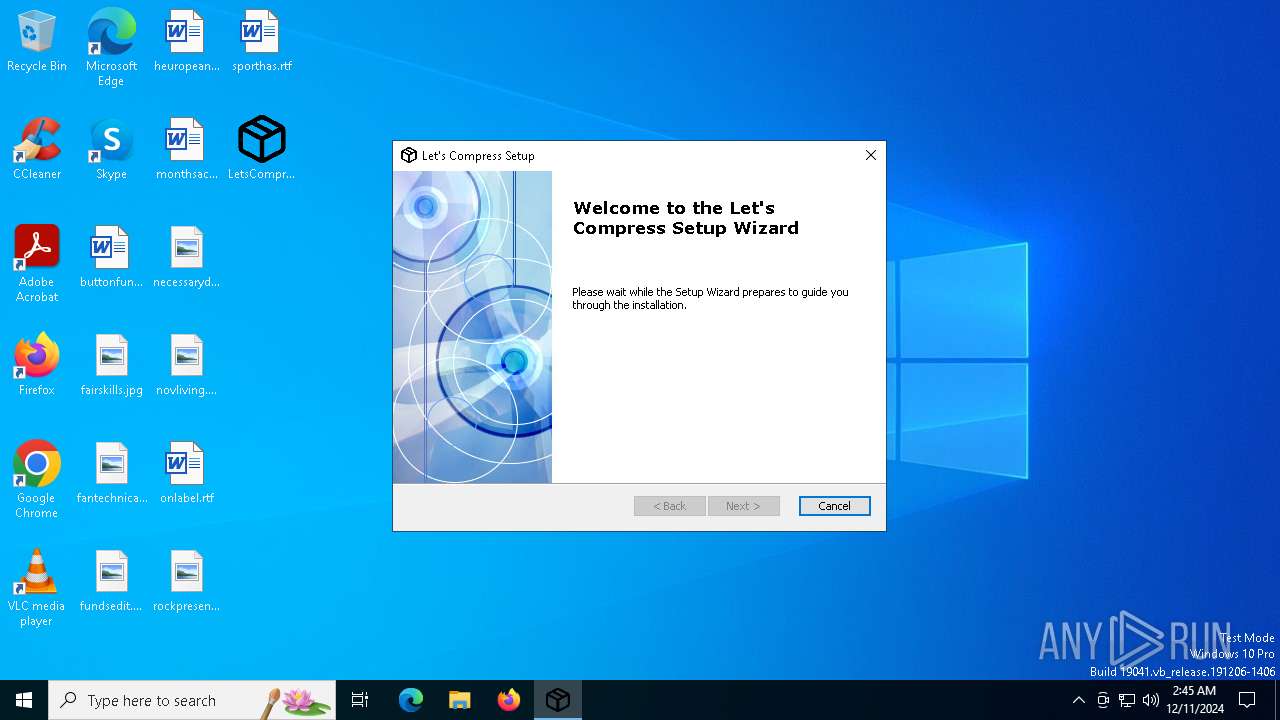
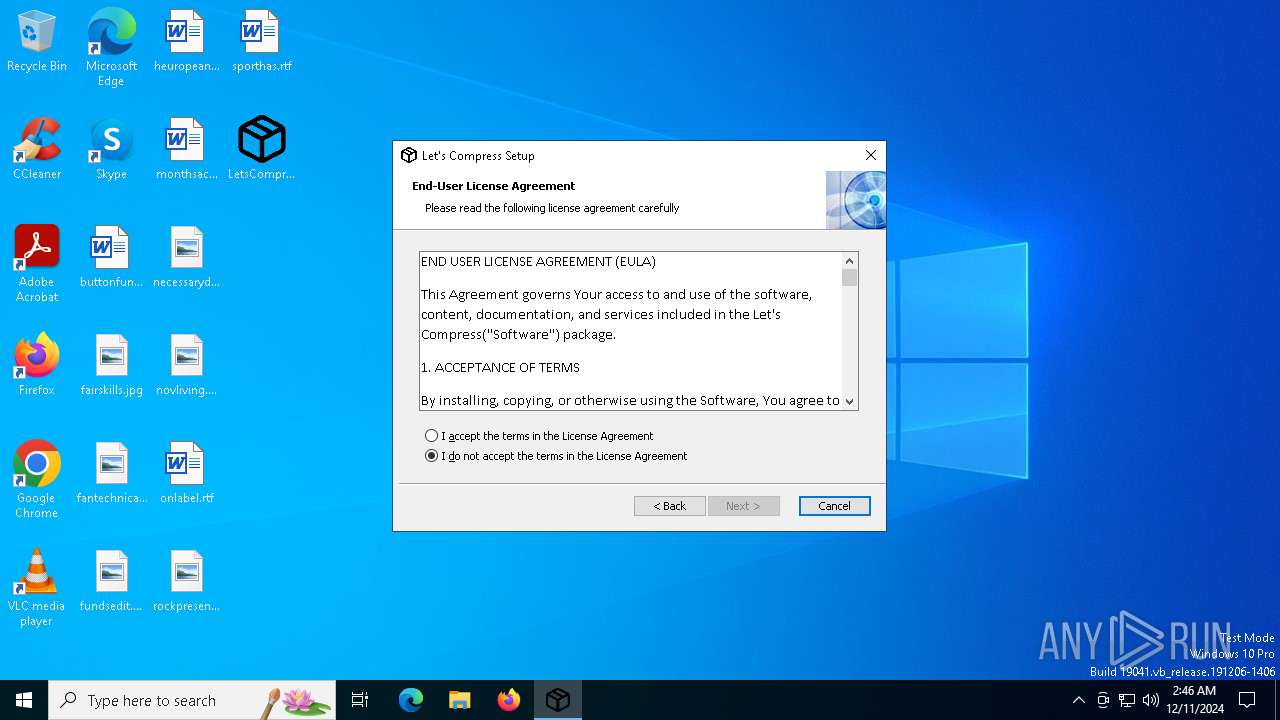
| File name: | LetsCompress.exe |
| Full analysis: | https://app.any.run/tasks/05a66dd3-abaf-4e27-a05d-7947236d7b34 |
| Verdict: | Malicious activity |
| Analysis date: | December 11, 2024, 02:45:35 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 58D6E317453F342F2385F5CDCEE5747B |
| SHA1: | 31367BD1073D5D2E609313D99B883D0F1591AC3D |
| SHA256: | 307AF128D05CF469817201A031D935DB0E9890E9CB56257D8B2ADBA51E2FF4F6 |
| SSDEEP: | 98304:IL0druM/vIX0pafjCHE6B5fMxNRlOqAhcNAjcXILafIKIkw3Gv2C+04k3N4slrg+:d78B7CGz19oA3VnYp9wU6yHa78K+A |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 3640)
- powershell.exe (PID: 5720)
Changes powershell execution policy (Bypass)
- msiexec.exe (PID: 236)
SUSPICIOUS
Reads security settings of Internet Explorer
- LetsCompress.exe (PID: 3584)
Checks Windows Trust Settings
- LetsCompress.exe (PID: 3584)
Reads the Windows owner or organization settings
- LetsCompress.exe (PID: 3584)
Process drops legitimate windows executable
- LetsCompress.exe (PID: 3584)
Executable content was dropped or overwritten
- LetsCompress.exe (PID: 3584)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 236)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 236)
The process hide an interactive prompt from the user
- msiexec.exe (PID: 236)
The process executes Powershell scripts
- msiexec.exe (PID: 236)
Reverses array data (POWERSHELL)
- powershell.exe (PID: 3640)
- powershell.exe (PID: 5720)
INFO
Reads the computer name
- LetsCompress.exe (PID: 3584)
- msiexec.exe (PID: 4548)
- msiexec.exe (PID: 236)
Reads Environment values
- LetsCompress.exe (PID: 3584)
- msiexec.exe (PID: 236)
Checks supported languages
- LetsCompress.exe (PID: 3584)
- msiexec.exe (PID: 4548)
- msiexec.exe (PID: 236)
The sample compiled with english language support
- LetsCompress.exe (PID: 3584)
Reads the machine GUID from the registry
- LetsCompress.exe (PID: 3584)
Creates files or folders in the user directory
- LetsCompress.exe (PID: 3584)
Checks proxy server information
- LetsCompress.exe (PID: 3584)
- powershell.exe (PID: 3640)
- powershell.exe (PID: 5720)
Reads the software policy settings
- LetsCompress.exe (PID: 3584)
- powershell.exe (PID: 3640)
- powershell.exe (PID: 5720)
Create files in a temporary directory
- msiexec.exe (PID: 236)
- LetsCompress.exe (PID: 3584)
- powershell.exe (PID: 3640)
- powershell.exe (PID: 5720)
The process uses the downloaded file
- powershell.exe (PID: 3640)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 3640)
- powershell.exe (PID: 5720)
Reads security settings of Internet Explorer
- powershell.exe (PID: 3640)
- powershell.exe (PID: 5720)
Disables trace logs
- powershell.exe (PID: 3640)
- powershell.exe (PID: 5720)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:08:08 12:49:22+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.36 |
| CodeSize: | 2534912 |
| InitializedDataSize: | 988160 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1e0862 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.4.0.0 |
| ProductVersionNumber: | 1.4.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Let's Compress |
| FileDescription: | Let's Compress Installer |
| FileVersion: | 1.4.0.0 |
| InternalName: | Let's Compress |
| LegalCopyright: | Copyright (C) 2024 Let's Compress |
| OriginalFileName: | Let's Compress.exe |
| ProductName: | Let's Compress |
| ProductVersion: | 1.4.0.0 |
Total processes
125
Monitored processes
7
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | C:\Windows\syswow64\MsiExec.exe -Embedding 3C28228D9EB9643BEB2B3037644E7B59 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3584 | "C:\Users\admin\Desktop\LetsCompress.exe" | C:\Users\admin\Desktop\LetsCompress.exe | explorer.exe | ||||||||||||
User: admin Company: Let's Compress Integrity Level: MEDIUM Description: Let's Compress Installer Version: 1.4.0.0 Modules
| |||||||||||||||
| 3640 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\pss7C3C.ps1" -propFile "C:\Users\admin\AppData\Local\Temp\msi7C38.txt" -scriptFile "C:\Users\admin\AppData\Local\Temp\scr7C39.ps1" -scriptArgsFile "C:\Users\admin\AppData\Local\Temp\scr7C3A.txt" -propSep " :<->: " -lineSep " <<:>> " -testPrefix "_testValue." | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4548 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4804 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5128 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5720 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\pss7509.ps1" -propFile "C:\Users\admin\AppData\Local\Temp\msi74F6.txt" -scriptFile "C:\Users\admin\AppData\Local\Temp\scr74F7.ps1" -scriptArgsFile "C:\Users\admin\AppData\Local\Temp\scr74F8.txt" -propSep " :<->: " -lineSep " <<:>> " -testPrefix "_testValue." | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 985
Read events
13 971
Write events
14
Delete events
0
Modification events
| (PID) Process: | (3640) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3640) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (3640) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3640) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3640) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (3640) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3640) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3640) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3640) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (3640) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
17
Suspicious files
4
Text files
26
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3584 | LetsCompress.exe | C:\Users\admin\AppData\Roaming\Let's Compress\Let's Compress 1.4.0.0\install\holder0.aiph | — | |
MD5:— | SHA256:— | |||
| 3584 | LetsCompress.exe | C:\Users\admin\AppData\Roaming\Let's Compress\Let's Compress 1.4.0.0\install\22AED8D\Let's Compress.msi | executable | |
MD5:77BEA04D70F6F5231500001585E187FF | SHA256:F7CDEB5E813B377D7D3086D5C4DA0646B9CD98E170886CBE831D38099CBE5B3E | |||
| 3584 | LetsCompress.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\357F04AD41BCF5FE18FCB69F60C6680F_D343022F8C5E519322B5D9E07C403E21 | der | |
MD5:89649037833A19AA4977DC27C607F615 | SHA256:BA7D59BFC8BD240974FF7577C4CABB0377D6DBFCF6DDD0537A3961AD57B06D43 | |||
| 3584 | LetsCompress.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\9CB4373A4252DE8D2212929836304EC5_1AB74AA2E3A56E1B8AD8D3FEC287554E | binary | |
MD5:B7C5ACE9D50587BF3748D5E0291F27FE | SHA256:1BD1B3222E75895C14EE2C728F434A6DF3330227D0002FC8E7D15A1ADB0D9313 | |||
| 3584 | LetsCompress.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9CB4373A4252DE8D2212929836304EC5_1AB74AA2E3A56E1B8AD8D3FEC287554E | der | |
MD5:7C6696A0F49A788B4EED1F9EEF9701E3 | SHA256:336BB257D562617CC8A05140013153FCF833F549302BCFB40139AE7A3D24FCF2 | |||
| 3584 | LetsCompress.exe | C:\Users\admin\AppData\Local\Temp\shi7988.tmp | executable | |
MD5:84A34BF3486F7B9B7035DB78D78BDD1E | SHA256:F85911C910B660E528D2CF291BAA40A92D09961996D6D84E7A53A7095C7CD96E | |||
| 3584 | LetsCompress.exe | C:\Users\admin\AppData\Local\Temp\MSI7AA5.tmp | executable | |
MD5:B7A6A99CBE6E762C0A61A8621AD41706 | SHA256:39FD8D36F8E5D915AD571EA429DB3C3DE6E9C160DBEA7C3E137C9BA4B7FD301D | |||
| 3584 | LetsCompress.exe | C:\Users\admin\AppData\Local\Temp\MSI7AF7.tmp | executable | |
MD5:B7A6A99CBE6E762C0A61A8621AD41706 | SHA256:39FD8D36F8E5D915AD571EA429DB3C3DE6E9C160DBEA7C3E137C9BA4B7FD301D | |||
| 3584 | LetsCompress.exe | C:\Users\admin\AppData\Local\Temp\MSI7AD6.tmp | executable | |
MD5:B7A6A99CBE6E762C0A61A8621AD41706 | SHA256:39FD8D36F8E5D915AD571EA429DB3C3DE6E9C160DBEA7C3E137C9BA4B7FD301D | |||
| 3584 | LetsCompress.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_3584\custicon | image | |
MD5:BE6D2F48AA6634FB2101C273C798D4D9 | SHA256:0E22BC2BF7184DFDB55223A11439304A453FB3574E3C9034A6497AF405C628EF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
22
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3700 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3700 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | — | 169.150.247.37:443 | https://e.letscompress.online/start | unknown | — | — | unknown |
— | — | GET | 200 | 169.150.247.38:443 | https://e.letscompress.online/letscompress_next_welcome | unknown | — | — | unknown |
3584 | LetsCompress.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/codesigningrootr45/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEHe9DgW3WQu2HUdhUx4%2Fde0%3D | unknown | — | — | whitelisted |
3584 | LetsCompress.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/gsgccr45evcodesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQaCbVYh07WONuW4e63Ydlu4AlbDAQUJZ3Q%2FFkJhmPF7POxEztXHAOSNhECDEa8nmSLUN2zOQqKig%3D%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3700 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 104.126.37.176:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3700 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3700 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
e.letscompress.online |
| unknown |
self.events.data.microsoft.com |
| whitelisted |