| File name: | 2025-05-16_467e55c524dd01b06e00be38e7151a0e_black-basta_elex_gcleaner_hijackloader_remcos |
| Full analysis: | https://app.any.run/tasks/9caa95d4-7743-447c-813c-42d35030d978 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 15:50:24 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | 467E55C524DD01B06E00BE38E7151A0E |
| SHA1: | 7250582746A80D54EB0F4C8520FFEB6F845C0146 |
| SHA256: | 30C832170ED8B795F21A97819C06EA24F8C9DB242A02B36E912DF76BF547BDF3 |
| SSDEEP: | 98304:zSYpVEm5sn6gNEkdfaTgmHihuRB3FKMvXj07kkFGZur7yv5FkGSthza1U7SZRYyr:5MGddJMGVqWMpdLTW |
MALICIOUS
Executing a file with an untrusted certificate
- 4972954724.exe (PID: 5552)
- 4972954724.exe (PID: 4120)
- install.exe (PID: 4448)
CANBIS mutex has been found
- 2025-05-16_467e55c524dd01b06e00be38e7151a0e_black-basta_elex_gcleaner_hijackloader_remcos.exe (PID: 3784)
SUSPICIOUS
There is functionality for communication over UDP network (YARA)
- 2025-05-16_467e55c524dd01b06e00be38e7151a0e_black-basta_elex_gcleaner_hijackloader_remcos.exe (PID: 3784)
Process drops legitimate windows executable
- 2025-05-16_467e55c524dd01b06e00be38e7151a0e_black-basta_elex_gcleaner_hijackloader_remcos.exe (PID: 3784)
- 4972954724.exe (PID: 4120)
- msiexec.exe (PID: 5400)
- TiWorker.exe (PID: 4200)
Reads security settings of Internet Explorer
- 2025-05-16_467e55c524dd01b06e00be38e7151a0e_black-basta_elex_gcleaner_hijackloader_remcos.exe (PID: 3784)
- install.exe (PID: 4448)
Executable content was dropped or overwritten
- 2025-05-16_467e55c524dd01b06e00be38e7151a0e_black-basta_elex_gcleaner_hijackloader_remcos.exe (PID: 3784)
- 4972954724.exe (PID: 4120)
- TiWorker.exe (PID: 4200)
Starts a Microsoft application from unusual location
- 4972954724.exe (PID: 4120)
- 4972954724.exe (PID: 5552)
Creates file in the systems drive root
- 4972954724.exe (PID: 4120)
- msiexec.exe (PID: 5400)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 5400)
- install.exe (PID: 4448)
The process drops C-runtime libraries
- msiexec.exe (PID: 5400)
- TiWorker.exe (PID: 4200)
INFO
Checks supported languages
- 2025-05-16_467e55c524dd01b06e00be38e7151a0e_black-basta_elex_gcleaner_hijackloader_remcos.exe (PID: 3784)
- 4972954724.exe (PID: 4120)
- install.exe (PID: 4448)
- msiexec.exe (PID: 5400)
Reads the computer name
- 2025-05-16_467e55c524dd01b06e00be38e7151a0e_black-basta_elex_gcleaner_hijackloader_remcos.exe (PID: 3784)
- 4972954724.exe (PID: 4120)
- install.exe (PID: 4448)
- msiexec.exe (PID: 5400)
The sample compiled with english language support
- 2025-05-16_467e55c524dd01b06e00be38e7151a0e_black-basta_elex_gcleaner_hijackloader_remcos.exe (PID: 3784)
- 4972954724.exe (PID: 4120)
- msiexec.exe (PID: 5400)
- TiWorker.exe (PID: 4200)
Process checks computer location settings
- 2025-05-16_467e55c524dd01b06e00be38e7151a0e_black-basta_elex_gcleaner_hijackloader_remcos.exe (PID: 3784)
Failed to create an executable file in Windows directory
- 2025-05-16_467e55c524dd01b06e00be38e7151a0e_black-basta_elex_gcleaner_hijackloader_remcos.exe (PID: 3784)
Reads the machine GUID from the registry
- 4972954724.exe (PID: 4120)
- install.exe (PID: 4448)
- msiexec.exe (PID: 5400)
The sample compiled with korean language support
- 4972954724.exe (PID: 4120)
- msiexec.exe (PID: 5400)
- TiWorker.exe (PID: 4200)
The sample compiled with french language support
- 4972954724.exe (PID: 4120)
- msiexec.exe (PID: 5400)
The sample compiled with japanese language support
- 4972954724.exe (PID: 4120)
- msiexec.exe (PID: 5400)
- TiWorker.exe (PID: 4200)
Create files in a temporary directory
- install.exe (PID: 4448)
The sample compiled with Italian language support
- 4972954724.exe (PID: 4120)
- msiexec.exe (PID: 5400)
- TiWorker.exe (PID: 4200)
The sample compiled with spanish language support
- 4972954724.exe (PID: 4120)
- msiexec.exe (PID: 5400)
- TiWorker.exe (PID: 4200)
The sample compiled with german language support
- 4972954724.exe (PID: 4120)
- msiexec.exe (PID: 5400)
- TiWorker.exe (PID: 4200)
The sample compiled with chinese language support
- 4972954724.exe (PID: 4120)
- msiexec.exe (PID: 5400)
- TiWorker.exe (PID: 4200)
Creates files or folders in the user directory
- install.exe (PID: 4448)
Reads the software policy settings
- install.exe (PID: 4448)
- msiexec.exe (PID: 5400)
- slui.exe (PID: 5392)
- TiWorker.exe (PID: 4200)
Checks proxy server information
- install.exe (PID: 4448)
- slui.exe (PID: 5392)
Executable content was dropped or overwritten
- msiexec.exe (PID: 5400)
Creates a software uninstall entry
- msiexec.exe (PID: 5400)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Borland Delphi 7 (55.2) |
|---|---|---|
| .exe | | | Win32 Executable Borland Delphi 5 (37.5) |
| .exe | | | InstallShield setup (3.5) |
| .exe | | | Win32 Executable Delphi generic (1.1) |
| .scr | | | Windows screen saver (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 46080 |
| InitializedDataSize: | 7680 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc254 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
131
Monitored processes
7
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3784 | "C:\Users\admin\Desktop\2025-05-16_467e55c524dd01b06e00be38e7151a0e_black-basta_elex_gcleaner_hijackloader_remcos.exe" | C:\Users\admin\Desktop\2025-05-16_467e55c524dd01b06e00be38e7151a0e_black-basta_elex_gcleaner_hijackloader_remcos.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 5 Modules
| |||||||||||||||
| 4120 | "C:\Users\admin\Desktop\4972954724.exe" | C:\Users\admin\Desktop\4972954724.exe | 2025-05-16_467e55c524dd01b06e00be38e7151a0e_black-basta_elex_gcleaner_hijackloader_remcos.exe | ||||||||||||
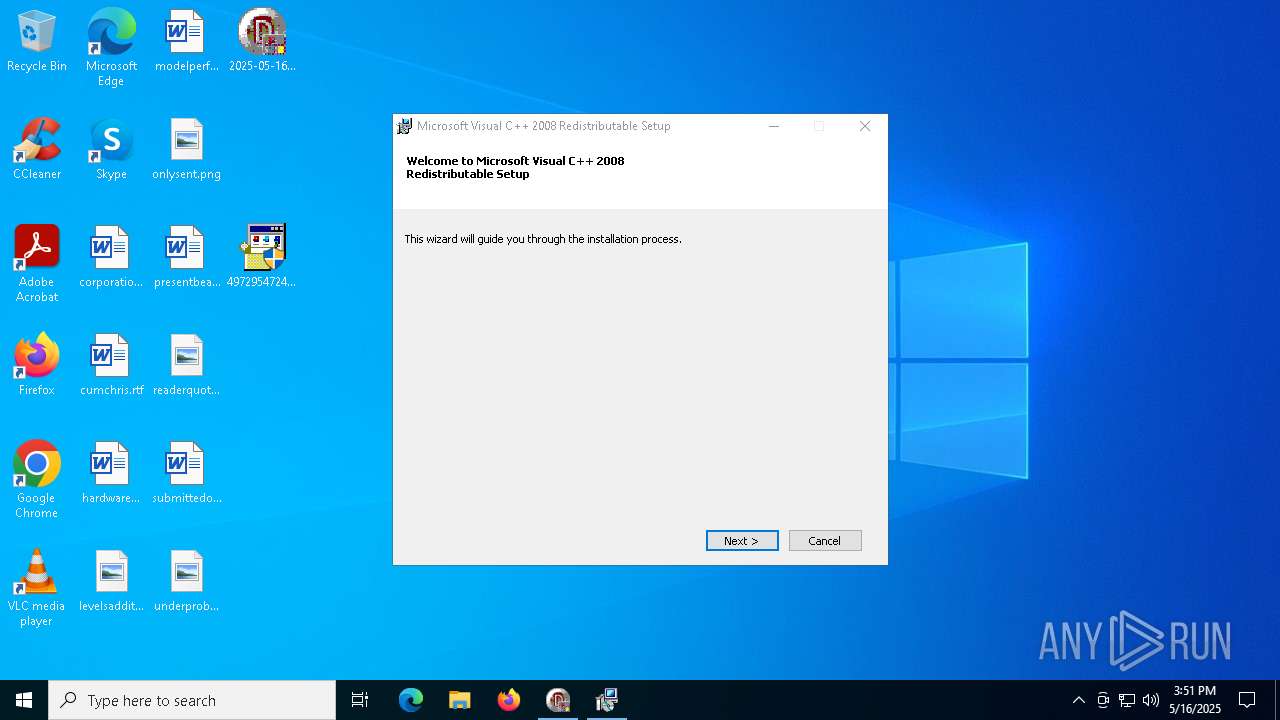
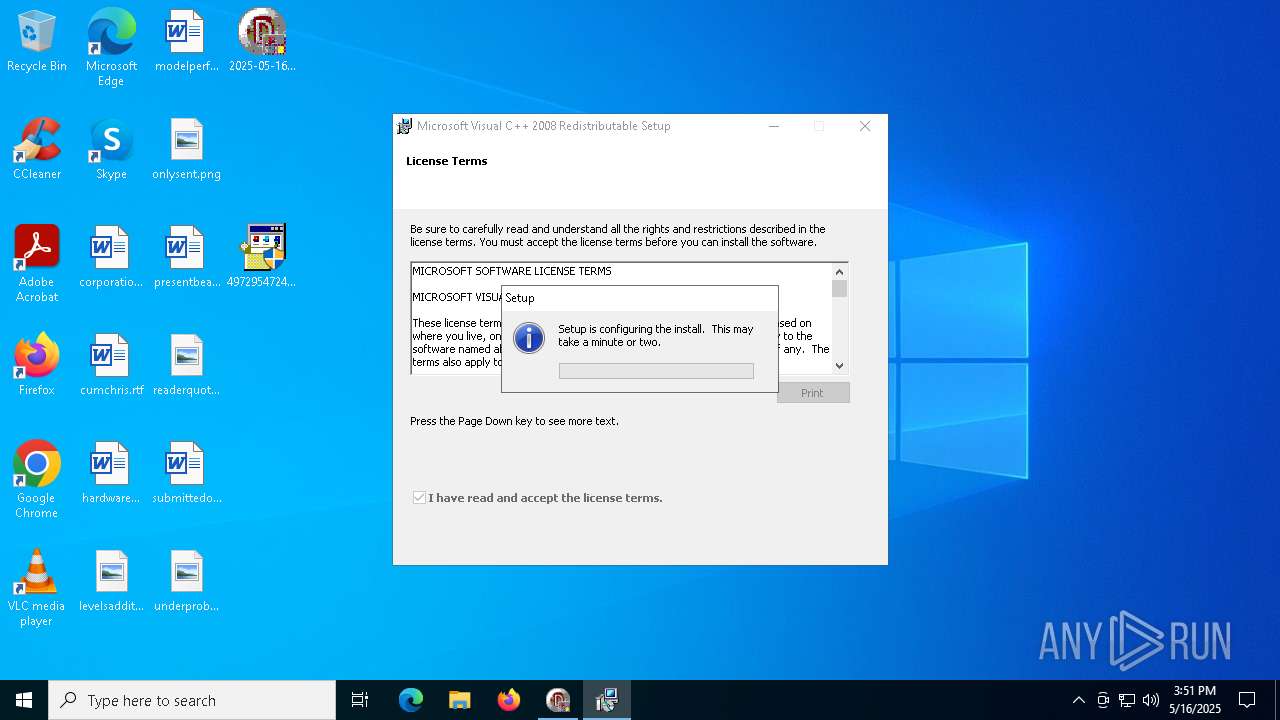
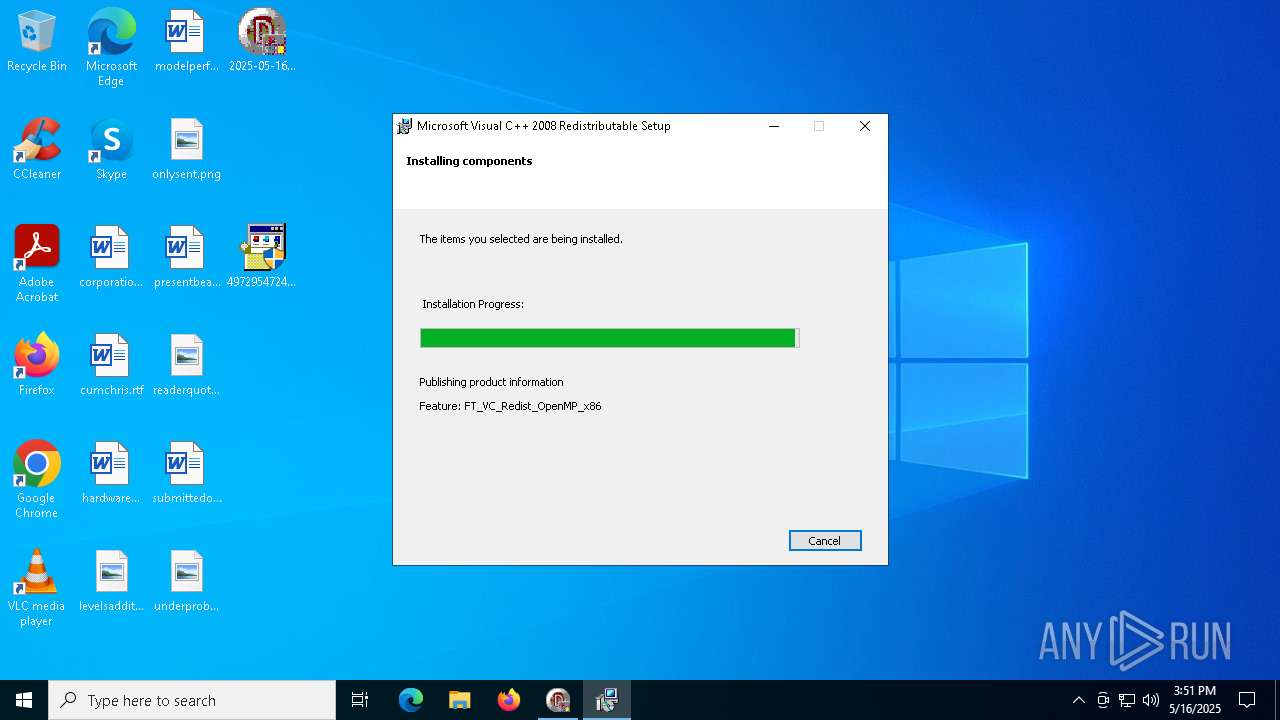
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2008 Redistributable Setup Exit code: 0 Version: 9.0.21022.08 Modules
| |||||||||||||||
| 4200 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4448 | c:\43da19558e196340877fcb02\.\install.exe | C:\43da19558e196340877fcb02\install.exe | 4972954724.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: External Installer Exit code: 0 Version: 9.0.21022.8 built by: RTM Modules
| |||||||||||||||
| 5392 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5400 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5552 | "C:\Users\admin\Desktop\4972954724.exe" | C:\Users\admin\Desktop\4972954724.exe | — | 2025-05-16_467e55c524dd01b06e00be38e7151a0e_black-basta_elex_gcleaner_hijackloader_remcos.exe | |||||||||||
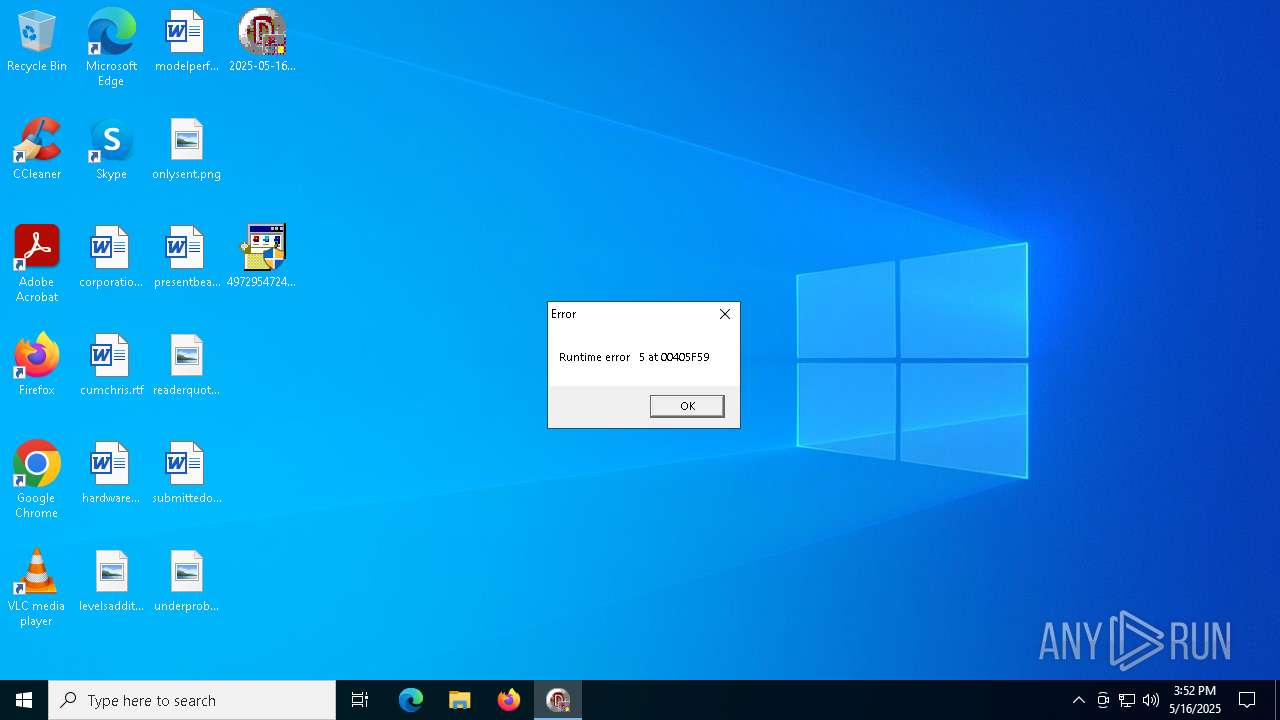
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Visual C++ 2008 Redistributable Setup Exit code: 3221226540 Version: 9.0.21022.08 Modules
| |||||||||||||||
Total events
16 439
Read events
15 982
Write events
386
Delete events
71
Modification events
| (PID) Process: | (5400) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | c:\Config.Msi\ |
Value: | |||
| (PID) Process: | (5400) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\4B35AE21A043D5F31BCBA4B3CEA4987A |
| Operation: | write | Name: | 6F9E66FF7E38E3A3FA41D89E8A906A4A |
Value: | |||
| (PID) Process: | (5400) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\CC1E60A59C989BD3B98CB5AF655BB8BF |
| Operation: | write | Name: | 6F9E66FF7E38E3A3FA41D89E8A906A4A |
Value: | |||
| (PID) Process: | (5400) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\A175F2FF45C63E132BE3A20682B3808A |
| Operation: | write | Name: | 6F9E66FF7E38E3A3FA41D89E8A906A4A |
Value: >mfc90cht.dll\Microsoft.VC90.MFCLOC,version="9.0.21022.8",publicKeyToken="1fc8b3b9a1e18e3b",processorArchitecture="x86",type="win32" | |||
| (PID) Process: | (5400) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\F04C2F9CDC82C2930A3CA3DACE31C0A0 |
| Operation: | write | Name: | 6F9E66FF7E38E3A3FA41D89E8A906A4A |
Value: | |||
| (PID) Process: | (5400) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\EC2108D4EC2B3943198B8B9A9B286F8B |
| Operation: | write | Name: | 6F9E66FF7E38E3A3FA41D89E8A906A4A |
Value: | |||
| (PID) Process: | (5400) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\0D8ABEF022D5A3D349D755E992FB70FD |
| Operation: | write | Name: | 6F9E66FF7E38E3A3FA41D89E8A906A4A |
Value: >\policy.9.0.Microsoft.VC90.MFCLOC,version="9.0.21022.8",publicKeyToken="1fc8b3b9a1e18e3b",processorArchitecture="x86",type="win32-policy" | |||
| (PID) Process: | (5400) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\64C620F6CB6D50833A0B11A78F749382 |
| Operation: | write | Name: | 6F9E66FF7E38E3A3FA41D89E8A906A4A |
Value: | |||
| (PID) Process: | (5400) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\AA35D58AD6095C13693E2EB19B51E4C2 |
| Operation: | write | Name: | 6F9E66FF7E38E3A3FA41D89E8A906A4A |
Value: | |||
| (PID) Process: | (5400) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\3F4F115D119AFC23CA11C979FE49B8CF |
| Operation: | write | Name: | 6F9E66FF7E38E3A3FA41D89E8A906A4A |
Value: >vcomp90.dll\Microsoft.VC90.OpenMP,version="9.0.21022.8",publicKeyToken="1fc8b3b9a1e18e3b",processorArchitecture="x86",type="win32" | |||
Executable files
86
Suspicious files
47
Text files
101
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4120 | 4972954724.exe | C:\43da19558e196340877fcb02\install.res.1041.dll | executable | |
MD5:13ED4517152203DE4BC52ACC0255D952 | SHA256:6183324FE24006BC3D8928029DCACCBDAE517EB09727F5DD47EA5AAEED3EE26D | |||
| 4120 | 4972954724.exe | C:\43da19558e196340877fcb02\vc_red.msi | executable | |
MD5:E0951D3CB1038EB2D2B2B2F336E1AB32 | SHA256:507AC60E145057764F13CF1AD5366A7E15DDC0DA5CC22216F69E3482697D5E88 | |||
| 4120 | 4972954724.exe | C:\43da19558e196340877fcb02\install.res.1033.dll | executable | |
MD5:9EDEB8B1C5C0A4CD3A3016B85108127D | SHA256:9BF7026A47DAAB7BB2948FD23E8CF42C06DD2E19EF8CDEA0AF7367453674A8F9 | |||
| 4120 | 4972954724.exe | C:\43da19558e196340877fcb02\install.exe | executable | |
MD5:520A6D1CBCC9CF642C625FE814C93C58 | SHA256:08966CE743AA1CBED0874933E104EF7B913188ECD8F0C679F7D8378516C51DA2 | |||
| 4120 | 4972954724.exe | C:\43da19558e196340877fcb02\install.res.1042.dll | executable | |
MD5:0D4FB4095EA49C1EC89B9E8DB0B936A3 | SHA256:7D86F3BA0232C2AC4B4FCE96E4CEBB23700312A032D5D0DB988EC6B358BE1686 | |||
| 4120 | 4972954724.exe | C:\43da19558e196340877fcb02\install.res.1036.dll | executable | |
MD5:5B6FF470CFA7087690E61F87E81EF78A | SHA256:2D1C0A1B17266CFF3BE7D46CF3020B176E4A058FD7FC57F7B6B97E0760CC45DB | |||
| 4120 | 4972954724.exe | C:\43da19558e196340877fcb02\install.res.1040.dll | executable | |
MD5:6310AB8FC9E3DBEE80592FC453A34FEE | SHA256:7774F2436C96A70B0CDC8176883EE7A4614353F17AD61BFBD5A8D7A1906483D3 | |||
| 4120 | 4972954724.exe | C:\43da19558e196340877fcb02\eula.1042.txt | text | |
MD5:9147A93F43D8E58218EBCB15FDA888C9 | SHA256:A75019AC38E0D3570633FA282F3D95D20763657F4A2FE851FAE52A3185D1EDED | |||
| 4120 | 4972954724.exe | C:\43da19558e196340877fcb02\install.res.1028.dll | executable | |
MD5:4151A4D07640863783F837E588235837 | SHA256:58475A90250C6818F73763775EEA6379E06DA6C38E8D2CF0F54EB6112A0A6AEE | |||
| 4120 | 4972954724.exe | C:\43da19558e196340877fcb02\eula.1040.txt | text | |
MD5:9147A93F43D8E58218EBCB15FDA888C9 | SHA256:A75019AC38E0D3570633FA282F3D95D20763657F4A2FE851FAE52A3185D1EDED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
21
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4448 | install.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/CSPCA.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6040 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4448 | install.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
5392 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
uk.undernet.org |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |