| File name: | kitty.exe |
| Full analysis: | https://app.any.run/tasks/411b75be-61e2-4d3e-91d3-c3751916247b |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 04:00:59 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | 92D8035346134F7F025A4760CBA8CECB |
| SHA1: | B1EBE1281175C8A0148D4B722509C21FC1BDFE5B |
| SHA256: | 30E157C9EF189D5F1FBE4073EEA2C8AD70CED14FE84CE757FC6ECFBFEA0B72AA |
| SSDEEP: | 196608:i1PZRBaHQrmdwE1MUxTyYJu7Ndda9vWKQrchLCwb74:6ZxrkfxTyQcNdda9vThLL4 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops python dynamic module
- kitty.exe (PID: 768)
Executable content was dropped or overwritten
- kitty.exe (PID: 768)
Process drops legitimate windows executable
- kitty.exe (PID: 768)
There is functionality for taking screenshot (YARA)
- kitty.exe (PID: 768)
Application launched itself
- kitty.exe (PID: 768)
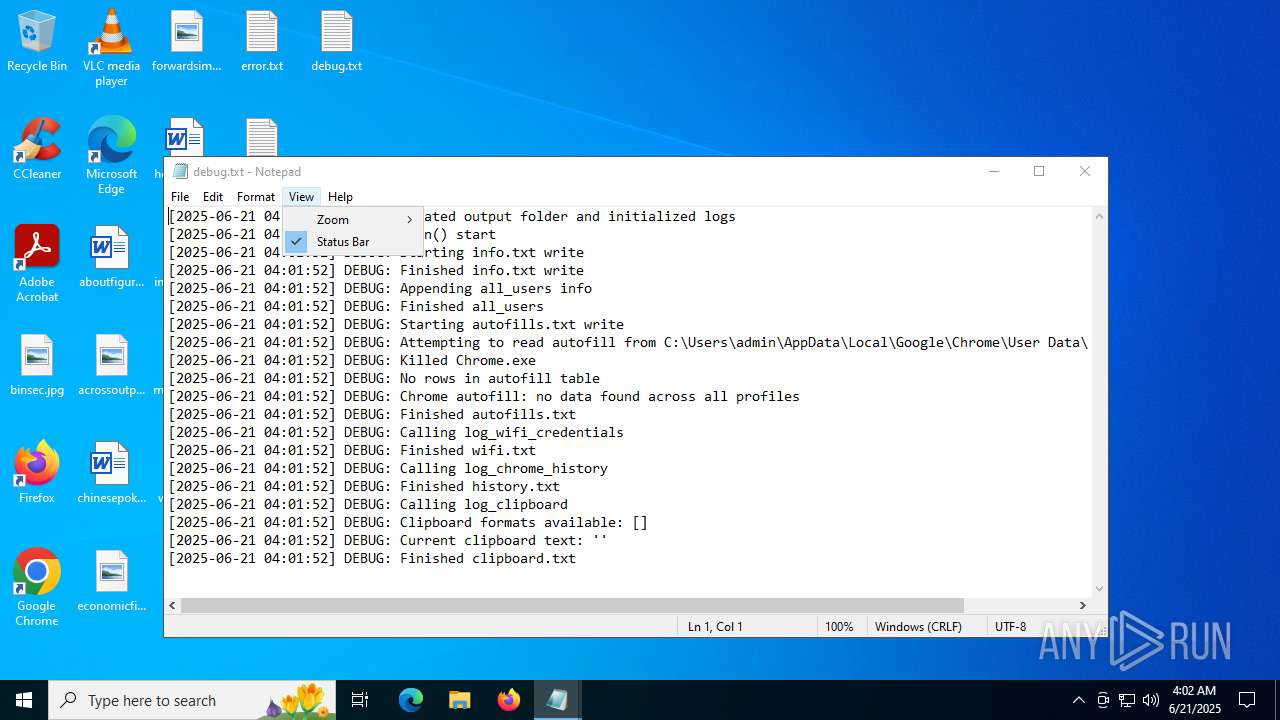
Loads Python modules
- kitty.exe (PID: 1036)
The process drops C-runtime libraries
- kitty.exe (PID: 768)
Uses TASKKILL.EXE to kill Browsers
- kitty.exe (PID: 1036)
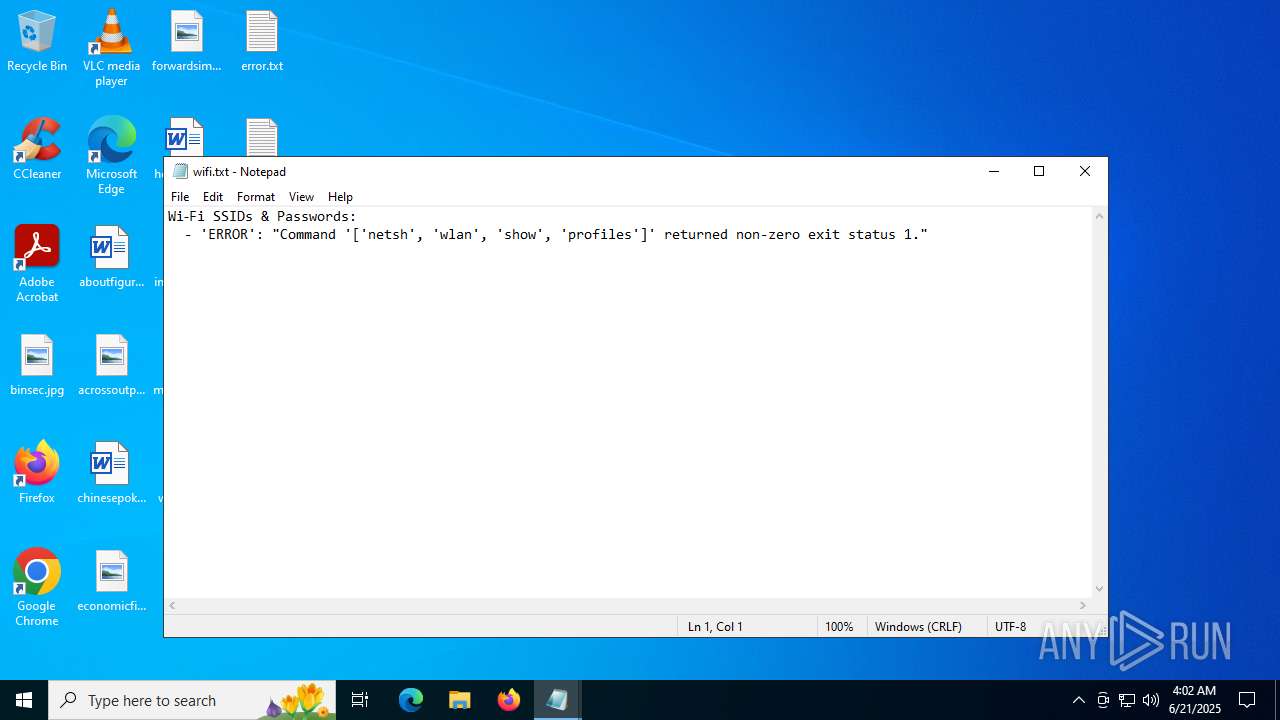
Uses NETSH.EXE to obtain data on the network
- kitty.exe (PID: 1036)
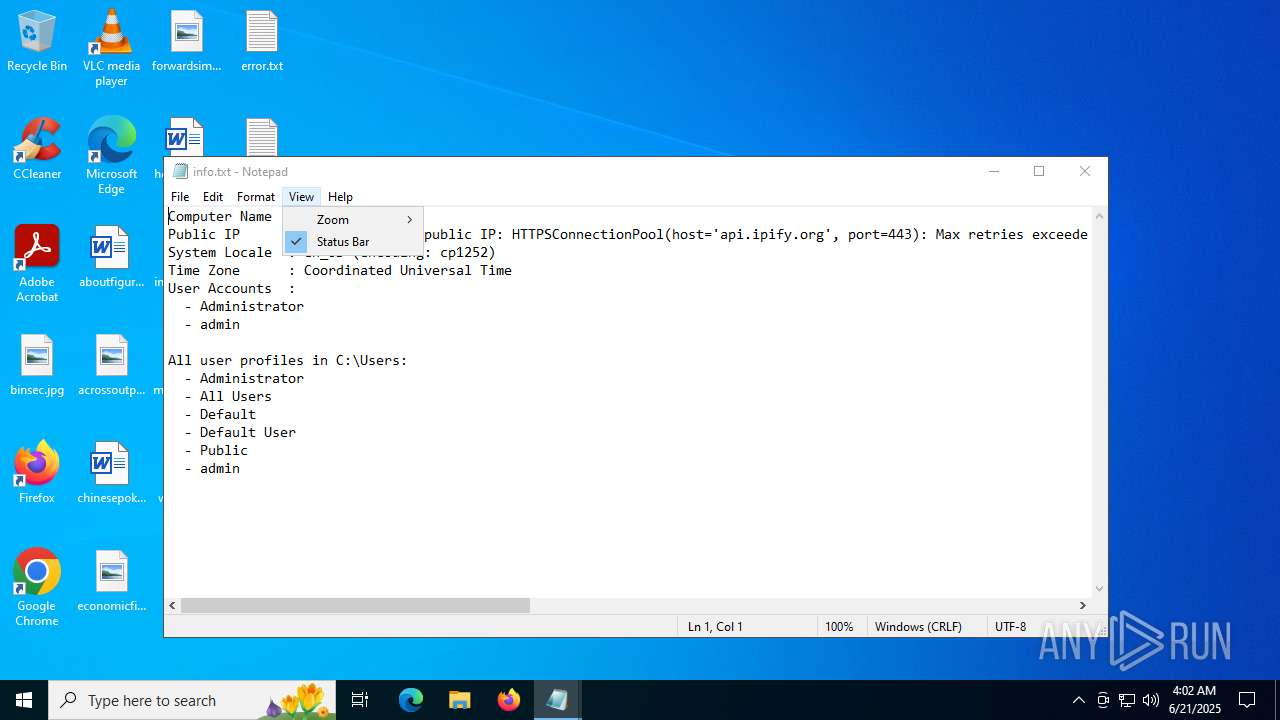
Checks for external IP
- svchost.exe (PID: 2200)
- kitty.exe (PID: 1036)
INFO
Checks supported languages
- kitty.exe (PID: 768)
- kitty.exe (PID: 1036)
Reads the computer name
- kitty.exe (PID: 768)
- kitty.exe (PID: 1036)
