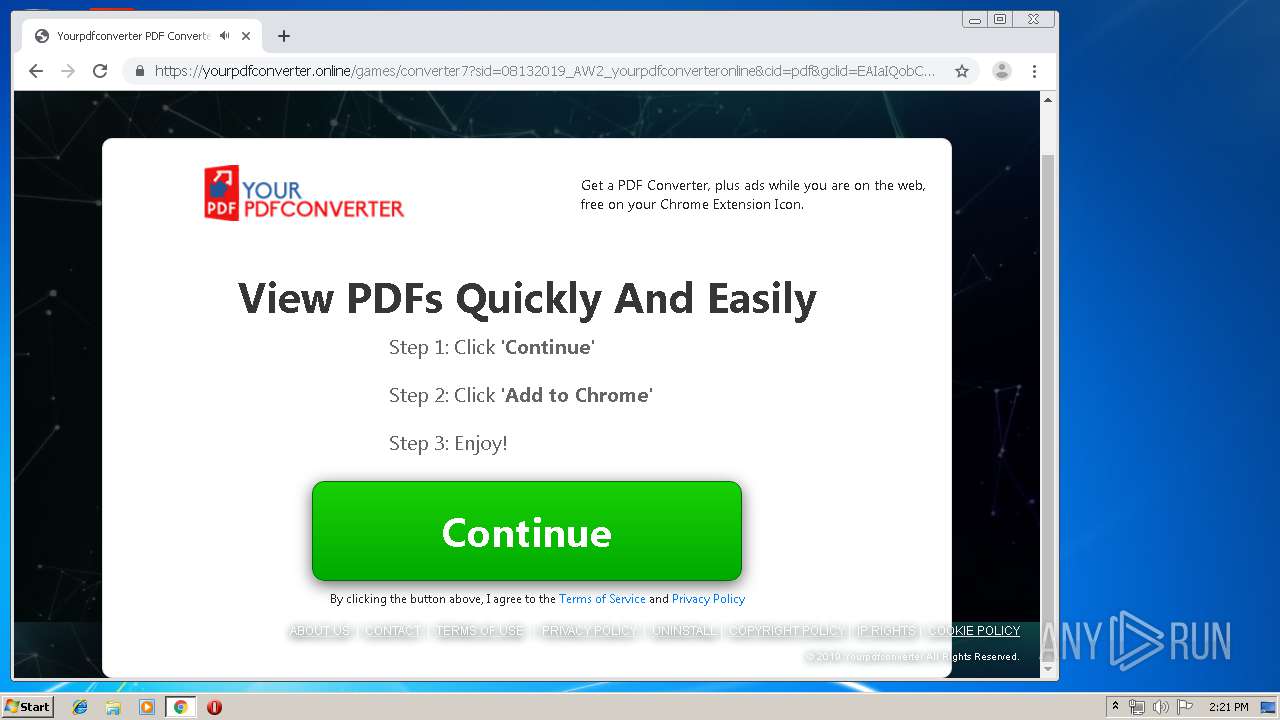
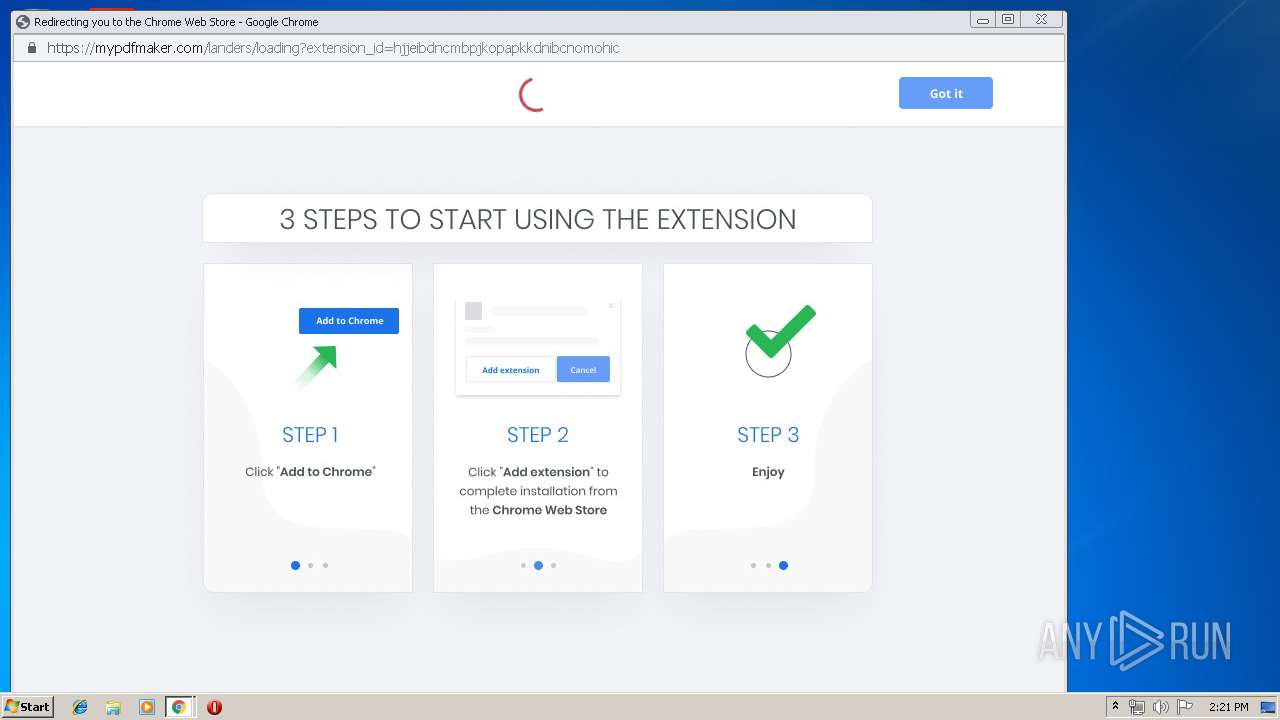
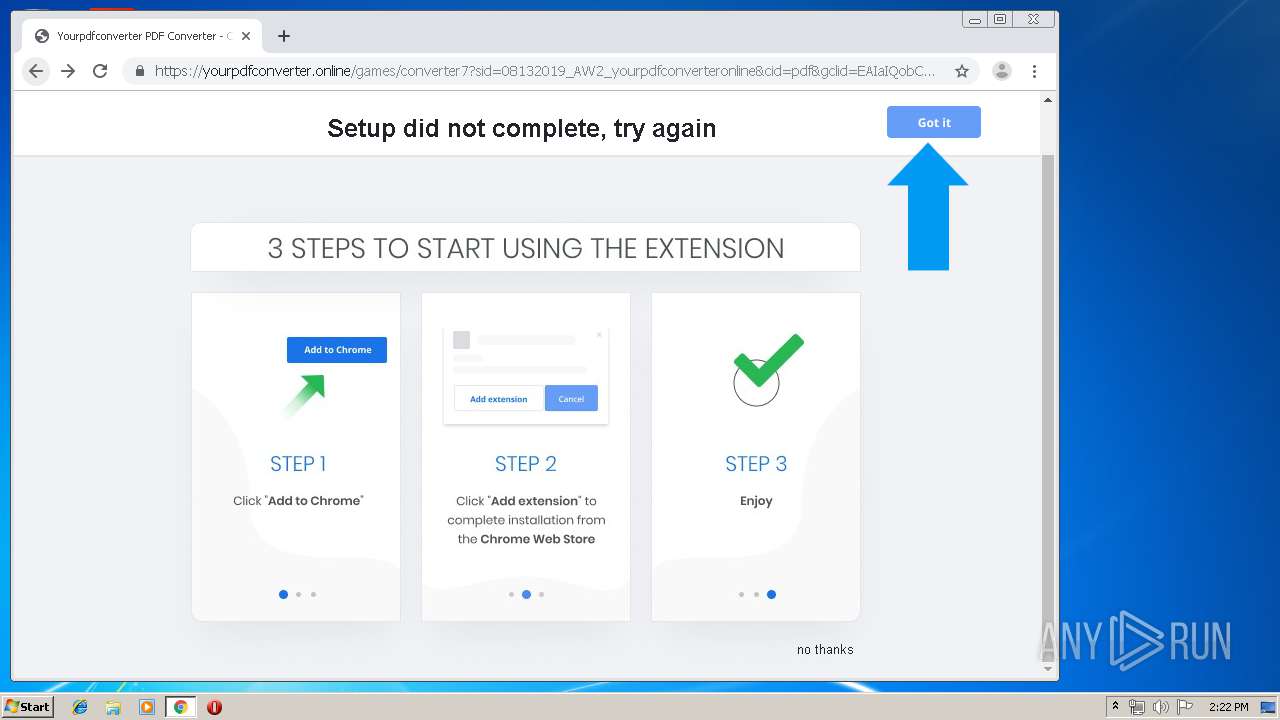
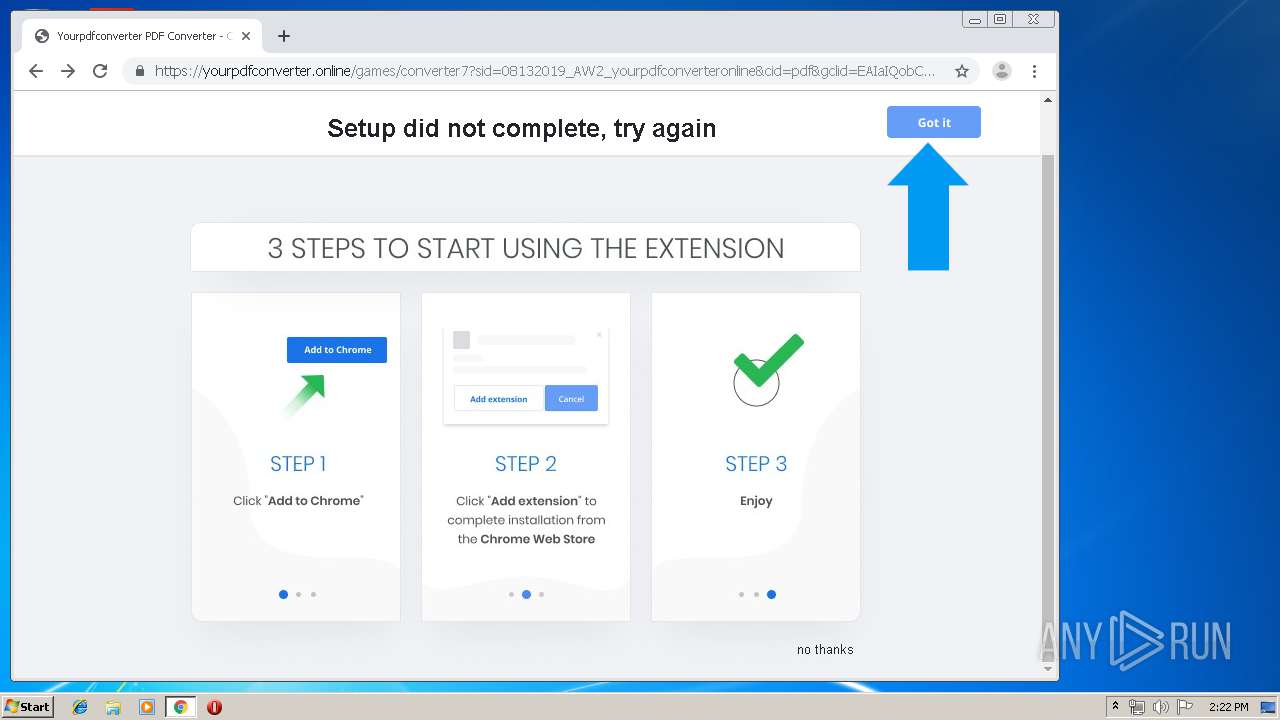
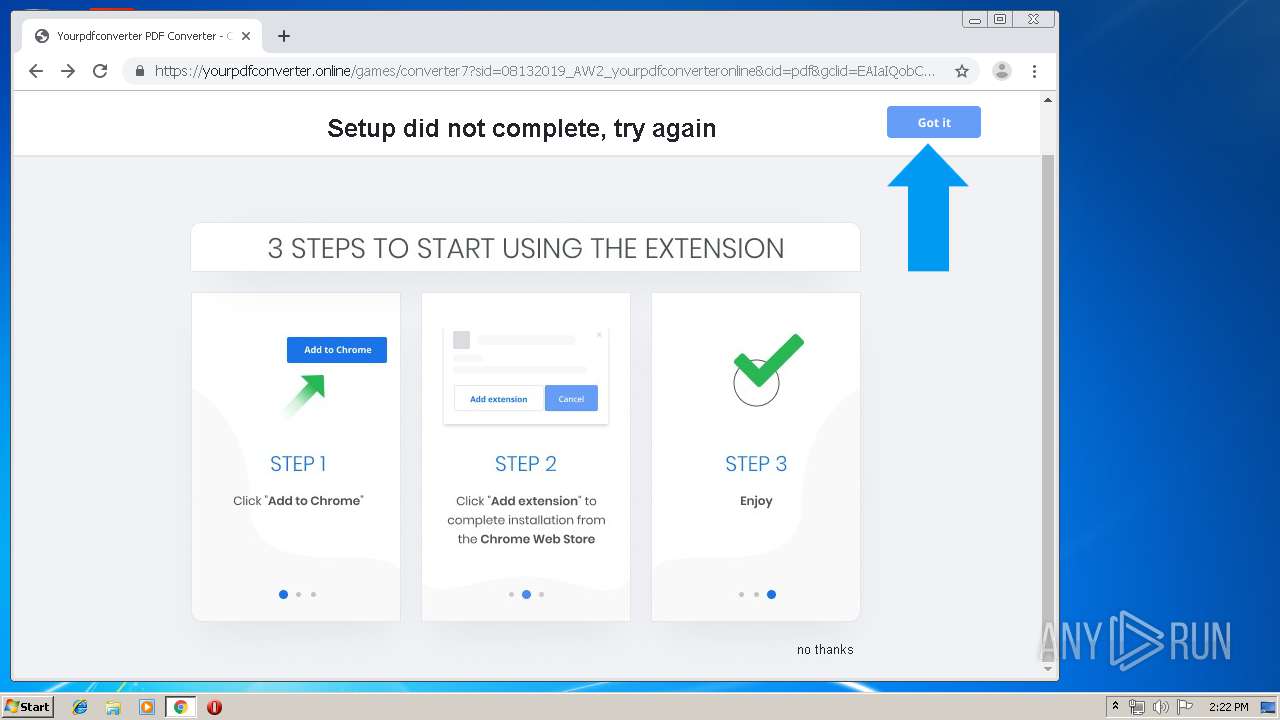
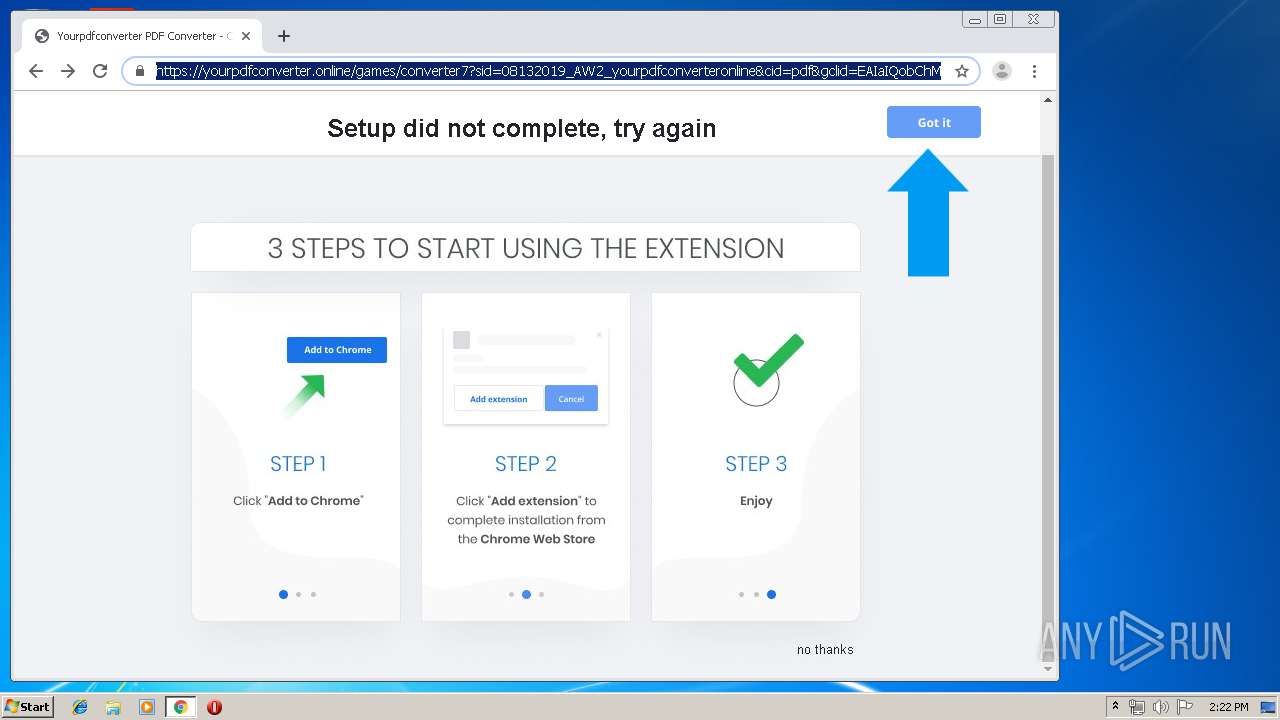
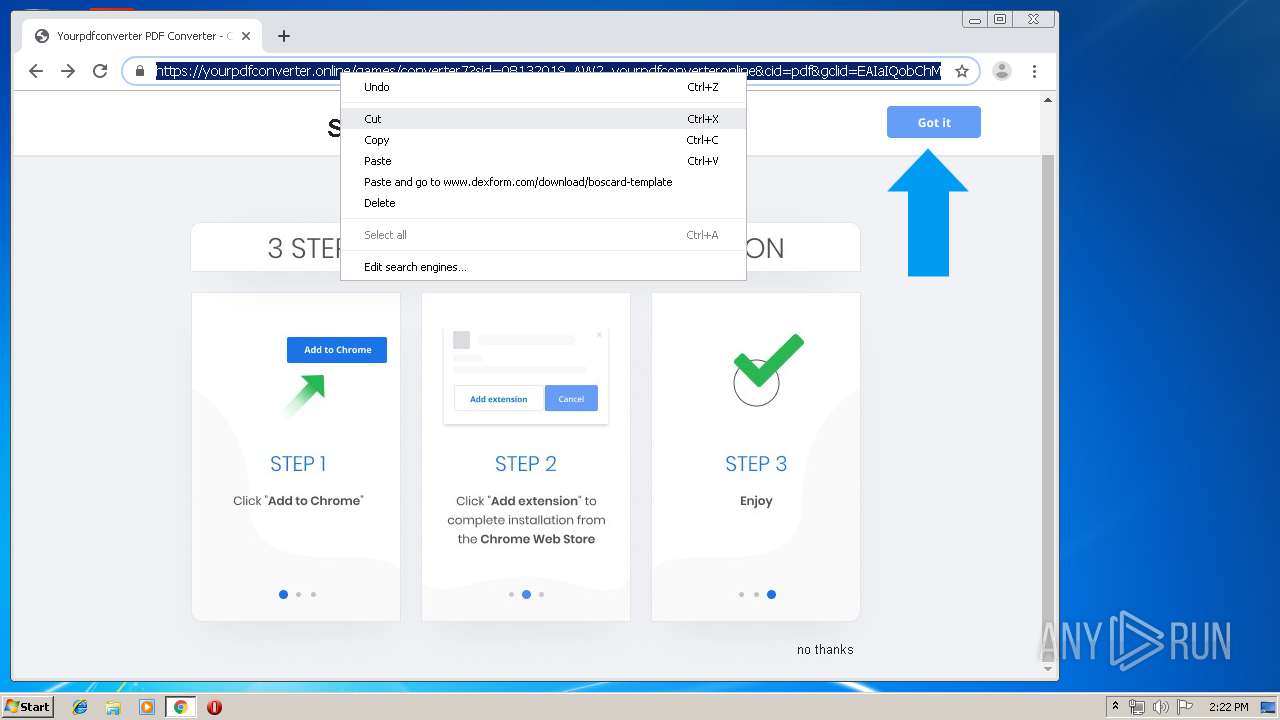
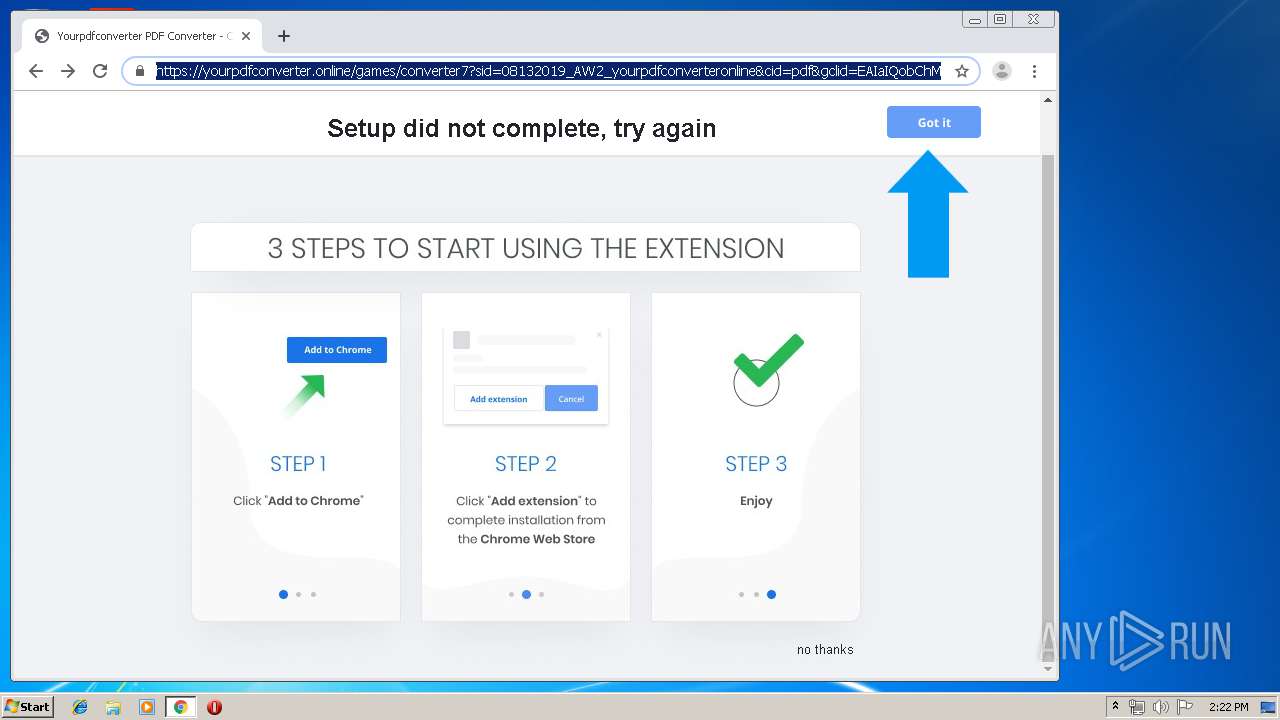
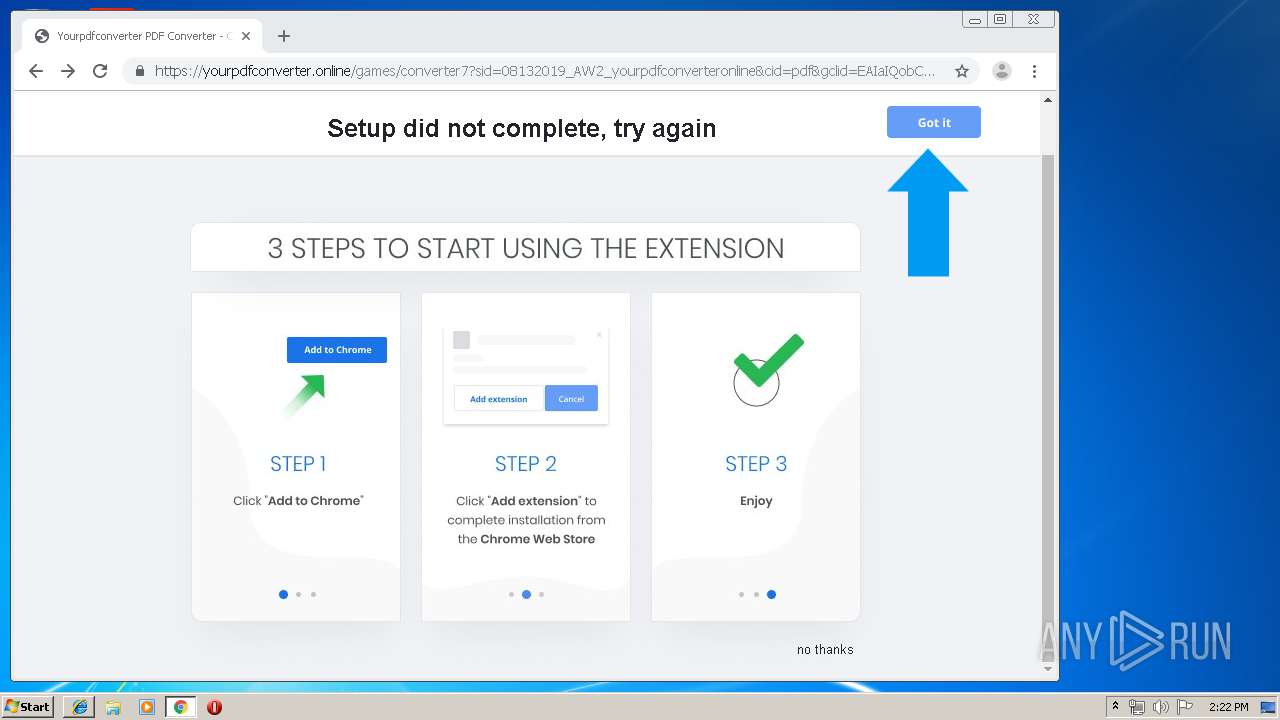
| URL: | http://www.dexform.com/download/boscard-template |
| Full analysis: | https://app.any.run/tasks/f1a58654-1331-41f5-9441-a530244be586 |
| Verdict: | Malicious activity |
| Analysis date: | August 13, 2019, 13:17:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 351210624E031769DC959E5193A30220 |
| SHA1: | FA05903B8FAF923C677002C66A214465ECB1D637 |
| SHA256: | 3022096F5E738EC7E599E93001CB81564825801A3F5608111120A9B99A1F20B3 |
| SSDEEP: | 3:N1KJS4BG8LloJNn:Cc4BNqb |
MALICIOUS
No malicious indicators.SUSPICIOUS
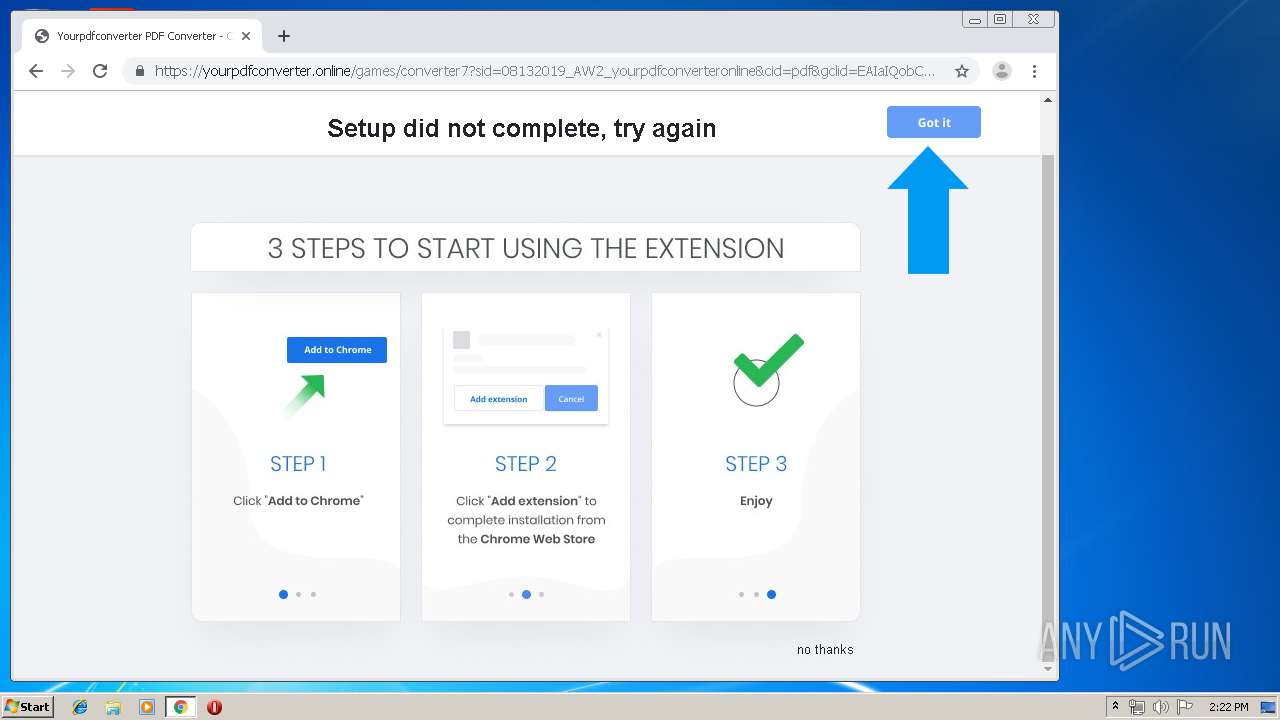
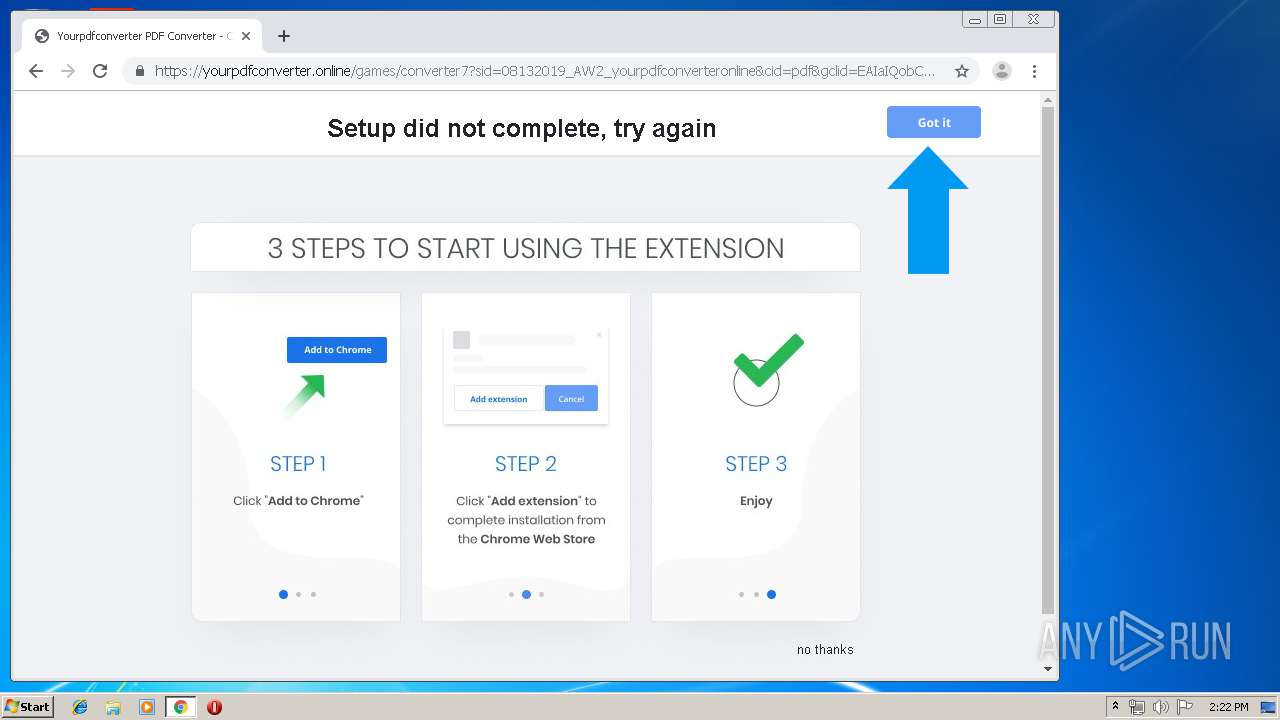
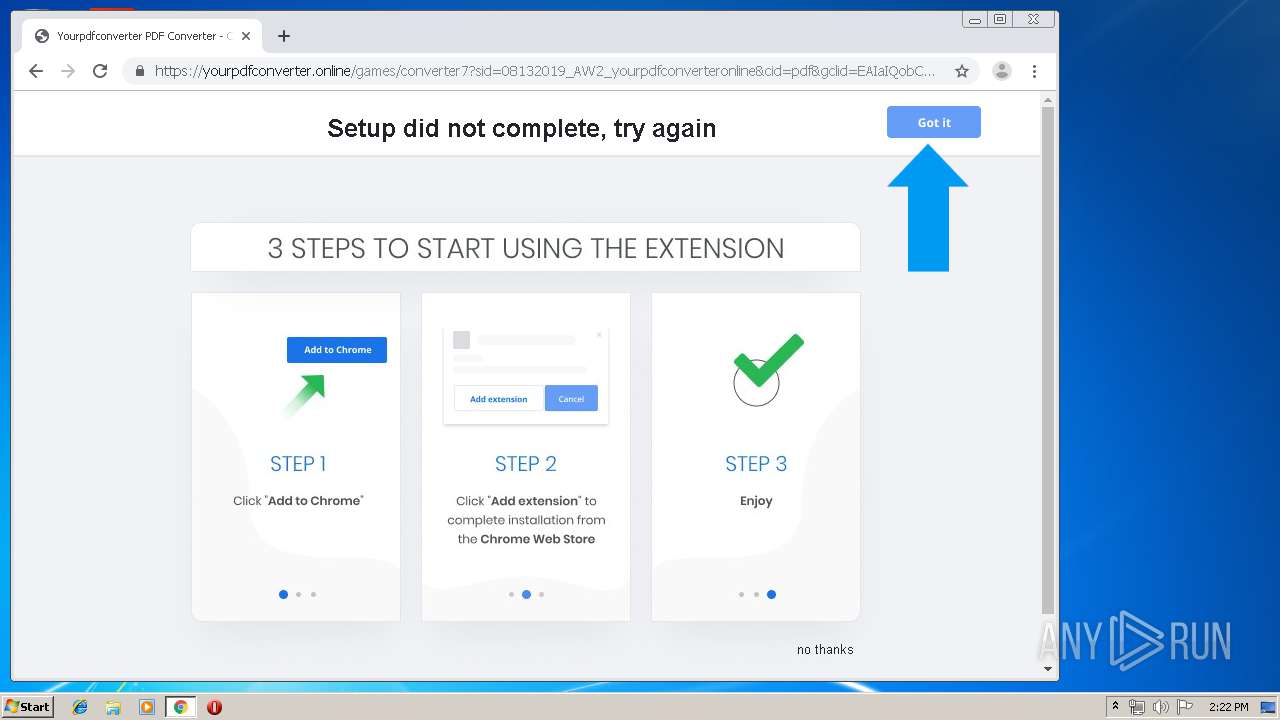
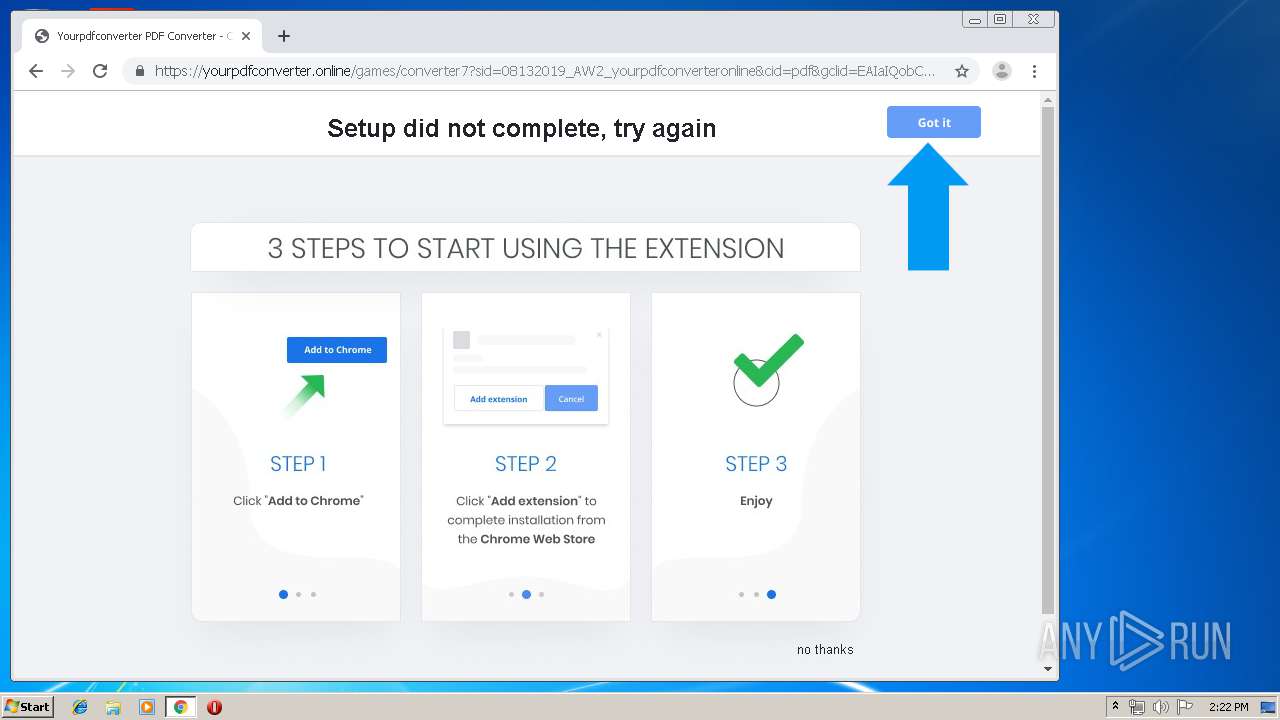
Modifies files in Chrome extension folder
- chrome.exe (PID: 3864)
Executed via COM
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3688)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3192)
INFO
Application launched itself
- iexplore.exe (PID: 2156)
- chrome.exe (PID: 3864)
Reads Internet Cache Settings
- iexplore.exe (PID: 3012)
- iexplore.exe (PID: 2888)
Changes internet zones settings
- iexplore.exe (PID: 2156)
- iexplore.exe (PID: 3968)
Reads internet explorer settings
- iexplore.exe (PID: 3012)
- iexplore.exe (PID: 2888)
Creates files in the user directory
- iexplore.exe (PID: 3012)
- iexplore.exe (PID: 2888)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3688)
- iexplore.exe (PID: 2156)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3192)
- iexplore.exe (PID: 3968)
Reads settings of System Certificates
- chrome.exe (PID: 3324)
Manual execution by user
- iexplore.exe (PID: 3968)
- chrome.exe (PID: 3864)
Changes settings of System certificates
- chrome.exe (PID: 3324)
- iexplore.exe (PID: 3968)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3968)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 3324)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
102
Monitored processes
65
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 352 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1004,4455330025425192957,10669872387464622422,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=8920184777435225793 --mojo-platform-channel-handle=4236 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 872 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,4455330025425192957,10669872387464622422,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16124512550209646910 --renderer-client-id=32 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3288 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1088 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1004,4455330025425192957,10669872387464622422,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=15103976003574283944 --mojo-platform-channel-handle=3472 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1212 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1004,4455330025425192957,10669872387464622422,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=9429781302036782609 --mojo-platform-channel-handle=3436 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1216 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1004,4455330025425192957,10669872387464622422,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=12894557815249635622 --mojo-platform-channel-handle=3800 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1440 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,4455330025425192957,10669872387464622422,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=6129999693970651659 --renderer-client-id=33 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1384 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1676 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,4455330025425192957,10669872387464622422,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7177496585316655436 --renderer-client-id=52 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2004 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1700 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,4455330025425192957,10669872387464622422,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=10170595127608490263 --renderer-client-id=53 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4012 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1828 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,4455330025425192957,10669872387464622422,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=10153303614771314758 --renderer-client-id=56 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3708 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1832 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,4455330025425192957,10669872387464622422,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=14124539221302853424 --renderer-client-id=41 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3012 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
1 745
Read events
1 459
Write events
275
Delete events
11
Modification events
| (PID) Process: | (2156) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2156) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2156) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2156) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2156) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2156) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000092000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2156) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {C35E6155-BDCC-11E9-9885-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2156) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2156) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 2 | |||
| (PID) Process: | (2156) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E307080002000D000D0011003900E200 | |||
Executable files
0
Suspicious files
171
Text files
354
Unknown types
31
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2156 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2156 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3012 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3012 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\E639IZMO\boscard-template[1].txt | — | |
MD5:— | SHA256:— | |||
| 3012 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3012 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@www.dexform[1].txt | text | |
MD5:— | SHA256:— | |||
| 3012 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\E639IZMO\boscard-template[1].htm | html | |
MD5:— | SHA256:— | |||
| 3012 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DK43QWNJ\css[1].txt | text | |
MD5:— | SHA256:— | |||
| 3012 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DK43QWNJ\custom[1].css | text | |
MD5:— | SHA256:— | |||
| 3012 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@dexform[1].txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
67
TCP/UDP connections
156
DNS requests
104
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3012 | iexplore.exe | GET | 200 | 104.28.4.241:80 | http://static.dexform.com/static/general/dexform/images/logo.png | US | image | 4.67 Kb | suspicious |
3012 | iexplore.exe | GET | 200 | 104.28.4.241:80 | http://static.dexform.com/static//general/dexform/css/html.css | US | text | 715 b | suspicious |
3012 | iexplore.exe | GET | 200 | 104.28.4.241:80 | http://static.dexform.com/static/general/dexform/css/site.css | US | text | 21.8 Kb | suspicious |
3012 | iexplore.exe | GET | 200 | 104.28.4.241:80 | http://static.dexform.com/media/docs/7954/custom.css | US | text | 1.52 Kb | suspicious |
3012 | iexplore.exe | GET | 200 | 104.28.4.241:80 | http://static.dexform.com/static/general/dexform/images/tokcha-banner2.jpg | US | image | 43.2 Kb | suspicious |
3012 | iexplore.exe | GET | 200 | 104.28.4.241:80 | http://static.dexform.com/media/docs/7954/boscard-template_preview1.png | US | image | 6.25 Kb | suspicious |
3012 | iexplore.exe | GET | 200 | 104.28.4.241:80 | http://static.dexform.com/media/docs/7954/boscard-template_bg1.png | US | image | 6.86 Kb | suspicious |
3012 | iexplore.exe | GET | 200 | 172.217.21.194:80 | http://pagead2.googlesyndication.com/pagead/js/adsbygoogle.js | US | text | 34.0 Kb | whitelisted |
3012 | iexplore.exe | GET | 200 | 104.28.4.241:80 | http://static.dexform.com/static/general/dexform/js/site.js | US | text | 1.01 Kb | suspicious |
3012 | iexplore.exe | GET | 200 | 172.217.18.106:80 | http://fonts.googleapis.com/css?family=Open+Sans:300,400,600,700&lang=en | US | text | 167 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3012 | iexplore.exe | 104.28.4.241:80 | www.dexform.com | Cloudflare Inc | US | shared |
2156 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3012 | iexplore.exe | 209.197.3.15:443 | maxcdn.bootstrapcdn.com | Highwinds Network Group, Inc. | US | whitelisted |
3012 | iexplore.exe | 172.217.18.106:80 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3012 | iexplore.exe | 172.217.23.163:80 | fonts.gstatic.com | Google Inc. | US | whitelisted |
3012 | iexplore.exe | 23.111.8.154:80 | oss.maxcdn.com | netDNA | US | unknown |
3012 | iexplore.exe | 172.217.21.194:80 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
3012 | iexplore.exe | 172.217.22.42:443 | ajax.googleapis.com | Google Inc. | US | whitelisted |
3012 | iexplore.exe | 216.58.206.14:80 | www.google-analytics.com | Google Inc. | US | whitelisted |
2156 | iexplore.exe | 104.28.5.241:80 | www.dexform.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.dexform.com |
| unknown |
www.bing.com |
| whitelisted |
static.dexform.com |
| suspicious |
maxcdn.bootstrapcdn.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
oss.maxcdn.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
ajax.googleapis.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |