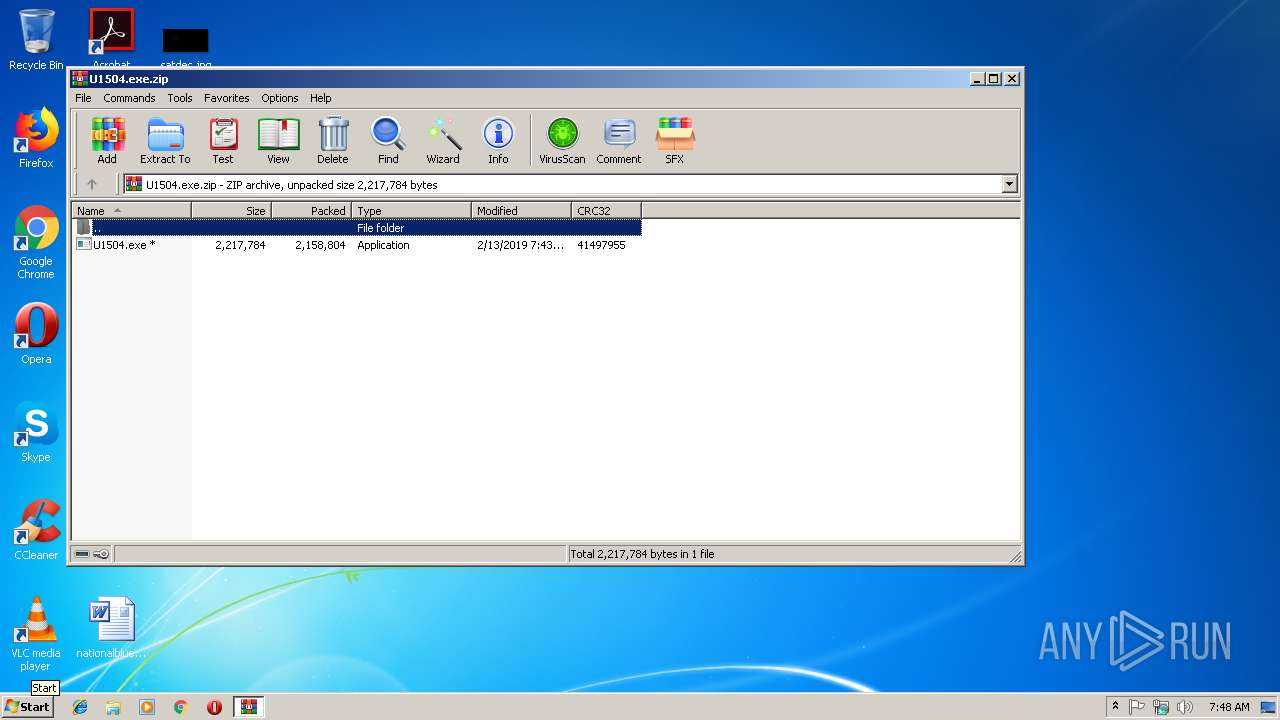
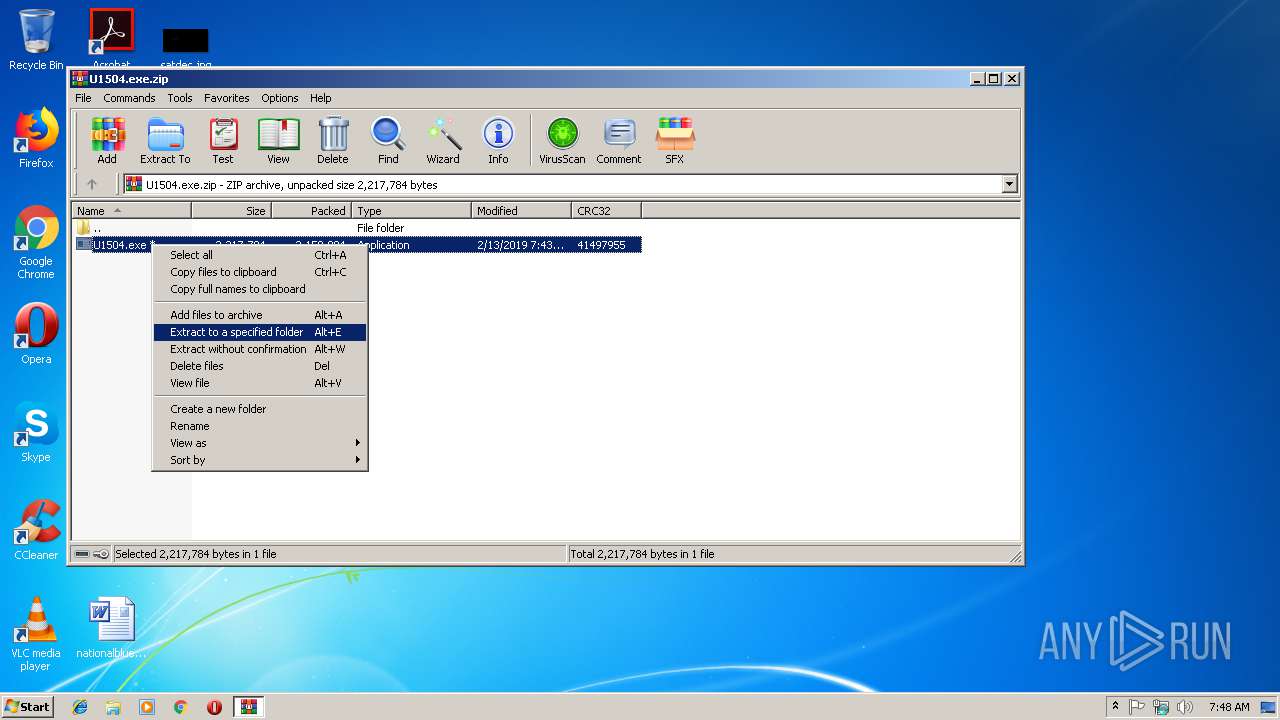
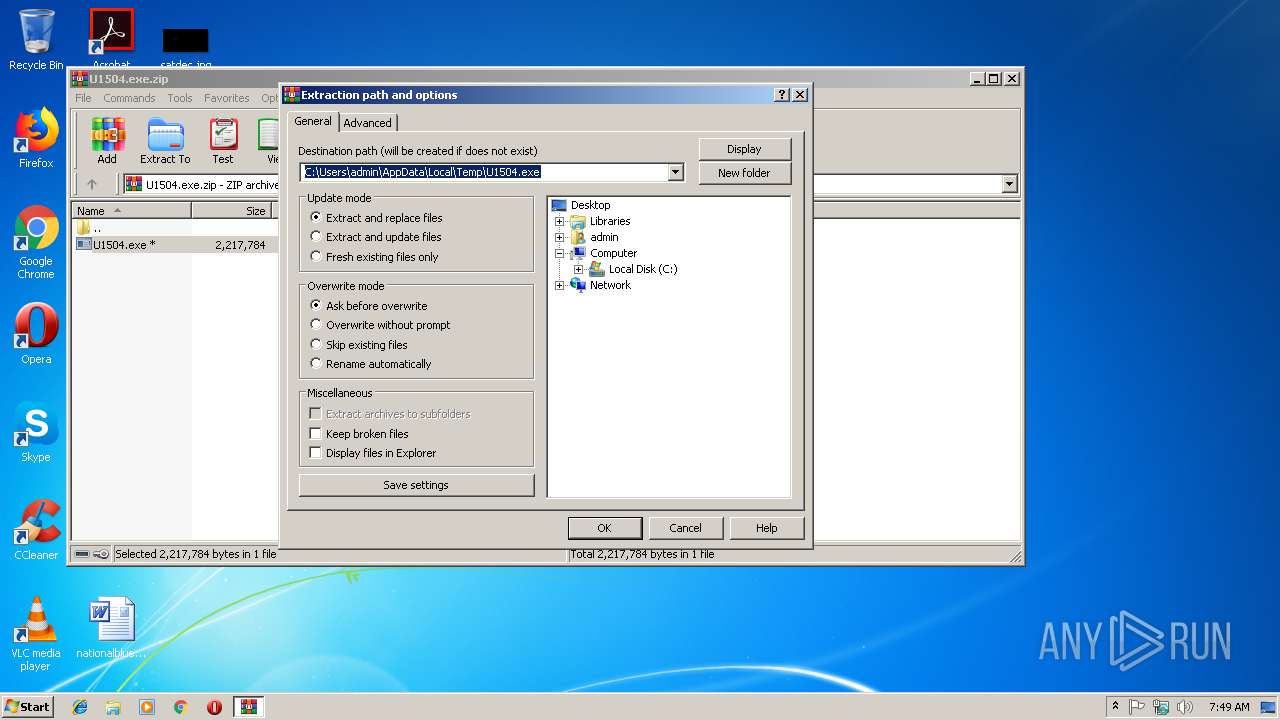
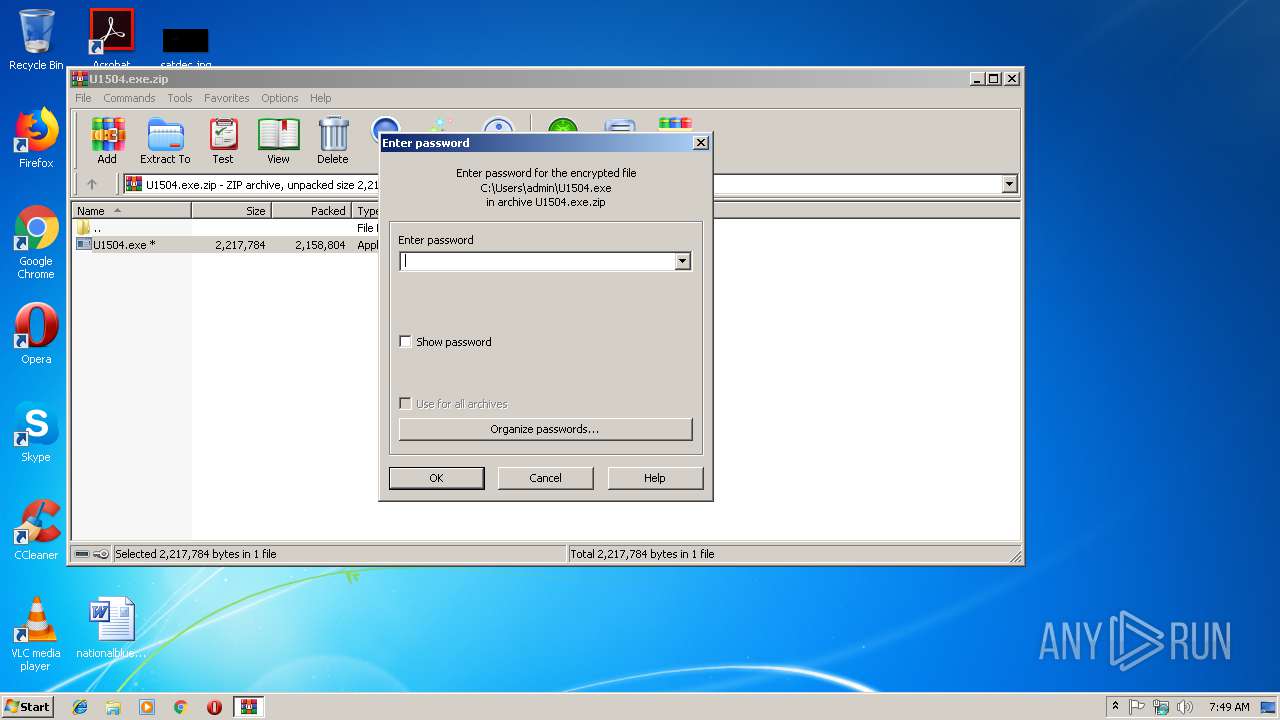
| File name: | U1504.exe.zip |
| Full analysis: | https://app.any.run/tasks/ffe4d0b9-954d-4ecc-a24b-7b6a0375f032 |
| Verdict: | Malicious activity |
| Analysis date: | February 13, 2019, 07:48:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 397A1426E4ECCCB0044339FCE2336954 |
| SHA1: | E9D2E4CDE467549CADA728A7C06744D3ADABE545 |
| SHA256: | 308BFE9973C76DFBEA7D4C5AE68C031050898D59665A73C9F2644F204AB4E59D |
| SSDEEP: | 49152:yoAo8jdUh/4x/IWLeK9twU2O9buQXKWu9a7mtc:oJjdUyIWL397Wpc |
MALICIOUS
Application was dropped or rewritten from another process
- U1504.exe (PID: 2408)
Changes internet zones settings
- U1504.exe (PID: 2408)
Changes settings of System certificates
- U1504.exe (PID: 2408)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3028)
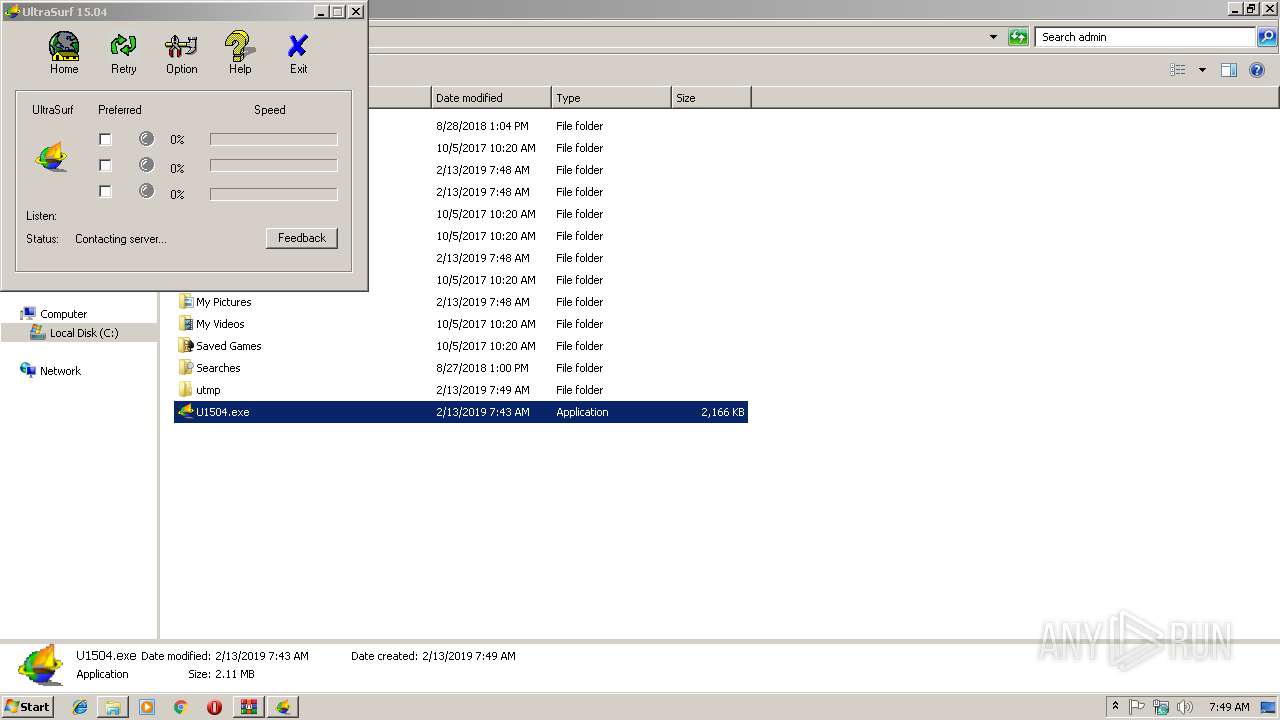
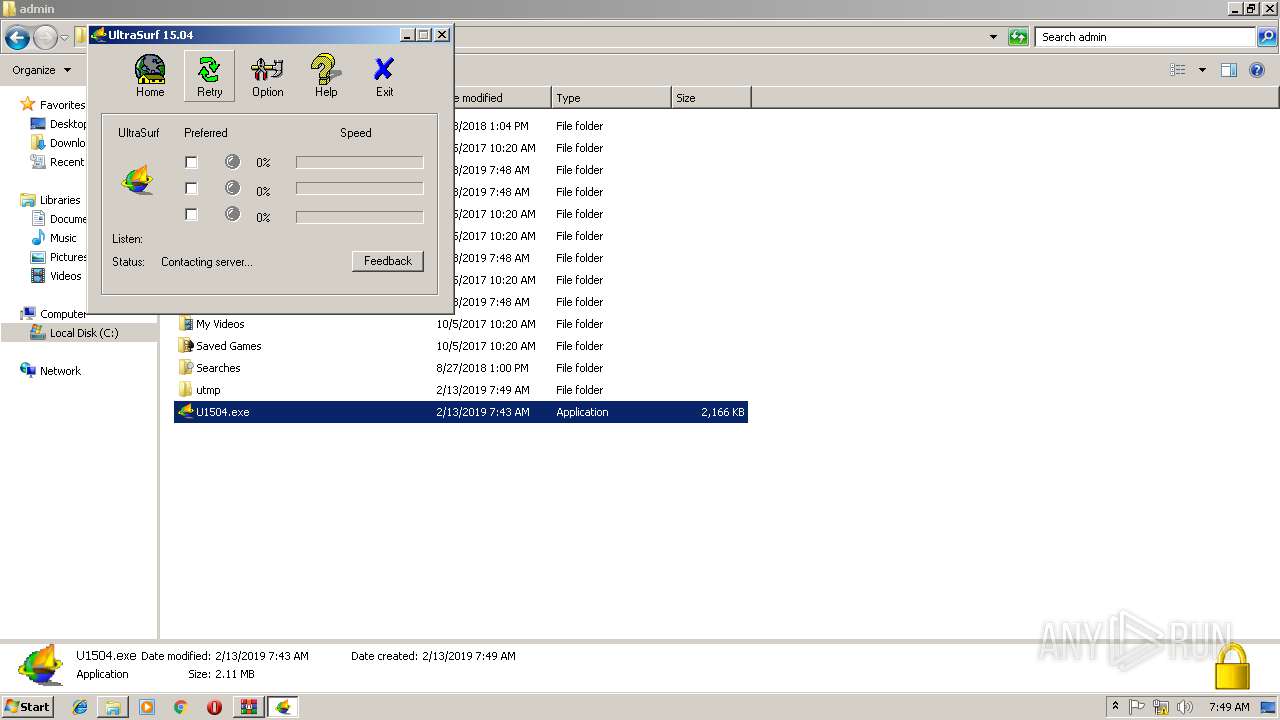
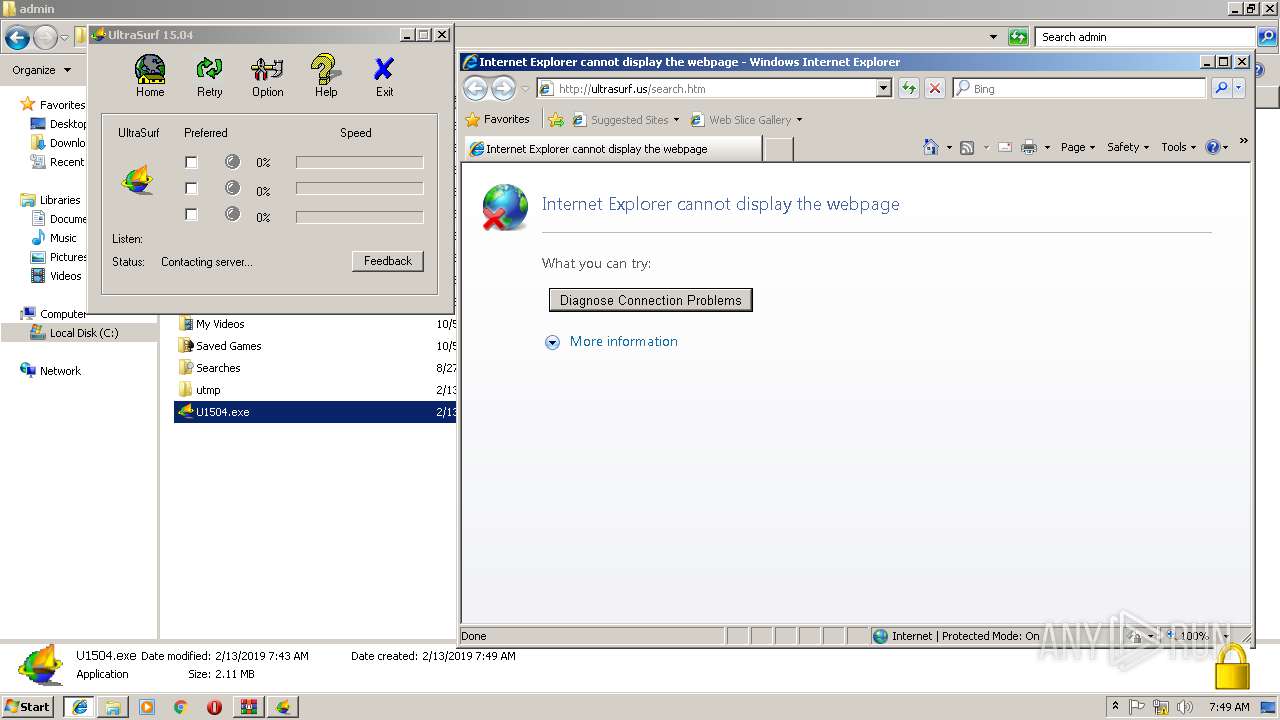
Uses RUNDLL32.EXE to load library
- U1504.exe (PID: 2408)
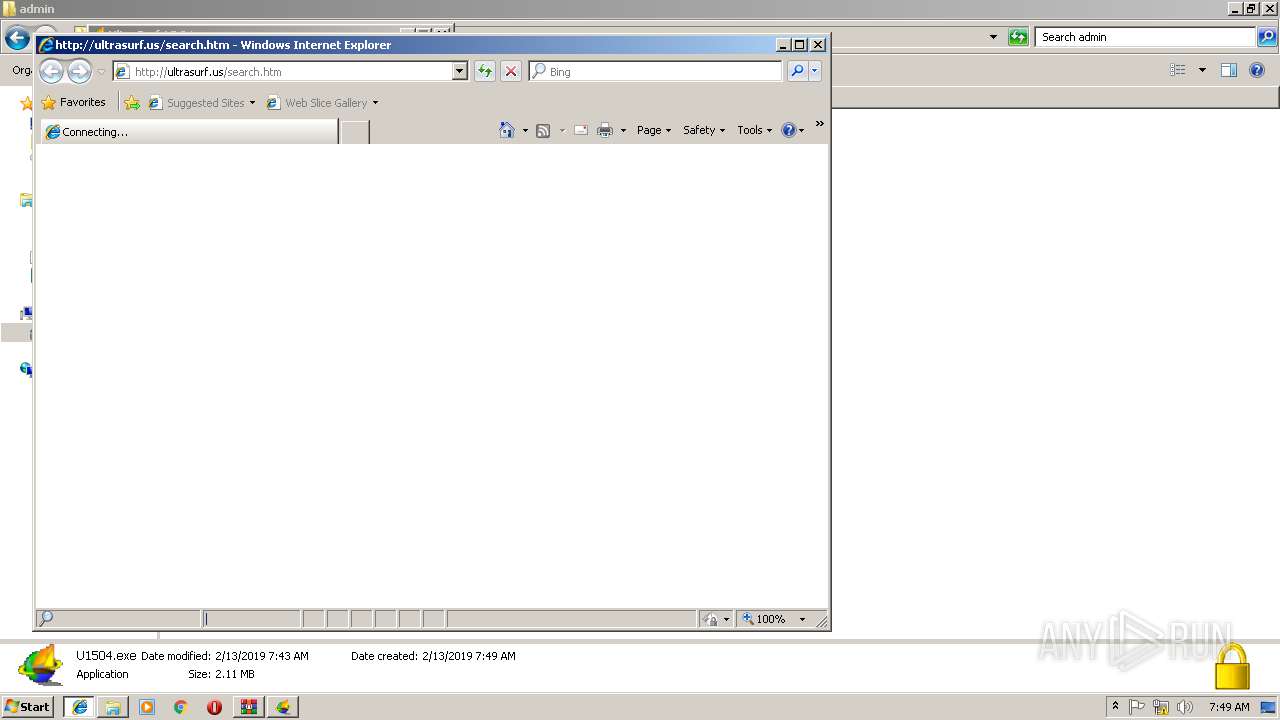
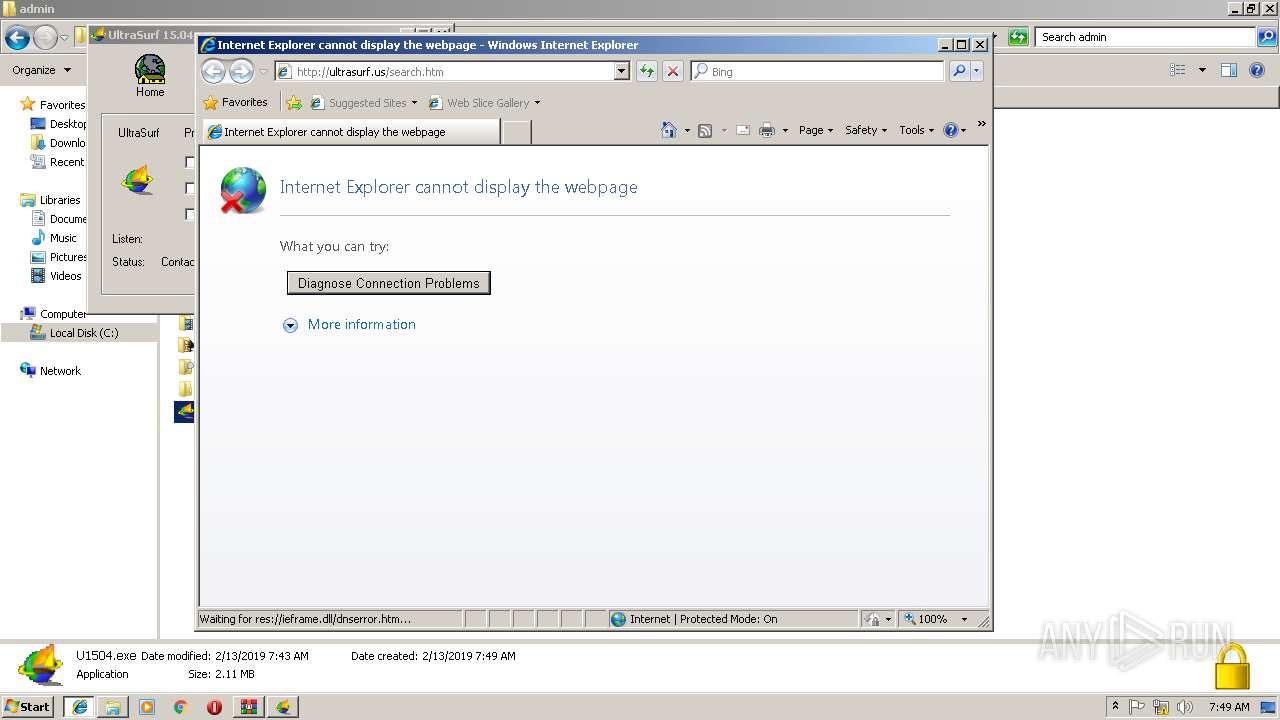
Starts Internet Explorer
- U1504.exe (PID: 2408)
Connects to unusual port
- U1504.exe (PID: 2408)
Reads Internet Cache Settings
- rundll32.exe (PID: 3676)
- rundll32.exe (PID: 3564)
Adds / modifies Windows certificates
- U1504.exe (PID: 2408)
INFO
Application launched itself
- iexplore.exe (PID: 3240)
Creates files in the user directory
- iexplore.exe (PID: 3788)
- iexplore.exe (PID: 3240)
Reads internet explorer settings
- iexplore.exe (PID: 3788)
Reads Internet Cache Settings
- iexplore.exe (PID: 3788)
Changes internet zones settings
- iexplore.exe (PID: 3240)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:02:13 07:43:29 |
| ZipCRC: | 0x41497955 |
| ZipCompressedSize: | 2158804 |
| ZipUncompressedSize: | 2217784 |
| ZipFileName: | U1504.exe |
Total processes
38
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2268 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 3221225547 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2408 | "C:\Users\admin\U1504.exe" | C:\Users\admin\U1504.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3028 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\U1504.exe.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3240 | "C:\Program Files\Internet Explorer\iexplore.exe" http://ultrasurf.us/search.htm | C:\Program Files\Internet Explorer\iexplore.exe | U1504.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3564 | "C:\Windows\system32\rundll32.exe" "C:\Windows\system32\WININET.dll",DispatchAPICall 1 | C:\Windows\system32\rundll32.exe | — | U1504.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3676 | "C:\Windows\system32\rundll32.exe" "C:\Windows\system32\WININET.dll",DispatchAPICall 1 | C:\Windows\system32\rundll32.exe | — | U1504.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3788 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3240 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
909
Read events
797
Write events
111
Delete events
1
Modification events
| (PID) Process: | (3028) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3028) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3028) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3028) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\U1504.exe.zip | |||
| (PID) Process: | (3028) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3028) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3028) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3028) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3028) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin | |||
| (PID) Process: | (3028) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
1
Suspicious files
3
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2408 | U1504.exe | C:\Users\admin\utmp\~ofgnqjwbc3l1y0q | binary | |
MD5:— | SHA256:— | |||
| 2408 | U1504.exe | C:\Users\admin\utmp\~pnckjujip0c6s2a | binary | |
MD5:— | SHA256:— | |||
| 2408 | U1504.exe | C:\Users\admin\utmp\~duwmfetmp7o7q1i | binary | |
MD5:— | SHA256:— | |||
| 3788 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\U2ZG9DE0\noConnect[1] | image | |
MD5:3CB8FACCD5DE434D415AB75C17E8FD86 | SHA256:6976C426E3AC66D66303C114B22B2B41109A7DE648BA55FFC3E5A53BD0DB09E7 | |||
| 3788 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\BWPPCY0O\httpErrorPagesScripts[1] | text | |
MD5:E7CA76A3C9EE0564471671D500E3F0F3 | SHA256:58268CA71A28973B756A48BBD7C9DC2F6B87B62AE343E582CE067C725275B63C | |||
| 3788 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\PP6KS563\errorPageStrings[1] | text | |
MD5:1A0563F7FB85A678771450B131ED66FD | SHA256:EB5678DE9D8F29CA6893D4E6CA79BD5AB4F312813820FE4997B009A2B1A1654C | |||
| 3788 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\dnserror[1] | html | |
MD5:68E03ED57EC741A4AFBBCD11FAB1BDBE | SHA256:1FF3334C3EB27033F8F37029FD72F648EDD4551FCE85FC1F5159FEAEA1439630 | |||
| 3788 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\ErrorPageTemplate[1] | text | |
MD5:F4FE1CB77E758E1BA56B8A8EC20417C5 | SHA256:8D018639281B33DA8EB3CE0B21D11E1D414E59024C3689F92BE8904EB5779B5F | |||
| 3788 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\BWPPCY0O\favcenter[1] | image | |
MD5:25D76EE5FB5B890F2CC022D94A42FE19 | SHA256:07D07A467E4988D3C377ACD6DC9E53ABCA6B64E8FBF70F6BE19D795A1619289B | |||
| 3788 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\PP6KS563\down[1] | image | |
MD5:555E83CE7F5D280D7454AF334571FB25 | SHA256:70F316A5492848BB8242D49539468830B353DDAA850964DB4E60A6D2D7DB4880 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
3
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2408 | U1504.exe | 64.182.160.129:31504 | — | CoreSpace, Inc. | US | unknown |
2408 | U1504.exe | 66.221.67.38:443 | — | CoreSpace, Inc. | US | unknown |
2408 | U1504.exe | 69.13.132.78:443 | — | CoreSpace, Inc. | US | unknown |
2408 | U1504.exe | 172.217.22.68:443 | www.google.com | Google Inc. | US | whitelisted |
2408 | U1504.exe | 172.217.22.5:443 | mail.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
d19ya6dk74n9uf.cloudfront.net |
| whitelisted |
www.google.com |
| malicious |
mail.google.com |
| shared |
Threats
Process | Message |
|---|---|
U1504.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|