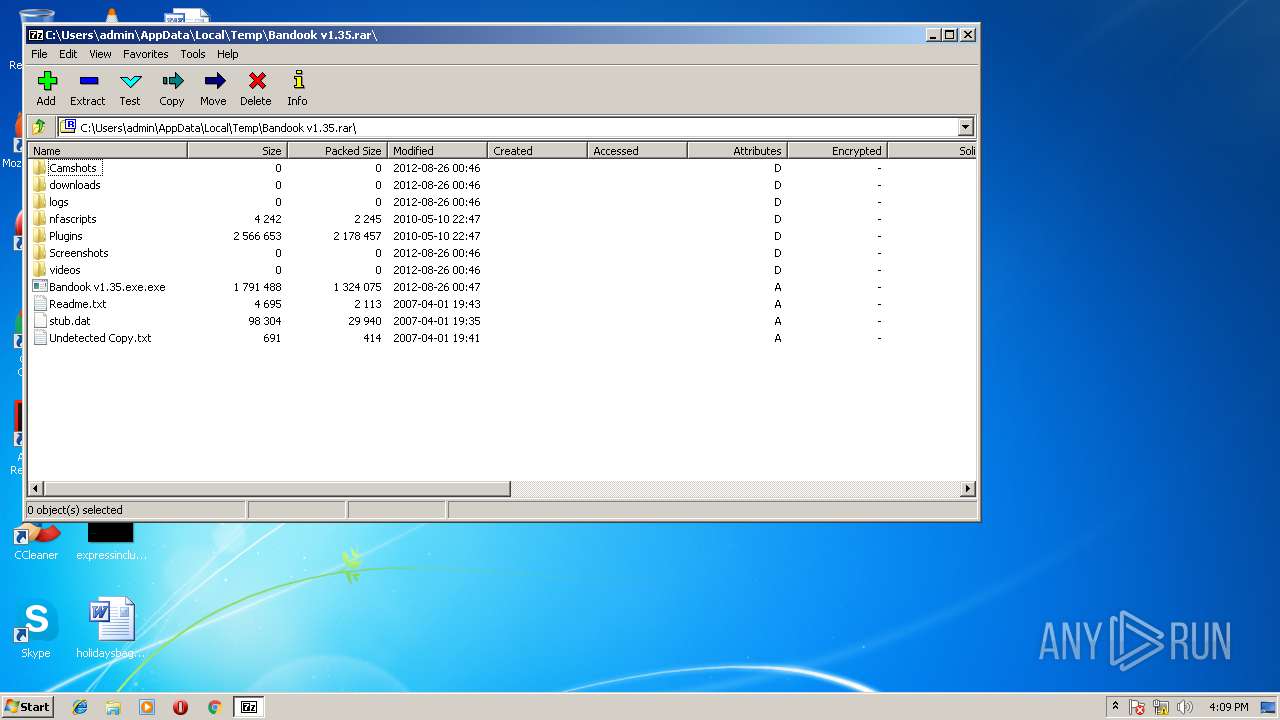
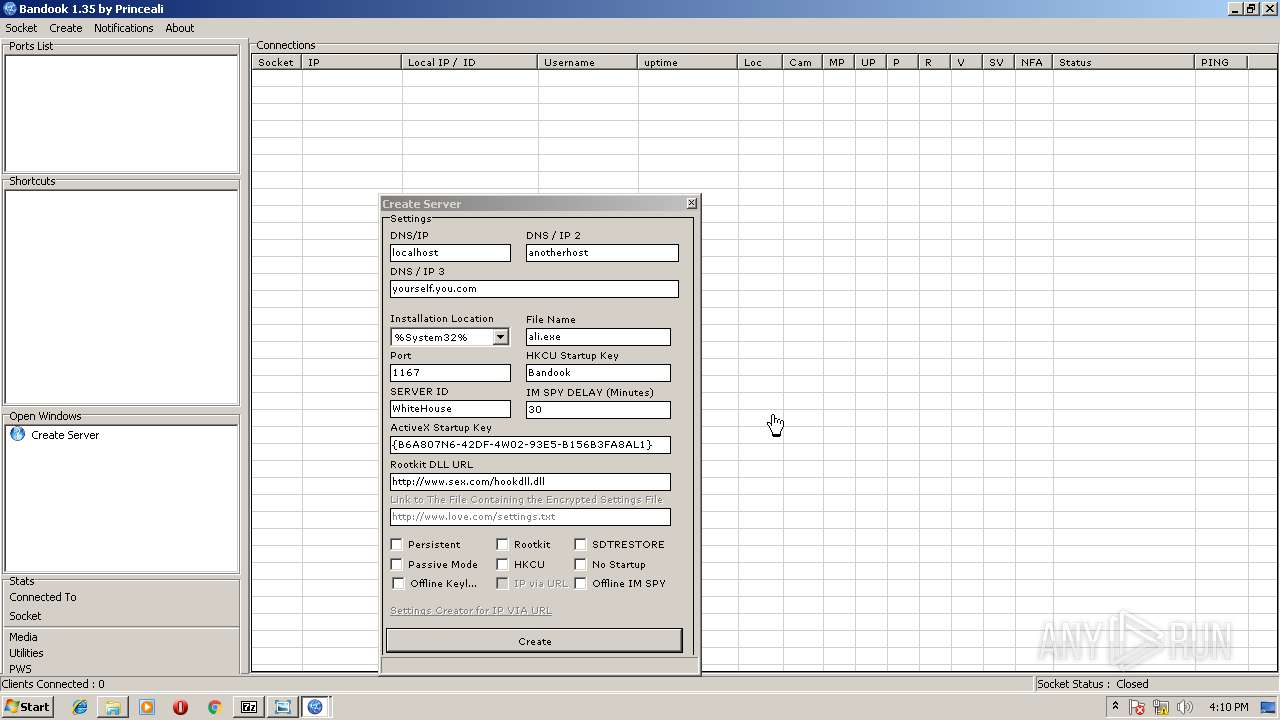
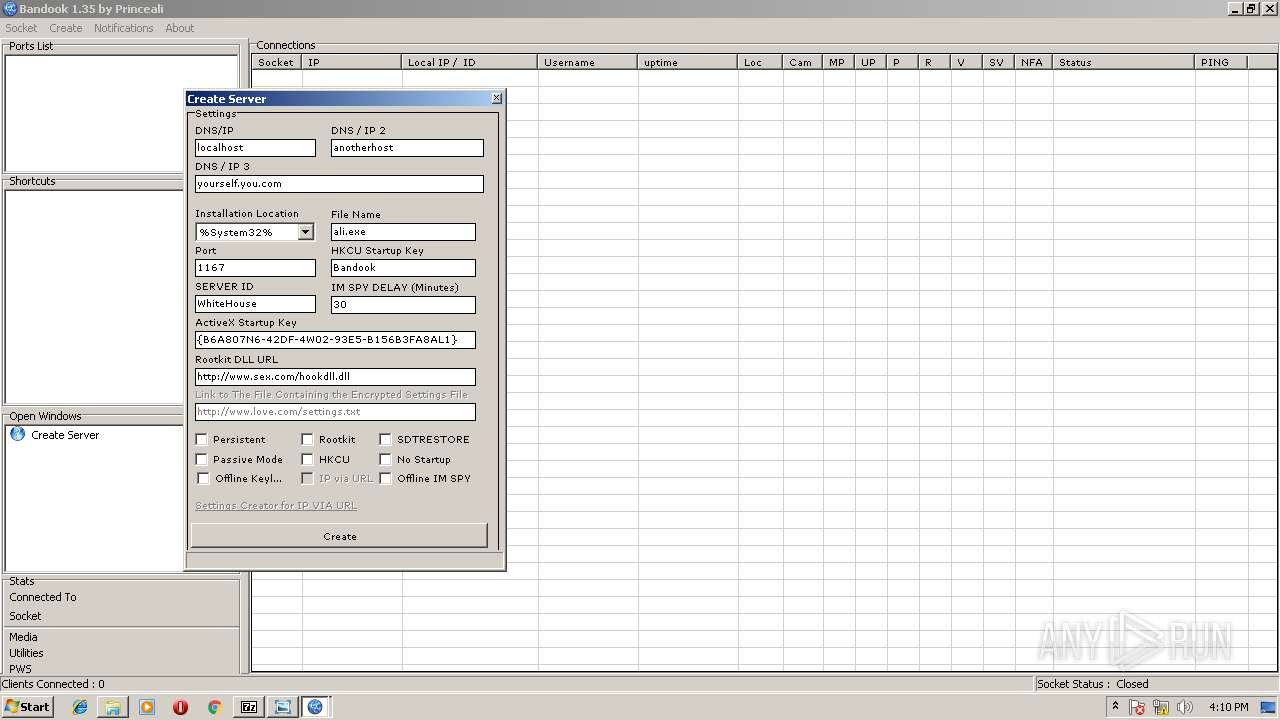
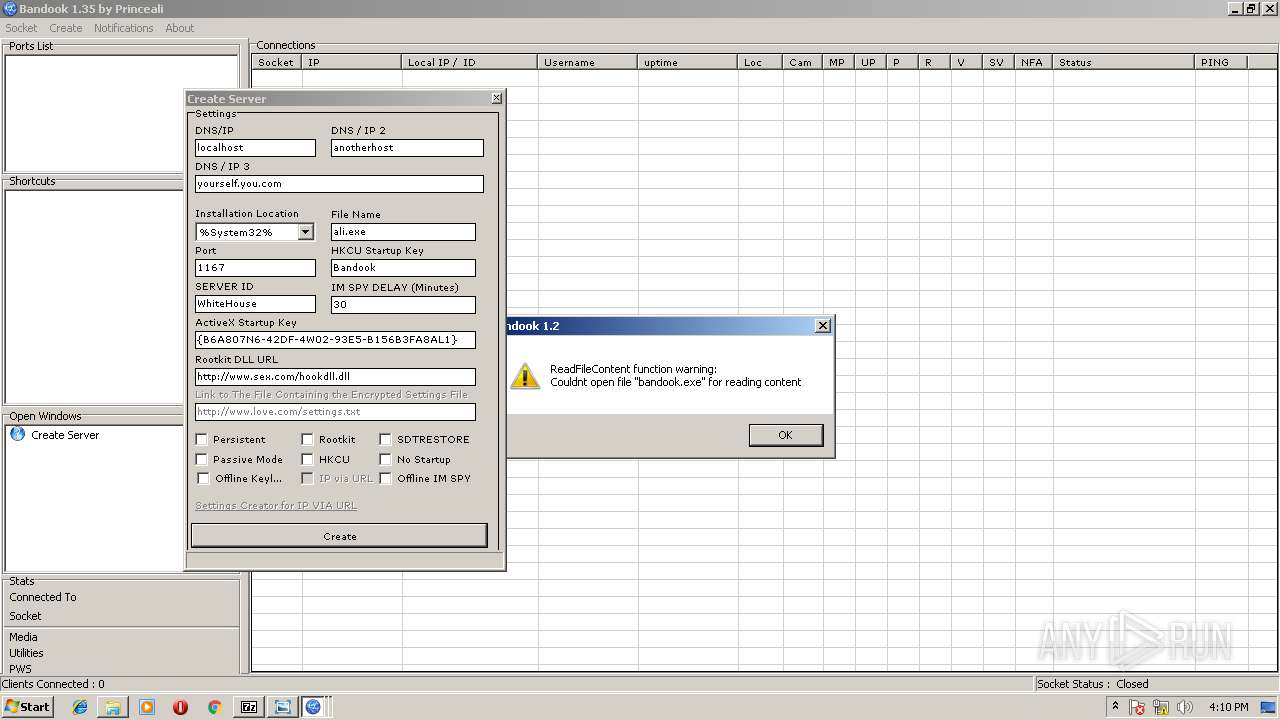
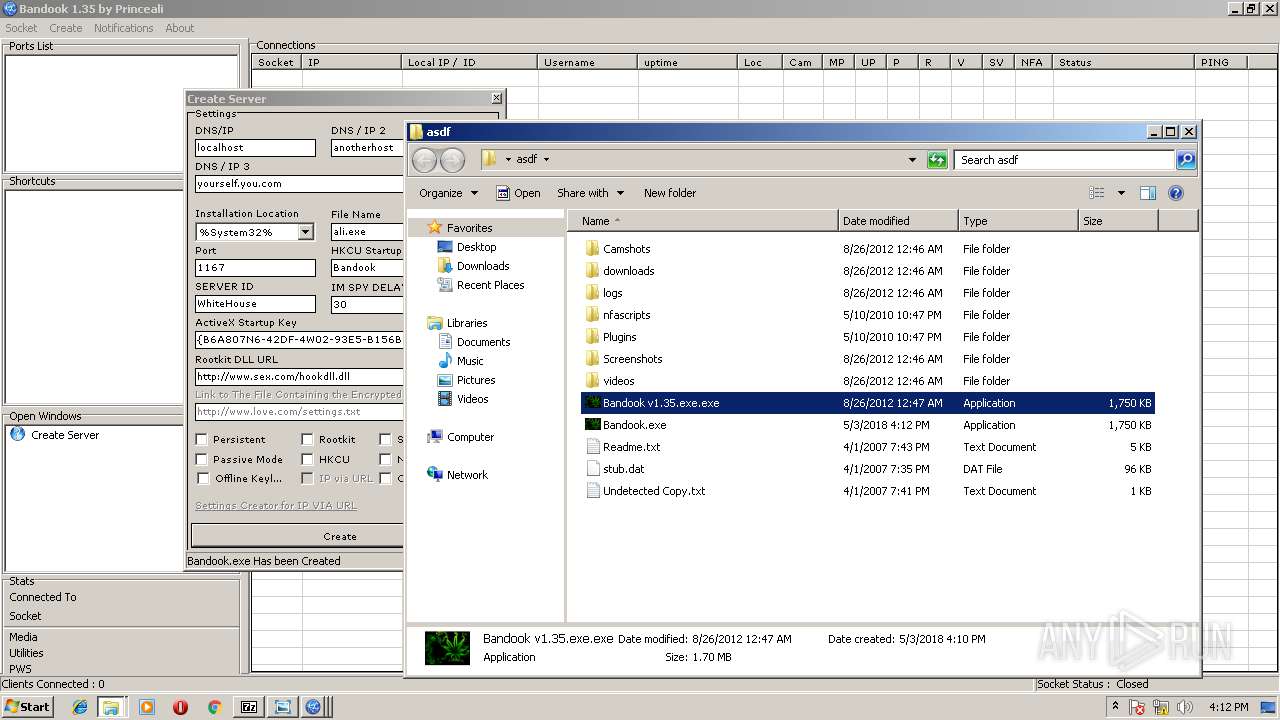
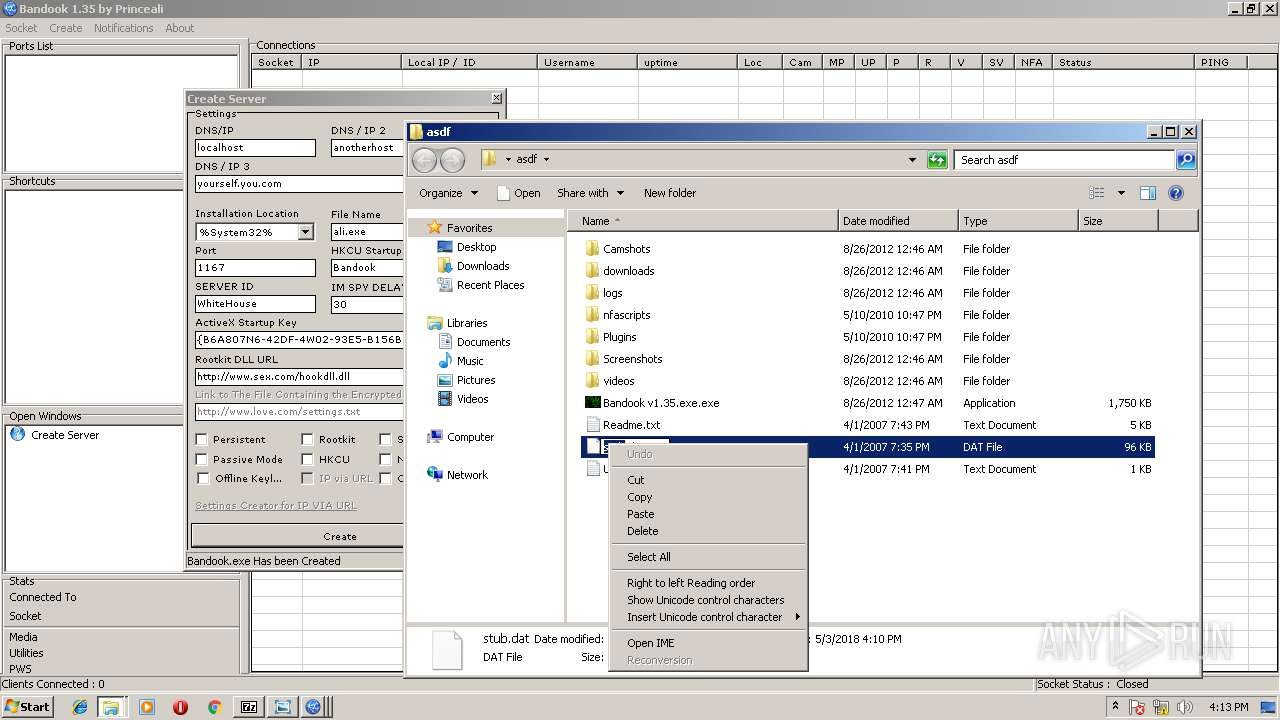
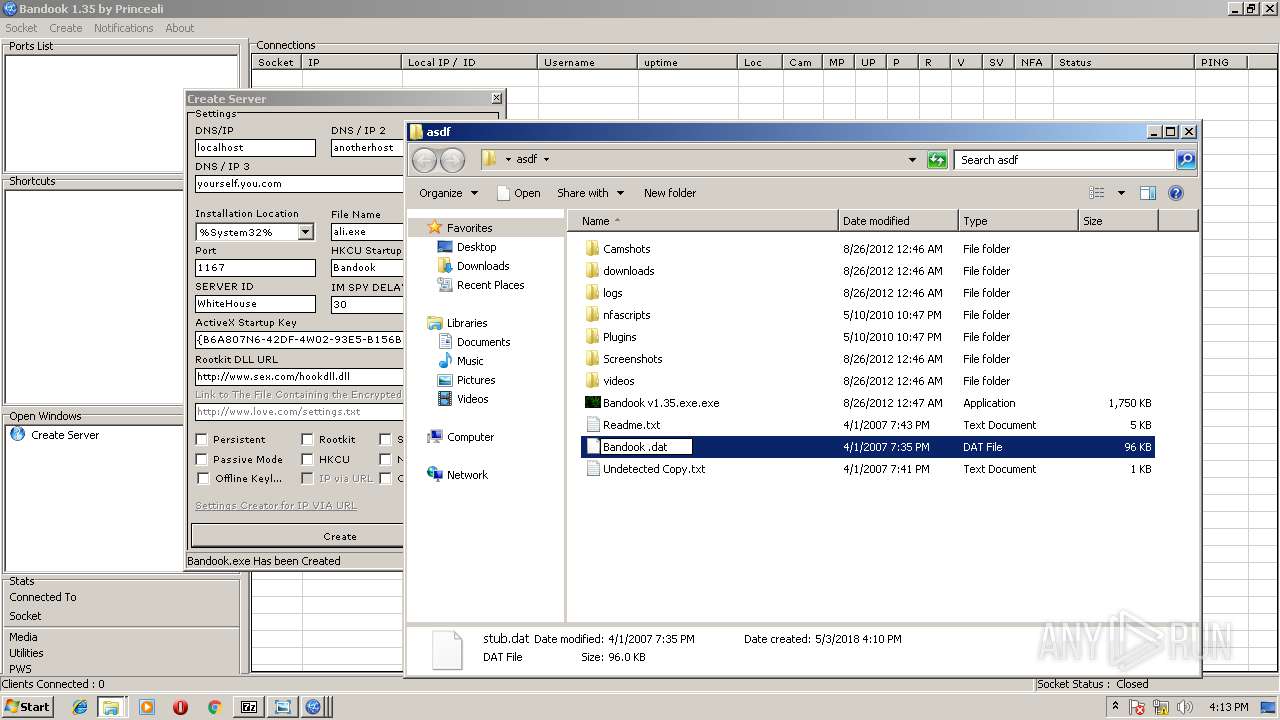
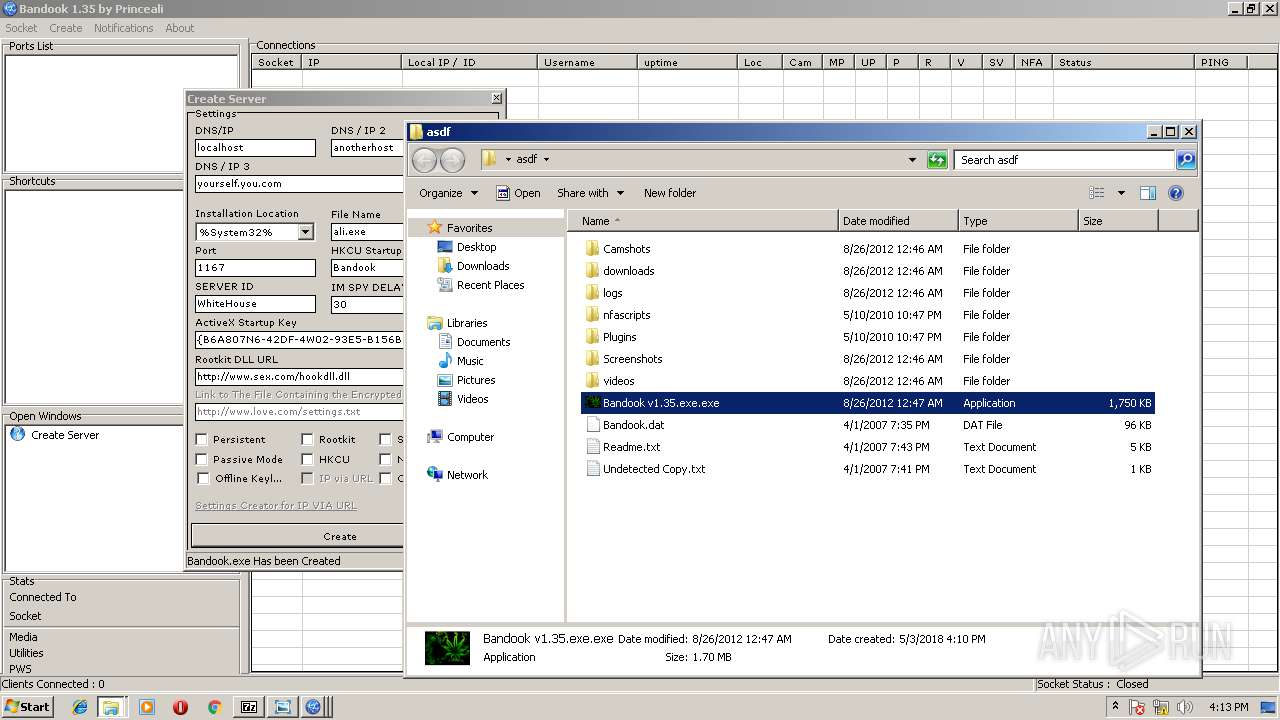
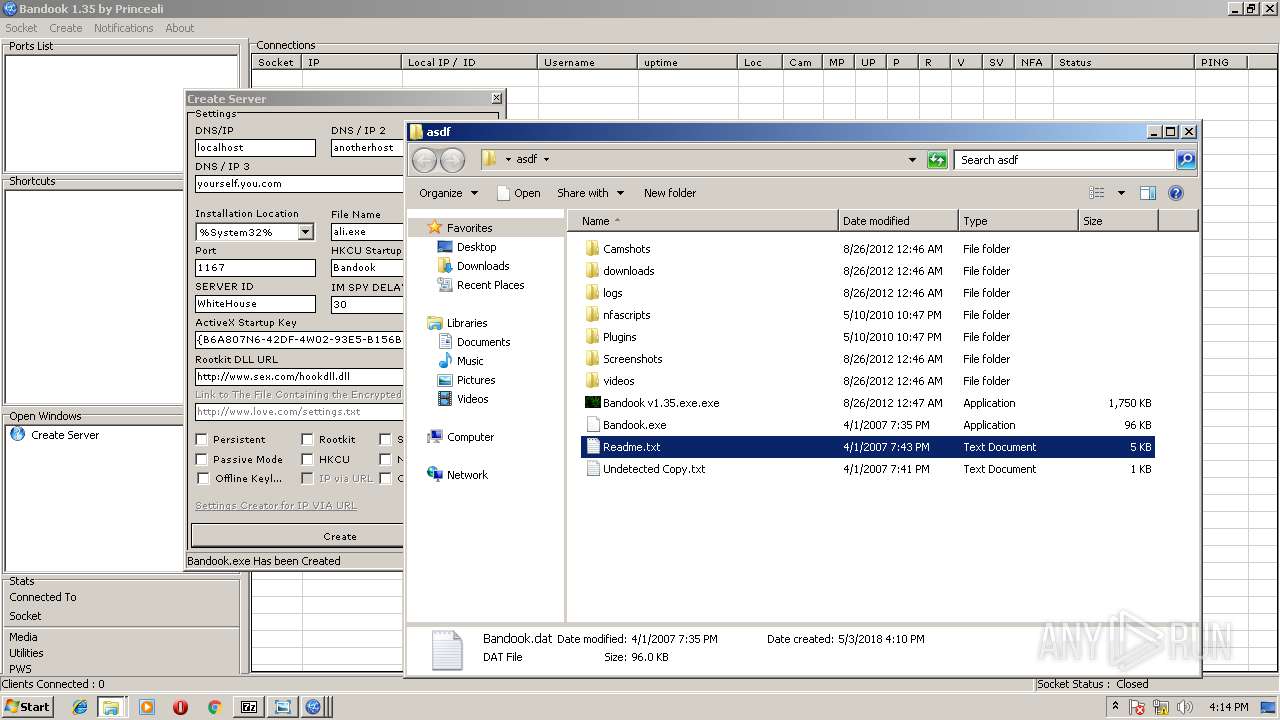
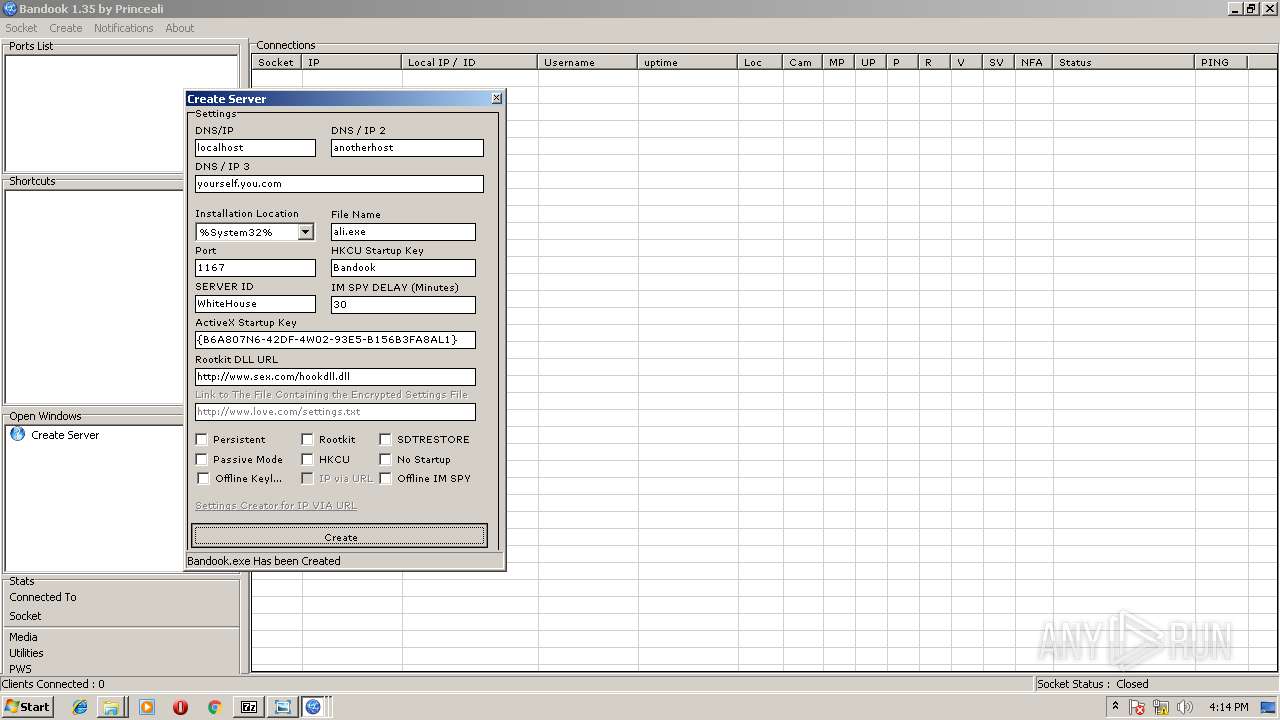
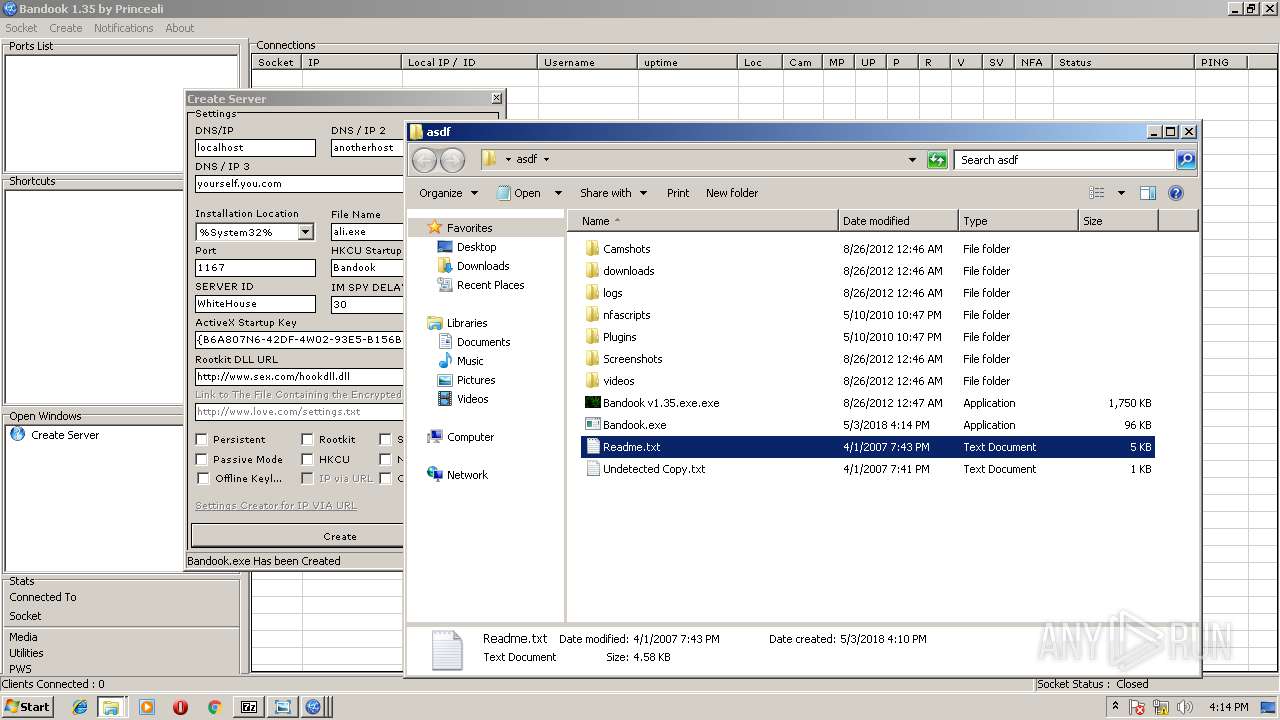
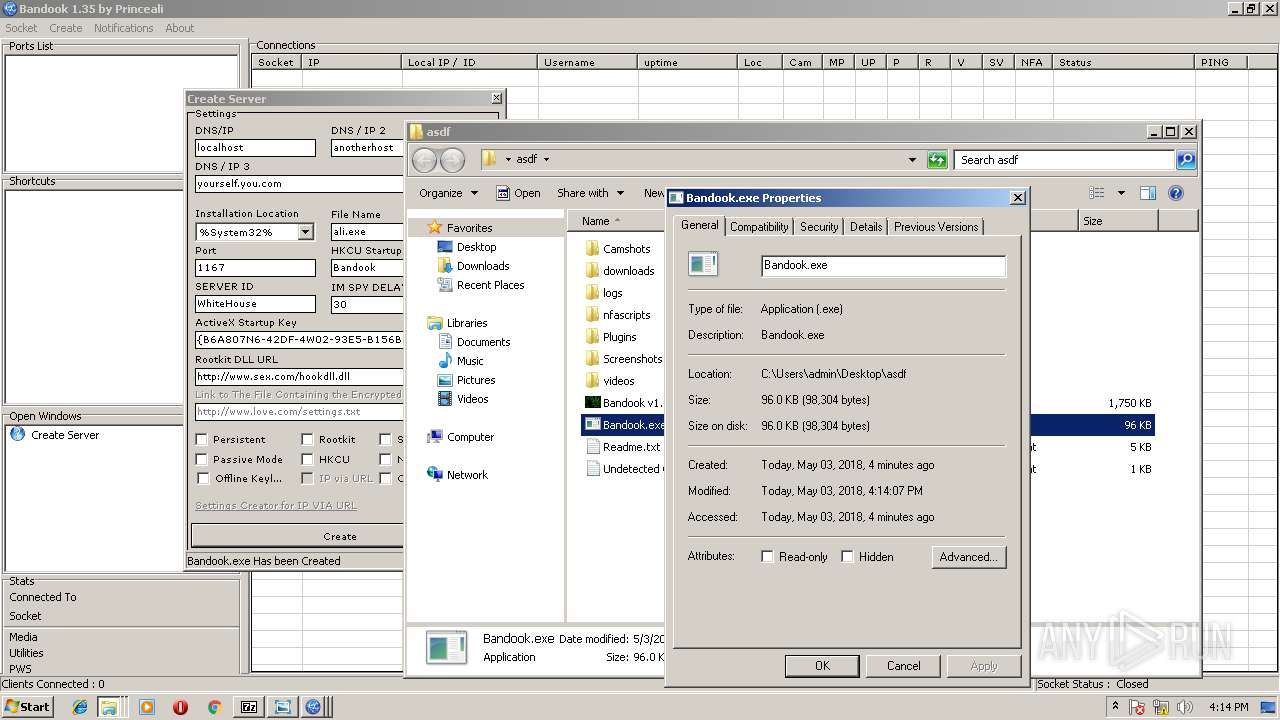
| File name: | Bandook v1.35.rar |
| Full analysis: | https://app.any.run/tasks/8f1a0c9c-0aca-47e5-8de4-b0939e95e31f |
| Verdict: | Malicious activity |
| Analysis date: | May 03, 2018, 15:09:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 425BBD854E4EB273D101DF90862617D2 |
| SHA1: | C9AEBE6B1D5F1D6BEDF4188FA6B980AE3A01A2C1 |
| SHA256: | 30EB4DC3C46CECEBA84384B6A89DA8D12CD00D8D9BC9E4E1CBC97610FC496BE1 |
| SSDEEP: | 98304:Ign0wDXWq+Ijscsz9hGDGPTFccqYEWeX4uLDW5s7LH:z0wDXWrCDGPpccTCIuLDW5QH |
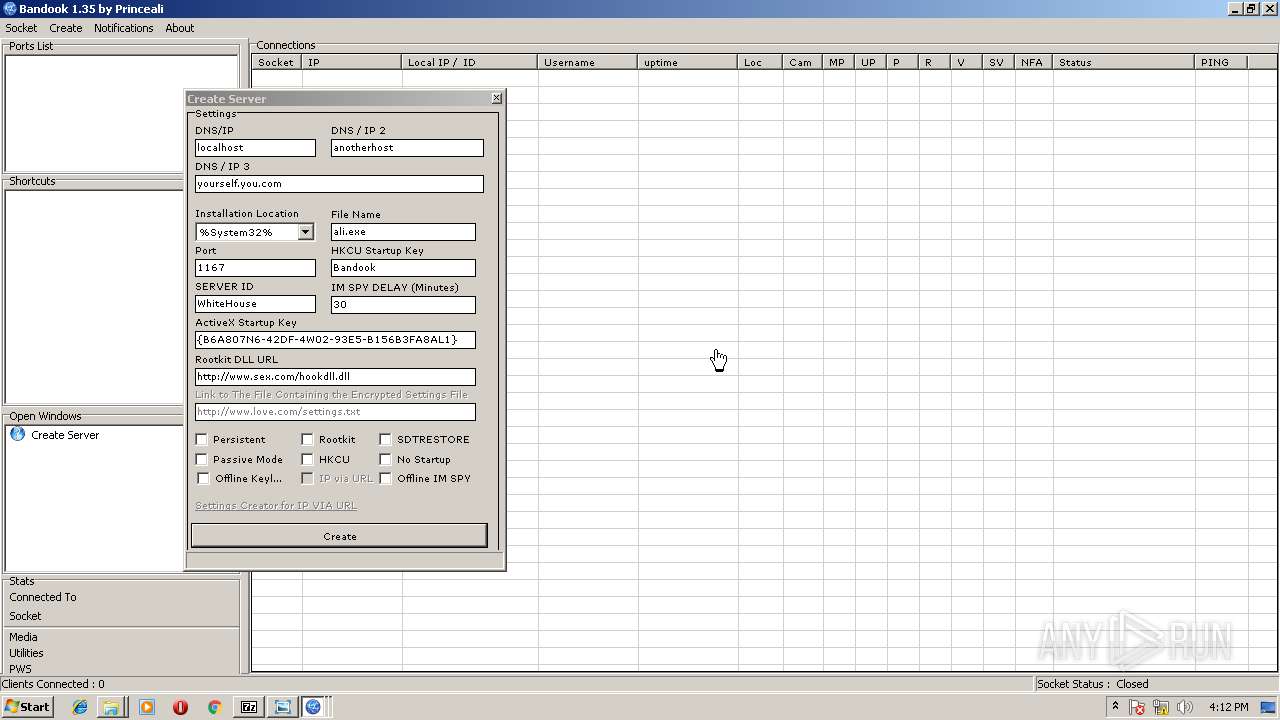
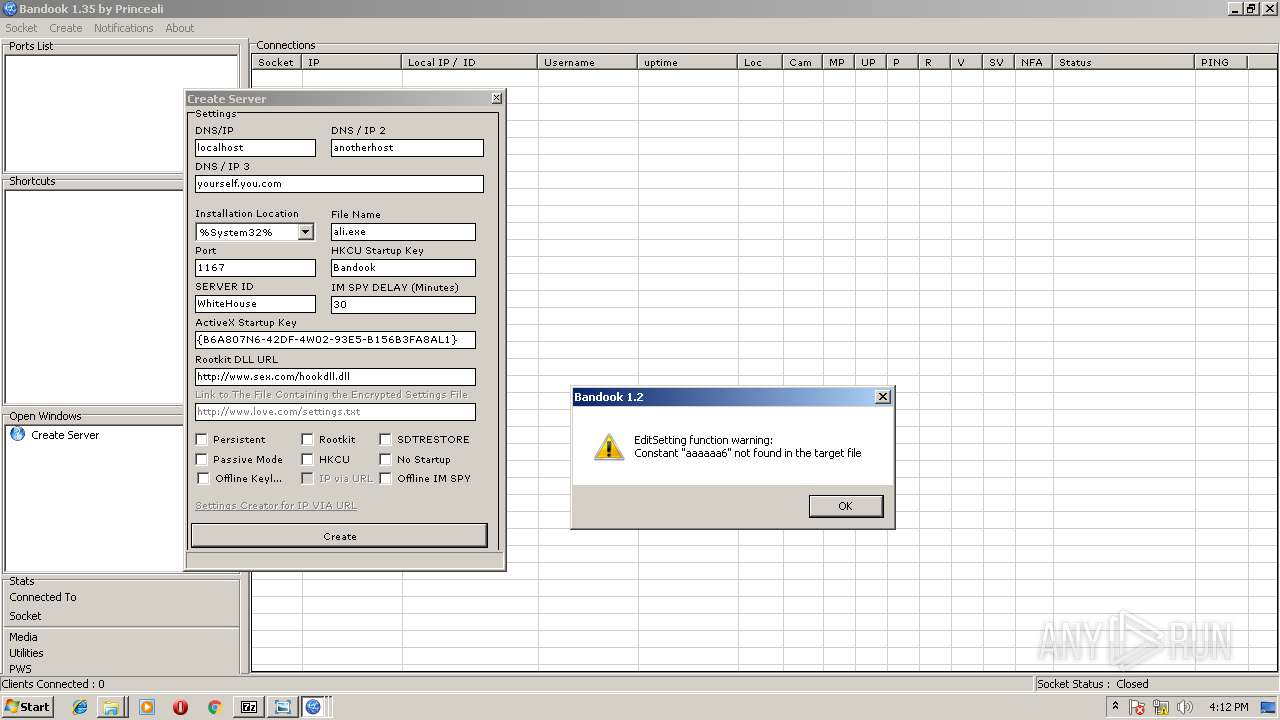
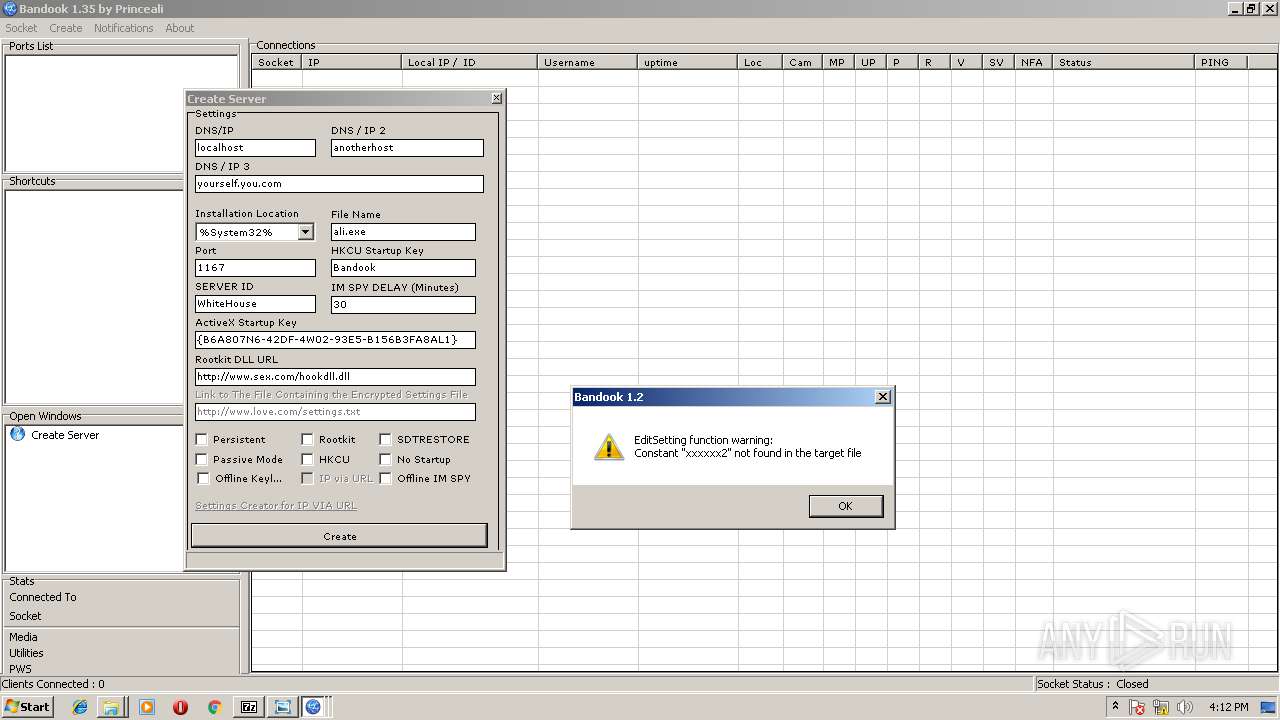
MALICIOUS
Application loaded dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1360)
Actions looks like stealing of personal data
- 7zFM.exe (PID: 2872)
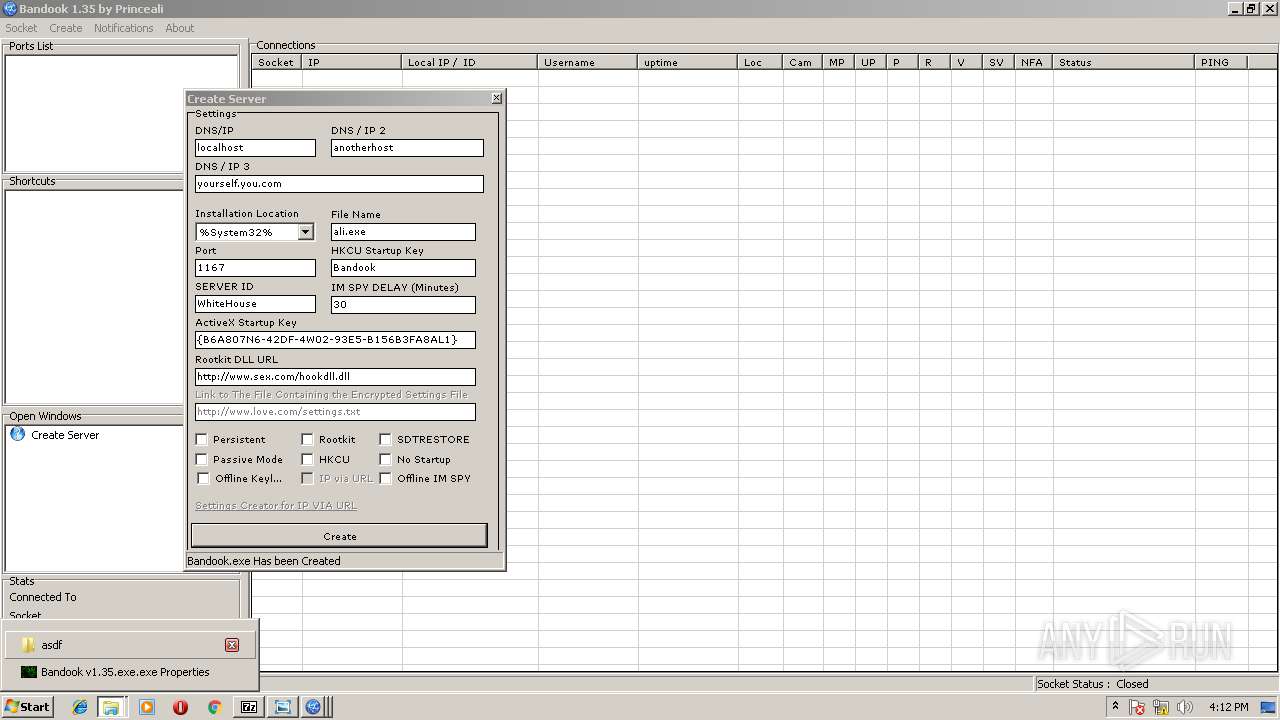
Application was dropped or rewritten from another process
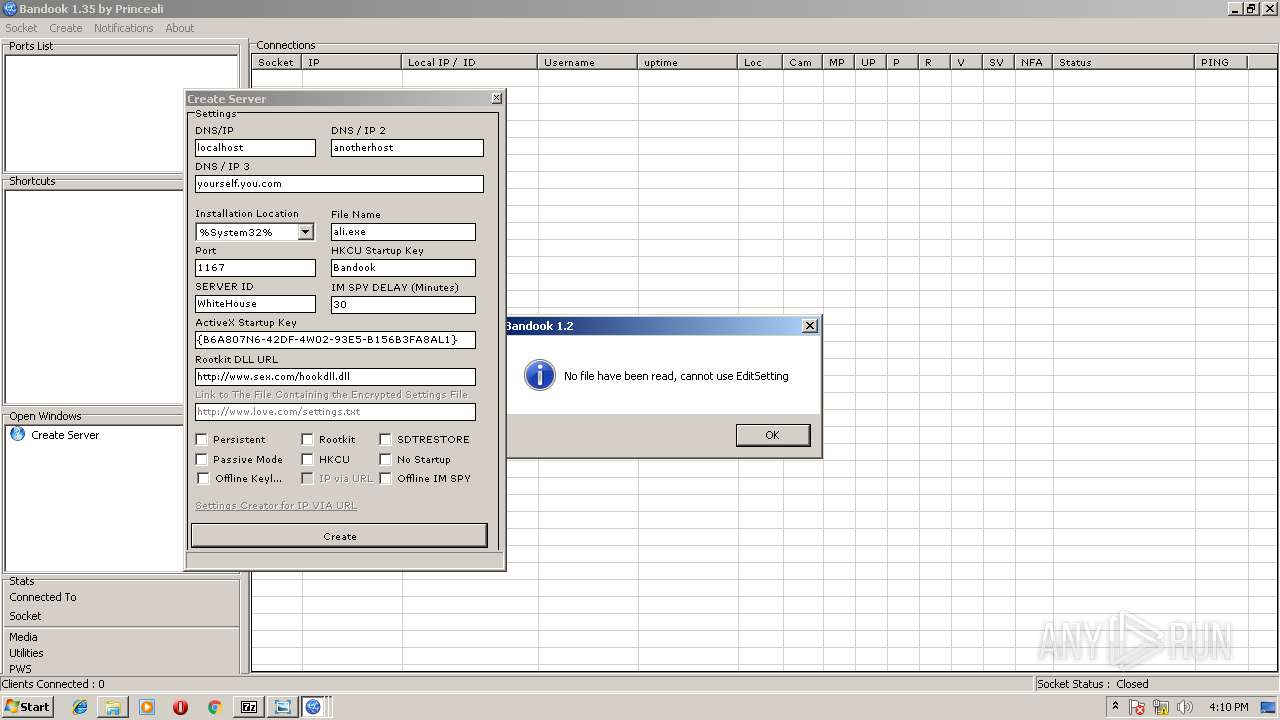
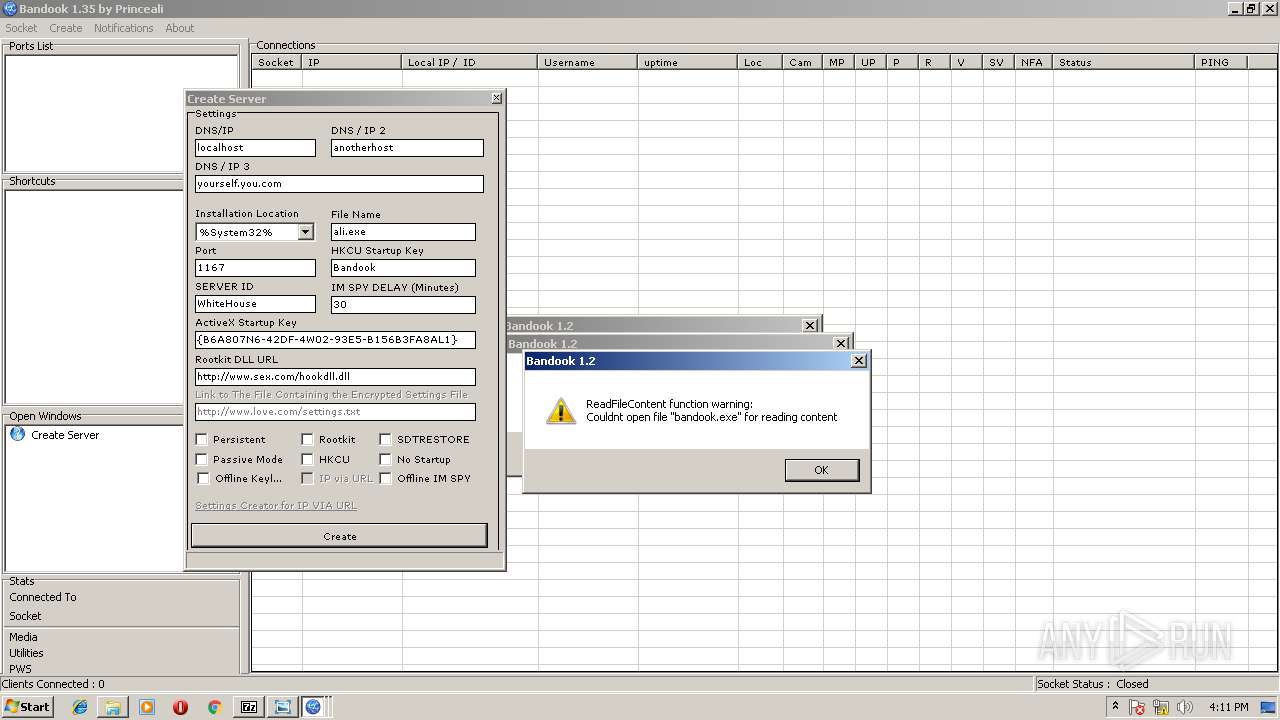
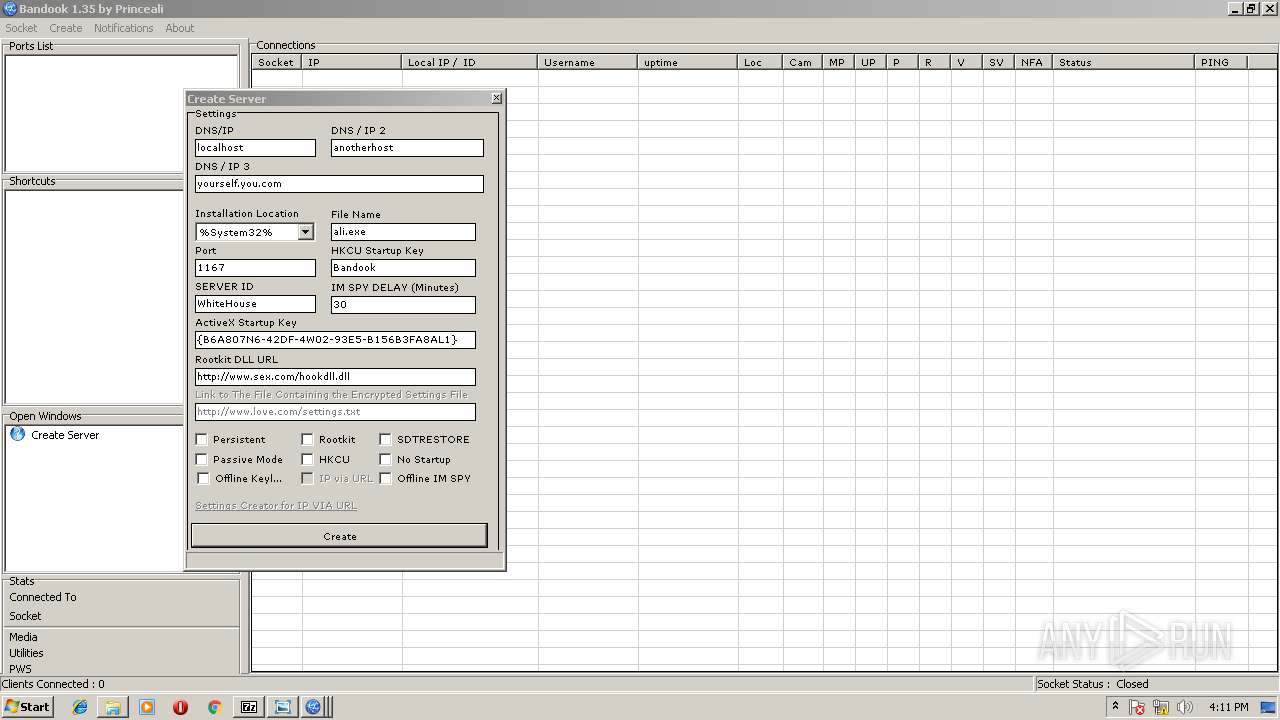
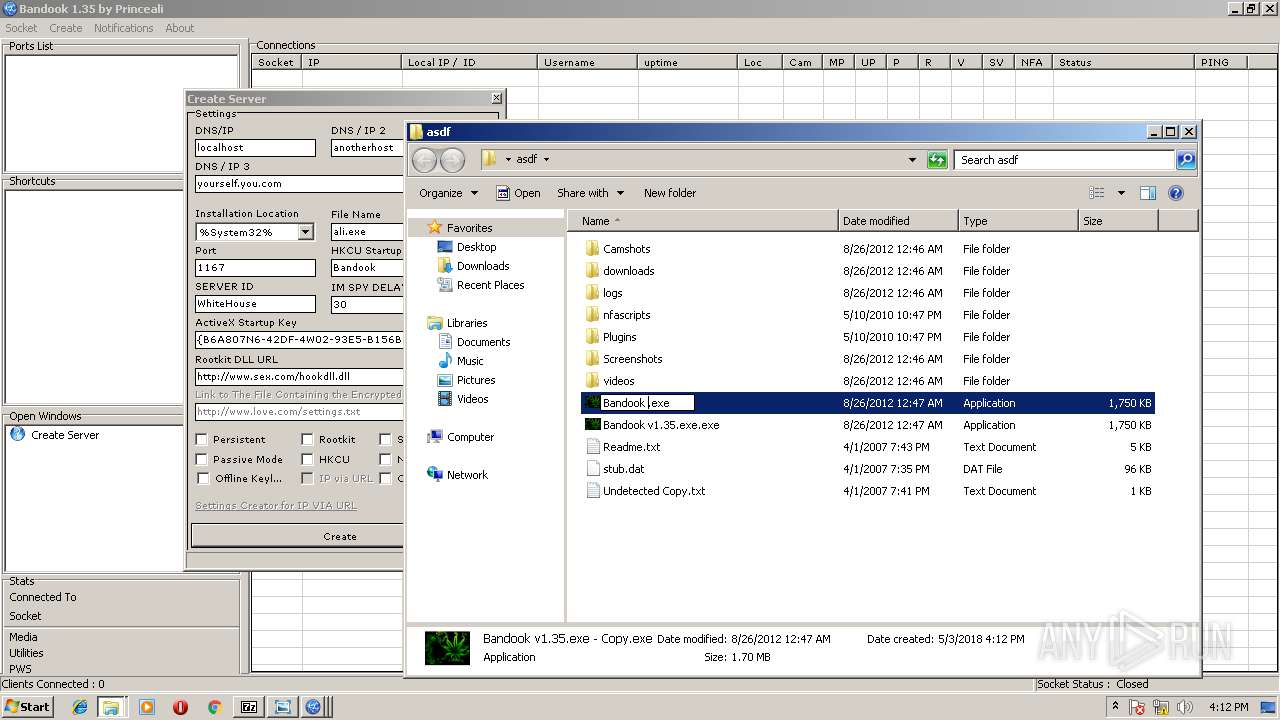
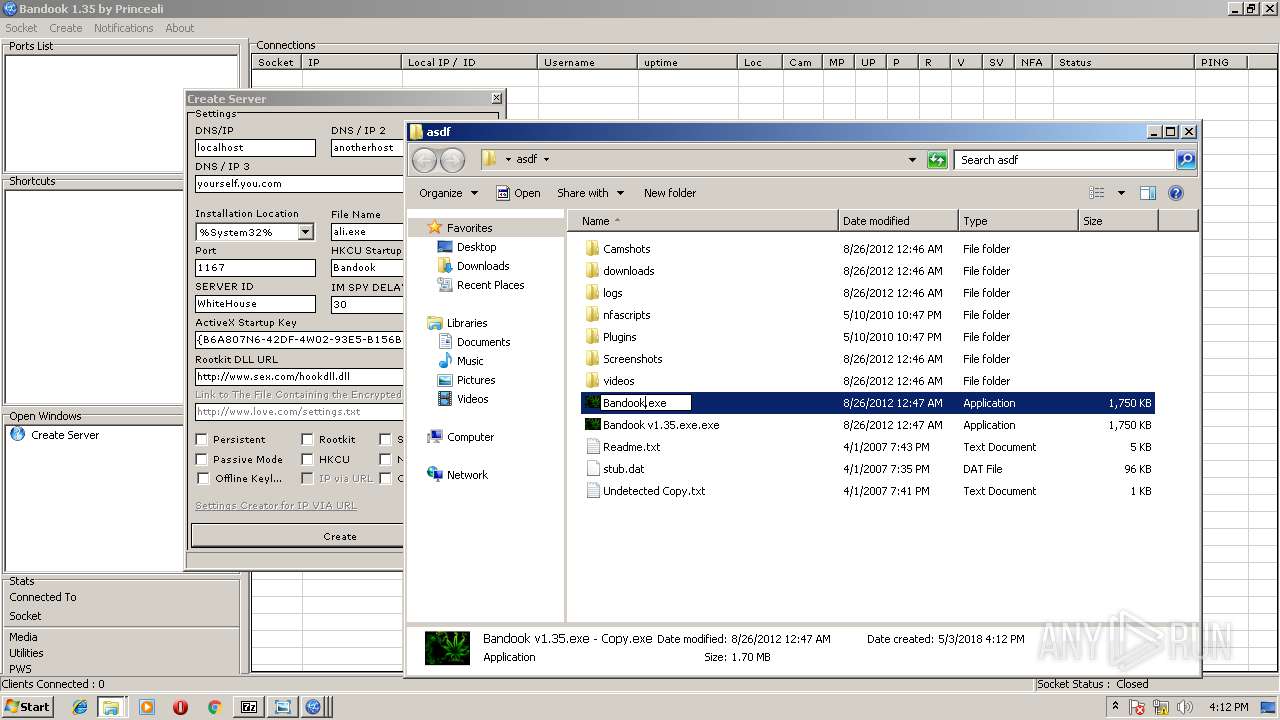
- BANDOOK V1.35.EXE (PID: 3312)
- Bandook.exe (PID: 3936)
- ali.exe (PID: 2216)
- Bandook v1.35.exe.exe (PID: 2108)
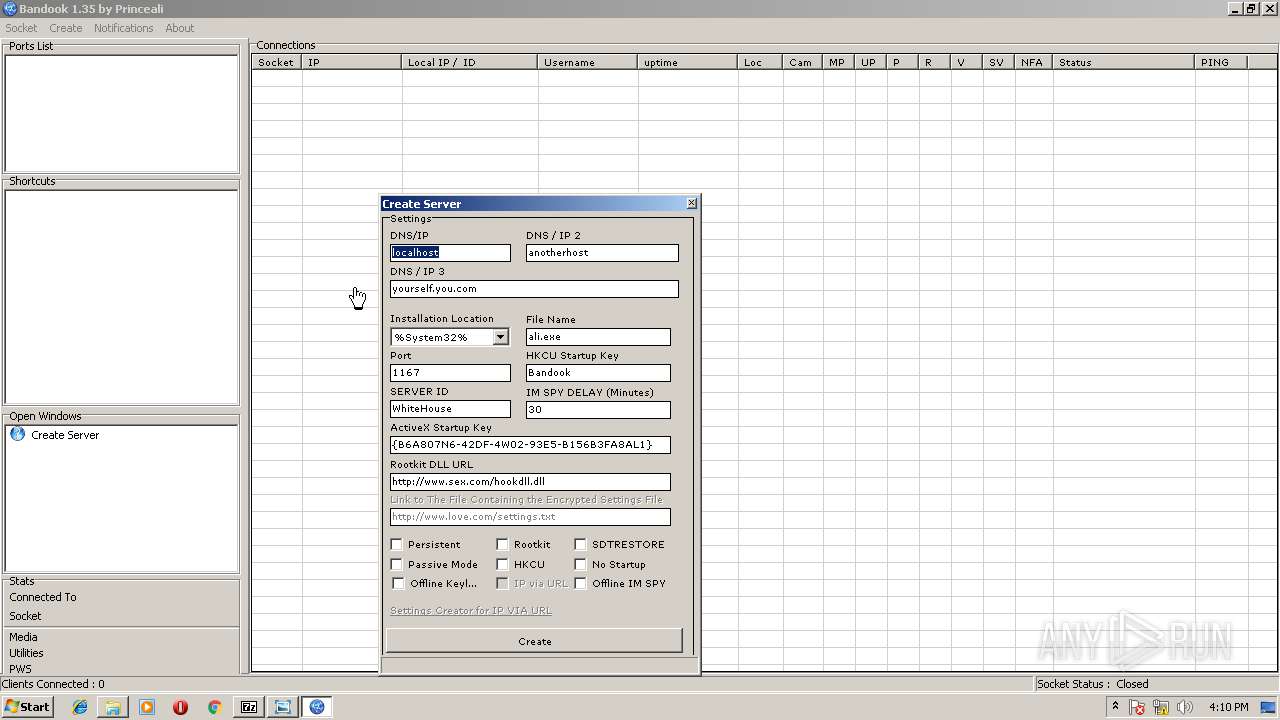
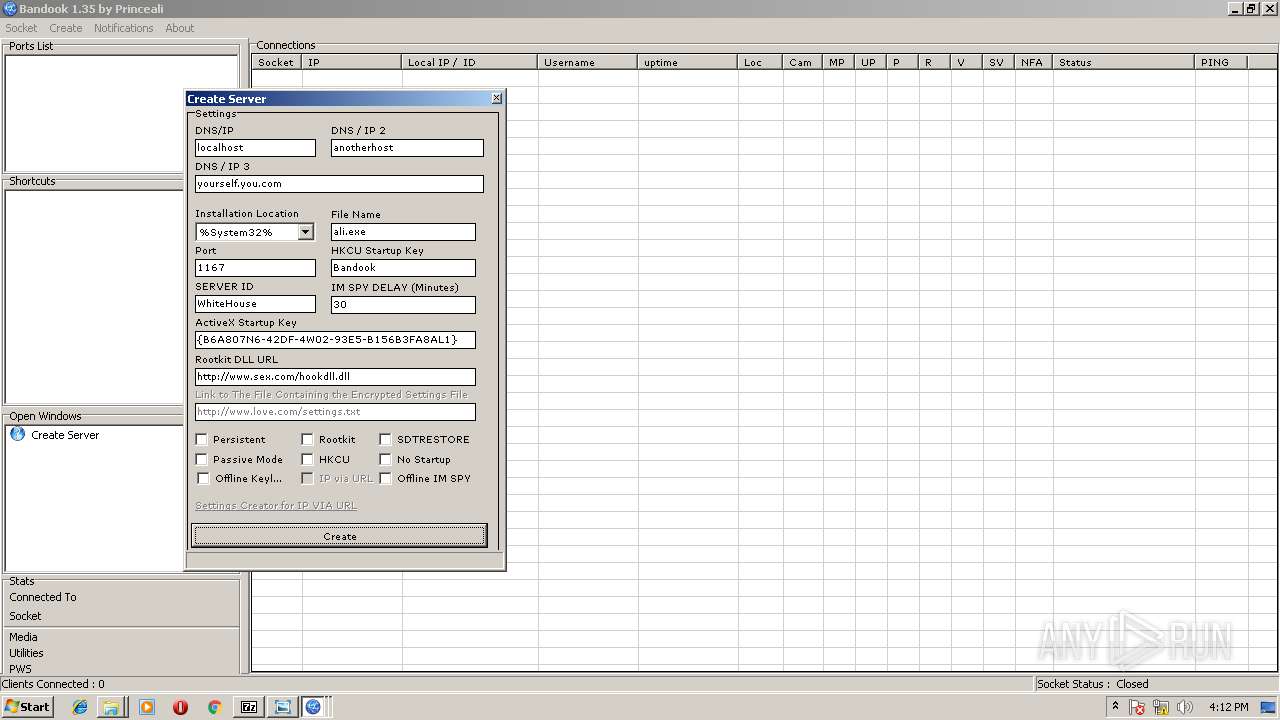
Changes the autorun value in the registry
- ali.exe (PID: 2216)
SUSPICIOUS
Starts itself from another location
- Bandook.exe (PID: 3936)
Starts Internet Explorer
- ali.exe (PID: 2216)
Creates files in the Windows directory
- Bandook.exe (PID: 3936)
INFO
Dropped object may contain URL's
- 7zFM.exe (PID: 2872)
- BANDOOK V1.35.EXE (PID: 3312)
- Bandook.exe (PID: 3936)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 320 |
|---|---|
| UncompressedSize: | 511 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2006:07:02 11:49:02 |
| PackingMethod: | Normal |
| ArchivedFileName: | nfascripts\destroy.nfa |
Total processes
49
Monitored processes
8
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1360 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe3_ Global\UsGthrCtrlFltPipeMssGthrPipe3 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2096 | "C:\Program Files\Internet Explorer\iexplore.exe" | C:\Program Files\Internet Explorer\iexplore.exe | — | ali.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
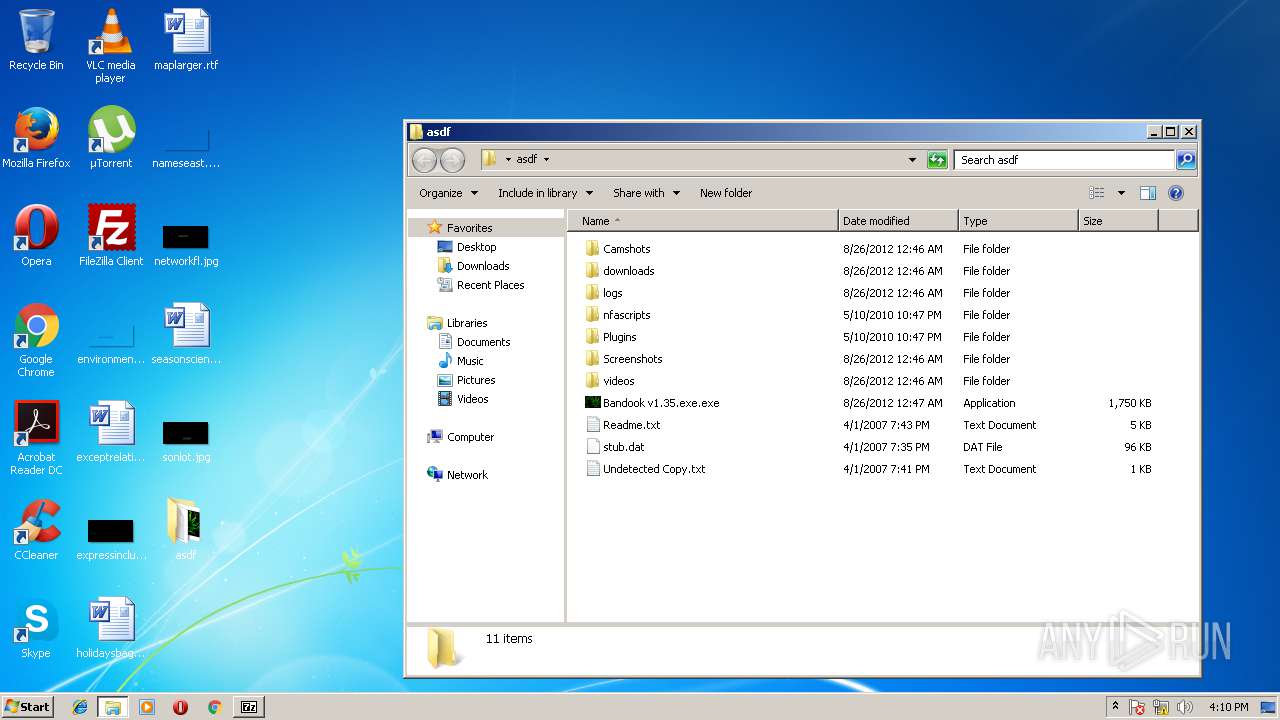
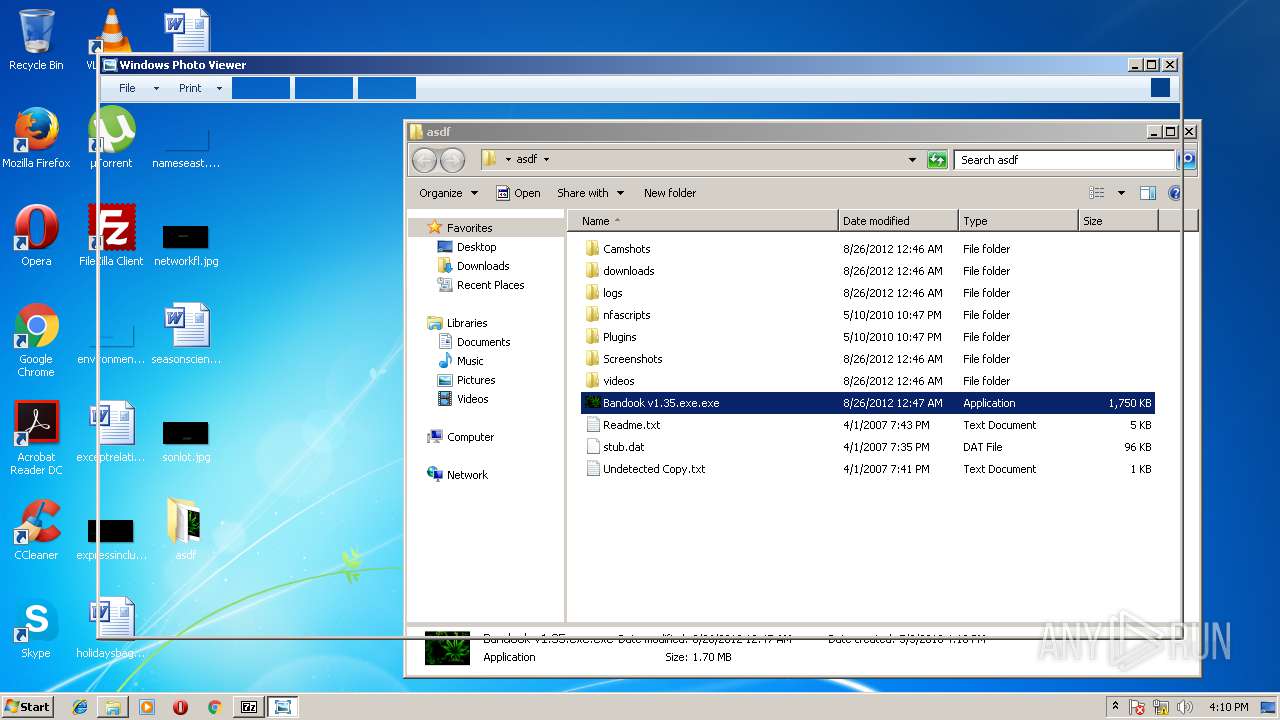
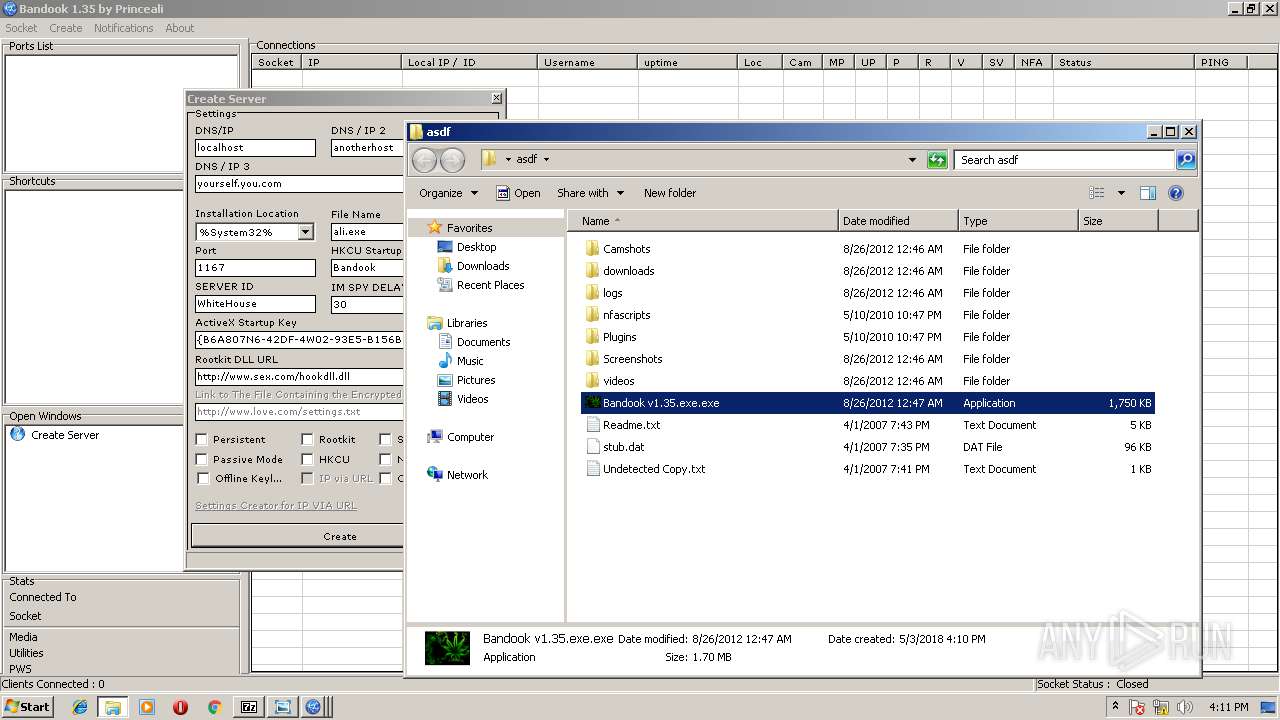
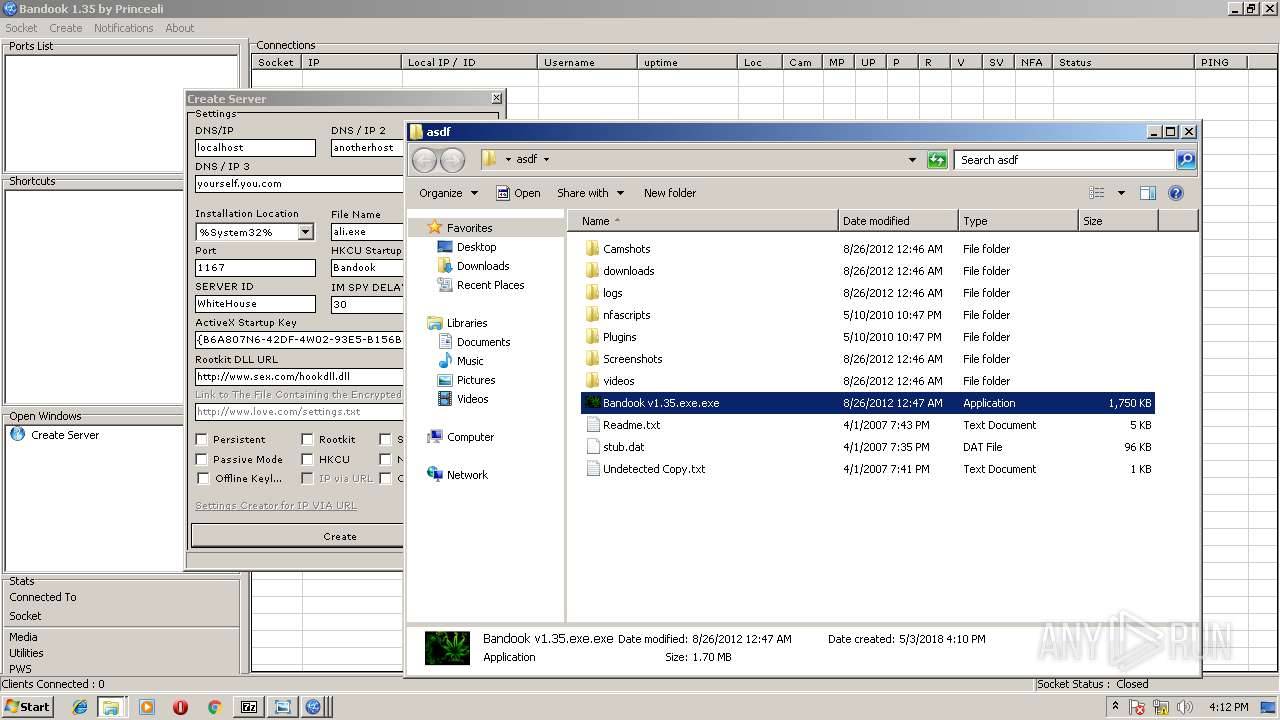
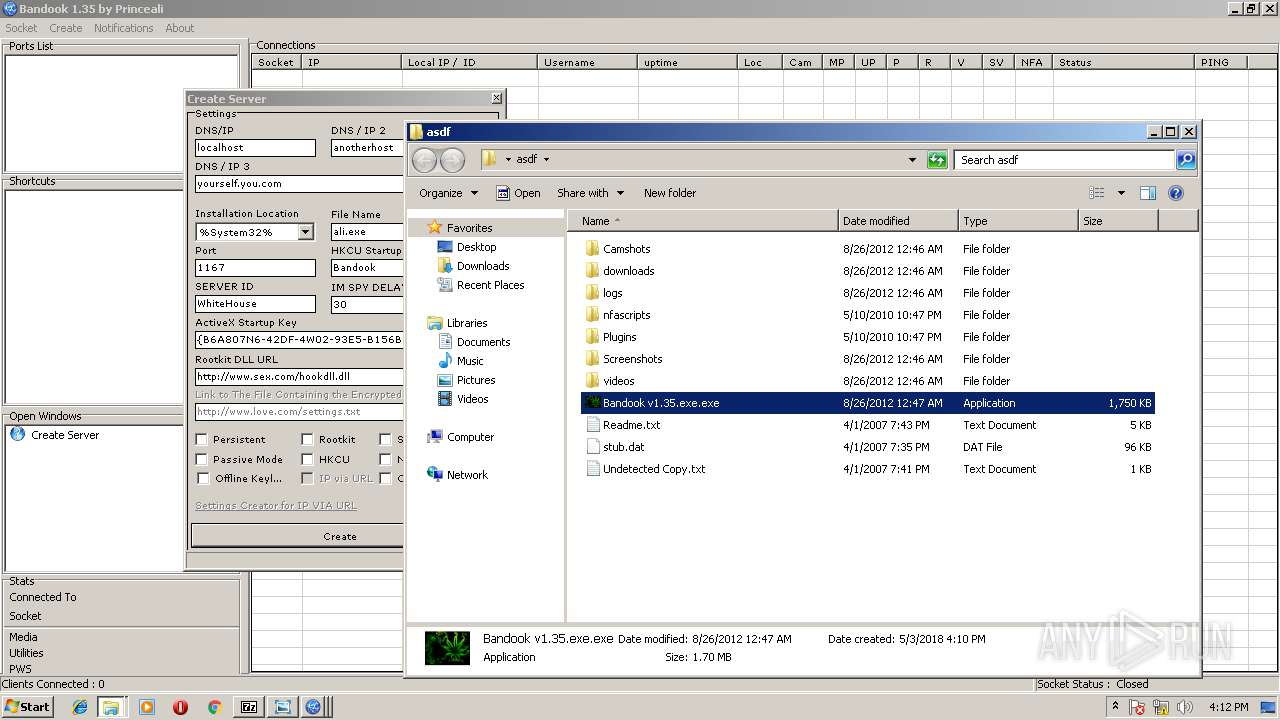
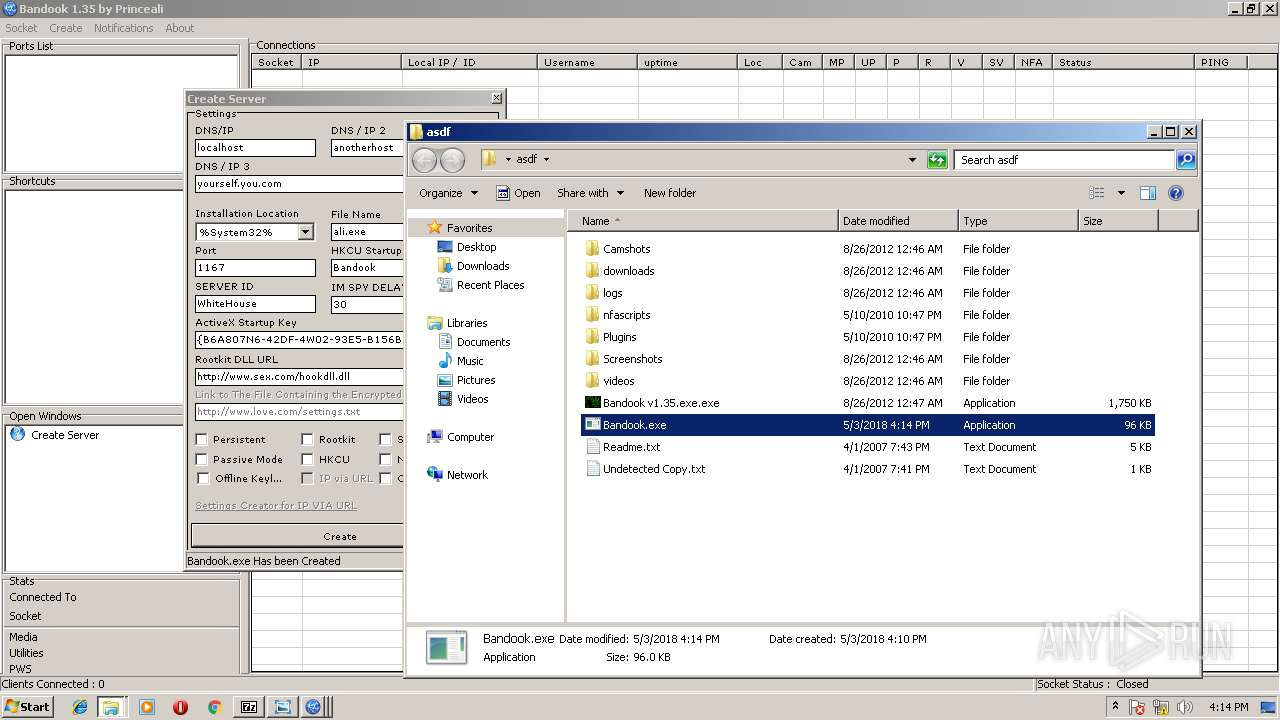
| 2108 | "C:\Users\admin\Desktop\asdf\Bandook v1.35.exe.exe" | C:\Users\admin\Desktop\asdf\Bandook v1.35.exe.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 2216 | C:\Windows\system32\ali.exe | C:\Windows\system32\ali.exe | Bandook.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2592 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2872 | "C:\Program Files\7-Zip\7zFM.exe" "C:\Users\admin\AppData\Local\Temp\Bandook v1.35.rar" | C:\Program Files\7-Zip\7zFM.exe | explorer.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip File Manager Exit code: 0 Version: 16.04 Modules
| |||||||||||||||
| 3312 | "C:\Users\admin\AppData\Local\Temp\BANDOOK V1.35.EXE" | C:\Users\admin\AppData\Local\Temp\BANDOOK V1.35.EXE | Bandook v1.35.exe.exe | ||||||||||||
User: admin Company: Nuclear Winter Crew Integrity Level: MEDIUM Description: Bandook FWB++ RAT Exit code: 0 Version: 1.3.5.0 Modules
| |||||||||||||||
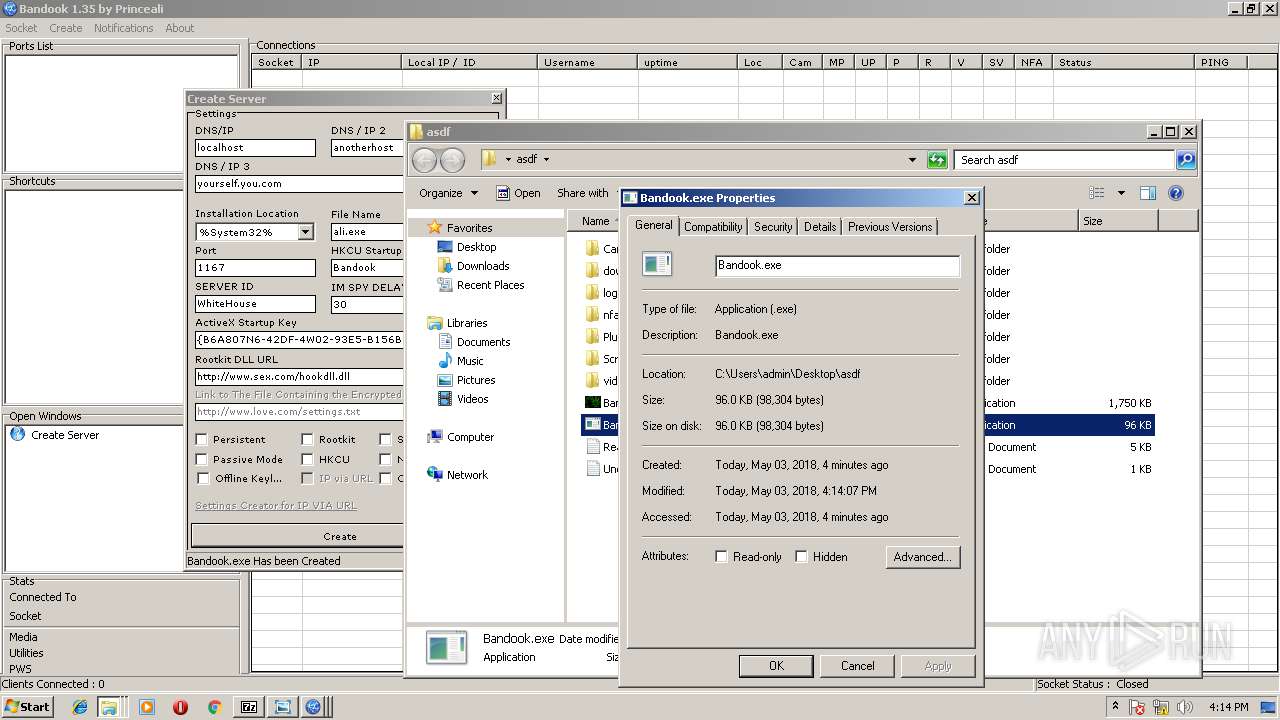
| 3936 | "C:\Users\admin\Desktop\asdf\Bandook.exe" | C:\Users\admin\Desktop\asdf\Bandook.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
1 548
Read events
1 516
Write events
32
Delete events
0
Modification events
| (PID) Process: | (2872) 7zFM.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\91\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2872) 7zFM.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\91\52C64B7E |
| Operation: | write | Name: | @C:\Program Files\Common Files\System\wab32res.dll,-4602 |
Value: Contact file | |||
| (PID) Process: | (2872) 7zFM.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\91\52C64B7E |
| Operation: | write | Name: | @"C:\Program Files\Windows Journal\Journal.exe",-3072 |
Value: Journal Document | |||
| (PID) Process: | (2872) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Discardable\PostSetup\ShellNew |
| Operation: | write | Name: | Classes |
Value: .bmp | |||
| (PID) Process: | (2872) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Discardable\PostSetup\ShellNew |
| Operation: | write | Name: | ~reserved~ |
Value: 0800000000000600 | |||
| (PID) Process: | (2872) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Width |
Value: 318 | |||
| (PID) Process: | (2872) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Height |
Value: 288 | |||
| (PID) Process: | (2872) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | CopyHistory |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C004400650073006B0074006F0070005C0061007300640066005C000000 | |||
| (PID) Process: | (2872) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM\Columns |
| Operation: | write | Name: | 7-Zip.Rar |
Value: 0100000004000000010000000400000001000000A00000000700000001000000640000000800000001000000640000000C00000001000000640000000A00000001000000640000000B00000001000000640000000900000001000000640000000F00000001000000640000000D00000001000000640000000E00000001000000640000001000000001000000640000001100000001000000640000001300000001000000640000001700000001000000640000001600000001000000640000002100000001000000640000001F0000000100000064000000200000000100000064000000 | |||
| (PID) Process: | (1360) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\91\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
16
Suspicious files
0
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2872 | 7zFM.exe | C:\Users\admin\Desktop\asdf | — | |
MD5:— | SHA256:— | |||
| 2872 | 7zFM.exe | C:\Users\admin\Desktop\asdf\nfascripts\olmert.nfa | text | |
MD5:E2294C4DF34C893038B252732FFFC98E | SHA256:35429B047C12159CD069FD6093DCFA1A0D3ABDE8BF0690D897FC3607B479E8BF | |||
| 2872 | 7zFM.exe | C:\Users\admin\Desktop\asdf\nfascripts\olmert2.nfa | text | |
MD5:7DDD4EE0A7D2A2E0E5DB014A995D0BD4 | SHA256:8FF735729726334FA766FC19044287B2CF5F933CA1060323D48CB8F276AD49B3 | |||
| 2872 | 7zFM.exe | C:\Users\admin\Desktop\asdf\nfascripts\destroy.nfa | text | |
MD5:8FD0E0C30DCA53DAF6D2C96E21D7BA9D | SHA256:8034CDD7D1994E1D061D19F2B60F13961A40FA3EE416AF234773D83B8133E96E | |||
| 2872 | 7zFM.exe | C:\Users\admin\Desktop\asdf\Plugins\bndkhook.dll | executable | |
MD5:0B313F78E7359E0316FAFF6F56C50765 | SHA256:3AC998883DB48A7DCEEE8ABDCCD461B23E194B7ECC476DAEB12BAAC03CDCDA16 | |||
| 2872 | 7zFM.exe | C:\Users\admin\Desktop\asdf\nfascripts\pcterrorist.nfa | text | |
MD5:8302FE259CA77C4B22E08F6DB54DCC30 | SHA256:1048E32F1D6E4451828FDE8D07434BEBDDC1928E45F39D62EC524DB8B061AB3B | |||
| 2872 | 7zFM.exe | C:\Users\admin\Desktop\asdf\nfascripts\Icons.nfa | text | |
MD5:DC9C2CA9FFA5EA0FD2A1B8E44FE12B7C | SHA256:92218310DFD24A25C40817A8AFA0E8F4F4FA92ADE1F41D24EE3A2C59EBB93A0E | |||
| 2872 | 7zFM.exe | C:\Users\admin\Desktop\asdf\Plugins\bndkmul.dll | executable | |
MD5:49221ECC541162C7A8A1EF83FED537D4 | SHA256:7C60029C9837E3FBAAA3050508E11C18B92FC4CBEA46A7F2BDB6E8C4A0B7F6AE | |||
| 2872 | 7zFM.exe | C:\Users\admin\Desktop\asdf\nfascripts\fuckfuckfuck.nfa | text | |
MD5:D373FDD7C7839D9BA3279A61ED25C4D0 | SHA256:44CA0393675CE91BA1AF516AF2507534FC60FE3E997C0CA8698BCB6007EACB20 | |||
| 2872 | 7zFM.exe | C:\Users\admin\Desktop\asdf\Plugins\nfa.bndk | executable | |
MD5:B709BECB4F8EC6BC7AB81E071B113690 | SHA256:B6AC220C5713C85BCE298B7406E284ADB5E3E6ECCE80AC56C1E3ED99EB9BCB96 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
Bandook v1.35.exe.exe | C:\Users\admin\AppData\Local\Temp\BANDOOK V1.35.EXE |
Bandook v1.35.exe.exe | C:\Users\admin\AppData\Local\Temp\DJACK.ICO |