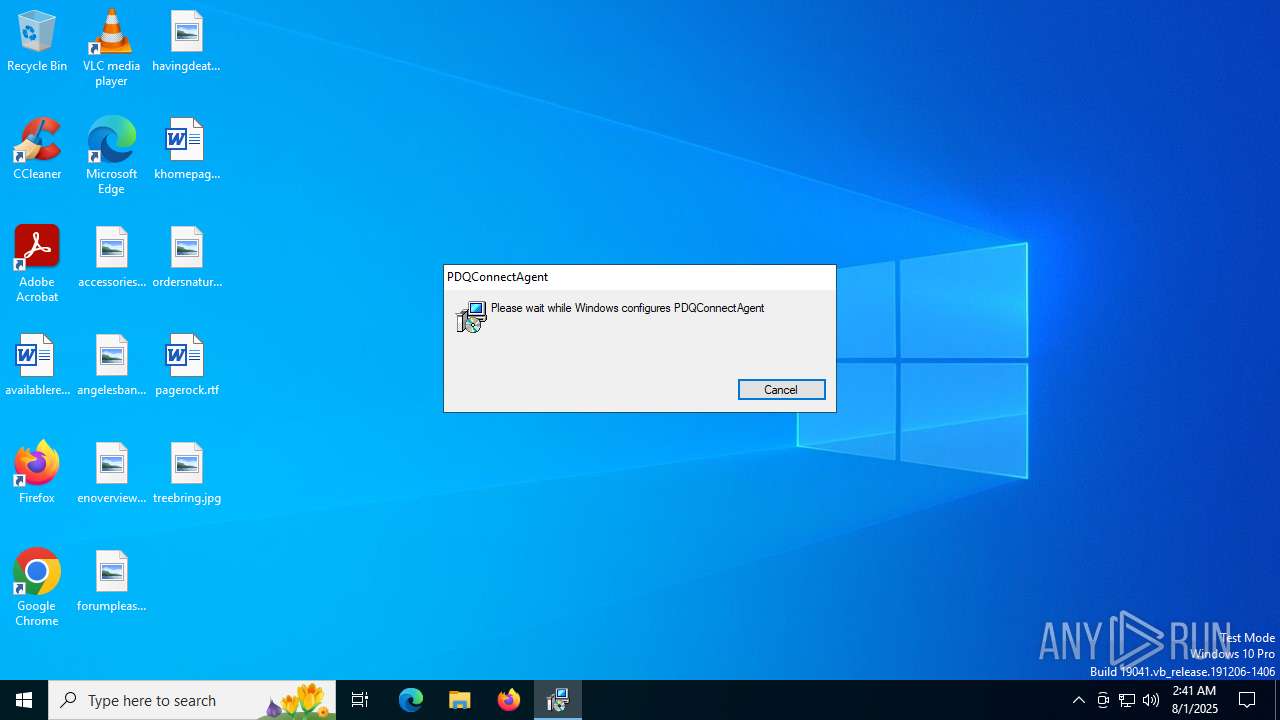
| File name: | verfacturaServiMaxnopaga.msi |
| Full analysis: | https://app.any.run/tasks/0c144d04-4355-44ea-972c-1e23f62399ce |
| Verdict: | Malicious activity |
| Analysis date: | August 01, 2025, 02:41:35 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: PDQConnectAgent, Author: PDQ.com, Keywords: Installer, Comments: This installer database contains the logic and data required to install PDQConnectAgent., Template: x64;1033, Revision Number: {881D68C5-5E81-49C0-BB0F-FD204AF7CC10}, Create Time/Date: Tue Jul 1 13:52:22 2025, Last Saved Time/Date: Tue Jul 1 13:52:22 2025, Number of Pages: 200, Number of Words: 2, Name of Creating Application: WiX Toolset (5.0.0.0), Security: 2 |
| MD5: | 236D071E84610000EBDEF49CF9944EE4 |
| SHA1: | 44BFDA46A16CEE7C40FB6D46914E950A3E5AB0B2 |
| SHA256: | 301E415DBAD6F52CE3CD31C47C4AB719A3672CC1A76D94C40A4C975D28E2E077 |
| SSDEEP: | 98304:sZc66NpYAWZX4KfTfyiDcLygd85msdyDsy4A4rp2Newf1GGzTykacWrVxNWQv0rJ:9QrXcN |
MALICIOUS
Changes powershell execution policy (Bypass)
- pdq-connect-agent.exe (PID: 2040)
Bypass execution policy to execute commands
- powershell.exe (PID: 2148)
- powershell.exe (PID: 5188)
- powershell.exe (PID: 5460)
- powershell.exe (PID: 2972)
- powershell.exe (PID: 4060)
- powershell.exe (PID: 1532)
- powershell.exe (PID: 3788)
- powershell.exe (PID: 5476)
- powershell.exe (PID: 1580)
- powershell.exe (PID: 5992)
- powershell.exe (PID: 2348)
- powershell.exe (PID: 6212)
- powershell.exe (PID: 5988)
- powershell.exe (PID: 7136)
- powershell.exe (PID: 1980)
- powershell.exe (PID: 6876)
- powershell.exe (PID: 5348)
- powershell.exe (PID: 7064)
- powershell.exe (PID: 4684)
- powershell.exe (PID: 5188)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 4800)
- pdq-connect-agent.exe (PID: 5468)
- pdq-connect-updater.exe (PID: 6408)
- pdq-connect-agent.exe (PID: 2040)
- WmiApSrv.exe (PID: 7008)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 4032)
Uses RUNDLL32.EXE to load library
- msiexec.exe (PID: 3620)
- msiexec.exe (PID: 3488)
- msiexec.exe (PID: 3756)
- msiexec.exe (PID: 3688)
Executable content was dropped or overwritten
- rundll32.exe (PID: 2040)
- rundll32.exe (PID: 2696)
- rundll32.exe (PID: 5460)
- rundll32.exe (PID: 2040)
- rundll32.exe (PID: 1644)
- pdq-connect-agent.exe (PID: 5468)
- rundll32.exe (PID: 6620)
- rundll32.exe (PID: 3688)
- rundll32.exe (PID: 6648)
- rundll32.exe (PID: 3108)
- rundll32.exe (PID: 4312)
- rundll32.exe (PID: 5240)
- rundll32.exe (PID: 1468)
- rundll32.exe (PID: 4196)
- rundll32.exe (PID: 3392)
- csc.exe (PID: 1128)
- powershell.exe (PID: 5992)
Application launched itself
- msiexec.exe (PID: 4032)
- powershell.exe (PID: 5348)
Starts SC.EXE for service management
- rundll32.exe (PID: 2040)
- rundll32.exe (PID: 6648)
Windows service management via SC.EXE
- sc.exe (PID: 4088)
- sc.exe (PID: 1808)
PDQConnect is probably used for system patching and software deployment
- sc.exe (PID: 4088)
- sc.exe (PID: 1808)
There is functionality for taking screenshot (YARA)
- msiexec.exe (PID: 1356)
The process bypasses the loading of PowerShell profile settings
- pdq-connect-agent.exe (PID: 2040)
- powershell.exe (PID: 5348)
Starts POWERSHELL.EXE for commands execution
- pdq-connect-agent.exe (PID: 2040)
- powershell.exe (PID: 5348)
Creates new GUID (POWERSHELL)
- powershell.exe (PID: 1532)
- powershell.exe (PID: 5992)
The process hide an interactive prompt from the user
- pdq-connect-agent.exe (PID: 2040)
The process hides Powershell's copyright startup banner
- pdq-connect-agent.exe (PID: 2040)
- powershell.exe (PID: 5348)
CSC.EXE is used to compile C# code
- csc.exe (PID: 1128)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 5808)
The process creates files with name similar to system file names
- powershell.exe (PID: 5992)
Detected use of alternative data streams (AltDS)
- powershell.exe (PID: 5992)
Process drops legitimate windows executable
- powershell.exe (PID: 5992)
INFO
Reads security settings of Internet Explorer
- msiexec.exe (PID: 1356)
An automatically generated document
- msiexec.exe (PID: 1356)
Checks proxy server information
- msiexec.exe (PID: 1356)
- slui.exe (PID: 1740)
Reads the computer name
- msiexec.exe (PID: 4032)
- msiexec.exe (PID: 3620)
- msiexec.exe (PID: 3488)
- pdq-connect-agent.exe (PID: 5468)
- msiexec.exe (PID: 3756)
- pdq-connect-updater.exe (PID: 6408)
- msiexec.exe (PID: 3688)
- pdq-connect-agent.exe (PID: 2040)
- DismHost.exe (PID: 5808)
Reads the software policy settings
- msiexec.exe (PID: 1356)
- msiexec.exe (PID: 4032)
- pdq-connect-updater.exe (PID: 6408)
- pdq-connect-agent.exe (PID: 5468)
- pdq-connect-agent.exe (PID: 2040)
- slui.exe (PID: 1740)
Creates files or folders in the user directory
- msiexec.exe (PID: 1356)
Checks supported languages
- msiexec.exe (PID: 4032)
- msiexec.exe (PID: 3620)
- msiexec.exe (PID: 3488)
- pdq-connect-updater.exe (PID: 6408)
- msiexec.exe (PID: 3688)
- pdq-connect-agent.exe (PID: 5468)
- msiexec.exe (PID: 3756)
- pdq-connect-agent.exe (PID: 2040)
- csc.exe (PID: 1128)
- cvtres.exe (PID: 6400)
- DismHost.exe (PID: 5808)
Reads the machine GUID from the registry
- msiexec.exe (PID: 4032)
- csc.exe (PID: 1128)
Manages system restore points
- SrTasks.exe (PID: 2692)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4032)
Create files in a temporary directory
- rundll32.exe (PID: 2040)
- rundll32.exe (PID: 1644)
The sample compiled with english language support
- msiexec.exe (PID: 4032)
- powershell.exe (PID: 5992)
PDQCONNECT has been detected
- msiexec.exe (PID: 3488)
- rundll32.exe (PID: 2040)
- pdq-connect-agent.exe (PID: 5468)
- rundll32.exe (PID: 6648)
- msiexec.exe (PID: 3688)
Creates files in the program directory
- rundll32.exe (PID: 5460)
- pdq-connect-agent.exe (PID: 5468)
- msiexec.exe (PID: 2348)
- msiexec.exe (PID: 5368)
- pdq-connect-agent.exe (PID: 2040)
Creates a software uninstall entry
- msiexec.exe (PID: 4032)
Application based on Rust
- pdq-connect-updater.exe (PID: 6408)
- pdq-connect-agent.exe (PID: 2040)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 1532)
- powershell.exe (PID: 5992)
- powershell.exe (PID: 1580)
- powershell.exe (PID: 7676)
Process checks computer location settings
- pdq-connect-agent.exe (PID: 2040)
Reads Environment values
- pdq-connect-agent.exe (PID: 2040)
- DismHost.exe (PID: 5808)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 1580)
Reads Windows Product ID
- powershell.exe (PID: 5992)
Gets data length (POWERSHELL)
- powershell.exe (PID: 5992)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5992)
- powershell.exe (PID: 2348)
- powershell.exe (PID: 7580)
- powershell.exe (PID: 7136)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | PDQConnectAgent |
| Author: | PDQ.com |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install PDQConnectAgent. |
| Template: | x64;1033 |
| RevisionNumber: | {881D68C5-5E81-49C0-BB0F-FD204AF7CC10} |
| CreateDate: | 2025:07:01 13:52:22 |
| ModifyDate: | 2025:07:01 13:52:22 |
| Pages: | 200 |
| Words: | 2 |
| Software: | WiX Toolset (5.0.0.0) |
| Security: | Read-only recommended |
Total processes
249
Monitored processes
102
Malicious processes
7
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1128 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\WINDOWS\TEMP\c4m2aft2\c4m2aft2.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1244 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1356 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\verfacturaServiMaxnopaga.msi | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1468 | rundll32.exe "C:\WINDOWS\Installer\MSI4CE9.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1658093 148 pdqconnectagent-setup!pdqconnectagent_setup.CustomActions.WriteToken | C:\Windows\System32\rundll32.exe | msiexec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1532 | "powershell.exe" -NoLogo -NonInteractive -NoProfile -ExecutionPolicy Bypass -Command - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | pdq-connect-agent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1580 | "powershell.exe" -NoLogo -NonInteractive -NoProfile -ExecutionPolicy Bypass -Command - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | pdq-connect-agent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1580 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1644 | rundll32.exe "C:\WINDOWS\Installer\MSI355.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1639296 16 WixSharp!WixSharp.ManagedProjectActions.WixSharp_BeforeInstall_Action | C:\Windows\System32\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1740 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1808 | "C:\WINDOWS\system32\sc.exe" start "PDQConnectAgent" | C:\Windows\System32\sc.exe | — | rundll32.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
199 890
Read events
199 270
Write events
457
Delete events
163
Modification events
| (PID) Process: | (4800) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000054276ED08D02DC01C0120000340E0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4800) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000054276ED08D02DC01C0120000300F0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4800) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000568B70D08D02DC01C0120000CC090000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4800) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000568B70D08D02DC01C01200000C190000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4800) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4800000000000000568B70D08D02DC01C0120000340E0000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4800) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4800) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | write | Name: | Element |
Value: 0000000000000000000000000000000006000000000000004800000000000000715E5C2FA985EB1190A89A9B763584210000000000000000745E5C2FA985EB1190A89A9B7635842100000000000000000000000000000000 | |||
| (PID) Process: | (4800) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4800) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | write | Name: | Element |
Value: \EFI\Microsoft\Boot\bootmgfw.efi | |||
| (PID) Process: | (4800) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
126
Suspicious files
44
Text files
138
Unknown types
37
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4032 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 4032 | msiexec.exe | C:\Windows\Installer\18f538.msi | — | |
MD5:— | SHA256:— | |||
| 1356 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | der | |
MD5:B528D5451B4F8BDE5C8461D21502CA31 | SHA256:18B286BD107C29DEA7F7B1D8BAD901C4AE823B410DA4293735BAD1CDE112C571 | |||
| 1356 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C8E534EE129F27D55460CE17FD628216_8DBAD5A433D1F9275321E076E8B744D4 | binary | |
MD5:C4BFE32F7AB90A9B5C1A4B2531C08B74 | SHA256:367E2642279EC116D951C5EFE0E8C48CC54BBD44EDA6101E8679A904D1E00B76 | |||
| 1356 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C8E534EE129F27D55460CE17FD628216_8DBAD5A433D1F9275321E076E8B744D4 | der | |
MD5:47E5A098445071AD9C43F84FBAD96499 | SHA256:726E4676509D1E42D9A90D277EB22471EAE88B485EF4EA2D0768754E1F2F19D8 | |||
| 4032 | msiexec.exe | C:\Windows\Installer\MSI355.tmp | executable | |
MD5:5936ADD89D2AF213C12316426EB54523 | SHA256:6C79392F615F66A5DA20076267CB68DA85FA800A74267B3CE7BDC07DB8224768 | |||
| 2040 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\SFXCAB7F77344EF4781EB834D1E2E7A836C47\pdqconnectagent-setup.exe | executable | |
MD5:1472372D4D702A45135BA18EB55A043D | SHA256:1A6585711DB9CCFA6E714DD531559F2F9A50081D6421BDBC0031B1FEF78C4814 | |||
| 4032 | msiexec.exe | C:\Windows\Installer\MSI17D.tmp | executable | |
MD5:5936ADD89D2AF213C12316426EB54523 | SHA256:6C79392F615F66A5DA20076267CB68DA85FA800A74267B3CE7BDC07DB8224768 | |||
| 2040 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\SFXCAB7F77344EF4781EB834D1E2E7A836C47\CustomAction.config | xml | |
MD5:C9C40AF1656F8531EAA647CACEB1E436 | SHA256:1A67F60962CA1CBF19873B62A8518EFE8C701A09CD609AF4C50ECC7F0B468BB8 | |||
| 1644 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\SFXCA859B17441F4DB2CAB772633EC08E1720\WixSharp.dll | executable | |
MD5:86E26888F15860835A2FF1423F25A513 | SHA256:4A05C81E1116C4CAC7269113FE50F3E20F9D247F20D6324F62B5C62A5D7B92A6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
45
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1356 | msiexec.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
1356 | msiexec.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEA5NZ%2FZDFskqO3oXzEaXao8%3D | unknown | — | — | whitelisted |
1356 | msiexec.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRhtVltVOu8OqBzmsd%2B%2FeFfks3xTQQUvGsiZZ2MaObmHgXx2HIl1LjgSMACEAvcoEuhCK%2FAlHGPdKmo6gs%3D | unknown | — | — | whitelisted |
2460 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2728 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2728 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 72.246.169.163:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
4088 | WmiPrvSE.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3480 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1356 | msiexec.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2460 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2460 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
6292 | svchost.exe | 184.30.18.9:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
app.pdq.com |
| whitelisted |
pdqinstallers.e9d69694c3d8f7465fd531512c22bd0f.r2.cloudflarestorage.com |
| malicious |
slscr.update.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
powershell.exe | PID=5992 TID=3556 DismApi.dll: - DismInitializeInternal
|
powershell.exe | PID=5992 TID=3556 DismApi.dll: <----- Starting DismApi.dll session -----> - DismInitializeInternal
|
powershell.exe | PID=5992 TID=3556 DismApi.dll: - DismInitializeInternal
|
powershell.exe | PID=5992 TID=3556 DismApi.dll: Host machine information: OS Version=10.0.19045, Running architecture=amd64, Number of processors=4 - DismInitializeInternal
|
powershell.exe | PID=5992 TID=3556 DismApi.dll: API Version 10.0.19041.3758 - DismInitializeInternal
|
powershell.exe | PID=5992 TID=3556 DismApi.dll: Parent process command line: "powershell.exe" -NoLogo -NonInteractive -NoProfile -ExecutionPolicy Bypass -Command - - DismInitializeInternal
|
powershell.exe | PID=5992 TID=3556 Enter DismInitializeInternal - DismInitializeInternal
|
powershell.exe | PID=5992 TID=3556 Input parameters: LogLevel: 2, LogFilePath: C:\WINDOWS\Logs\DISM\dism.log, ScratchDirectory: (null) - DismInitializeInternal
|
powershell.exe | PID=5992 TID=3556 Initialized GlobalConfig - DismInitializeInternal
|
powershell.exe | PID=5992 TID=3556 Initialized SessionTable - DismInitializeInternal
|