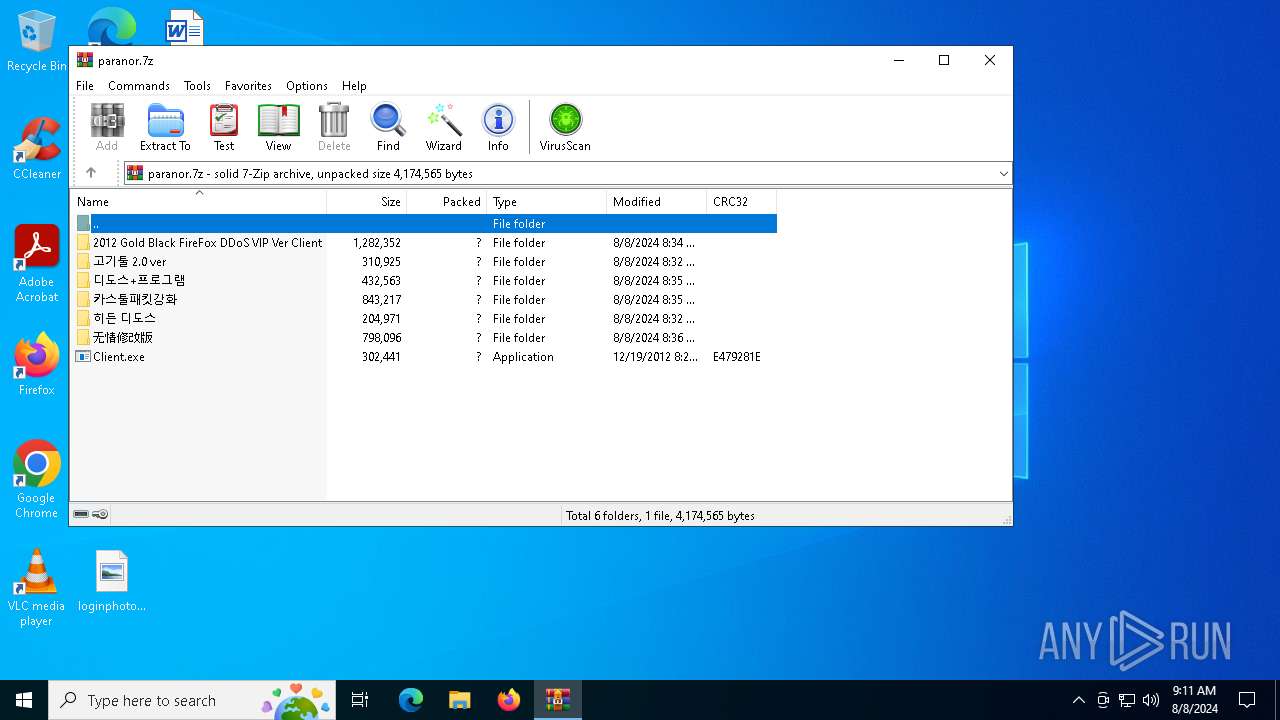
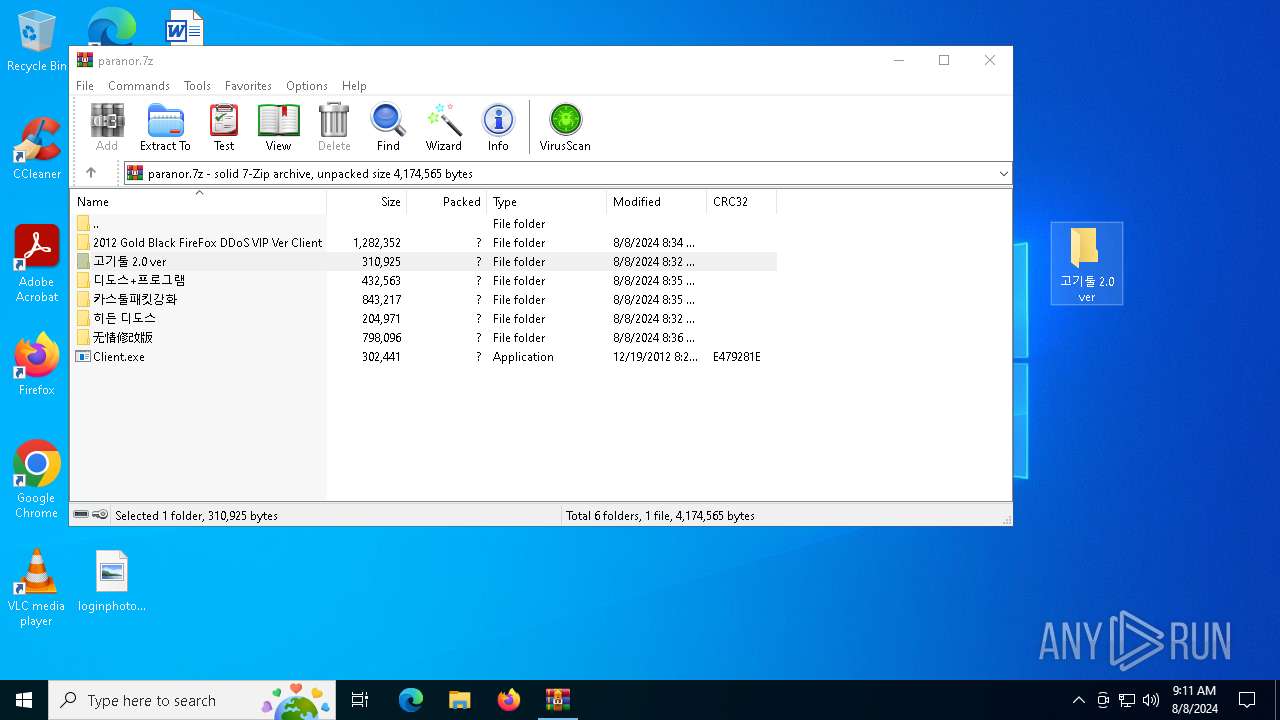
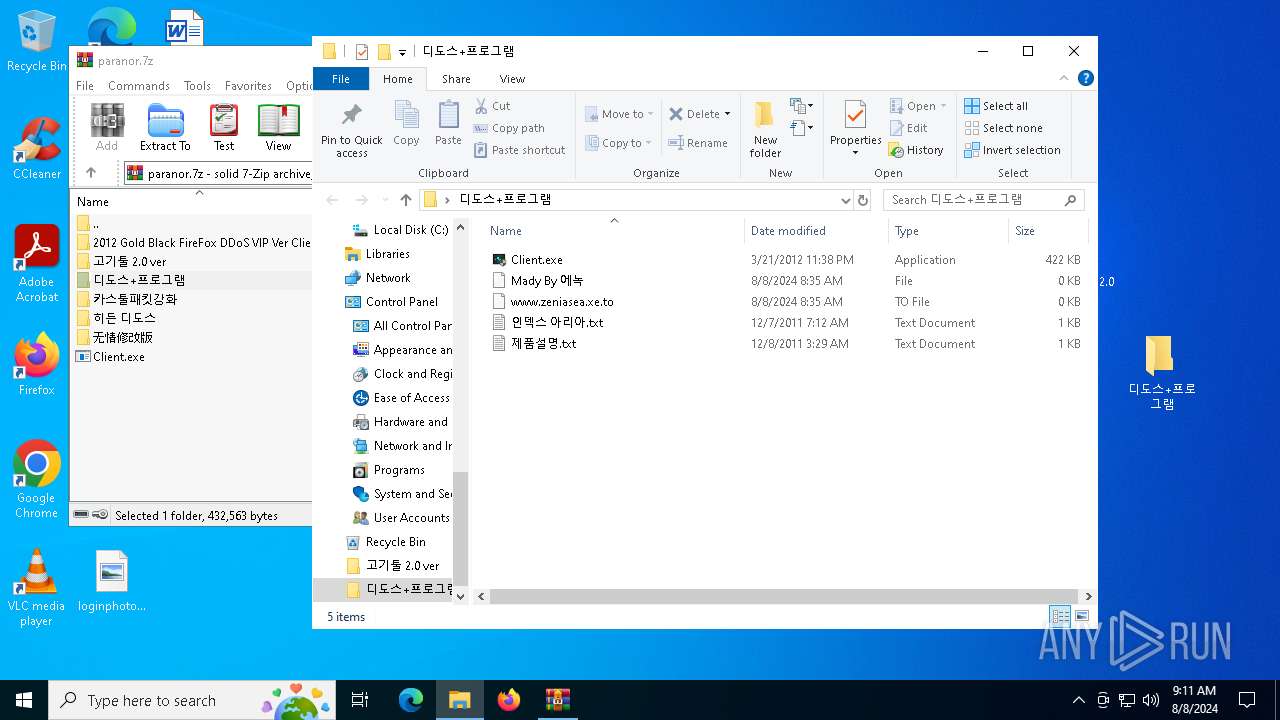
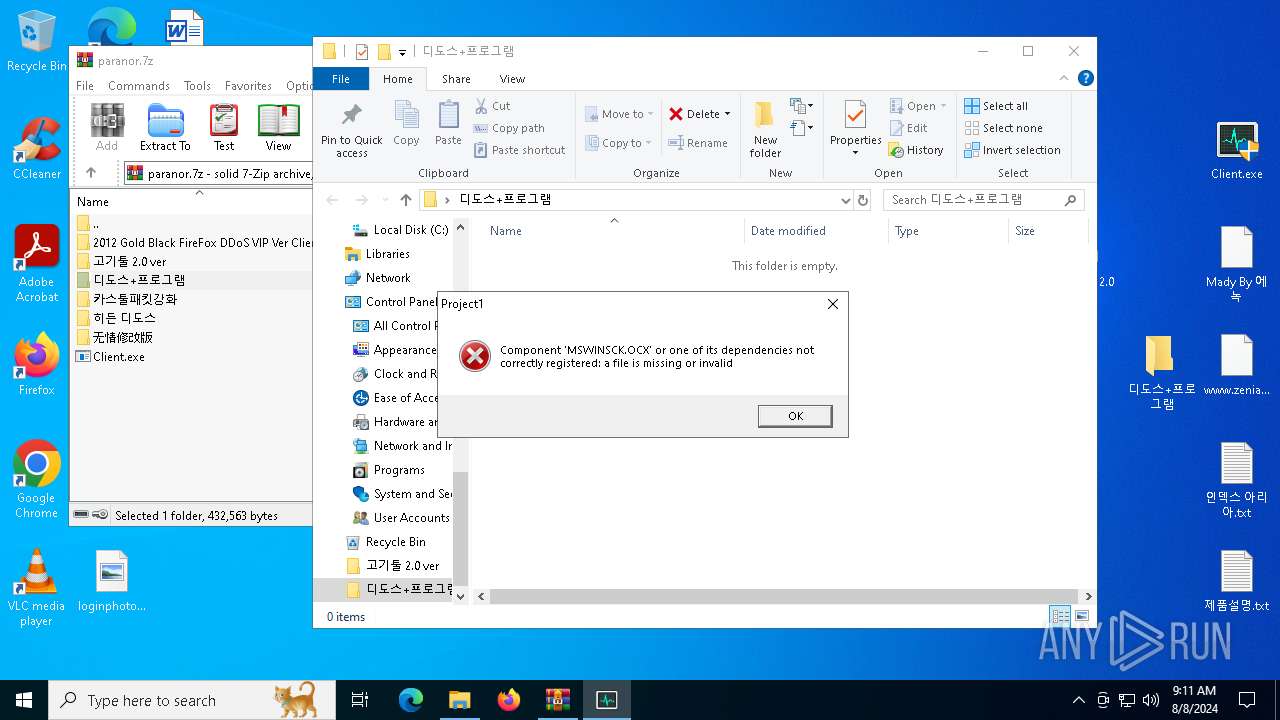
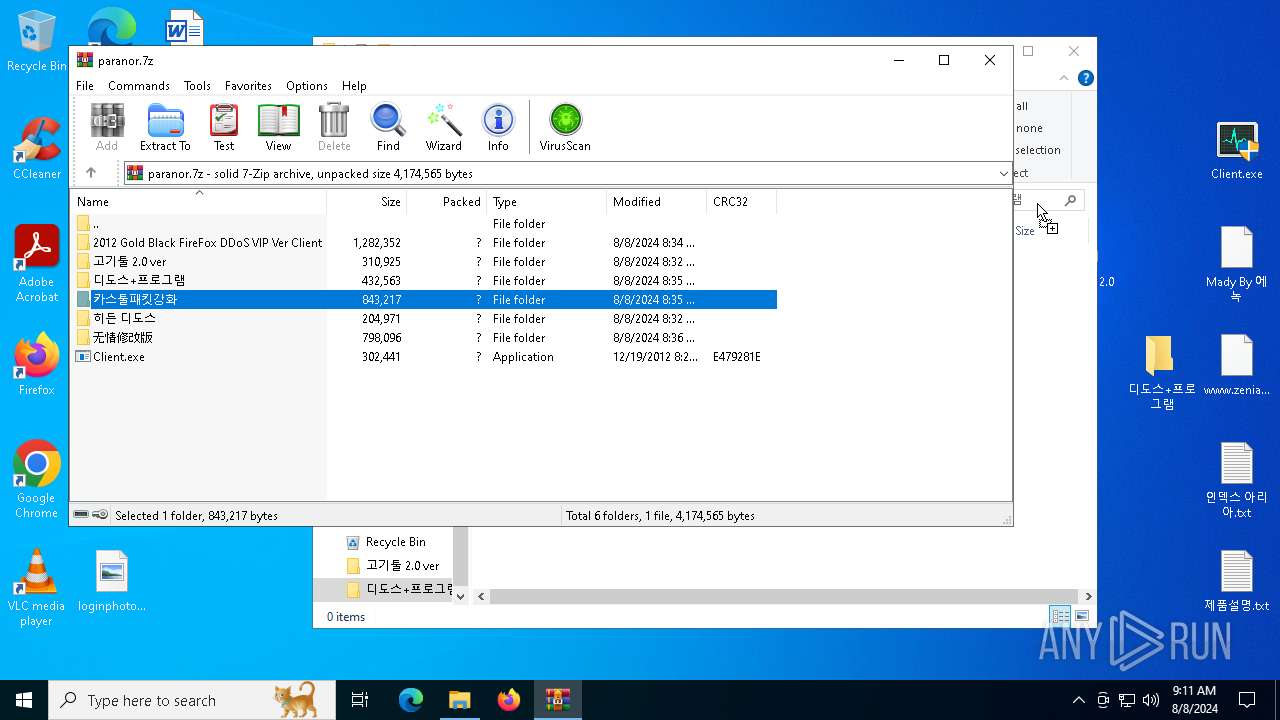
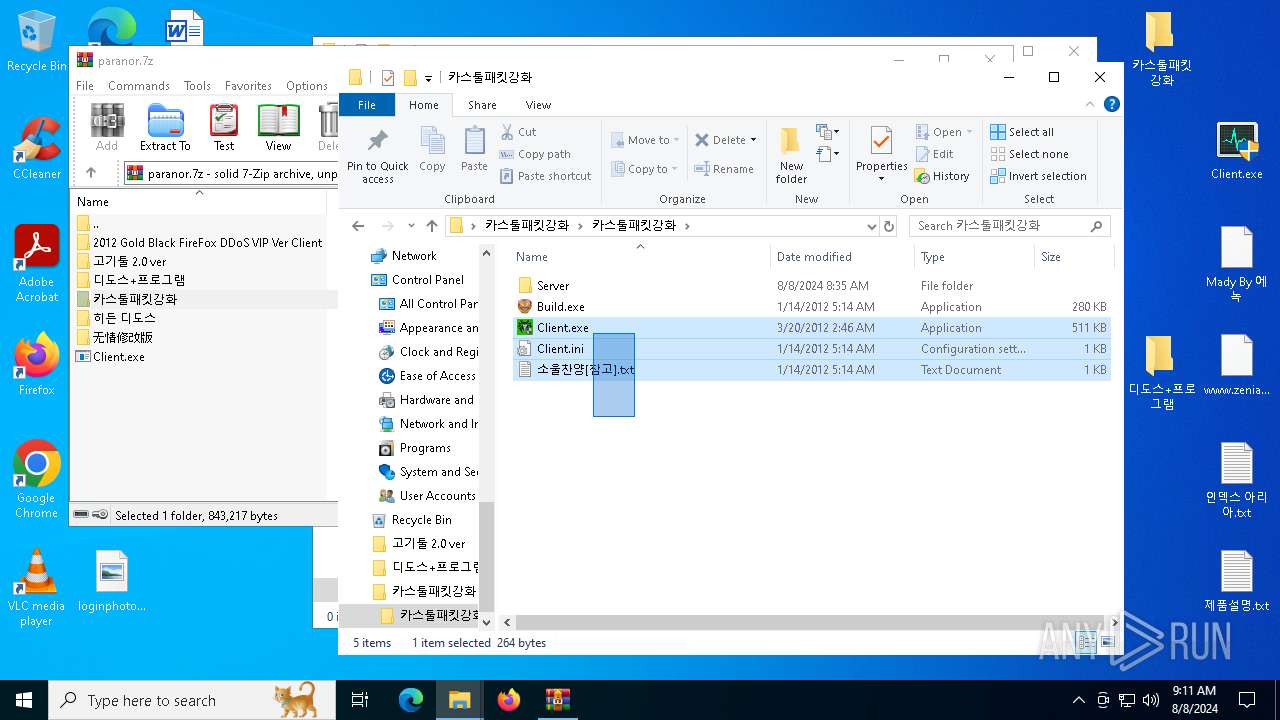
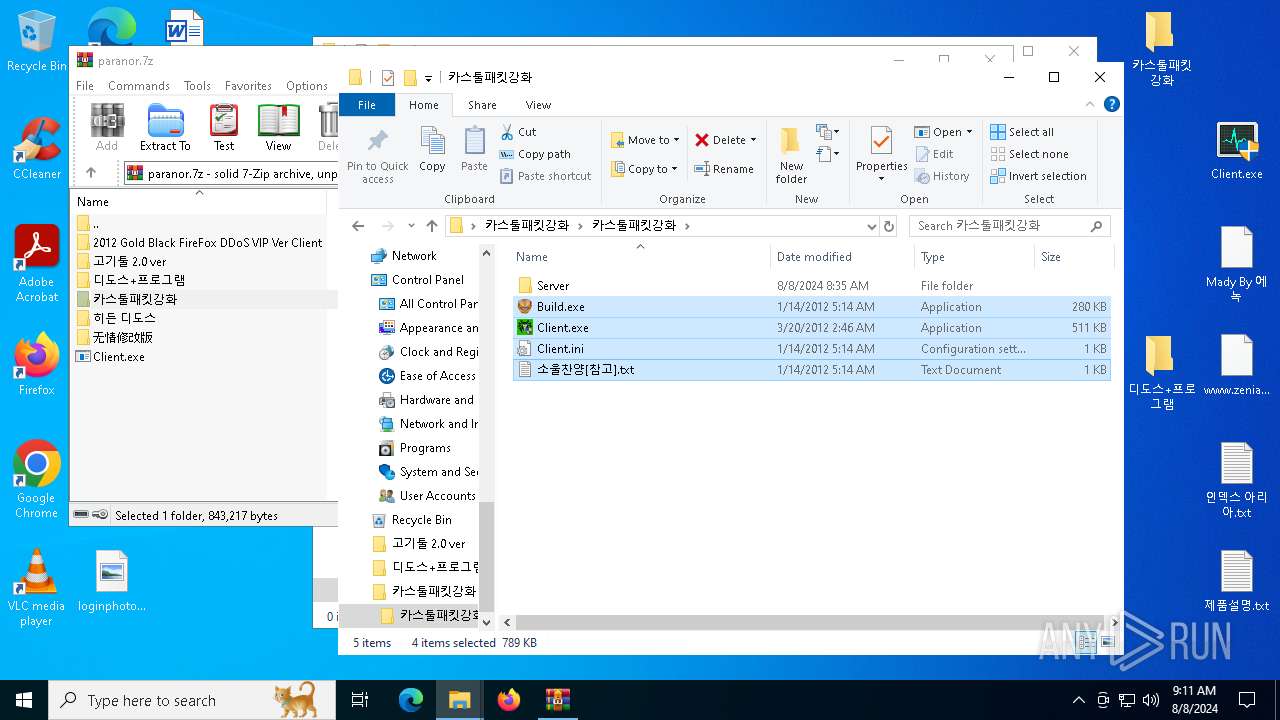
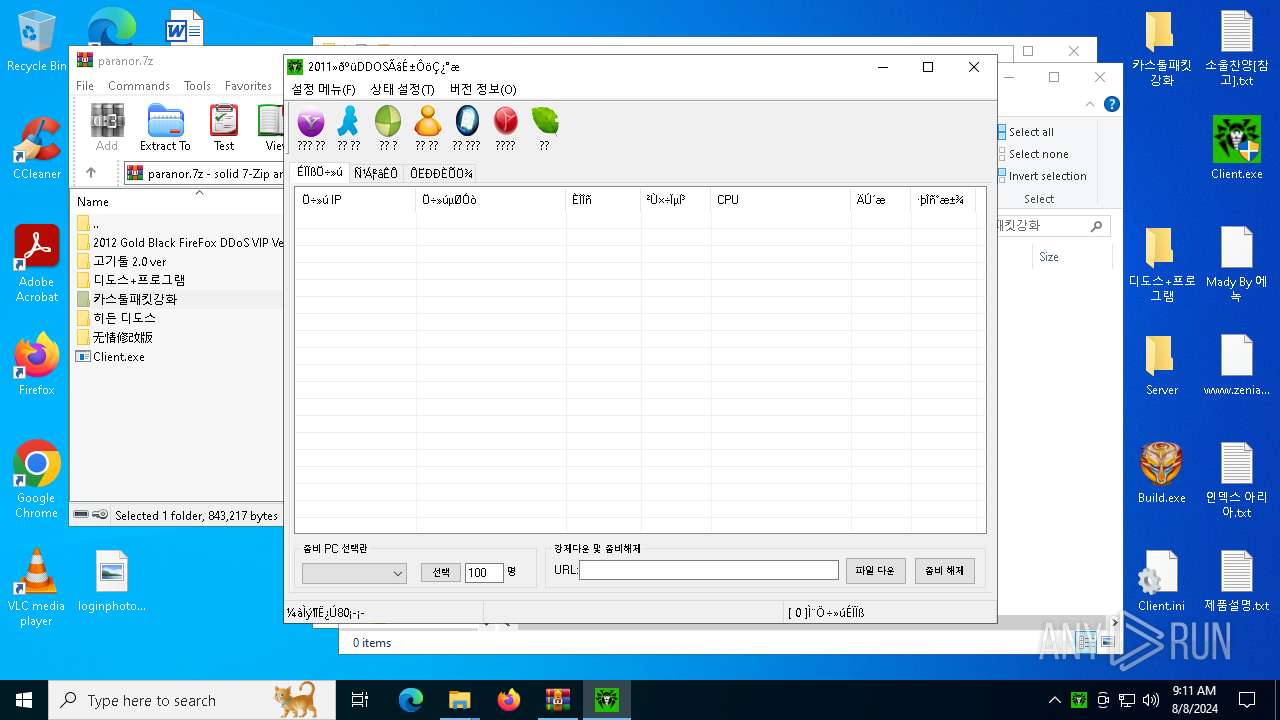
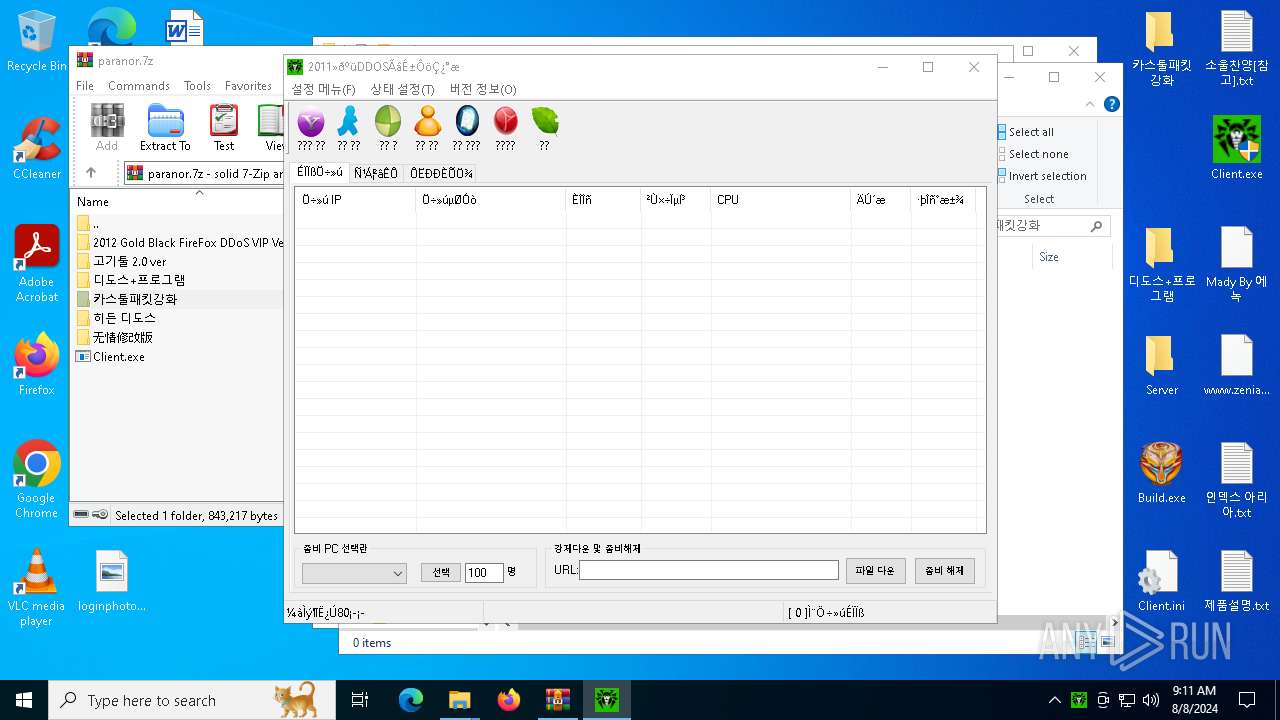
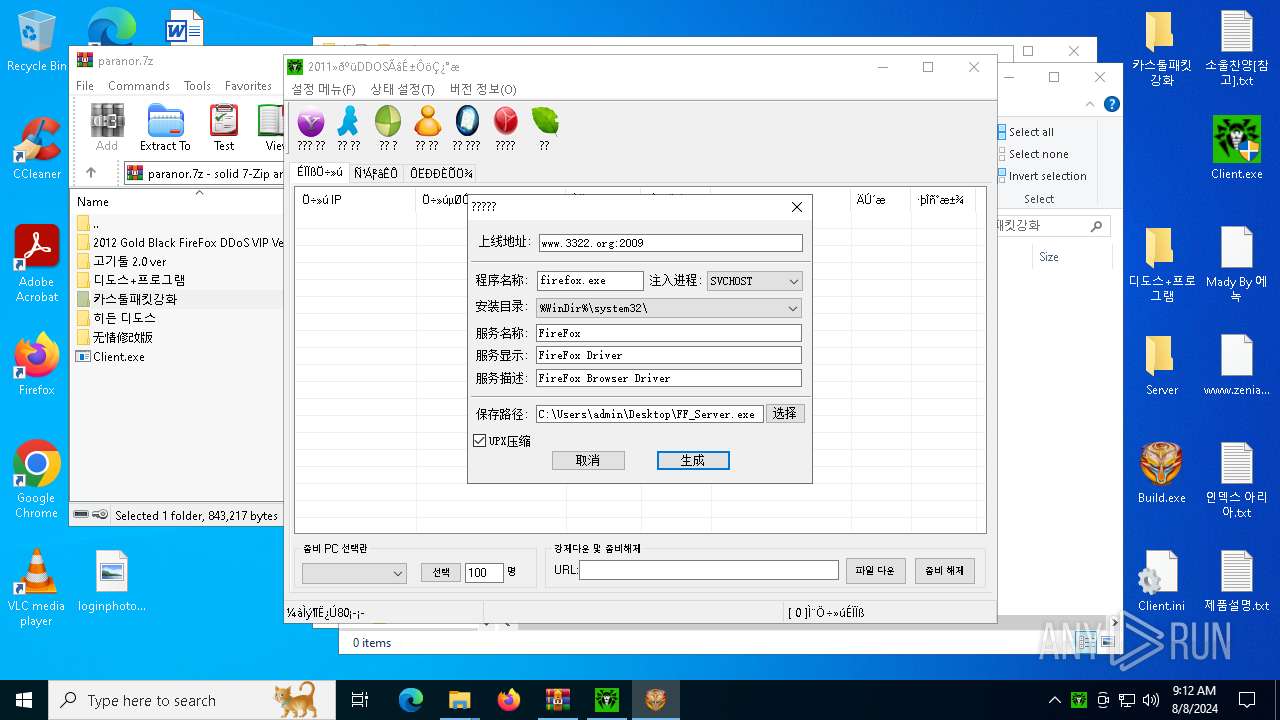
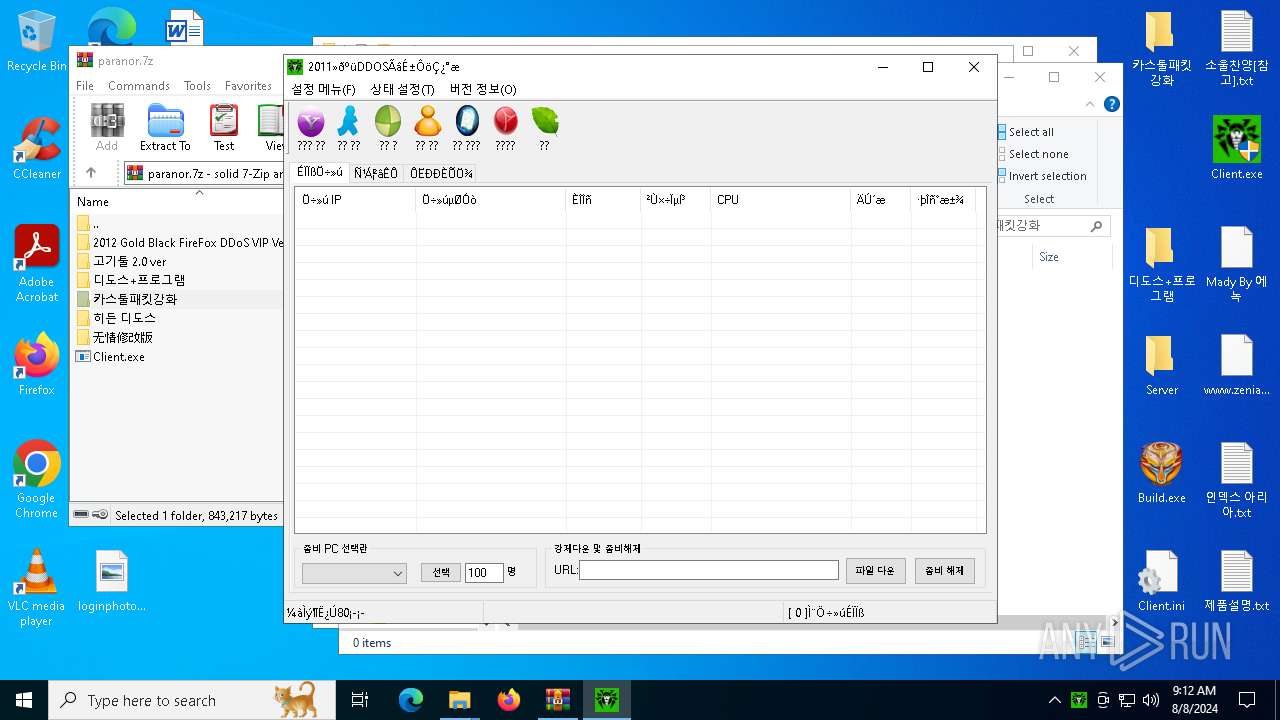
| File name: | paranor.7z |
| Full analysis: | https://app.any.run/tasks/3e5e2181-002e-4232-9479-afccfc4705a8 |
| Verdict: | Malicious activity |
| Analysis date: | August 08, 2024, 09:11:05 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 3D234118EACD7EC9FFEBED5B00827A5F |
| SHA1: | 6272ABB9F0E7D391EBA4FE22A416EF8CEF77BAC9 |
| SHA256: | 30F4561861E99D1B04D30395A4A671D9291EF1A2261FC22E7F8C80B1E9EA43B7 |
| SSDEEP: | 98304:KVPflCFjd+dDxmo6kZVQ/BpEmi8ovZmbLHSJQTBRGBZxTmkJX7cPjEHncCR5rmK2:tSxqeQY72 |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6380)
- Client.exe (PID: 6688)
- 123.exe (PID: 6844)
- OneDriveSetup.exe (PID: 7452)
Scans artifacts that could help determine the target
- OneDrive.exe (PID: 6776)
Changes the autorun value in the registry
- OneDriveSetup.exe (PID: 7452)
SUSPICIOUS
Creates file in the systems drive root
- Client.exe (PID: 6688)
- Client.exe (PID: 6856)
- 123.exe (PID: 6844)
- Client.exe (PID: 5064)
- Client.exe (PID: 5244)
- 123.exe (PID: 3324)
- WerFault.exe (PID: 6192)
- WinRAR.exe (PID: 2152)
- WinRAR.exe (PID: 5144)
- firefox.exe (PID: 6140)
Executable content was dropped or overwritten
- Client.exe (PID: 6688)
- 123.exe (PID: 6844)
- OneDriveSetup.exe (PID: 7452)
Reads the date of Windows installation
- Client.exe (PID: 6688)
- Client.exe (PID: 5244)
- OneDrive.exe (PID: 6776)
- OneDriveSetup.exe (PID: 7452)
Reads security settings of Internet Explorer
- Client.exe (PID: 6688)
- Client.exe (PID: 5244)
- OneDrive.exe (PID: 6776)
- WinRAR.exe (PID: 2152)
- OneDriveSetup.exe (PID: 7412)
- OneDriveSetup.exe (PID: 7452)
Executes as Windows Service
- imgmmy.exe (PID: 6288)
Creates or modifies Windows services
- 123.exe (PID: 6844)
Executes application which crashes
- 123.exe (PID: 3324)
Changes Internet Explorer settings (feature browser emulation)
- OneDrive.exe (PID: 6776)
- OneDriveSetup.exe (PID: 7452)
Creates/Modifies COM task schedule object
- OneDrive.exe (PID: 6776)
- OneDriveSetup.exe (PID: 7452)
Checks Windows Trust Settings
- OneDrive.exe (PID: 6776)
- OneDriveSetup.exe (PID: 7412)
- OneDriveSetup.exe (PID: 7452)
Application launched itself
- WinRAR.exe (PID: 2152)
- OneDriveSetup.exe (PID: 7412)
Process drops legitimate windows executable
- OneDriveSetup.exe (PID: 7452)
The process creates files with name similar to system file names
- OneDriveSetup.exe (PID: 7452)
The process drops C-runtime libraries
- OneDriveSetup.exe (PID: 7452)
Creates a software uninstall entry
- OneDriveSetup.exe (PID: 7452)
INFO
Manual execution by a user
- Client.exe (PID: 6688)
- Client.exe (PID: 876)
- Client.exe (PID: 6672)
- Client.exe (PID: 5244)
- Build.exe (PID: 7052)
- OneDrive.exe (PID: 6776)
- WinRAR.exe (PID: 2152)
- firefox.exe (PID: 4784)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6380)
- firefox.exe (PID: 6140)
Checks supported languages
- Client.exe (PID: 6688)
- Client.exe (PID: 6856)
- 123.exe (PID: 6844)
- imgmmy.exe (PID: 6288)
- Client.exe (PID: 5244)
- Client.exe (PID: 5064)
- Build.exe (PID: 7052)
- OneDrive.exe (PID: 6776)
- 123.exe (PID: 3324)
- TextInputHost.exe (PID: 3880)
- OneDriveSetup.exe (PID: 7412)
- OneDriveSetup.exe (PID: 7452)
- FileSyncConfig.exe (PID: 7660)
- OneDrive.exe (PID: 7684)
Reads the computer name
- Client.exe (PID: 6688)
- 123.exe (PID: 6844)
- imgmmy.exe (PID: 6288)
- Client.exe (PID: 6856)
- Client.exe (PID: 5244)
- Client.exe (PID: 5064)
- Build.exe (PID: 7052)
- OneDrive.exe (PID: 6776)
- 123.exe (PID: 3324)
- OneDriveSetup.exe (PID: 7412)
- OneDriveSetup.exe (PID: 7452)
- TextInputHost.exe (PID: 3880)
- OneDrive.exe (PID: 7684)
Process checks computer location settings
- Client.exe (PID: 6688)
- Client.exe (PID: 5244)
- OneDrive.exe (PID: 6776)
- OneDriveSetup.exe (PID: 7452)
Reads CPU info
- imgmmy.exe (PID: 6288)
- OneDrive.exe (PID: 6776)
Reads Environment values
- imgmmy.exe (PID: 6288)
- OneDrive.exe (PID: 6776)
- OneDrive.exe (PID: 7684)
Create files in a temporary directory
- Client.exe (PID: 6856)
- OneDrive.exe (PID: 6776)
- OneDriveSetup.exe (PID: 7452)
Checks proxy server information
- WerFault.exe (PID: 6192)
- OneDrive.exe (PID: 6776)
Reads the software policy settings
- WerFault.exe (PID: 6192)
- OneDrive.exe (PID: 6776)
- OneDriveSetup.exe (PID: 7412)
- OneDriveSetup.exe (PID: 7452)
Creates files or folders in the user directory
- WerFault.exe (PID: 6192)
- OneDrive.exe (PID: 6776)
- OneDriveSetup.exe (PID: 7412)
- OneDriveSetup.exe (PID: 7452)
- OneDrive.exe (PID: 7684)
VMProtect protector has been detected
- imgmmy.exe (PID: 6288)
Reads Microsoft Office registry keys
- OneDrive.exe (PID: 6776)
- firefox.exe (PID: 6140)
- OneDrive.exe (PID: 7684)
Reads the machine GUID from the registry
- OneDrive.exe (PID: 6776)
- OneDriveSetup.exe (PID: 7412)
- OneDriveSetup.exe (PID: 7452)
- OneDrive.exe (PID: 7684)
Reads the time zone
- OneDrive.exe (PID: 6776)
Application launched itself
- firefox.exe (PID: 4784)
- firefox.exe (PID: 6140)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 5144)
- firefox.exe (PID: 6140)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
173
Monitored processes
32
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 876 | "C:\Users\admin\Desktop\Client.exe" | C:\Users\admin\Desktop\Client.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2152 | "C:\Program Files\WinRAR\WinRAR.exe" a -ep1 -scul -r0 -iext -- Client.rar C:\Client.exe | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3324 | "C:\123.exe" | C:\123.exe | Client.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: HIGH Description: Server Exit code: 3221225477 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 3880 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 4064 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2904 -childID 1 -isForBrowser -prefsHandle 2896 -prefMapHandle 2892 -prefsLen 30953 -prefMapSize 244343 -jsInitHandle 1232 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {8a77bc7e-2561-45a0-b079-133c059539d5} 6140 "\\.\pipe\gecko-crash-server-pipe.6140" 27f42953150 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 4784 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 5064 | "C:\Client.exe" | C:\Client.exe | — | Client.exe | |||||||||||
User: admin Company: 2011火狐DDOS改进版 Integrity Level: HIGH Description: QQ:528988114 Exit code: 2 Version: 3, 0, 0, 1 Modules
| |||||||||||||||
| 5144 | "C:\Program Files\WinRAR\WinRAR.exe" -elevate2152 | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: HIGH Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 5144 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5392 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 5384 -prefMapHandle 5380 -prefsLen 34713 -prefMapSize 244343 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {8abf7001-e7b1-4b75-acf6-f8a367ad2ff0} 6140 "\\.\pipe\gecko-crash-server-pipe.6140" 27f45071510 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 5244 | "C:\Users\admin\Desktop\Client.exe" | C:\Users\admin\Desktop\Client.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
50 105
Read events
49 026
Write events
513
Delete events
566
Modification events
| (PID) Process: | (6380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\paranor.7z | |||
| (PID) Process: | (6380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6688) Client.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6688) Client.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
232
Suspicious files
224
Text files
440
Unknown types
23
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6192 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_123.exe_4372bed4a7a799395bdccaa16bada5f78e264a19_62d46436_40892e3b-4851-43f4-84f6-4afa788fab08\Report.wer | — | |
MD5:— | SHA256:— | |||
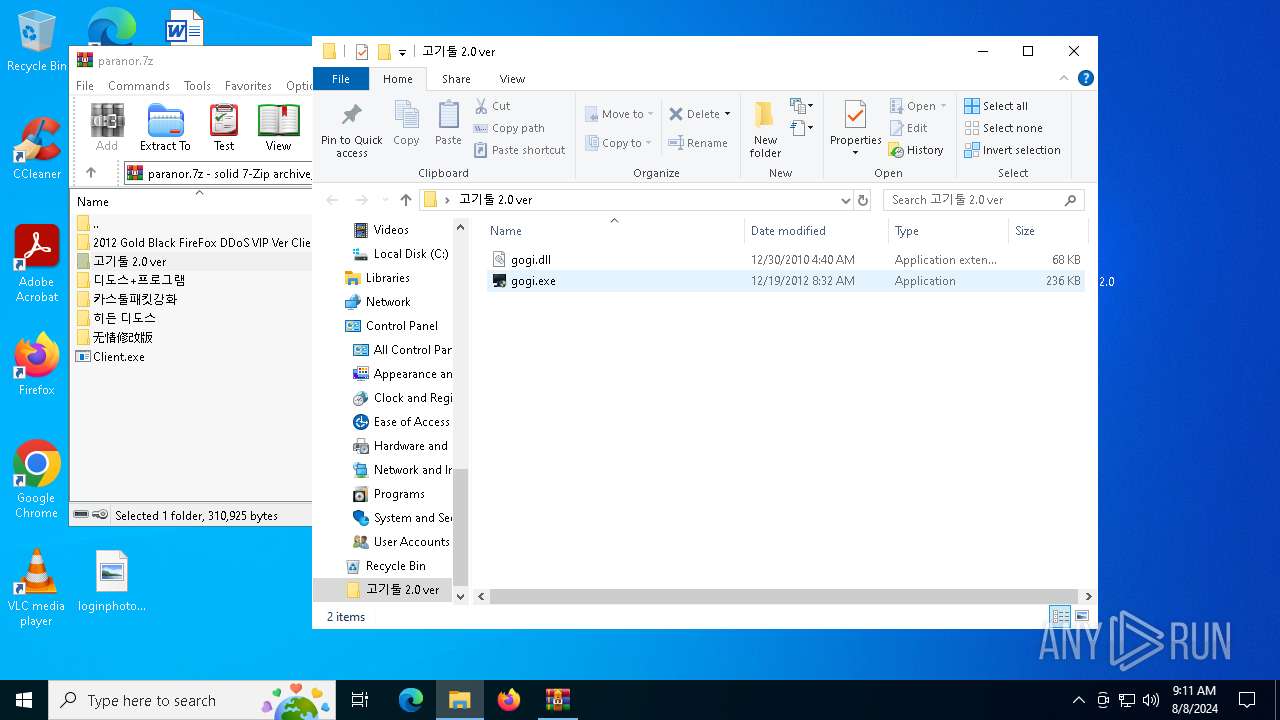
| 6380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6380.8494\고기툴 2.0 ver\gogi.dll | executable | |
MD5:75981EC1E63555A0AF71F72268D133CF | SHA256:4D1C67472BC1C788166732447E9AAC102486FD908CBC7E125D3878254BCE9D41 | |||
| 6856 | Client.exe | C:\Users\admin\AppData\Local\Temp\~DF359C2DED60F45FFE.TMP | binary | |
MD5:81EF5D2C0D6C26336B8A2E68F74E3D74 | SHA256:E74B5795288BF7006CCC08AD4BCBA7F4B7A4FACF55405C93653F2F331AF6184E | |||
| 6380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6380.10886\카스툴패킷강화\카스툴패킷강화\Client.ini | ini | |
MD5:2CF1B0C6F860492C69CDFEC79F7073DF | SHA256:879B2B0E0A84A5A7781B58F7B357DA6532E0A854FF33C848CA47835EAF17BA6F | |||
| 6844 | 123.exe | C:\Windows\SysWOW64\imgmmy.exe | executable | |
MD5:FEC169E05B7AD3EBACB6CD66D4E57100 | SHA256:685D384CEB439C018AA259345F75E5A28CB3CCCE61772E4AB556967519F083D2 | |||
| 6380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6380.9077\디도스+프로그램\Client.exe | executable | |
MD5:C4C009CDCE24A619519E668D734BCF73 | SHA256:3F4A0C0938A23DD5EC7D81246C645609749D1DC3DF8260957002633D623C58B4 | |||
| 6380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6380.8494\고기툴 2.0 ver\gogi.exe | executable | |
MD5:01203D9FBF08ED330EC5CBBEF0FD1F90 | SHA256:80B7FE675F6C74FDF84875C83B50B8F80D9A1C64B213E908FDF5057B60F377CE | |||
| 6380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6380.9077\디도스+프로그램\인덱스 아리아.txt | text | |
MD5:0C1EEAEC031EFD80ED5D7429BDE5F9E4 | SHA256:F5C2C798E6859362A47BB352C10EBD2896AE9E9BBDCDC71FC5A81C6F5EE500CC | |||
| 6380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6380.9077\디도스+프로그램\제품설명.txt | text | |
MD5:6B60E61FDBCAC4CBAB187E429CCE3E18 | SHA256:2B7193DAAE6120BD0833977F29FB0B3330BE60D60A3FE83FF098A0D32A13D631 | |||
| 6688 | Client.exe | C:\Client.exe | executable | |
MD5:724C19A9D89B603F0AC73EC213BF89D5 | SHA256:550F375209715DD22D9EBC296F4C8A3E7435F54D37B12B79E18EDF7F4D1289DD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
35
TCP/UDP connections
113
DNS requests
138
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4920 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4920 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6896 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6944 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6776 | OneDrive.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6776 | OneDrive.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
6140 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
6140 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
6140 | firefox.exe | POST | 200 | 95.101.54.112:80 | http://r11.o.lencr.org/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4040 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5116 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5336 | SearchApp.exe | 92.123.104.36:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4920 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
mp662002.codns.com |
| whitelisted |