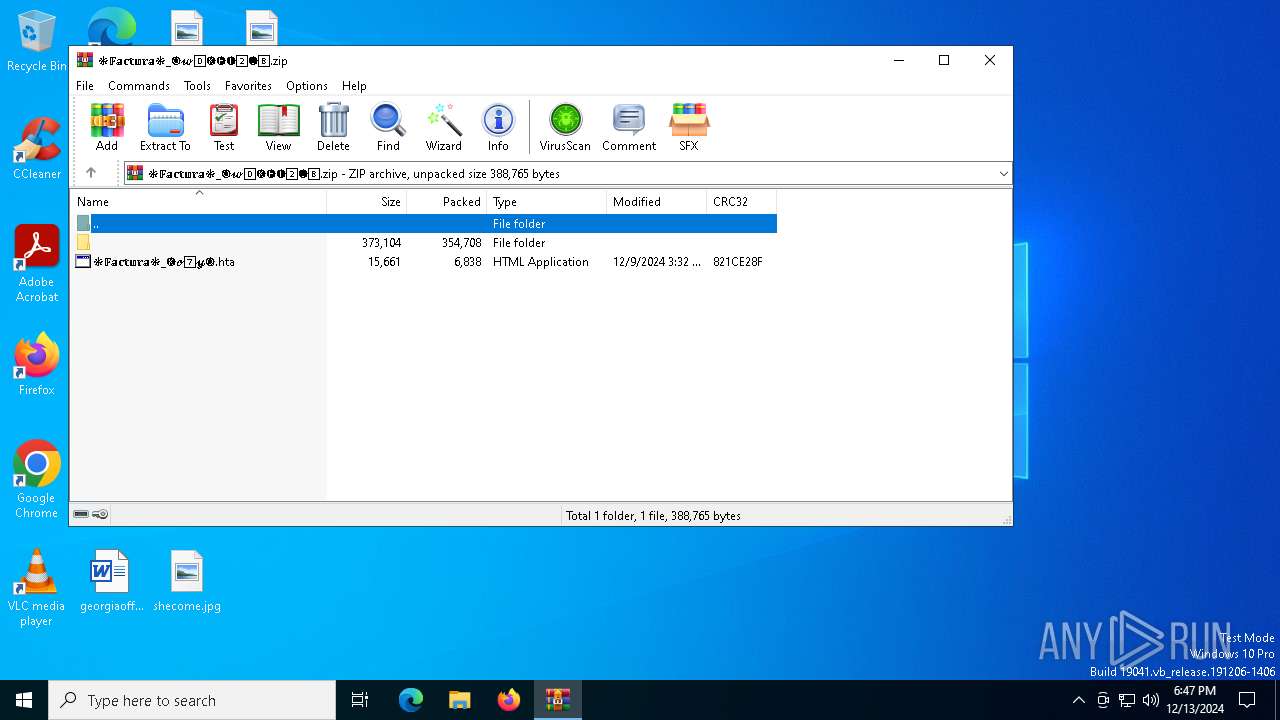
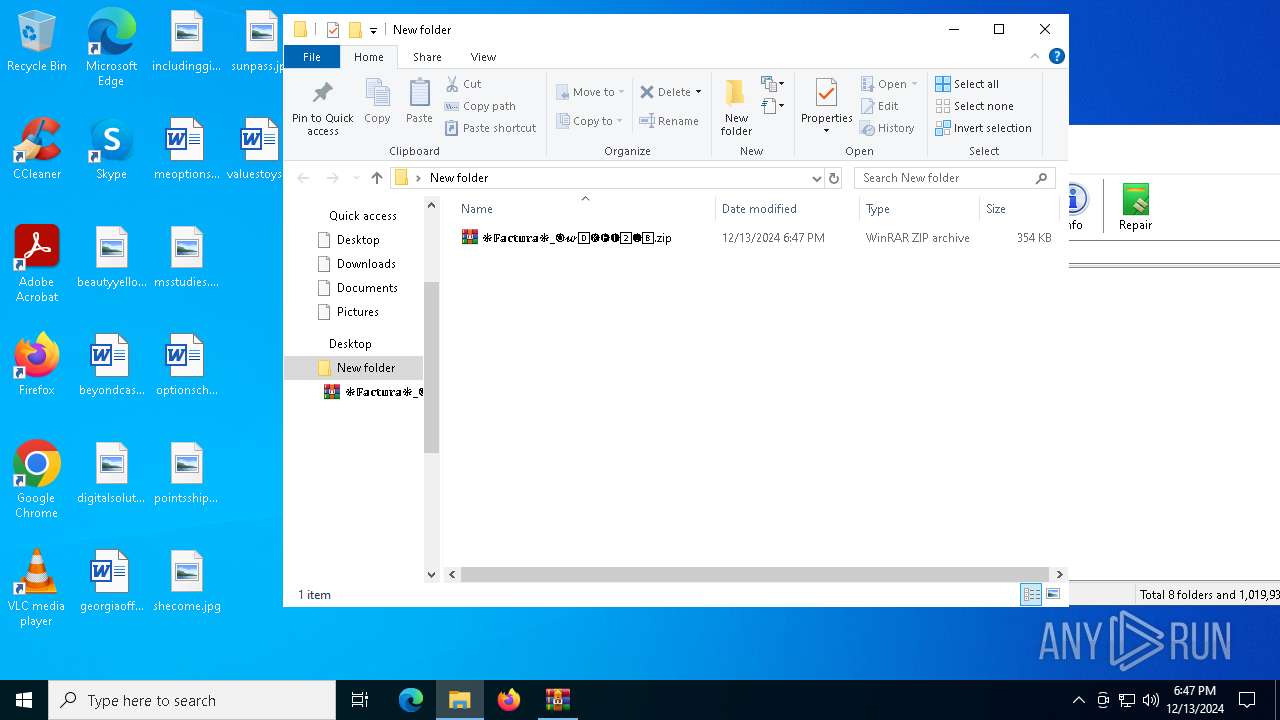
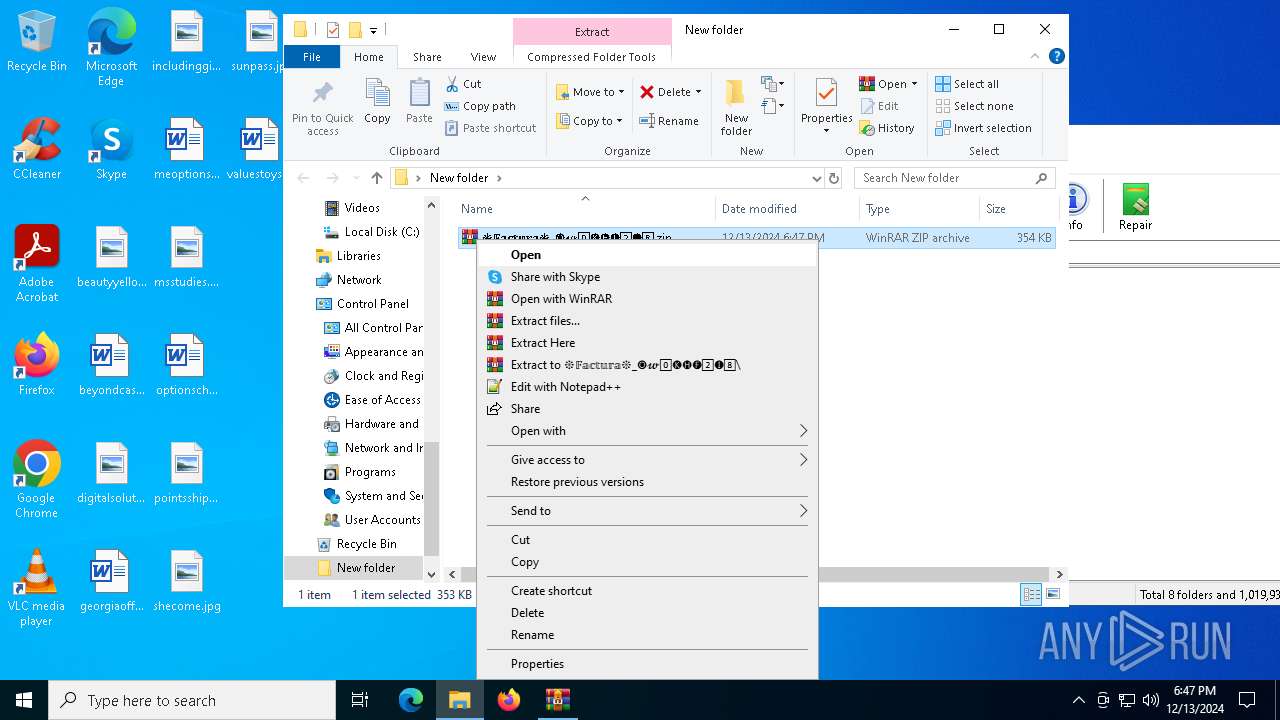
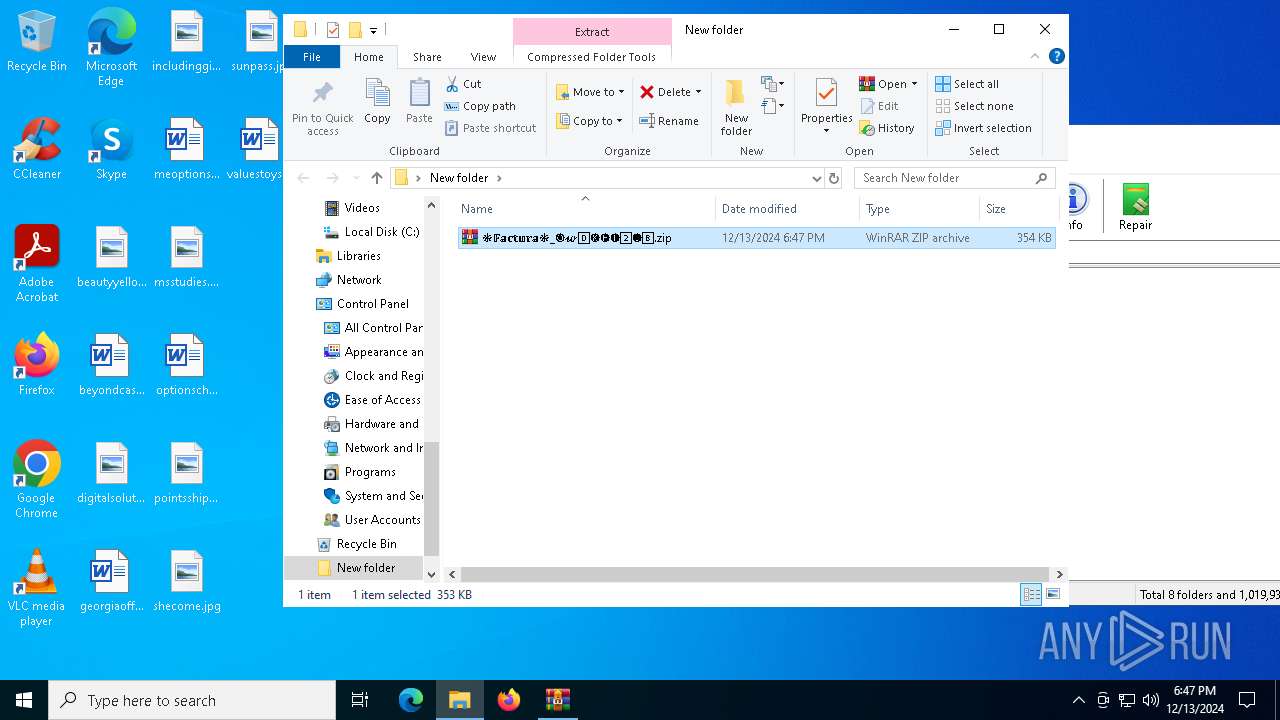
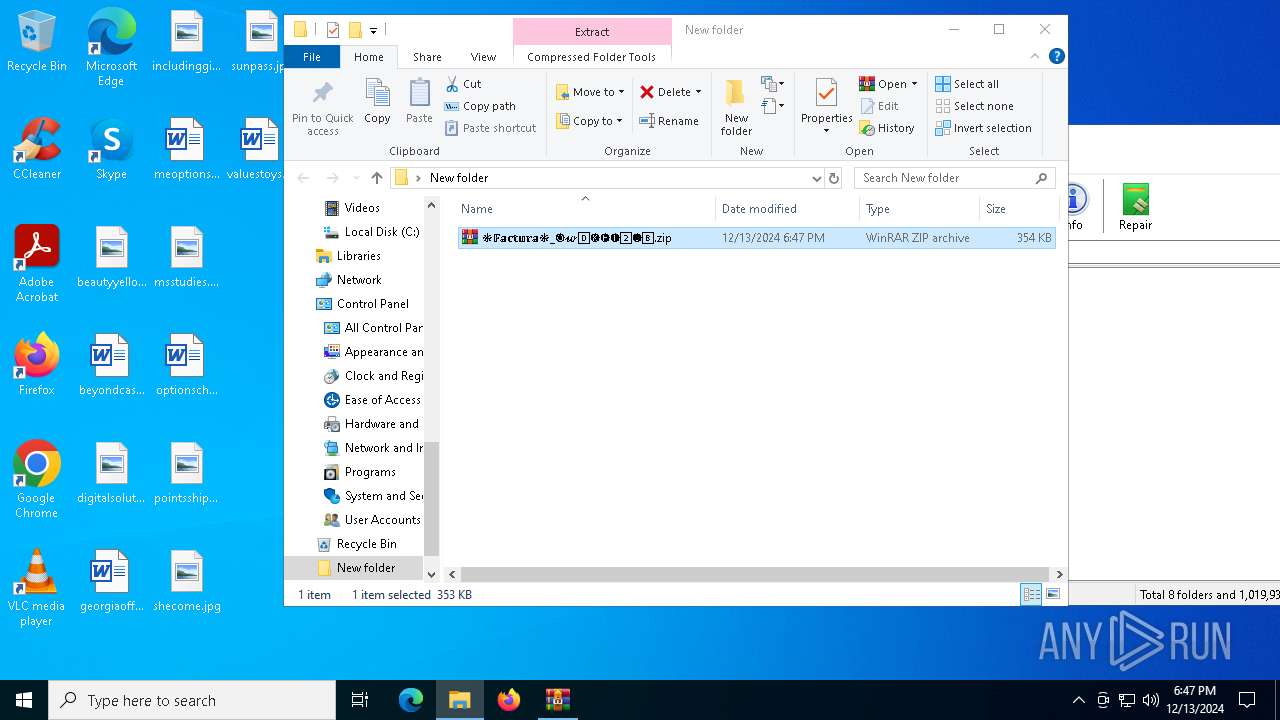
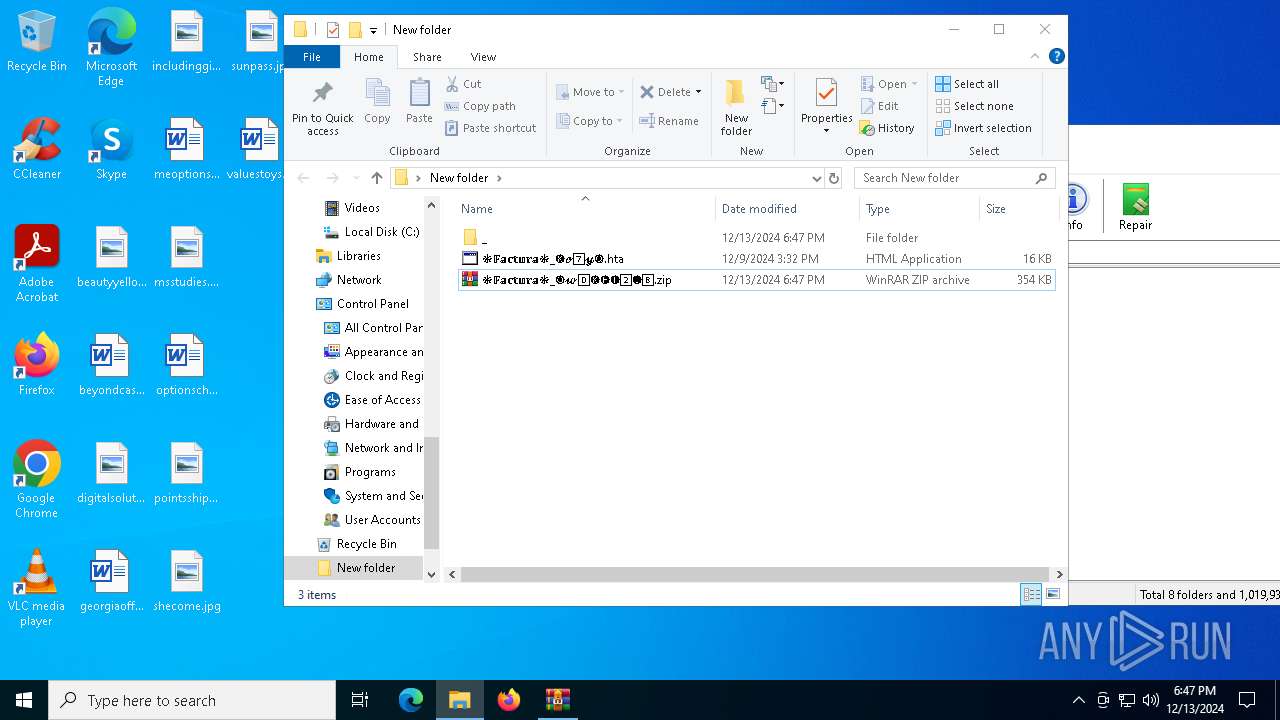
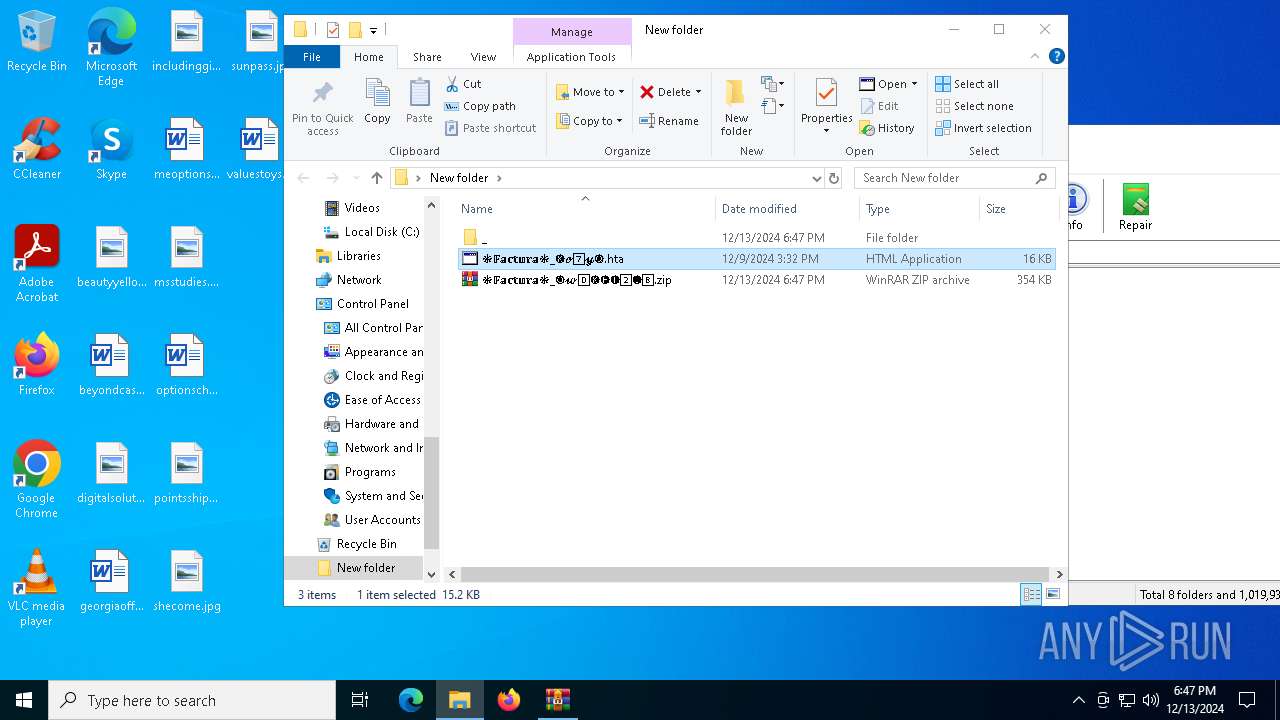
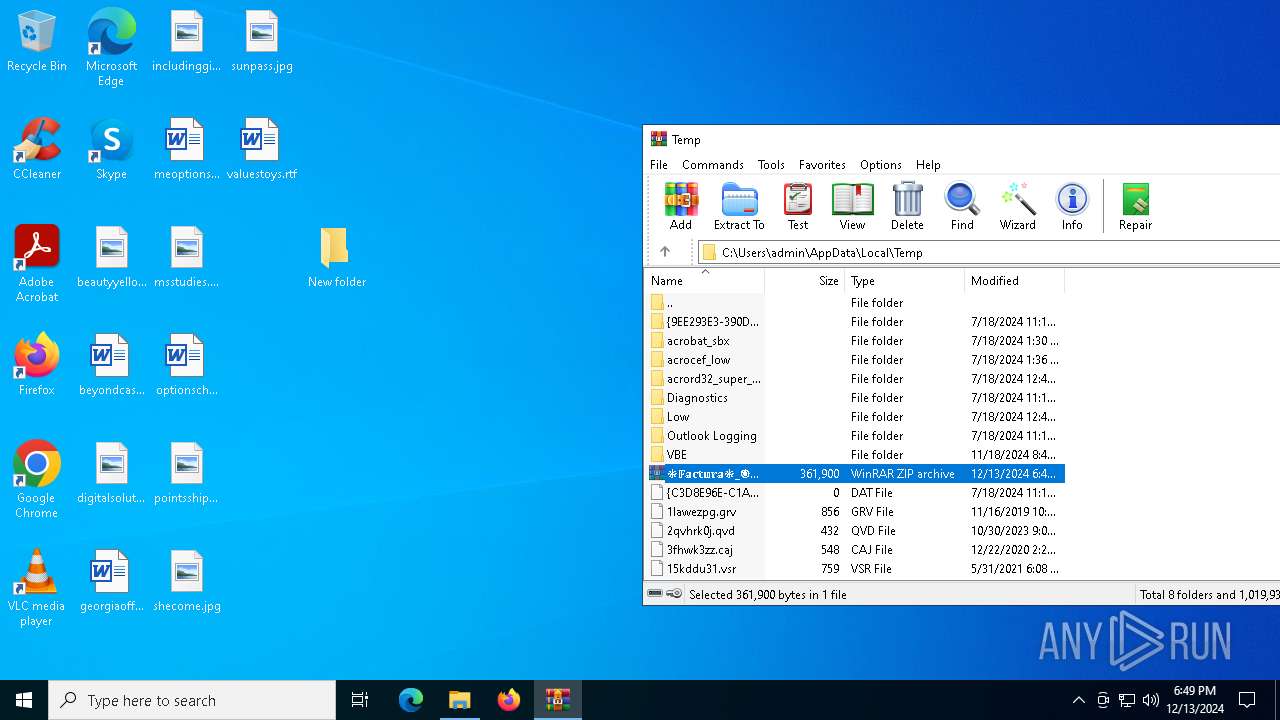
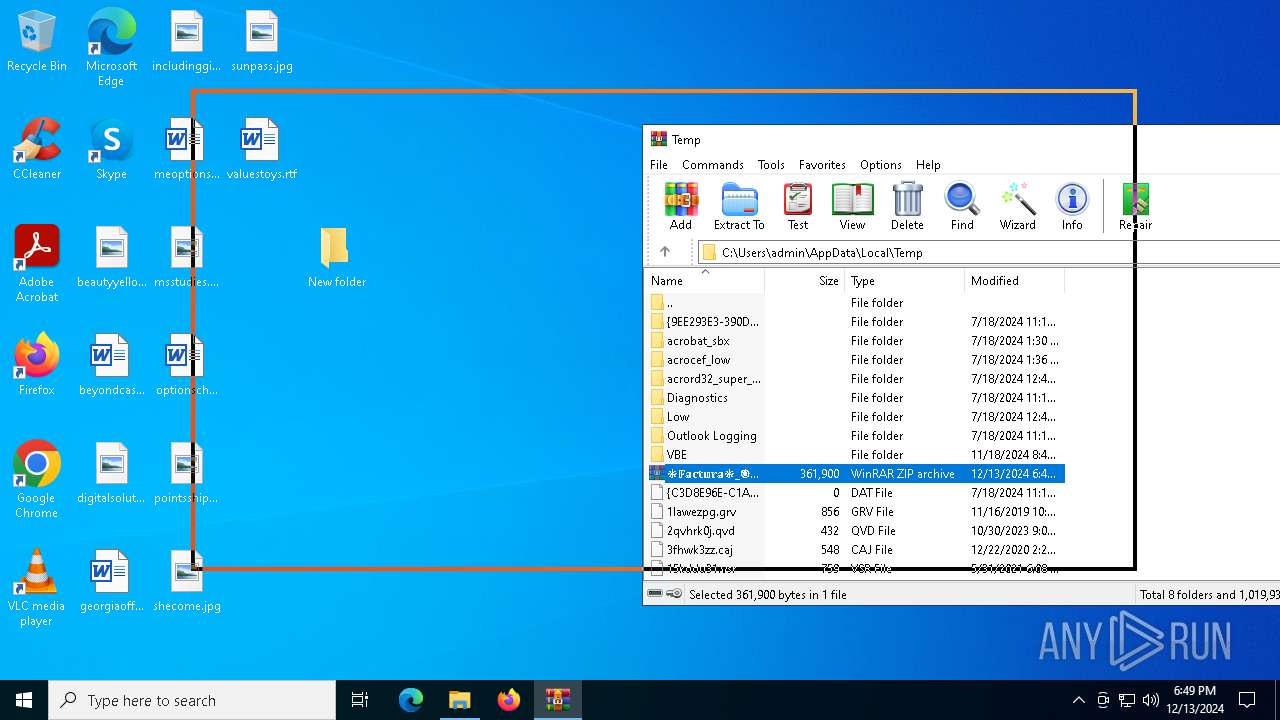
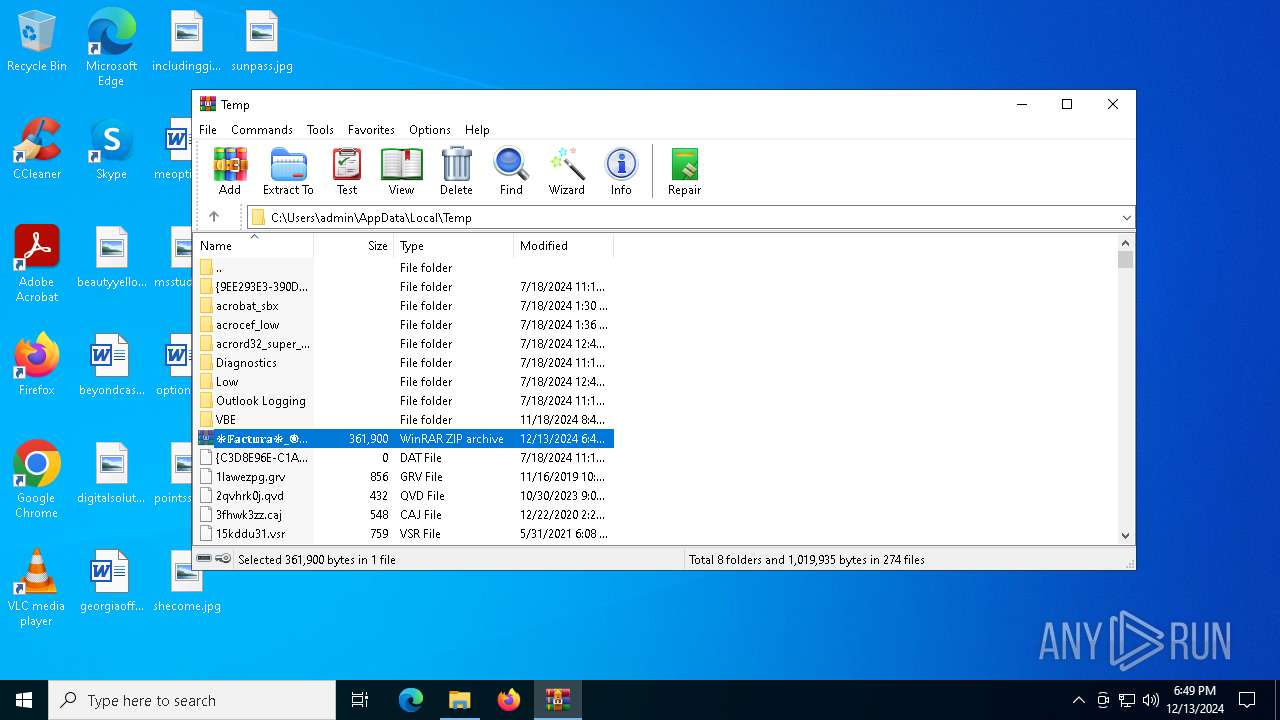
| File name: | ❉𝔽𝕒𝕔𝕥𝕦𝕣𝕒❉_🅞𝔀0⃣🅚🅗🅕2⃣🅘8⃣.zip |
| Full analysis: | https://app.any.run/tasks/534305c6-c8ca-4e8b-8939-cb537f426161 |
| Verdict: | Malicious activity |
| Analysis date: | December 13, 2024, 18:47:00 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 404CAD545DB00D81D04A3A366721632B |
| SHA1: | FB949F241ABEC5E3CB00DA162626221B604DD05D |
| SHA256: | 305A6DF392D0A8F38D156E6C1D5403FD78E6F7ECE57A3AD8CA7171B1ECA8502B |
| SSDEEP: | 12288:lUkgpWgALGPWHC0BbCz0lVYzpjNSeJWD8EmvBFdWdJvr87:ikgpxALGPWHC0BbCzGVajNSeJWD8dvBH |
MALICIOUS
Accesses environment variables (SCRIPT)
- mshta.exe (PID: 4704)
Gets username (SCRIPT)
- mshta.exe (PID: 4704)
Checks whether a specified folder exists (SCRIPT)
- mshta.exe (PID: 4704)
Accesses BIOS(Win32_BIOS, may evade sandboxes) via WMI (SCRIPT)
- mshta.exe (PID: 4704)
SUSPICIOUS
Accesses current user name via WMI (SCRIPT)
- mshta.exe (PID: 4704)
Gets computer name (SCRIPT)
- mshta.exe (PID: 4704)
Accesses computer name via WMI (SCRIPT)
- mshta.exe (PID: 4704)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- mshta.exe (PID: 4704)
Creates FileSystem object to access computer's file system (SCRIPT)
- mshta.exe (PID: 4704)
Accesses OperatingSystem(Win32_OperatingSystem) via WMI (SCRIPT)
- mshta.exe (PID: 4704)
Executes WMI query (SCRIPT)
- mshta.exe (PID: 4704)
Accesses language version of the operating system installed via WMI (SCRIPT)
- mshta.exe (PID: 4704)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 3188)
Manual execution by a user
- WinRAR.exe (PID: 3188)
- mshta.exe (PID: 4704)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3188)
The process uses the downloaded file
- mshta.exe (PID: 4704)
Checks proxy server information
- mshta.exe (PID: 4704)
Reads Internet Explorer settings
- mshta.exe (PID: 4704)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:12:09 15:32:58 |
| ZipCRC: | 0xdcbf5db0 |
| ZipCompressedSize: | 354708 |
| ZipUncompressedSize: | 373104 |
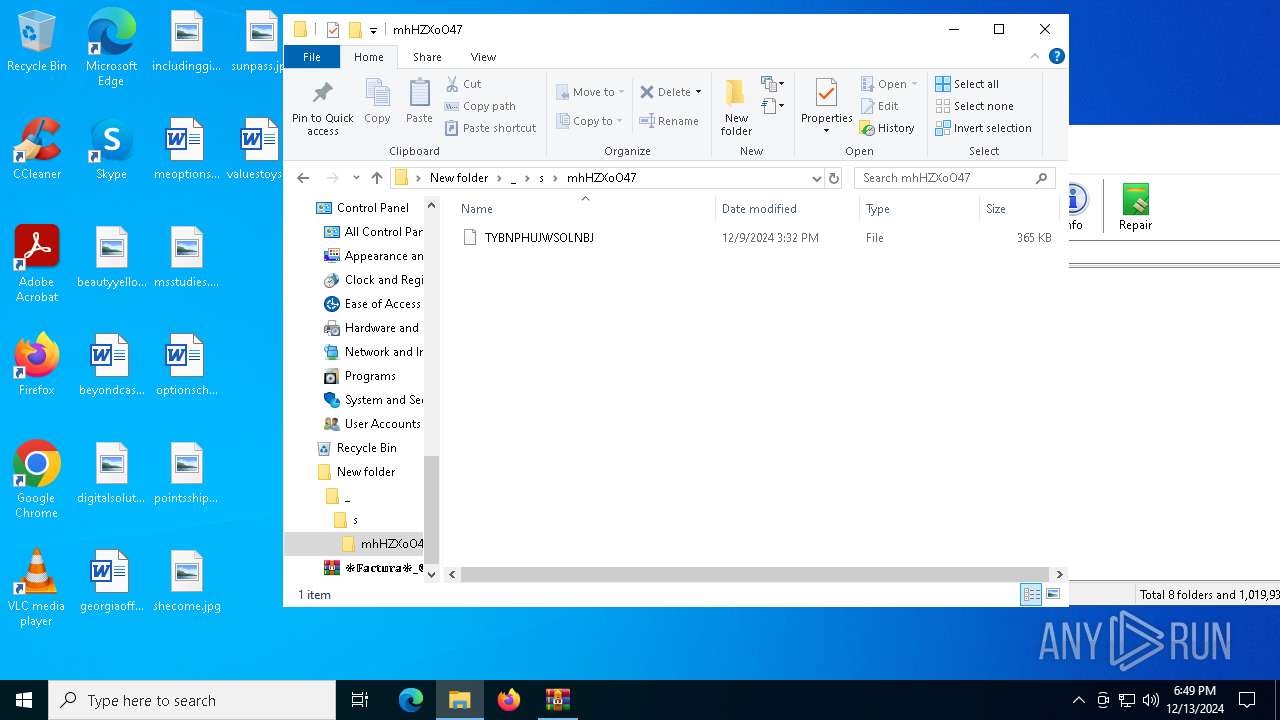
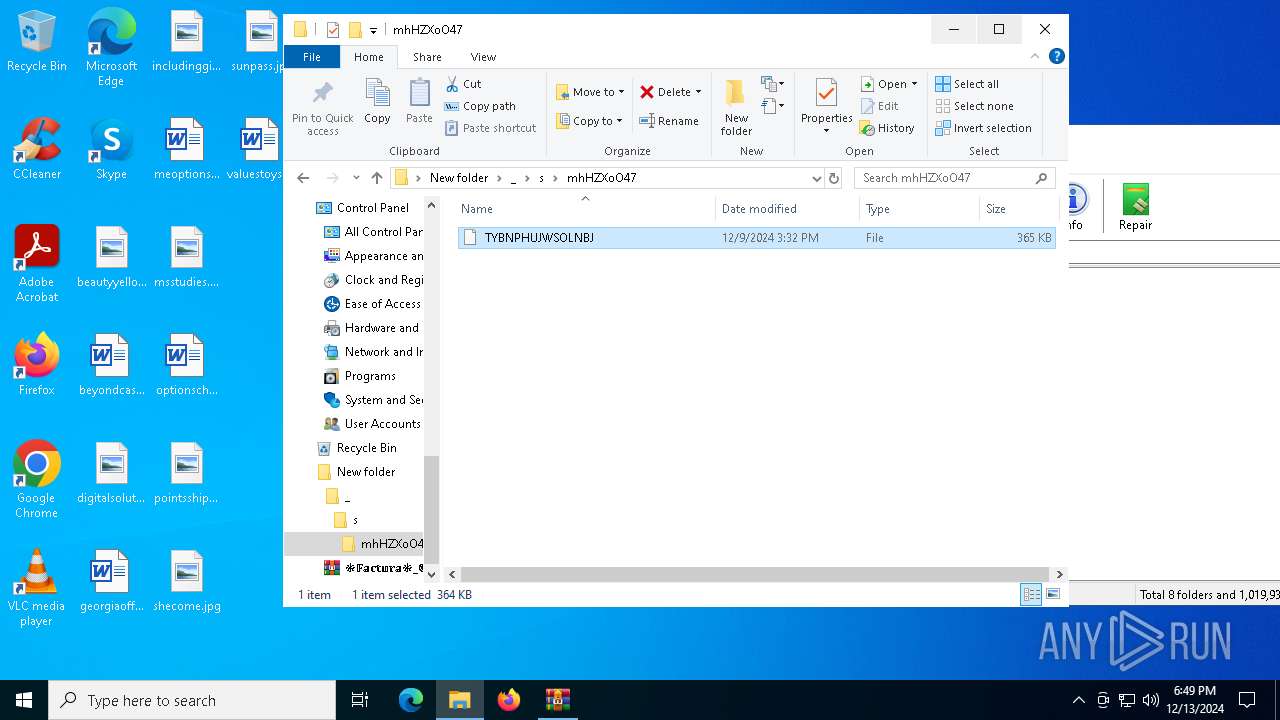
| ZipFileName: | /\s/mhHZXoO47/ TYBNPHUJWSOLNBJ |
Total processes
132
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3188 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\New folder\❉𝔽𝕒𝕔𝕥𝕦𝕣𝕒❉_🅞𝔀0⃣🅚🅗🅕2⃣🅘8⃣.zip" "C:\Users\admin\Desktop\New folder\" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4704 | "C:\Windows\SysWOW64\mshta.exe" "C:\Users\admin\Desktop\New folder\❉𝔽𝕒𝕔𝕥𝕦𝕣𝕒❉_🅚𝓸7⃣𝔂🅠.hta" {1E460BD7-F1C3-4B2E-88BF-4E770A288AF5}{1E460BD7-F1C3-4B2E-88BF-4E770A288AF5} | C:\Windows\SysWOW64\mshta.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5400 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\❉𝔽𝕒𝕔𝕥𝕦𝕣𝕒❉_🅞𝔀0⃣🅚🅗🅕2⃣🅘8⃣.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5728 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 491
Read events
4 469
Write events
22
Delete events
0
Modification events
| (PID) Process: | (5400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
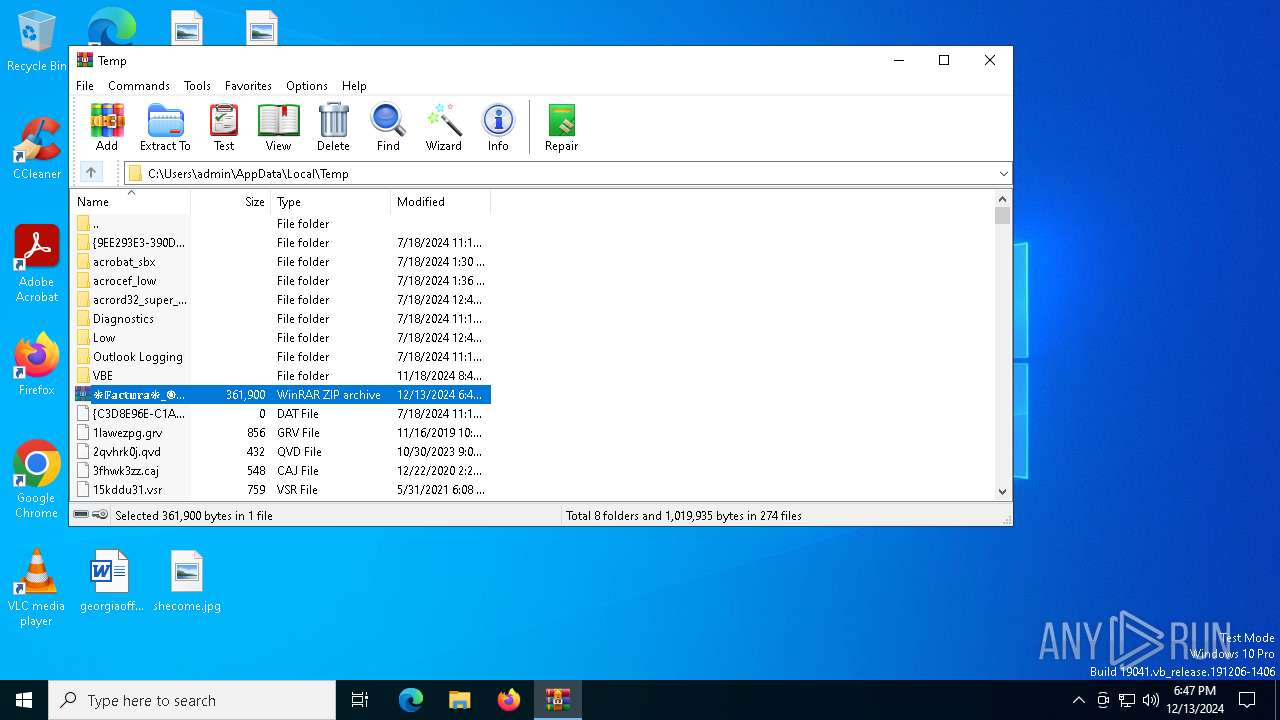
Value: C:\Users\admin\AppData\Local\Temp\❉𝔽𝕒𝕔𝕥𝕦𝕣𝕒❉_🅞𝔀0⃣🅚🅗🅕2⃣🅘8⃣.zip | |||
| (PID) Process: | (5400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (5400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
1
Suspicious files
5
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4704 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:3DFCA46E00FFA4795C72A41375F159D3 | SHA256:DCBA1A505396539BAC40A7253C9F5DCCF06CBB79957E21D56305E1FC3AF5F40E | |||
| 4704 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\3F31858D3C5AF811791DCCEE0B3F72C8 | binary | |
MD5:5F9819D6B7D509CFD871B384F44195DE | SHA256:284B9E42CA25BE9AA795EDEFD2F2FB18CEE6BDD8823F5277D763EE8A0D2F995A | |||
| 4704 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\3F31858D3C5AF811791DCCEE0B3F72C8 | binary | |
MD5:DCC6F5F7436C678558C267E21252A0A2 | SHA256:8E558989718374BD385AE9CB61A83B18A2C0D3E35F9D2C3EBBC4E5F730C910F9 | |||
| 4704 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\dTA7xo[1].js | text | |
MD5:9060E4D6ACECA93BE3054FD62EA4D074 | SHA256:146AC20BA24CA23414F52DCAB0E9D47B49D07FD0DA9C9169B16FA250728A8BF1 | |||
| 4704 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\75CA58072B9926F763A91F0CC2798706_056B48C93C4964C2E64C0A8958238656 | binary | |
MD5:C67AE7CC9E13EC57562B9A564D4983DA | SHA256:5C1AEED75865AC443B6920D853898D0C0DBCBAEE8CB7D03026153080FD034EF4 | |||
| 4704 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\cid[1].htm | xml | |
MD5:53F473D90FE95FA3F915B0D8551E5B14 | SHA256:DF72B1CDA478564FA0073E54628B070777F5DF2B0500C3A89B74F423760110DB | |||
| 3188 | WinRAR.exe | C:\Users\admin\Desktop\New folder\_\s\mhHZXoO47\ TYBNPHUJWSOLNBJ | executable | |
MD5:B28B54B38F5CD12BDB8139006CF4E840 | SHA256:764D6E3DDB8A9D9AFE701E05FFE5A3E5F807A069FC1EEB4EE8B164A0A211CFC3 | |||
| 3188 | WinRAR.exe | C:\Users\admin\Desktop\New folder\❉𝔽𝕒𝕔𝕥𝕦𝕣𝕒❉_🅚𝓸7⃣𝔂🅠.hta | html | |
MD5:6EF7AA1D4381566AEBBC86B3DFCA11DD | SHA256:51E7D9FB5AE11E68CF8F370A10C38E75E4C3AB4DBAB86AF880BA9075E5BA73E3 | |||
| 4704 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\75CA58072B9926F763A91F0CC2798706_056B48C93C4964C2E64C0A8958238656 | binary | |
MD5:35B50FBE6A802F397699A202F8B3432C | SHA256:38C3CD36D21E7BD0BD5EAC76F2ED93CA4308DA7E8DD16AEE74E627DFDA82893F | |||
| 4704 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\cid[1].htm | html | |
MD5:081C39B2C1F82509F248495BDD15EFC6 | SHA256:7A42EBE680C1D203FEB1DD1192BCCA3FB4A4A764AF0548727003B1A64F07D31D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
38
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7112 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6260 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2892 | svchost.exe | GET | 200 | 2.23.197.184:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
4704 | mshta.exe | GET | 200 | 18.66.145.213:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkpLy9ROx7U76vGUhC06D6E%3D | unknown | — | — | unknown |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7112 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4704 | mshta.exe | GET | 200 | 184.24.77.79:80 | http://r11.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBQaUrm0WeTDM5ghfoZtS72KO9ZnzgQUCLkRO6XQhRi06g%2BgrZ%2BGHo78OCcCEgPieppUddNlEt5PgIEXQIXD4w%3D%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3560 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 104.126.37.128:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |