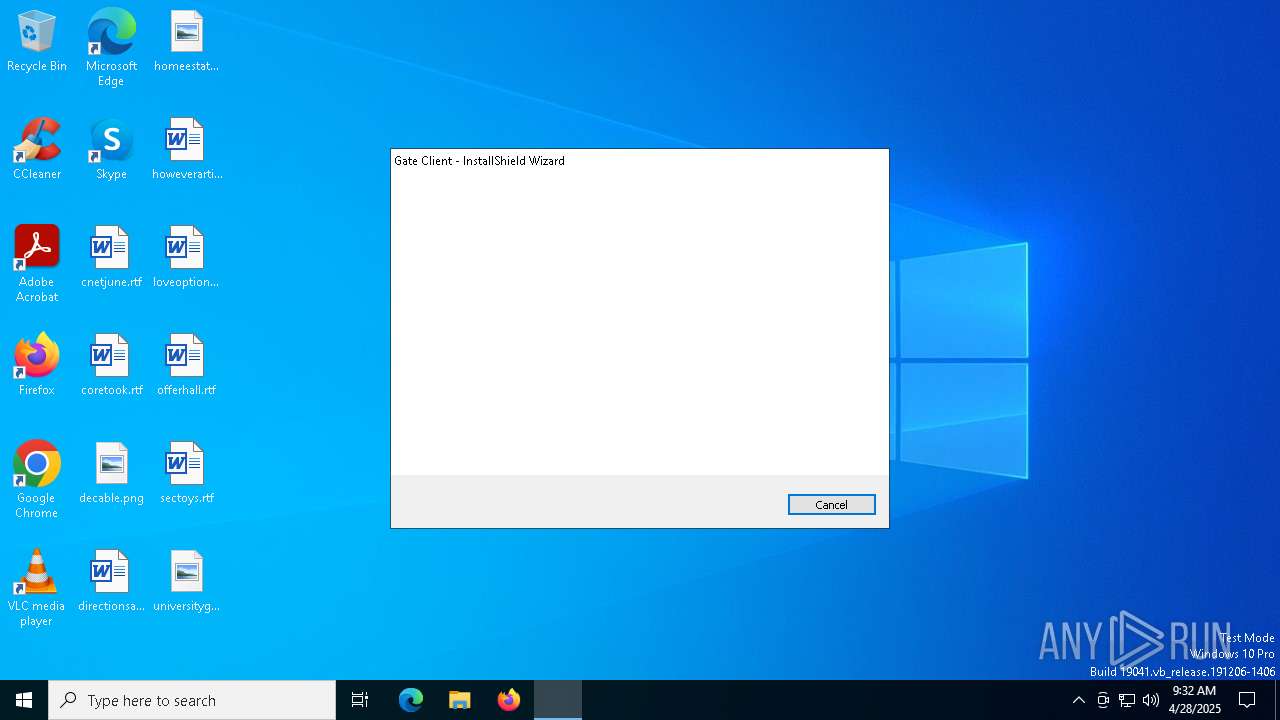
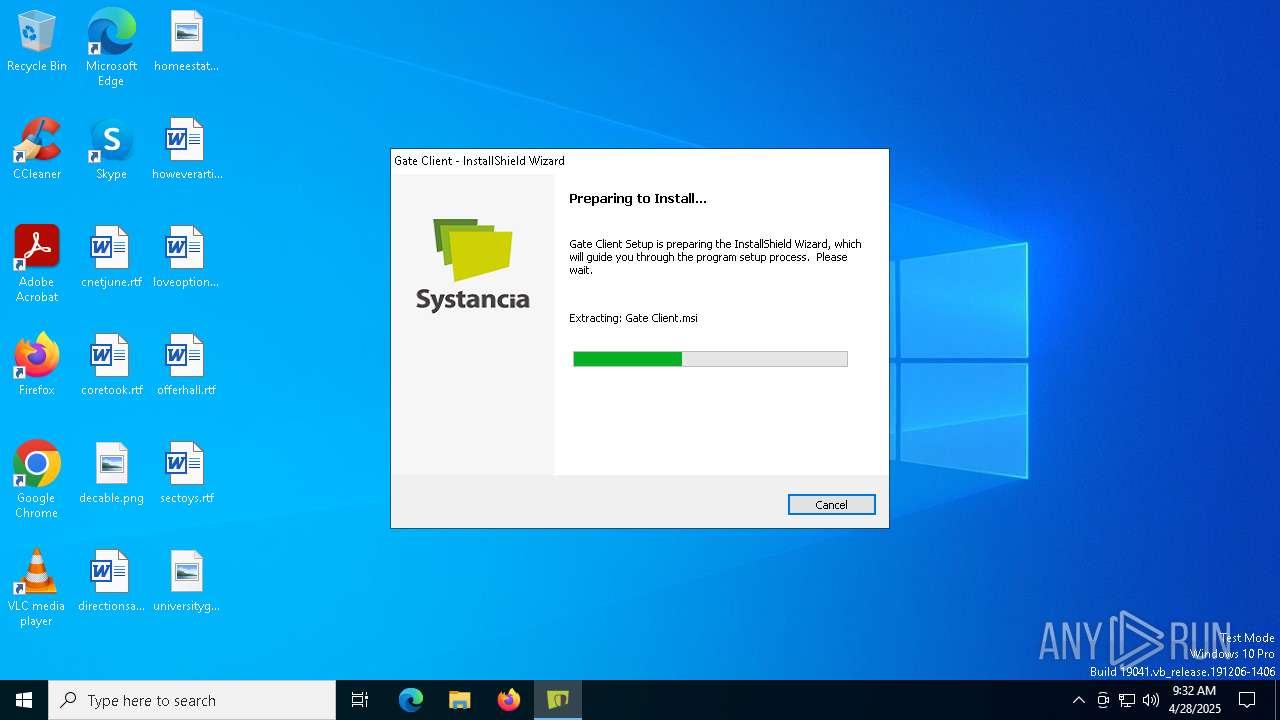
| File name: | setup_Gate_Client.exe |
| Full analysis: | https://app.any.run/tasks/7705d362-55ce-4253-af76-fe2eab8bc1ca |
| Verdict: | Malicious activity |
| Analysis date: | April 28, 2025, 09:32:12 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 39CE5FF448C6B677A154920D1D140D20 |
| SHA1: | 8BA2411A141C7A7112D50C724C3291FE9A83DED9 |
| SHA256: | 3073ED233057DBA1FF244F257904B1E2CB87F62E79C0BC7CA4E56C63525F614D |
| SSDEEP: | 98304:1WoIWpffcKE3hdAAI+cpZOKwDGwQlk5Tf+S+PRCy/y19Z7lfIveQRINXr8nQ+xmx:2SyOtK/M3qUa7hqIaXpaVEbofaC9cA |
MALICIOUS
Reads the value of a key from the registry (SCRIPT)
- msiexec.exe (PID: 1532)
SUSPICIOUS
Executable content was dropped or overwritten
- setup_Gate_Client.exe (PID: 7152)
Starts itself from another location
- setup_Gate_Client.exe (PID: 7152)
There is functionality for taking screenshot (YARA)
- setup_Gate_Client.exe (PID: 7152)
- setup_Gate_Client.exe (PID: 3300)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 5024)
Application launched itself
- msiexec.exe (PID: 5024)
Accesses WMI object display name (SCRIPT)
- msiexec.exe (PID: 5352)
Executes application which crashes
- ipdivaclient.exe (PID: 2344)
- ipdivaclient.exe (PID: 5956)
- ipdivaclient.exe (PID: 1188)
The process deletes folder without confirmation
- setup_Gate_Client.exe (PID: 3300)
Starts CMD.EXE for commands execution
- setup_Gate_Client.exe (PID: 3300)
INFO
Create files in a temporary directory
- setup_Gate_Client.exe (PID: 7152)
- setup_Gate_Client.exe (PID: 3300)
- msiexec.exe (PID: 5728)
The sample compiled with english language support
- setup_Gate_Client.exe (PID: 7152)
- msiexec.exe (PID: 4724)
- msiexec.exe (PID: 5024)
Reads the computer name
- setup_Gate_Client.exe (PID: 7152)
- setup_Gate_Client.exe (PID: 3300)
- msiexec.exe (PID: 5024)
- msiexec.exe (PID: 5728)
- msiexec.exe (PID: 1532)
- msiexec.exe (PID: 5352)
Checks supported languages
- setup_Gate_Client.exe (PID: 7152)
- setup_Gate_Client.exe (PID: 3300)
- msiexec.exe (PID: 5024)
- msiexec.exe (PID: 5728)
- msiexec.exe (PID: 1532)
- msiexec.exe (PID: 5352)
Reads the software policy settings
- msiexec.exe (PID: 4724)
- msiexec.exe (PID: 5024)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 4724)
Executable content was dropped or overwritten
- msiexec.exe (PID: 5728)
- msiexec.exe (PID: 4724)
- msiexec.exe (PID: 5024)
The sample compiled with french language support
- msiexec.exe (PID: 5728)
- msiexec.exe (PID: 5024)
Reads the machine GUID from the registry
- msiexec.exe (PID: 5024)
Reads Environment values
- msiexec.exe (PID: 5352)
Manual execution by a user
- ipdivaclient.exe (PID: 5956)
- ipdivaclient.exe (PID: 1188)
- ipdivaclient.exe (PID: 2344)
Creates a software uninstall entry
- msiexec.exe (PID: 5024)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:07:09 11:55:58+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.39 |
| CodeSize: | 677376 |
| InitializedDataSize: | 676864 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5b7a0 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 8.9.49.0 |
| ProductVersionNumber: | 8.9.49.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Systancia |
| FileDescription: | B49-241122 |
| FileVersion: | 8.9.49 |
| InternalName: | Setup |
| LegalCopyright: | Copyright © Systancia |
| OriginalFileName: | setup_Gate_Client.exe |
| ProductName: | Gate Client |
| ProductVersion: | 8.9.49 |
| InternalBuildNumber: | 212776 |
| ISInternalVersion: | 30.0.157 |
| ISInternalDescription: | Setup Launcher Unicode |
Total processes
157
Monitored processes
20
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 644 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | "C:\WINDOWS\system32\cmd.exe" /c rmdir /s /q "C:\Users\admin\AppData\Local\Temp\{9C78B490-0081-4202-AF31-5137BD93F948}" | C:\Windows\SysWOW64\cmd.exe | — | setup_Gate_Client.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1188 | "C:\Program Files (x86)\Systancia\IPdiva\IpDiva Client\ipdivaclient.exe" | C:\Program Files (x86)\Systancia\IPdiva\IpDiva Client\ipdivaclient.exe | explorer.exe | ||||||||||||
User: admin Company: Systancia Integrity Level: MEDIUM Description: GateClient Exit code: 3221225725 Version: 8.9.1.37 Modules
| |||||||||||||||
| 1532 | C:\Windows\syswow64\MsiExec.exe -Embedding 76776111A1F496280149F6F84E440578 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2084 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 1188 -s 888 | C:\Windows\SysWOW64\WerFault.exe | — | ipdivaclient.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2344 | "C:\Program Files (x86)\Systancia\IPdiva\IpDiva Client\ipdivaclient.exe" | C:\Program Files (x86)\Systancia\IPdiva\IpDiva Client\ipdivaclient.exe | explorer.exe | ||||||||||||
User: admin Company: Systancia Integrity Level: MEDIUM Description: GateClient Exit code: 3221225725 Version: 8.9.1.37 Modules
| |||||||||||||||
| 3300 | C:\Users\admin\AppData\Local\Temp\{9C78B490-0081-4202-AF31-5137BD93F948}\setup_Gate_Client.exe /q"C:\Users\admin\AppData\Local\Temp\setup_Gate_Client.exe" /tempdisk1folder"C:\Users\admin\AppData\Local\Temp\{9C78B490-0081-4202-AF31-5137BD93F948}" /IS_temp /waitingforchildprocess | C:\Users\admin\AppData\Local\Temp\{9C78B490-0081-4202-AF31-5137BD93F948}\setup_Gate_Client.exe | — | setup_Gate_Client.exe | |||||||||||
User: admin Company: Systancia Integrity Level: HIGH Description: B49-241122 Exit code: 0 Version: 8.9.49 Modules
| |||||||||||||||
| 4008 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4724 | "C:\WINDOWS\system32\MSIEXEC.EXE" /i "C:\Users\admin\AppData\Local\Temp\{9C78B490-0081-4202-AF31-5137BD93F948}\Gate Client.msi" SETUPEXEDIR="C:\Users\admin\AppData\Local\Temp" SETUPEXENAME="setup_Gate_Client.exe" | C:\Windows\SysWOW64\msiexec.exe | setup_Gate_Client.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5024 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 358
Read events
14 238
Write events
108
Delete events
12
Modification events
| (PID) Process: | (3300) setup_Gate_Client.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion |
| Operation: | delete value | Name: | %IS_PREREQ%-Gate Client |
Value: | |||
| (PID) Process: | (3300) setup_Gate_Client.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion |
| Operation: | delete value | Name: | %IS_PREREQF%-Gate Client |
Value: | |||
| (PID) Process: | (3300) setup_Gate_Client.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | delete value | Name: | ISSetupPrerequisistes |
Value: | |||
| (PID) Process: | (3300) setup_Gate_Client.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion |
| Operation: | write | Name: | %IS_PREREQCMD%-Gate Client |
Value: "C:\Users\admin\AppData\Local\Temp\setup_Gate_Client.exe" /waitingforchildprocess" | |||
| (PID) Process: | (4724) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{618736E0-3C3D-11CF-810C-00AA00389B71}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (4724) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{618736E0-3C3D-11CF-810C-00AA00389B71}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (4724) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Volatile\00\MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{03022430-ABC4-11D0-BDE2-00AA001A1953}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (4724) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Volatile\00\MACHINE\SOFTWARE\Classes\Interface\{03022430-ABC4-11D0-BDE2-00AA001A1953}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (5728) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings |
| Operation: | write | Name: | JITDebug |
Value: 0 | |||
| (PID) Process: | (5024) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: A0130000DE013E7420B8DB01 | |||
Executable files
9
Suspicious files
33
Text files
27
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3300 | setup_Gate_Client.exe | C:\Users\admin\AppData\Local\Temp\{9C78B490-0081-4202-AF31-5137BD93F948}\Gate Client.msi | — | |
MD5:— | SHA256:— | |||
| 5024 | msiexec.exe | C:\Windows\Installer\10f455.msi | — | |
MD5:— | SHA256:— | |||
| 7152 | setup_Gate_Client.exe | C:\Users\admin\AppData\Local\Temp\~B941.tmp | text | |
MD5:B6C464C3B75B68507E45EE3711AB8AF4 | SHA256:87533F5B5B8BAEAFA1D95CAF72439DEDF37856B157D51D52D8562F21210D1A4F | |||
| 7152 | setup_Gate_Client.exe | C:\Users\admin\AppData\Local\Temp\{9C78B490-0081-4202-AF31-5137BD93F948}\setup_Gate_Client.exe | executable | |
MD5:39CE5FF448C6B677A154920D1D140D20 | SHA256:3073ED233057DBA1FF244F257904B1E2CB87F62E79C0BC7CA4E56C63525F614D | |||
| 3300 | setup_Gate_Client.exe | C:\Users\admin\AppData\Local\Temp\~BA1A.tmp | text | |
MD5:B6C464C3B75B68507E45EE3711AB8AF4 | SHA256:87533F5B5B8BAEAFA1D95CAF72439DEDF37856B157D51D52D8562F21210D1A4F | |||
| 7152 | setup_Gate_Client.exe | C:\Users\admin\AppData\Local\Temp\{9C78B490-0081-4202-AF31-5137BD93F948}\_ISMSIDEL.INI | binary | |
MD5:0B8133884A759385A073ED86FB95C905 | SHA256:13DBD40BF8665BF9F232EB09227AAB556FCEBCF47463ED2DCB43C3DD2CB678AC | |||
| 7152 | setup_Gate_Client.exe | C:\Users\admin\AppData\Local\Temp\~B962.tmp | text | |
MD5:B6C464C3B75B68507E45EE3711AB8AF4 | SHA256:87533F5B5B8BAEAFA1D95CAF72439DEDF37856B157D51D52D8562F21210D1A4F | |||
| 7152 | setup_Gate_Client.exe | C:\Users\admin\AppData\Local\Temp\~B972.tmp | text | |
MD5:B6C464C3B75B68507E45EE3711AB8AF4 | SHA256:87533F5B5B8BAEAFA1D95CAF72439DEDF37856B157D51D52D8562F21210D1A4F | |||
| 3300 | setup_Gate_Client.exe | C:\Users\admin\AppData\Local\Temp\{9C78B490-0081-4202-AF31-5137BD93F948}\0x0409.ini | text | |
MD5:1196F20CA8BCAA637625E6A061D74C9E | SHA256:CDB316D7F9AA2D854EB28F7A333426A55CC65FA7D31B0BDF8AE108E611583D29 | |||
| 7152 | setup_Gate_Client.exe | C:\Users\admin\AppData\Local\Temp\~B961.tmp | text | |
MD5:B6C464C3B75B68507E45EE3711AB8AF4 | SHA256:87533F5B5B8BAEAFA1D95CAF72439DEDF37856B157D51D52D8562F21210D1A4F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
22
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5400 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5400 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |