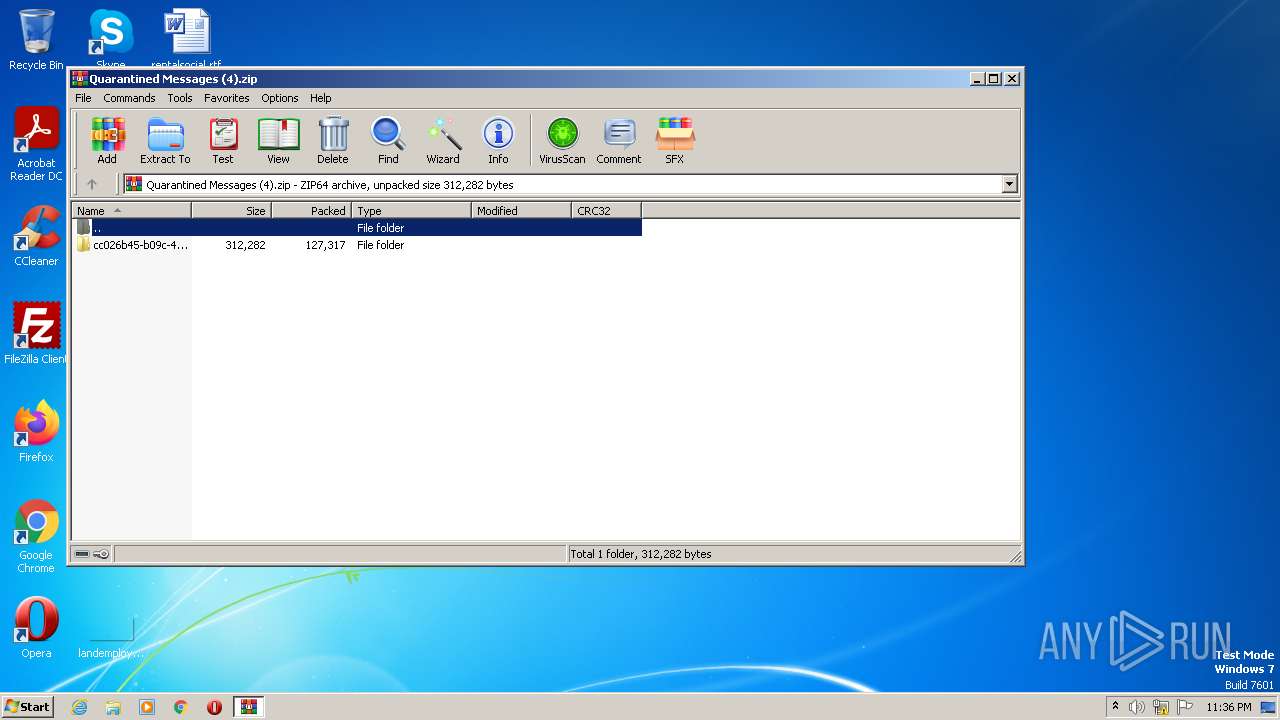
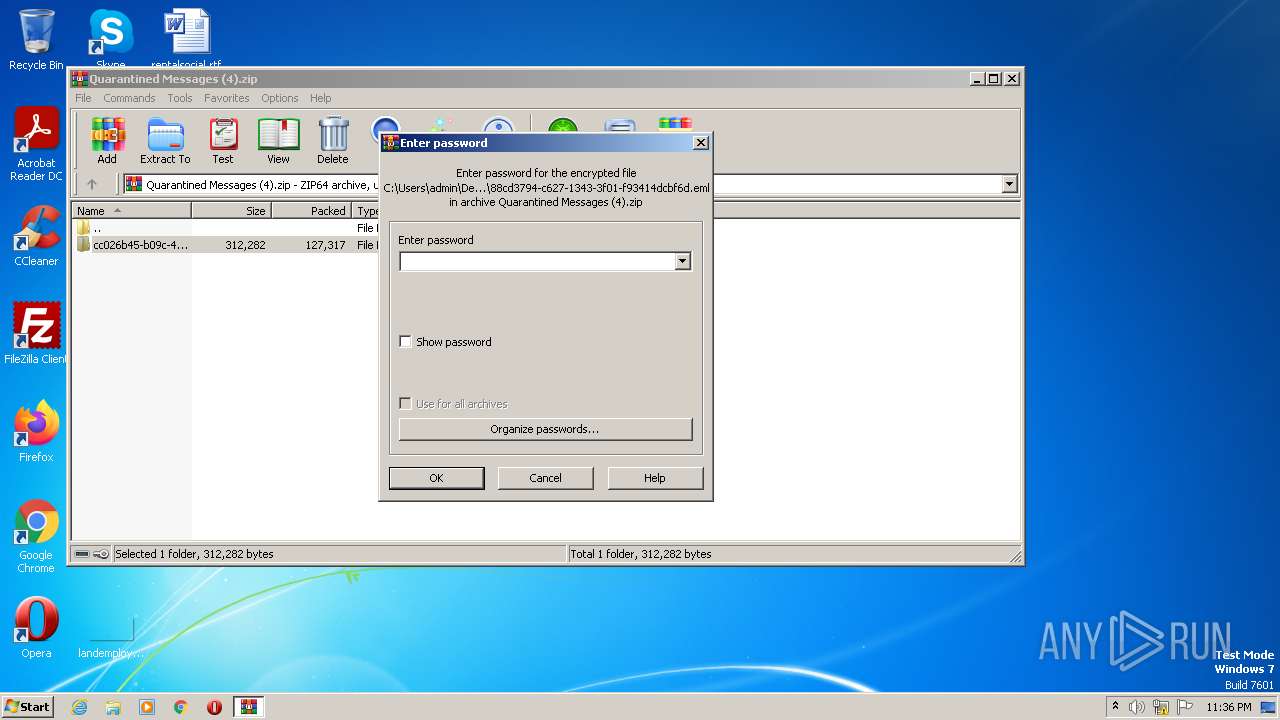
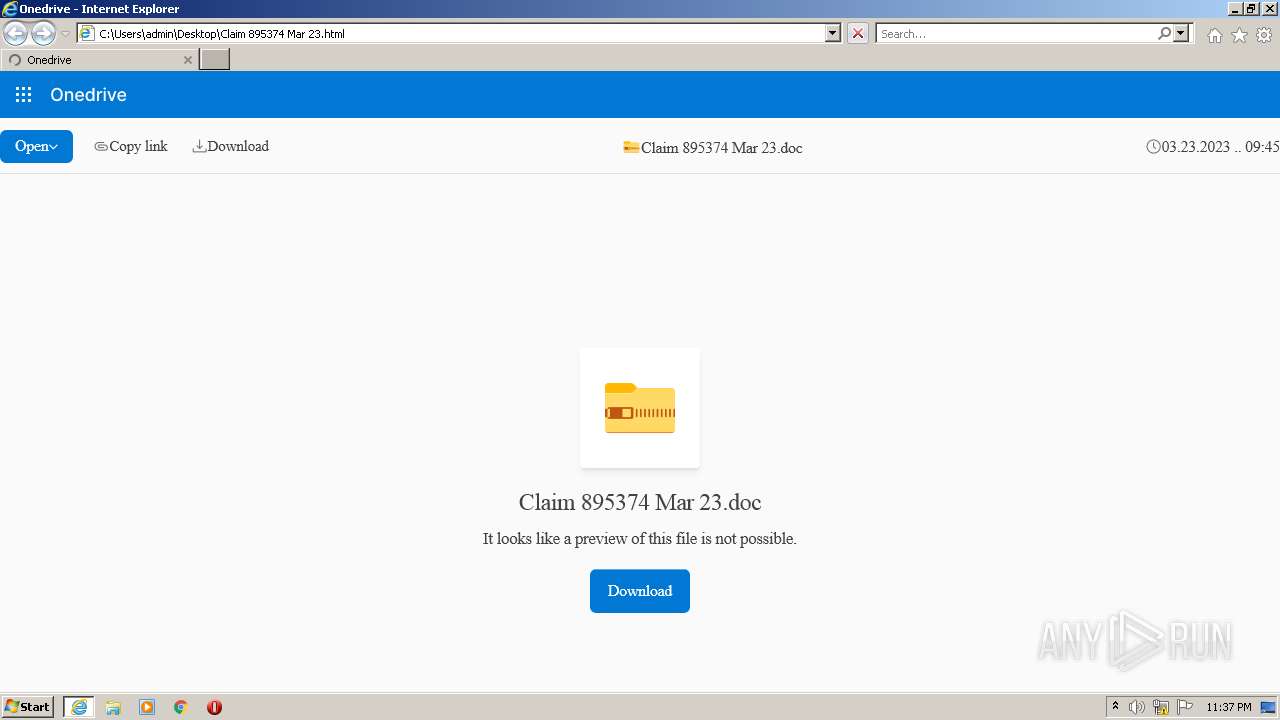
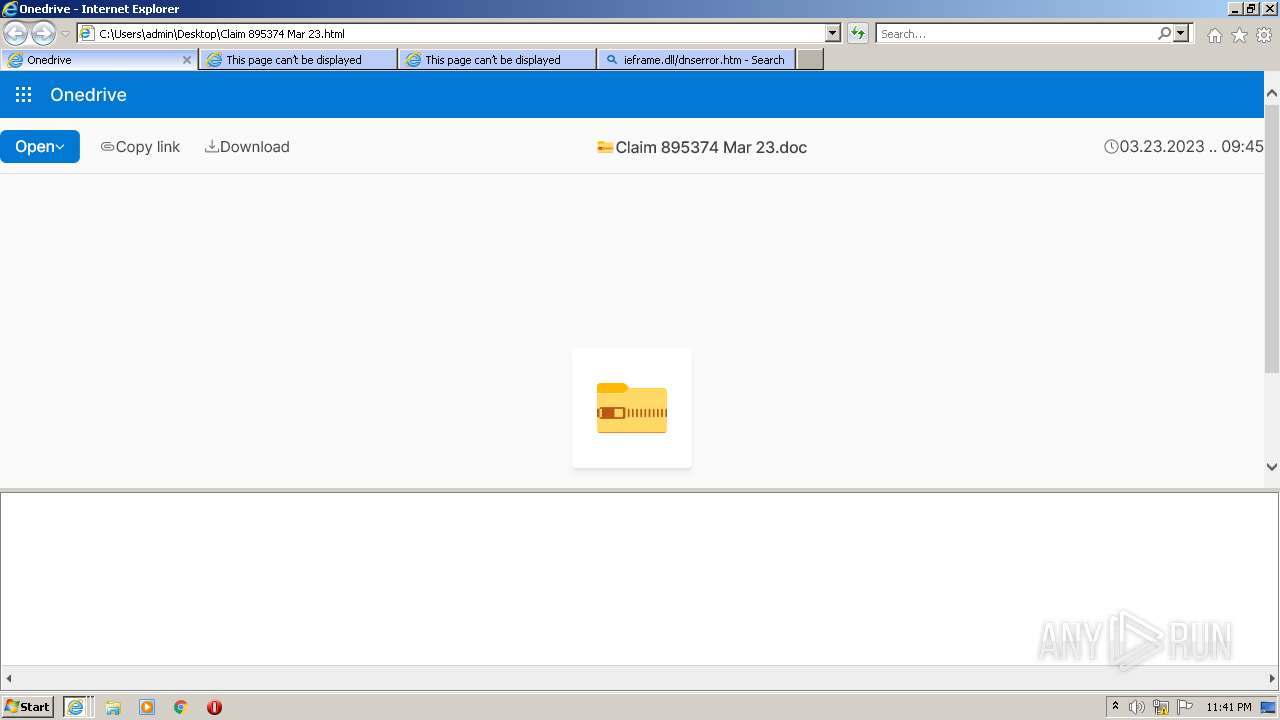
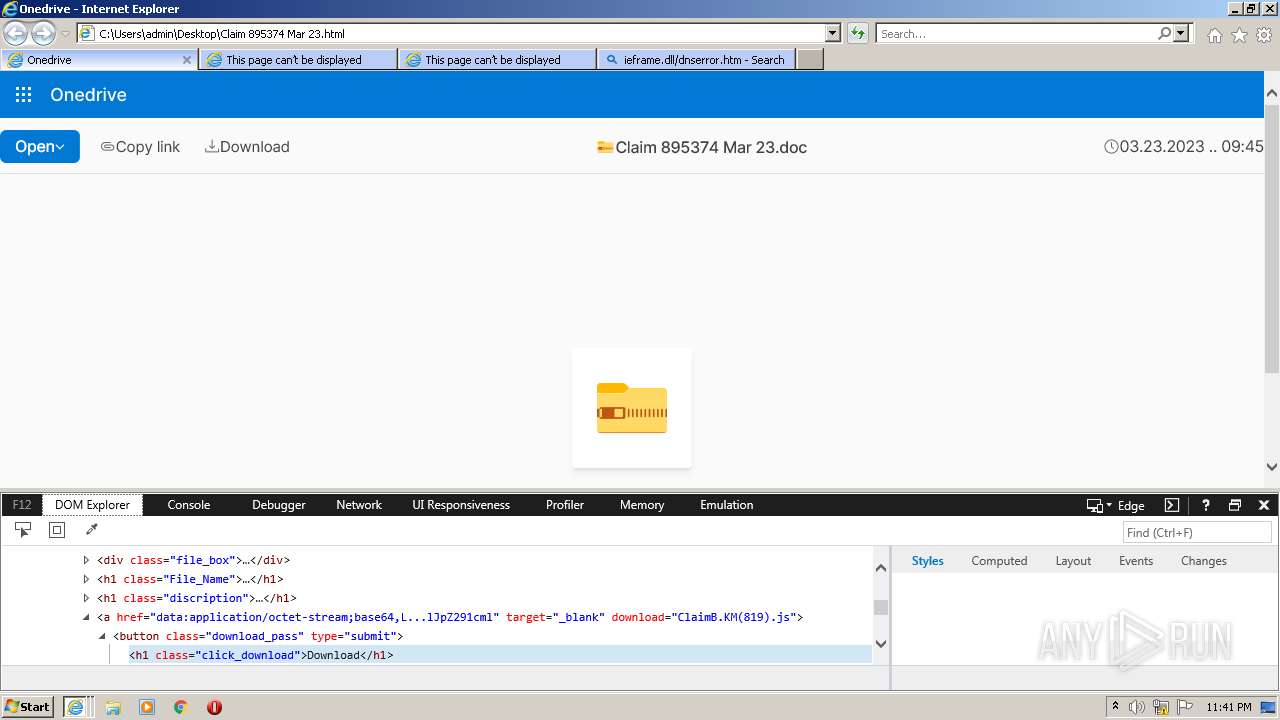
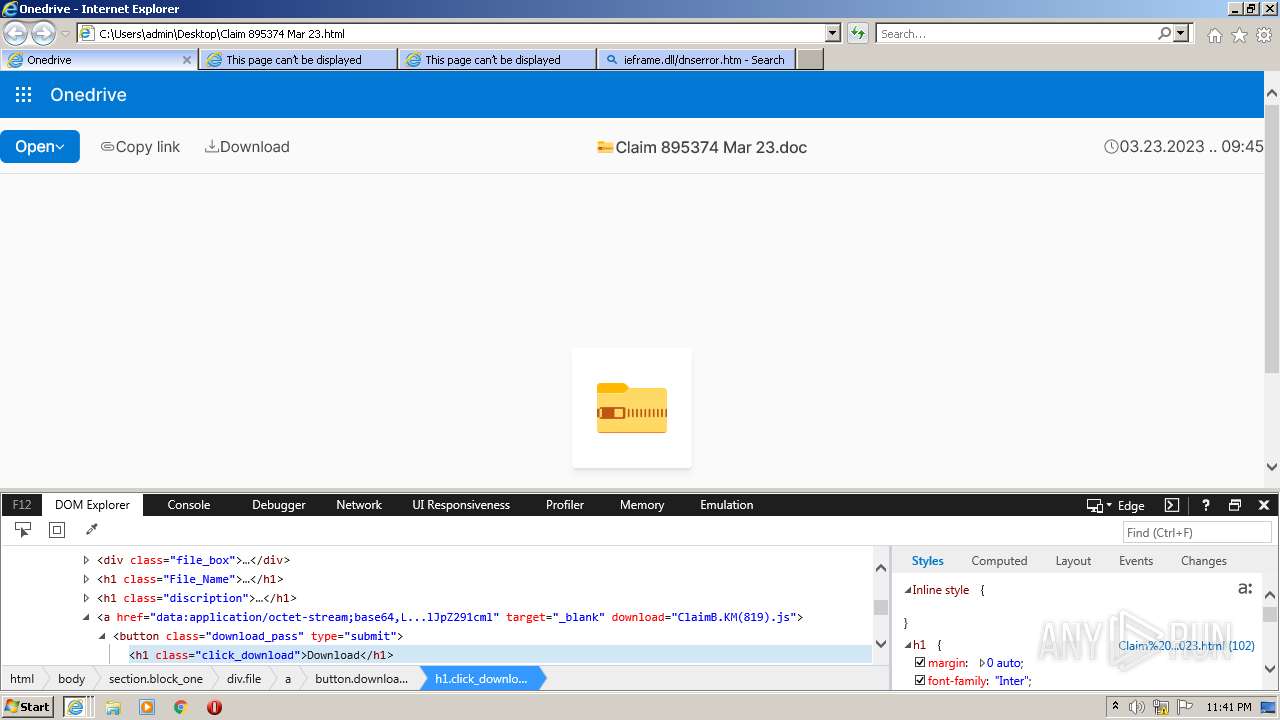
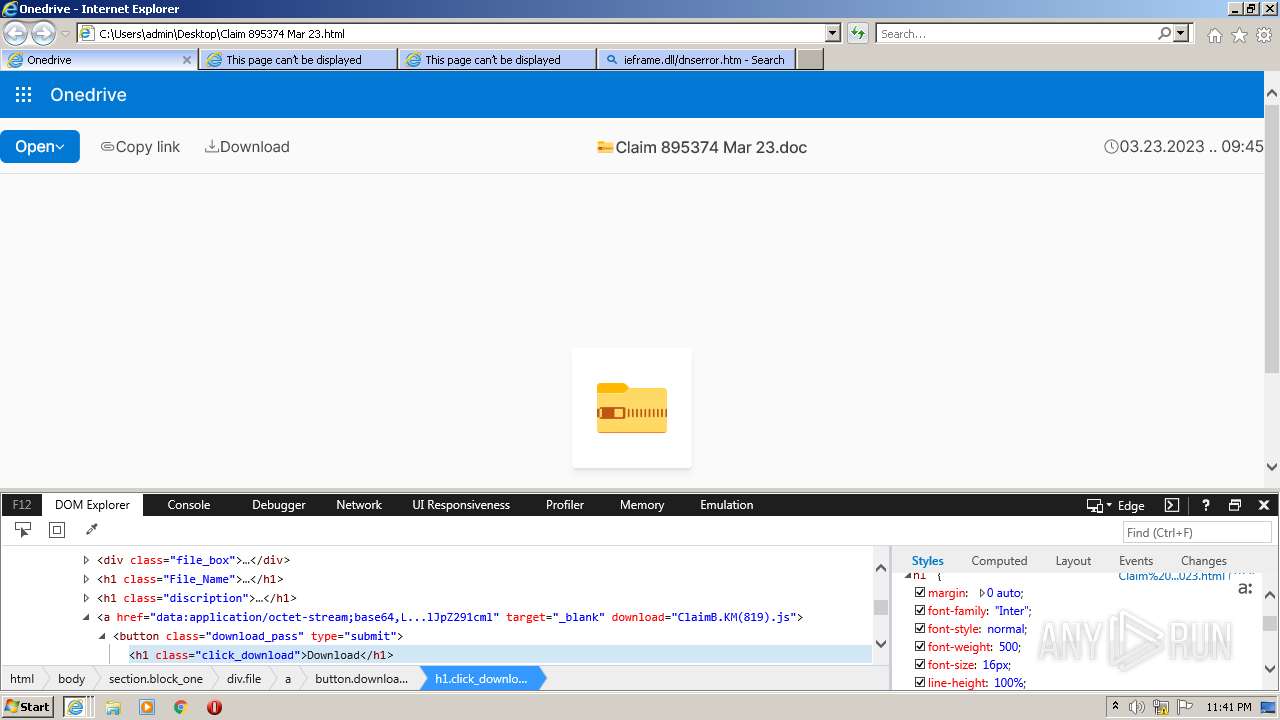
| File name: | Quarantined Messages (4).zip |
| Full analysis: | https://app.any.run/tasks/aa7111f2-c307-4a3f-afb8-439ec332f8ca |
| Verdict: | Malicious activity |
| Analysis date: | March 31, 2023, 22:36:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v4.5 to extract |
| MD5: | C6946E7417C96158201CCAD64F254AFE |
| SHA1: | 09791E92B7CB31A15E2C09664DC294F86F58F70D |
| SHA256: | 2FEDA6EEDAA541F640199F9F5E5999BF69E88CA598BC4F252D8BDC5768841038 |
| SSDEEP: | 1536:4mu1SofH2rFZf7PjojXV4/wu9nRwDcotEwkaMf6UtvCteE9fUZsnROAiDu4kX0nr:4muN25YV80ckI9f6McecfUZsT4ncDTwb |
MALICIOUS
No malicious indicators.SUSPICIOUS
Probably uses Microsoft diagnostics tool to execute malicious payload
- iexplore.exe (PID: 584)
Reads the Internet Settings
- OUTLOOK.EXE (PID: 1124)
- sdiagnhost.exe (PID: 2696)
Executable content was dropped or overwritten
- msdt.exe (PID: 2272)
Reads security settings of Internet Explorer
- msdt.exe (PID: 2272)
- sdiagnhost.exe (PID: 2696)
Searches for installed software
- OUTLOOK.EXE (PID: 1124)
Reads settings of System Certificates
- msdt.exe (PID: 2272)
Executes as Windows Service
- IEEtwCollector.exe (PID: 1788)
INFO
The process checks LSA protection
- OUTLOOK.EXE (PID: 1124)
- msdt.exe (PID: 2272)
- sdiagnhost.exe (PID: 2696)
- IEEtwCollector.exe (PID: 1788)
Checks proxy server information
- OUTLOOK.EXE (PID: 1124)
Process checks computer location settings
- OUTLOOK.EXE (PID: 1124)
Manual execution by a user
- OUTLOOK.EXE (PID: 1124)
- iexplore.exe (PID: 584)
Checks supported languages
- OUTLOOK.EXE (PID: 1124)
Reads the computer name
- OUTLOOK.EXE (PID: 1124)
Creates files or folders in the user directory
- OUTLOOK.EXE (PID: 1124)
- msdt.exe (PID: 2272)
The process uses the downloaded file
- OUTLOOK.EXE (PID: 1124)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 1124)
Create files in a temporary directory
- OUTLOOK.EXE (PID: 1124)
- iexplore.exe (PID: 584)
- msdt.exe (PID: 2272)
Reads the machine GUID from the registry
- OUTLOOK.EXE (PID: 1124)
Application launched itself
- iexplore.exe (PID: 584)
Reads the time zone
- IEEtwCollector.exe (PID: 1788)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
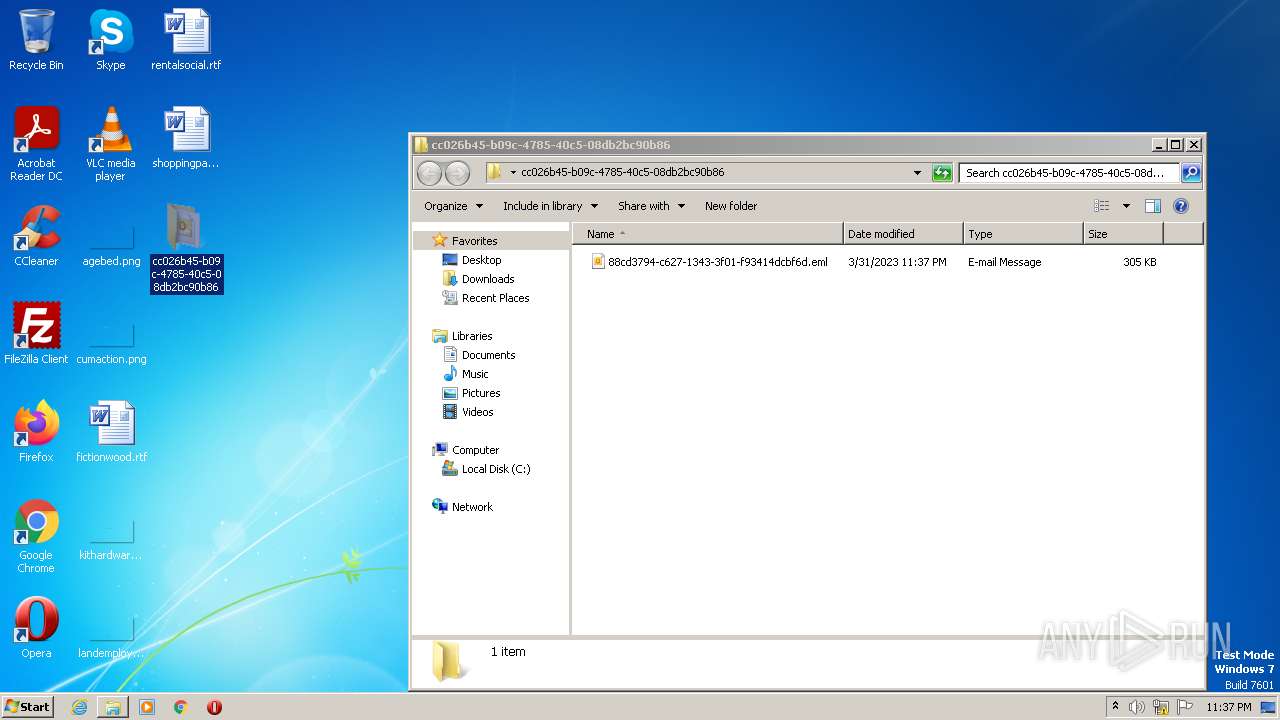
| ZipFileName: | cc026b45-b09c-4785-40c5-08db2bc90b86/88cd3794-c627-1343-3f01-f93414dcbf6d.eml |
|---|---|
| ZipUncompressedSize: | 4294967295 |
| ZipCompressedSize: | 4294967295 |
| ZipCRC: | 0xb674c02d |
| ZipModifyDate: | 2023:03:31 22:36:24 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0009 |
| ZipRequiredVersion: | 45 |
Total processes
54
Monitored processes
11
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 584 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\Desktop\Claim 895374 Mar 23.html | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 976 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:584 CREDAT:1316116 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1124 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\Desktop\cc026b45-b09c-4785-40c5-08db2bc90b86\88cd3794-c627-1343-3f01-f93414dcbf6d.eml" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 1788 | C:\Windows\system32\IEEtwCollector.exe /V | C:\Windows\System32\IEEtwCollector.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: IE ETW Collector Service Exit code: 0 Version: 11.00.9600.19597 (winblue_ltsb_escrow.191216-1311) Modules
| |||||||||||||||
| 2272 | -modal 196948 -skip TRUE -path C:\Windows\diagnostics\system\networking -af C:\Users\admin\AppData\Local\Temp\NDFFEFD.tmp -ep NetworkDiagnosticsWeb | C:\Windows\System32\msdt.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Diagnostics Troubleshooting Wizard Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2428 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:584 CREDAT:2692415 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2668 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Quarantined Messages (4).zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2696 | C:\Windows\System32\sdiagnhost.exe -Embedding | C:\Windows\System32\sdiagnhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Scripted Diagnostics Native Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3308 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:584 CREDAT:1905929 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3648 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:584 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
75 822
Read events
74 344
Write events
1 428
Delete events
50
Modification events
| (PID) Process: | (2668) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
4
Suspicious files
80
Text files
410
Unknown types
56
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1124 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR5986.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1124 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 2668 | WinRAR.exe | C:\Users\admin\Desktop\cc026b45-b09c-4785-40c5-08db2bc90b86\88cd3794-c627-1343-3f01-f93414dcbf6d.eml | eml | |
MD5:— | SHA256:— | |||
| 1124 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 1124 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1124 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmp5B2C.tmp | text | |
MD5:— | SHA256:— | |||
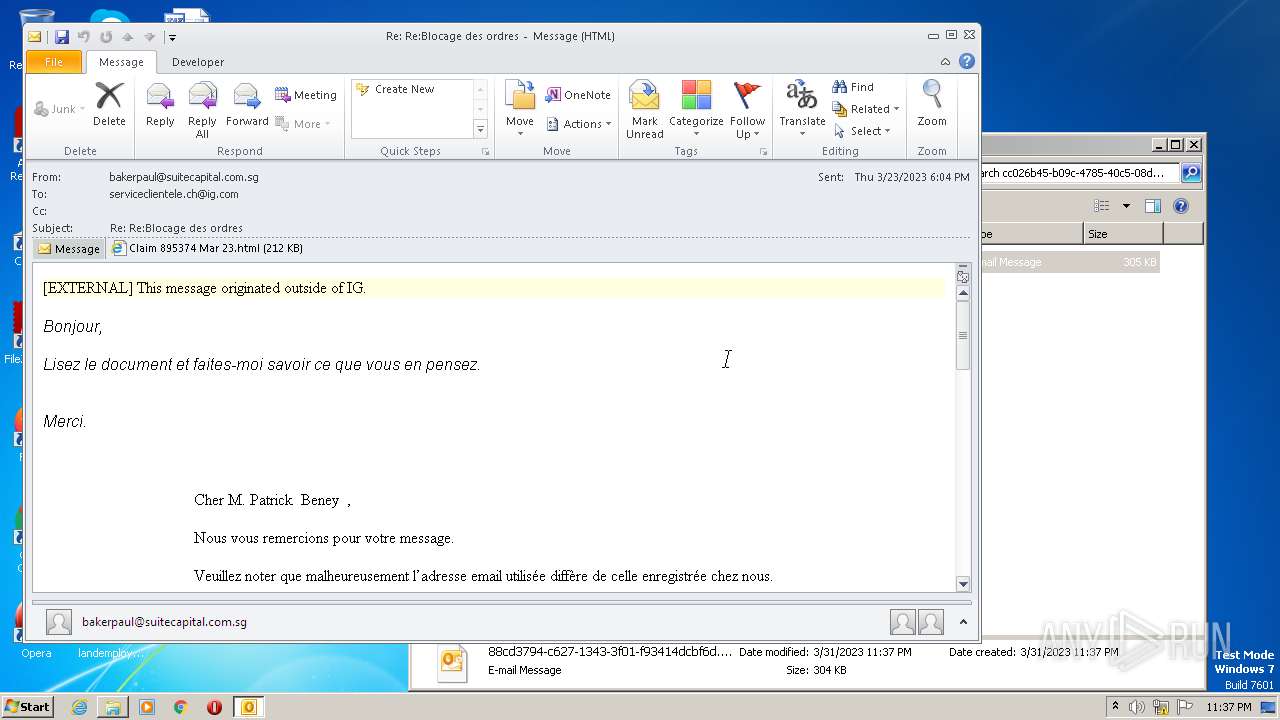
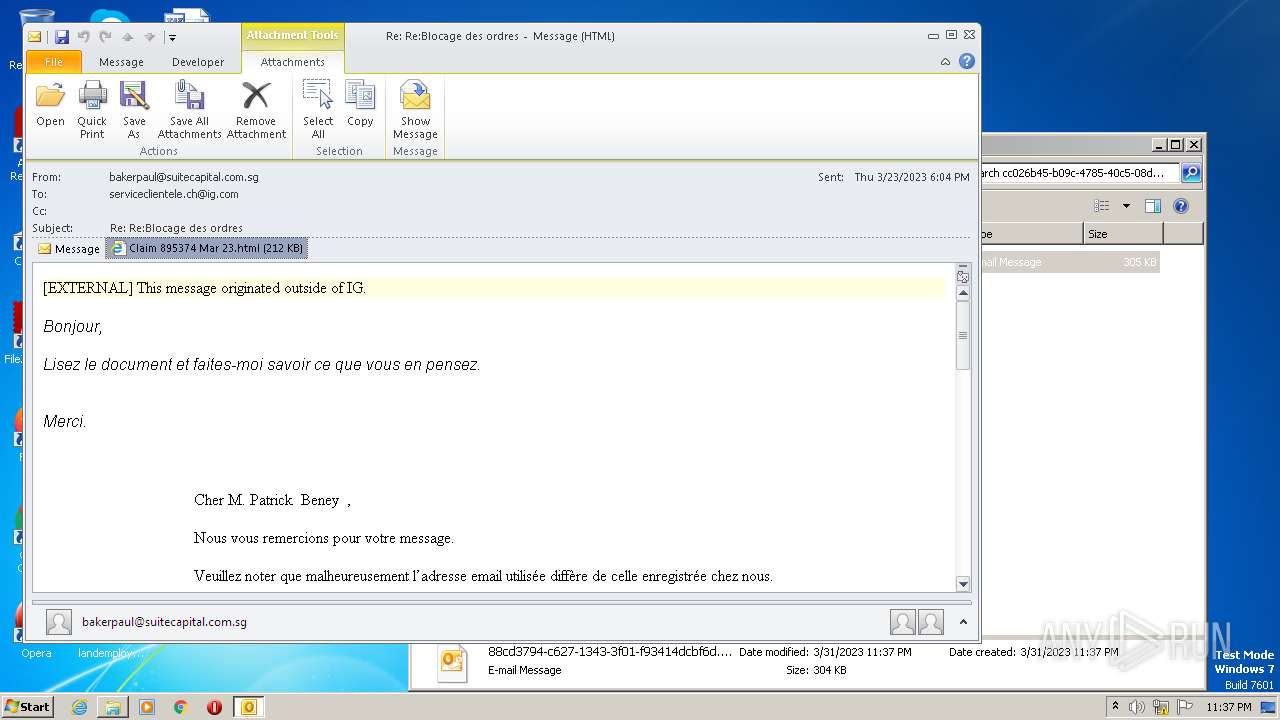
| 1124 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\QQNG35G3\Claim 895374 Mar 23 (2).html | html | |
MD5:— | SHA256:— | |||
| 1124 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\QQNG35G3\Claim 895374 Mar 23.html | html | |
MD5:— | SHA256:— | |||
| 1124 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_ContactPrefs_2_1AF9ECA7CA270A42AD3969255491E0C3.dat | xml | |
MD5:BBCF400BD7AE536EB03054021D6A6398 | SHA256:383020065C1F31F4FB09F448599A6D5E532C390AF4E5B8AF0771FE17A23222AD | |||
| 1124 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{2D54AEE5-8FBB-4B7C-AC33-F6726ABEBB6A}.tmp | ini | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
43
DNS requests
27
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
584 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
3648 | iexplore.exe | GET | 200 | 216.58.212.163:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
3648 | iexplore.exe | GET | 200 | 216.58.212.163:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDTHapPXttJahK0MpJdGmyD | US | der | 472 b | whitelisted |
3648 | iexplore.exe | GET | 200 | 216.58.212.163:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEGuOw5S%2FgZeuCs2W38ctSDs%3D | US | der | 471 b | whitelisted |
3648 | iexplore.exe | GET | 200 | 8.241.11.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e56267937126398a | US | compressed | 4.70 Kb | whitelisted |
584 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | der | 471 b | whitelisted |
584 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
584 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
3648 | iexplore.exe | GET | 200 | 216.58.212.163:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
3648 | iexplore.exe | GET | 200 | 8.248.113.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?303635a1627bc152 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1124 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3648 | iexplore.exe | 8.248.113.254:80 | ctldl.windowsupdate.com | LEVEL3 | US | suspicious |
3648 | iexplore.exe | 142.250.185.106:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
584 | iexplore.exe | 204.79.197.200:443 | www.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3648 | iexplore.exe | 142.250.185.131:443 | fonts.gstatic.com | GOOGLE | US | whitelisted |
3648 | iexplore.exe | 216.58.212.163:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
584 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
976 | iexplore.exe | 204.79.197.200:443 | www.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
976 | iexplore.exe | 13.107.21.200:443 | www.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |