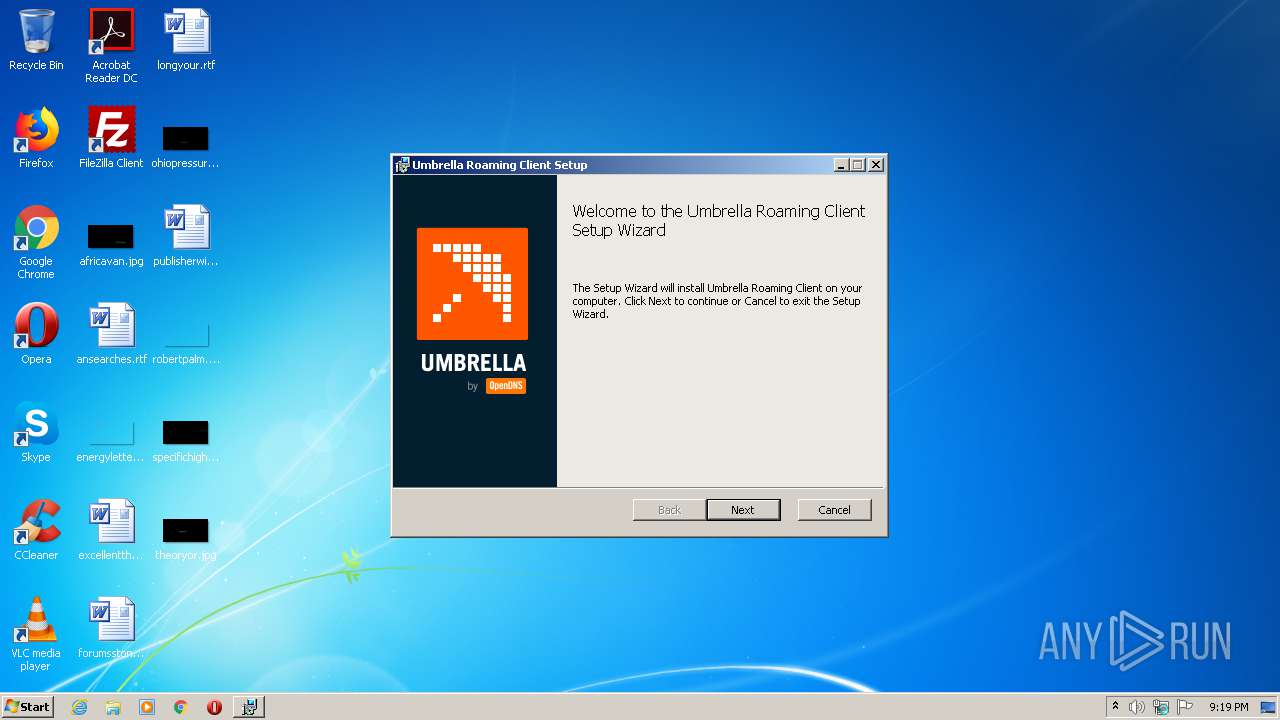
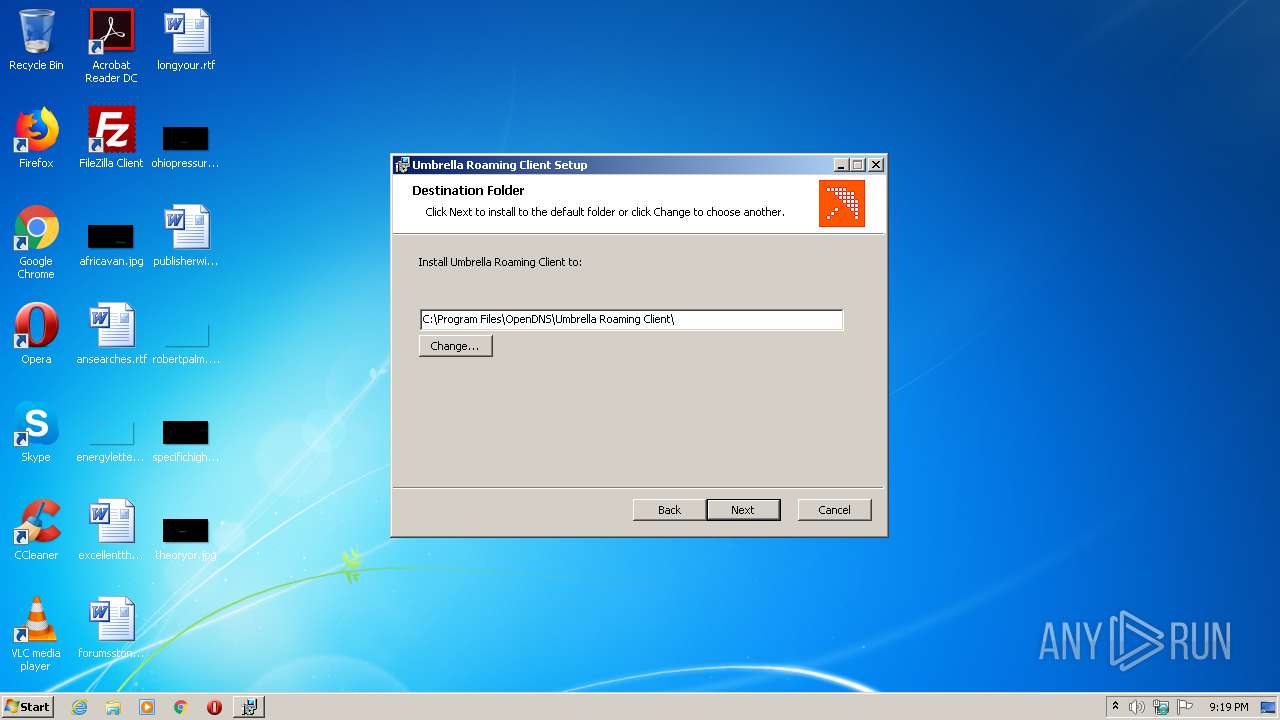
| File name: | Setup.msi |
| Full analysis: | https://app.any.run/tasks/3a4a9a94-6f8e-439f-b301-c6c605007ba3 |
| Verdict: | Malicious activity |
| Analysis date: | March 25, 2021, 21:19:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Code page: 1252, Title: Installation Database, Subject: Umbrella Roaming Client, Author: OpenDNS, Keywords: Installer, Comments: This installer database contains the logic and data required to install Umbrella Roaming Client., Template: Intel;1033, Revision Number: {91AA28DE-EFFA-4A8C-A3EB-79C704A955A4}, Create Time/Date: Wed Dec 16 14:20:54 2020, Last Saved Time/Date: Wed Dec 16 14:20:54 2020, Number of Pages: 200, Number of Words: 2, Name of Creating Application: Windows Installer XML Toolset (3.11.2.4516), Security: 2 |
| MD5: | 19C4FE4C683E133D0DCC14E238A399D0 |
| SHA1: | 337806494C9A49F718ABCD4AFFBC293D666A65A0 |
| SHA256: | 301DB85270B118F294AAC15B1428AAAAD65903C71D544A02E5B0C0AD108956DD |
| SSDEEP: | 49152:6n+alKePa2M6yOK1isJrS9xv9aEl+1E1nUIox/21URQw9uP:6nxKeC2BK80y5Mq+5Nx6UX9u |
MALICIOUS
Loads dropped or rewritten executable
- rundll32.exe (PID: 3736)
- rundll32.exe (PID: 1024)
- ERCService.exe (PID: 3512)
- ERCInterface.exe (PID: 2604)
- rundll32.exe (PID: 4084)
- rundll32.exe (PID: 1328)
Drops executable file immediately after starts
- rundll32.exe (PID: 3736)
- rundll32.exe (PID: 1024)
- rundll32.exe (PID: 1328)
Writes to a start menu file
- msiexec.exe (PID: 2208)
Application was dropped or rewritten from another process
- ERCService.exe (PID: 3512)
- ERCInterface.exe (PID: 2604)
- UmbrellaDiagnostic.exe (PID: 2616)
- RemoveOpenDNSBFEFilters.exe (PID: 2928)
Changes settings of System certificates
- MsiExec.exe (PID: 2712)
SUSPICIOUS
Executable content was dropped or overwritten
- rundll32.exe (PID: 3736)
- msiexec.exe (PID: 1656)
- rundll32.exe (PID: 1024)
- msiexec.exe (PID: 2208)
- rundll32.exe (PID: 1328)
Drops a file with too old compile date
- rundll32.exe (PID: 3736)
- rundll32.exe (PID: 1328)
Uses RUNDLL32.EXE to load library
- MsiExec.exe (PID: 2796)
- MsiExec.exe (PID: 2096)
- MsiExec.exe (PID: 2712)
Drops a file that was compiled in debug mode
- rundll32.exe (PID: 3736)
- rundll32.exe (PID: 1024)
- msiexec.exe (PID: 2208)
- rundll32.exe (PID: 1328)
Executed as Windows Service
- vssvc.exe (PID: 2228)
- ERCService.exe (PID: 3512)
Creates a directory in Program Files
- msiexec.exe (PID: 2208)
Creates files in the program directory
- rundll32.exe (PID: 4084)
- ERCService.exe (PID: 3512)
Creates files in the Windows directory
- ERCService.exe (PID: 3512)
- UmbrellaDiagnostic.exe (PID: 2616)
Reads internet explorer settings
- ERCInterface.exe (PID: 2604)
Uses NETSTAT.EXE to discover network connections
- UmbrellaDiagnostic.exe (PID: 2616)
Uses TASKLIST.EXE to query information about running processes
- UmbrellaDiagnostic.exe (PID: 2616)
Uses IPCONFIG.EXE to discover IP address
- UmbrellaDiagnostic.exe (PID: 2616)
Uses SYSTEMINFO.EXE to read environment
- UmbrellaDiagnostic.exe (PID: 2616)
Starts CMD.EXE for commands execution
- UmbrellaDiagnostic.exe (PID: 2616)
- netstat.exe (PID: 272)
Checks for external IP
- nslookup.exe (PID: 1976)
- nslookup.exe (PID: 996)
Executes PowerShell scripts
- UmbrellaDiagnostic.exe (PID: 2616)
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 3952)
INFO
Application launched itself
- msiexec.exe (PID: 2208)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 2096)
- MsiExec.exe (PID: 2796)
- MsiExec.exe (PID: 2712)
Low-level read access rights to disk partition
- vssvc.exe (PID: 2228)
Creates files in the program directory
- msiexec.exe (PID: 2208)
Creates a software uninstall entry
- msiexec.exe (PID: 2208)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | Umbrella Roaming Client |
| Author: | OpenDNS |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install Umbrella Roaming Client. |
| Template: | Intel;1033 |
| RevisionNumber: | {91AA28DE-EFFA-4A8C-A3EB-79C704A955A4} |
| CreateDate: | 2020:12:16 14:20:54 |
| ModifyDate: | 2020:12:16 14:20:54 |
| Pages: | 200 |
| Words: | 2 |
| Software: | Windows Installer XML Toolset (3.11.2.4516) |
| Security: | Read-only recommended |
Total processes
169
Monitored processes
72
Malicious processes
11
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
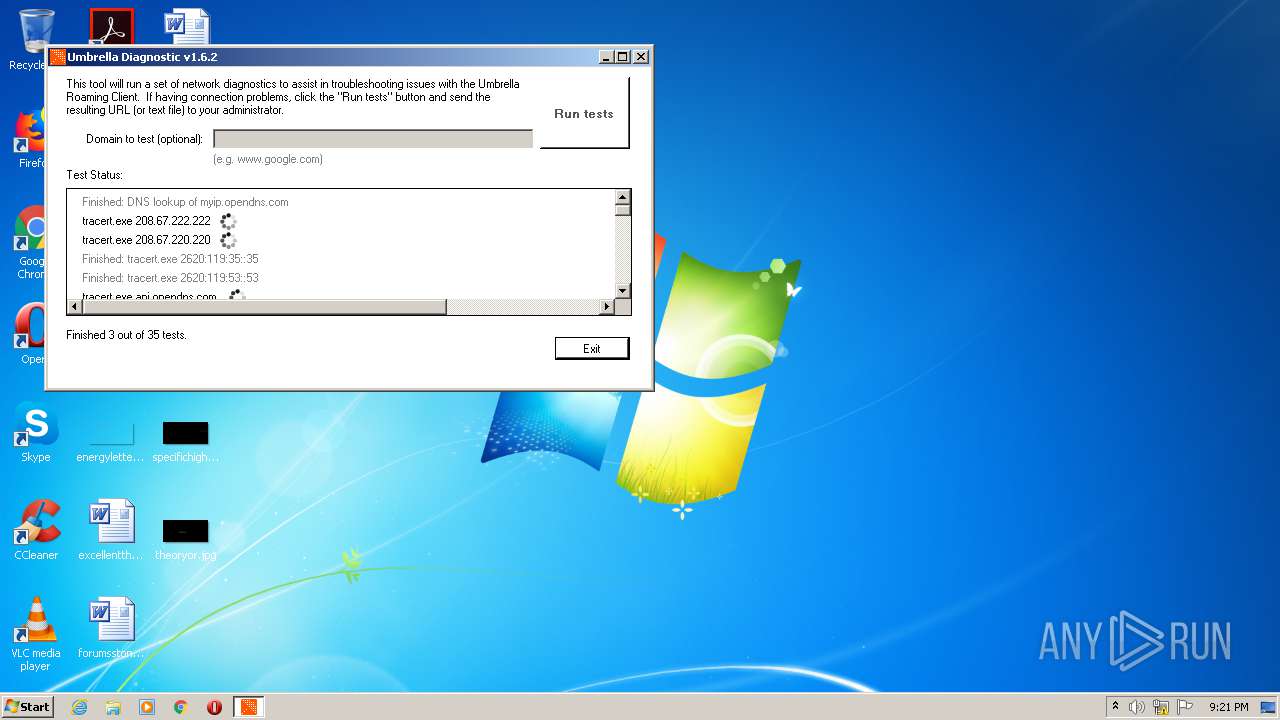
| 120 | "C:\Windows\system32\nslookup.exe" -timeout=10 -type=txt -port=5353 debug.opendns.com. 2620:119:53::53 | C:\Windows\system32\nslookup.exe | — | UmbrellaDiagnostic.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: nslookup Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 184 | "C:\Windows\system32\ipconfig.exe" /all | C:\Windows\system32\ipconfig.exe | — | UmbrellaDiagnostic.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IP Configuration Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 272 | "C:\Windows\system32\netstat.exe" -rn | C:\Windows\system32\netstat.exe | — | UmbrellaDiagnostic.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Netstat Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 536 | "C:\Windows\system32\tracert.exe" 2620:119:35::35 | C:\Windows\system32\tracert.exe | — | UmbrellaDiagnostic.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Traceroute Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 588 | "C:\Windows\system32\tracert.exe" 2620:119:53::53 | C:\Windows\system32\tracert.exe | — | UmbrellaDiagnostic.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Traceroute Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 632 | "C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe" -Command "(New-Object System.Net.WebClient).DownloadString(\"http://67.215.70.91:8081/malware.htm\")" | C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe | UmbrellaDiagnostic.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 924 | "C:\Windows\system32\ping.exe" -n 5 www.opendns.com | C:\Windows\system32\ping.exe | — | UmbrellaDiagnostic.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 928 | "C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe" -Command "(New-Object System.Net.WebClient).DownloadString(\"http://67.215.70.91:8081/favicon.ico\")" | C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe | UmbrellaDiagnostic.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 996 | "C:\Windows\system32\nslookup.exe" -timeout=10 myip.opendns.com. 208.67.220.220 | C:\Windows\system32\nslookup.exe | UmbrellaDiagnostic.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: nslookup Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1024 | rundll32.exe "C:\Windows\Installer\MSI4782.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_345984 8 InstallerCustomActions!InstallerCustomActions.CustomActions.ReadOrgInfo | C:\Windows\system32\rundll32.exe | MsiExec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 268
Read events
1 844
Write events
409
Delete events
15
Modification events
| (PID) Process: | (1656) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1656) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13C\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\p2pcollab.dll,-8042 |
Value: Peer to Peer Trust | |||
| (PID) Process: | (1656) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13C\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\qagentrt.dll,-10 |
Value: System Health Authentication | |||
| (PID) Process: | (1656) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13C\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dnsapi.dll,-103 |
Value: Domain Name System (DNS) Server Trust | |||
| (PID) Process: | (1656) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13C\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\fveui.dll,-843 |
Value: BitLocker Drive Encryption | |||
| (PID) Process: | (1656) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13C\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\fveui.dll,-844 |
Value: BitLocker Data Recovery Agent | |||
| (PID) Process: | (2208) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 400000000000000060BBB9A5BC21D701A0080000C0060000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2208) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 400000000000000060BBB9A5BC21D701A0080000C0060000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2228) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000BC5414A6BC21D701B4080000E0040000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2228) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000BC5414A6BC21D701B4080000FC000000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
32
Suspicious files
5
Text files
13
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1656 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIC1B7.tmp | — | |
MD5:— | SHA256:— | |||
| 2208 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 2208 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF1630988161204F55.TMP | — | |
MD5:— | SHA256:— | |||
| 2208 | msiexec.exe | C:\Windows\Installer\MSI46C5.tmp | — | |
MD5:— | SHA256:— | |||
| 2228 | vssvc.exe | C: | — | |
MD5:— | SHA256:— | |||
| 1024 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI4782.tmp-\log4net.dll | — | |
MD5:— | SHA256:— | |||
| 1024 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI4782.tmp-\NETWORKLIST.dll | — | |
MD5:— | SHA256:— | |||
| 1024 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI4782.tmp-\stdole.dll | — | |
MD5:— | SHA256:— | |||
| 1024 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI4782.tmp-\CustomAction.config | — | |
MD5:— | SHA256:— | |||
| 2208 | msiexec.exe | C:\Windows\Installer\MSI490A.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
42
DNS requests
54
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3568 | powershell.exe | GET | — | 67.215.70.91:80 | http://67.215.70.91/malware.htm | US | — | — | unknown |
2268 | powershell.exe | GET | — | 67.215.70.91:80 | http://67.215.70.91/favicon.ico | US | — | — | unknown |
4076 | powershell.exe | GET | — | 67.215.70.92:80 | http://67.215.70.92/some/page | US | — | — | unknown |
2616 | UmbrellaDiagnostic.exe | GET | — | 67.215.69.69:80 | http://67.215.69.69/ | US | — | — | unknown |
2616 | UmbrellaDiagnostic.exe | GET | 302 | 146.112.196.76:80 | http://bpb.opendns.com/monitor/ | DE | html | 127 b | whitelisted |
3592 | powershell.exe | GET | 200 | 146.112.62.40:80 | http://146.112.62.40/unproxied.html | unknown | html | 1.10 Kb | malicious |
3860 | powershell.exe | GET | 200 | 146.112.62.40:8081 | http://146.112.62.40:8081/favicon.ico | unknown | image | 5.30 Kb | malicious |
3496 | powershell.exe | GET | 200 | 146.112.62.40:80 | http://146.112.62.40/favicon.ico | unknown | image | 5.30 Kb | malicious |
1460 | powershell.exe | GET | 302 | 146.112.62.39:80 | http://146.112.62.39/some/page | unknown | html | 161 b | unknown |
3632 | powershell.exe | GET | 302 | 146.112.62.40:8081 | http://146.112.62.40:8081/malware.htm | unknown | html | 161 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2608 | nslookup.exe | 208.67.220.220:53 | — | OpenDNS, LLC | US | suspicious |
1976 | nslookup.exe | 208.67.222.222:53 | — | OpenDNS, LLC | US | malicious |
2768 | nslookup.exe | 208.67.220.220:53 | — | OpenDNS, LLC | US | suspicious |
996 | nslookup.exe | 208.67.220.220:53 | — | OpenDNS, LLC | US | suspicious |
3828 | nslookup.exe | 4.2.2.1:53 | — | Level 3 Communications, Inc. | US | unknown |
3864 | nslookup.exe | 192.33.4.12:53 | — | Cogent Communications | US | unknown |
1764 | nslookup.exe | 208.67.222.222:53 | — | OpenDNS, LLC | US | malicious |
1376 | nslookup.exe | 208.67.222.222:53 | — | OpenDNS, LLC | US | malicious |
3632 | powershell.exe | 146.112.62.40:8081 | — | OpenDNS, LLC | — | malicious |
3592 | powershell.exe | 146.112.62.40:80 | — | OpenDNS, LLC | — | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
myip.opendns.com |
| shared |
222.222.67.208.in-addr.arpa |
| unknown |
2.100.168.192.in-addr.arpa |
| whitelisted |
220.220.67.208.in-addr.arpa |
| unknown |
5.3.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.5.3.0.0.9.1.1.0.0.2.6.2.ip6.arpa |
| unknown |
3.5.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.3.5.0.0.9.1.1.0.0.2.6.2.ip6.arpa |
| unknown |
api.opendns.com |
| suspicious |
bpb.opendns.com |
| whitelisted |
block.opendns.com |
| unknown |
hit-adult.opendns.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1048 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup Domain (myip.opendns .com in DNS lookup) |
1976 | nslookup.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup Domain (myip.opendns .com in DNS lookup) |
996 | nslookup.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup Domain (myip.opendns .com in DNS lookup) |
1976 | nslookup.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup Domain (myip.opendns .com in DNS lookup) |
996 | nslookup.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup Domain (myip.opendns .com in DNS lookup) |
Process | Message |
|---|---|
ERCService.exe | OpenDNS-ERC: 2021-03-25 21:20:31 [3512] [INFO ] < 4> Start logging...
|
ERCService.exe | OpenDNS-ERC: 2021-03-25 21:20:31 [3512] [INFO ] < 4> ***** Starting ERC Service version 2.2.580
|
ERCService.exe | OpenDNS-ERC: 2021-03-25 21:20:31 [3512] [FATAL] < 4> Fatal Output Enabled
|
ERCService.exe | OpenDNS-ERC: 2021-03-25 21:20:31 [3512] [ERROR] < 4> Error Output Enabled
|
ERCService.exe | OpenDNS-ERC: 2021-03-25 21:20:31 [3512] [WARN ] < 4> Warn Output Enabled
|
ERCService.exe | OpenDNS-ERC: 2021-03-25 21:20:31 [3512] [NOTICE] < 4> Notice Output Enabled
|
ERCService.exe | OpenDNS-ERC: 2021-03-25 21:20:31 [3512] [INFO ] < 4> Info Output Enabled
|
ERCService.exe | OpenDNS-ERC: 2021-03-25 21:20:31 [3512] [DEBUG] < 4> Debug Output Enabled
|
ERCService.exe | OpenDNS-ERC: 2021-03-25 21:20:32 [3512] [INFO ] < 4> udpating ACL on C:\ProgramData\OpenDNS\ERC
|
ERCService.exe | OpenDNS-ERC: 2021-03-25 21:20:32 [3512] [DEBUG] < 4> NicWatcher: NIC cache system not running, getting all NICs without using cache.
|