The sample compiled with english language support
- kitty.exe (PID: 768)
Create files in a temporary directory
- kitty.exe (PID: 768)
- kitty.exe (PID: 1036)
PyInstaller has been detected (YARA)
- kitty.exe (PID: 768)
Checks proxy server information
- kitty.exe (PID: 1036)
- slui.exe (PID: 4708)
Manual execution by a user
- notepad.exe (PID: 5900)
- notepad.exe (PID: 4968)
- notepad.exe (PID: 6320)
- notepad.exe (PID: 2072)
- notepad.exe (PID: 4888)
- rundll32.exe (PID: 5008)
- notepad.exe (PID: 6828)
Reads security settings of Internet Explorer
- notepad.exe (PID: 6320)
- notepad.exe (PID: 5900)
- notepad.exe (PID: 4968)
- notepad.exe (PID: 4888)
- notepad.exe (PID: 2072)
- notepad.exe (PID: 6828)
- rundll32.exe (PID: 5008)
Reads the software policy settings
- slui.exe (PID: 4708)
Reads Microsoft Office registry keys
- rundll32.exe (PID: 5008)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (57.6) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.9) |
| .exe | | | Generic Win/DOS Executable (2.6) |
| .exe | | | DOS Executable Generic (2.6) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:06:21 02:58:41+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.42 |
| CodeSize: | 173568 |
| InitializedDataSize: | 155648 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xce20 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
144
Monitored processes
15
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 768 | "C:\Users\admin\Desktop\kitty.exe" | C:\Users\admin\Desktop\kitty.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1036 | "C:\Users\admin\Desktop\kitty.exe" | C:\Users\admin\Desktop\kitty.exe | kitty.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1984 | netsh wlan show profiles | C:\Windows\System32\netsh.exe | — | kitty.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
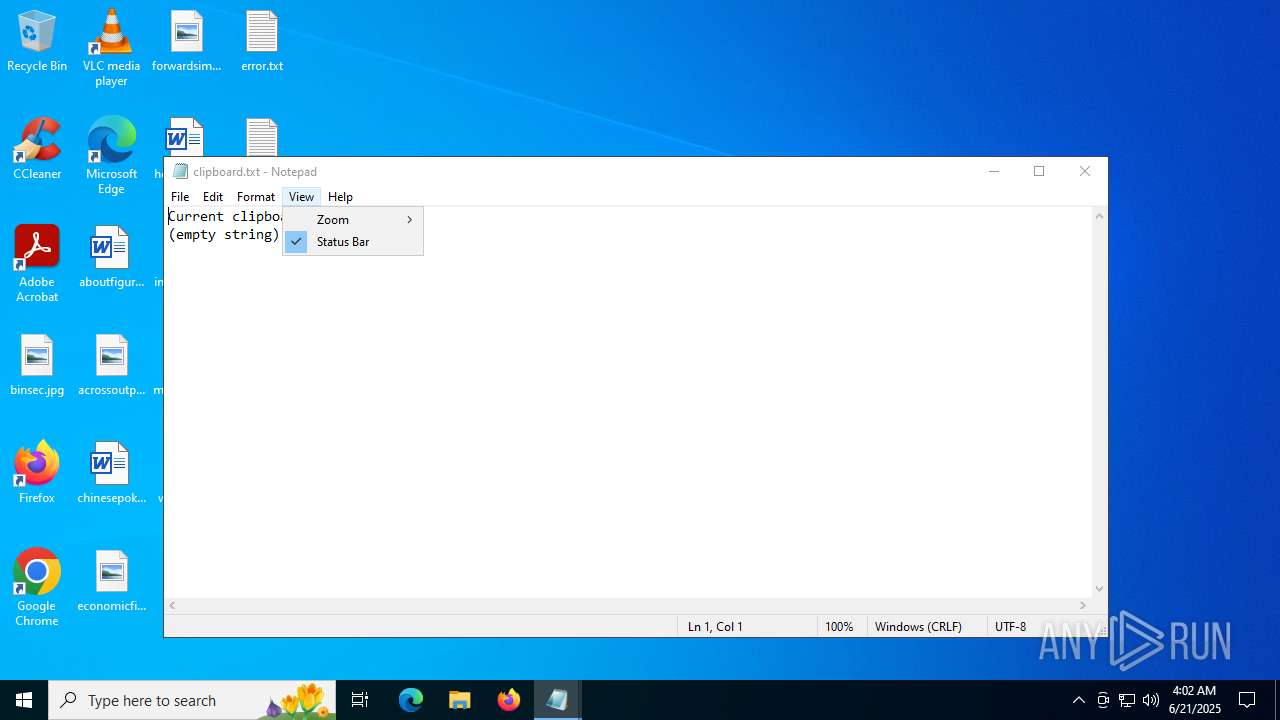
| 2072 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\clipboard.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4708 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4888 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\info.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4968 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\history.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5008 | "C:\WINDOWS\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\Desktop\screen_1.png | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
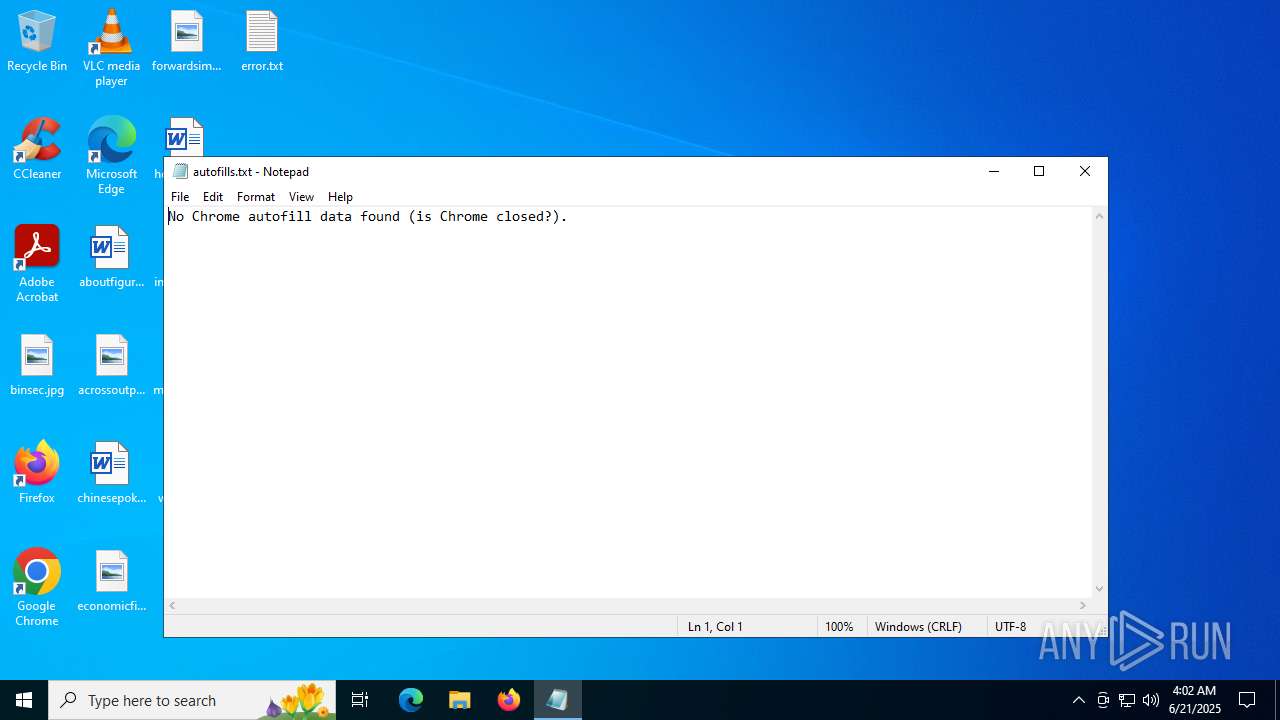
| 5900 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\autofills.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 622
Read events
10 605
Write events
17
Delete events
0
Modification events
| (PID) Process: | (5008) rundll32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.png\OpenWithProgids |
| Operation: | write | Name: | pngfile |
Value: | |||
| (PID) Process: | (5008) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MrtCache\C:%5CProgram Files%5CWindowsApps%5CMicrosoft.ScreenSketch_10.1907.2471.0_x64__8wekyb3d8bbwe%5Cmicrosoft.system.package.metadata%5CS-1-5-21-1693682860-607145093-2874071422-1001-MergedResources-0.pri\1d8b7afeb5c569c\55e3c056 |
| Operation: | write | Name: | @{microsoft.screensketch_10.1907.2471.0_x64__8wekyb3d8bbwe?ms-resource://microsoft.screensketch/files/assets/screensketchsquare44x44logo.png} |
Value: C:\Program Files\WindowsApps\Microsoft.ScreenSketch_10.1907.2471.0_x64__8wekyb3d8bbwe\Assets\ScreenSketchSquare44x44Logo.targetsize-16_contrast-black.png | |||
Executable files
78
Suspicious files
6
Text files
939
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 768 | kitty.exe | C:\Users\admin\AppData\Local\Temp\_MEI7682\PIL\_imagingmath.cp312-win_amd64.pyd | executable | |
MD5:7F5BA18AF48B19B89F4FF89C509F1745 | SHA256:045E0EF62086176AB38DDF8E52A840A39FFD50121A2694C09D35853CCB73C4FB | |||
| 768 | kitty.exe | C:\Users\admin\AppData\Local\Temp\_MEI7682\PIL\_imaging.cp312-win_amd64.pyd | executable | |
MD5:2B071B2EFF704F30B8A59D5B6D06C845 | SHA256:286CB70BFF80BCFD68E8BCEC15F019A433C213E9AF1998A241177009CB2ACB39 | |||
| 768 | kitty.exe | C:\Users\admin\AppData\Local\Temp\_MEI7682\PIL\_webp.cp312-win_amd64.pyd | executable | |
MD5:A21A05FB1CB9830977DF1ED788B805D6 | SHA256:6C7AF1E7C6D500F39BBF29E5DB9F897F3BCBB830117E6B6AD177FE1965413152 | |||
| 768 | kitty.exe | C:\Users\admin\AppData\Local\Temp\_MEI7682\VCRUNTIME140_1.dll | executable | |
MD5:F8DFA78045620CF8A732E67D1B1EB53D | SHA256:A113F192195F245F17389E6ECBED8005990BCB2476DDAD33F7C4C6C86327AFE5 | |||
| 768 | kitty.exe | C:\Users\admin\AppData\Local\Temp\_MEI7682\_decimal.pyd | executable | |
MD5:7AE94F5A66986CBC1A2B3C65A8D617F3 | SHA256:DA8BB3D54BBBA20D8FA6C2FD0A4389AEC80AB6BD490B0ABEF5BD65097CBC0DA4 | |||
| 768 | kitty.exe | C:\Users\admin\AppData\Local\Temp\_MEI7682\PIL\_imagingcms.cp312-win_amd64.pyd | executable | |
MD5:F9936AF55479CF0DCB14735628E65DC1 | SHA256:D037B8AF3B59C56E70C38A044EF4532730C77C5602F8EE8B76E2A5FDCFEA21B7 | |||
| 768 | kitty.exe | C:\Users\admin\AppData\Local\Temp\_MEI7682\VCRUNTIME140.dll | executable | |
MD5:BE8DBE2DC77EBE7F88F910C61AEC691A | SHA256:4D292623516F65C80482081E62D5DADB759DC16E851DE5DB24C3CBB57B87DB83 | |||
| 768 | kitty.exe | C:\Users\admin\AppData\Local\Temp\_MEI7682\_asyncio.pyd | executable | |
MD5:90A38A8271379A371A2A4C580E9CD97D | SHA256:3B46FA8F966288EAD65465468C8E300B9179F5D7B39AA25D7231FF3702CA7887 | |||
| 768 | kitty.exe | C:\Users\admin\AppData\Local\Temp\_MEI7682\_bz2.pyd | executable | |
MD5:30F396F8411274F15AC85B14B7B3CD3D | SHA256:CB15D6CC7268D3A0BD17D9D9CEC330A7C1768B1C911553045C73BC6920DE987F | |||
| 768 | kitty.exe | C:\Users\admin\AppData\Local\Temp\_MEI7682\_cffi_backend.cp312-win_amd64.pyd | executable | |
MD5:FCB71CE882F99EC085D5875E1228BDC1 | SHA256:86F136553BA301C70E7BADA8416B77EB4A07F76CCB02F7D73C2999A38FA5FA5B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
46
DNS requests
19
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 200 | 40.126.31.69:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 200 | 40.126.31.67:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 16.7 Kb | whitelisted |
— | — | POST | 200 | 40.126.31.67:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
— | — | POST | 200 | 40.126.31.131:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.55.104.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.159.2:443 | https://login.live.com/RST2.srf | unknown | xml | 10.3 Kb | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.126.31.1:443 | https://login.live.com/RST2.srf | unknown | xml | 11.0 Kb | whitelisted |
— | — | POST | 200 | 20.190.159.68:443 | https://login.live.com/RST2.srf | unknown | xml | 10.3 Kb | whitelisted |
— | — | GET | 304 | 4.245.163.56:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5896 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3576 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.55.104.190:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
login.live.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
api.ipify.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
1036 | kitty.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |