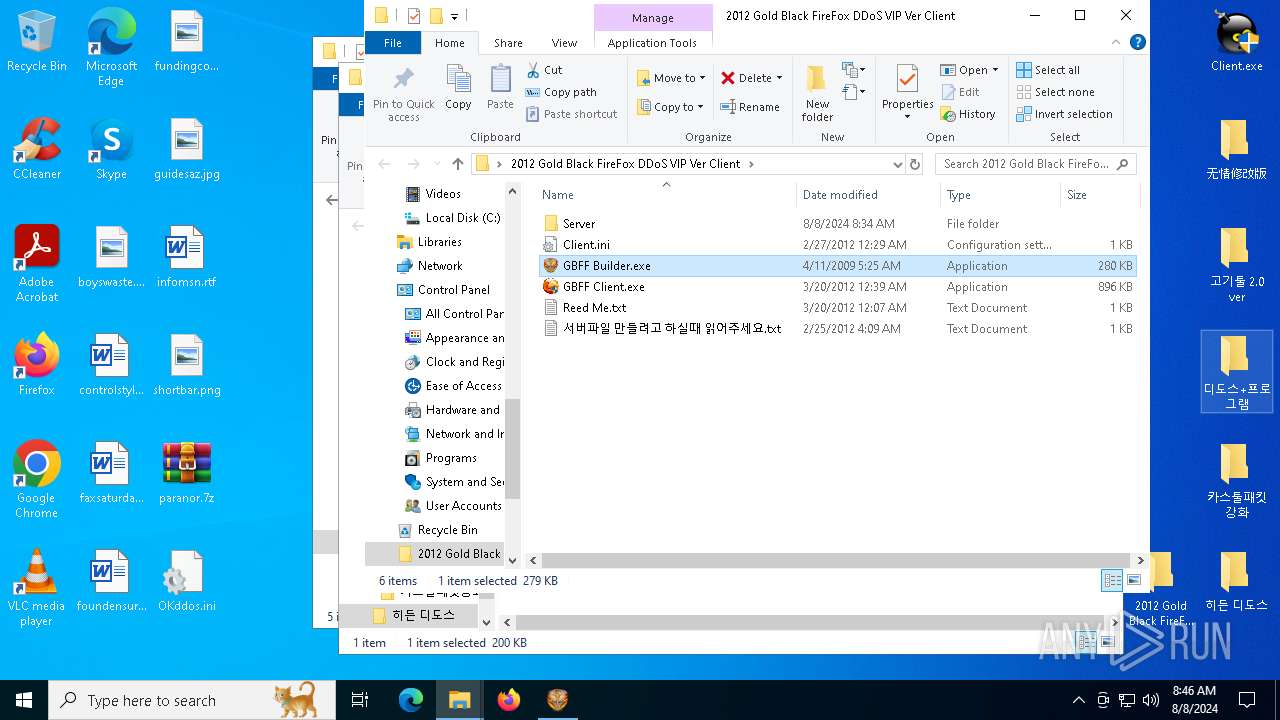
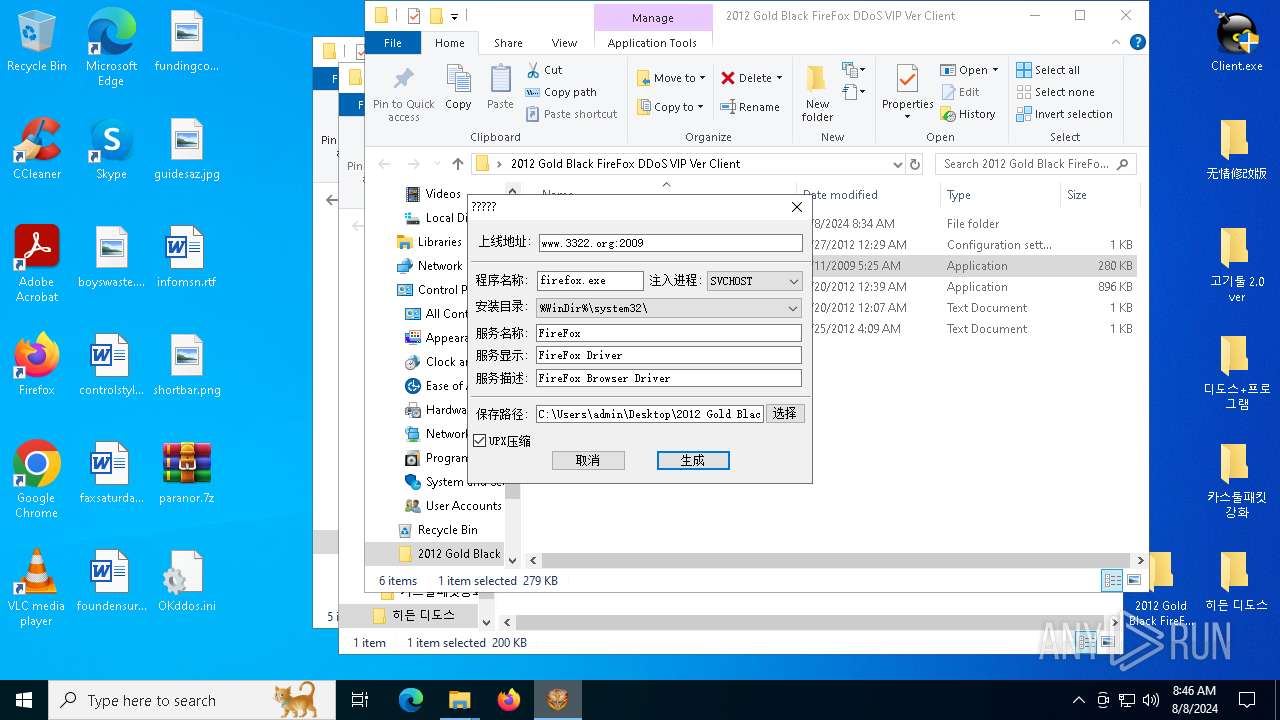
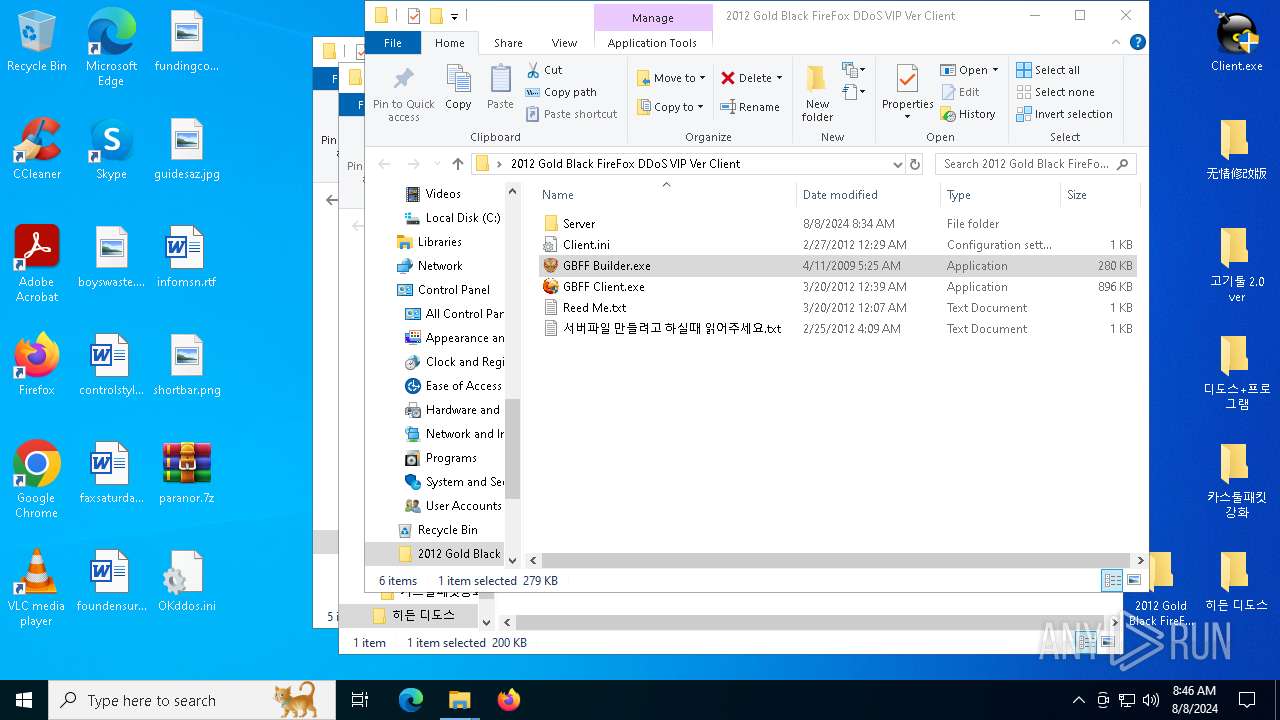
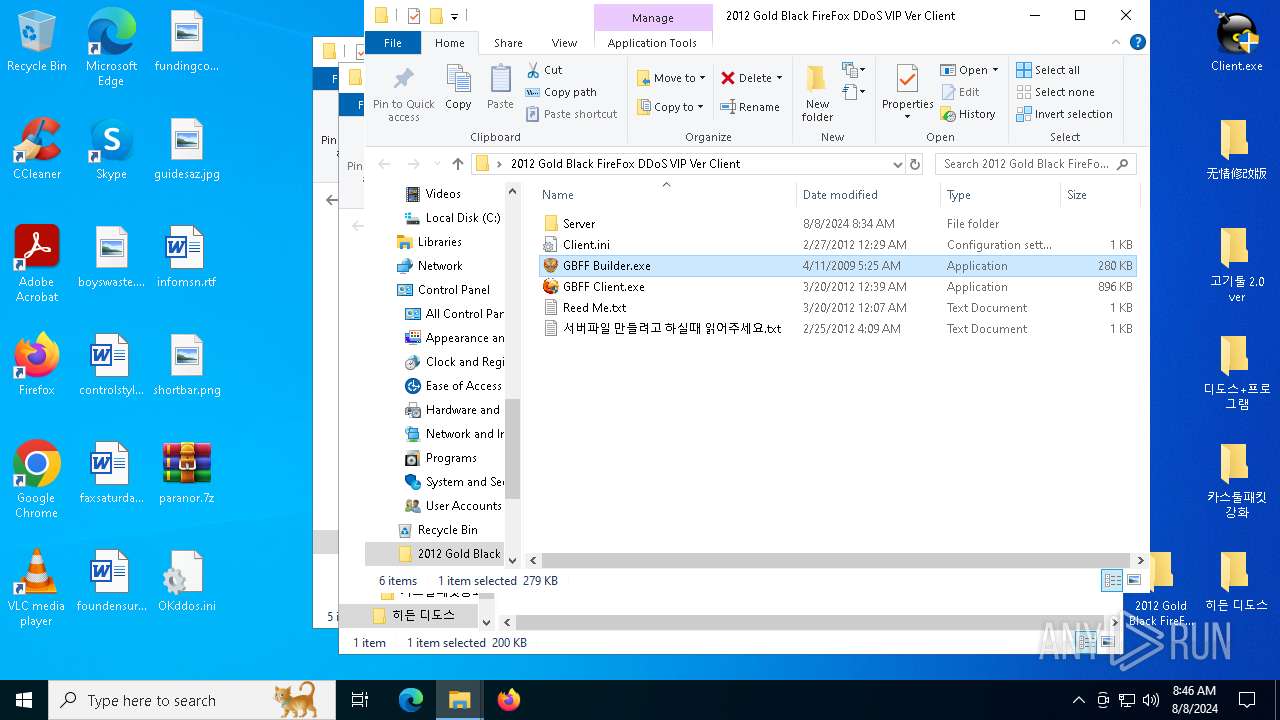
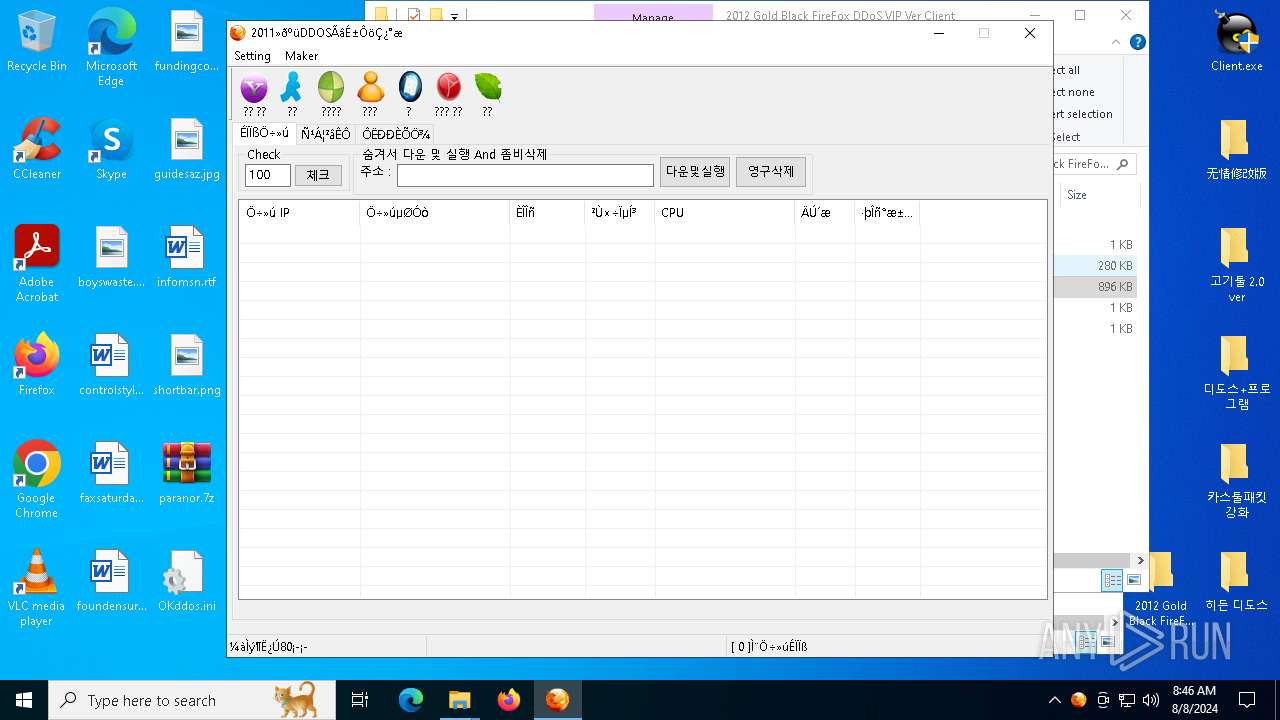
| File name: | paranor.7z |
| Full analysis: | https://app.any.run/tasks/85c60484-e163-4288-add9-ac00195e8acf |
| Verdict: | Malicious activity |
| Analysis date: | August 08, 2024, 08:43:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 3D234118EACD7EC9FFEBED5B00827A5F |
| SHA1: | 6272ABB9F0E7D391EBA4FE22A416EF8CEF77BAC9 |
| SHA256: | 30F4561861E99D1B04D30395A4A671D9291EF1A2261FC22E7F8C80B1E9EA43B7 |
| SSDEEP: | 98304:KVPflCFjd+dDxmo6kZVQ/BpEmi8ovZmbLHSJQTBRGBZxTmkJX7cPjEHncCR5rmK2:tSxqeQY72 |
MALICIOUS
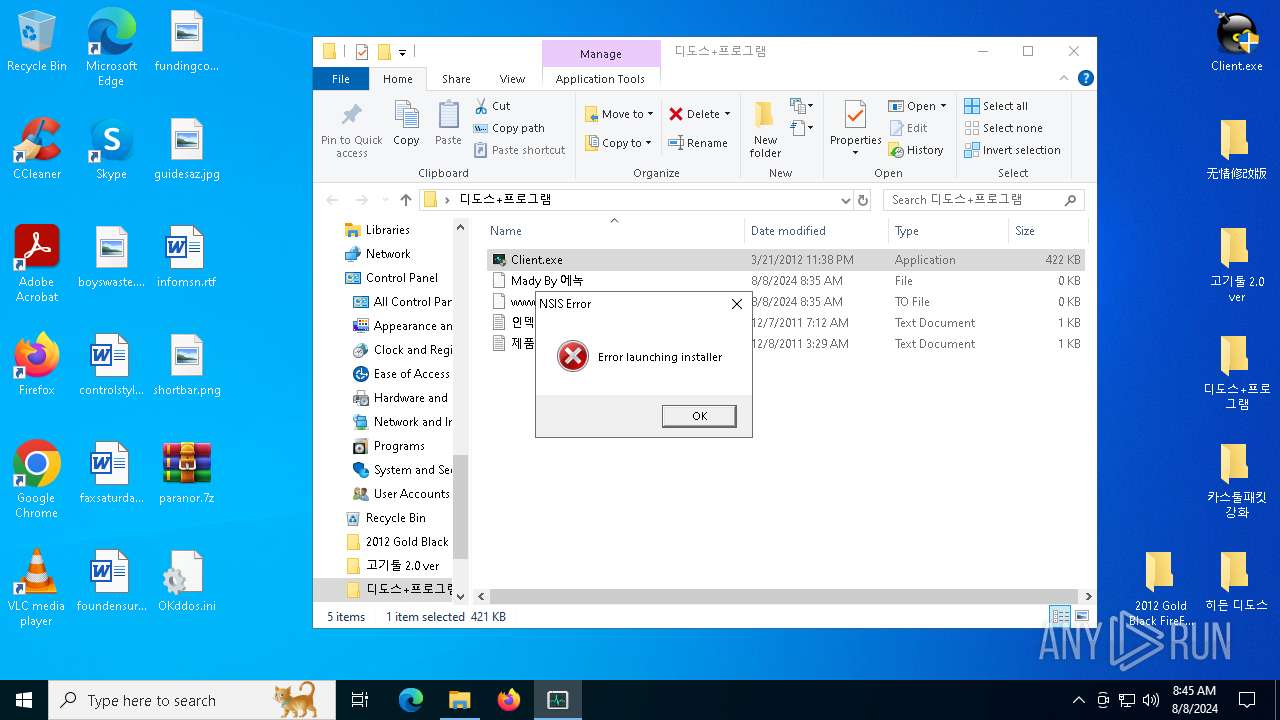
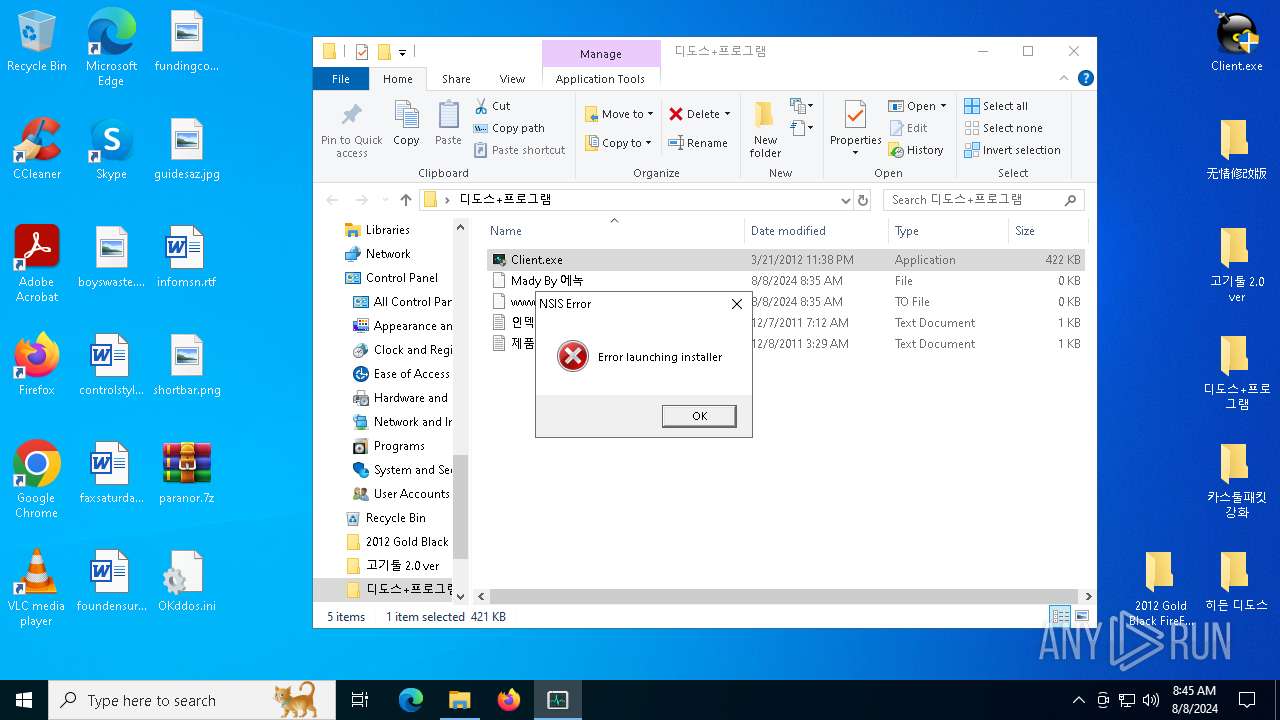
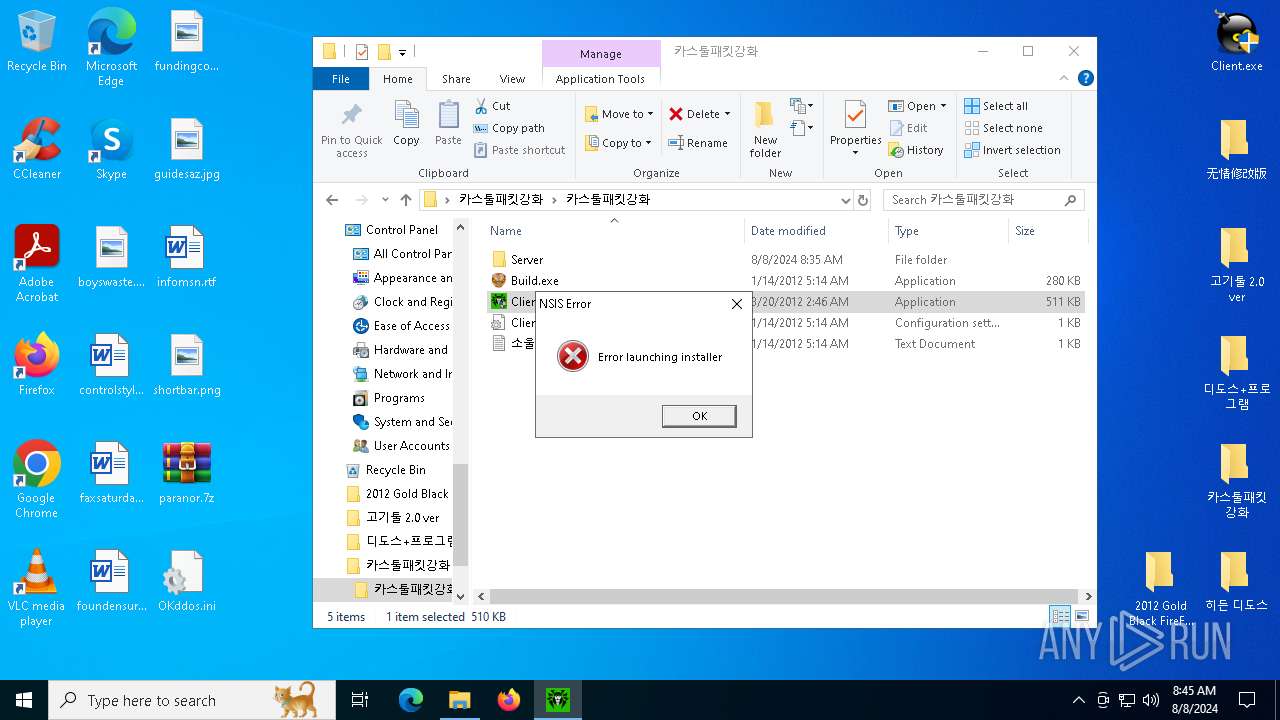
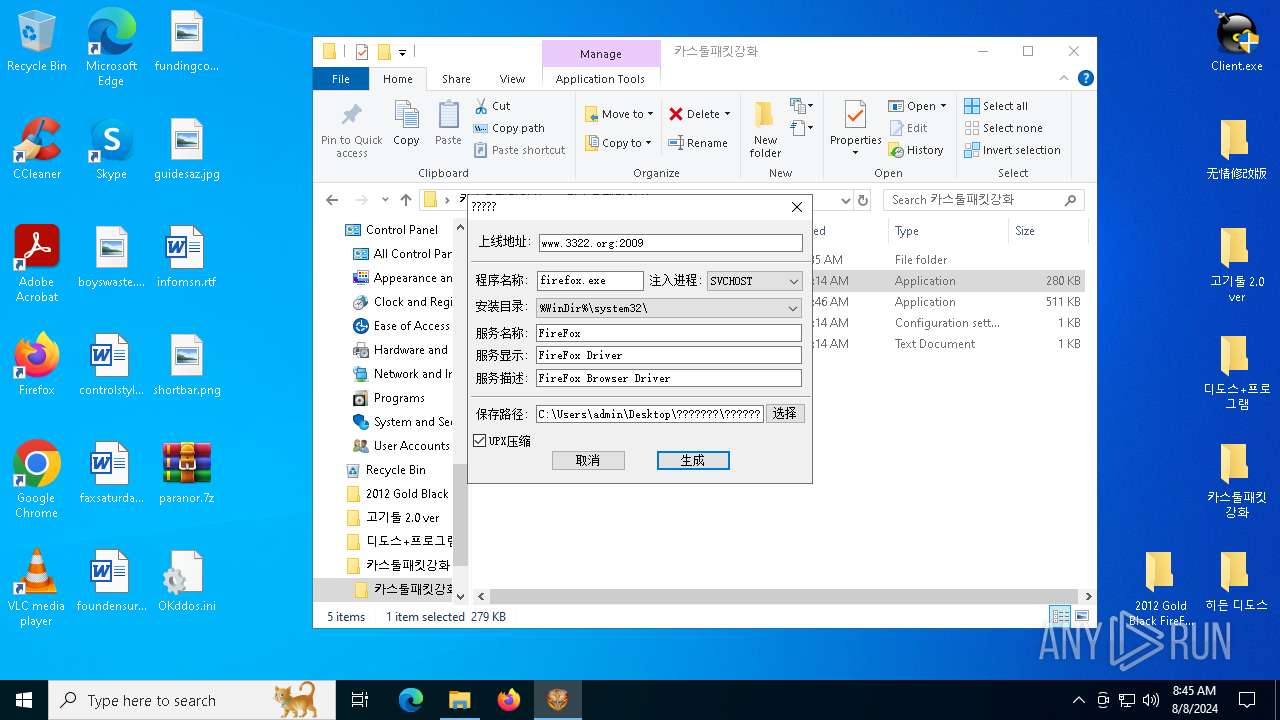
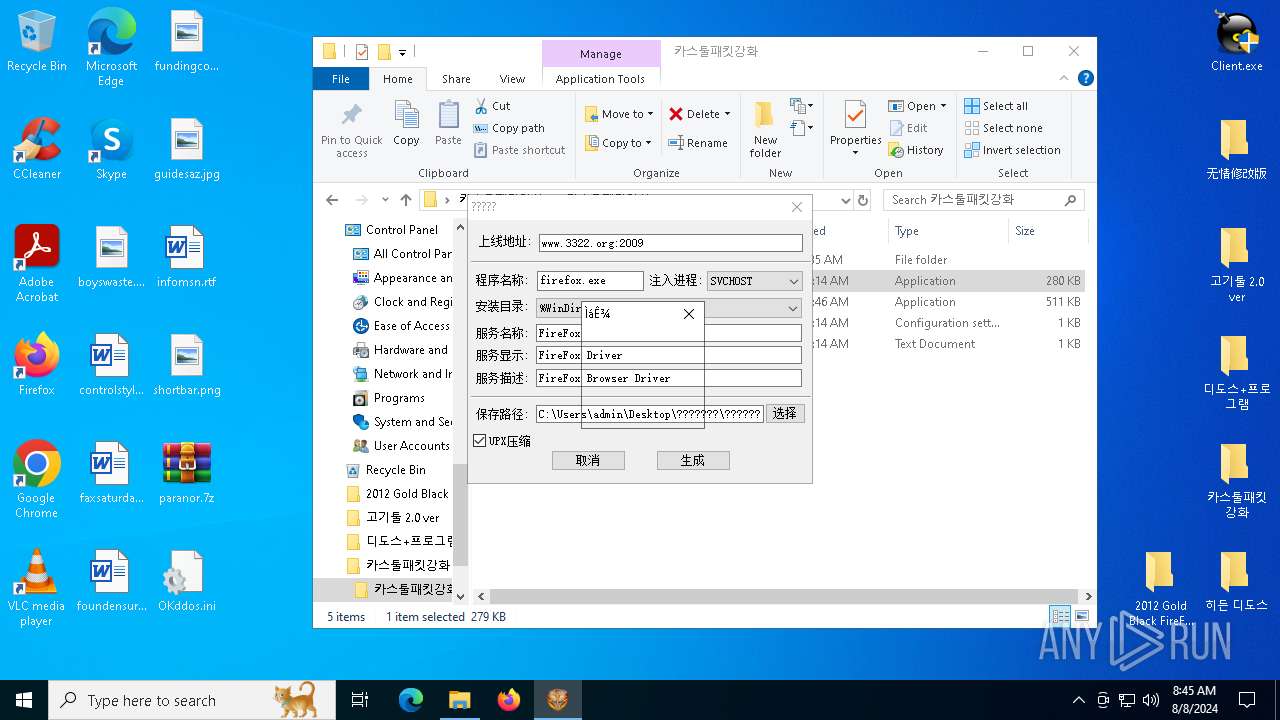
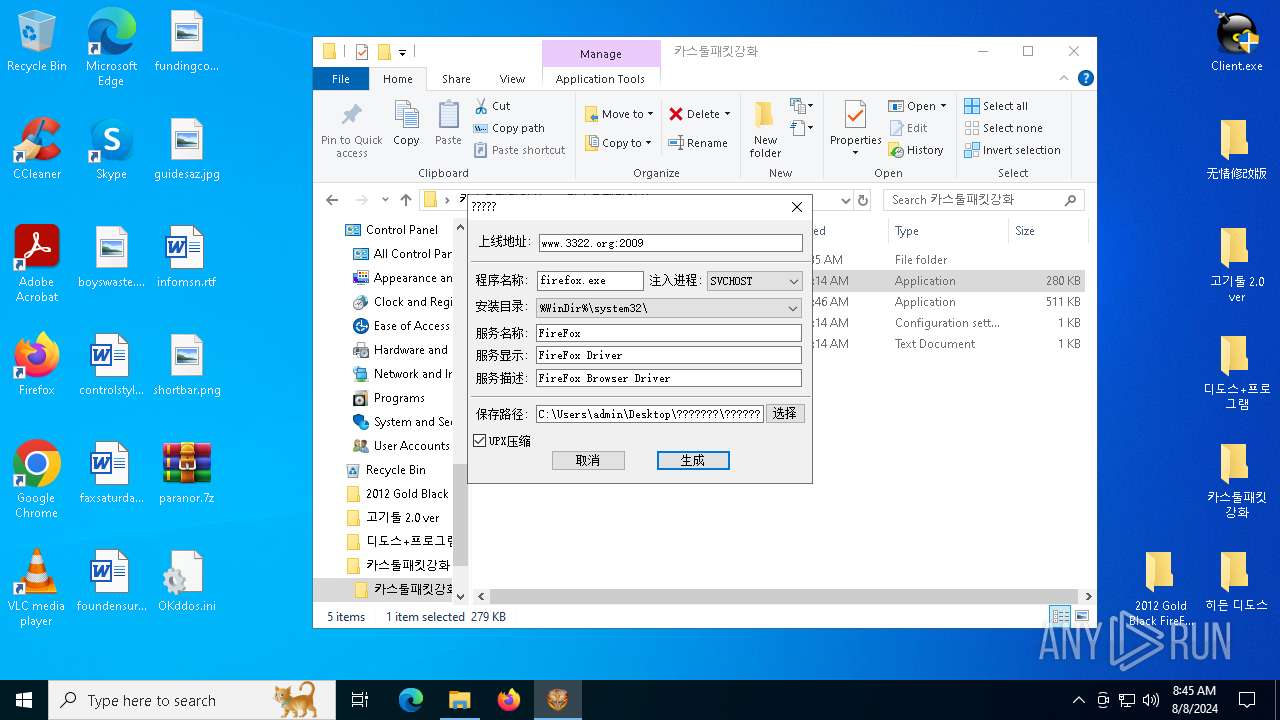
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6700)
- Client.exe (PID: 3372)
- install.exe (PID: 2224)
- GBFF Client.exe (PID: 4064)
- 123.exe (PID: 7100)
Scans artifacts that could help determine the target
- Client.exe (PID: 3180)
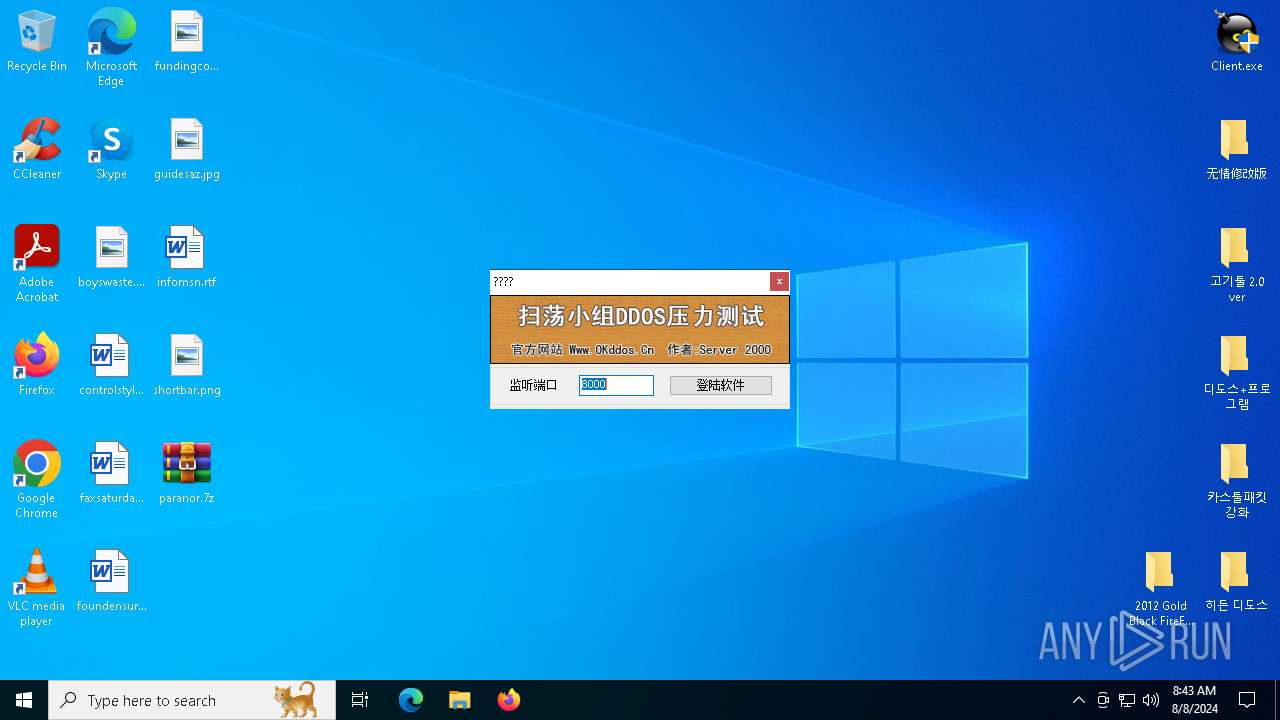
Connects to the CnC server
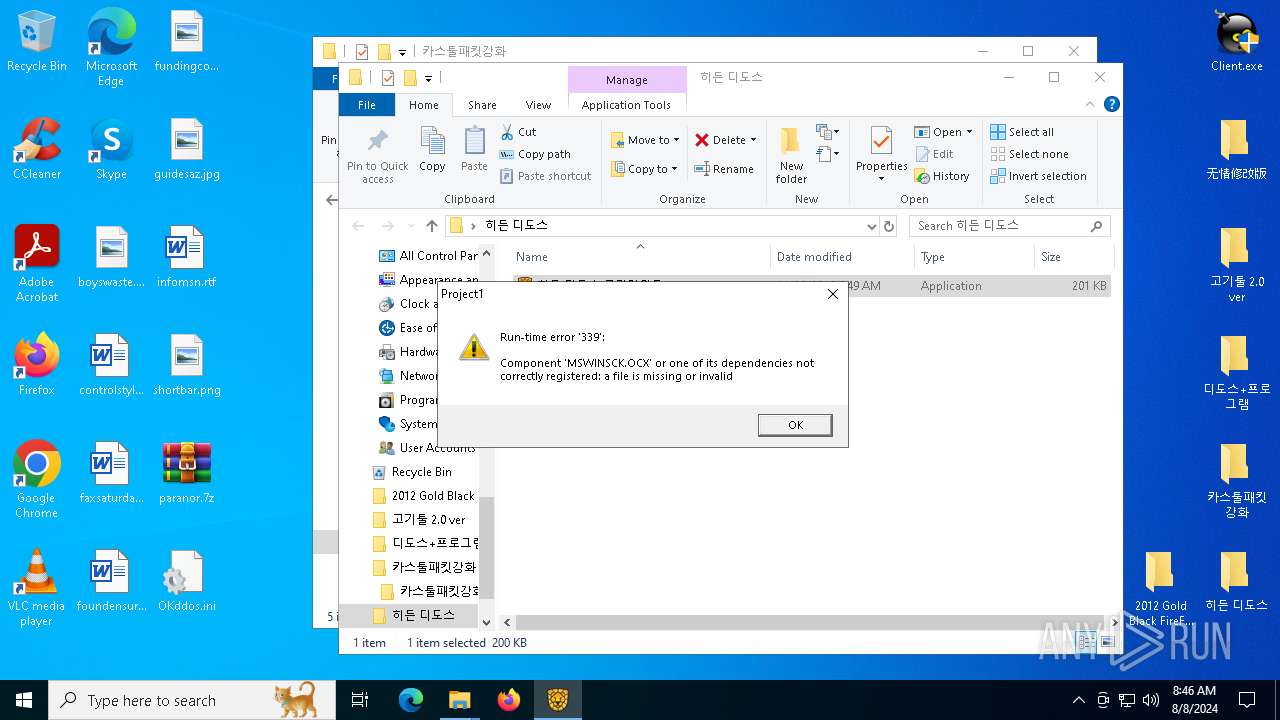
- 히든 디도스 클라이언트.exe (PID: 6388)
SUSPICIOUS
Creates file in the systems drive root
- Client.exe (PID: 3372)
- Client.exe (PID: 3180)
- install.exe (PID: 2224)
- GBFF Client.exe (PID: 4064)
- 123.exe (PID: 7100)
Executable content was dropped or overwritten
- Client.exe (PID: 3372)
- install.exe (PID: 2224)
- GBFF Client.exe (PID: 4064)
- 123.exe (PID: 7100)
Reads security settings of Internet Explorer
- Client.exe (PID: 3372)
- Client.exe (PID: 3180)
- Build.exe (PID: 252)
- GBFF Client.exe (PID: 4064)
Reads the date of Windows installation
- Client.exe (PID: 3372)
- GBFF Client.exe (PID: 4064)
Creates or modifies Windows services
- install.exe (PID: 2224)
- 123.exe (PID: 7100)
Reads Microsoft Outlook installation path
- Client.exe (PID: 3180)
Executes as Windows Service
- xonvom.exe (PID: 6216)
- hydjuc.exe (PID: 5656)
Reads Internet Explorer settings
- Client.exe (PID: 3180)
Checks Windows Trust Settings
- Client.exe (PID: 3180)
Contacting a server suspected of hosting an CnC
- 히든 디도스 클라이언트.exe (PID: 6388)
INFO
Checks supported languages
- Client.exe (PID: 3372)
- Client.exe (PID: 3180)
- install.exe (PID: 2224)
- xonvom.exe (PID: 6216)
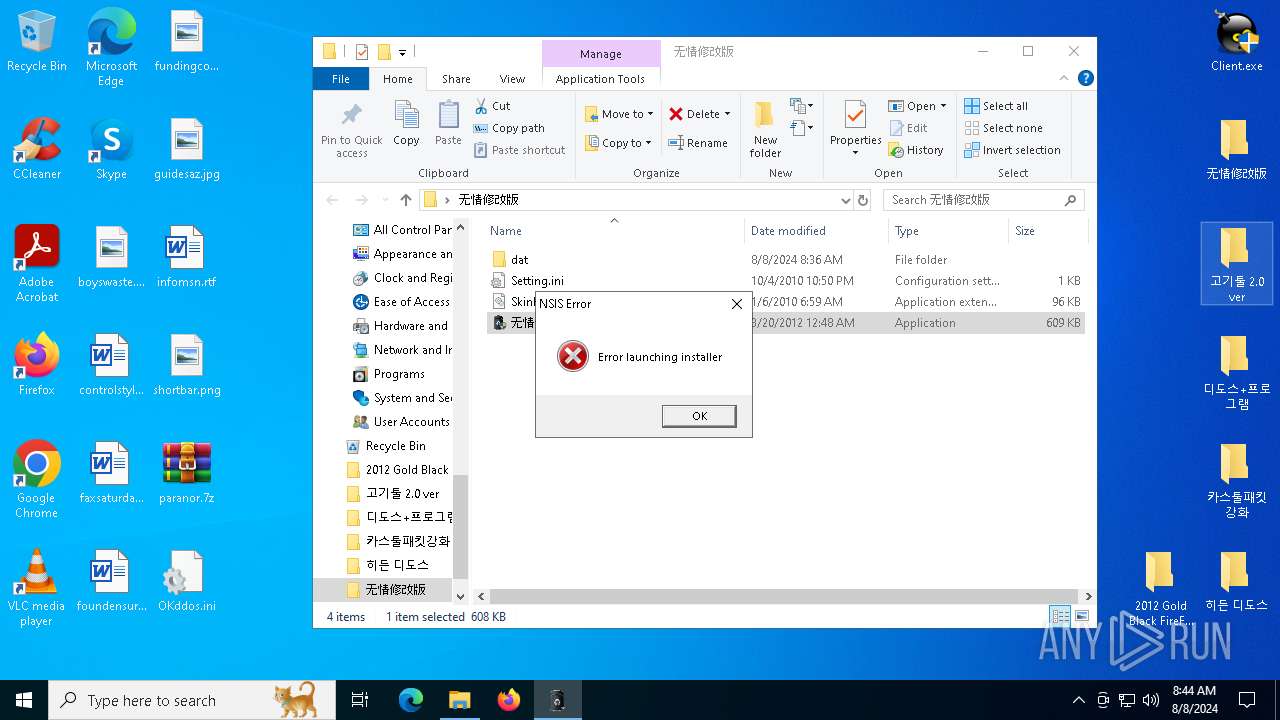
- 无情修改版.exe (PID: 6384)
- 无情修改版.exe (PID: 3160)
- gogi.exe (PID: 6408)
- Client.exe (PID: 1236)
- Build.exe (PID: 7112)
- Build.exe (PID: 252)
- Build.exe (PID: 6576)
- Client.exe (PID: 1432)
- GBFF Client.exe (PID: 4064)
- GBFF Builder.exe (PID: 6696)
- 히든 디도스 클라이언트.exe (PID: 6388)
- GBFF Client.exe (PID: 7160)
- 123.exe (PID: 7100)
- hydjuc.exe (PID: 5656)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6700)
Manual execution by a user
- Client.exe (PID: 3372)
- Client.exe (PID: 4644)
- 无情修改版.exe (PID: 6188)
- 无情修改版.exe (PID: 6384)
- 无情修改版.exe (PID: 3160)
- gogi.exe (PID: 6408)
- Client.exe (PID: 1432)
- Build.exe (PID: 7112)
- Build.exe (PID: 252)
- Build.exe (PID: 6576)
- Client.exe (PID: 1236)
- GBFF Builder.exe (PID: 6696)
- GBFF Client.exe (PID: 7036)
- GBFF Client.exe (PID: 4064)
- 히든 디도스 클라이언트.exe (PID: 6396)
- 히든 디도스 클라이언트.exe (PID: 6388)
Reads the computer name
- Client.exe (PID: 3372)
- xonvom.exe (PID: 6216)
- Client.exe (PID: 3180)
- install.exe (PID: 2224)
- 无情修改版.exe (PID: 3160)
- 无情修改版.exe (PID: 6384)
- gogi.exe (PID: 6408)
- Client.exe (PID: 1236)
- Build.exe (PID: 7112)
- Build.exe (PID: 252)
- Build.exe (PID: 6576)
- Client.exe (PID: 1432)
- GBFF Builder.exe (PID: 6696)
- GBFF Client.exe (PID: 4064)
- 히든 디도스 클라이언트.exe (PID: 6388)
- 123.exe (PID: 7100)
- hydjuc.exe (PID: 5656)
- GBFF Client.exe (PID: 7160)
Process checks computer location settings
- Client.exe (PID: 3372)
- GBFF Client.exe (PID: 4064)
Reads Environment values
- xonvom.exe (PID: 6216)
- hydjuc.exe (PID: 5656)
Reads CPU info
- xonvom.exe (PID: 6216)
- hydjuc.exe (PID: 5656)
Checks proxy server information
- Client.exe (PID: 3180)
Creates files or folders in the user directory
- Client.exe (PID: 3180)
Process checks Internet Explorer phishing filters
- Client.exe (PID: 3180)
Reads the software policy settings
- Client.exe (PID: 3180)
- 히든 디도스 클라이언트.exe (PID: 6388)
Reads the machine GUID from the registry
- Client.exe (PID: 3180)
VMProtect protector has been detected
- xonvom.exe (PID: 6216)
- hydjuc.exe (PID: 5656)
- GBFF Client.exe (PID: 7160)
UPX packer has been detected
- Build.exe (PID: 252)
- GBFF Client.exe (PID: 7160)
Create files in a temporary directory
- 히든 디도스 클라이언트.exe (PID: 6388)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
164
Monitored processes
24
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | "C:\Users\admin\Desktop\카스툴패킷강화\카스툴패킷강화\Build.exe" | C:\Users\admin\Desktop\카스툴패킷강화\카스툴패킷강화\Build.exe | explorer.exe | ||||||||||||
User: admin Company: QQ:555121 Integrity Level: MEDIUM Description: 火狐DDOS压力测试 Exit code: 0 Version: 3, 0, 0, 1 Modules
| |||||||||||||||
| 1236 | "C:\Users\admin\Desktop\카스툴패킷강화\카스툴패킷강화\Client.exe" | C:\Users\admin\Desktop\카스툴패킷강화\카스툴패킷강화\Client.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 2 Modules
| |||||||||||||||
| 1432 | "C:\Users\admin\Desktop\디도스+프로그램\Client.exe" | C:\Users\admin\Desktop\디도스+프로그램\Client.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 2 Modules
| |||||||||||||||
| 2224 | "C:\install.exe" | C:\install.exe | Client.exe | ||||||||||||
User: admin Company: Anonymous Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3160 | "C:\Users\admin\Desktop\无情修改版\无情修改版.exe" | C:\Users\admin\Desktop\无情修改版\无情修改版.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 2 Modules
| |||||||||||||||
| 3180 | "C:\Client.exe" | C:\Client.exe | Client.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Client Microsoft 基础类应用程序 Exit code: 2 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 3372 | "C:\Users\admin\Desktop\Client.exe" | C:\Users\admin\Desktop\Client.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
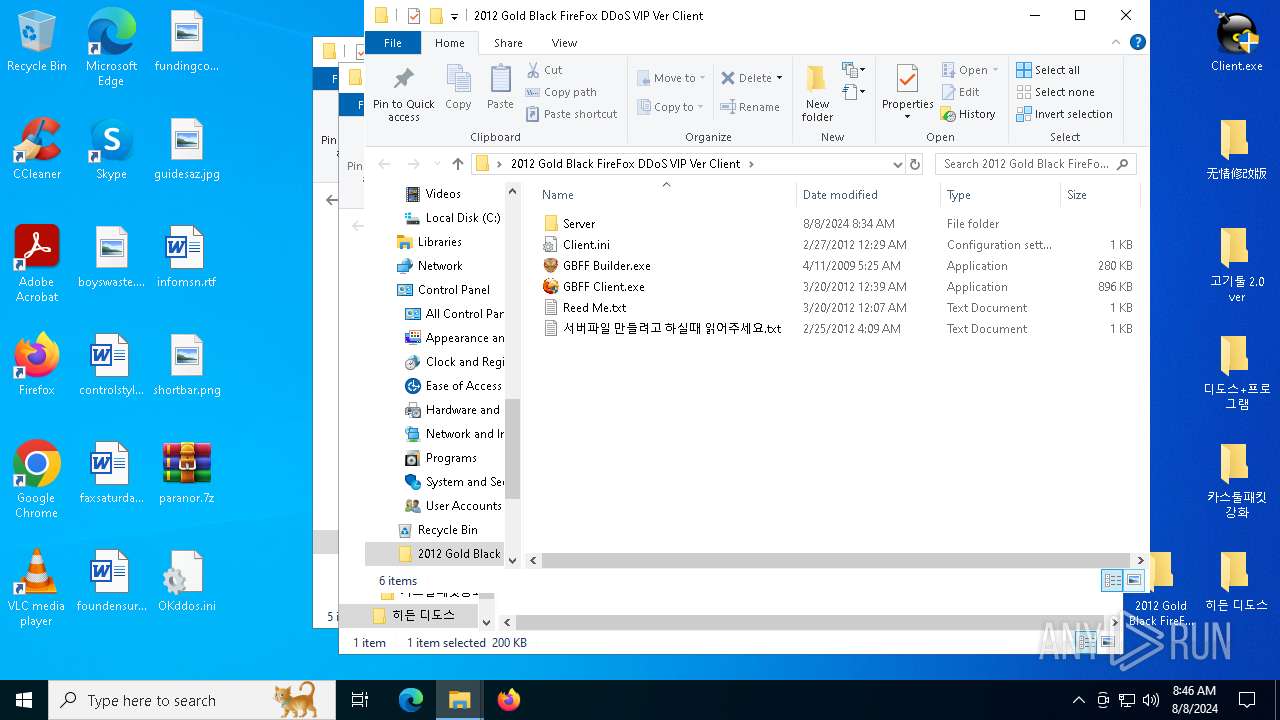
| 4064 | "C:\Users\admin\Desktop\2012 Gold Black FireFox DDoS VIP Ver Client\GBFF Client.exe" | C:\Users\admin\Desktop\2012 Gold Black FireFox DDoS VIP Ver Client\GBFF Client.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 4644 | "C:\Users\admin\Desktop\Client.exe" | C:\Users\admin\Desktop\Client.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 5656 | C:\WINDOWS\SysWOW64\hydjuc.exe | C:\Windows\SysWOW64\hydjuc.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Integrity Level: SYSTEM Description: Server Version: 1, 0, 0, 1 Modules
| |||||||||||||||
Total events
20 620
Read events
20 466
Write events
146
Delete events
8
Modification events
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\paranor.7z | |||
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
20
Suspicious files
8
Text files
13
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6700.42616\디도스+프로그램\인덱스 아리아.txt | text | |
MD5:0C1EEAEC031EFD80ED5D7429BDE5F9E4 | SHA256:F5C2C798E6859362A47BB352C10EBD2896AE9E9BBDCDC71FC5A81C6F5EE500CC | |||
| 6700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6700.42616\2012 Gold Black FireFox DDoS VIP Ver Client\Reed Me.txt | text | |
MD5:9F55CC3C625F60F17A17B509AF0F05B2 | SHA256:6ADED02F86AB169A774FD07960FE4E1573F69B562289362C357037595801C80A | |||
| 6700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6700.42616\2012 Gold Black FireFox DDoS VIP Ver Client\Server\Server1.rar | compressed | |
MD5:A97B3168F15E2E7EC42FB9E378656967 | SHA256:B8A1B9C805594D872CEADC50A63487B5F3CEBB800EC3A16DD5B8C736DC0C426B | |||
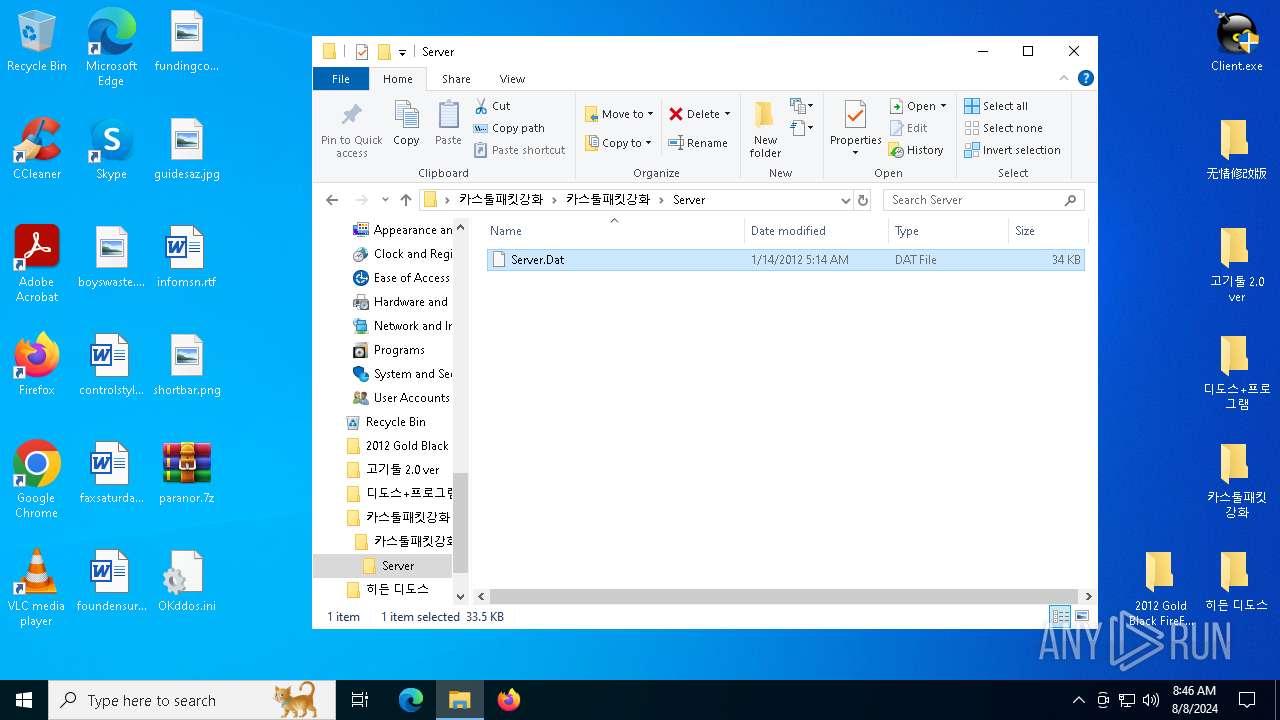
| 6700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6700.42616\카스툴패킷강화\카스툴패킷강화\Server\Server.Dat | executable | |
MD5:94FEE570220BAF8B735E96E0FAB910C3 | SHA256:F089590C57F095058D2DDE975428D47BBC3A655A599D3AE1F3EBF779F369DF70 | |||
| 6700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6700.42616\카스툴패킷강화\카스툴패킷강화\Client.ini | ini | |
MD5:2CF1B0C6F860492C69CDFEC79F7073DF | SHA256:879B2B0E0A84A5A7781B58F7B357DA6532E0A854FF33C848CA47835EAF17BA6F | |||
| 6700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6700.42616\2012 Gold Black FireFox DDoS VIP Ver Client\Client.ini | ini | |
MD5:FC5B5A6BBE21A3E2E141EF011BE7C9A6 | SHA256:F8A4D87F4D83F0800D5F747D5CFACCAF5FDC2792BE99FF0571191A781C54EBFE | |||
| 6700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6700.42616\2012 Gold Black FireFox DDoS VIP Ver Client\Server\Server2.rar | compressed | |
MD5:A7A854166EB85FB9A6C4A4599556546A | SHA256:DC596A1257E7723D409B60BE340468A4703B779790D90D13A741B917BDF16493 | |||
| 6700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6700.42616\2012 Gold Black FireFox DDoS VIP Ver Client\서버파일 만들려고 하실때 읽어주세요.txt | text | |
MD5:0B237E5E29FFEF02EAC4D6D2EB8D268B | SHA256:C1E3F94B505F58EC7AB78EFD7F218A6F6A78E19C80FB1F79B93C4FEC781F1D9E | |||
| 6700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6700.42616\无情修改版\Setting.ini | text | |
MD5:64E5A53729D662DC9DD2F0B8F7044BCE | SHA256:3749EADDCF1C468C0B98B067B8BF800C8E6CC3FD273DB405899AD9E91DF8F131 | |||
| 6700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6700.42616\无情修改版\dat\Cache.dat | executable | |
MD5:61A2FE475E0EC4C19ACCBE268FDAA219 | SHA256:A3F99793B01ED4549C6973356F20697CEC5FDC1090C2B2826AC037350C5764FD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
46
DNS requests
63
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6352 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6376 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3180 | Client.exe | GET | 200 | 38.174.232.2:80 | http://www.okddos.cn/tj.js | unknown | — | — | unknown |
5244 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3180 | Client.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/rootr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDQHuXxad%2F5c1K2Rl1mo%3D | unknown | — | — | whitelisted |
6388 | 히든 디도스 클라이언트.exe | GET | 302 | 23.206.208.172:80 | http://blog.naver.com/PostView.nhn?blogId=enoch_rvn&logNo=50129408978&parentCategoryNo=1&viewDate=¤tPage=1&listtype=0&userTopListOpen=false&userTopListCount=5&userTopListManageOpen=false&userTopListCurrentPage=undefined | unknown | — | — | whitelisted |
3180 | Client.exe | GET | 200 | 104.18.21.226:80 | http://ocsp2.globalsign.com/rootr3/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCDQHuXyId%2FGI71DM6hVc%3D | unknown | — | — | whitelisted |
3180 | Client.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/gsrsaovsslca2018/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBRrcGT%2BanRD3C1tW3nsrKeuXC7DPwQU%2BO9%2F8s14Z6jeb48kjYjxhwMCs%2BsCDE5AA6ZetoH4f0vY6w%3D%3D | unknown | — | — | whitelisted |
3180 | Client.exe | GET | 200 | 38.174.232.2:80 | http://www.okddos.cn/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2680 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
876 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5336 | SearchApp.exe | 92.123.104.66:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5244 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
th.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |
competitionkill.codns.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6388 | 히든 디도스 클라이언트.exe | Malware Command and Control Activity Detected | ET MALWARE W32/Mepaow.Backdoor Initial Checkin to Intermediary Pre-CnC |
6388 | 히든 디도스 클라이언트.exe | Potentially Bad Traffic | ET INFO Referrer-Policy set to unsafe-url |