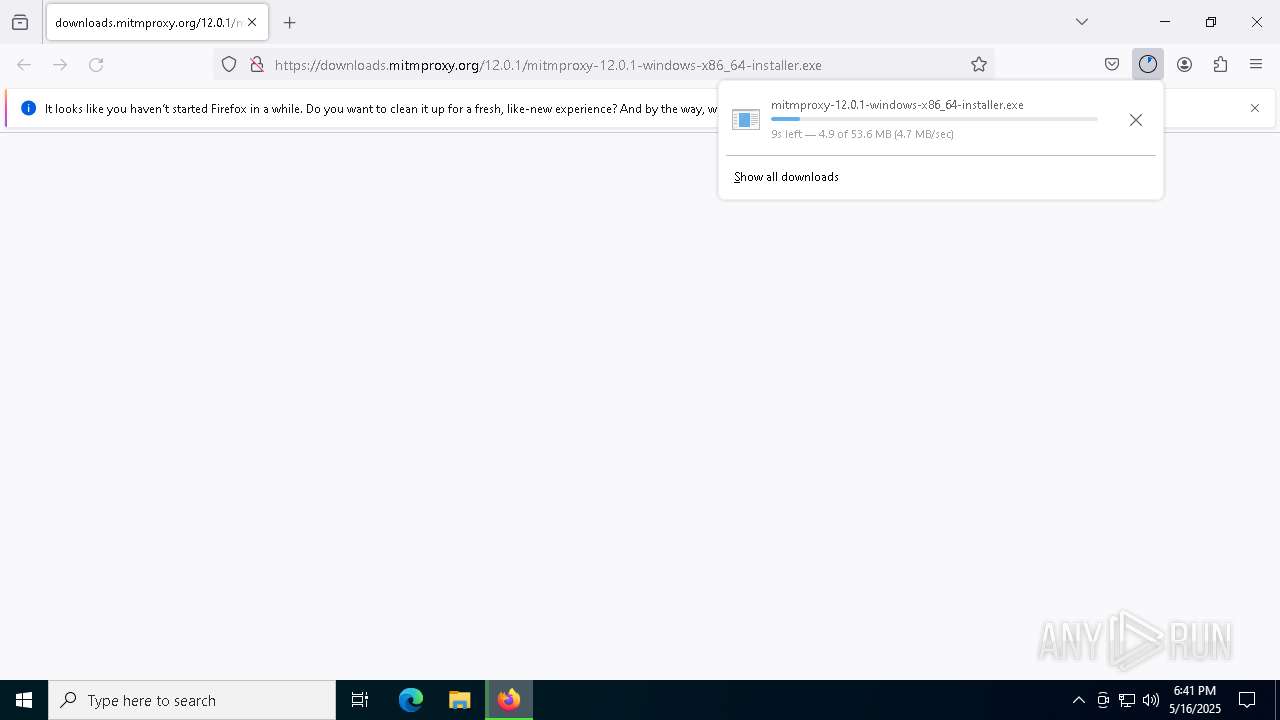
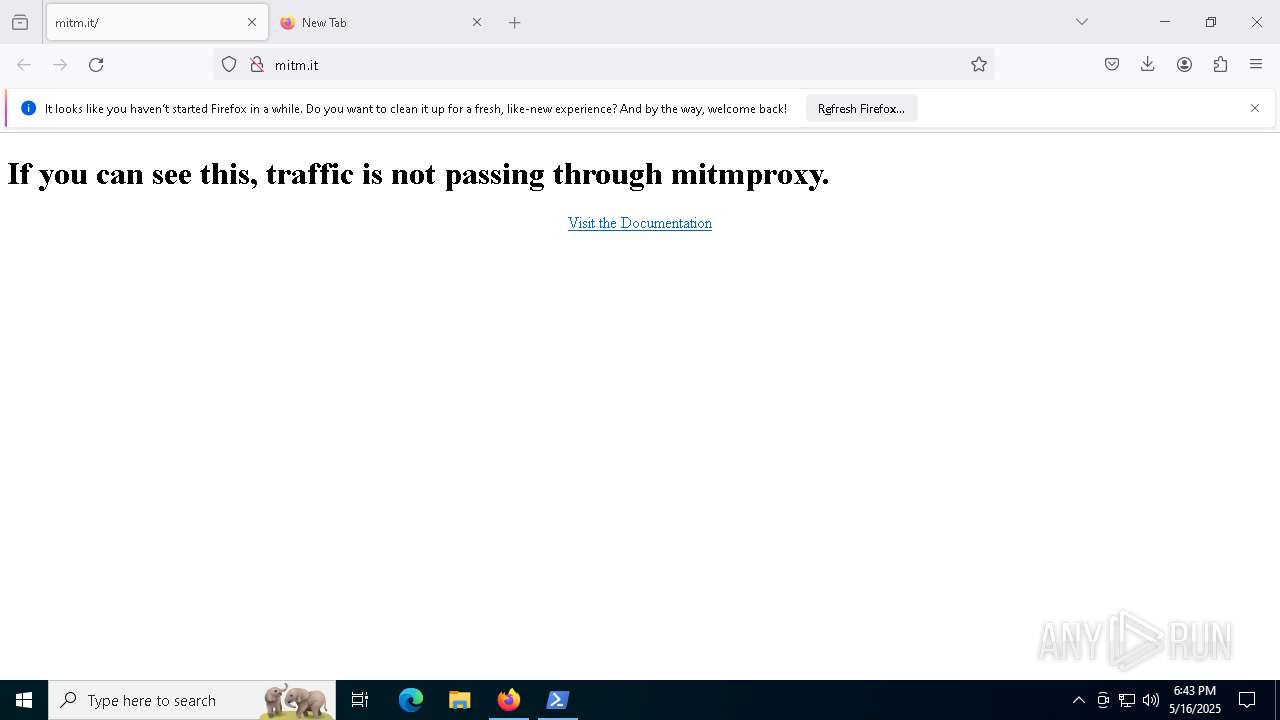
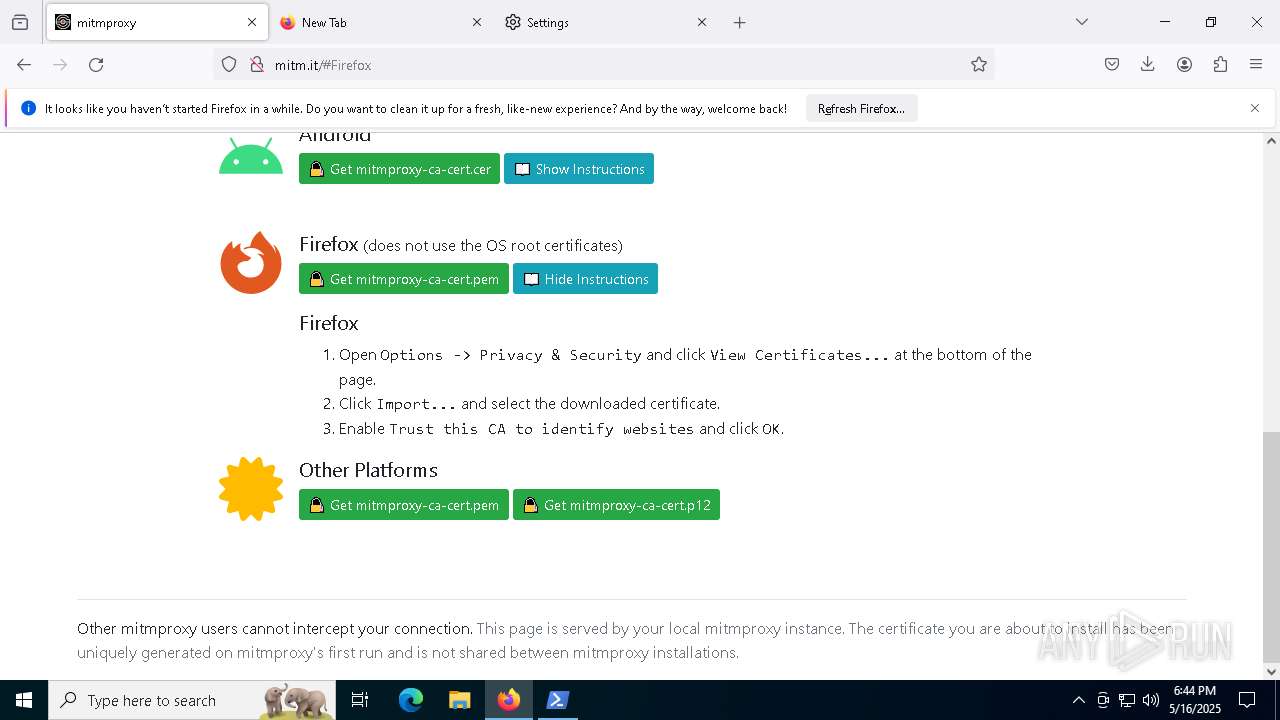
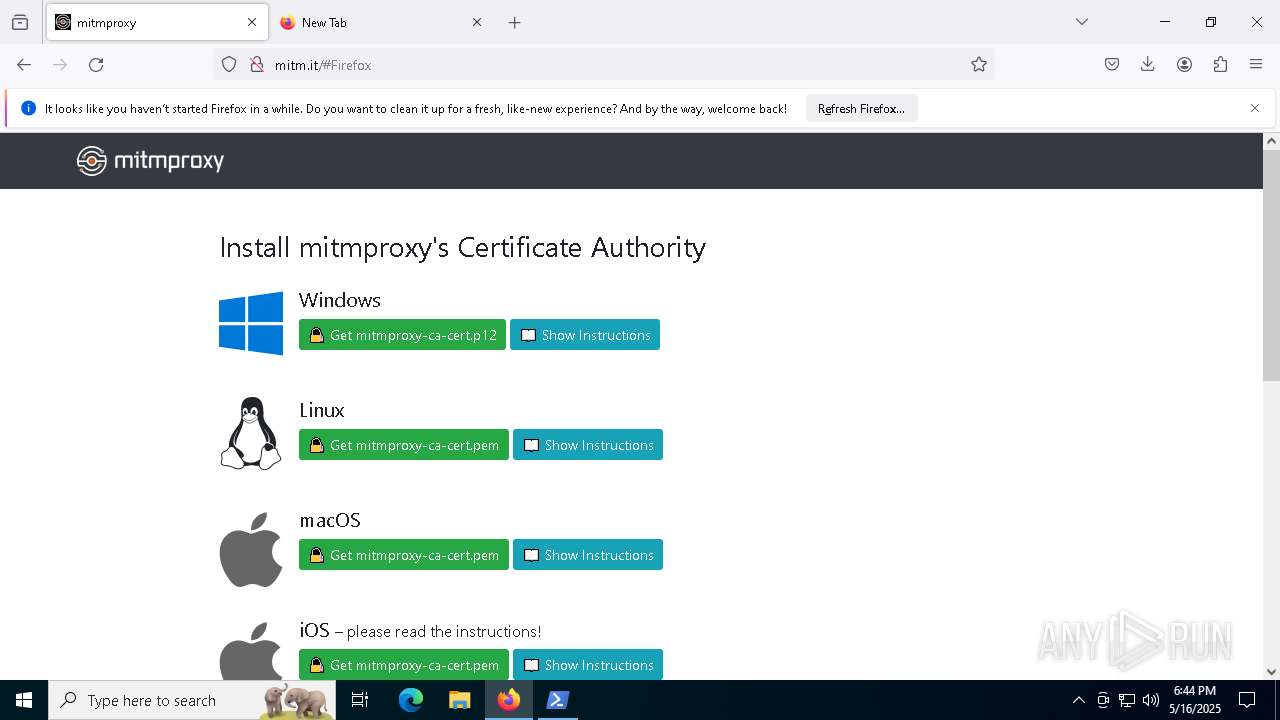
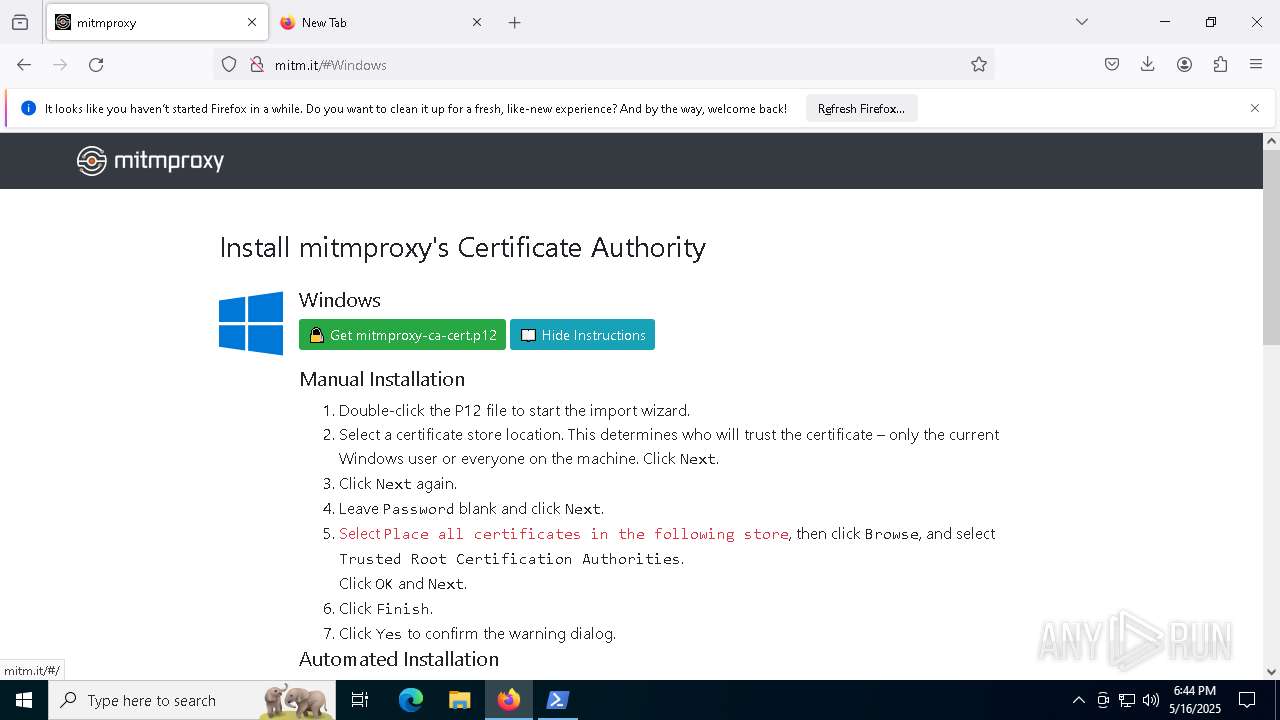
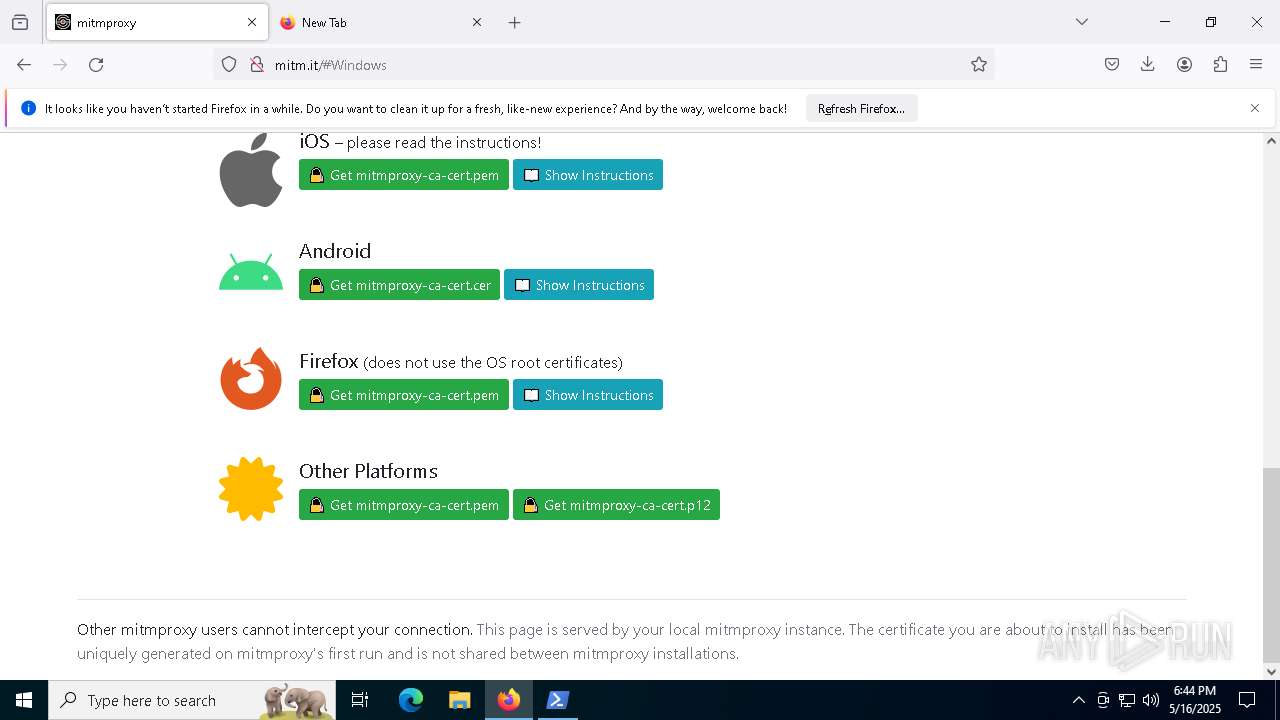
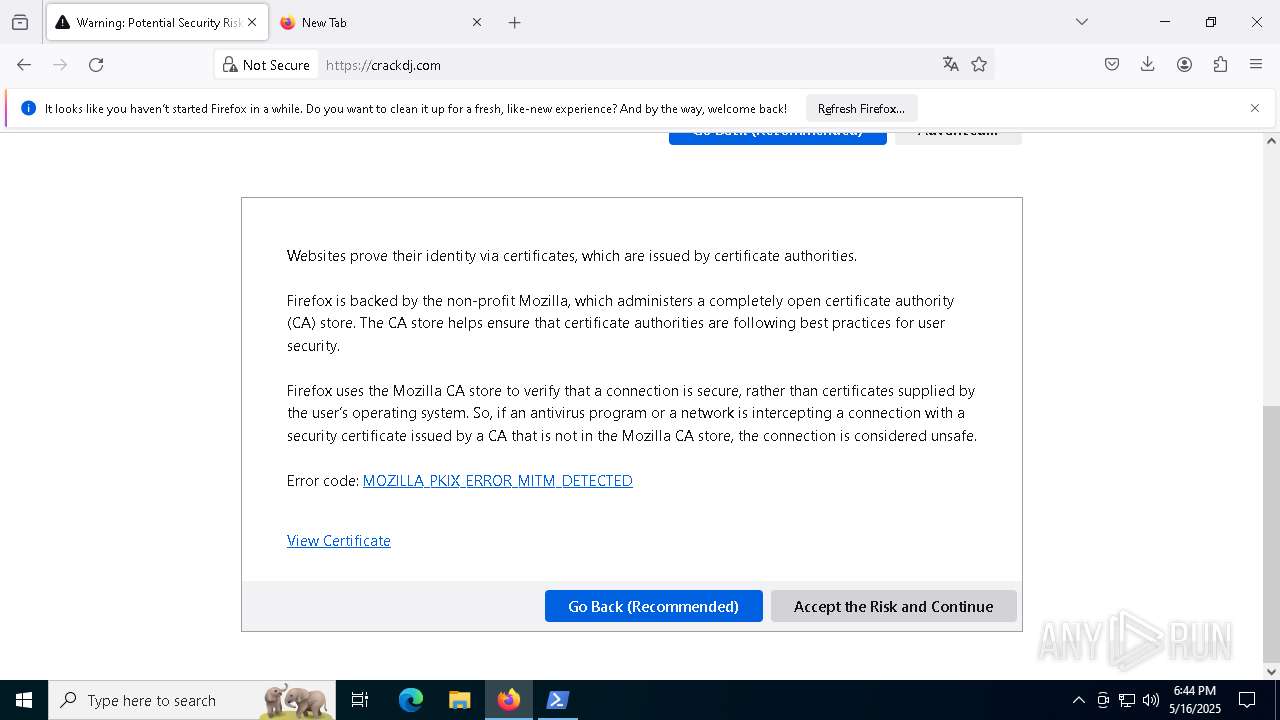
| URL: | https://downloads.mitmproxy.org/12.0.1/mitmproxy-12.0.1-windows-x86_64-installer.exe |
| Full analysis: | https://app.any.run/tasks/5f9da713-e2fc-441b-b903-c445cf387b43 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 18:41:34 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 1D752F98574EDD25F1B4EA186B070CBF |
| SHA1: | DE0C4DD0E86A3505BBB519C5B2548BAE5038E4D1 |
| SHA256: | 30D62023FB7F918322B861A0713B33215BDB6D102087EF86F203B3C1C7368CE7 |
| SSDEEP: | 3:N8SE4Lxu5WTQobISDUXWRBXLNn:2S0chTXLN |
MALICIOUS
Malicious driver has been detected
- mitmproxy-12.0.1-windows-x86_64-installer.exe (PID: 1012)
SUSPICIOUS
Executable content was dropped or overwritten
- mitmproxy-12.0.1-windows-x86_64-installer.exe (PID: 1012)
Process drops python dynamic module
- mitmproxy-12.0.1-windows-x86_64-installer.exe (PID: 1012)
The process drops C-runtime libraries
- mitmproxy-12.0.1-windows-x86_64-installer.exe (PID: 1012)
Starts CMD.EXE for commands execution
- mitmproxy-12.0.1-windows-x86_64-installer.exe (PID: 1012)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1600)
- powershell.exe (PID: 7696)
The process executes Powershell scripts
- cmd.exe (PID: 1600)
Application launched itself
- powershell.exe (PID: 7696)
Process drops legitimate windows executable
- mitmproxy-12.0.1-windows-x86_64-installer.exe (PID: 1012)
Drops a system driver (possible attempt to evade defenses)
- mitmproxy-12.0.1-windows-x86_64-installer.exe (PID: 1012)
Creates a software uninstall entry
- mitmproxy-12.0.1-windows-x86_64-installer.exe (PID: 1012)
There is functionality for taking screenshot (YARA)
- mitmproxy-12.0.1-windows-x86_64-installer.exe (PID: 1012)
INFO
Application launched itself
- firefox.exe (PID: 2800)
- firefox.exe (PID: 5048)
Executable content was dropped or overwritten
- firefox.exe (PID: 2800)
The sample compiled with english language support
- mitmproxy-12.0.1-windows-x86_64-installer.exe (PID: 1012)
Checks supported languages
- mitmproxy-12.0.1-windows-x86_64-installer.exe (PID: 1012)
Reads the computer name
- mitmproxy-12.0.1-windows-x86_64-installer.exe (PID: 1012)
Create files in a temporary directory
- mitmproxy-12.0.1-windows-x86_64-installer.exe (PID: 1012)
Reads CPU info
- mitmproxy-12.0.1-windows-x86_64-installer.exe (PID: 1012)
Reads Environment values
- mitmproxy-12.0.1-windows-x86_64-installer.exe (PID: 1012)
Process checks whether UAC notifications are on
- mitmproxy-12.0.1-windows-x86_64-installer.exe (PID: 1012)
Reads the time zone
- mitmproxy-12.0.1-windows-x86_64-installer.exe (PID: 1012)
Creates files in the program directory
- mitmproxy-12.0.1-windows-x86_64-installer.exe (PID: 1012)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
166
Monitored processes
28
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1012 | "C:\Users\admin\Downloads\mitmproxy-12.0.1-windows-x86_64-installer.exe" | C:\Users\admin\Downloads\mitmproxy-12.0.1-windows-x86_64-installer.exe | firefox.exe | ||||||||||||
User: admin Company: mitmproxy.org Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1272 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1600 | C:\WINDOWS\system32\cmd.exe /s /c " powershell -File "C:\Program Files\mitmproxy\run.ps1" mitmproxy" | C:\Windows\System32\cmd.exe | — | mitmproxy-12.0.1-windows-x86_64-installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2040 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2344 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2800 | "C:\Program Files\Mozilla Firefox\firefox.exe" https://downloads.mitmproxy.org/12.0.1/mitmproxy-12.0.1-windows-x86_64-installer.exe | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 4008 | "C:\Program Files\mitmproxy\bin\mitmproxy.exe" | C:\Program Files\mitmproxy\bin\mitmproxy.exe | powershell.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
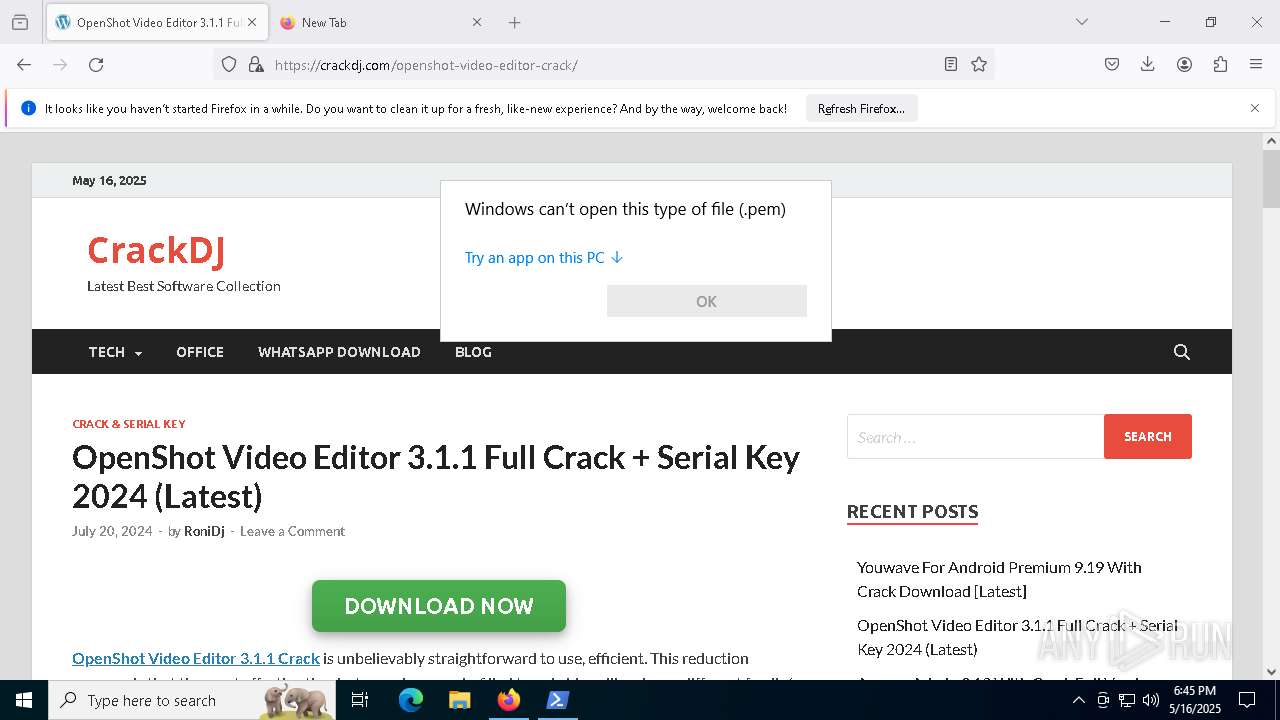
| 4644 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5048 | "C:\Program Files\Mozilla Firefox\firefox.exe" "https://downloads.mitmproxy.org/12.0.1/mitmproxy-12.0.1-windows-x86_64-installer.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
Total events
34 153
Read events
34 128
Write events
25
Delete events
0
Modification events
| (PID) Process: | (2800) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (2800) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (1012) mitmproxy-12.0.1-windows-x86_64-installer.exe | Key: | HKEY_CURRENT_USER\Environment |
| Operation: | write | Name: | Path |
Value: %USERPROFILE%\AppData\Local\Microsoft\WindowsApps;;C:\Program Files\mitmproxy\bin | |||
| (PID) Process: | (1012) mitmproxy-12.0.1-windows-x86_64-installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\mitmproxy 12.0.1 |
| Operation: | write | Name: | DisplayVersion |
Value: 12.0.1 | |||
| (PID) Process: | (1012) mitmproxy-12.0.1-windows-x86_64-installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\mitmproxy 12.0.1 |
| Operation: | write | Name: | Publisher |
Value: mitmproxy.org | |||
| (PID) Process: | (1012) mitmproxy-12.0.1-windows-x86_64-installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\mitmproxy 12.0.1 |
| Operation: | write | Name: | DisplayName |
Value: mitmproxy | |||
| (PID) Process: | (1012) mitmproxy-12.0.1-windows-x86_64-installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\mitmproxy 12.0.1 |
| Operation: | write | Name: | UrlInfoAbout |
Value: | |||
| (PID) Process: | (1012) mitmproxy-12.0.1-windows-x86_64-installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\mitmproxy 12.0.1 |
| Operation: | write | Name: | HelpLink |
Value: | |||
| (PID) Process: | (1012) mitmproxy-12.0.1-windows-x86_64-installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\mitmproxy 12.0.1 |
| Operation: | write | Name: | Comments |
Value: | |||
| (PID) Process: | (1012) mitmproxy-12.0.1-windows-x86_64-installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\mitmproxy 12.0.1 |
| Operation: | write | Name: | Contact |
Value: | |||
Executable files
107
Suspicious files
221
Text files
163
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2800 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 2800 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2823318777ntouromlalnodry--naod.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2800 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:2C99A16AED3906D92FFE3EF1808E2753 | SHA256:08412578CC3BB4922388F8FF8C23962F616B69A1588DA720ADE429129C73C452 | |||
| 2800 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2800 | firefox.exe | C:\Users\admin\Downloads\mitmproxy-12.K2HXb4Zt.0.1-windows-x86_64-installer.exe.part | — | |
MD5:— | SHA256:— | |||
| 2800 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:C95DDC2B1A525D1A243E4C294DA2F326 | SHA256:3A5919E086BFB31E36110CF636D2D5109EB51F2C410B107F126126AB25D67363 | |||
| 2800 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 2800 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\datareporting\glean\db\data.safe.bin | binary | |
MD5:D30F5B10F3D4B3992E4D666F622163F4 | SHA256:2585819A7401A308DA879FA416278E473CEA5F6D0D24C59F514C5A698C61D03A | |||
| 2800 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 2800 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
125
TCP/UDP connections
148
DNS requests
138
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.185:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2800 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
2800 | firefox.exe | POST | 200 | 172.217.16.195:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
2800 | firefox.exe | POST | 200 | 184.24.77.55:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
2800 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
2800 | firefox.exe | POST | 200 | 184.24.77.78:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
2800 | firefox.exe | POST | 200 | 172.217.16.195:80 | http://o.pki.goog/s/wr3/FIY | unknown | — | — | whitelisted |
2800 | firefox.exe | POST | 200 | 184.24.77.78:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
2800 | firefox.exe | POST | 200 | 172.217.16.195:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.185:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2800 | firefox.exe | 34.36.137.203:443 | contile.services.mozilla.com | — | — | whitelisted |
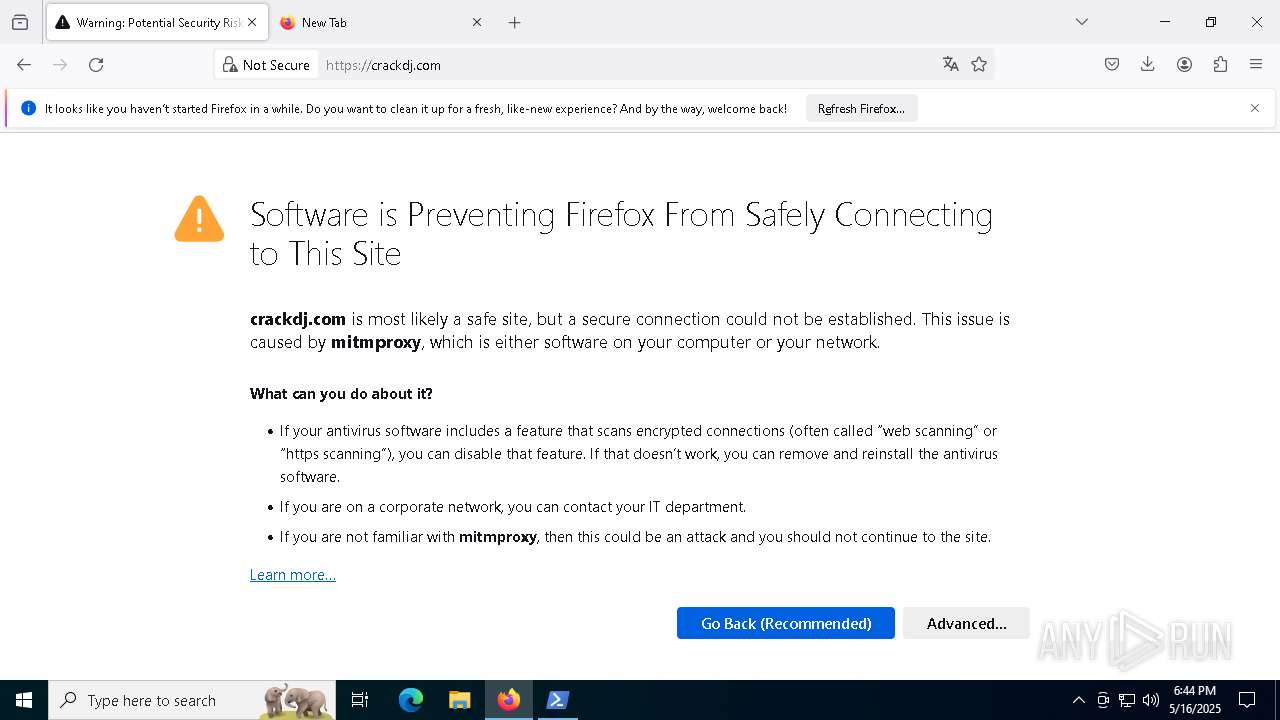
2800 | firefox.exe | 104.21.38.107:443 | downloads.mitmproxy.org | CLOUDFLARENET | — | malicious |
2800 | firefox.exe | 34.107.243.93:443 | push.services.mozilla.com | GOOGLE | US | whitelisted |
2800 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
2800 | firefox.exe | 184.24.77.55:80 | r10.o.lencr.org | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
downloads.mitmproxy.org |
| malicious |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |