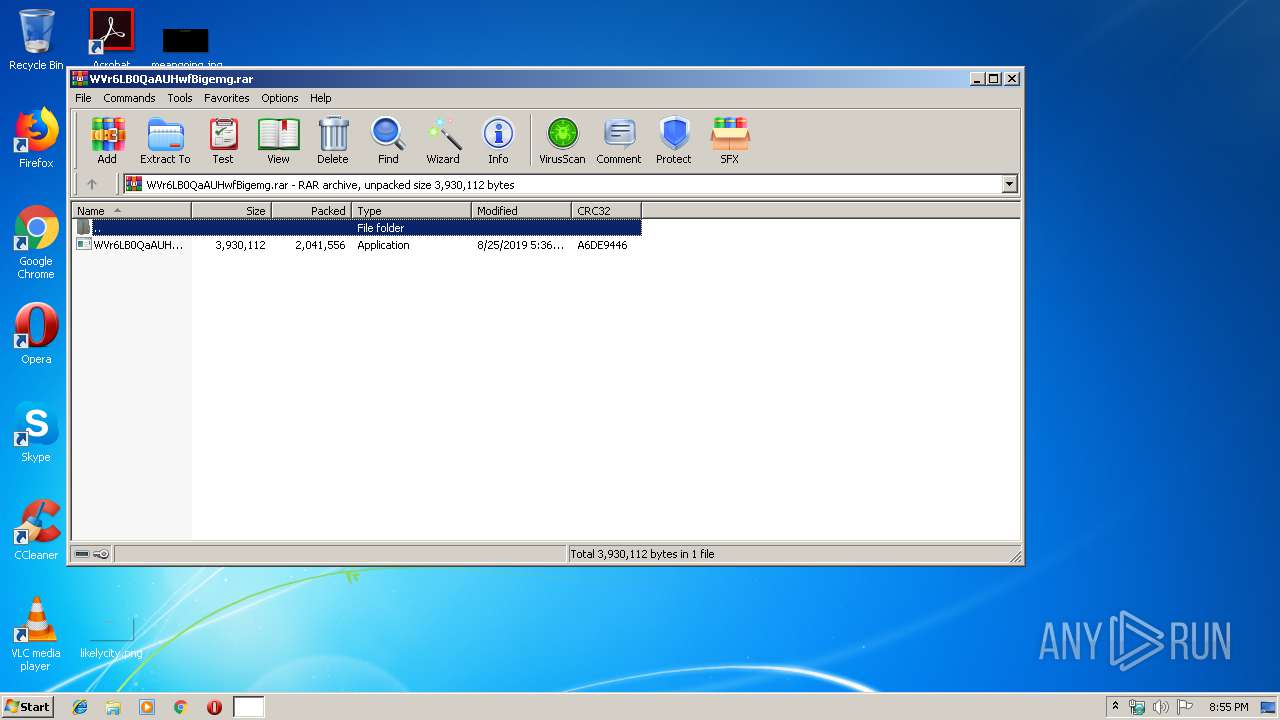
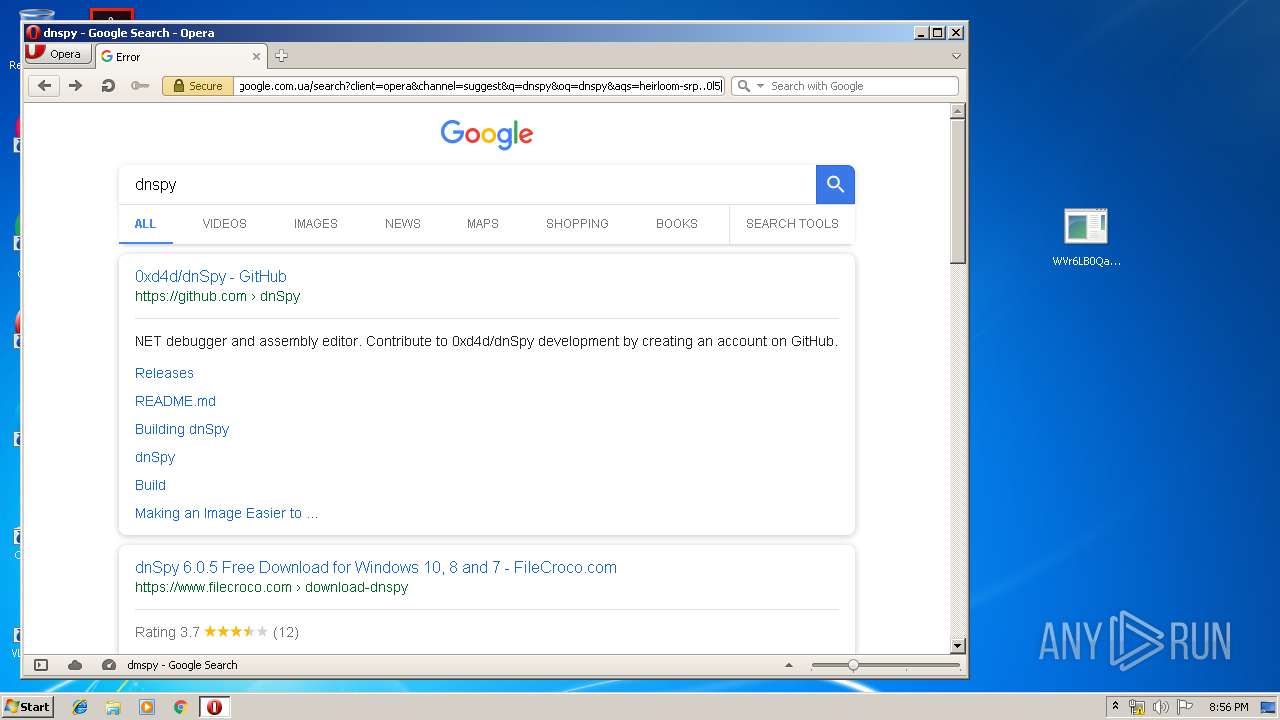
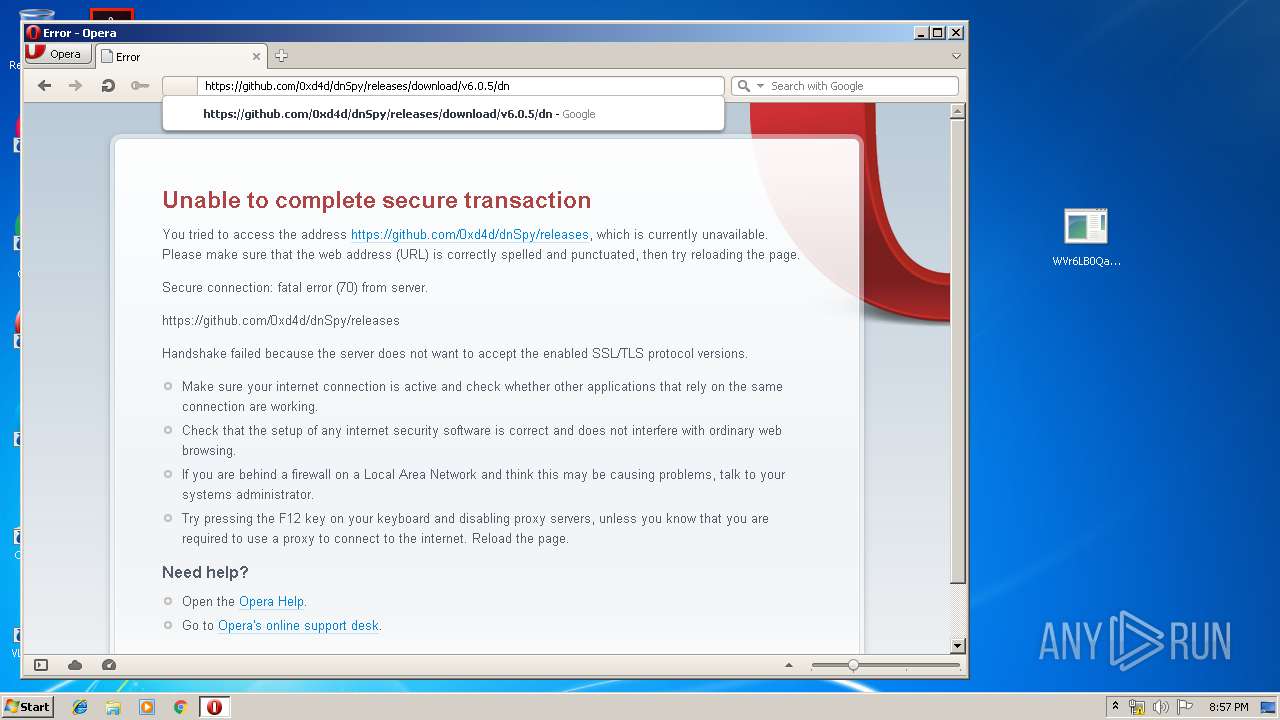
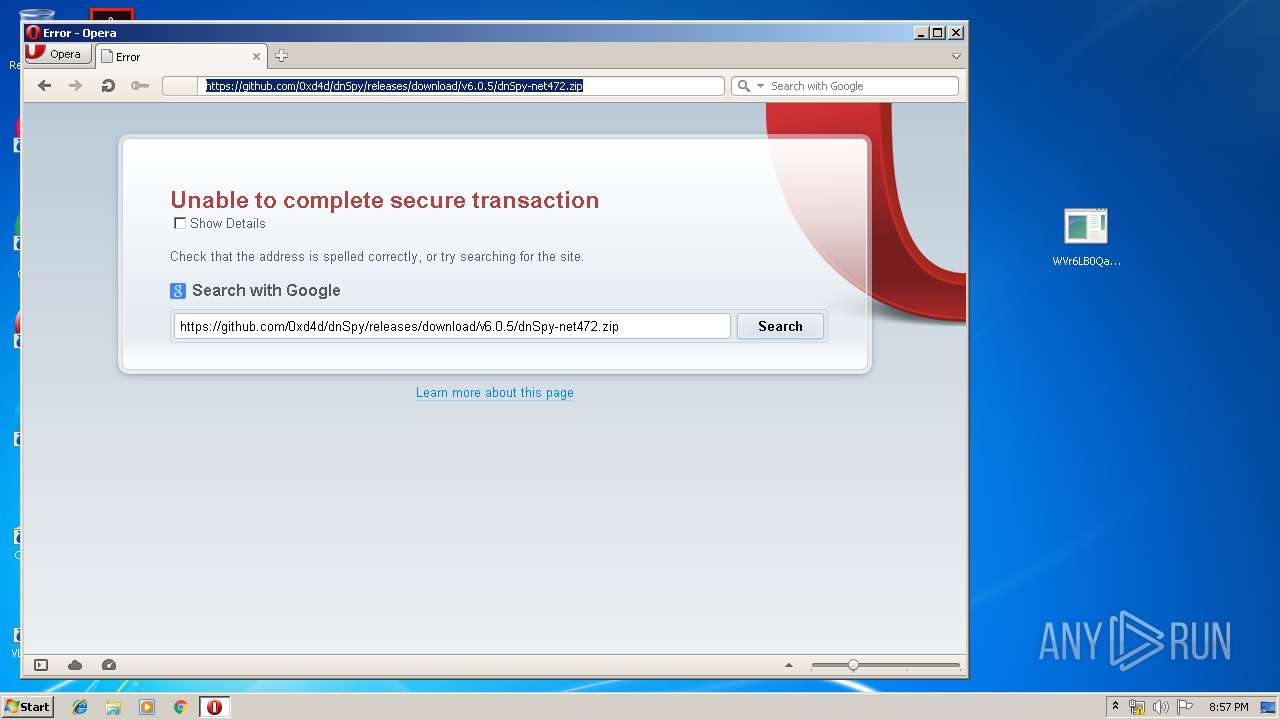
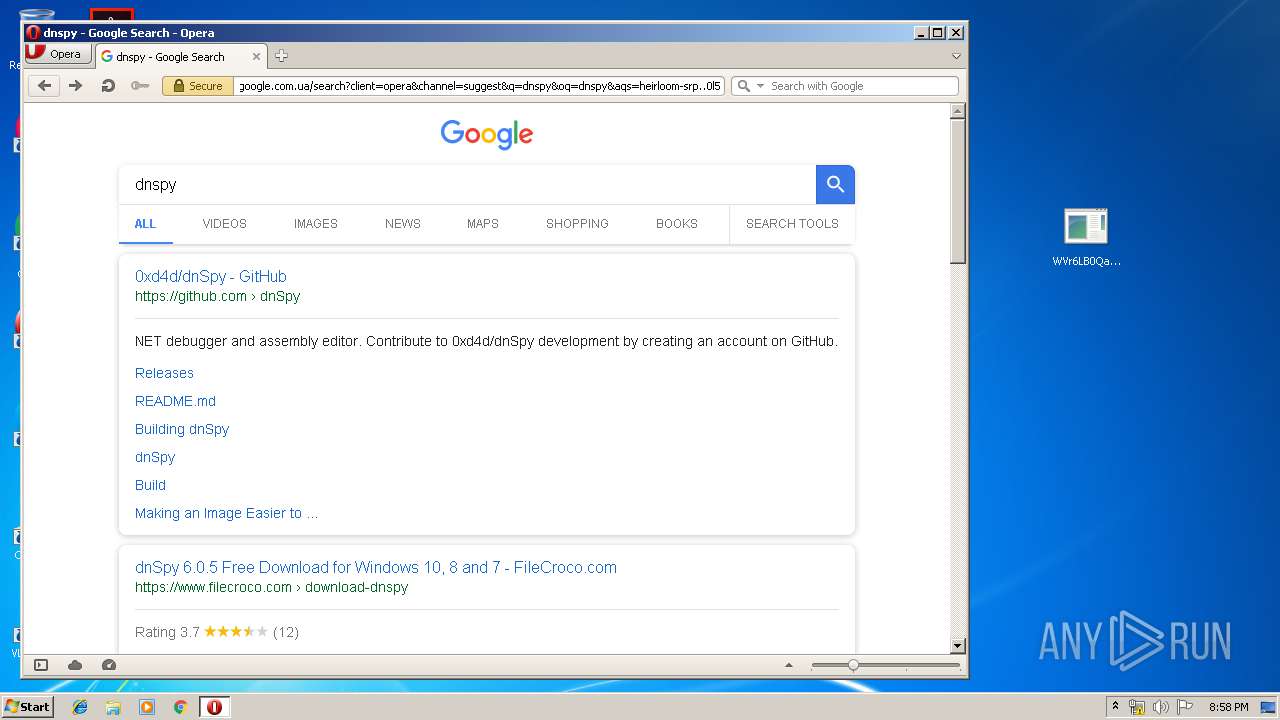
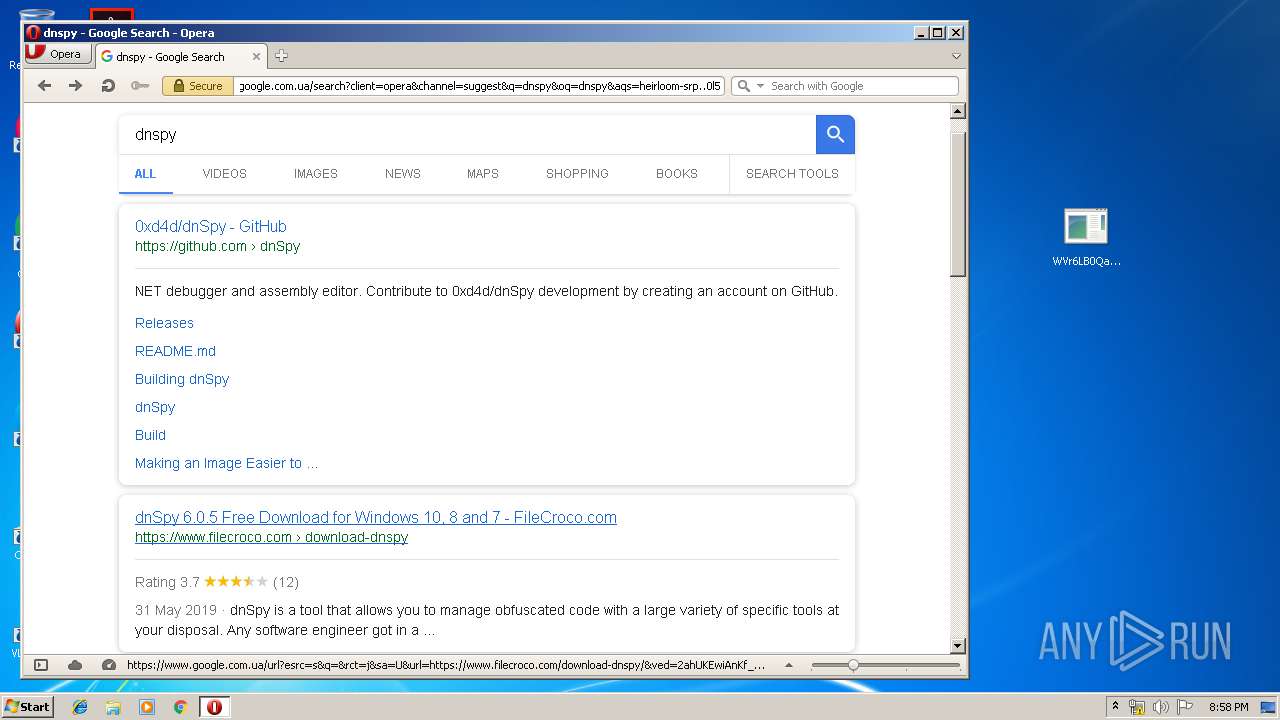
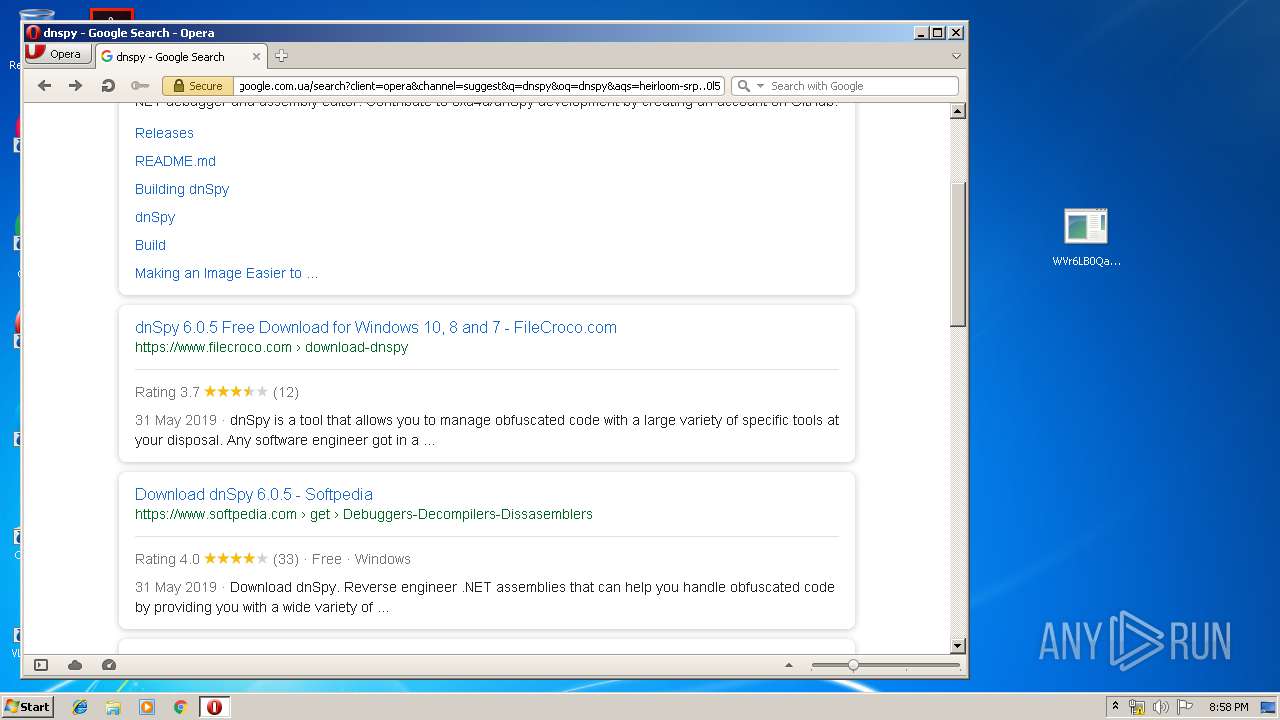
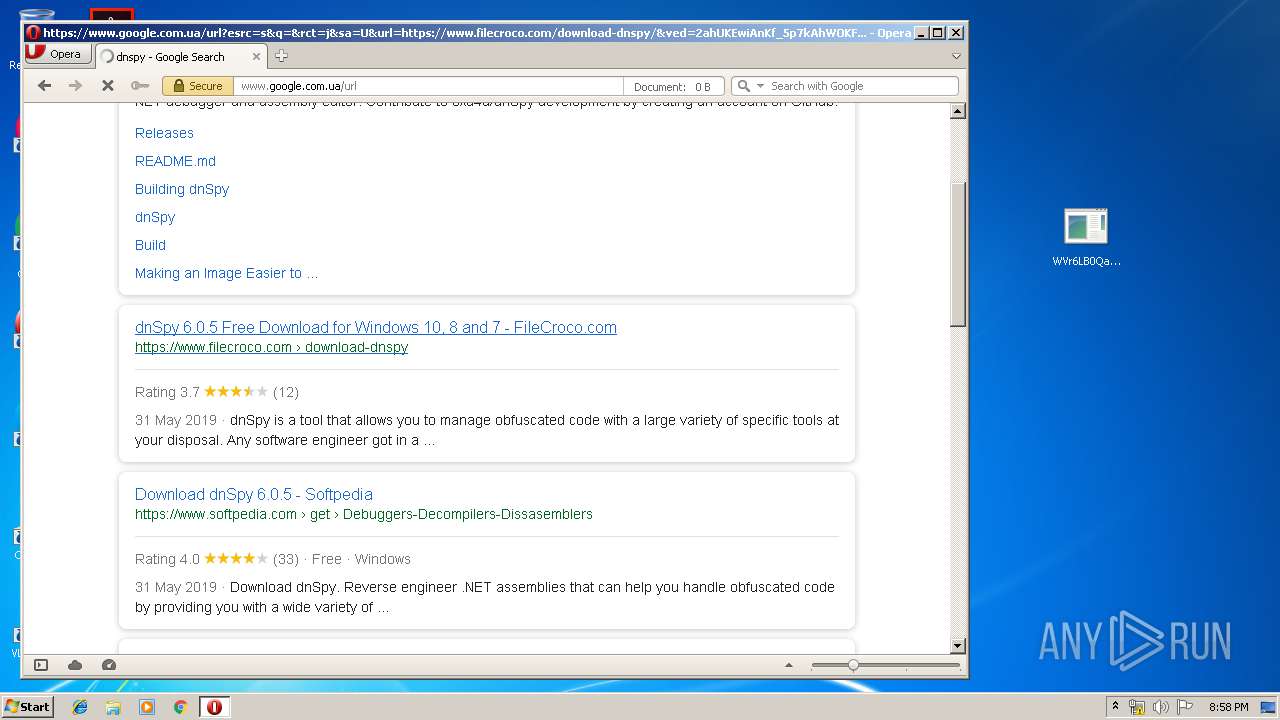
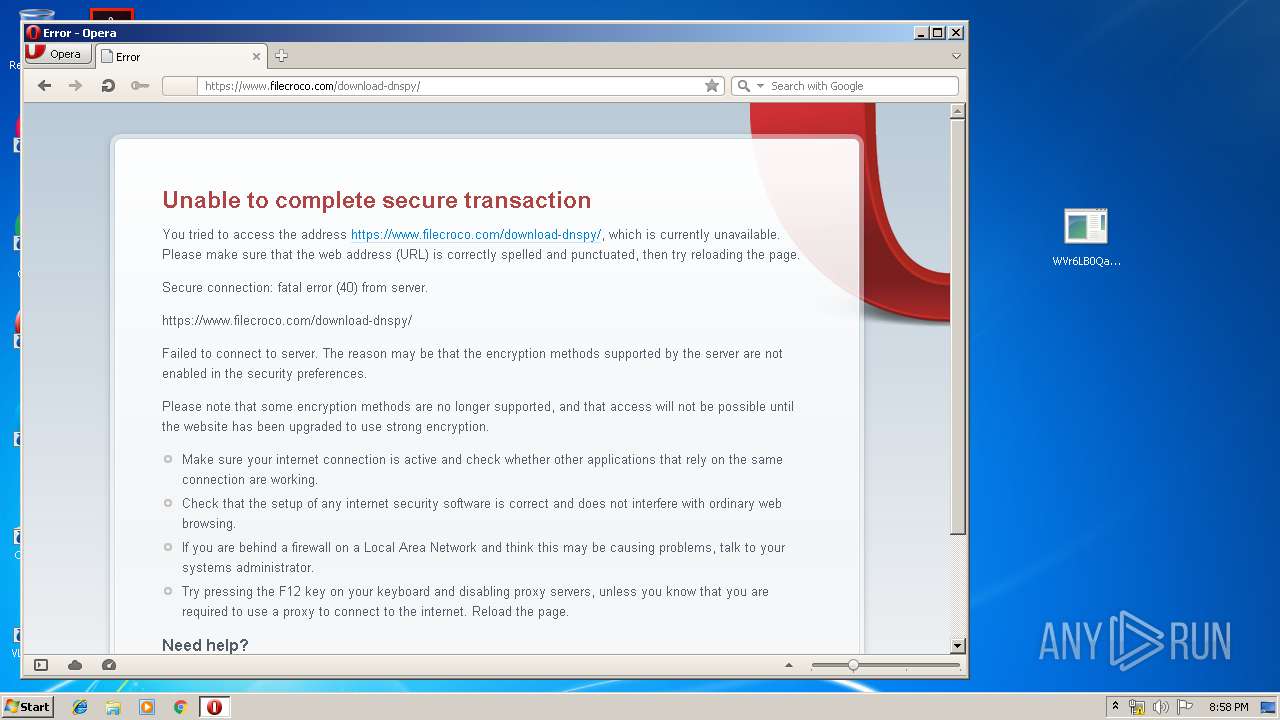
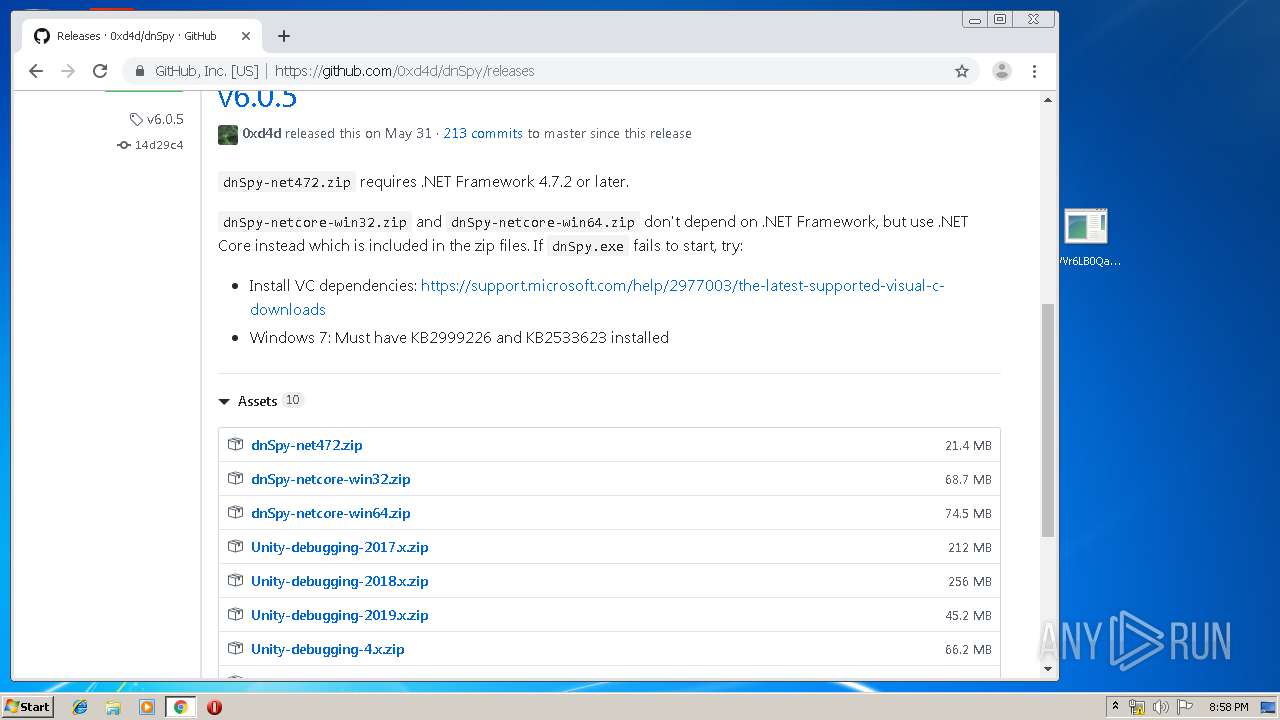
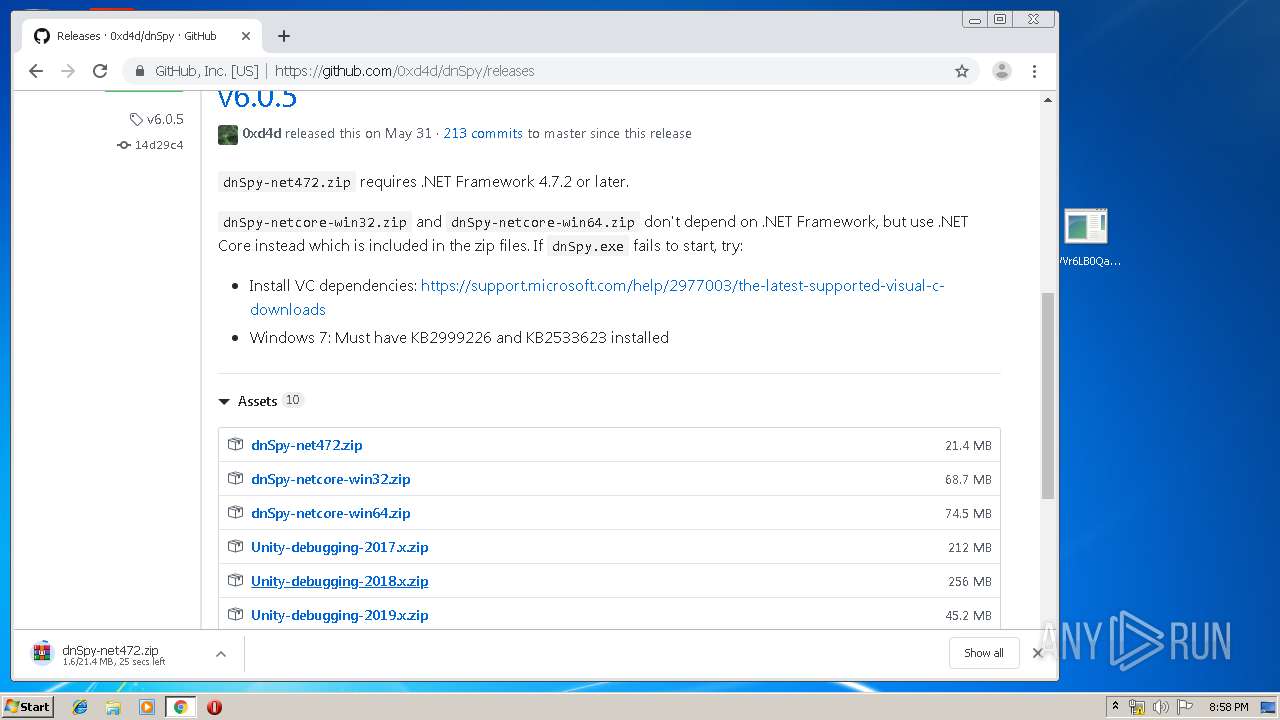
| File name: | WVr6LB0QaAUHwfBigemg.rar |
| Full analysis: | https://app.any.run/tasks/240bb030-4ad3-4a7a-a604-34308d5b42e2 |
| Verdict: | Malicious activity |
| Analysis date: | August 25, 2019, 19:54:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 4F31449BC51E655675009195BDD5696B |
| SHA1: | 96CE50B1147994C17AF6CF2AAB5A3E088A8EBE28 |
| SHA256: | 307CCEB9F2FCFFAED9C1085C4CE7F5F3C870B287F4A652358FDE5DF3B15EE481 |
| SSDEEP: | 49152:y8YVSD4rnDOH7sZhukWI4U+R7TCoi6YSn6CE1XCSxC:BswH7KHW0+lCx6xn6CEBCh |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2072)
- dnSpy.exe (PID: 2724)
Application was dropped or rewritten from another process
- dnSpy.exe (PID: 2724)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3724)
- WinRAR.exe (PID: 3196)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2412)
Creates files in the program directory
- dnSpy.exe (PID: 2724)
INFO
Manual execution by user
- opera.exe (PID: 3820)
- chrome.exe (PID: 2412)
- WinRAR.exe (PID: 3604)
- WinRAR.exe (PID: 3196)
- dnSpy.exe (PID: 2724)
Reads Internet Cache Settings
- chrome.exe (PID: 2412)
Creates files in the user directory
- opera.exe (PID: 3820)
Application launched itself
- chrome.exe (PID: 2412)
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 3196)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
71
Monitored processes
33
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 564 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1016,6187303025903886722,10844240645833322152,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=8955830751524010001 --mojo-platform-channel-handle=1048 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 772 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,6187303025903886722,10844240645833322152,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5283553144711821845 --renderer-client-id=24 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2808 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 880 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2428 --on-initialized-event-handle=312 --parent-handle=316 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1456 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1016,6187303025903886722,10844240645833322152,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=16423622311953085091 --mojo-platform-channel-handle=3252 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1720 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1016,6187303025903886722,10844240645833322152,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=6450200419849002176 --mojo-platform-channel-handle=2696 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2072 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe3_ Global\UsGthrCtrlFltPipeMssGthrPipe3 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2260 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1016,6187303025903886722,10844240645833322152,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=14586607052180157252 --mojo-platform-channel-handle=2636 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2348 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1016,6187303025903886722,10844240645833322152,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=1786949313062723452 --mojo-platform-channel-handle=2728 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2412 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2448 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1016,6187303025903886722,10844240645833322152,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=13737599289957353690 --mojo-platform-channel-handle=3136 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
2 072
Read events
1 821
Write events
246
Delete events
5
Modification events
| (PID) Process: | (3724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3724) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\WVr6LB0QaAUHwfBigemg.rar | |||
| (PID) Process: | (3724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
333
Suspicious files
207
Text files
496
Unknown types
38
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3820 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\oprD2F4.tmp | — | |
MD5:— | SHA256:— | |||
| 3820 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\oprD382.tmp | — | |
MD5:— | SHA256:— | |||
| 3820 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr00001.tmp | — | |
MD5:— | SHA256:— | |||
| 3820 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\H6WHNY7KU9NYY4B9QBIJ.temp | — | |
MD5:— | SHA256:— | |||
| 3820 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\oprE46B.tmp | — | |
MD5:— | SHA256:— | |||
| 3820 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\oprF66E.tmp | — | |
MD5:— | SHA256:— | |||
| 3820 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\16ec093b8f51508f.customDestinations-ms~RF16df29.TMP | binary | |
MD5:— | SHA256:— | |||
| 3820 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opssl6.dat | binary | |
MD5:— | SHA256:— | |||
| 3820 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\tasks.xml | xml | |
MD5:— | SHA256:— | |||
| 3820 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\16ec093b8f51508f.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
46
TCP/UDP connections
266
DNS requests
92
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3820 | opera.exe | GET | — | 93.184.220.29:80 | http://crl4.digicert.com/DigiCertGlobalRootG2.crl | US | — | — | whitelisted |
3820 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl4.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 528 b | whitelisted |
3820 | opera.exe | GET | 200 | 93.184.220.29:80 | http://s.symcb.com/pca3-g5.crl | US | der | 712 b | whitelisted |
3820 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl4.digicert.com/DigiCertGlobalRootG2.crl | US | der | 517 b | whitelisted |
3820 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/sha2-ha-server-g6.crl | US | binary | 322 Kb | whitelisted |
3820 | opera.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEASnjI9aXa5Un%2BQBbbRyiuM%3D | US | der | 471 b | whitelisted |
3820 | opera.exe | GET | 200 | 13.35.254.155:80 | http://crl.rootca1.amazontrust.com/rootca1.crl | US | der | 439 b | whitelisted |
3820 | opera.exe | GET | 200 | 172.217.22.3:80 | http://ocsp.pki.goog/GTSGIAG3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT27bBjYjKBmjX2jXWgnQJKEapsrQQUd8K4UJpndnaxLcKG0IOgfqZ%2BuksCEDTAT%2FSTMSEdGvz7Z5nVeLc%3D | US | der | 471 b | whitelisted |
3820 | opera.exe | GET | 302 | 185.26.182.110:80 | http://redir.opera.com/speeddials/amazon/ | unknown | html | 293 b | whitelisted |
3820 | opera.exe | GET | 302 | 185.26.182.110:80 | http://redir.opera.com/speeddials/amazon/ | unknown | html | 293 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3820 | opera.exe | 52.58.73.114:443 | x.bidswitch.net | Amazon.com, Inc. | DE | unknown |
3820 | opera.exe | 216.58.207.66:443 | cm.g.doubleclick.net | Google Inc. | US | whitelisted |
3820 | opera.exe | 34.95.120.147:443 | us-u.openx.net | — | US | unknown |
3820 | opera.exe | 185.26.182.94:443 | certs.opera.com | Opera Software AS | — | whitelisted |
3820 | opera.exe | 93.184.220.29:80 | crl4.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3820 | opera.exe | 185.26.182.93:80 | certs.opera.com | Opera Software AS | — | whitelisted |
3820 | opera.exe | 185.26.182.110:80 | redir.opera.com | Opera Software AS | — | unknown |
3820 | opera.exe | 99.86.1.130:80 | www.amazon.co.uk | AT&T Services, Inc. | US | unknown |
3820 | opera.exe | 99.86.1.130:443 | www.amazon.co.uk | AT&T Services, Inc. | US | unknown |
3820 | opera.exe | 13.35.250.160:443 | images-eu.ssl-images-amazon.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
certs.opera.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |
redir.opera.com |
| whitelisted |
sitecheck2.opera.com |
| whitelisted |
www.amazon.co.uk |
| whitelisted |
s.symcb.com |
| whitelisted |
images-eu.ssl-images-amazon.com |
| whitelisted |
m.media-amazon.com |
| whitelisted |
fls-eu.amazon.co.uk |
| whitelisted |
images-na.ssl-images-amazon.com |
| shared |