| File name: | 0bc68db77e687fa52b2f367994c5bc6f.exe |
| Full analysis: | https://app.any.run/tasks/ce7937fd-de16-4bd8-9e64-eb212aad8bfa |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | December 14, 2024, 02:51:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 0BC68DB77E687FA52B2F367994C5BC6F |
| SHA1: | ECF69C28AA53920F6279AD29D5BC9BB02542E841 |
| SHA256: | 3055D261F05A0656B1B92D9FA8ED3A72111A3A5C6D036D13D3D3A304CA99B987 |
| SSDEEP: | 98304:ZFrKdQD56mtoFgfhJiJ5zPHY+Pewr+XMg27aQ4Y27ieBxu++LAYj6gNIKe3y7kls:ZudcpA |
MALICIOUS
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 6548)
- wscript.exe (PID: 420)
- wscript.exe (PID: 4596)
- wscript.exe (PID: 7032)
- wscript.exe (PID: 2324)
- wscript.exe (PID: 5876)
- wscript.exe (PID: 6336)
- wscript.exe (PID: 4944)
- wscript.exe (PID: 6536)
- wscript.exe (PID: 6872)
- wscript.exe (PID: 3040)
- wscript.exe (PID: 3524)
- wscript.exe (PID: 3540)
- wscript.exe (PID: 1864)
- wscript.exe (PID: 6608)
- wscript.exe (PID: 6436)
- wscript.exe (PID: 4872)
- wscript.exe (PID: 3724)
- wscript.exe (PID: 6960)
- wscript.exe (PID: 1616)
- wscript.exe (PID: 736)
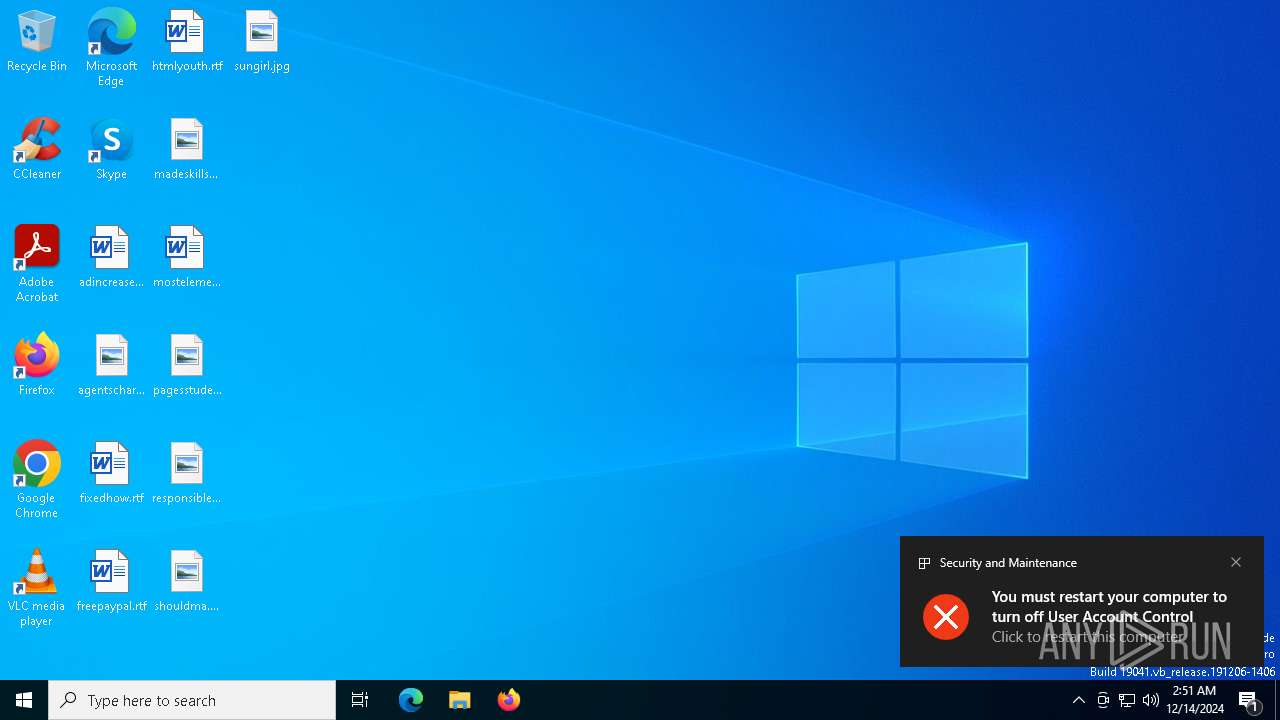
UAC/LUA settings modification
- SavesintoHost.exe (PID: 7156)
- dllhost.exe (PID: 5316)
- dllhost.exe (PID: 6540)
- dllhost.exe (PID: 7096)
- dllhost.exe (PID: 2928)
- dllhost.exe (PID: 6784)
- dllhost.exe (PID: 2292)
- dllhost.exe (PID: 5828)
- dllhost.exe (PID: 6520)
- dllhost.exe (PID: 4128)
- dllhost.exe (PID: 6712)
- dllhost.exe (PID: 6480)
Changes the autorun value in the registry
- SavesintoHost.exe (PID: 7156)
Changes the login/logoff helper path in the registry
- SavesintoHost.exe (PID: 7156)
DARKCRYSTAL has been detected (SURICATA)
- dllhost.exe (PID: 5316)
- dllhost.exe (PID: 6540)
- dllhost.exe (PID: 7096)
- dllhost.exe (PID: 2928)
- dllhost.exe (PID: 6784)
- dllhost.exe (PID: 2292)
- dllhost.exe (PID: 5828)
- dllhost.exe (PID: 6520)
- dllhost.exe (PID: 4128)
- dllhost.exe (PID: 6712)
- dllhost.exe (PID: 6480)
Deletes a file (SCRIPT)
- wscript.exe (PID: 420)
- wscript.exe (PID: 7032)
- wscript.exe (PID: 6336)
- wscript.exe (PID: 6536)
- wscript.exe (PID: 6872)
- wscript.exe (PID: 3524)
- wscript.exe (PID: 6608)
- wscript.exe (PID: 4872)
- wscript.exe (PID: 6960)
- wscript.exe (PID: 736)
SUSPICIOUS
Reads security settings of Internet Explorer
- 0bc68db77e687fa52b2f367994c5bc6f.exe (PID: 6468)
- ShellExperienceHost.exe (PID: 1540)
- SavesintoHost.exe (PID: 7156)
- dllhost.exe (PID: 5316)
- dllhost.exe (PID: 6540)
- dllhost.exe (PID: 7096)
- dllhost.exe (PID: 2928)
- dllhost.exe (PID: 6784)
- dllhost.exe (PID: 2292)
- dllhost.exe (PID: 5828)
- dllhost.exe (PID: 6520)
- dllhost.exe (PID: 4128)
- dllhost.exe (PID: 6712)
- dllhost.exe (PID: 6480)
Executable content was dropped or overwritten
- 0bc68db77e687fa52b2f367994c5bc6f.exe (PID: 6468)
- SavesintoHost.exe (PID: 7156)
- dllhost.exe (PID: 5316)
The process creates files with name similar to system file names
- 0bc68db77e687fa52b2f367994c5bc6f.exe (PID: 6468)
- SavesintoHost.exe (PID: 7156)
The process executes VB scripts
- 0bc68db77e687fa52b2f367994c5bc6f.exe (PID: 6468)
- dllhost.exe (PID: 5316)
- dllhost.exe (PID: 6540)
- dllhost.exe (PID: 7096)
- dllhost.exe (PID: 2928)
- dllhost.exe (PID: 6784)
- dllhost.exe (PID: 2292)
- dllhost.exe (PID: 5828)
- dllhost.exe (PID: 6520)
- dllhost.exe (PID: 4128)
- dllhost.exe (PID: 6712)
- dllhost.exe (PID: 6480)
Executing commands from a ".bat" file
- wscript.exe (PID: 6548)
- SavesintoHost.exe (PID: 7156)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 6548)
- SavesintoHost.exe (PID: 7156)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6548)
- wscript.exe (PID: 420)
- wscript.exe (PID: 7032)
- wscript.exe (PID: 6336)
- wscript.exe (PID: 6536)
- wscript.exe (PID: 6872)
- wscript.exe (PID: 3524)
- wscript.exe (PID: 6608)
- wscript.exe (PID: 4872)
- wscript.exe (PID: 6960)
- wscript.exe (PID: 736)
Executed via WMI
- schtasks.exe (PID: 3060)
- schtasks.exe (PID: 5592)
- schtasks.exe (PID: 3876)
- schtasks.exe (PID: 3544)
- schtasks.exe (PID: 4136)
- schtasks.exe (PID: 5588)
- schtasks.exe (PID: 3552)
- schtasks.exe (PID: 4604)
- schtasks.exe (PID: 4052)
- schtasks.exe (PID: 5748)
- schtasks.exe (PID: 6516)
- schtasks.exe (PID: 6496)
- schtasks.exe (PID: 1380)
- schtasks.exe (PID: 6460)
- schtasks.exe (PID: 6632)
- schtasks.exe (PID: 6720)
- schtasks.exe (PID: 644)
- schtasks.exe (PID: 1792)
- schtasks.exe (PID: 4428)
- schtasks.exe (PID: 6768)
- schtasks.exe (PID: 7016)
- schtasks.exe (PID: 7004)
- schtasks.exe (PID: 7048)
- schtasks.exe (PID: 6872)
- schtasks.exe (PID: 6868)
- schtasks.exe (PID: 1356)
- schtasks.exe (PID: 2008)
- schtasks.exe (PID: 6608)
- schtasks.exe (PID: 6564)
- schtasks.exe (PID: 6336)
- schtasks.exe (PID: 3288)
- schtasks.exe (PID: 3144)
- schtasks.exe (PID: 3060)
- schtasks.exe (PID: 2928)
- schtasks.exe (PID: 4136)
- schtasks.exe (PID: 6516)
- schtasks.exe (PID: 4740)
- schtasks.exe (PID: 932)
- schtasks.exe (PID: 6520)
- schtasks.exe (PID: 6296)
- schtasks.exe (PID: 6540)
- schtasks.exe (PID: 6460)
- schtasks.exe (PID: 2736)
- schtasks.exe (PID: 3612)
- schtasks.exe (PID: 628)
- schtasks.exe (PID: 644)
- schtasks.exe (PID: 4428)
- schtasks.exe (PID: 448)
- schtasks.exe (PID: 6784)
- schtasks.exe (PID: 7016)
- schtasks.exe (PID: 7012)
Reads the date of Windows installation
- SavesintoHost.exe (PID: 7156)
- dllhost.exe (PID: 5316)
- dllhost.exe (PID: 6540)
- dllhost.exe (PID: 7096)
- dllhost.exe (PID: 2928)
- dllhost.exe (PID: 6784)
- dllhost.exe (PID: 2292)
- dllhost.exe (PID: 5828)
- dllhost.exe (PID: 6520)
- dllhost.exe (PID: 4128)
- dllhost.exe (PID: 6712)
- dllhost.exe (PID: 6480)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 6908)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 4596)
- wscript.exe (PID: 420)
- wscript.exe (PID: 7032)
- wscript.exe (PID: 2324)
- wscript.exe (PID: 5876)
- wscript.exe (PID: 6336)
- wscript.exe (PID: 6536)
- wscript.exe (PID: 4944)
- wscript.exe (PID: 6872)
- wscript.exe (PID: 3040)
- wscript.exe (PID: 3540)
- wscript.exe (PID: 3524)
- wscript.exe (PID: 6608)
- wscript.exe (PID: 1864)
- wscript.exe (PID: 4872)
- wscript.exe (PID: 6436)
- wscript.exe (PID: 6960)
- wscript.exe (PID: 3724)
- wscript.exe (PID: 1616)
- wscript.exe (PID: 736)
- wscript.exe (PID: 6584)
- wscript.exe (PID: 6980)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- wscript.exe (PID: 420)
- wscript.exe (PID: 7032)
- wscript.exe (PID: 6336)
- wscript.exe (PID: 6536)
- wscript.exe (PID: 6872)
- wscript.exe (PID: 3524)
- wscript.exe (PID: 6608)
- wscript.exe (PID: 4872)
- wscript.exe (PID: 6960)
- wscript.exe (PID: 736)
- wscript.exe (PID: 6980)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 420)
- wscript.exe (PID: 7032)
- wscript.exe (PID: 6336)
- wscript.exe (PID: 6536)
- wscript.exe (PID: 6872)
- wscript.exe (PID: 3524)
- wscript.exe (PID: 6608)
- wscript.exe (PID: 4872)
- wscript.exe (PID: 6960)
- wscript.exe (PID: 736)
INFO
Reads the computer name
- 0bc68db77e687fa52b2f367994c5bc6f.exe (PID: 6468)
- SavesintoHost.exe (PID: 7156)
- ShellExperienceHost.exe (PID: 1540)
- dllhost.exe (PID: 5316)
- dllhost.exe (PID: 6540)
- dllhost.exe (PID: 7096)
- dllhost.exe (PID: 2928)
- dllhost.exe (PID: 6784)
- dllhost.exe (PID: 2292)
- dllhost.exe (PID: 5828)
- dllhost.exe (PID: 6520)
- dllhost.exe (PID: 4128)
- dllhost.exe (PID: 6712)
- dllhost.exe (PID: 6480)
Checks supported languages
- 0bc68db77e687fa52b2f367994c5bc6f.exe (PID: 6468)
- SavesintoHost.exe (PID: 7156)
- ShellExperienceHost.exe (PID: 1540)
- dllhost.exe (PID: 5316)
- dllhost.exe (PID: 6540)
- dllhost.exe (PID: 7096)
- dllhost.exe (PID: 2928)
- dllhost.exe (PID: 6784)
- dllhost.exe (PID: 2292)
- dllhost.exe (PID: 5828)
- dllhost.exe (PID: 6520)
- dllhost.exe (PID: 4128)
- dllhost.exe (PID: 6712)
- dllhost.exe (PID: 6480)
The process uses the downloaded file
- 0bc68db77e687fa52b2f367994c5bc6f.exe (PID: 6468)
- wscript.exe (PID: 6548)
- SavesintoHost.exe (PID: 7156)
- dllhost.exe (PID: 5316)
- dllhost.exe (PID: 6540)
- dllhost.exe (PID: 7096)
- dllhost.exe (PID: 2928)
- dllhost.exe (PID: 6784)
- dllhost.exe (PID: 2292)
- dllhost.exe (PID: 5828)
- dllhost.exe (PID: 6520)
- dllhost.exe (PID: 4128)
- dllhost.exe (PID: 6712)
- dllhost.exe (PID: 6480)
Process checks computer location settings
- 0bc68db77e687fa52b2f367994c5bc6f.exe (PID: 6468)
- SavesintoHost.exe (PID: 7156)
- dllhost.exe (PID: 5316)
- dllhost.exe (PID: 6540)
- dllhost.exe (PID: 7096)
- dllhost.exe (PID: 2928)
- dllhost.exe (PID: 6784)
- dllhost.exe (PID: 2292)
- dllhost.exe (PID: 5828)
- dllhost.exe (PID: 6520)
- dllhost.exe (PID: 4128)
- dllhost.exe (PID: 6712)
- dllhost.exe (PID: 6480)
The sample compiled with english language support
- 0bc68db77e687fa52b2f367994c5bc6f.exe (PID: 6468)
- SavesintoHost.exe (PID: 7156)
- dllhost.exe (PID: 5316)
Drops encrypted VBS script (Microsoft Script Encoder)
- 0bc68db77e687fa52b2f367994c5bc6f.exe (PID: 6468)
- wscript.exe (PID: 6548)
Reads Environment values
- SavesintoHost.exe (PID: 7156)
- dllhost.exe (PID: 5316)
- dllhost.exe (PID: 6540)
- dllhost.exe (PID: 7096)
- dllhost.exe (PID: 2928)
- dllhost.exe (PID: 6784)
- dllhost.exe (PID: 2292)
- dllhost.exe (PID: 5828)
- dllhost.exe (PID: 6520)
- dllhost.exe (PID: 4128)
- dllhost.exe (PID: 6712)
- dllhost.exe (PID: 6480)
Reads the machine GUID from the registry
- SavesintoHost.exe (PID: 7156)
- dllhost.exe (PID: 5316)
- dllhost.exe (PID: 6540)
- dllhost.exe (PID: 7096)
- dllhost.exe (PID: 2928)
- dllhost.exe (PID: 6784)
- dllhost.exe (PID: 2292)
- dllhost.exe (PID: 5828)
- dllhost.exe (PID: 6520)
- dllhost.exe (PID: 4128)
- dllhost.exe (PID: 6712)
- dllhost.exe (PID: 6480)
Process checks whether UAC notifications are on
- SavesintoHost.exe (PID: 7156)
- dllhost.exe (PID: 5316)
- dllhost.exe (PID: 6540)
- dllhost.exe (PID: 7096)
- dllhost.exe (PID: 2928)
- dllhost.exe (PID: 6784)
- dllhost.exe (PID: 2292)
- dllhost.exe (PID: 5828)
- dllhost.exe (PID: 6520)
- dllhost.exe (PID: 4128)
- dllhost.exe (PID: 6712)
- dllhost.exe (PID: 6480)
Creates files in the program directory
- SavesintoHost.exe (PID: 7156)
Create files in a temporary directory
- SavesintoHost.exe (PID: 7156)
- dllhost.exe (PID: 5316)
- dllhost.exe (PID: 6540)
- dllhost.exe (PID: 7096)
- dllhost.exe (PID: 2928)
- dllhost.exe (PID: 6784)
- dllhost.exe (PID: 2292)
- dllhost.exe (PID: 5828)
- dllhost.exe (PID: 6520)
- dllhost.exe (PID: 4128)
- dllhost.exe (PID: 6712)
- dllhost.exe (PID: 6480)
Reads Microsoft Office registry keys
- dllhost.exe (PID: 5316)
- dllhost.exe (PID: 6540)
- dllhost.exe (PID: 7096)
- dllhost.exe (PID: 2928)
- dllhost.exe (PID: 6784)
- dllhost.exe (PID: 2292)
- dllhost.exe (PID: 5828)
- dllhost.exe (PID: 6520)
- dllhost.exe (PID: 4128)
- dllhost.exe (PID: 6712)
- dllhost.exe (PID: 6480)
Disables trace logs
- dllhost.exe (PID: 5316)
- dllhost.exe (PID: 6540)
- dllhost.exe (PID: 7096)
- dllhost.exe (PID: 2928)
- dllhost.exe (PID: 6784)
- dllhost.exe (PID: 2292)
- dllhost.exe (PID: 5828)
- dllhost.exe (PID: 6520)
- dllhost.exe (PID: 4128)
- dllhost.exe (PID: 6712)
- dllhost.exe (PID: 6480)
Checks proxy server information
- dllhost.exe (PID: 5316)
- dllhost.exe (PID: 6540)
- dllhost.exe (PID: 7096)
- dllhost.exe (PID: 2928)
- dllhost.exe (PID: 6784)
- dllhost.exe (PID: 2292)
- dllhost.exe (PID: 5828)
- dllhost.exe (PID: 6520)
- dllhost.exe (PID: 4128)
- dllhost.exe (PID: 6712)
- dllhost.exe (PID: 6480)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:12:01 18:00:55+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 201216 |
| InitializedDataSize: | 114176 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1ec40 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
223
Monitored processes
95
Malicious processes
33
Suspicious processes
11
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 420 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\8823b91d-a66f-43a2-aab7-c619bd39c5e1.vbs" | C:\Windows\System32\wscript.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 448 | schtasks.exe /create /tn "IdleI" /sc MINUTE /mo 14 /tr "'C:\Recovery\OEM\Idle.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 628 | schtasks.exe /create /tn "servicess" /sc MINUTE /mo 9 /tr "'C:\Program Files (x86)\MSBuild\Microsoft\Windows Workflow Foundation\v3.0\services.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | schtasks.exe /create /tn "taskhostw" /sc ONLOGON /tr "'C:\found.000\dir_00000002.chk\taskhostw.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | schtasks.exe /create /tn "services" /sc ONLOGON /tr "'C:\Program Files (x86)\MSBuild\Microsoft\Windows Workflow Foundation\v3.0\services.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\641b3dba-b3f3-4870-b453-55de42ecf109.vbs" | C:\Windows\System32\wscript.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 932 | schtasks.exe /create /tn "smss" /sc ONLOGON /tr "'C:\Recovery\Logs\smss.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1356 | schtasks.exe /create /tn "spoolsv" /sc ONLOGON /tr "'C:\Windows\assembly\NativeImages_v2.0.50727_32\Temp\spoolsv.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1380 | schtasks.exe /create /tn "spoolsvs" /sc MINUTE /mo 10 /tr "'C:\Windows\assembly\NativeImages_v2.0.50727_32\Temp\spoolsv.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1540 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
40 510
Read events
40 367
Write events
143
Delete events
0
Modification events
| (PID) Process: | (6468) 0bc68db77e687fa52b2f367994c5bc6f.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbe\OpenWithProgids |
| Operation: | write | Name: | VBEFile |
Value: | |||
| (PID) Process: | (6468) 0bc68db77e687fa52b2f367994c5bc6f.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
| (PID) Process: | (7156) SavesintoHost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (7156) SavesintoHost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | ConsentPromptBehaviorAdmin |
Value: 0 | |||
| (PID) Process: | (7156) SavesintoHost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | PromptOnSecureDesktop |
Value: 0 | |||
| (PID) Process: | (7156) SavesintoHost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 23004100430042006C006F00620000000000000000000000010000000000000000000000 | |||
| (PID) Process: | (1540) ShellExperienceHost.exe | Key: | \REGISTRY\A\{4cccb9b0-08b6-891c-a396-62996fda4f69}\LocalState |
| Operation: | write | Name: | PeekBadges |
Value: 5B005D000000B4C6ED20D34DDB01 | |||
| (PID) Process: | (1540) ShellExperienceHost.exe | Key: | \REGISTRY\A\{4cccb9b0-08b6-891c-a396-62996fda4f69}\LocalState |
| Operation: | write | Name: | PeekBadges |
Value: 5B005D000000562AF020D34DDB01 | |||
| (PID) Process: | (7156) SavesintoHost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | taskhostw |
Value: "C:\found.000\dir_00000002.chk\taskhostw.exe" | |||
| (PID) Process: | (7156) SavesintoHost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | taskhostw |
Value: "C:\found.000\dir_00000002.chk\taskhostw.exe" | |||
Executable files
19
Suspicious files
1
Text files
43
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6468 | 0bc68db77e687fa52b2f367994c5bc6f.exe | C:\comSurrogatecontainercomponentRef\4Vp3r4P.vbe | binary | |
MD5:5D646684DEBBC53C0C7EC5FA65F23216 | SHA256:CDDD4A030F867ACB39A0E7697732CBD57BB2E5E9F0D81FC1E7D752D57C1EE195 | |||
| 6468 | 0bc68db77e687fa52b2f367994c5bc6f.exe | C:\comSurrogatecontainercomponentRef\QZY1IZ9a6YLs5.bat | text | |
MD5:CBBA91293FED3DFB5A3A0CD0EC53B505 | SHA256:062CFF19B7BE8C7D9C9941F75B9225982EB3799A766EE73659251F7D0C0B299D | |||
| 7156 | SavesintoHost.exe | C:\Users\Administrator\Searches\105eec298f1910 | text | |
MD5:217119E3A1D8A722AF7DEF05A433814A | SHA256:33CE25F3CACA5289C95C5282B943B92EF0C0AA997705705FA1B659B7A9D5EA19 | |||
| 6468 | 0bc68db77e687fa52b2f367994c5bc6f.exe | C:\comSurrogatecontainercomponentRef\SavesintoHost.exe | executable | |
MD5:3AA1BBD17D68B0B67B7423F1FE09B05B | SHA256:7362F82084BCDF47B0927674AD678F66214E8D4F2783A0B9338EE4EB773C3474 | |||
| 7156 | SavesintoHost.exe | C:\Users\Default\088424020bedd6 | text | |
MD5:D2E3D477A2A1761216F341C2D4225CD5 | SHA256:E97544A91C09C41A502002F1F262863AEE2F95D10B60FBB56F6855A1AE6A1B4A | |||
| 7156 | SavesintoHost.exe | C:\found.000\dir_00000002.chk\TextInputHost.exe | executable | |
MD5:3AA1BBD17D68B0B67B7423F1FE09B05B | SHA256:7362F82084BCDF47B0927674AD678F66214E8D4F2783A0B9338EE4EB773C3474 | |||
| 7156 | SavesintoHost.exe | C:\Users\Administrator\Searches\uhssvc.exe | executable | |
MD5:3AA1BBD17D68B0B67B7423F1FE09B05B | SHA256:7362F82084BCDF47B0927674AD678F66214E8D4F2783A0B9338EE4EB773C3474 | |||
| 7156 | SavesintoHost.exe | C:\found.000\dir_00000002.chk\22eafd247d37c3 | text | |
MD5:4C5D73BD9B72206F10C401C85166FEAC | SHA256:5F0780F74CD91A2781BBD2E22062F634BFBD4F1F3F3CE23F13EB605EDCA01392 | |||
| 7156 | SavesintoHost.exe | C:\Users\Default\conhost.exe | executable | |
MD5:3AA1BBD17D68B0B67B7423F1FE09B05B | SHA256:7362F82084BCDF47B0927674AD678F66214E8D4F2783A0B9338EE4EB773C3474 | |||
| 7156 | SavesintoHost.exe | C:\found.000\dir_00000002.chk\ea9f0e6c9e2dcd | text | |
MD5:E2A6F08A52C11C66ED16917132255FB2 | SHA256:044A59FA9648C449AC8F4D14DBCB0246F93BDCB6BD65874655E241AD1D637F99 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
31
TCP/UDP connections
43
DNS requests
18
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.32.238.107:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6092 | svchost.exe | GET | 200 | 23.32.238.107:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.38.73.129:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6092 | svchost.exe | GET | 200 | 23.38.73.129:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5316 | dllhost.exe | GET | 403 | 141.8.192.138:80 | http://a1063683.xsph.ru/2172ee40.php?gcnWXuE9MUipBZc=bVK2py9yji&Y5YSB7xC1sNfAEv19t=v6&c890477b200ba1ffc8ef461f54aaad3b=c3ccc9b0173ab12b589ddb5b569d75e1&61cb0d9d4a37c6ca1c8fa3a413f36a41=gYxEWNxQmZxcDOjJmNihTZzImNkRzNiFzMldjMzQWYhhTNmhzYjNWO&gcnWXuE9MUipBZc=bVK2py9yji&Y5YSB7xC1sNfAEv19t=v6 | unknown | — | — | whitelisted |
5316 | dllhost.exe | GET | 403 | 141.8.192.138:80 | http://a1063683.xsph.ru/2172ee40.php?gcnWXuE9MUipBZc=bVK2py9yji&Y5YSB7xC1sNfAEv19t=v6&c890477b200ba1ffc8ef461f54aaad3b=c3ccc9b0173ab12b589ddb5b569d75e1&61cb0d9d4a37c6ca1c8fa3a413f36a41=gYxEWNxQmZxcDOjJmNihTZzImNkRzNiFzMldjMzQWYhhTNmhzYjNWO&gcnWXuE9MUipBZc=bVK2py9yji&Y5YSB7xC1sNfAEv19t=v6 | unknown | — | — | whitelisted |
6240 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7052 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.32.238.107:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6092 | svchost.exe | 23.32.238.107:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.38.73.129:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6092 | svchost.exe | 23.38.73.129:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.19.80.27:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
a1063683.xsph.ru |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Misc activity | ET INFO Observed DNS Query to xsph .ru Domain |
5316 | dllhost.exe | A Network Trojan was detected | ET MALWARE DCRAT Activity (GET) |
6540 | dllhost.exe | A Network Trojan was detected | ET MALWARE DCRAT Activity (GET) |
7096 | dllhost.exe | A Network Trojan was detected | ET MALWARE DCRAT Activity (GET) |
2928 | dllhost.exe | A Network Trojan was detected | ET MALWARE DCRAT Activity (GET) |
6784 | dllhost.exe | A Network Trojan was detected | ET MALWARE DCRAT Activity (GET) |
2292 | dllhost.exe | A Network Trojan was detected | ET MALWARE DCRAT Activity (GET) |
5828 | dllhost.exe | A Network Trojan was detected | ET MALWARE DCRAT Activity (GET) |
6520 | dllhost.exe | A Network Trojan was detected | ET MALWARE DCRAT Activity (GET) |
4128 | dllhost.exe | A Network Trojan was detected | ET MALWARE DCRAT Activity (GET) |