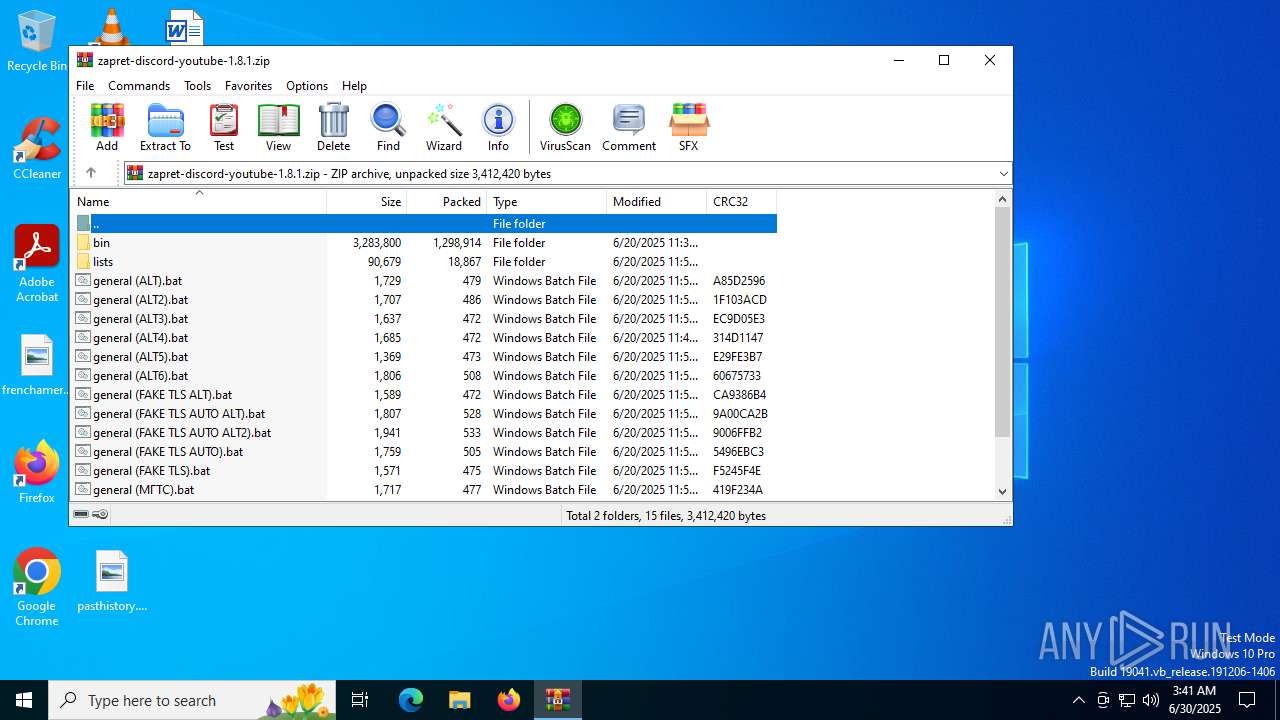
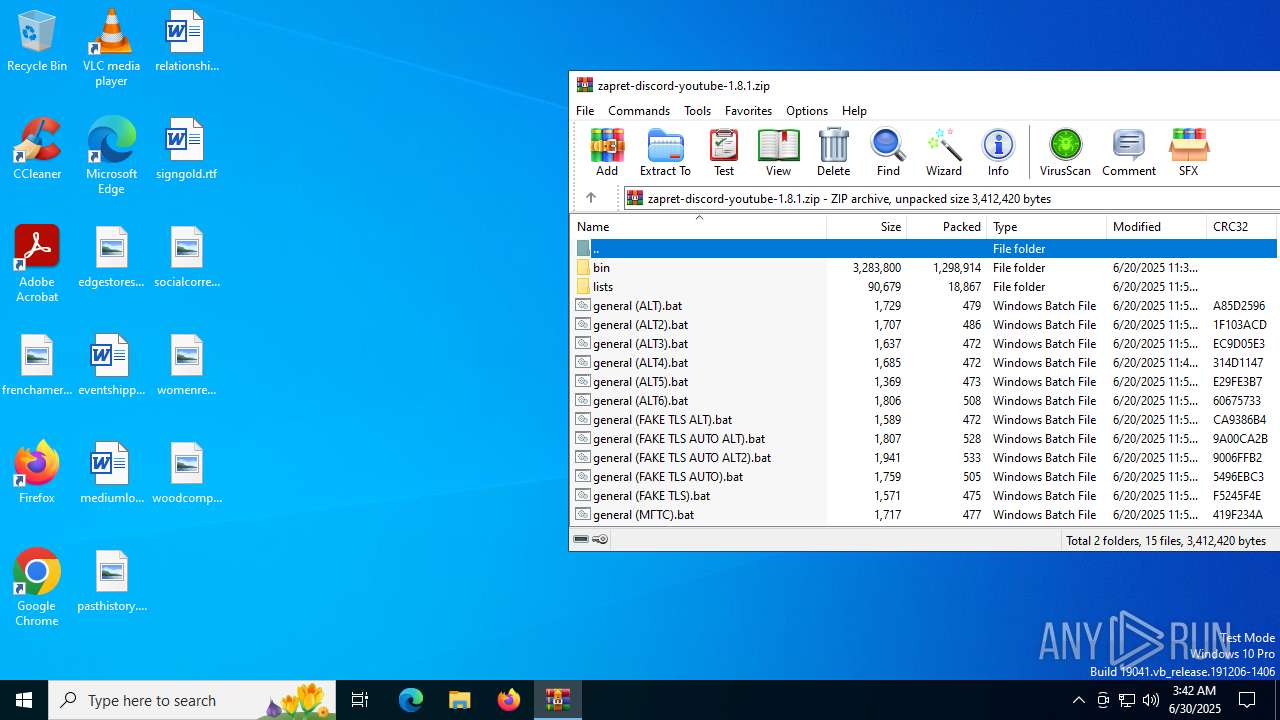
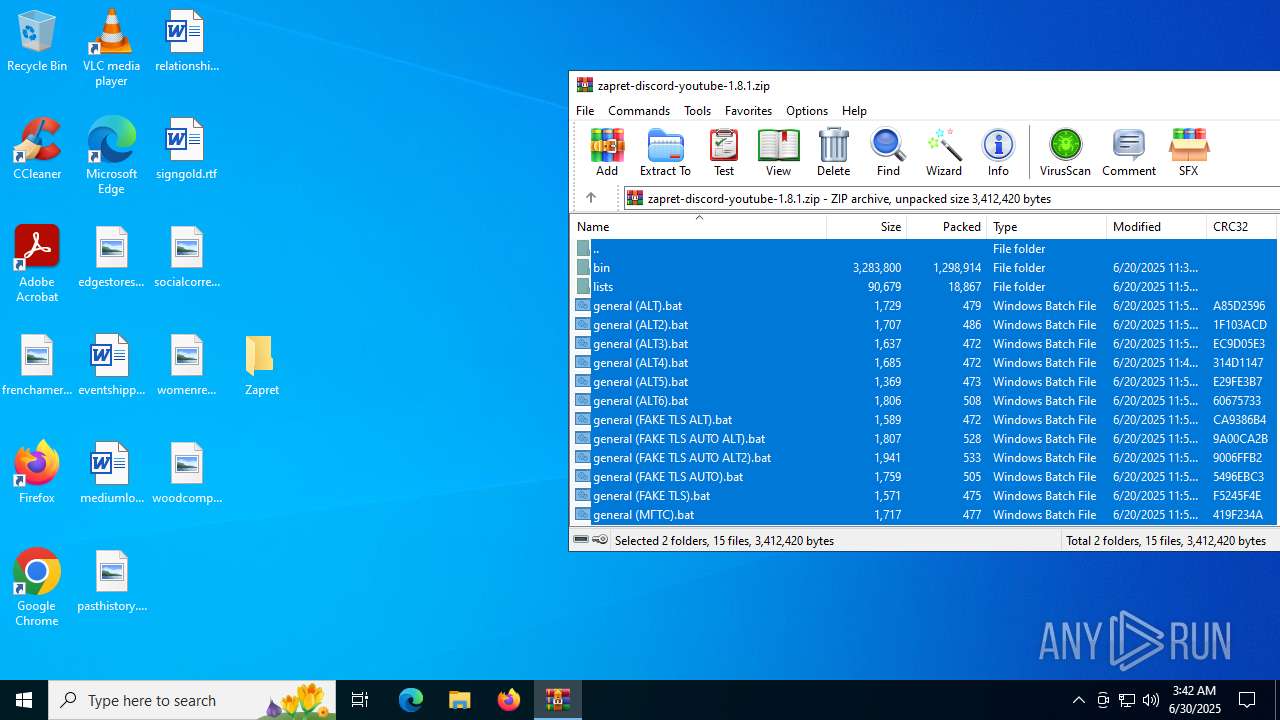
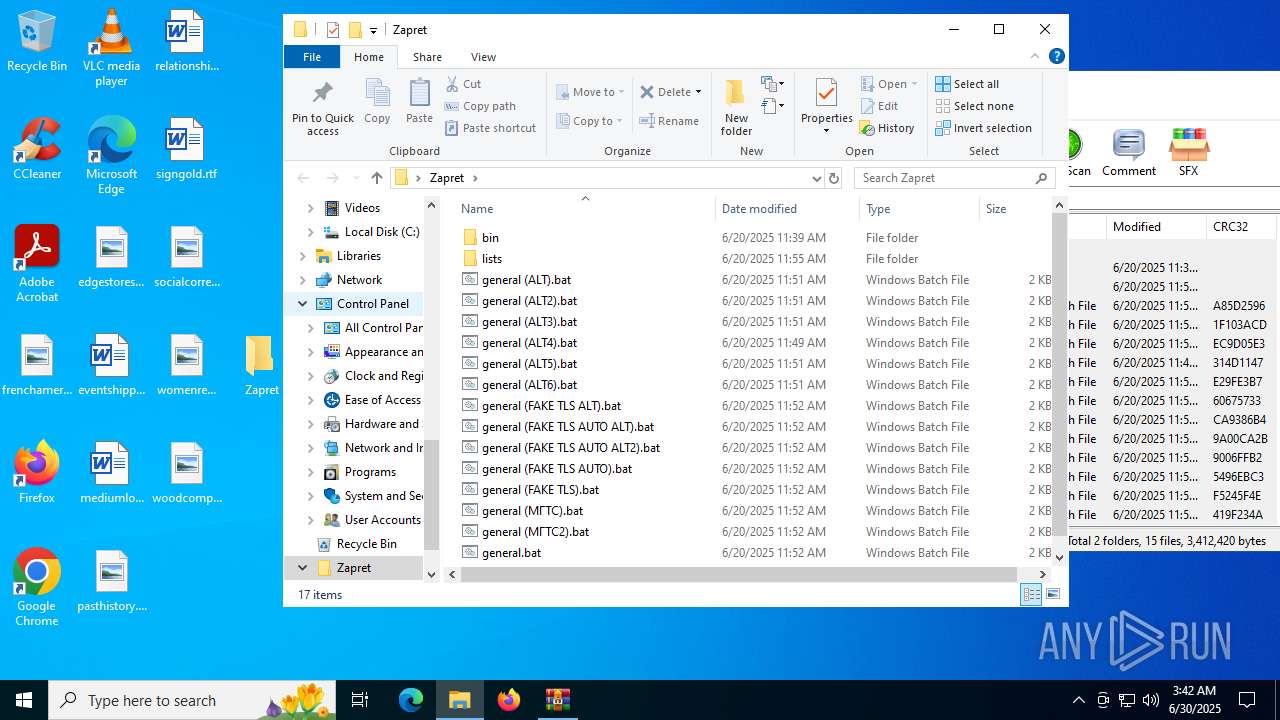
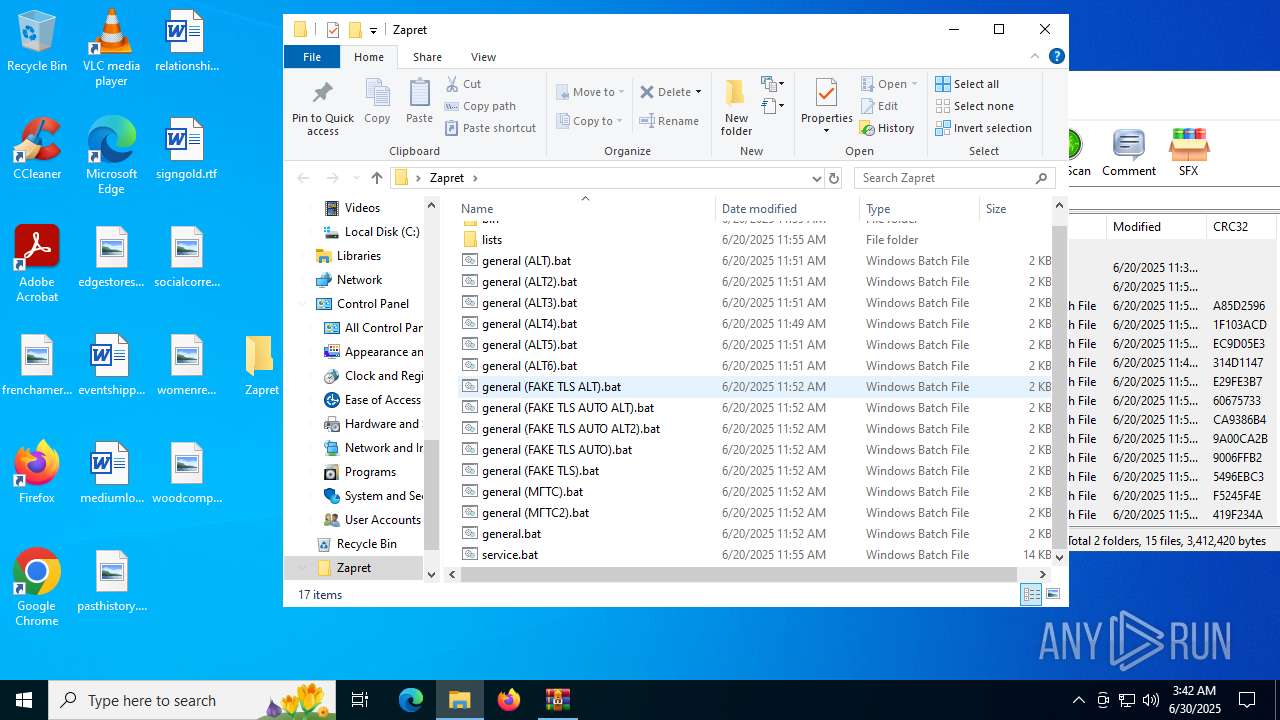
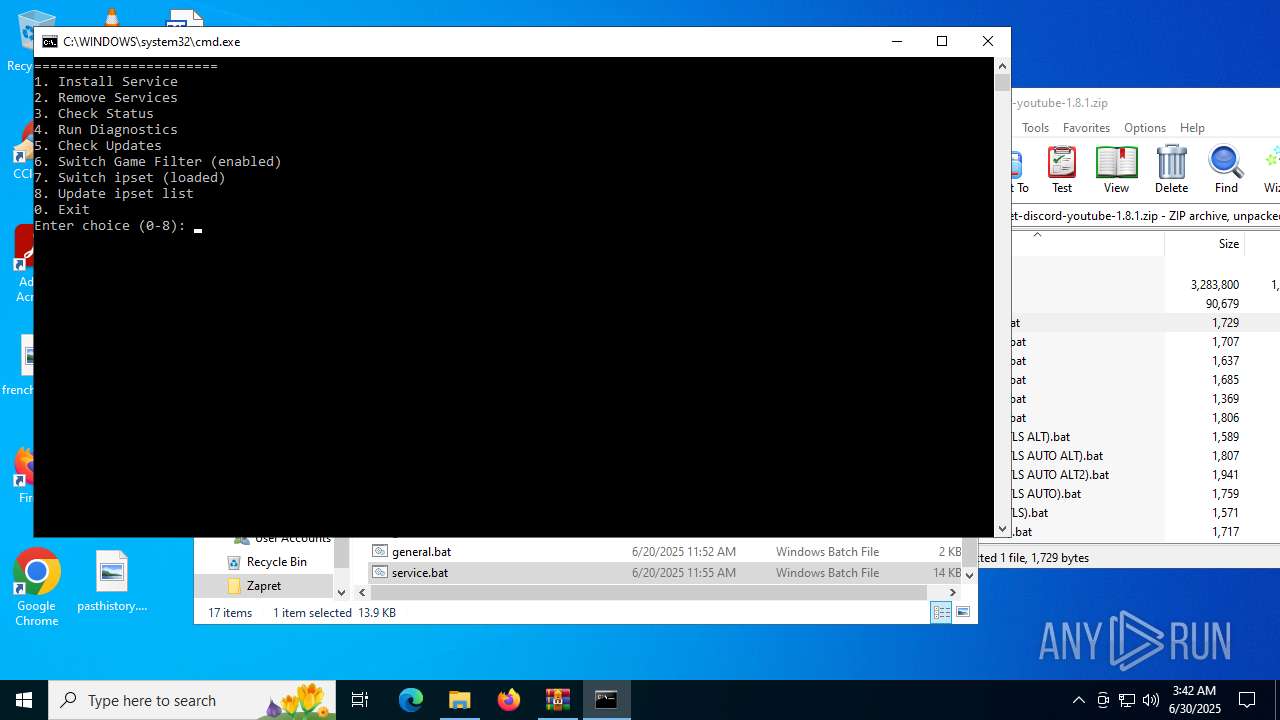
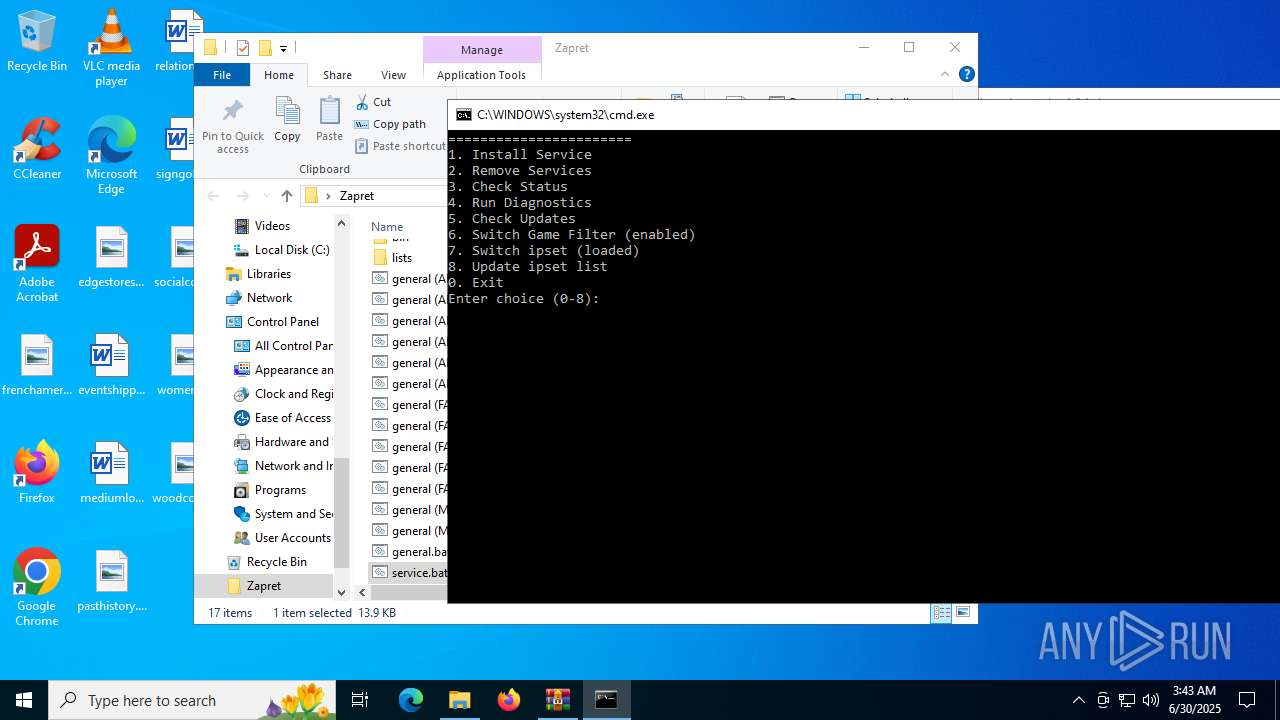
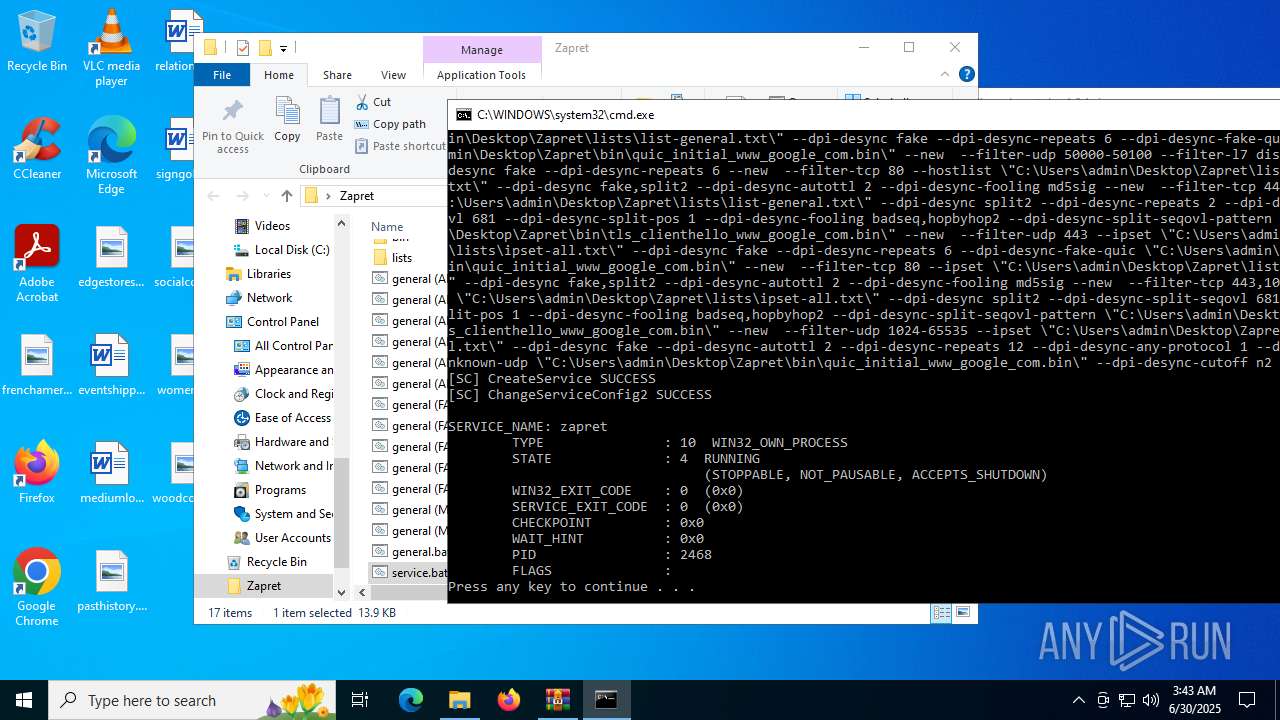
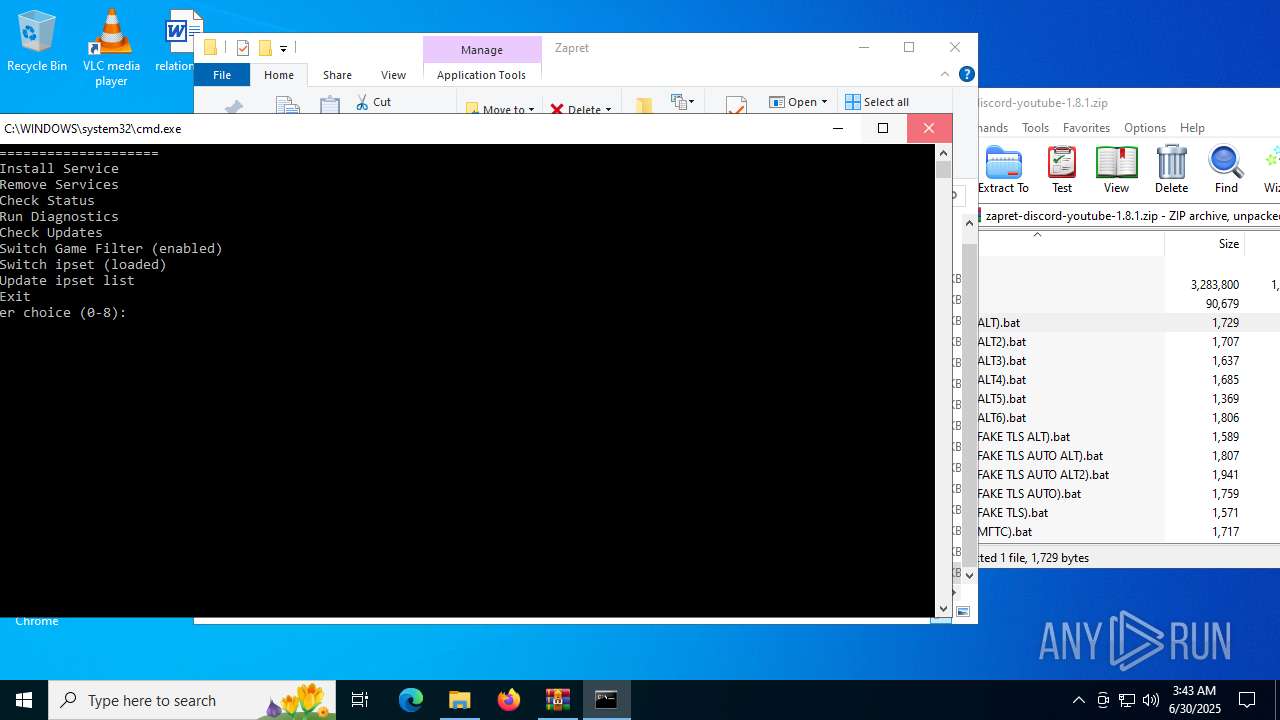
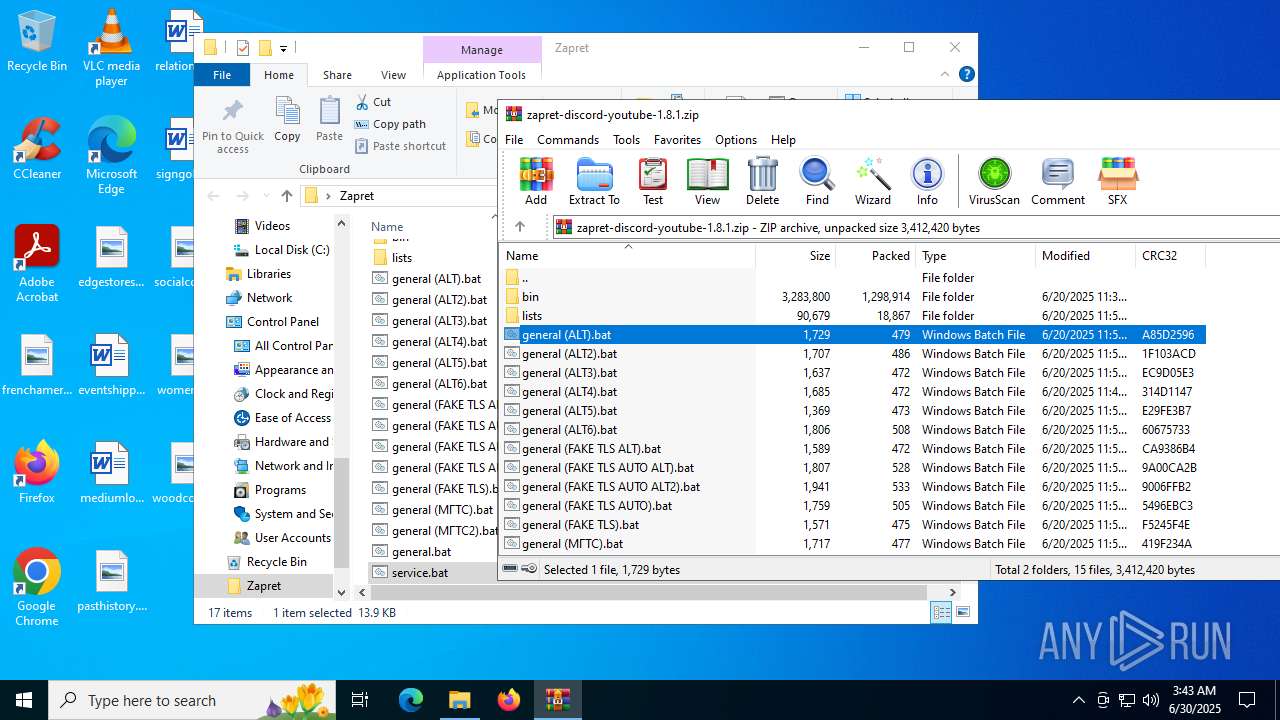
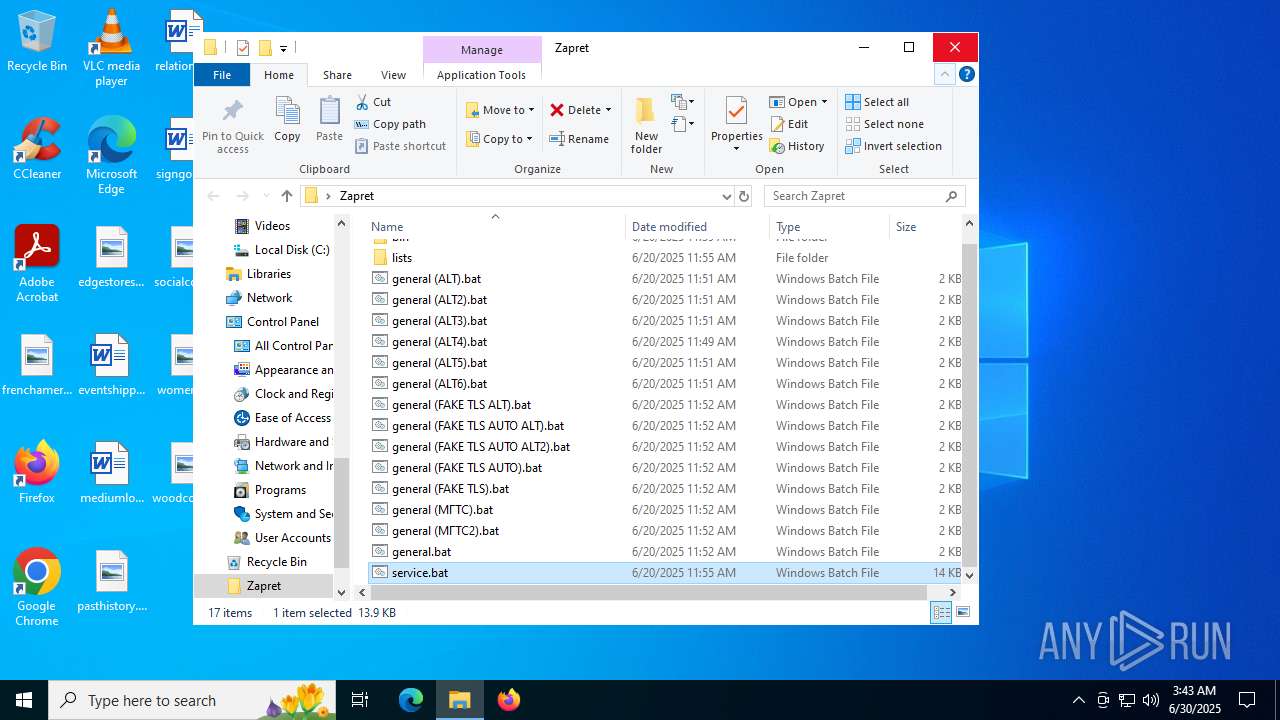
| File name: | zapret-discord-youtube-1.8.1.zip |
| Full analysis: | https://app.any.run/tasks/3cf32ef1-aba9-4e55-afc5-72ec12e56019 |
| Verdict: | Malicious activity |
| Analysis date: | June 30, 2025, 03:41:52 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 9C89182226E73F03E9E1C09C9EF10C2C |
| SHA1: | F029742BA3834EC9AF4465EA4AA80CF94DE3B335 |
| SHA256: | 30698809A1EBF51A4A44E914000235069EFAC911A104C3FD2FC04748CFE5059B |
| SSDEEP: | 49152:cvw/Cv8X9eQS0s7eWvRlefNYLw1yD1LE6tVz64qEu1KufrHNW3FzmUS74G6+hefm:x/e8teQzUJRlSNYLeyD1DhdqCirtW3FY |
MALICIOUS
Detects Cygwin installation
- WinRAR.exe (PID: 5080)
Malicious driver has been detected
- WinRAR.exe (PID: 5080)
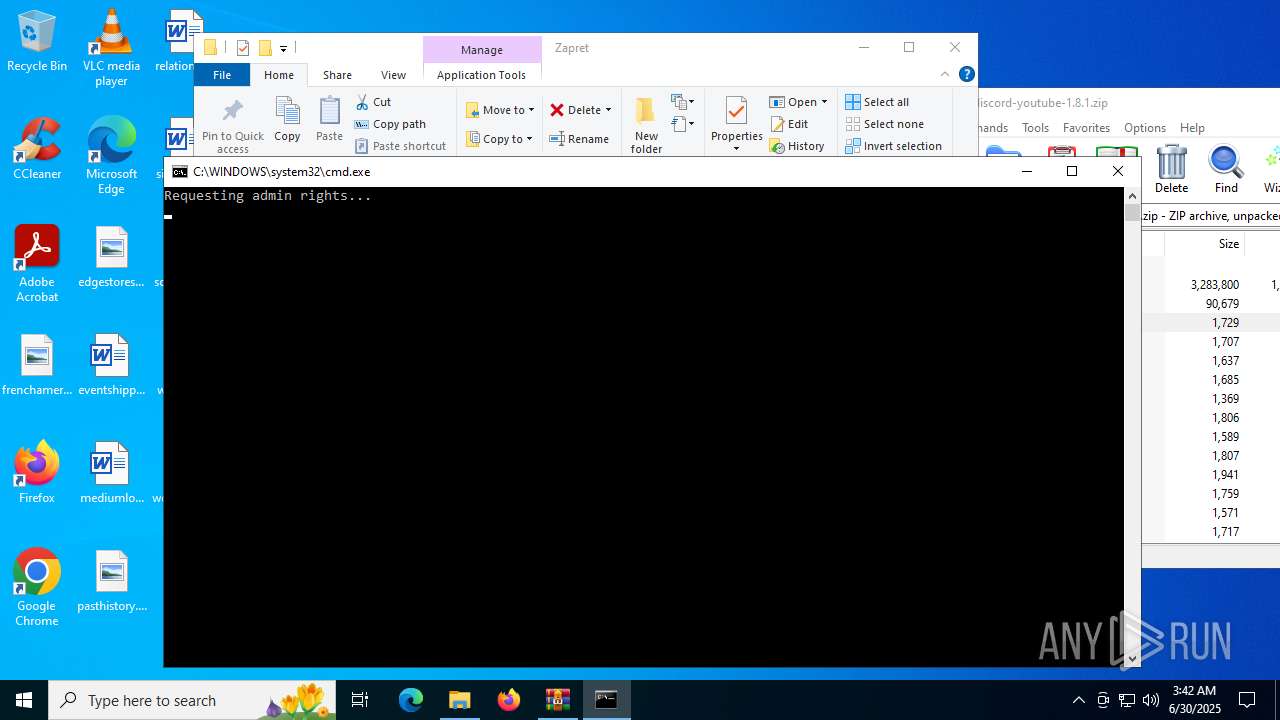
Starts NET.EXE for service management
- cmd.exe (PID: 2192)
- net.exe (PID: 1352)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 5080)
Starts process via Powershell
- powershell.exe (PID: 3636)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 3636)
- cmd.exe (PID: 2192)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2800)
Executing commands from a ".bat" file
- powershell.exe (PID: 3636)
- cmd.exe (PID: 2192)
Starts application with an unusual extension
- cmd.exe (PID: 2192)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2192)
Application launched itself
- cmd.exe (PID: 2192)
Hides command output
- cmd.exe (PID: 888)
Windows service management via SC.EXE
- sc.exe (PID: 684)
- sc.exe (PID: 2388)
- sc.exe (PID: 3000)
Creates a new Windows service
- sc.exe (PID: 432)
Starts SC.EXE for service management
- cmd.exe (PID: 2192)
Executes as Windows Service
- winws.exe (PID: 2468)
INFO
Manual execution by a user
- cmd.exe (PID: 2800)
The sample compiled with english language support
- WinRAR.exe (PID: 5080)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5080)
Checks supported languages
- chcp.com (PID: 3924)
- chcp.com (PID: 1984)
- chcp.com (PID: 5104)
- chcp.com (PID: 6636)
- winws.exe (PID: 2468)
- chcp.com (PID: 4968)
Changes the display of characters in the console
- cmd.exe (PID: 2192)
Reads the computer name
- winws.exe (PID: 2468)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:06:20 14:39:12 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | bin/ |
Total processes
219
Monitored processes
85
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 72 | findstr ":" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 432 | sc create zapret binPath= "\"C:\Users\admin\Desktop\Zapret\bin\winws.exe\" --wf-tcp 80,443,1024-65535 --wf-udp 443,50000-50100,1024-65535 --filter-udp 443 --hostlist \"C:\Users\admin\Desktop\Zapret\lists\list-general.txt\" --dpi-desync fake --dpi-desync-repeats 6 --dpi-desync-fake-quic \"C:\Users\admin\Desktop\Zapret\bin\quic_initial_www_google_com.bin\" --new --filter-udp 50000-50100 --filter-l7 discord,stun --dpi-desync fake --dpi-desync-repeats 6 --new --filter-tcp 80 --hostlist \"C:\Users\admin\Desktop\Zapret\lists\list-general.txt\" --dpi-desync fake,split2 --dpi-desync-autottl 2 --dpi-desync-fooling md5sig --new --filter-tcp 443 --hostlist \"C:\Users\admin\Desktop\Zapret\lists\list-general.txt\" --dpi-desync split2 --dpi-desync-repeats 2 --dpi-desync-split-seqovl 681 --dpi-desync-split-pos 1 --dpi-desync-fooling badseq,hopbyhop2 --dpi-desync-split-seqovl-pattern \"C:\Users\admin\Desktop\Zapret\bin\tls_clienthello_www_google_com.bin\" --new --filter-udp 443 --ipset \"C:\Users\admin\Desktop\Zapret\lists\ipset-all.txt\" --dpi-desync fake --dpi-desync-repeats 6 --dpi-desync-fake-quic \"C:\Users\admin\Desktop\Zapret\bin\quic_initial_www_google_com.bin\" --new --filter-tcp 80 --ipset \"C:\Users\admin\Desktop\Zapret\lists\ipset-all.txt\" --dpi-desync fake,split2 --dpi-desync-autottl 2 --dpi-desync-fooling md5sig --new --filter-tcp 443,1024-65535 --ipset \"C:\Users\admin\Desktop\Zapret\lists\ipset-all.txt\" --dpi-desync split2 --dpi-desync-split-seqovl 681 --dpi-desync-split-pos 1 --dpi-desync-fooling badseq,hopbyhop2 --dpi-desync-split-seqovl-pattern \"C:\Users\admin\Desktop\Zapret\bin\tls_clienthello_www_google_com.bin\" --new --filter-udp 1024-65535 --ipset \"C:\Users\admin\Desktop\Zapret\lists\ipset-all.txt\" --dpi-desync fake --dpi-desync-autottl 2 --dpi-desync-repeats 12 --dpi-desync-any-protocol 1 --dpi-desync-fake-unknown-udp \"C:\Users\admin\Desktop\Zapret\bin\quic_initial_www_google_com.bin\" --dpi-desync-cutoff n2" DisplayName= "zapret" start= auto | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo %LISTS%list-general.txt " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | sc delete zapret | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 888 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo chcp 65001 > nul " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1216 | findstr ":" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1324 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo %BIN%tls_clienthello_www_google_com.bin " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1352 | findstr /i "winws.exe" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1352 | net stop zapret | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1512 | findstr /i "winws.exe" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 164
Read events
10 140
Write events
24
Delete events
0
Modification events
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\zapret-discord-youtube-1.8.1.zip | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
4
Suspicious files
3
Text files
20
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5080 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5080.25110\bin\tls_clienthello_www_google_com.bin | binary | |
MD5:41E47557F16690DF1781F67C8712714E | SHA256:F966351AE376963DFFBCB5B94256872649B9CDAAB8C5175025936FA50E07DC19 | |||
| 5080 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5080.25110\general (ALT2).bat | text | |
MD5:B7A7EEAF083E94219A2D7F5073A6B5F4 | SHA256:79A035EC51926585D8046D1E17CA34DB68F8069FDDC864704360B8C92E7BEDA3 | |||
| 5080 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5080.25110\bin\cygwin1.dll | executable | |
MD5:A1C82ED072DC079DD7851F82D9AA7678 | SHA256:103104A52E5293CE418944725DF19E2BF81AD9269B9A120D71D39028E821499B | |||
| 5080 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5080.25110\general (ALT3).bat | text | |
MD5:05E6BED20602B7446CE108AF184937AA | SHA256:52C9615FAC65EF030CB31BAB6C5226A1A86216C52570F19964506F0990AD3296 | |||
| 5080 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5080.25110\bin\WinDivert.dll | executable | |
MD5:B2014D33EE645112D5DC16FE9D9FCBFF | SHA256:C1E060EE19444A259B2162F8AF0F3FE8C4428A1C6F694DCE20DE194AC8D7D9A2 | |||
| 5080 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5080.25110\bin\WinDivert64.sys | executable | |
MD5:89ED5BE7EA83C01D0DE33D3519944AA5 | SHA256:8DA085332782708D8767BCACE5327A6EC7283C17CFB85E40B03CD2323A90DDC2 | |||
| 5080 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5080.25110\bin\winws.exe | executable | |
MD5:2008323884A0101D616142447D19F820 | SHA256:8DC19655C2940A64D9FAE717E7942CF11EEB39AF9DEA695DB31C335DF762A18E | |||
| 5080 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5080.25110\general (ALT).bat | text | |
MD5:4CBFC3D0DC8D04E3BC5F94DD93EC2857 | SHA256:AF117A9F7EF0668B6CA14AEB8CE40EA21D8D008DDA3636627DF60ED8B22B77B2 | |||
| 5080 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5080.25110\general (ALT4).bat | text | |
MD5:4B68B32CAB7661AC135EED77F25ADB2F | SHA256:18A4560815EFAAFECF1A5566A8B7C9338DA96C87C04515D7A746FF3EF19E6D22 | |||
| 5080 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5080.25110\general (ALT5).bat | text | |
MD5:374635972157D5CEF34340C1FD697E04 | SHA256:5A4688161D1CDE8043511CC111464DEE9C8226C611AB7C1F048CA4F11169F084 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
23
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.20.245.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7020 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1180 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1180 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3964 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 2.20.245.139:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
7020 | svchost.exe | 20.190.159.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7020 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |