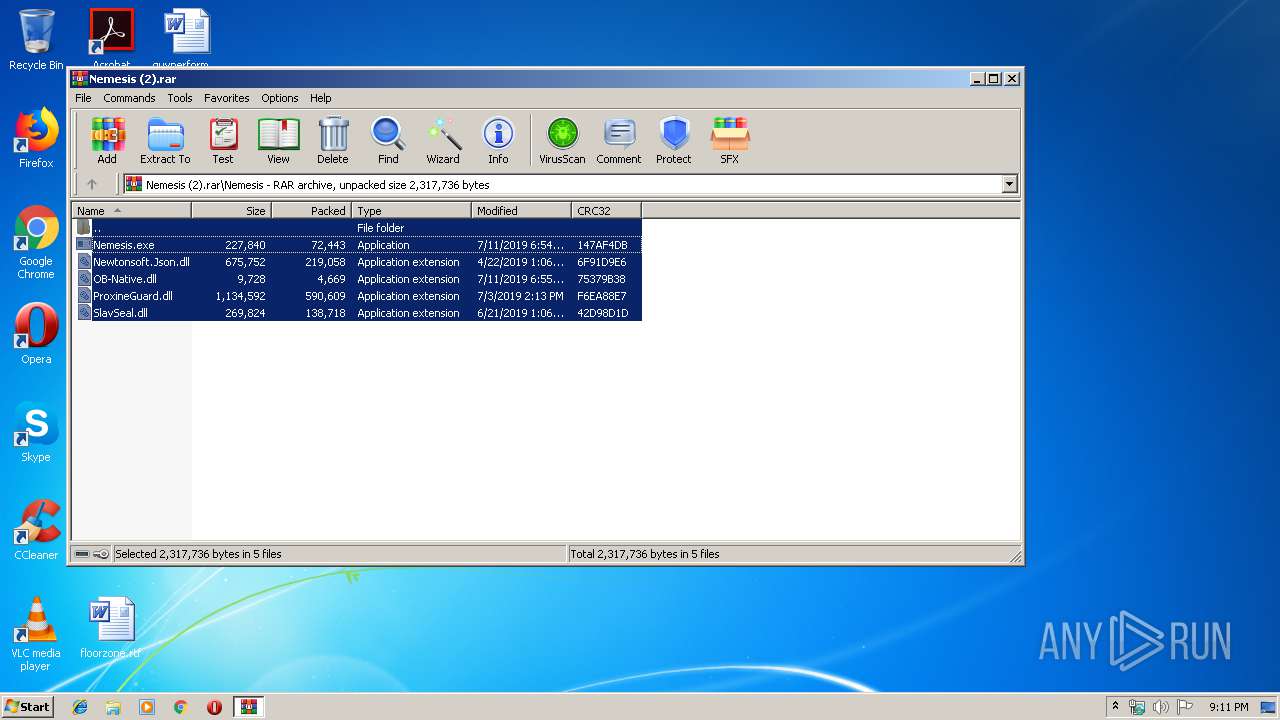
| File name: | Nemesis (2).rar |
| Full analysis: | https://app.any.run/tasks/780f58fe-675e-433d-9ab1-a2336c585ee3 |
| Verdict: | Malicious activity |
| Analysis date: | July 11, 2019, 20:11:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | BFDA8B8489B38CCAE1128CB81D432CAE |
| SHA1: | 2F4903293EFF13782EC8873F36C0FA3865FE1D62 |
| SHA256: | 30B3286EA1D76124C9A2DA704C5628C097C93B69042D3468CF39F201DE01AF0B |
| SSDEEP: | 24576:6k9gvKhtDYP5kqRxaP5dz2ssi7SyrVS0mB96i5:6kivKHEP5re5Upj0m76o |
MALICIOUS
Application was dropped or rewritten from another process
- Nemesis.exe (PID: 3100)
- Nemesis.exe (PID: 1148)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1808)
- Nemesis.exe (PID: 1148)
Changes settings of System certificates
- Nemesis.exe (PID: 1148)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2392)
- Nemesis.exe (PID: 1148)
Reads internet explorer settings
- Nemesis.exe (PID: 1148)
Adds / modifies Windows certificates
- Nemesis.exe (PID: 1148)
INFO
Reads settings of System Certificates
- Nemesis.exe (PID: 1148)
Manual execution by user
- Nemesis.exe (PID: 3100)
- Nemesis.exe (PID: 1148)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
42
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1148 | "C:\Users\admin\Desktop\Nemesis.exe" | C:\Users\admin\Desktop\Nemesis.exe | explorer.exe | ||||||||||||
User: admin Company: 19754 Integrity Level: HIGH Description: Nemesis Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1808 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe8_ Global\UsGthrCtrlFltPipeMssGthrPipe8 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2392 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Nemesis (2).rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3100 | "C:\Users\admin\Desktop\Nemesis.exe" | C:\Users\admin\Desktop\Nemesis.exe | — | explorer.exe | |||||||||||
User: admin Company: 19754 Integrity Level: MEDIUM Description: Nemesis Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
491
Read events
460
Write events
31
Delete events
0
Modification events
| (PID) Process: | (2392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2392) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Nemesis (2).rar | |||
| (PID) Process: | (2392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1148) Nemesis.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Nemesis_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1148) Nemesis.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Nemesis_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
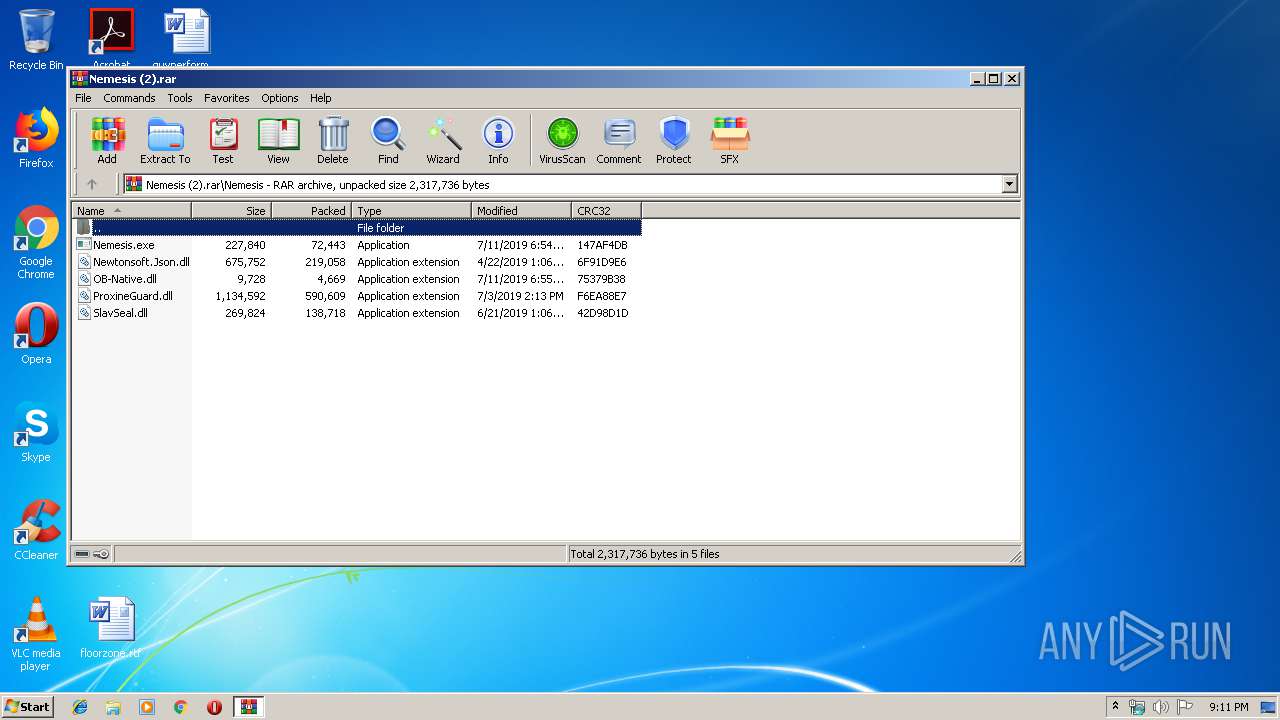
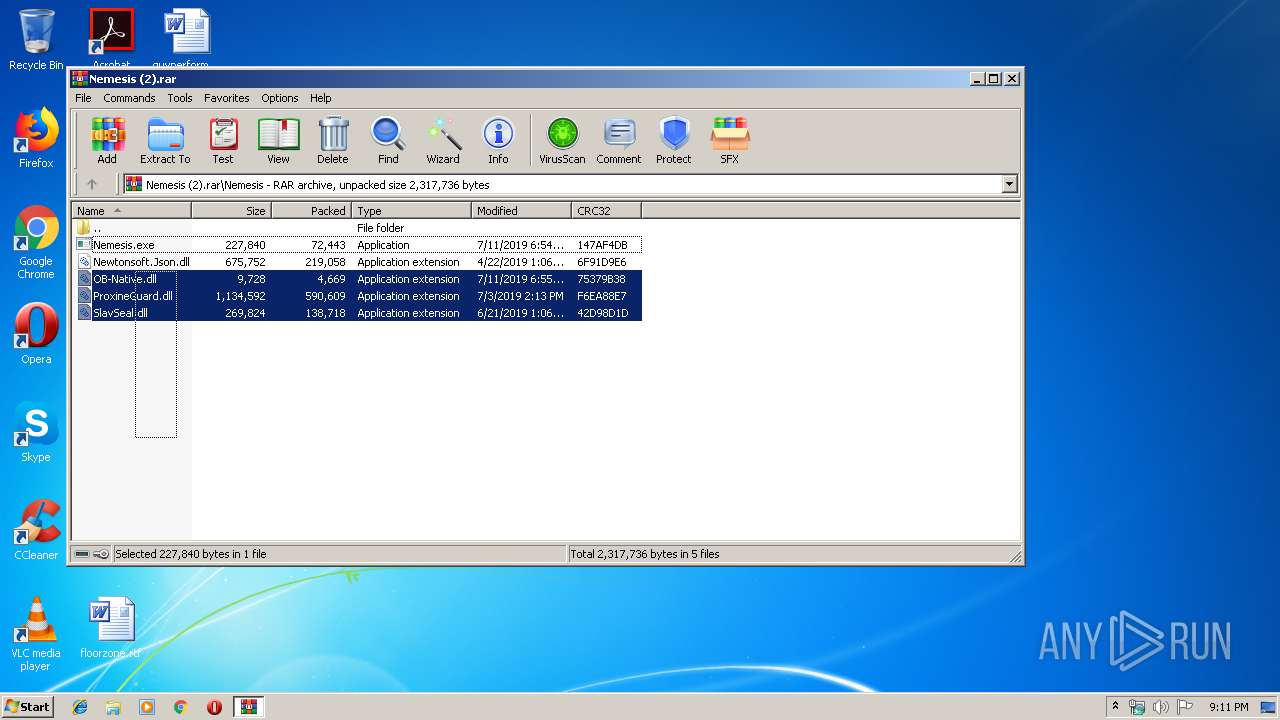
Executable files
6
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2392.39104\Nemesis\Nemesis.exe | executable | |
MD5:— | SHA256:— | |||
| 2392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2392.39104\Nemesis\ProxineGuard.dll | executable | |
MD5:— | SHA256:— | |||
| 2392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2392.39104\Nemesis\OB-Native.dll | executable | |
MD5:E833484E615275397572EE4521212A3B | SHA256:1623CE75EAFBEA439B2DDB02C3D186DB9541D21CAD4D583096FCF1DFE4AD28A1 | |||
| 2392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2392.39104\Nemesis\SlavSeal.dll | executable | |
MD5:— | SHA256:— | |||
| 1148 | Nemesis.exe | C:\Users\admin\Desktop\OB-Native.dll | executable | |
MD5:E833484E615275397572EE4521212A3B | SHA256:1623CE75EAFBEA439B2DDB02C3D186DB9541D21CAD4D583096FCF1DFE4AD28A1 | |||
| 2392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2392.39104\Nemesis\Newtonsoft.Json.dll | executable | |
MD5:4DF6C8781E70C3A4912B5BE796E6D337 | SHA256:3598CCCAD5B535FEA6F93662107A4183BFD6167BF1D0F80260436093EDC2E3AF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
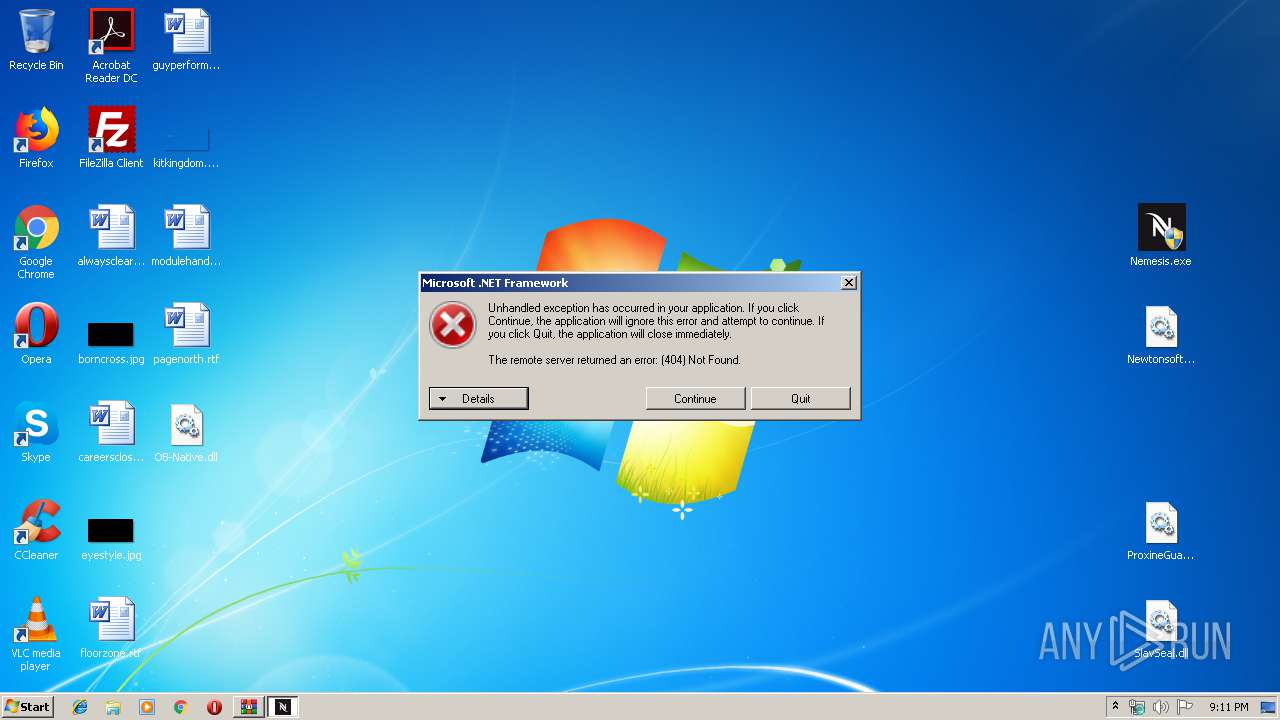
1148 | Nemesis.exe | GET | 404 | 148.251.158.38:80 | http://pizzaxyz.bplaced.net/Version.html | DE | html | 6.85 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1148 | Nemesis.exe | 148.251.158.38:80 | pizzaxyz.bplaced.net | Hetzner Online GmbH | DE | suspicious |
1148 | Nemesis.exe | 104.28.31.132:443 | panel.slav.vodka | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pizzaxyz.bplaced.net |
| suspicious |
panel.slav.vodka |
| suspicious |
dns.msftncsi.com |
| shared |