| File name: | MCSPScanner-0.0.7-win-32bit-fixed.exe |
| Full analysis: | https://app.any.run/tasks/ab41fba2-d842-449e-8cc1-ccead5548230 |
| Verdict: | Malicious activity |
| Analysis date: | July 26, 2025, 15:25:02 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | C796281658A07F497D230DEBBA2EBF54 |
| SHA1: | E48F8CE1EC011FED24151417B1E616281689286C |
| SHA256: | 30E0093DFC36930ECDC331EAE21B5313058D035EC48A410A377E0DE8CB38D4C6 |
| SSDEEP: | 98304:cknAxzWkqDarPgV6/QI5fY9XDoqC13YbHmOl+9yPlEIHBy4ALeHL1nI6aMWm7Mwf:SQlEYl0BlLfpl+gynY3BRBuyo |
MALICIOUS
No malicious indicators.SUSPICIOUS
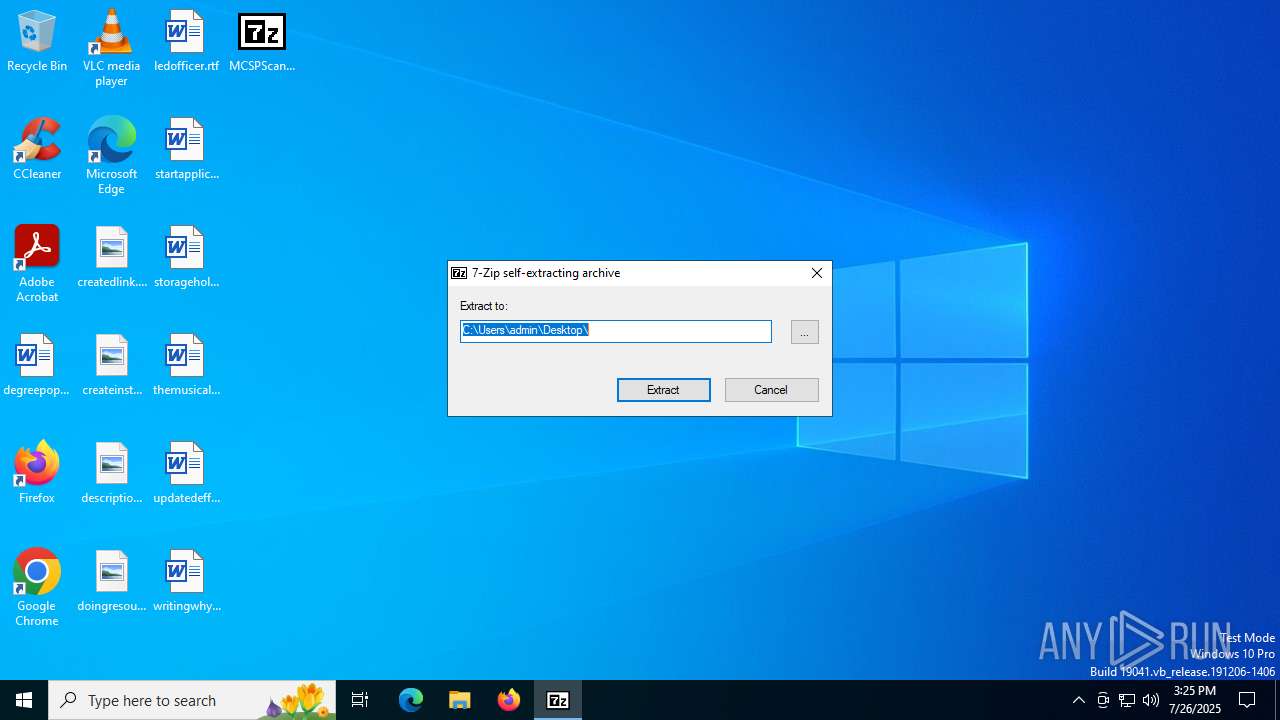
Drops 7-zip archiver for unpacking
- MCSPScanner-0.0.7-win-32bit-fixed.exe (PID: 1976)
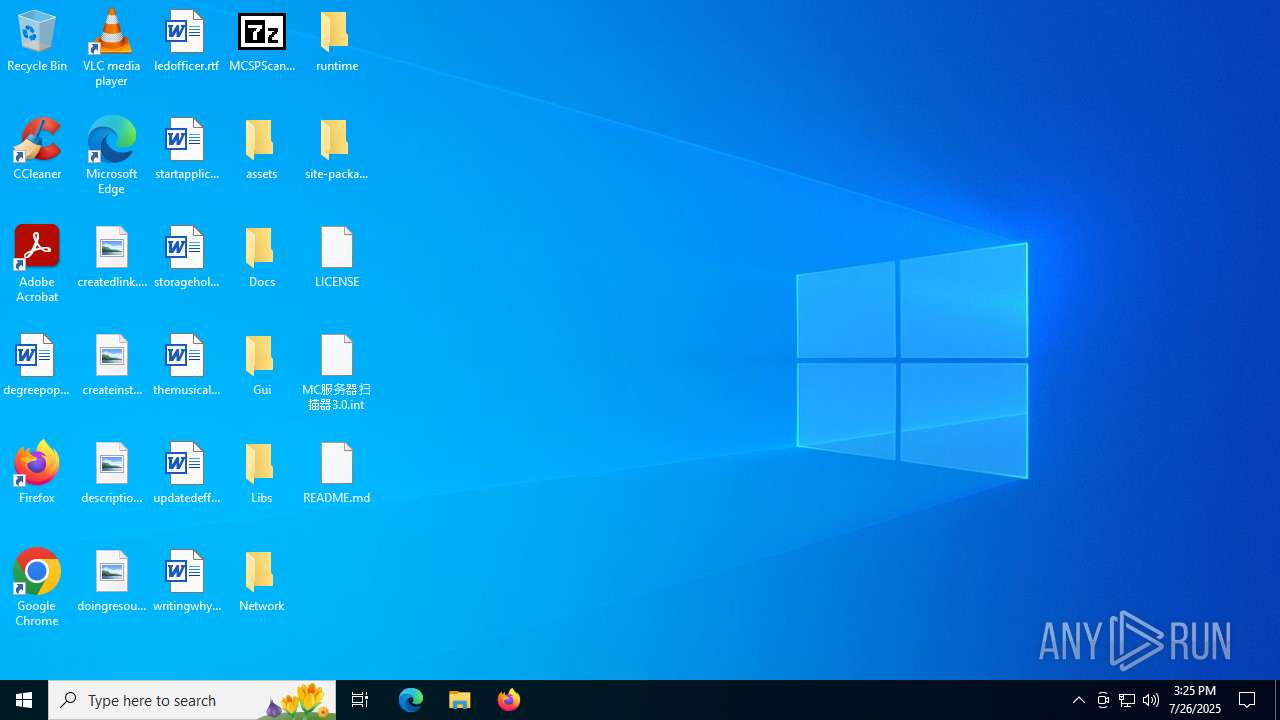
Executable content was dropped or overwritten
- MCSPScanner-0.0.7-win-32bit-fixed.exe (PID: 1976)
Process drops python dynamic module
- MCSPScanner-0.0.7-win-32bit-fixed.exe (PID: 1976)
The process drops C-runtime libraries
- MCSPScanner-0.0.7-win-32bit-fixed.exe (PID: 1976)
Process drops legitimate windows executable
- MCSPScanner-0.0.7-win-32bit-fixed.exe (PID: 1976)
The process executes via Task Scheduler
- updater.exe (PID: 4320)
Application launched itself
- updater.exe (PID: 4320)
INFO
The sample compiled with english language support
- MCSPScanner-0.0.7-win-32bit-fixed.exe (PID: 1976)
Reads the computer name
- MCSPScanner-0.0.7-win-32bit-fixed.exe (PID: 1976)
- updater.exe (PID: 4320)
Checks supported languages
- MCSPScanner-0.0.7-win-32bit-fixed.exe (PID: 1976)
- updater.exe (PID: 4320)
- updater.exe (PID: 5416)
Process checks whether UAC notifications are on
- updater.exe (PID: 4320)
Manual execution by a user
- cmd.exe (PID: 2528)
- notepad.exe (PID: 4216)
- FileHistory.exe (PID: 1508)
Reads security settings of Internet Explorer
- notepad.exe (PID: 4216)
- FileHistory.exe (PID: 1508)
Checks proxy server information
- slui.exe (PID: 4160)
Reads the software policy settings
- slui.exe (PID: 4160)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:06:20 08:00:00+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 175104 |
| InitializedDataSize: | 55808 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x28a0c |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 23.1.0.0 |
| ProductVersionNumber: | 23.1.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Igor Pavlov |
| FileDescription: | 7z SFX |
| FileVersion: | 23.01 |
| InternalName: | 7z.sfx |
| LegalCopyright: | Copyright (c) 1999-2023 Igor Pavlov |
| OriginalFileName: | 7z.sfx.exe |
| ProductName: | 7-Zip |
| ProductVersion: | 23.01 |
Total processes
142
Monitored processes
9
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1508 | "C:\WINDOWS\System32\FileHistory.exe" "C:\Users\admin\Downloads" | C:\Windows\System32\FileHistory.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: File History Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1976 | "C:\Users\admin\Desktop\MCSPScanner-0.0.7-win-32bit-fixed.exe" | C:\Users\admin\Desktop\MCSPScanner-0.0.7-win-32bit-fixed.exe | explorer.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7z SFX Exit code: 0 Version: 23.01 Modules
| |||||||||||||||
| 2464 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2528 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\fetch_macholib.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2976 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4160 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4216 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\README.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4320 | "C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe" --wake --system | C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Updater Exit code: 0 Version: 134.0.6985.0 Modules
| |||||||||||||||
| 5416 | "C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe" --crash-handler --system "--database=C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\Crashpad" --url=https://clients2.google.com/cr/report --annotation=prod=Update4 --annotation=ver=134.0.6985.0 "--attachment=C:\Program Files (x86)\Google\GoogleUpdater\updater.log" --initial-client-data=0x298,0x29c,0x2a0,0x274,0x2a4,0x111c460,0x111c46c,0x111c478 | C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe | — | updater.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Updater Exit code: 0 Version: 134.0.6985.0 Modules
| |||||||||||||||
Total events
4 331
Read events
4 331
Write events
0
Delete events
0
Modification events
Executable files
33
Suspicious files
9
Text files
480
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1976 | MCSPScanner-0.0.7-win-32bit-fixed.exe | C:\Users\admin\Desktop\assets\UnifontExMono.ttf | — | |
MD5:— | SHA256:— | |||
| 1976 | MCSPScanner-0.0.7-win-32bit-fixed.exe | C:\Users\admin\Desktop\assets\openfrp_hosts.json | binary | |
MD5:B881CFCB1D2FD3C34D54ECC46A06D087 | SHA256:BBC27EE7B15532F7427897BFADF46C5497E323FE3CDA4AFE2D242D7B124E56DC | |||
| 1976 | MCSPScanner-0.0.7-win-32bit-fixed.exe | C:\Users\admin\Desktop\assets\server_icon.png | image | |
MD5:7D3AEC8C26FABB5AD07DA23F40A4F634 | SHA256:123DA85DE83347EEE53B5DADACB61DC1A06544D116420A1765013AC0D36C1197 | |||
| 1976 | MCSPScanner-0.0.7-win-32bit-fixed.exe | C:\Users\admin\Desktop\assets\protocol_map.json | text | |
MD5:FA2D1247BC9F12BC6734819ED2075F0E | SHA256:E88B52B2EC3F914F1609F2C0CE70BFE328D6A2CFFBDEF47E2EF7CE0953DB572F | |||
| 1976 | MCSPScanner-0.0.7-win-32bit-fixed.exe | C:\Users\admin\Desktop\assets\icon.ico | image | |
MD5:ED834D0E4BB77A253AA3CC8025EFB3B2 | SHA256:B524FFC7F81A91CAF85B82F544D26FDFCDBE8C03CD8F61FEE8677F6EABBF9D68 | |||
| 1976 | MCSPScanner-0.0.7-win-32bit-fixed.exe | C:\Users\admin\Desktop\assets\TaskbarLib.tlb | binary | |
MD5:CAB6E20882B5A172517637BA95202B33 | SHA256:C3D9122198F06A8E532F3D01B5E6C7763B1BEA7D8137ED684E5114277F3437A3 | |||
| 1976 | MCSPScanner-0.0.7-win-32bit-fixed.exe | C:\Users\admin\Desktop\Gui\PortsRangeGui.py | text | |
MD5:C5E3DF463CE0E792D7B11E40510CDDB6 | SHA256:C9081CA12CDE7974DE57E428EB042A2A216A4A97EFF046CC19129653379439D0 | |||
| 1976 | MCSPScanner-0.0.7-win-32bit-fixed.exe | C:\Users\admin\Desktop\Gui\ScanBarGui.py | text | |
MD5:B52E3589570111553B70F4CA36DC8EE3 | SHA256:131F45B2AB63B05B0B8F36C686BA53898999E7004DA2F767C5683E66ABADFD23 | |||
| 1976 | MCSPScanner-0.0.7-win-32bit-fixed.exe | C:\Users\admin\Desktop\Docs\README_EN.md | text | |
MD5:3F62FEF0C6E81C3A83ED8BB6057C7BF1 | SHA256:E13E0A76B621C1C0DBE0B93C852DA80E5615E033E10C2B377F385AB9FFC6B112 | |||
| 1976 | MCSPScanner-0.0.7-win-32bit-fixed.exe | C:\Users\admin\Desktop\Gui\InfoGui.py | text | |
MD5:842FE8917BC331EA11F5732FB89344D3 | SHA256:F4B9B3772C1F0789A5F1E73B690EBFFD9C240E757B498780C27A2C360F2B78AF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
39
TCP/UDP connections
42
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.55.110.211:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.55.110.211:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
236 | RUXIMICS.exe | GET | 200 | 23.55.110.211:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
236 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.159.73:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 400 | 20.190.159.73:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.159.130:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.159.128:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
236 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.55.110.211:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.55.110.211:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
236 | RUXIMICS.exe | 23.55.110.211:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |