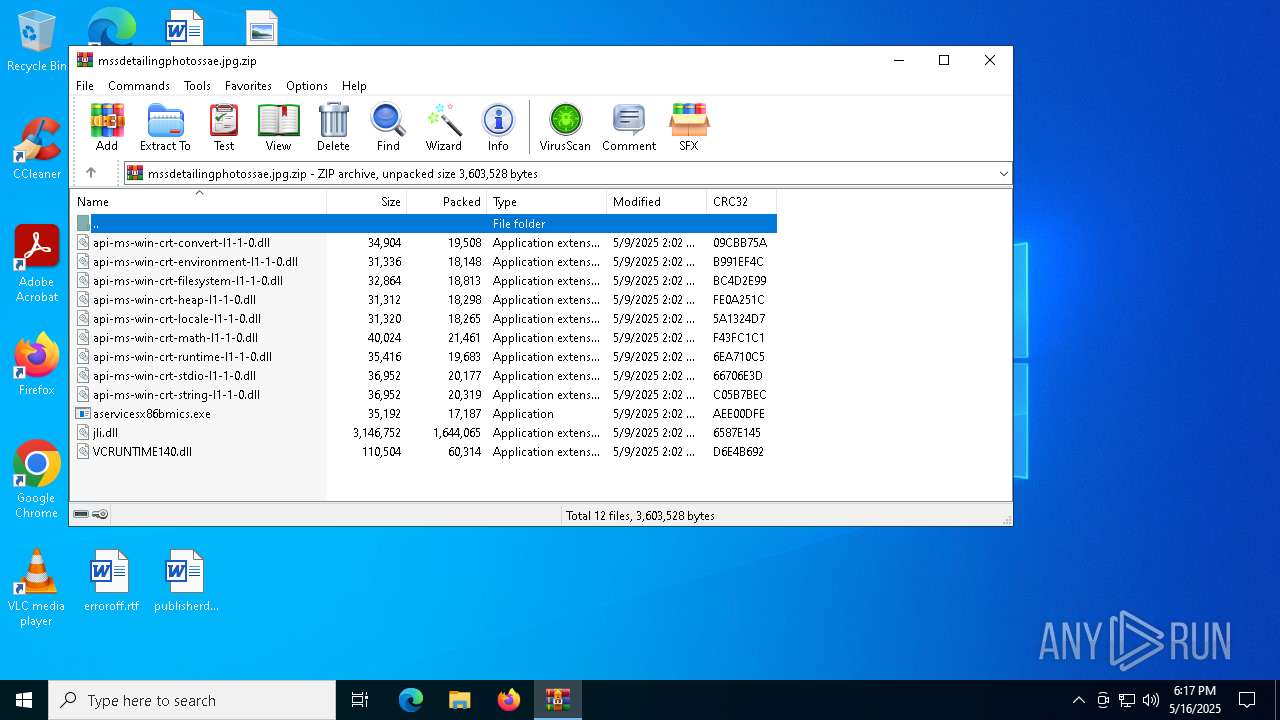
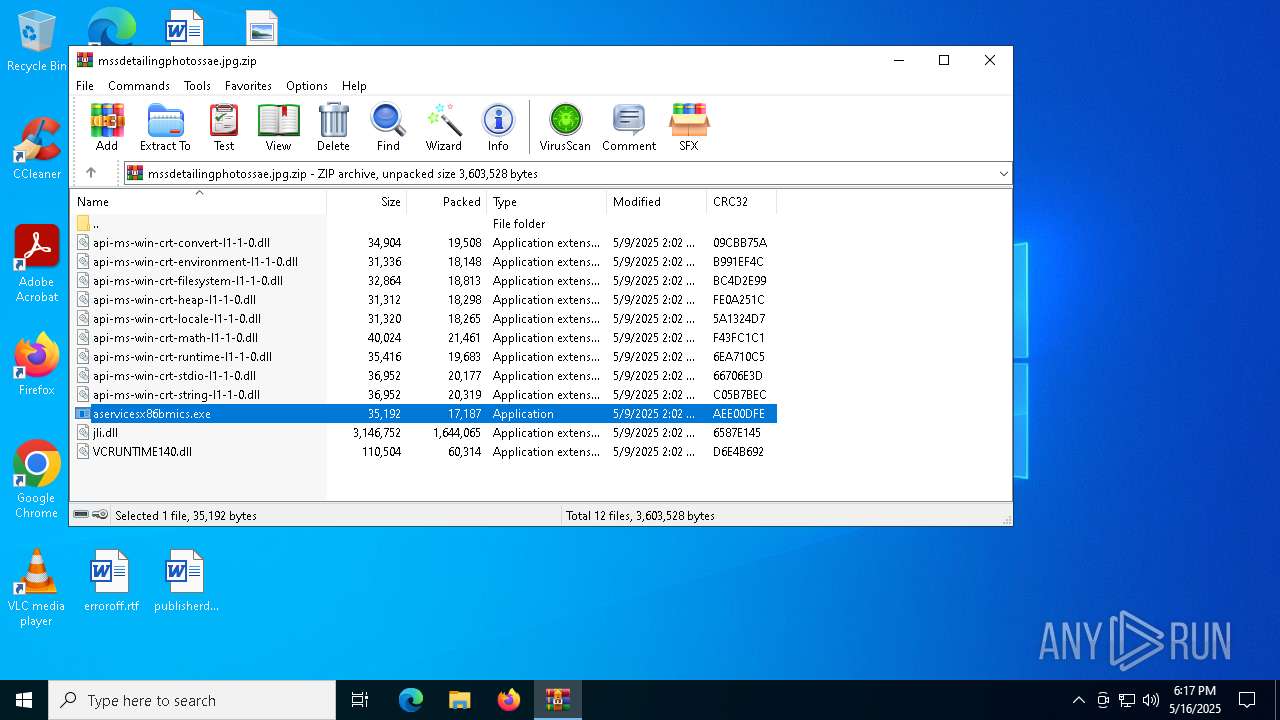
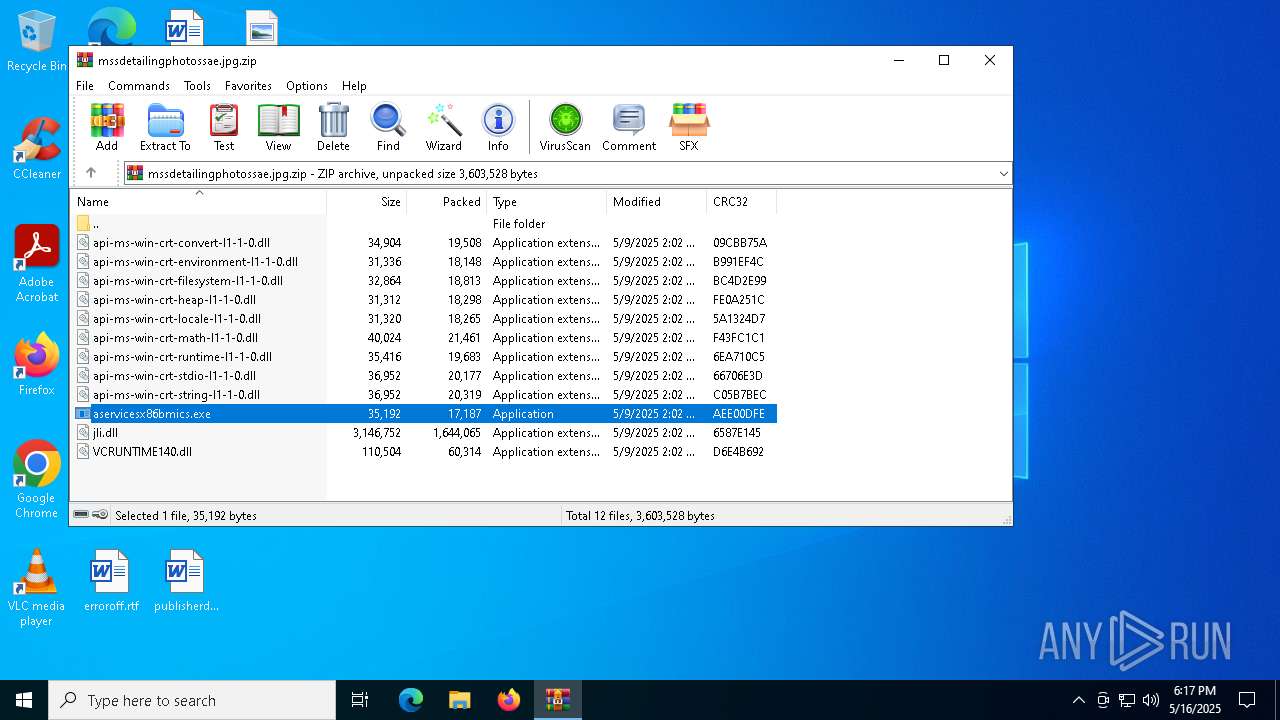
| download: | /mssdetailingphotossae.jpg |
| Full analysis: | https://app.any.run/tasks/e52dfa76-ce57-4d21-b4ac-7cf75a8b78ce |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 18:17:38 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
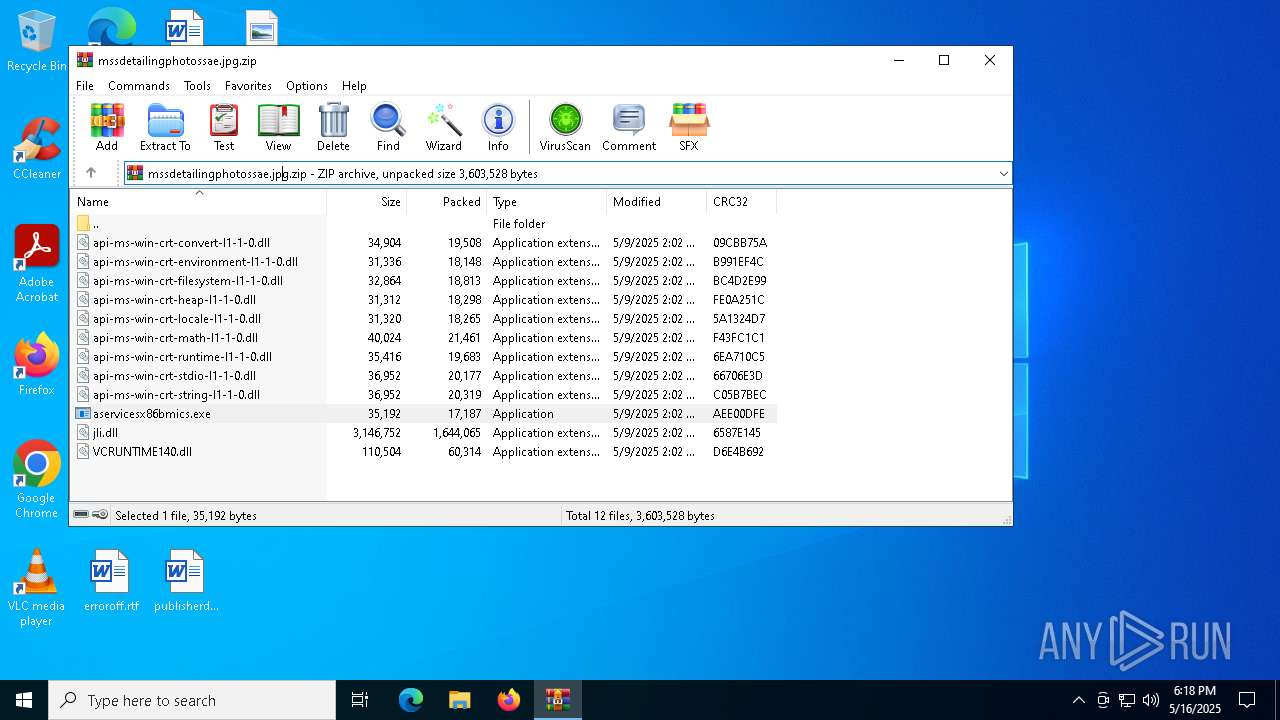
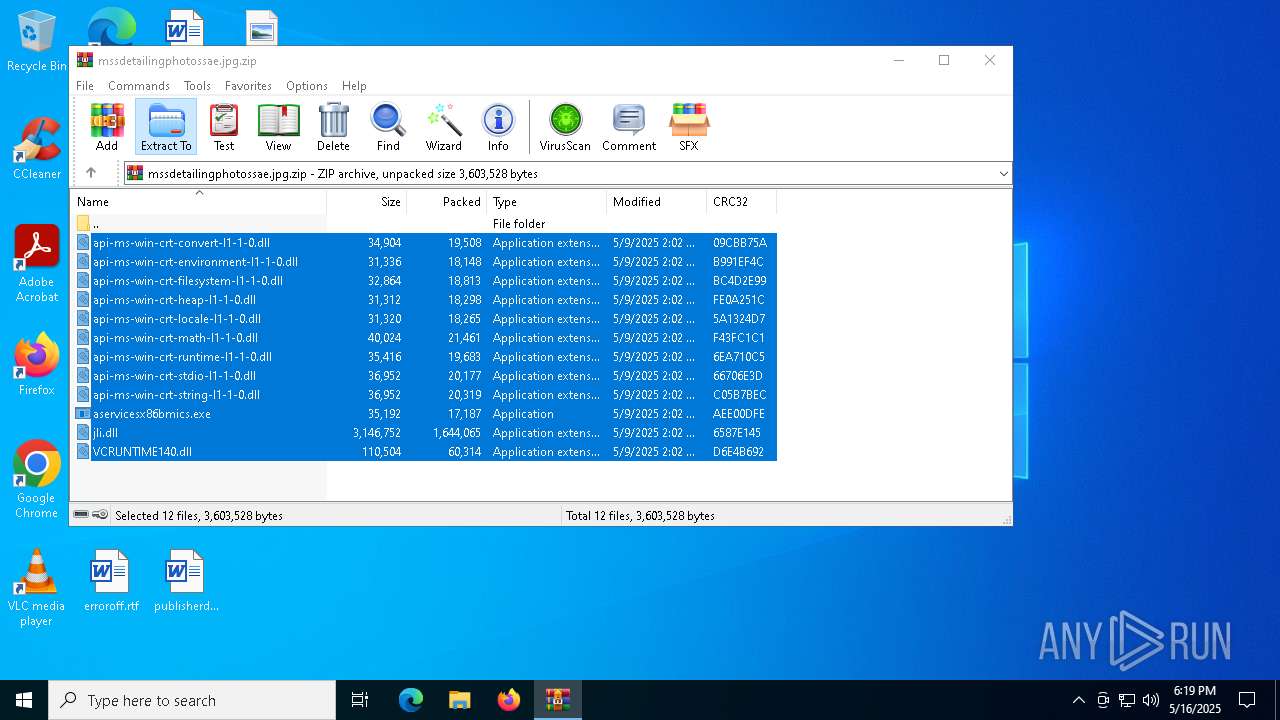
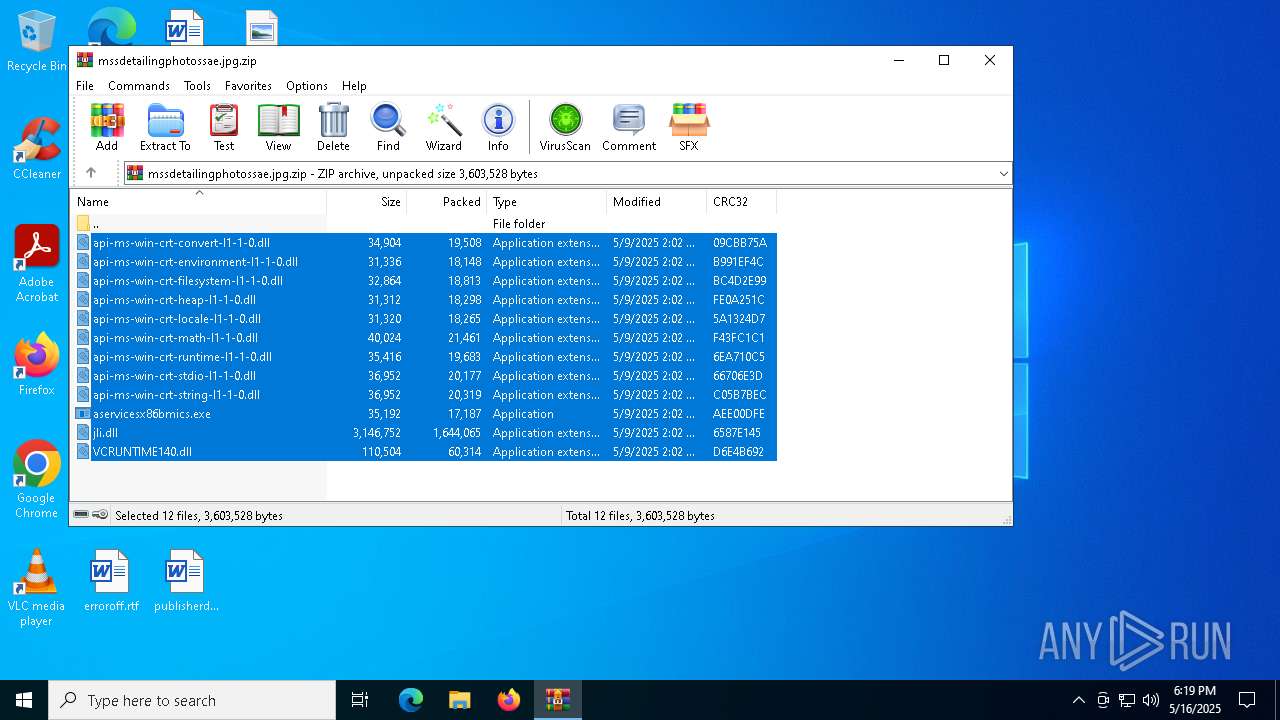
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | D652CD3C471B2AAA2E060A7CBDEEDE93 |
| SHA1: | 8C54336C0DB6AA5D35EF5A23D2C8E16BB1BB3AB2 |
| SHA256: | 30659DA3F746A54C390205B9B524D96BC74DBA107B78152A39734845ED0E58AB |
| SSDEEP: | 98304:IT7qit+fDlAyeq1EMHPAup3xw7eUc4zDo6cywWoAP4l2xeWQU5fziNPv13hIOhCw:jYC |
MALICIOUS
No malicious indicators.SUSPICIOUS
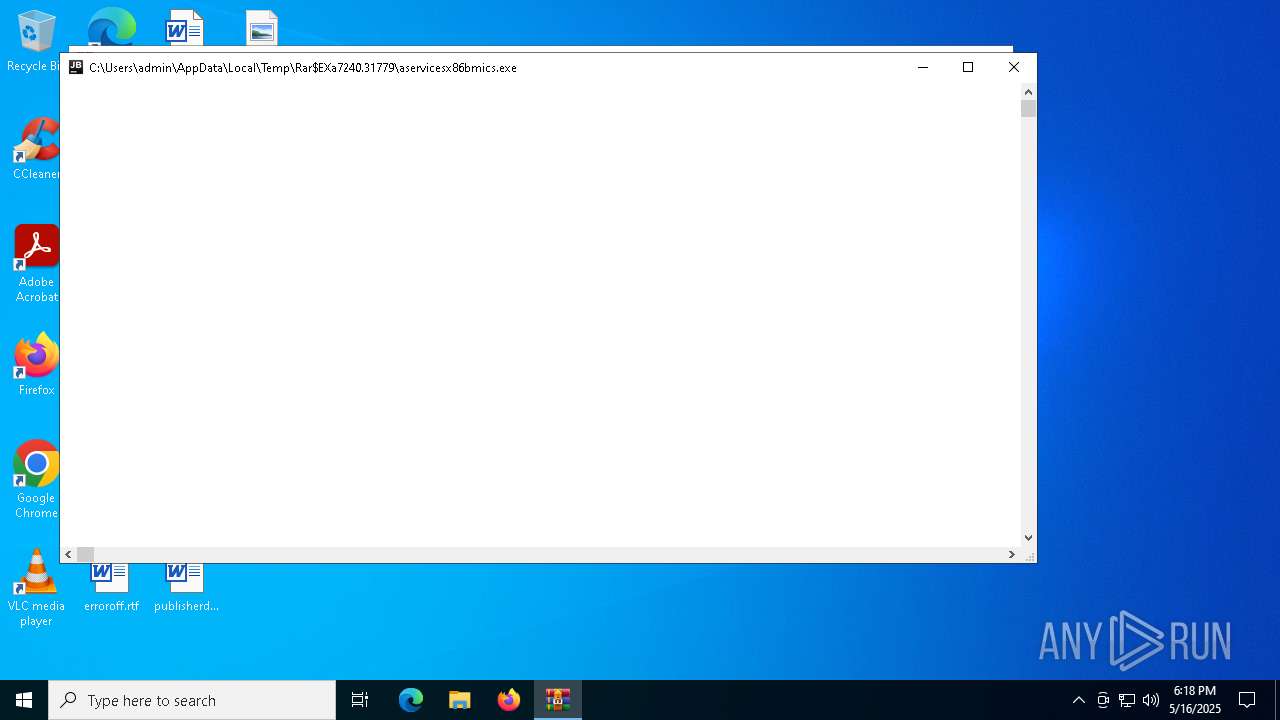
Process drops legitimate windows executable
- WinRAR.exe (PID: 7240)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7240)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7240)
The sample compiled with english language support
- WinRAR.exe (PID: 7240)
Manual execution by a user
- aservicesx86bmics.exe (PID: 2852)
- aservicesx86bmics.exe (PID: 1228)
Process checks computer location settings
- aservicesx86bmics.exe (PID: 8068)
- aservicesx86bmics.exe (PID: 2852)
- aservicesx86bmics.exe (PID: 1228)
Checks supported languages
- aservicesx86bmics.exe (PID: 2852)
- aservicesx86bmics.exe (PID: 1228)
- aservicesx86bmics.exe (PID: 8068)
Reads the computer name
- aservicesx86bmics.exe (PID: 2852)
- aservicesx86bmics.exe (PID: 8068)
- aservicesx86bmics.exe (PID: 1228)
Reads the software policy settings
- slui.exe (PID: 7448)
- slui.exe (PID: 8180)
Checks proxy server information
- slui.exe (PID: 8180)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:09 02:02:16 |
| ZipCRC: | 0x09cbb75a |
| ZipCompressedSize: | 19508 |
| ZipUncompressedSize: | 34904 |
| ZipFileName: | api-ms-win-crt-convert-l1-1-0.dll |
Total processes
144
Monitored processes
10
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1228 | "C:\Users\admin\Desktop\aservicesx86bmics.exe" | C:\Users\admin\Desktop\aservicesx86bmics.exe | explorer.exe | ||||||||||||
User: admin Company: JetBrains s.r.o. Integrity Level: HIGH Description: OpenJDK Platform binary Exit code: 0 Version: 21.0.6.0 Modules
| |||||||||||||||
| 2852 | "C:\Users\admin\Desktop\aservicesx86bmics.exe" | C:\Users\admin\Desktop\aservicesx86bmics.exe | — | explorer.exe | |||||||||||
User: admin Company: JetBrains s.r.o. Integrity Level: MEDIUM Description: OpenJDK Platform binary Exit code: 0 Version: 21.0.6.0 Modules
| |||||||||||||||
| 4408 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | aservicesx86bmics.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5380 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | aservicesx86bmics.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7240 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\mssdetailingphotossae.jpg.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7416 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7448 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8068 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7240.31779\aservicesx86bmics.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa7240.31779\aservicesx86bmics.exe | — | WinRAR.exe | |||||||||||
User: admin Company: JetBrains s.r.o. Integrity Level: MEDIUM Description: OpenJDK Platform binary Exit code: 0 Version: 21.0.6.0 Modules
| |||||||||||||||
| 8092 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | aservicesx86bmics.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8180 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 860
Read events
3 826
Write events
21
Delete events
13
Modification events
| (PID) Process: | (7240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\mssdetailingphotossae.jpg.zip | |||
| (PID) Process: | (7240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (7240) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
24
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7240.31779\api-ms-win-crt-filesystem-l1-1-0.dll | executable | |
MD5:54EB561A8E658C7B457A87FA2646DBCA | SHA256:20BF07800532ACEECE3125D15BDBAD7BB388A0DB0832D0815444F39EFB8067C4 | |||
| 7240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7240.31779\api-ms-win-crt-runtime-l1-1-0.dll | executable | |
MD5:A94A620BBE0C9B533105C9DBCCB43828 | SHA256:F371D80F157A5351D1FB0010800A8AC90658E6CC987D64D4A37A6C5177A1DDB7 | |||
| 7240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7240.31779\api-ms-win-crt-heap-l1-1-0.dll | executable | |
MD5:DFEEF74E654901DB308085607BDD4DB9 | SHA256:3A1A525343C5030D540EDBA2D24A2DD4A19295FC7D8093F72287036B2694ADAD | |||
| 7240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7240.31779\api-ms-win-crt-environment-l1-1-0.dll | executable | |
MD5:5D80170D375794F1F76826F8774BA841 | SHA256:F55D78EFF45CB33083DCC43834AE73636061D169B87A3BE31692FA76312759BF | |||
| 7240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7240.31779\api-ms-win-crt-string-l1-1-0.dll | executable | |
MD5:A259C233A97A660527CC3D4229FA9867 | SHA256:A78B01327BE05F1D190F103E632EE79AA73C7282853A84813C697002A23EA745 | |||
| 7240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7240.31779\VCRUNTIME140.dll | executable | |
MD5:2F997AF9DB67751B77522579667AADEC | SHA256:C34ACBD0D382A1216A7C1A54CB8975964532E8DEBE8D10B236CD0BF219ED8F37 | |||
| 7240 | WinRAR.exe | C:\Users\admin\Desktop\api-ms-win-crt-convert-l1-1-0.dll | executable | |
MD5:5ED40E8A58EA3AFB2CB8F5A750AB6CC4 | SHA256:909CAC9E7856EC110624E71CB92DFEE4D2E220C7B6F5B4F2C90DDE447791BB31 | |||
| 7240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7240.31779\api-ms-win-crt-math-l1-1-0.dll | executable | |
MD5:C2FDC2B0976514559EEE8AB6E6D5864E | SHA256:8177E81EACDB65BD6101878C59060D16EAF273AFE5E1D0D92D1A54B1A7953674 | |||
| 7240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7240.31779\jli.dll | executable | |
MD5:54BC156FE300B4C3384B764835C4DD97 | SHA256:5F694057E20FFBEF2DF5ACD67A4CC8199CBE90131BA5CA75189D7DC42F7125BA | |||
| 7240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7240.31779\aservicesx86bmics.exe | executable | |
MD5:2EF81362606BDE8910406528ED9DCF84 | SHA256:2851C7F2DFD516262C92D0DA5E56E08FD3ABF6D9C2448DE5C497E3B221100190 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
22
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.199:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7916 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7916 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4944 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.199:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7916 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
7916 | SIHClient.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
login.live.com |
| whitelisted |