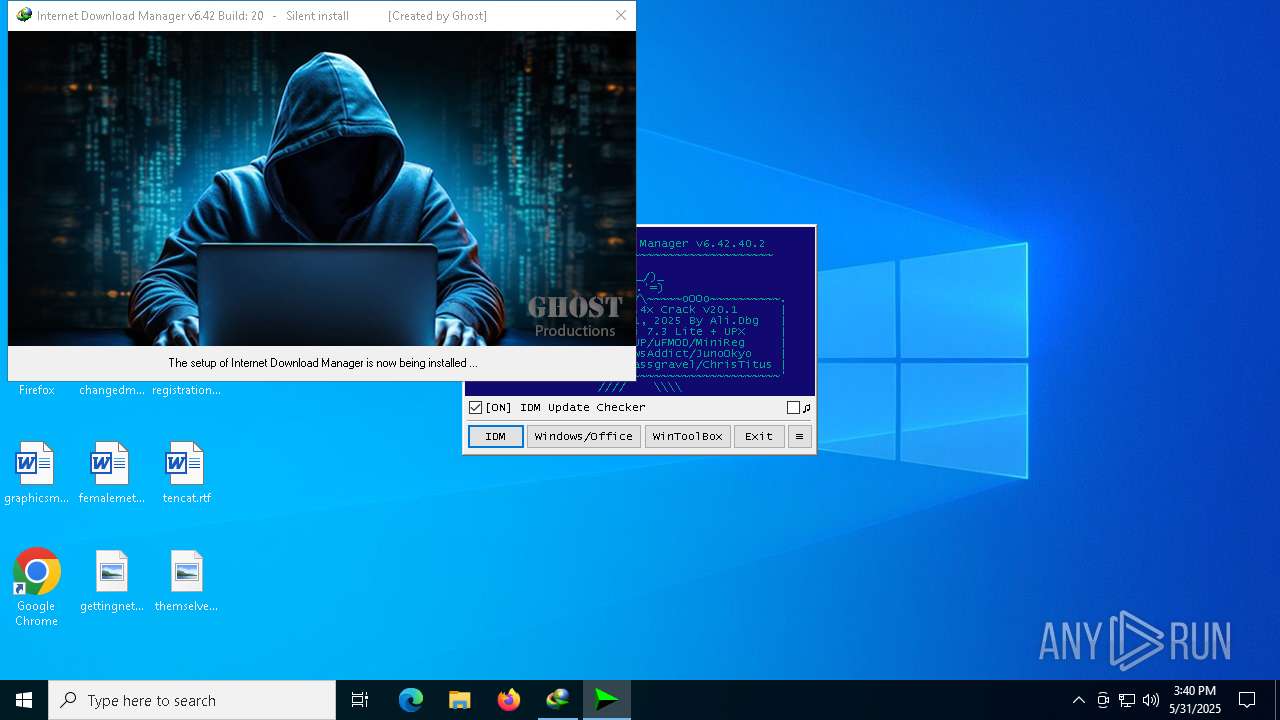
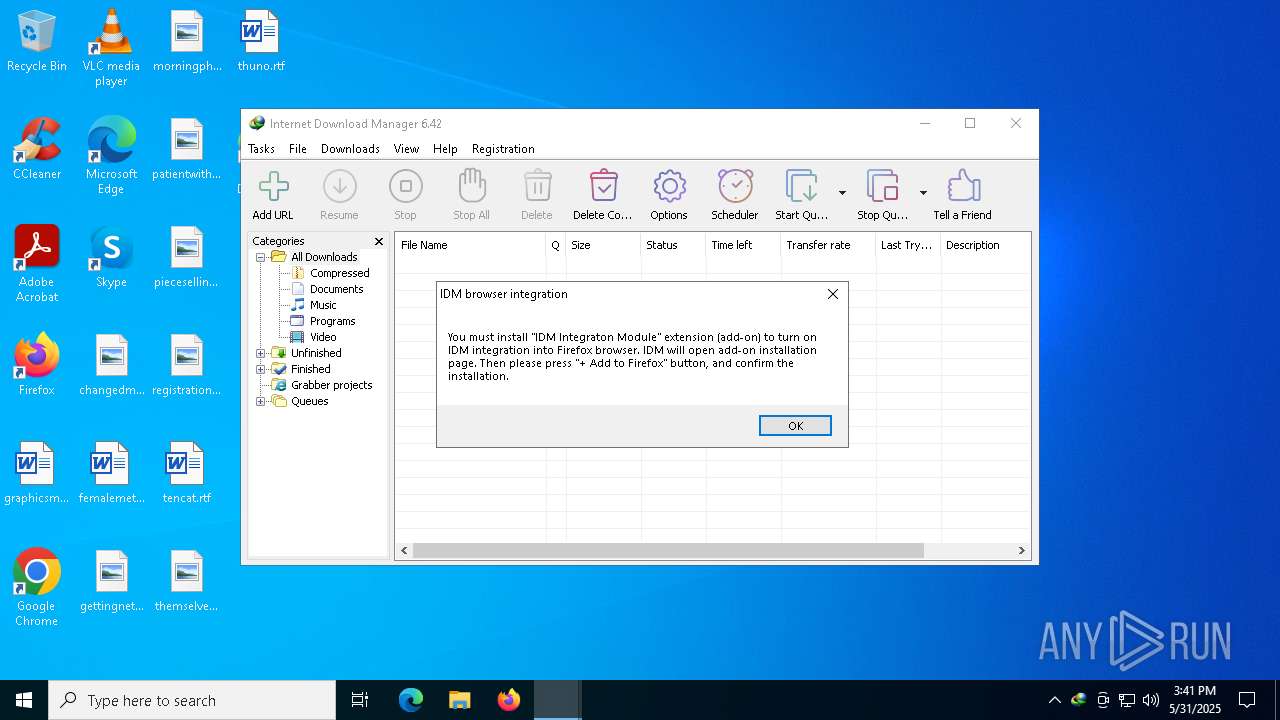
| File name: | Internet Download Manager v6.42 Build20 by Ghost.exe |
| Full analysis: | https://app.any.run/tasks/32287594-2c19-422c-9562-48fa6389c74b |
| Verdict: | Malicious activity |
| Analysis date: | May 31, 2025, 15:40:27 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | 847338A4170A611AECD2DDCCC45985F0 |
| SHA1: | 9F6867C54B155E9E3071C7B8860434E62CDD5A22 |
| SHA256: | 30D8ECEDFC8BC5B13CAB01ECAC80C4E86C34732169E90DDAFCB05FBA778FE67D |
| SSDEEP: | 98304:p8Cgzkib1obp+hPoMi1hezfq7LtPnDbIjDuaHjulHWzCNbSKkGqLq615AqKVH7/i:H0Mui+OuB7d51sj/e1e2Uz |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- IDM1.tmp (PID: 5568)
- IDMan.exe (PID: 4560)
- Uninstall.exe (PID: 4452)
- IDMan.exe (PID: 7232)
GENERIC has been found (auto)
- rundll32.exe (PID: 1452)
- drvinst.exe (PID: 1804)
- Internet Download Manager v6.42 Build20 by Ghost.exe (PID: 5124)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 7952)
- wscript.exe (PID: 8096)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 7952)
- wscript.exe (PID: 8096)
Changes the autorun value in the registry
- rundll32.exe (PID: 1452)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 7952)
- wscript.exe (PID: 8096)
Deletes a file (SCRIPT)
- wscript.exe (PID: 7952)
- wscript.exe (PID: 8096)
Starts NET.EXE for service management
- net.exe (PID: 7548)
- Uninstall.exe (PID: 4452)
SUSPICIOUS
Reads security settings of Internet Explorer
- Internet Download Manager v6.42 Build20 by Ghost.exe (PID: 5124)
- IDM1.tmp (PID: 5568)
- IDMan.exe (PID: 4560)
- Uninstall.exe (PID: 4452)
Starts application with an unusual extension
- idman642build40.exe (PID: 1852)
- cmd.exe (PID: 1196)
Executable content was dropped or overwritten
- Internet Download Manager v6.42 Build20 by Ghost.exe (PID: 5124)
- IDMan.exe (PID: 4560)
- rundll32.exe (PID: 1452)
- drvinst.exe (PID: 1804)
- Fix.exe (PID: 6156)
The process creates files with name similar to system file names
- IDM1.tmp (PID: 5568)
Creates a software uninstall entry
- IDM1.tmp (PID: 5568)
Creates/Modifies COM task schedule object
- IDM1.tmp (PID: 5568)
- regsvr32.exe (PID: 5332)
- regsvr32.exe (PID: 6880)
- regsvr32.exe (PID: 7380)
- IDMan.exe (PID: 4560)
- regsvr32.exe (PID: 7768)
- regsvr32.exe (PID: 7280)
- regsvr32.exe (PID: 2692)
- regsvr32.exe (PID: 900)
- regsvr32.exe (PID: 5304)
Uses RUNDLL32.EXE to load library
- Uninstall.exe (PID: 4452)
Drops a system driver (possible attempt to evade defenses)
- rundll32.exe (PID: 1452)
- drvinst.exe (PID: 1804)
Creates files in the driver directory
- drvinst.exe (PID: 1804)
The process downloads a VBScript from the remote host
- Fix.exe (PID: 6156)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 8096)
- wscript.exe (PID: 7952)
Adds, changes, or deletes HTTP request header (SCRIPT)
- wscript.exe (PID: 7952)
- wscript.exe (PID: 8096)
Creates or modifies Windows services
- drvinst.exe (PID: 7832)
- Uninstall.exe (PID: 4452)
The process executes VB scripts
- Fix.exe (PID: 6156)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 7952)
- wscript.exe (PID: 8096)
Sets XML DOM element text (SCRIPT)
- wscript.exe (PID: 7952)
- wscript.exe (PID: 8096)
There is functionality for taking screenshot (YARA)
- Internet Download Manager v6.42 Build20 by Ghost.exe (PID: 5124)
Uses REG/REGEDIT.EXE to modify registry
- Fix.exe (PID: 6156)
- cmd.exe (PID: 1196)
- cmd.exe (PID: 2908)
Executing commands from a ".bat" file
- Fix.exe (PID: 6156)
- cmd.exe (PID: 1196)
Starts CMD.EXE for commands execution
- Fix.exe (PID: 6156)
- cmd.exe (PID: 516)
- cmd.exe (PID: 1196)
Application launched itself
- cmd.exe (PID: 516)
- cmd.exe (PID: 1196)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 1196)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 1196)
Hides command output
- cmd.exe (PID: 2908)
- cmd.exe (PID: 7716)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7716)
- cmd.exe (PID: 7388)
- cmd.exe (PID: 1196)
INFO
The sample compiled with english language support
- Internet Download Manager v6.42 Build20 by Ghost.exe (PID: 5124)
- IDMan.exe (PID: 4560)
- drvinst.exe (PID: 1804)
- Fix.exe (PID: 6156)
- rundll32.exe (PID: 1452)
Checks supported languages
- Internet Download Manager v6.42 Build20 by Ghost.exe (PID: 5124)
- idman642build40.exe (PID: 1852)
- IDM1.tmp (PID: 5568)
- idmBroker.exe (PID: 6744)
- IDMan.exe (PID: 4560)
- Uninstall.exe (PID: 4452)
- drvinst.exe (PID: 1804)
- Fix.exe (PID: 6156)
- drvinst.exe (PID: 7832)
- chcp.com (PID: 4120)
Reads mouse settings
- Internet Download Manager v6.42 Build20 by Ghost.exe (PID: 5124)
Reads the computer name
- Internet Download Manager v6.42 Build20 by Ghost.exe (PID: 5124)
- idman642build40.exe (PID: 1852)
- IDM1.tmp (PID: 5568)
- idmBroker.exe (PID: 6744)
- IDMan.exe (PID: 4560)
- Uninstall.exe (PID: 4452)
- Fix.exe (PID: 6156)
- drvinst.exe (PID: 1804)
- drvinst.exe (PID: 7832)
Process checks computer location settings
- Internet Download Manager v6.42 Build20 by Ghost.exe (PID: 5124)
- IDM1.tmp (PID: 5568)
- Uninstall.exe (PID: 4452)
- IDMan.exe (PID: 4560)
INTERNETDOWNLOADMANAGER mutex has been found
- idman642build40.exe (PID: 1852)
- IDM1.tmp (PID: 5568)
- IDMan.exe (PID: 4560)
Create files in a temporary directory
- idman642build40.exe (PID: 1852)
- Internet Download Manager v6.42 Build20 by Ghost.exe (PID: 5124)
- IDM1.tmp (PID: 5568)
- IDMan.exe (PID: 4560)
- Fix.exe (PID: 6156)
- rundll32.exe (PID: 1452)
- reg.exe (PID: 7748)
Creates files in the program directory
- IDM1.tmp (PID: 5568)
- IDMan.exe (PID: 4560)
- Fix.exe (PID: 6156)
Creates files or folders in the user directory
- IDM1.tmp (PID: 5568)
- IDMan.exe (PID: 4560)
- Fix.exe (PID: 6156)
Reads the machine GUID from the registry
- IDMan.exe (PID: 4560)
- drvinst.exe (PID: 1804)
Reads the software policy settings
- IDMan.exe (PID: 4560)
- drvinst.exe (PID: 1804)
Checks proxy server information
- IDMan.exe (PID: 4560)
- wscript.exe (PID: 8096)
- wscript.exe (PID: 7952)
Disables trace logs
- IDMan.exe (PID: 4560)
Launch of the file from Registry key
- rundll32.exe (PID: 1452)
Reads the time zone
- runonce.exe (PID: 7456)
Reads security settings of Internet Explorer
- runonce.exe (PID: 7456)
UPX packer has been detected
- Internet Download Manager v6.42 Build20 by Ghost.exe (PID: 5124)
The process uses AutoIt
- Internet Download Manager v6.42 Build20 by Ghost.exe (PID: 5124)
Checks operating system version
- cmd.exe (PID: 1196)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 7292)
- powershell.exe (PID: 1180)
Manual execution by a user
- IDMan.exe (PID: 7232)
Changes the display of characters in the console
- cmd.exe (PID: 1196)
Application launched itself
- firefox.exe (PID: 6560)
- firefox.exe (PID: 4224)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (40) |
|---|---|---|
| .exe | | | UPX compressed Win32 Executable (26) |
| .exe | | | Win32 EXE Yoda's Crypter (25.6) |
| .exe | | | Win32 Executable (generic) (4.3) |
| .exe | | | Generic Win/DOS Executable (1.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:05:31 06:59:07+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 385024 |
| InitializedDataSize: | 12623872 |
| UninitializedDataSize: | 13172736 |
| EntryPoint: | 0xcee9d0 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.42.20.0 |
| ProductVersionNumber: | 16.42.20.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
| FileVersion: | 6.42.20.0 |
| Comments: | Silent install |
| FileDescription: | Internet Download Manager |
| ProductVersion: | 16.42.20.0 |
| CompanyName: | Ghost Productions |
| LegalCopyright: | Ghost |
Total processes
236
Monitored processes
103
Malicious processes
11
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4988 -childID 3 -isForBrowser -prefsHandle 4980 -prefMapHandle 4248 -prefsLen 38176 -prefMapSize 244583 -jsInitHandle 1352 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {1e40817b-a549-478f-89ae-3d84c1f2aa2b} 4224 "\\.\pipe\gecko-crash-server-pipe.4224" 142ddc72a10 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 232 | cmd | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 444 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4872 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 4860 -prefMapHandle 4864 -prefsLen 36588 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {91bb8d83-12cf-4a4f-90cd-72f8e0350632} 4224 "\\.\pipe\gecko-crash-server-pipe.4224" 142ddab5310 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 516 | C:\WINDOWS\system32\cmd.exe /c echo prompt $E | cmd | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | reg query "HKCU\Software\DownloadManager" "/v" "LstCheck" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | powershell.exe "([System.Security.Principal.NTAccount](Get-WmiObject -Class Win32_ComputerSystem).UserName).Translate([System.Security.Principal.SecurityIdentifier]).Value" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 716 | reg query "HKCU\Software\DownloadManager" "/v" "radxcnt" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 776 | "C:\Windows\System32\regsvr32.exe" /s "C:\Program Files (x86)\Internet Download Manager\IDMShellExt64.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | IDMan.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
55 286
Read events
54 813
Write events
331
Delete events
142
Modification events
| (PID) Process: | (5568) IDM1.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Internet Download Manager |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files (x86)\Internet Download Manager\Uninstall.exe | |||
| (PID) Process: | (5568) IDM1.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Internet Download Manager |
| Operation: | write | Name: | DisplayName |
Value: Internet Download Manager | |||
| (PID) Process: | (5568) IDM1.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Internet Download Manager |
| Operation: | write | Name: | DisplayVersion |
Value: 6.42.40 | |||
| (PID) Process: | (5568) IDM1.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Internet Download Manager |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files (x86)\Internet Download Manager\IDMan.exe | |||
| (PID) Process: | (5568) IDM1.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Internet Download Manager |
| Operation: | write | Name: | Publisher |
Value: Tonec Inc. | |||
| (PID) Process: | (5568) IDM1.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Internet Download Manager |
| Operation: | write | Name: | URLInfoAbout |
Value: http://www.internetdownloadmanager.com | |||
| (PID) Process: | (5568) IDM1.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Internet Download Manager |
| Operation: | write | Name: | HelpLink |
Value: http://www.internetdownloadmanager.com/contact_us.html | |||
| (PID) Process: | (5568) IDM1.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{94D09862-1875-4FC9-B434-91CF25C840A1}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (5568) IDM1.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{4BD46AAE-C51F-4BF7-8BC0-2E86E33D1873}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (5568) IDM1.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{0055C089-8582-441B-A0BF-17B458C2A3A8} |
| Operation: | write | Name: | NoExplorer |
Value: 1 | |||
Executable files
20
Suspicious files
73
Text files
38
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5124 | Internet Download Manager v6.42 Build20 by Ghost.exe | C:\Users\admin\AppData\Local\Temp\Ghost\idman642build40.exe | executable | |
MD5:C523542A1E9D110FA18357D4BEC6CF45 | SHA256:F7694BE6DDE9B2D60C2FEE25D44F6AA58757A16C5D45F8BBF4D7DA217559A65F | |||
| 5568 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\Grabber Help.lnk | binary | |
MD5:8EACB34050FBF863FA914FB61563FA53 | SHA256:832E774CAF996F9F4375D68CC0838294E8F8C1F71115E01A77FE3D4504577D1E | |||
| 5568 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\license.lnk | binary | |
MD5:FF8D0178641B125873545108A1A7D2BA | SHA256:9F40C9ADAAD44F3FB281886927F3E695192B019D0FB5DE351DABABD44D3659B4 | |||
| 5568 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\TUTORIALS.lnk | binary | |
MD5:2CFF46ACD0E79C2D8C2EABD602DAD3EB | SHA256:57AADB29FAE4564BD17B794A3D60B2F5BC300EA92E20BD3115114A12549D03CC | |||
| 5568 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\Internet Download Manager.lnk | binary | |
MD5:2DB578821A97EA9FE794C2C1C5E8A1F1 | SHA256:003F50FCC9C0A66C7DEA31A0F28895185462EA2F74E8003EC938890BA8B3BED0 | |||
| 5568 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\IDM Help.lnk | binary | |
MD5:2EDE69C872CE573D335EC30845A196B8 | SHA256:1643678A338348C0FDBEC378AD8234E9A9B145649CDBA75948EDEF2510E4648F | |||
| 5124 | Internet Download Manager v6.42 Build20 by Ghost.exe | C:\Users\admin\AppData\Local\Temp\~DF53F64E2A62CDC1D6.TMP | binary | |
MD5:474DC7DA78BD08BB45C9549DB1A46342 | SHA256:93BFDBCEDD978A3C9B62BC10375509150841D717784E0704F49D098A684148F3 | |||
| 5568 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\Internet Download Manager.lnk | binary | |
MD5:ED00CB0E6093A7C589DD8586B3EB88E9 | SHA256:A387F3E5A5BC510FB10CC7856BCE760B02E3B506C9D70A42DA3369FCB9094919 | |||
| 5568 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\Grabber Help.lnk | binary | |
MD5:C2B159BB3913F6C4691B966B5C89E3A0 | SHA256:3477AB9A34DDD2EC76BA3F29CBBFEAD205790BE71212A93FA6162F1672488128 | |||
| 5124 | Internet Download Manager v6.42 Build20 by Ghost.exe | C:\Users\admin\AppData\Local\Temp\Ghost\Banner.jpg | image | |
MD5:AA2A2EBD443366E37324B87E399A78AE | SHA256:9B4C3645E0AC4D30BE53802511EC952976D2E21847E67485C211B1E6A63F5169 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
23
DNS requests
24
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7560 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7560 | svchost.exe | GET | 200 | 2.20.245.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7952 | wscript.exe | GET | 200 | 142.250.185.227:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
8096 | wscript.exe | GET | 200 | 18.173.205.43:80 | http://ocsps.ssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQg3SSkKA74hABkhmlBtJTz8w3hlAQU%2BWC71OPVNPa49QaAJadz20ZpqJ4CEAOj9NBgMFKjN844CogwMYw%3D | unknown | — | — | whitelisted |
8096 | wscript.exe | GET | 200 | 18.173.205.43:80 | http://ocsps.ssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSOZnI3uW4l91H%2Fnmb99iT4JNV7YwQUv8Fah%2F8o%2BkE9%2FbdP5B2voGFYKb0CEF67H4z5kSV9LdlHbOP2Rts%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5604 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5604 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7952 | wscript.exe | GET | 200 | 142.250.185.227:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7504 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7560 | svchost.exe | 2.20.245.139:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
7560 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7560 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
8096 | wscript.exe | 169.61.27.133:443 | www.internetdownloadmanager.com | SOFTLAYER | US | whitelisted |
7952 | wscript.exe | 188.114.97.3:443 | idm.0dy.ir | CLOUDFLARENET | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
idm.0dy.ir |
| unknown |
www.internetdownloadmanager.com |
| whitelisted |
c.pki.goog |
| whitelisted |
ocsps.ssl.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |