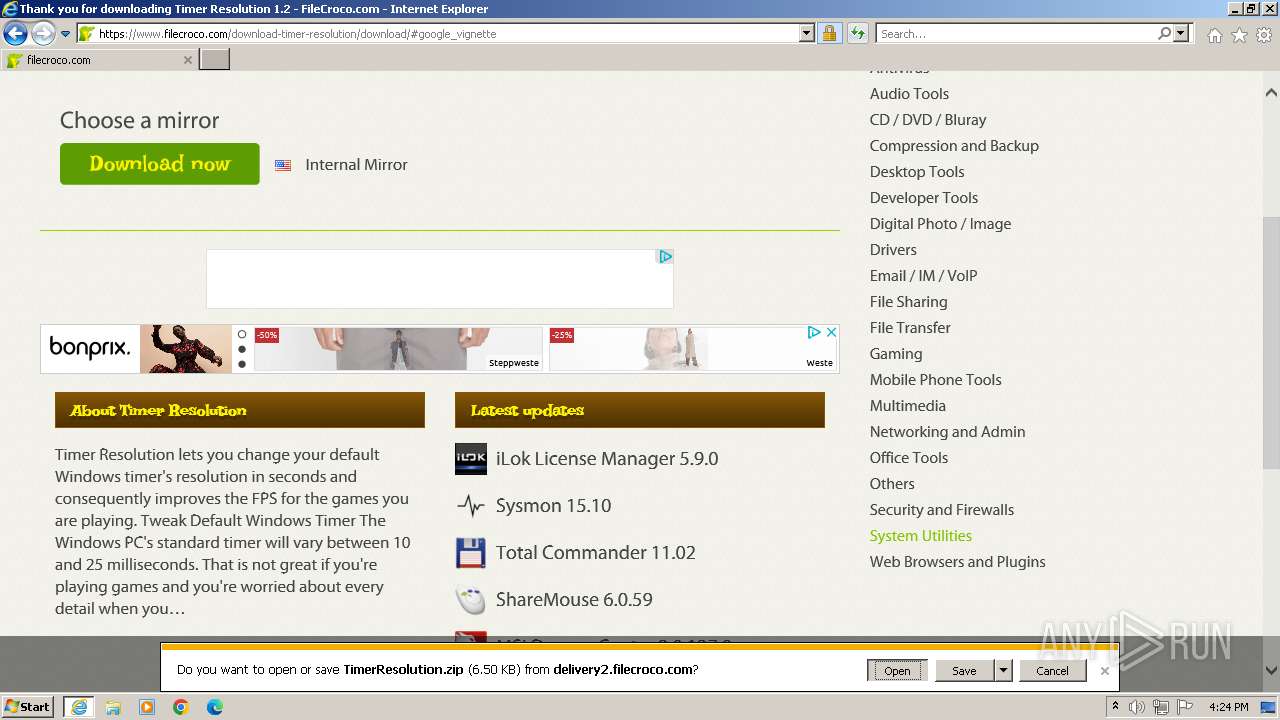
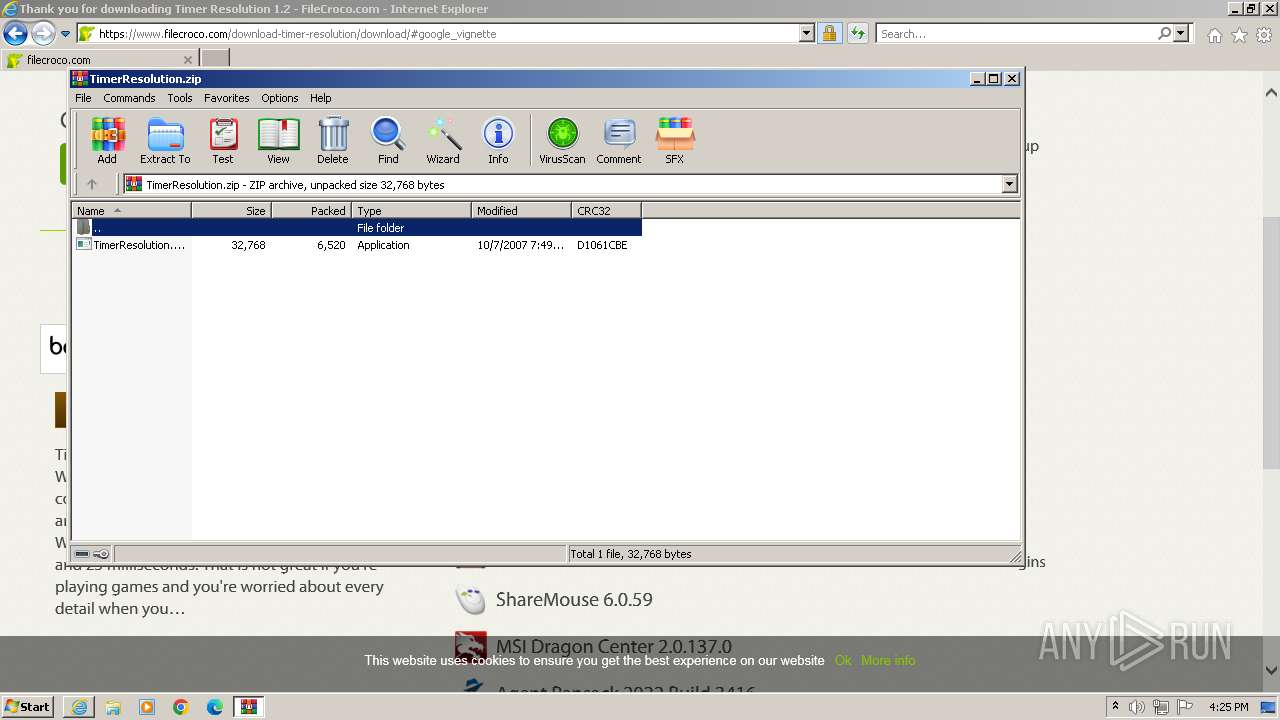
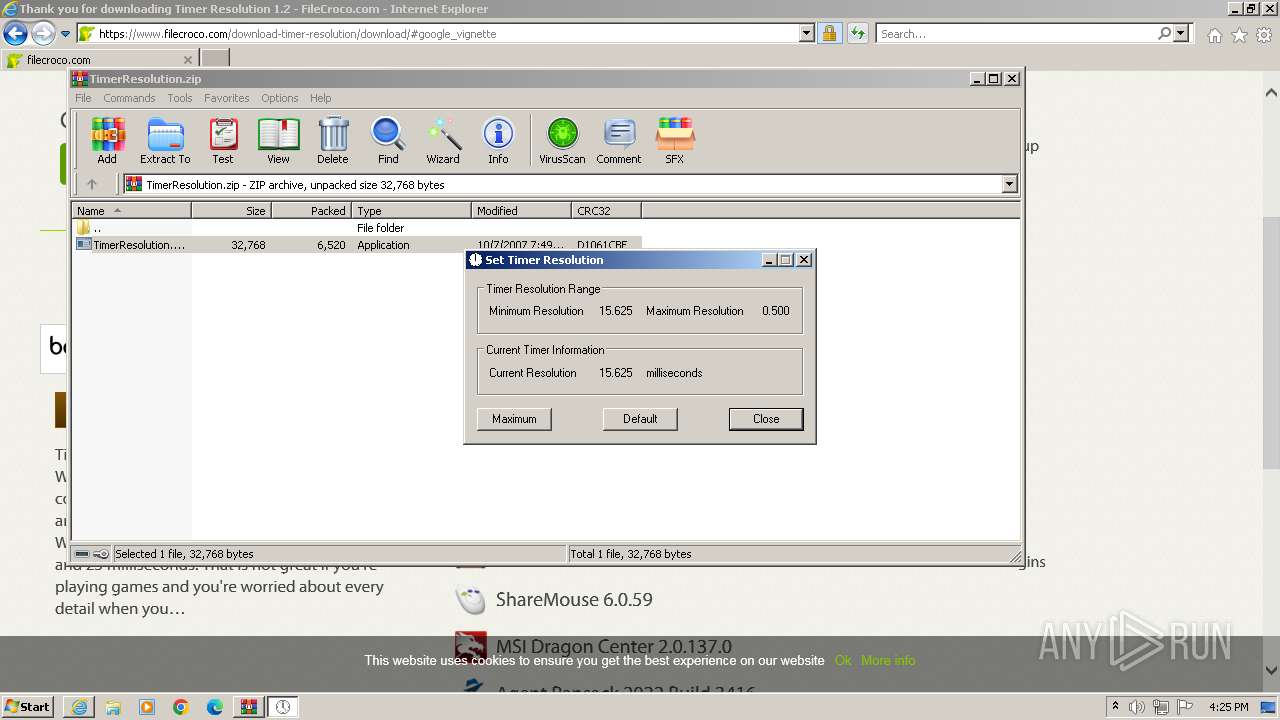
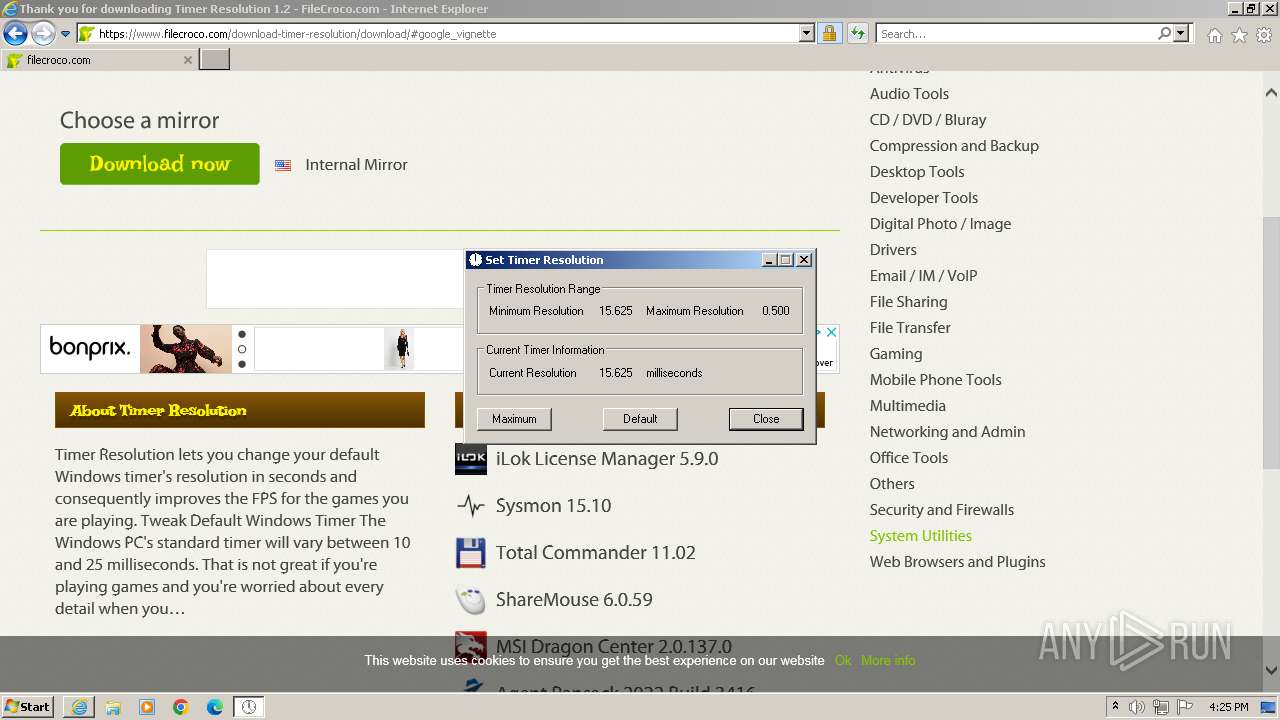
| URL: | https://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=&ved=2ahUKEwjQo6HC67mCAxXYXfEDHcxWDQAQFnoECBUQAQ&url=https%3A%2F%2Fwww.filecroco.com%2Fdownload-timer-resolution%2F&usg=AOvVaw2638nveZZI32lfOolCWTsR&opi=89978449 |
| Full analysis: | https://app.any.run/tasks/bee0b16d-bf49-4a10-ae3e-40eb0c0cce0c |
| Verdict: | Malicious activity |
| Analysis date: | November 10, 2023, 16:24:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| SHA1: | D13F199F29FC37CFFA9CE039A12EAC1742A6026E |
| SHA256: | 30EDE4696B06F2F135B781317451F99E5114621A3C60F24DFCF1DF9F5A485F42 |
| SSDEEP: | 6:2OLI2sq+w5N6eESFYNRR3zDXKRL/XEIzXESD2A9xJaOga:2V2/NTEuY5vXKRLXrXEa2cxoM |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 3196)
Checks supported languages
- wmpnscfg.exe (PID: 4072)
- TimerResolution.exe (PID: 1856)
Reads the computer name
- wmpnscfg.exe (PID: 4072)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 4072)
Manual execution by a user
- wmpnscfg.exe (PID: 4072)
The process uses the downloaded file
- iexplore.exe (PID: 3196)
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 3764)
- WinRAR.exe (PID: 1604)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1604)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
41
Monitored processes
6
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1604 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\TimerResolution.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | iexplore.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
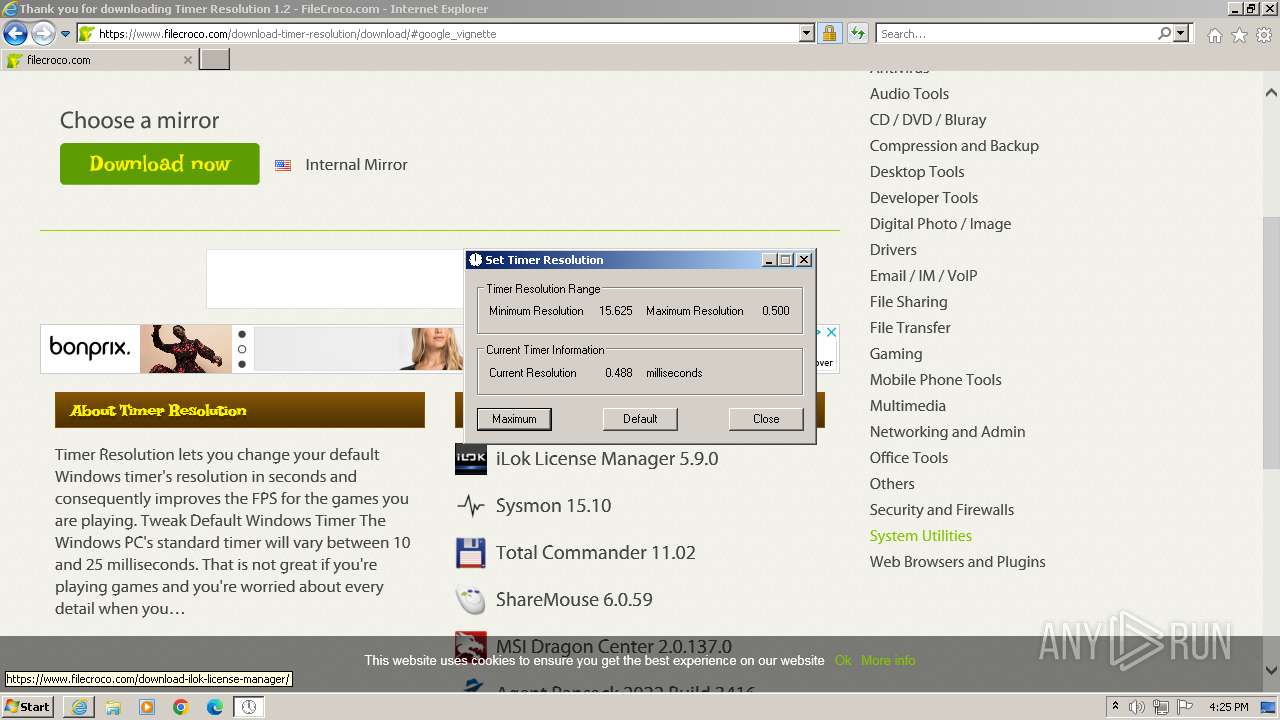
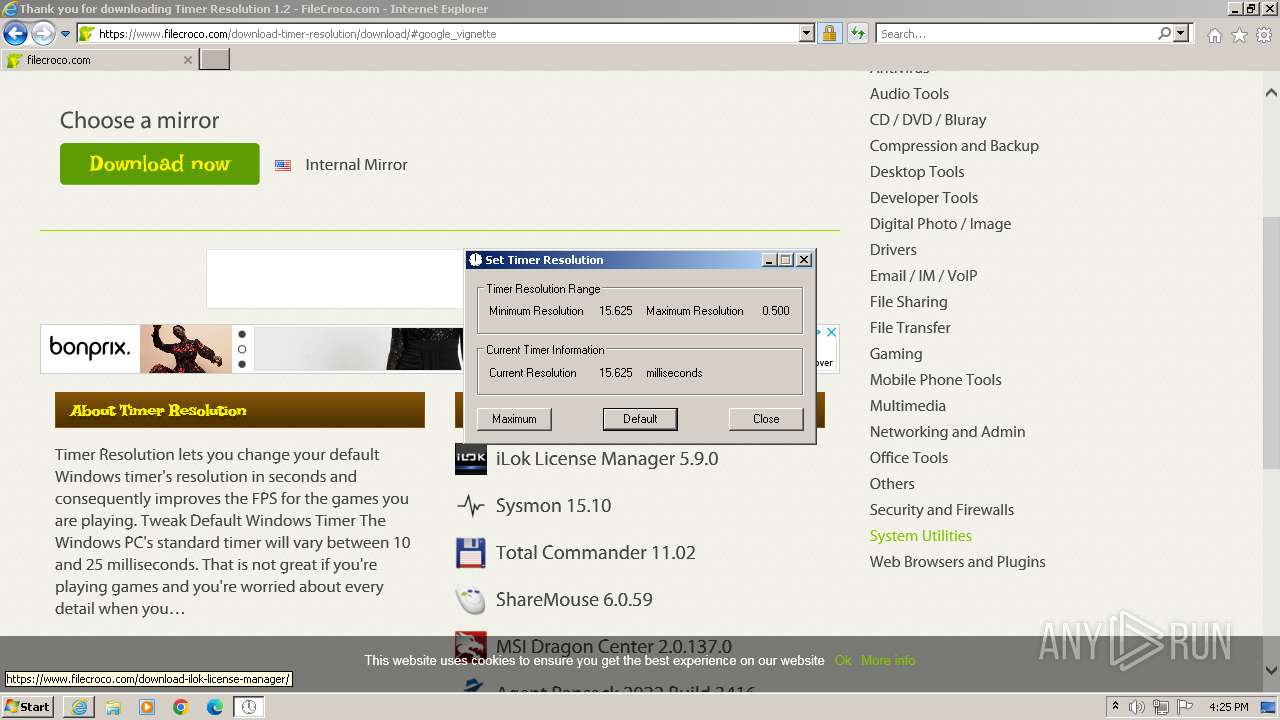
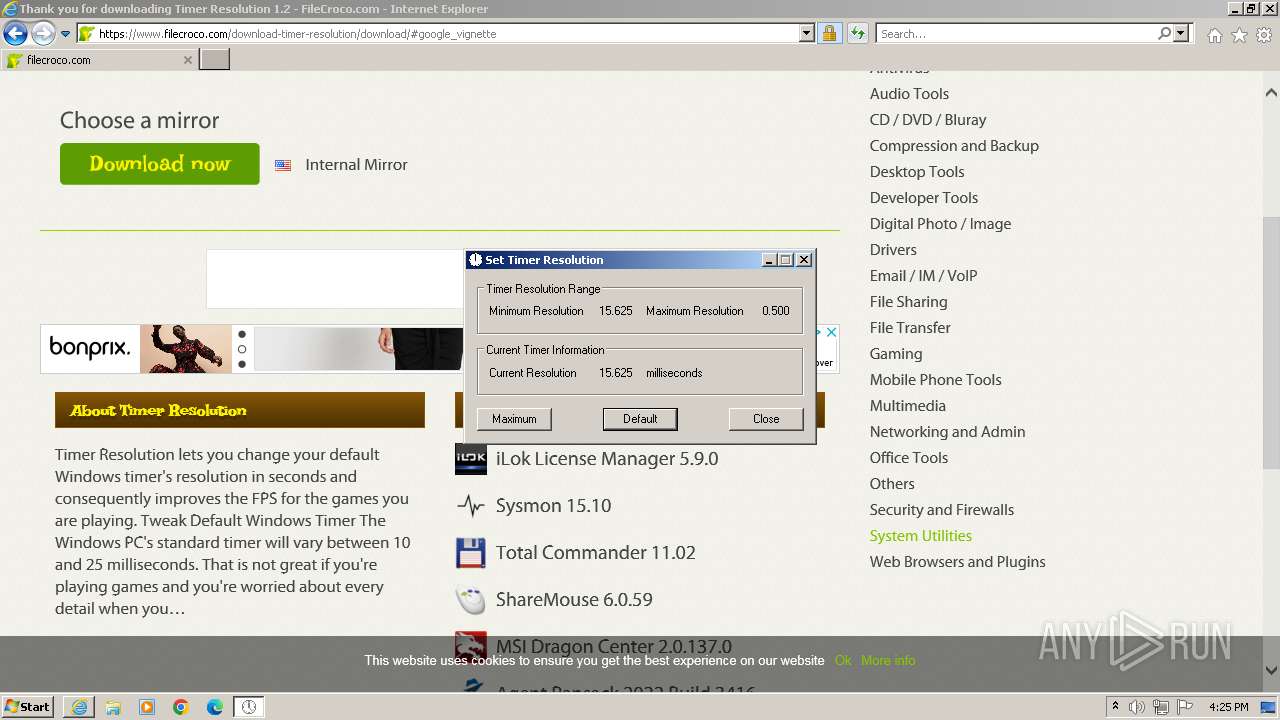
| 1856 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1604.48515\TimerResolution.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1604.48515\TimerResolution.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: TimerResolution Exit code: 2 Version: 1, 2, 0, 1 Modules
| |||||||||||||||
| 2896 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3196 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3196 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=&ved=2ahUKEwjQo6HC67mCAxXYXfEDHcxWDQAQFnoECBUQAQ&url=https%3A%2F%2Fwww.filecroco.com%2Fdownload-timer-resolution%2F&usg=AOvVaw2638nveZZI32lfOolCWTsR&opi=89978449" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3764 | C:\Windows\system32\Macromed\Flash\FlashUtil32_32_0_0_453_ActiveX.exe -Embedding | C:\Windows\System32\Macromed\Flash\FlashUtil32_32_0_0_453_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 32.0 r0 Exit code: 0 Version: 32,0,0,453 Modules
| |||||||||||||||
| 4072 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
35 499
Read events
35 362
Write events
132
Delete events
5
Modification events
| (PID) Process: | (3196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3196) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
1
Suspicious files
132
Text files
186
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2896 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 2896 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:96E8965A347D660D8B3B2C08706DA7BD | SHA256:81960561F7F0E9176B7B454DF74933D2A62003EFED0CE6049DD33BD08244BEEF | |||
| 2896 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:AC89A852C2AAA3D389B2D2DD312AD367 | SHA256:0B720E19270C672F9B6E0EC40B468AC49376807DE08A814573FE038779534F45 | |||
| 2896 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\T917RV2D.txt | text | |
MD5:882F820FAF4313C9BA0F04F3EF34F95C | SHA256:2A4BD2CAEEB76E91772D6CE5B9EF010BCA8A3E55FEBA618100F7654BADBE297C | |||
| 2896 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A16C6C16D94F76E0808C087DFC657D99_5B226F2301FD399CF34ABA67B4DC6AC8 | binary | |
MD5:5A25C2C37DE1D82E4320C349B998631C | SHA256:552E59E64A1BB4BA2A08D9F1A94F5ED9839834EA748A784ED89524895797D8CE | |||
| 2896 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A16C6C16D94F76E0808C087DFC657D99_5B226F2301FD399CF34ABA67B4DC6AC8 | binary | |
MD5:B72B6F52E25D1F16D178CABF196F8C74 | SHA256:AACE14D790B4F446B7EF23FBB243279DFDBBC3EBF0E9ECCDA69E44DEA521FF21 | |||
| 2896 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:80E11CB29B97B016EB35D0EBCAA0B8CA | SHA256:24D149FE8DD0086ED90F26D69AA1060020E6F414D1377B18AC8DB73E0121C1C3 | |||
| 2896 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\postratings-css-383046c4039e44bdfd68dd3beed92926[1].css | text | |
MD5:79ACBB2CCED848C9F9BA08B2AC790362 | SHA256:3D138B2397BC5493F655D6851C415468642419DE9F335DE648093C8D8A1D407C | |||
| 2896 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\1UMH9XLZ.txt | text | |
MD5:C15C8D86F7FEDBE5A4777BCD09675B2D | SHA256:BB0B8015AF4121F87921B7E1B8E8F9FCAD6929E7194D60CE80CC2DE540EE768B | |||
| 2896 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\url[1].htm | html | |
MD5:0DBECCC4AB9B657D4EFDB359F4CE3142 | SHA256:F3D21380B698A720B66DA21F4852F77430FE4AAE957461AF9F6EB7F7F4CE33FD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
59
TCP/UDP connections
155
DNS requests
67
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2896 | iexplore.exe | GET | 200 | 8.241.121.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d1270903ad75d1e2 | unknown | compressed | 4.66 Kb | unknown |
2896 | iexplore.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
2896 | iexplore.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
2896 | iexplore.exe | GET | 200 | 8.241.121.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?822bc3f82f78ba1a | unknown | compressed | 4.66 Kb | unknown |
2896 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | binary | 1.42 Kb | unknown |
2896 | iexplore.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
2896 | iexplore.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDVmzu%2BcVBN4gnIj8OT7hC4 | unknown | binary | 472 b | unknown |
2896 | iexplore.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEGVmiIEBSm6bEqwxkt71qts%3D | unknown | binary | 471 b | unknown |
2896 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | binary | 471 b | unknown |
3196 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2896 | iexplore.exe | 8.241.121.254:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2896 | iexplore.exe | 142.250.186.163:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
2896 | iexplore.exe | 188.114.97.3:443 | www.filecroco.com | CLOUDFLARENET | NL | unknown |
2896 | iexplore.exe | 172.217.18.2:443 | pagead2.googlesyndication.com | GOOGLE | US | whitelisted |
2896 | iexplore.exe | 192.0.73.2:443 | secure.gravatar.com | AUTOMATTIC | US | whitelisted |
2896 | iexplore.exe | 23.45.238.53:443 | s7.addthis.com | AKAMAI-AS | DE | unknown |
2896 | iexplore.exe | 104.16.57.101:443 | static.cloudflareinsights.com | CLOUDFLARENET | — | unknown |
2896 | iexplore.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | unknown |
2896 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.filecroco.com |
| unknown |
pagead2.googlesyndication.com |
| whitelisted |
secure.gravatar.com |
| whitelisted |
s7.addthis.com |
| whitelisted |
static.cloudflareinsights.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |