| URL: | https://www.gyan.dev/ffmpeg/builds/ffmpeg-git-essentials.7z |
| Full analysis: | https://app.any.run/tasks/53df6568-fa1f-4bbb-b8b7-5fd441ee5b92 |
| Verdict: | Malicious activity |
| Analysis date: | December 10, 2024, 18:01:58 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | D95620E948A180AFF9C25891023E6552 |
| SHA1: | C7290D1746CE49FEB42E89003A1B6E88118069C1 |
| SHA256: | 30186161B2AB1F66D9F56F6A1B18E39B8392A6E548B40B61775F299242BB7DC5 |
| SSDEEP: | 3:N8DSL0ATuoKwIPVkf:2OLbgo |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops python dynamic module
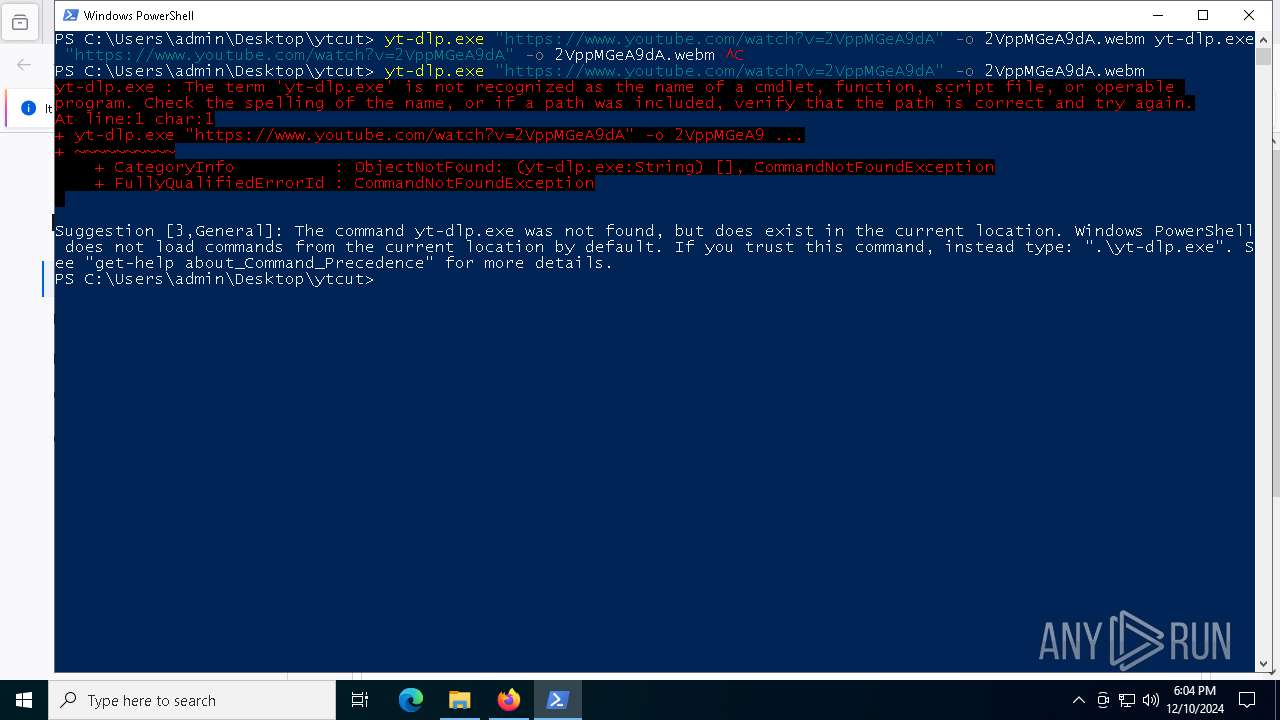
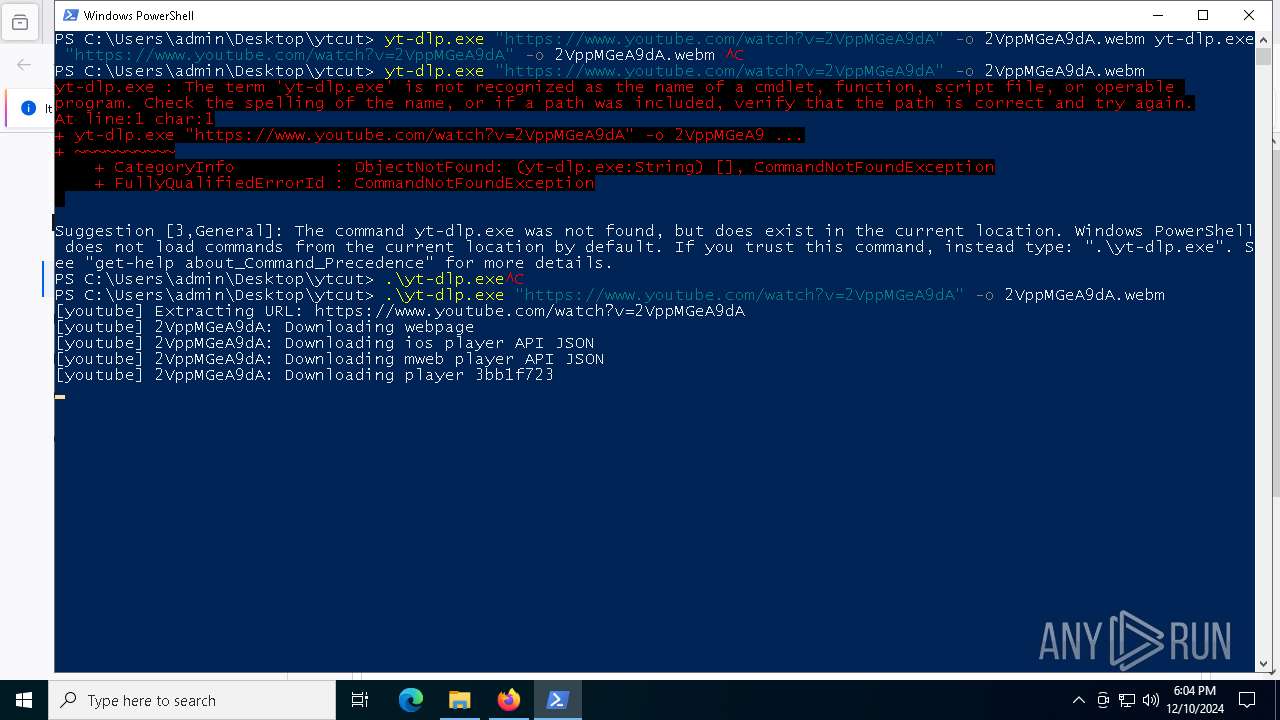
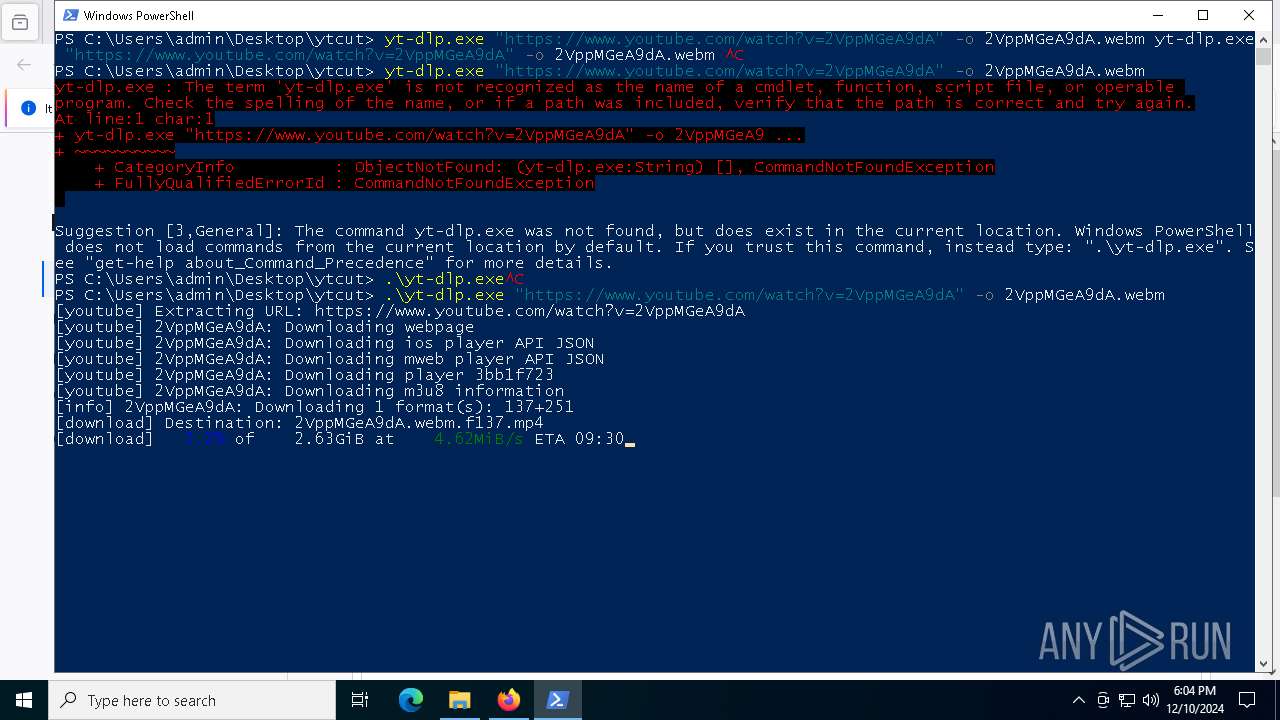
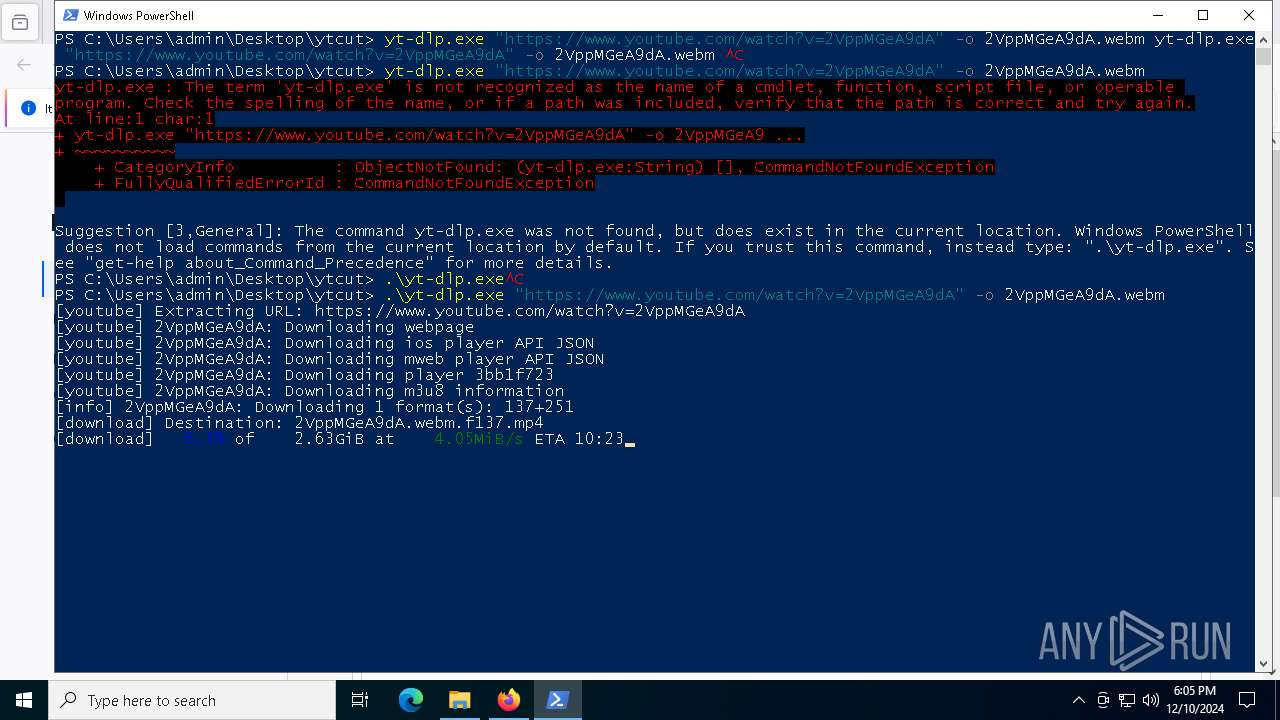
- yt-dlp.exe (PID: 6404)
Process drops legitimate windows executable
- yt-dlp.exe (PID: 6404)
Executable content was dropped or overwritten
- yt-dlp.exe (PID: 6404)
The process drops C-runtime libraries
- yt-dlp.exe (PID: 6404)
Application launched itself
- yt-dlp.exe (PID: 6404)
Loads Python modules
- yt-dlp.exe (PID: 5748)
Starts CMD.EXE for commands execution
- yt-dlp.exe (PID: 5748)
Found regular expressions for crypto-addresses (YARA)
- yt-dlp.exe (PID: 5748)
INFO
The process uses the downloaded file
- powershell.exe (PID: 6196)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6196)
Checks current location (POWERSHELL)
- powershell.exe (PID: 6196)
Create files in a temporary directory
- yt-dlp.exe (PID: 6404)
The sample compiled with english language support
- yt-dlp.exe (PID: 6404)
Checks supported languages
- yt-dlp.exe (PID: 5748)
- ffmpeg.exe (PID: 7704)
Reads the machine GUID from the registry
- yt-dlp.exe (PID: 5748)
Checks operating system version
- yt-dlp.exe (PID: 5748)
Checks proxy server information
- yt-dlp.exe (PID: 5748)
PyInstaller has been detected (YARA)
- yt-dlp.exe (PID: 5748)
- yt-dlp.exe (PID: 6404)
Reads the computer name
- yt-dlp.exe (PID: 5748)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
145
Monitored processes
9
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3612 | C:\WINDOWS\system32\cmd.exe /c "ver" | C:\Windows\System32\cmd.exe | — | yt-dlp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3984 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4136 | C:\WINDOWS\system32\cmd.exe /c "ver" | C:\Windows\System32\cmd.exe | — | yt-dlp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5576 | C:\WINDOWS\system32\cmd.exe /c "ver" | C:\Windows\System32\cmd.exe | — | yt-dlp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
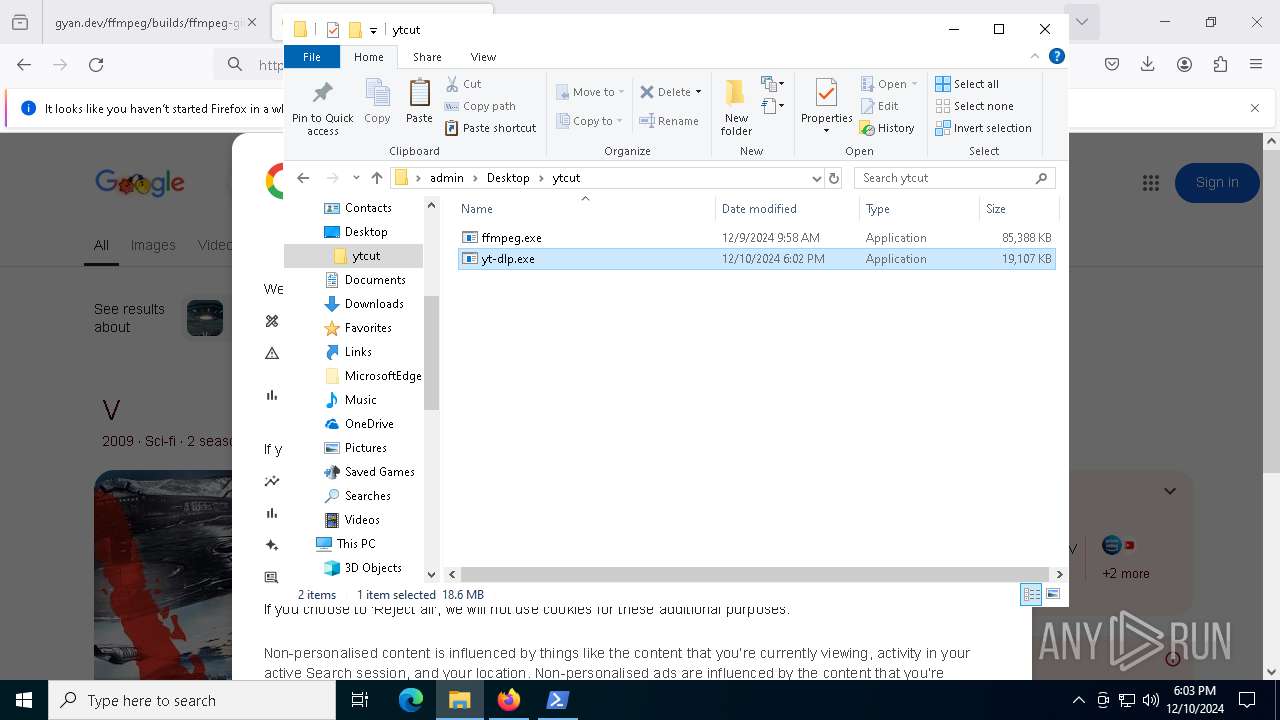
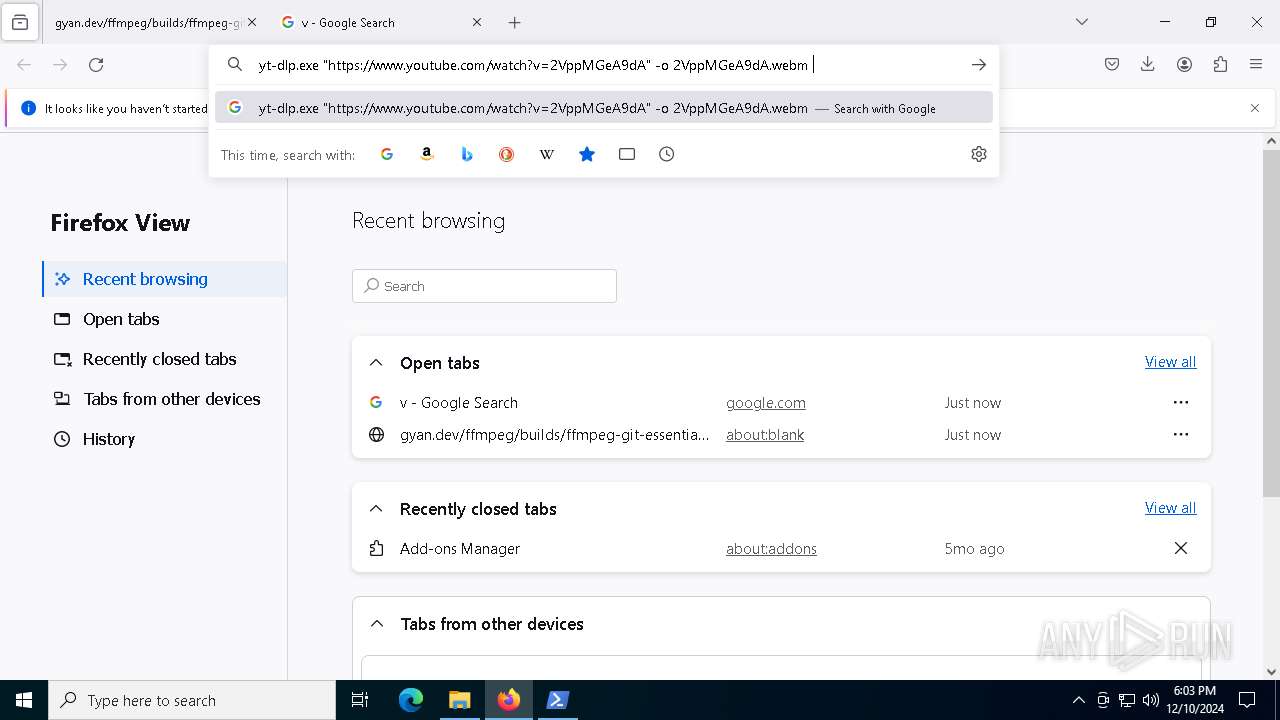
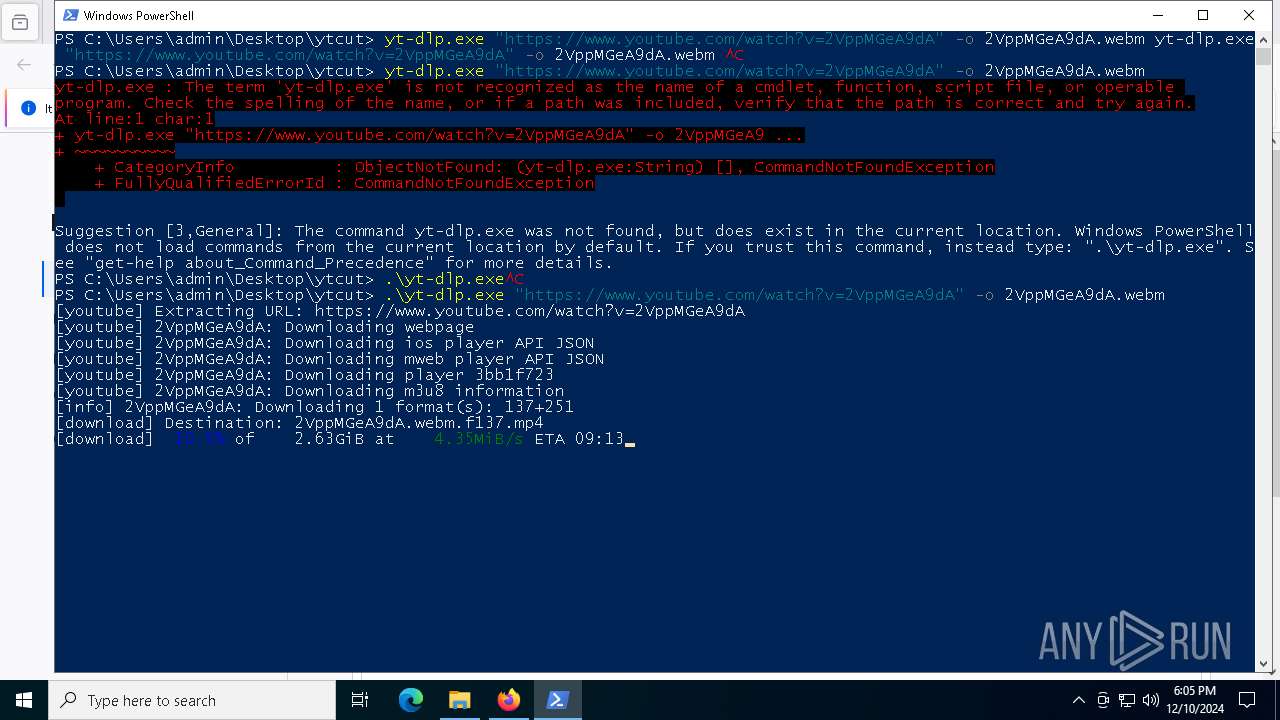
| 5748 | "C:\Users\admin\Desktop\ytcut\yt-dlp.exe" https://www.youtube.com/watch?v=2VppMGeA9dA -o 2VppMGeA9dA.webm | C:\Users\admin\Desktop\ytcut\yt-dlp.exe | yt-dlp.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6196 | "PowerShell.exe" -noexit -command Set-Location -literalPath 'C:\Users\admin\Desktop\ytcut' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6404 | "C:\Users\admin\Desktop\ytcut\yt-dlp.exe" https://www.youtube.com/watch?v=2VppMGeA9dA -o 2VppMGeA9dA.webm | C:\Users\admin\Desktop\ytcut\yt-dlp.exe | powershell.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 7704 | ffmpeg -bsfs | C:\Users\admin\Desktop\ytcut\ffmpeg.exe | — | yt-dlp.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 8024 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\ffmpeg-2024-12-09-git-d21134313f-essentials_build.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
8 437
Read events
8 403
Write events
21
Delete events
13
Modification events
| (PID) Process: | (8024) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (8024) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (8024) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (8024) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\ffmpeg-2024-12-09-git-d21134313f-essentials_build.7z | |||
| (PID) Process: | (8024) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (8024) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (8024) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (8024) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (8024) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (8024) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
116
Suspicious files
11
Text files
26
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 8024 | WinRAR.exe | C:\Users\admin\Desktop\ytcut\ffmpeg.exe | — | |
MD5:— | SHA256:— | |||
| 6196 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt | text | |
MD5:16B920DC9B3B830F07496308DC8E6CCC | SHA256:69EB04723CCFB919047F6C6DDFB32EC66973047306234CC4FD02429D994472BC | |||
| 6196 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\YAQOJA2F0W155A8L1A7A.temp | binary | |
MD5:26AE7DD7A0BAD3A2DEF2F4A2ED574A38 | SHA256:F4C2D6FB3F3F059186C4DB3CED0AFB6E43146CD4939B68C42CE045EA02A3FE57 | |||
| 6404 | yt-dlp.exe | C:\Users\admin\AppData\Local\Temp\_MEI64042\Cryptodome\Cipher\_raw_aes.pyd | executable | |
MD5:E306365BDC8D15B2F477E5AF252D0B59 | SHA256:2DCAC73EA3240A008D115BAC0EA4D7C65C8162676AB30BCAF7527C22B98B4929 | |||
| 6196 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_hyoh4upi.qxb.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6404 | yt-dlp.exe | C:\Users\admin\AppData\Local\Temp\_MEI64042\Cryptodome\Cipher\_raw_aesni.pyd | executable | |
MD5:973F11DE023C9337F35F9BB55C6154A6 | SHA256:483758336267F8842F5432BB83300EA0FCB49C4E0B29962CBD7F27B1C3DFC56A | |||
| 6404 | yt-dlp.exe | C:\Users\admin\AppData\Local\Temp\_MEI64042\Cryptodome\Cipher\_raw_blowfish.pyd | executable | |
MD5:F86637FA9E2246C36B6FFB90CA83E66C | SHA256:933330BD2D55DE985B45BDD12B99291B4507C830CD6CC9E917CEDD1E49E878EC | |||
| 6404 | yt-dlp.exe | C:\Users\admin\AppData\Local\Temp\_MEI64042\Cryptodome\Cipher\_raw_cast.pyd | executable | |
MD5:AC98B10064264B49DE13F66E60CD47B5 | SHA256:8621AC7A3E09367BB0C529FDD3D178F20EDFA193FE0D19A02DE424A6BBA45229 | |||
| 6404 | yt-dlp.exe | C:\Users\admin\AppData\Local\Temp\_MEI64042\Cryptodome\Cipher\_ARC4.pyd | executable | |
MD5:F3A0DEF1BA9F7CF5DA771F5E7C29CA3F | SHA256:362C42BD62E5751E9B647BD575D483CC510DC862AB6098E6893EDCF3F44A567E | |||
| 6404 | yt-dlp.exe | C:\Users\admin\AppData\Local\Temp\_MEI64042\Cryptodome\Cipher\_raw_arc2.pyd | executable | |
MD5:31F8353B80EA438AA705A7986DF24ED3 | SHA256:89A51C145166DD24CF83D358ADE292B23F20B94BE783D5FE33A9DA2D7F2C14EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
48
TCP/UDP connections
125
DNS requests
163
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.24.77.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4024 | svchost.exe | GET | 200 | 184.24.77.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4024 | svchost.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
— | — | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
— | — | POST | 200 | 2.16.206.143:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
— | — | POST | 200 | 2.16.206.143:80 | http://e6.o.lencr.org/ | unknown | — | — | whitelisted |
— | — | POST | 200 | 142.250.181.227:80 | http://o.pki.goog/s/wr3/yvU | unknown | — | — | whitelisted |
— | — | POST | 200 | 2.16.206.143:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.24.77.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4024 | svchost.exe | 184.24.77.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.37.237.227:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4024 | svchost.exe | 23.37.237.227:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.16.204.160:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.218.210.69:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
www.gyan.dev |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
gyan.nfshost.com |
| unknown |