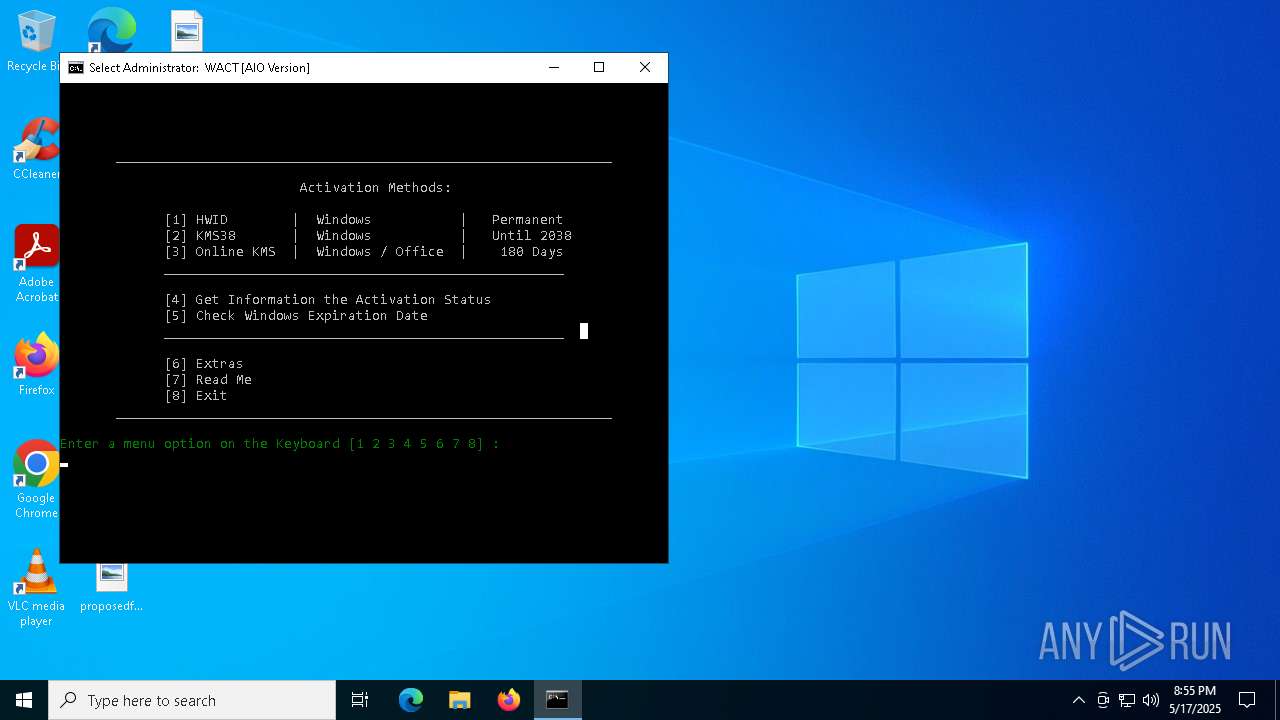
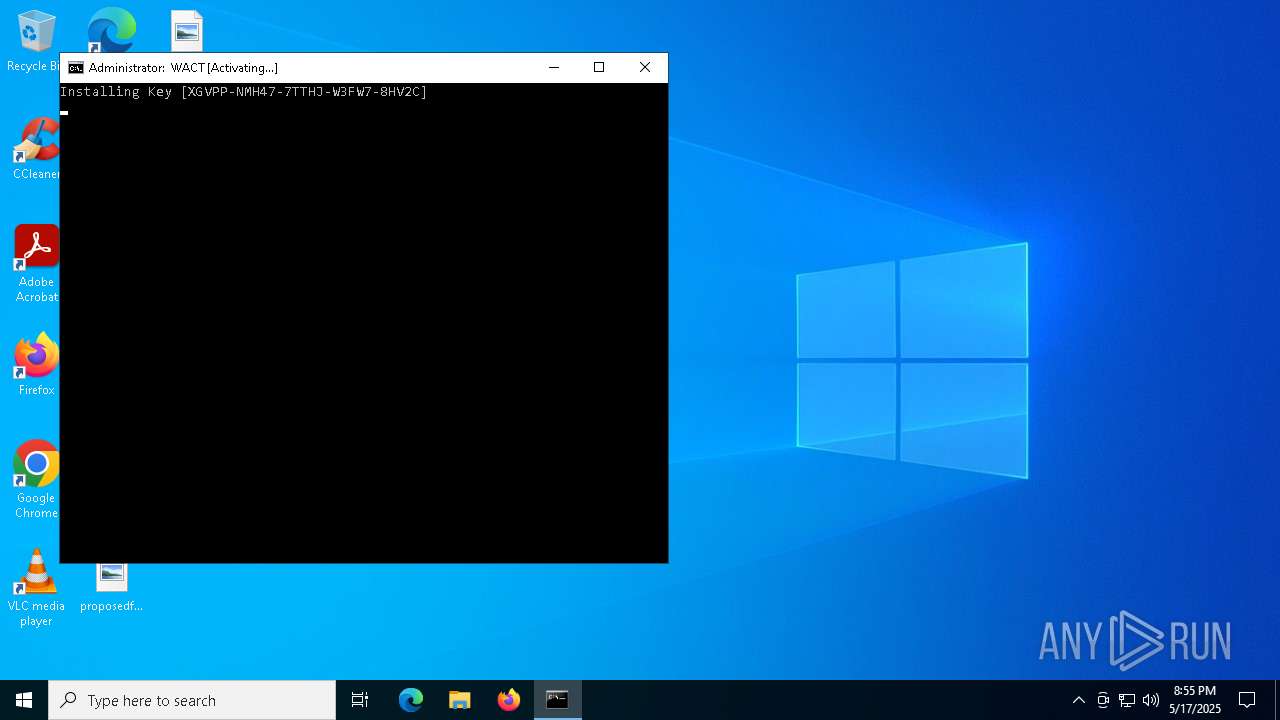
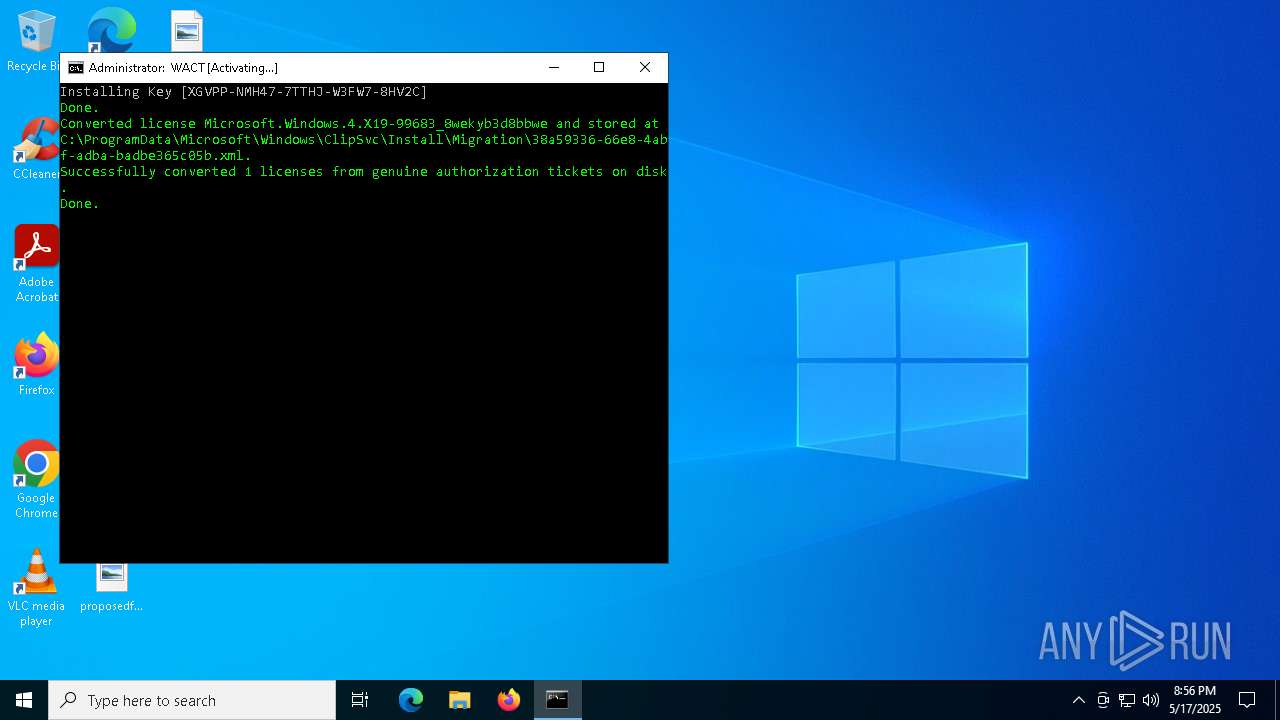
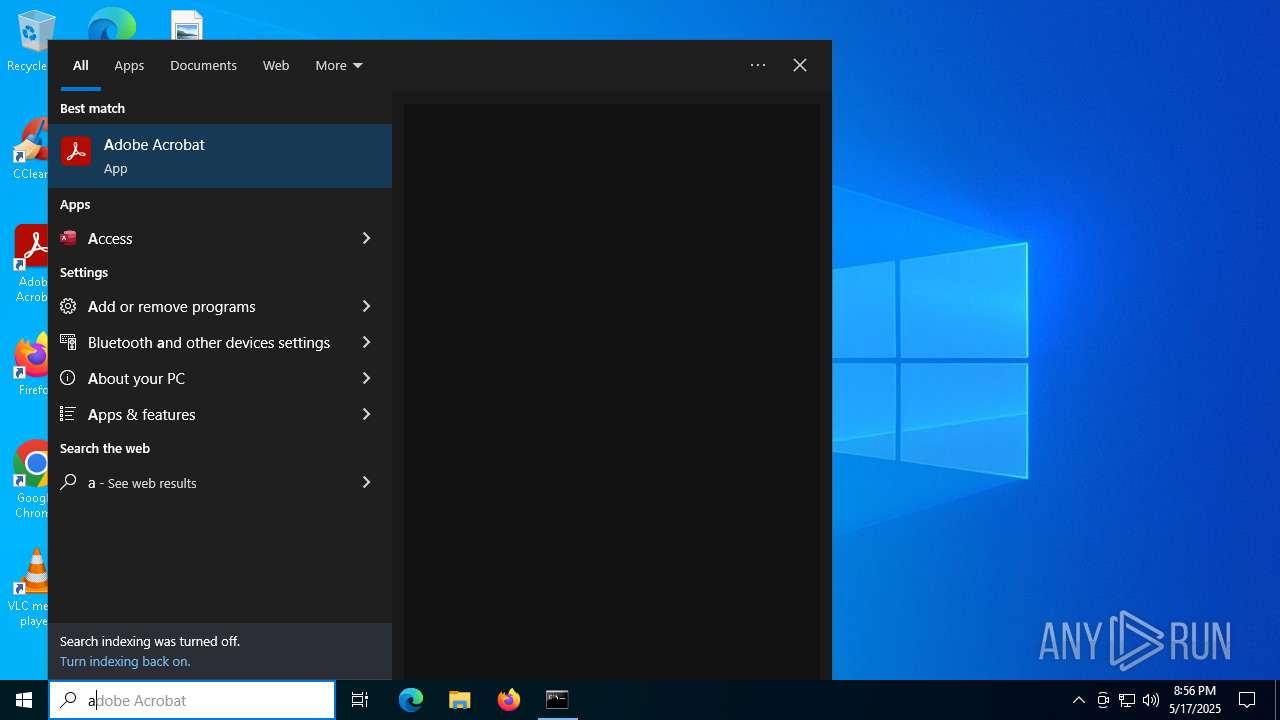
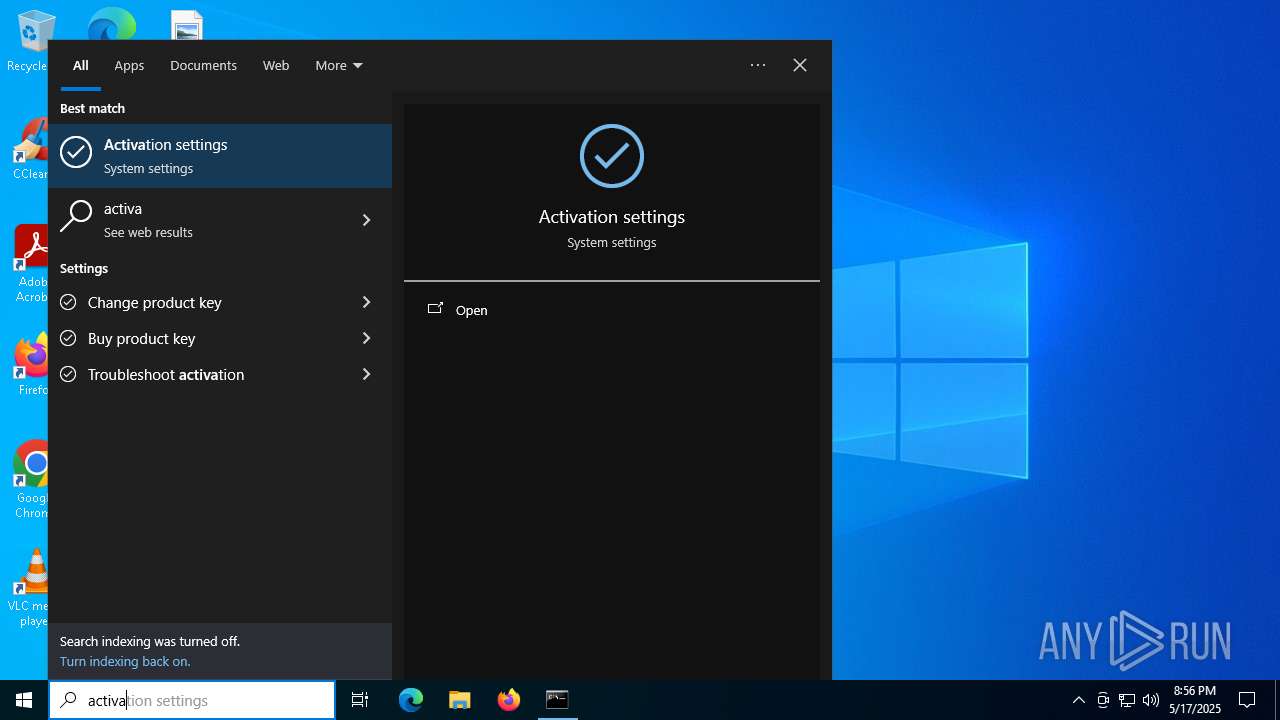
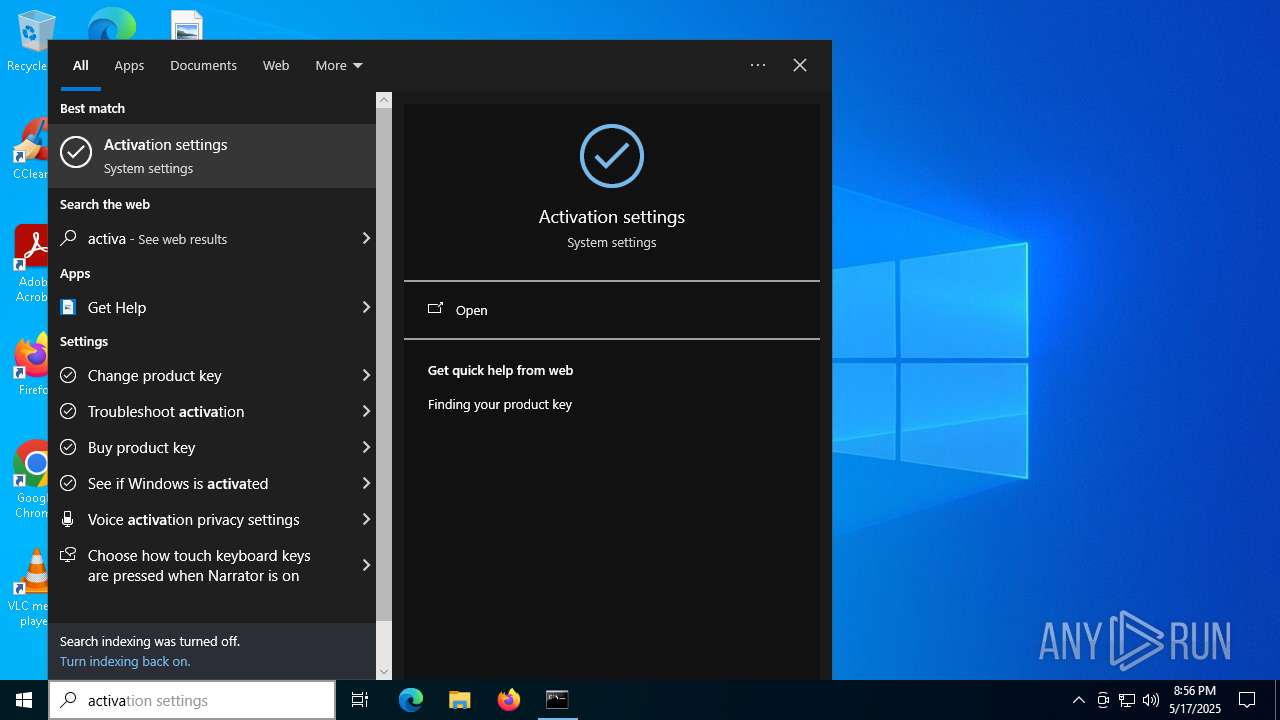
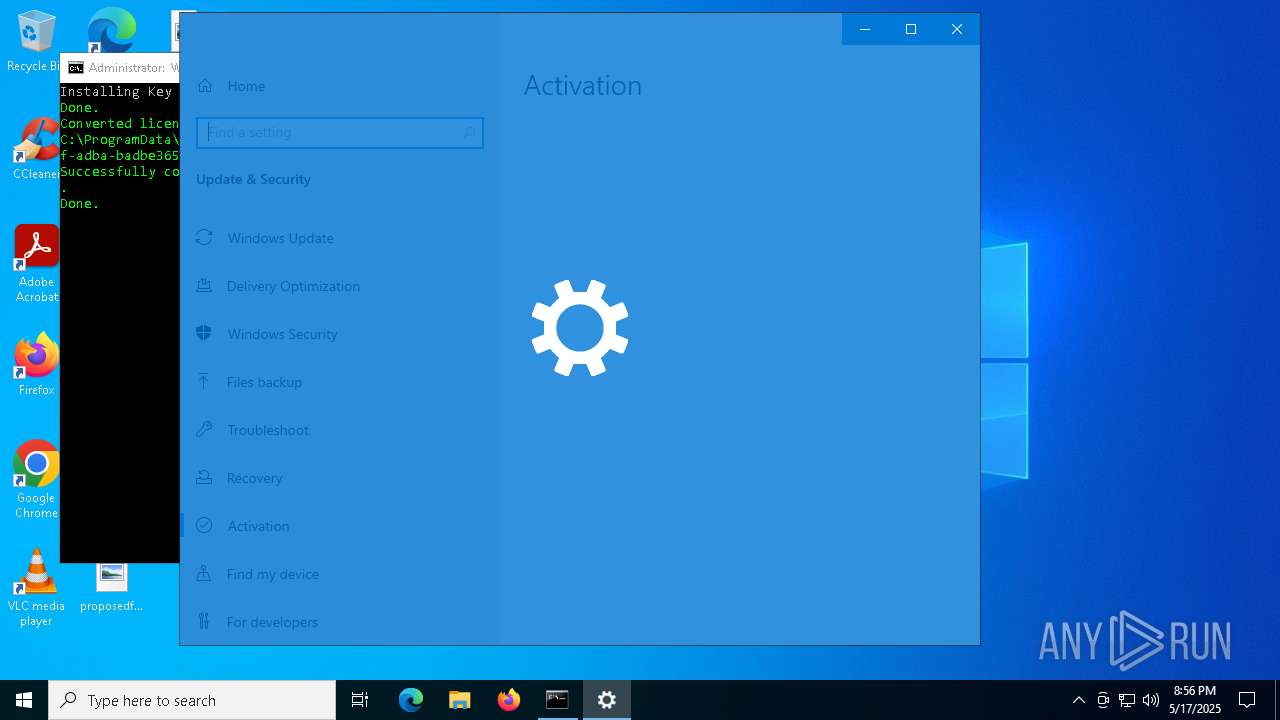
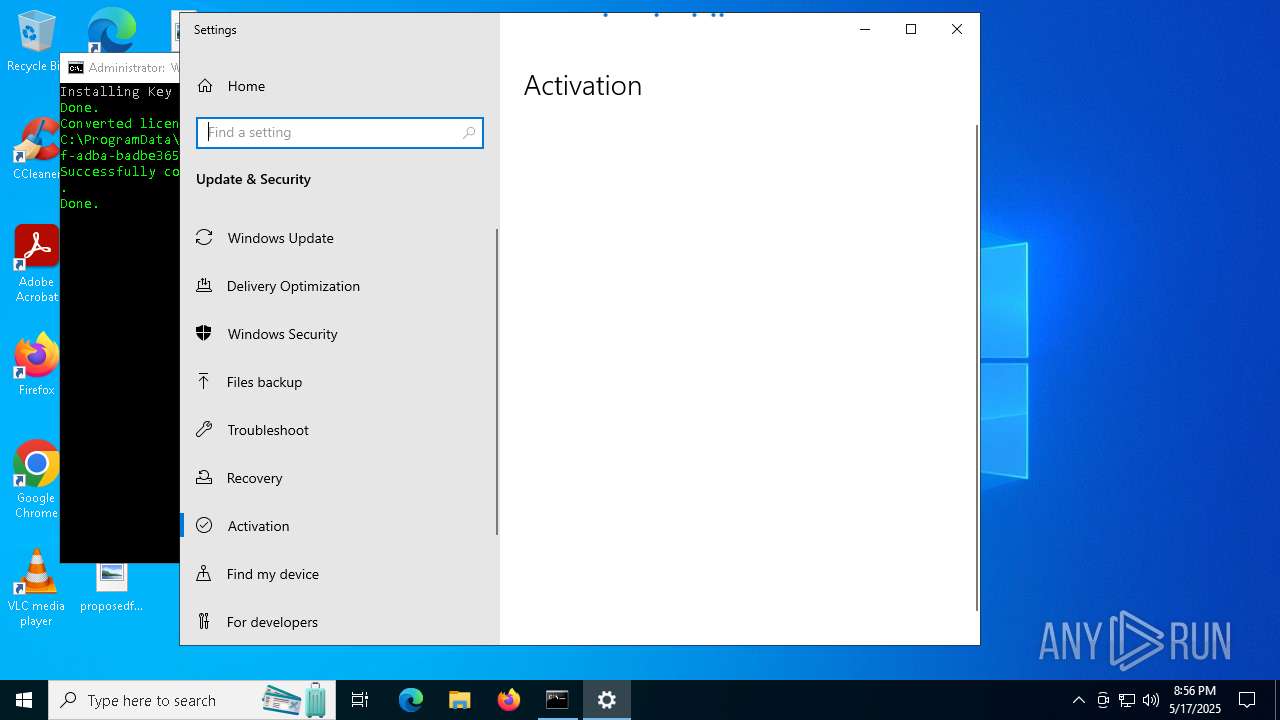
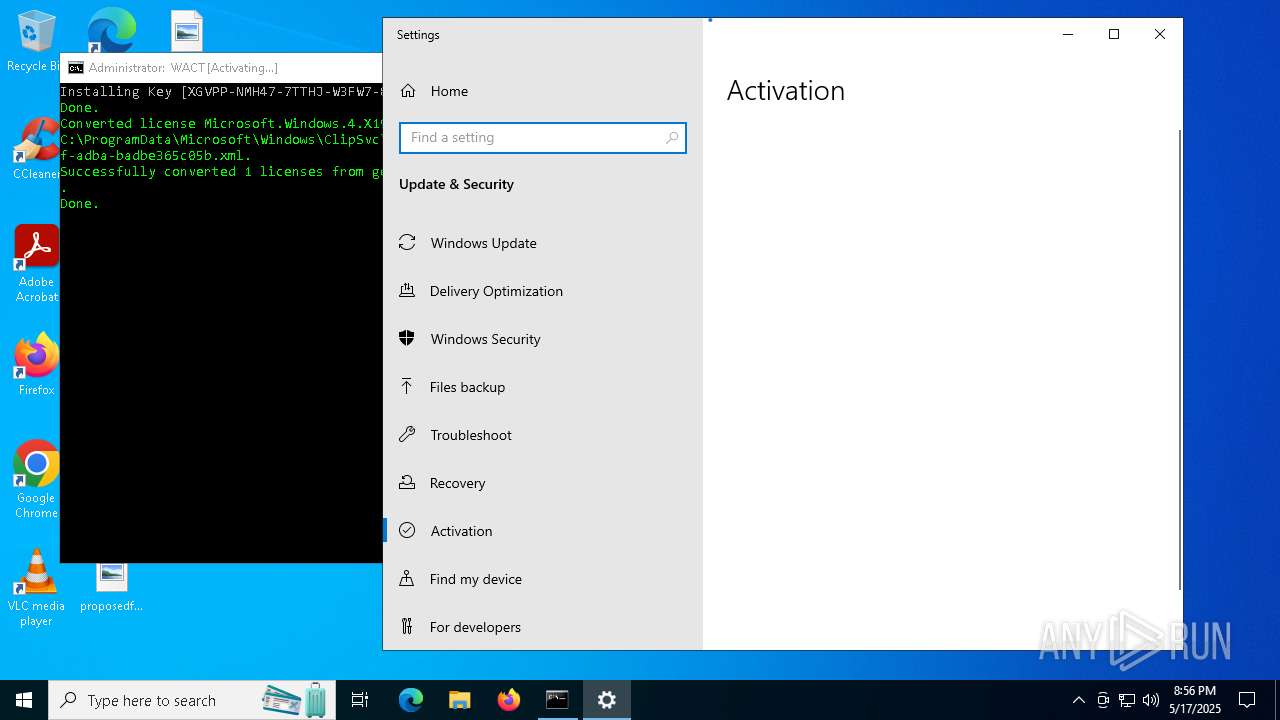
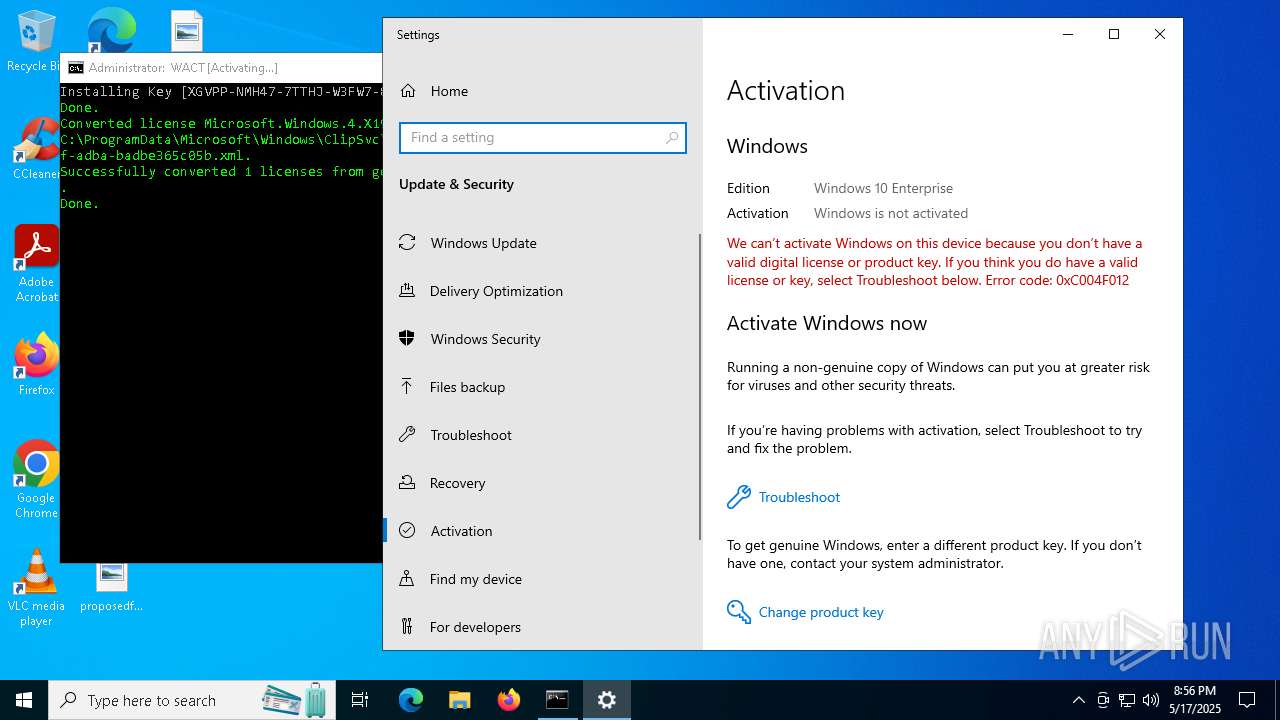
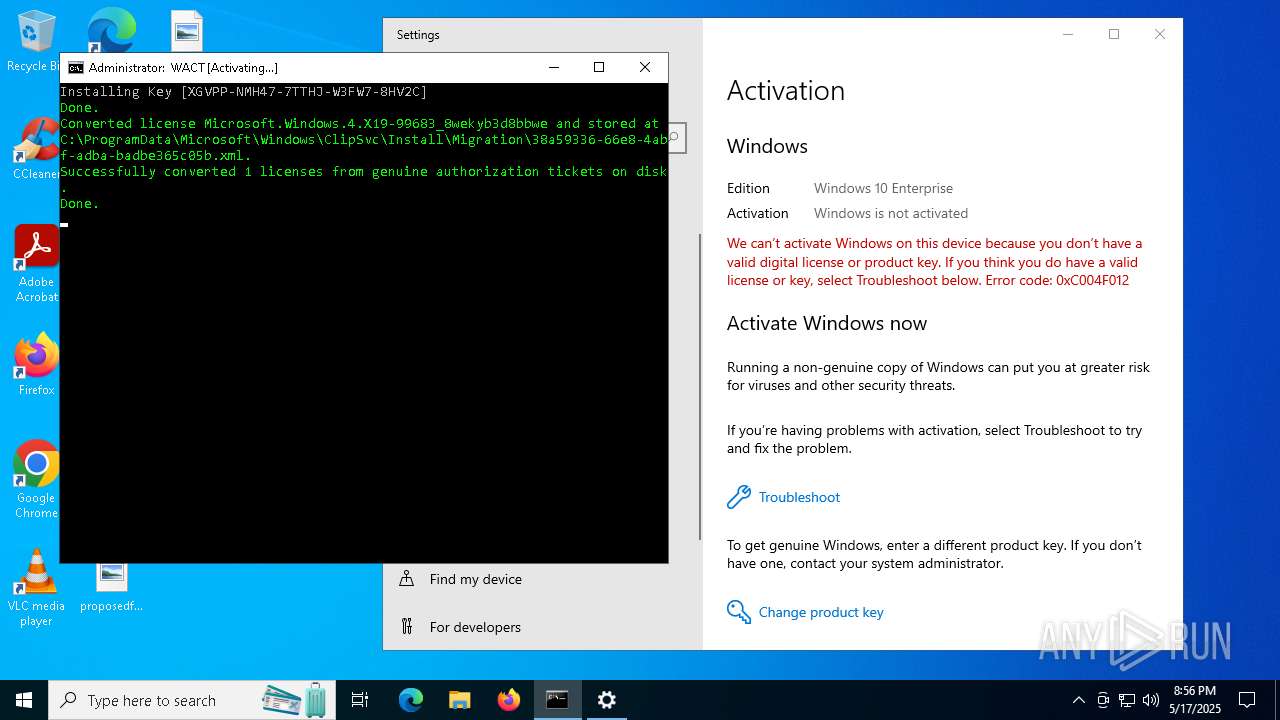
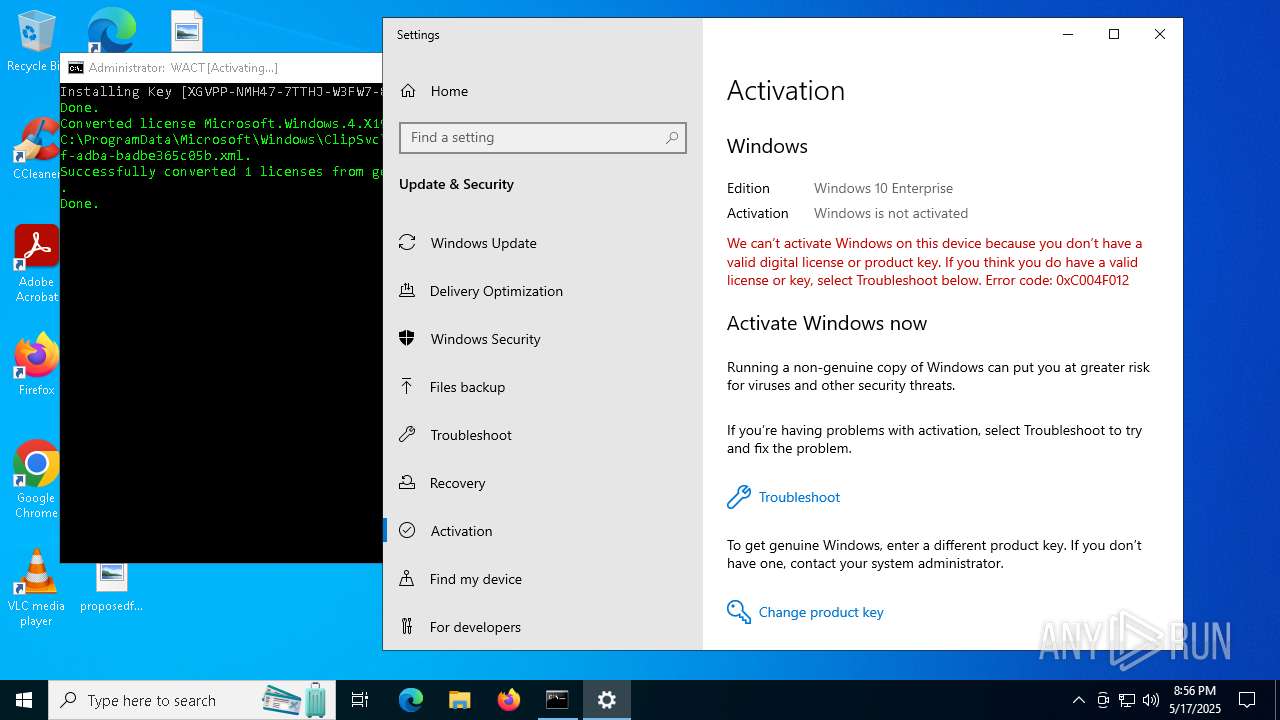
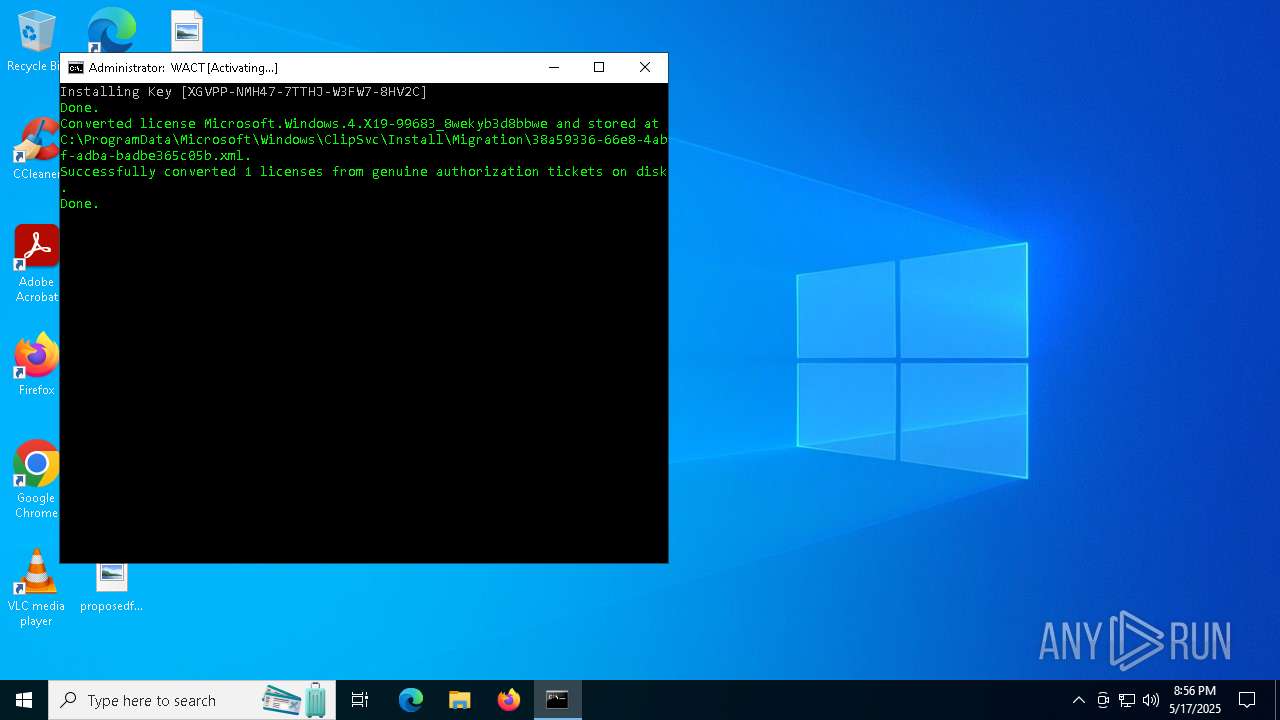
| File name: | WACT_AIO.bat |
| Full analysis: | https://app.any.run/tasks/4c0cc267-601e-414e-98b3-53db1c7a7cf5 |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2025, 20:55:30 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with CRLF line terminators |
| MD5: | 79D81FFE01D8D526736E58C9D48324B3 |
| SHA1: | 450BCA55C673A17B9B8FD69799842755D0E2E2E0 |
| SHA256: | 30217AC7B9C113AEE33DAEFFB5B7ACA9C62F9F0A75E5636B2ECBB1F6ADCBD941 |
| SSDEEP: | 6144:I96cEqR1F6sCKKztZlKoi1PpNpNxUXE+v+5Ur:YVDVCKH1hNq0+W5Ur |
MALICIOUS
No malicious indicators.SUSPICIOUS
Runs shell command (SCRIPT)
- wscript.exe (PID: 4448)
The process executes VB scripts
- cmd.exe (PID: 6516)
- cmd.exe (PID: 6876)
Executing commands from a ".bat" file
- wscript.exe (PID: 4448)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 4448)
- cmd.exe (PID: 6876)
Starts application with an unusual extension
- cmd.exe (PID: 6876)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 6876)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6876)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 6876)
Manipulates environment variables
- powershell.exe (PID: 900)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 6876)
CSC.EXE is used to compile C# code
- csc.exe (PID: 4428)
Executes script without checking the security policy
- powershell.exe (PID: 900)
Unpacks CAB file
- expand.exe (PID: 4920)
Executable content was dropped or overwritten
- csc.exe (PID: 4428)
- expand.exe (PID: 4920)
- cmd.exe (PID: 6876)
Hides command output
- cmd.exe (PID: 2088)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 4776)
- cscript.exe (PID: 4932)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 4776)
- cscript.exe (PID: 4932)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 4776)
- cscript.exe (PID: 4932)
Application launched itself
- cmd.exe (PID: 6876)
- ClipUp.exe (PID: 5132)
INFO
Starts MODE.COM to configure console settings
- mode.com (PID: 660)
- mode.com (PID: 2148)
- mode.com (PID: 6456)
Checks supported languages
- mode.com (PID: 660)
- mode.com (PID: 2148)
- mode.com (PID: 6456)
- chcp.com (PID: 5024)
- csc.exe (PID: 4428)
- expand.exe (PID: 4920)
- gatherosstatemodified.exe (PID: 1116)
- cvtres.exe (PID: 5544)
Changes the display of characters in the console
- cmd.exe (PID: 6876)
Create files in a temporary directory
- cvtres.exe (PID: 5544)
- csc.exe (PID: 4428)
- ClipUp.exe (PID: 6036)
Reads security settings of Internet Explorer
- cscript.exe (PID: 4776)
- cscript.exe (PID: 4932)
Reads the machine GUID from the registry
- expand.exe (PID: 4920)
- csc.exe (PID: 4428)
- gatherosstatemodified.exe (PID: 1116)
Creates files in the program directory
- ClipUp.exe (PID: 6036)
Reads the computer name
- gatherosstatemodified.exe (PID: 1116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
165
Monitored processes
31
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | mode 76, 30 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 900 | powershell -nop -c $f=[IO.File]::ReadAllText($env:0)-split':bat2file\:.*';iex($f[1]); X(1) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 968 | "C:\WINDOWS\System32\SLUI.exe" RuleId=31e71c49-8da7-4a2f-ad92-45d98a1c79ba;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=8b351c9c-f398-4515-9900-09df49427262;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1116 | C:\WACTFILES\gatherosstatemodified.exe Pfn=Microsoft.Windows.4.X19-99683_8wekyb3d8bbwe;DownlevelGenuineState=1 | C:\WACTFILES\gatherosstatemodified.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Gather Downlevel OS Activation State Exit code: 0 Version: 10.0.14393.0 (rs1_release.160715-1616) Modules
| |||||||||||||||
| 1196 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | reg query "HKLM\SYSTEM\CurrentControlSet\Control\ProductOptions" /v OSProductPfn | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2088 | C:\WINDOWS\system32\cmd.exe /c reg query "HKLM\SYSTEM\CurrentControlSet\Control\ProductOptions" /v OSProductPfn 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2148 | mode 76, 30 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3240 | powershell write-host -fore DarkGreen Enter a menu option on the Keyboard [1,2,3,4,5,6,7,8] : | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4428 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\b31rescw\b31rescw.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
Total events
15 848
Read events
15 846
Write events
2
Delete events
0
Modification events
| (PID) Process: | (4448) wscript.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.FriendlyAppName |
Value: Windows Command Processor | |||
| (PID) Process: | (4448) wscript.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.ApplicationCompany |
Value: Microsoft Corporation | |||
Executable files
4
Suspicious files
5
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6516 | cmd.exe | C:\Users\admin\AppData\Local\Temp\OEgetPriv_WACT_AIO.vbs | text | |
MD5:D14A6C18536B08C2D91CC10129CEC2CA | SHA256:88F0E55BE41422957E8F4FEC8CAF0F9ED4E68D1F0290171BA8F4BD26C19FA17D | |||
| 900 | powershell.exe | C:\Users\admin\Desktop\1 | compressed | |
MD5:7492829A6D0BD32B501EB2C4938FE2EE | SHA256:1A258168F2B78A246D7C7A5F15CB07BF40564C08A18D9C9970AEE5191AFD00CC | |||
| 900 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_iapi1xbc.rvz.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 900 | powershell.exe | C:\Users\admin\AppData\Local\Temp\b31rescw\b31rescw.cmdline | text | |
MD5:FFCE41041569A4E26332A9EE47DB932F | SHA256:BF2A5E89BE150DAAEAE886F962B103D9B48C7DF8AC761AF7744015B6F0467258 | |||
| 4428 | csc.exe | C:\Users\admin\AppData\Local\Temp\b31rescw\b31rescw.dll | executable | |
MD5:5060CE4BA595A1F81962DD213833C4BF | SHA256:8E9235A0AAC98087CD75DDB24B865CB84F07A6F8B516372D61D4A8BE663C371B | |||
| 4428 | csc.exe | C:\Users\admin\AppData\Local\Temp\b31rescw\CSC10541583AAC5415EABEE579E4616568.TMP | binary | |
MD5:F4FA05709AA400E402C74594CEE5FF8B | SHA256:E4D788189EF515DBE7875FDA759BF0DBDC6A095D6E9DE221B63AFB41F963DF0C | |||
| 4428 | csc.exe | C:\Users\admin\AppData\Local\Temp\b31rescw\b31rescw.out | text | |
MD5:F38E8315722FF394EFF57A33271D5DB8 | SHA256:FF2ECFE001859358FDD6157FEFE9B99F2BCB4A300E3656AF9DA41EB4A3717794 | |||
| 3240 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_w2z1302u.1do.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 900 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:B377FCB800F28F51B14D8BD54DE0DA24 | SHA256:971A0E8C24040935162D02A2CF0F015624BB52C6EDF5DBEE5B9DA23637A2B531 | |||
| 4920 | expand.exe | C:\Users\admin\Desktop\gatherosstatemodified.exe | executable | |
MD5:892FAE48577E46EABD9FBBC4107D924C | SHA256:4A6EBF681B69C0D28EBF51E6E6DA05974DC1166502B174293BC6585B0814DA7B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
35
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6592 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6592 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6592 | SIHClient.exe | GET | 200 | 23.216.77.18:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
6592 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
6592 | SIHClient.exe | GET | 200 | 23.216.77.18:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
6592 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
6592 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6592 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |