| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/14f3097a-a327-4b75-af8e-1a03cb6dc7ce |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | August 03, 2024, 22:03:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
Drops the executable file immediately after the start
- t.exe (PID: 6780)
- 4363463463464363463463463.exe (PID: 6556)
- a.exe (PID: 6828)
- 883712215.exe (PID: 5944)
- pi.exe (PID: 2456)
- tpeinf.exe (PID: 7148)
- nxmr.exe (PID: 3520)
- 15633737.exe (PID: 6924)
- cmd.exe (PID: 1812)
- Shopzilla.pif (PID: 6784)
- sysarddrvs.exe (PID: 6904)
- pei.exe (PID: 32)
- npp.exe (PID: 3700)
- sysmablsvr.exe (PID: 6932)
- wupgrdsv.exe (PID: 3324)
- 309071531.exe (PID: 7184)
- sysmysldrv.exe (PID: 2608)
- sylsplvc.exe (PID: 6832)
- 4363463463464363463463463.exe (PID: 7116)
- Destover.exe (PID: 7212)
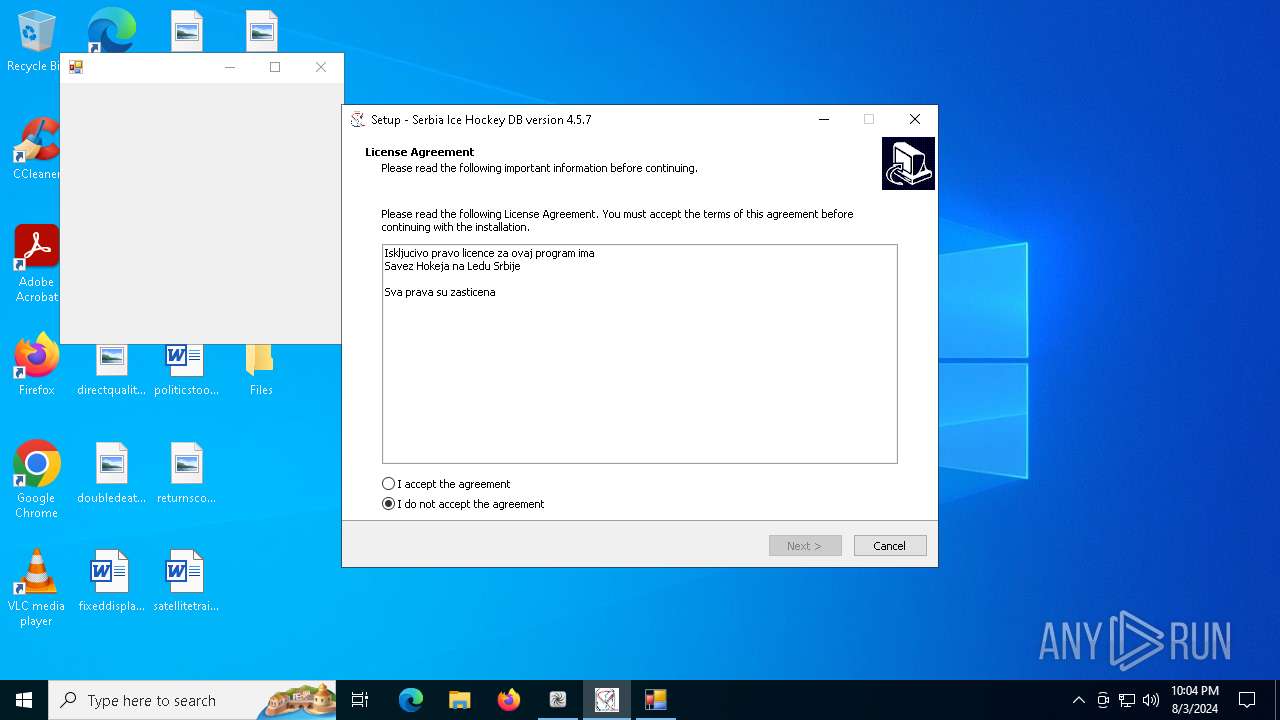
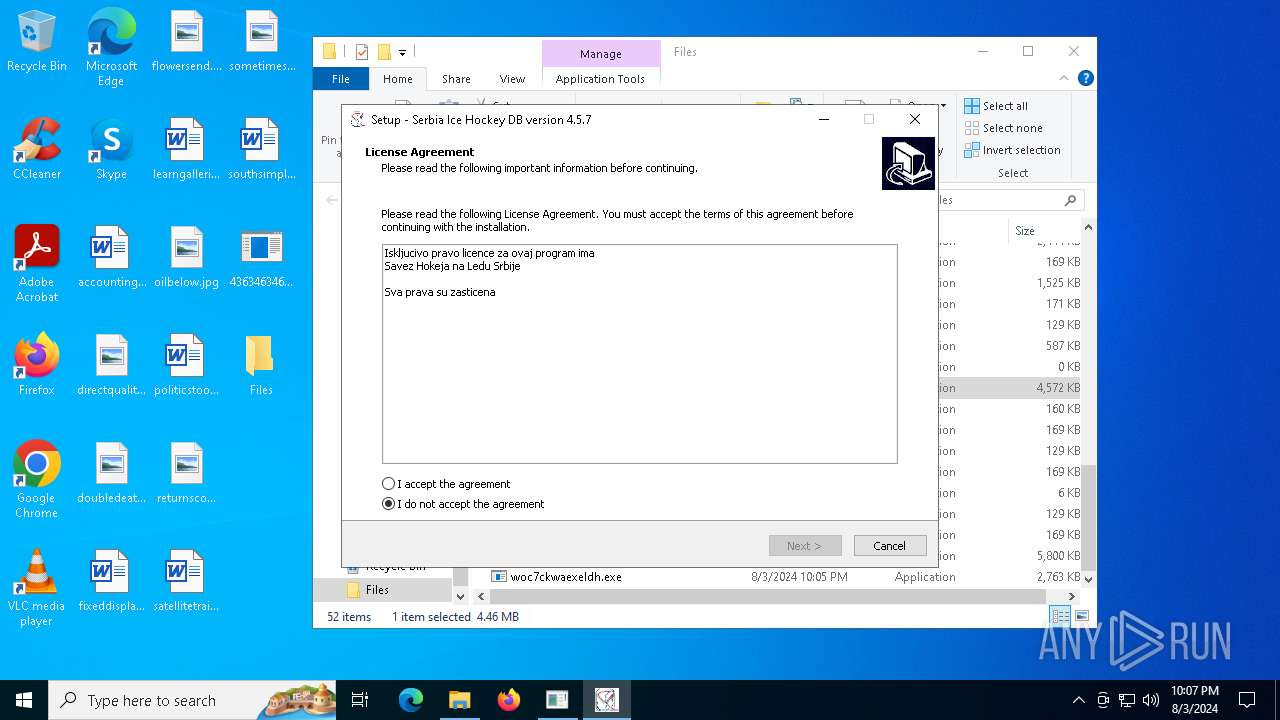
- SrbijaSetupHokej.exe (PID: 6536)
- SrbijaSetupHokej.tmp (PID: 6812)
- powershell.exe (PID: 8960)
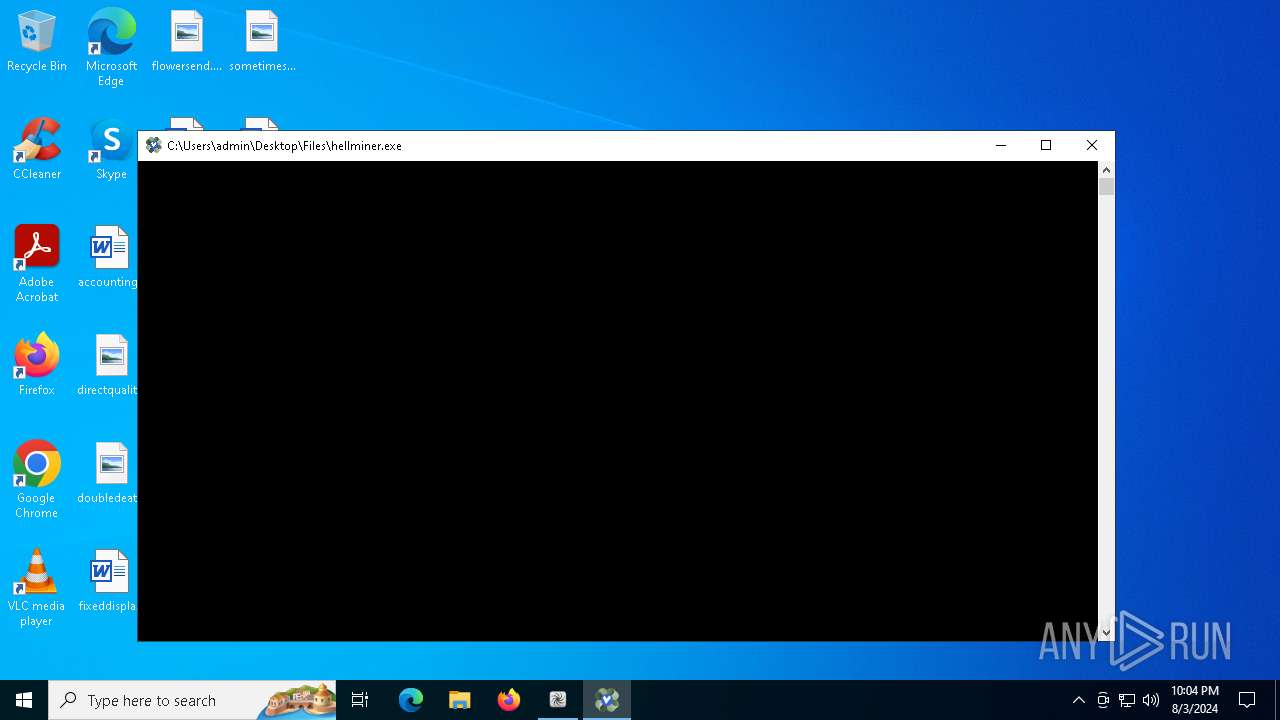
- hellminer.exe (PID: 8832)
- powershell.exe (PID: 10092)
- Botkiller.exe (PID: 8424)
- Botkiller.exe (PID: 1236)
- loader.exe (PID: 5072)
- rhsgn_protected.exe (PID: 5900)
- svchost.com (PID: 8476)
- ARA.exe (PID: 6816)
- NoMoreRansom.exe (PID: 8904)
- Msblockreview.exe (PID: 4100)
- Hokej.exe (PID: 1492)
- Msblockreview.exe (PID: 8944)
- Hokej.exe (PID: 8848)
- Botkiller.exe (PID: 6236)
- svchost.com (PID: 9596)
- SrbijaSetupHokej.exe (PID: 6124)
- SrbijaSetupHokej.exe (PID: 2508)
- SrbijaSetupHokej.tmp (PID: 6624)
Changes the autorun value in the registry
- t.exe (PID: 6780)
- a.exe (PID: 6828)
- 883712215.exe (PID: 5944)
- pi.exe (PID: 2456)
- Installer.exe (PID: 8236)
- NoMoreRansom.exe (PID: 8904)
Changes Security Center notification settings
- sysarddrvs.exe (PID: 6904)
- sysmablsvr.exe (PID: 6932)
- sysmysldrv.exe (PID: 2608)
- sylsplvc.exe (PID: 6832)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 6428)
- sysarddrvs.exe (PID: 6904)
- sysmysldrv.exe (PID: 2608)
- cmd.exe (PID: 6960)
Changes the Windows auto-update feature
- sysarddrvs.exe (PID: 6904)
- sysmablsvr.exe (PID: 6932)
- sysmysldrv.exe (PID: 2608)
- Shopzilla.pif (PID: 7008)
Creates or modifies Windows services
- sysarddrvs.exe (PID: 6904)
- sysmablsvr.exe (PID: 6932)
- sysmysldrv.exe (PID: 2608)
Changes appearance of the Explorer extensions
- sysmablsvr.exe (PID: 6932)
- sysarddrvs.exe (PID: 6904)
- sysmysldrv.exe (PID: 2608)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 6556)
- 4363463463464363463463463.exe (PID: 7116)
DCRAT has been detected (YARA)
- 4363463463464363463463463.exe (PID: 6556)
- 4363463463464363463463463.exe (PID: 7116)
Connects to the CnC server
- sysmablsvr.exe (PID: 6932)
- sysarddrvs.exe (PID: 6904)
- sysmysldrv.exe (PID: 2608)
- svchost.exe (PID: 2256)
- sylsplvc.exe (PID: 6832)
- notepad.exe (PID: 7432)
- 25072023.exe (PID: 9492)
PHORPIEX has been detected (SURICATA)
- sysarddrvs.exe (PID: 6904)
- sysmablsvr.exe (PID: 6932)
- svchost.exe (PID: 2256)
- sysmysldrv.exe (PID: 2608)
- sylsplvc.exe (PID: 6832)
- 4363463463464363463463463.exe (PID: 6556)
PHORPIEX has been detected (YARA)
- sysarddrvs.exe (PID: 6904)
- sysmablsvr.exe (PID: 6932)
- sysmysldrv.exe (PID: 2608)
LUMMA has been detected (YARA)
- sysarddrvs.exe (PID: 6904)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 6696)
- findstr.exe (PID: 1356)
Uses Task Scheduler to autorun other applications
- Shopzilla.pif (PID: 6784)
Actions looks like stealing of personal data
- peinf.exe (PID: 6900)
- build.exe (PID: 5196)
- vbc.exe (PID: 9300)
- 25072023.exe (PID: 9492)
- svchost.com (PID: 8476)
- Botkiller.exe (PID: 8424)
Application was injected by another process
- explorer.exe (PID: 4552)
Runs injected code in another process
- 2.exe (PID: 6464)
Attempt to connect to SMB server
- System (PID: 4)
MINER has been detected (SURICATA)
- notepad.exe (PID: 7432)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2256)
SMOKE has been detected (SURICATA)
- explorer.exe (PID: 4552)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 8252)
- cmd.exe (PID: 8900)
Run PowerShell with an invisible window
- powershell.exe (PID: 8732)
RISEPRO has been detected (YARA)
- Shopzilla.pif (PID: 7008)
Stealers network behavior
- 25072023.exe (PID: 9492)
REDLINE has been detected (SURICATA)
- 25072023.exe (PID: 9492)
METASTEALER has been detected (SURICATA)
- 25072023.exe (PID: 9492)
Troldesh is detected
- NoMoreRansom.exe (PID: 8904)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 3980)
NjRAT is detected
- Botkiller.exe (PID: 1236)
- Botkiller.exe (PID: 6236)
SUSPICIOUS
Reads security settings of Internet Explorer
- 4363463463464363463463463.exe (PID: 6556)
- sysarddrvs.exe (PID: 6904)
- sysmablsvr.exe (PID: 6932)
- 2692121105.exe (PID: 2532)
- Downaqzh.exe (PID: 1288)
- sysmysldrv.exe (PID: 2608)
- QuizPokemon.exe (PID: 5292)
- tpeinf.exe (PID: 7148)
- DownSysSoft.exe (PID: 3384)
- 15633737.exe (PID: 6924)
- npp.exe (PID: 3700)
- pei.exe (PID: 32)
- sylsplvc.exe (PID: 6832)
- 309071531.exe (PID: 7184)
- 4363463463464363463463463.exe (PID: 7116)
- poolsdnkjfdbndklsnfgb.exe (PID: 8020)
- random.exe (PID: 8028)
- cmd.exe (PID: 9992)
- Botkiller.exe (PID: 8424)
- Botkiller.exe (PID: 1236)
- loader.exe (PID: 5072)
- rhsgn_protected.exe (PID: 5900)
- ARA.exe (PID: 6816)
- Msblockreview.exe (PID: 4100)
- Msblockreview.exe (PID: 8944)
- Hokej.exe (PID: 1492)
- Botkiller.exe (PID: 6236)
- SRBIJA~1.tmp (PID: 9460)
Reads the date of Windows installation
- 4363463463464363463463463.exe (PID: 6556)
- sysarddrvs.exe (PID: 6904)
- sysmysldrv.exe (PID: 2608)
- QuizPokemon.exe (PID: 5292)
- 4363463463464363463463463.exe (PID: 7116)
- random.exe (PID: 8028)
- Botkiller.exe (PID: 8424)
- loader.exe (PID: 5072)
- rhsgn_protected.exe (PID: 5900)
- ARA.exe (PID: 6816)
- Msblockreview.exe (PID: 4100)
- Msblockreview.exe (PID: 8944)
- Hokej.exe (PID: 1492)
- Botkiller.exe (PID: 1236)
- SRBIJA~1.tmp (PID: 9460)
Executable content was dropped or overwritten
- 4363463463464363463463463.exe (PID: 6556)
- t.exe (PID: 6780)
- a.exe (PID: 6828)
- 883712215.exe (PID: 5944)
- pi.exe (PID: 2456)
- tpeinf.exe (PID: 7148)
- nxmr.exe (PID: 3520)
- 15633737.exe (PID: 6924)
- cmd.exe (PID: 1812)
- Shopzilla.pif (PID: 6784)
- pei.exe (PID: 32)
- npp.exe (PID: 3700)
- wupgrdsv.exe (PID: 3324)
- 309071531.exe (PID: 7184)
- explorer.exe (PID: 4552)
- 4363463463464363463463463.exe (PID: 7116)
- Destover.exe (PID: 7212)
- hellminer.exe (PID: 8832)
- SrbijaSetupHokej.exe (PID: 6536)
- SrbijaSetupHokej.tmp (PID: 6812)
- powershell.exe (PID: 10092)
- Botkiller.exe (PID: 8424)
- loader.exe (PID: 5072)
- Botkiller.exe (PID: 1236)
- rhsgn_protected.exe (PID: 5900)
- svchost.com (PID: 8476)
- ARA.exe (PID: 6816)
- NoMoreRansom.exe (PID: 8904)
- Msblockreview.exe (PID: 4100)
- Hokej.exe (PID: 1492)
- Msblockreview.exe (PID: 8944)
- Hokej.exe (PID: 8848)
- Botkiller.exe (PID: 6236)
- SrbijaSetupHokej.exe (PID: 6124)
- SrbijaSetupHokej.exe (PID: 2508)
- svchost.com (PID: 9596)
- SrbijaSetupHokej.tmp (PID: 6624)
Starts itself from another location
- t.exe (PID: 6780)
- a.exe (PID: 6828)
- 883712215.exe (PID: 5944)
- pi.exe (PID: 2456)
- sysmysldrv.exe (PID: 2608)
- Msblockreview.exe (PID: 4100)
- Msblockreview.exe (PID: 8944)
Connects to unusual port
- 4363463463464363463463463.exe (PID: 6556)
- Downaqzh.exe (PID: 1288)
- DownSysSoft.exe (PID: 3384)
- aaa.exe (PID: 1132)
- notepad.exe (PID: 7432)
- Shopzilla.pif (PID: 7008)
- QQ.exe (PID: 8704)
- sysarddrvs.exe (PID: 6904)
- sysmablsvr.exe (PID: 6932)
- sylsplvc.exe (PID: 6832)
- sysmysldrv.exe (PID: 2608)
- 4363463463464363463463463.exe (PID: 7116)
- %C4%A7%BE%A7.exe (PID: 8664)
- cmd.exe (PID: 9992)
- vbc.exe (PID: 9300)
- 25072023.exe (PID: 9492)
- Hokej.exe (PID: 1492)
- Hokej.exe (PID: 8848)
Potential Corporate Privacy Violation
- 4363463463464363463463463.exe (PID: 6556)
- Downaqzh.exe (PID: 1288)
- tpeinf.exe (PID: 7148)
- System (PID: 4)
- DownSysSoft.exe (PID: 3384)
- notepad.exe (PID: 7432)
- 309071531.exe (PID: 7184)
- 4363463463464363463463463.exe (PID: 7116)
- 15633737.exe (PID: 6924)
Creates or modifies Windows services
- sysarddrvs.exe (PID: 6904)
- sysmablsvr.exe (PID: 6932)
- sysmysldrv.exe (PID: 2608)
Starts CMD.EXE for commands execution
- sysarddrvs.exe (PID: 6904)
- sysmysldrv.exe (PID: 2608)
- QuizPokemon.exe (PID: 5292)
- cmd.exe (PID: 1812)
- Installer.exe (PID: 8236)
- powershell.exe (PID: 8732)
- hellminer.exe (PID: 9160)
- hellminer.exe (PID: 5072)
- random.exe (PID: 8028)
- wscript.exe (PID: 3980)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6428)
- cmd.exe (PID: 6960)
- explorer.exe (PID: 4552)
- cmd.exe (PID: 8252)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 6428)
- cmd.exe (PID: 6960)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 6556)
- 4363463463464363463463463.exe (PID: 7116)
Connects to the server without a host name
- sysarddrvs.exe (PID: 6904)
- sysmablsvr.exe (PID: 6932)
- sysmysldrv.exe (PID: 2608)
- 4363463463464363463463463.exe (PID: 6556)
- 4363463463464363463463463.exe (PID: 7116)
Detected use of alternative data streams (AltDS)
- powershell.exe (PID: 4324)
- powershell.exe (PID: 6752)
Executing commands from ".cmd" file
- QuizPokemon.exe (PID: 5292)
The process executes via Task Scheduler
- wupgrdsv.exe (PID: 3324)
- wupgrdsv.exe (PID: 8104)
Get information on the list of running processes
- cmd.exe (PID: 1812)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1812)
Application launched itself
- cmd.exe (PID: 1812)
- Shopzilla.pif (PID: 6784)
- hellminer.exe (PID: 8832)
- RegAsm.exe (PID: 8300)
- hellminer.exe (PID: 9160)
- soft.exe (PID: 300)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 1812)
- Shopzilla.pif (PID: 6784)
Suspicious file concatenation
- cmd.exe (PID: 6032)
Starts application with an unusual extension
- cmd.exe (PID: 1812)
- Shopzilla.pif (PID: 6784)
- 4363463463464363463463463.exe (PID: 7116)
- loader.exe (PID: 5072)
- rhsgn_protected.exe (PID: 5900)
- Msblockreview.exe (PID: 4100)
- Hokej.exe (PID: 1492)
- Botkiller.exe (PID: 1236)
- explorer.exe (PID: 4552)
The executable file from the user directory is run by the CMD process
- Shopzilla.pif (PID: 6784)
- Msblockreview.exe (PID: 4100)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 1812)
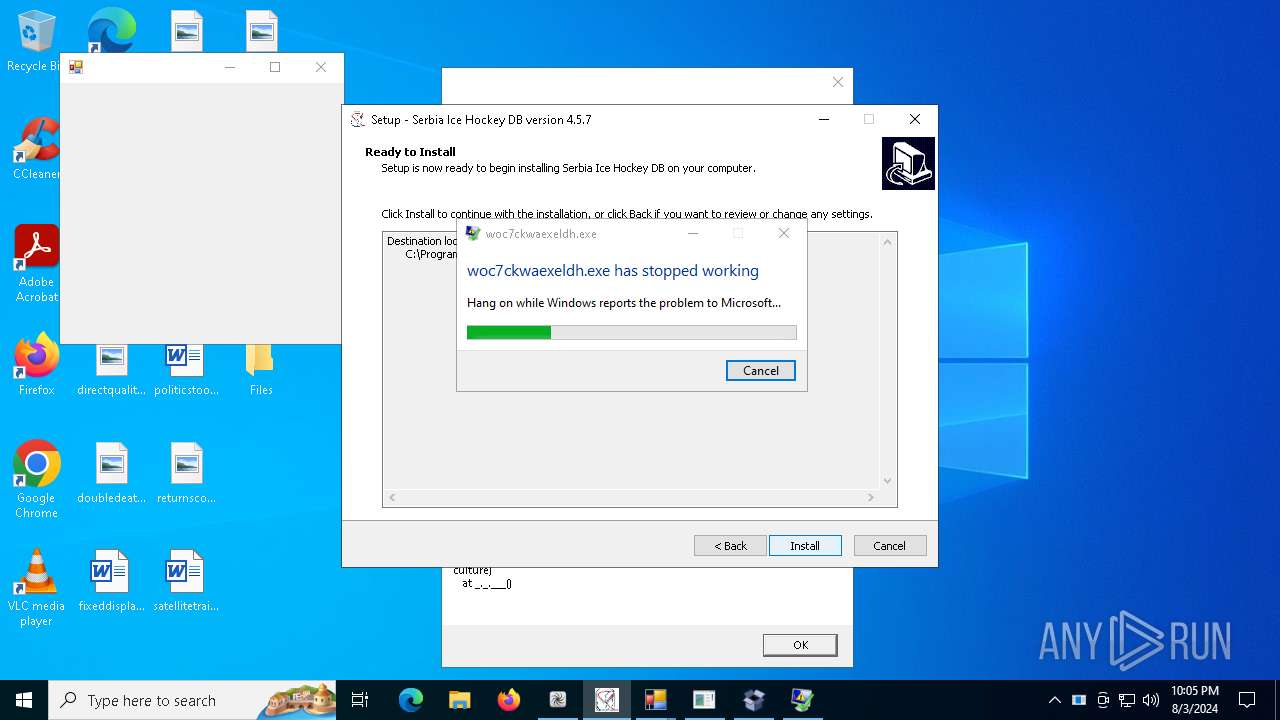
Executes application which crashes
- peinf.exe (PID: 6900)
- SCP.Desktop.Client.IssueView.exe (PID: 10168)
- woc7ckwaexeldh.exe (PID: 7332)
- Hokej.exe (PID: 1492)
Drops a system driver (possible attempt to evade defenses)
- wupgrdsv.exe (PID: 3324)
Searches for installed software
- build.exe (PID: 5196)
- SrbijaSetupHokej.tmp (PID: 6624)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2256)
Process drops legitimate windows executable
- 4363463463464363463463463.exe (PID: 7116)
- Destover.exe (PID: 7212)
- hellminer.exe (PID: 8832)
- powershell.exe (PID: 8960)
- powershell.exe (PID: 10092)
- rhsgn_protected.exe (PID: 5900)
Starts a Microsoft application from unusual location
- Destover.exe (PID: 7212)
- Installer.exe (PID: 8236)
- FileCoAuth.exe (PID: 8656)
Checks Windows Trust Settings
- poolsdnkjfdbndklsnfgb.exe (PID: 8020)
- Botkiller.exe (PID: 1236)
- Botkiller.exe (PID: 6236)
Executing commands from a ".bat" file
- Installer.exe (PID: 8236)
- powershell.exe (PID: 8732)
- random.exe (PID: 8028)
- wscript.exe (PID: 3980)
Request a resource from the Internet using PowerShell's cmdlet
- cmd.exe (PID: 8252)
Powershell scripting: start process
- cmd.exe (PID: 8252)
The process drops C-runtime libraries
- hellminer.exe (PID: 8832)
- powershell.exe (PID: 8960)
- powershell.exe (PID: 10092)
Downloads file from URI
- powershell.exe (PID: 8960)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 8900)
Loads Python modules
- hellminer.exe (PID: 9160)
- hellminer.exe (PID: 5072)
Process drops python dynamic module
- hellminer.exe (PID: 8832)
Uses WMIC.EXE to obtain CPU information
- hellminer.exe (PID: 9160)
Uses WMIC.EXE to obtain operating system information
- hellminer.exe (PID: 9160)
Contacting a server suspected of hosting an Exploit Kit
- 4363463463464363463463463.exe (PID: 7116)
Reads the Windows owner or organization settings
- SrbijaSetupHokej.tmp (PID: 6812)
- SrbijaSetupHokej.tmp (PID: 6624)
The process creates files with name similar to system file names
- 4363463463464363463463463.exe (PID: 6556)
- NoMoreRansom.exe (PID: 8904)
- Msblockreview.exe (PID: 8944)
- Botkiller.exe (PID: 1236)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 10092)
Probably fake Windows Update file has been dropped
- 4363463463464363463463463.exe (PID: 6556)
Lists all scheduled tasks
- schtasks.exe (PID: 9624)
The process executes VB scripts
- woc7ckwaexeldh.exe (PID: 7332)
Adds/modifies Windows certificates
- 25072023.exe (PID: 9492)
Mutex name with non-standard characters
- Botkiller.exe (PID: 8424)
- svchost.com (PID: 8476)
- svchost.com (PID: 5904)
- svchost.com (PID: 8120)
- Msblockreview.exe (PID: 4100)
- svchost.com (PID: 8740)
- svchost.com (PID: 3256)
- svchost.com (PID: 6700)
- svchost.com (PID: 6564)
- svchost.com (PID: 9596)
Uses TASKKILL.EXE to kill process
- Botkiller.exe (PID: 1236)
- Botkiller.exe (PID: 6236)
There is functionality for taking screenshot (YARA)
- QQ.exe (PID: 8704)
Runs shell command (SCRIPT)
- wscript.exe (PID: 3980)
Executed via WMI
- schtasks.exe (PID: 9124)
- schtasks.exe (PID: 7340)
- schtasks.exe (PID: 1452)
- schtasks.exe (PID: 1184)
- schtasks.exe (PID: 8828)
- schtasks.exe (PID: 9560)
- schtasks.exe (PID: 9604)
- schtasks.exe (PID: 7960)
- schtasks.exe (PID: 9760)
- schtasks.exe (PID: 8732)
- schtasks.exe (PID: 1128)
- schtasks.exe (PID: 7528)
- schtasks.exe (PID: 8920)
- schtasks.exe (PID: 9892)
- schtasks.exe (PID: 8908)
- schtasks.exe (PID: 8744)
- schtasks.exe (PID: 9536)
- schtasks.exe (PID: 8644)
- schtasks.exe (PID: 6448)
- schtasks.exe (PID: 8624)
- schtasks.exe (PID: 6596)
- schtasks.exe (PID: 7488)
- schtasks.exe (PID: 8532)
- schtasks.exe (PID: 7704)
- schtasks.exe (PID: 7348)
- schtasks.exe (PID: 8072)
- schtasks.exe (PID: 9008)
- schtasks.exe (PID: 10180)
- schtasks.exe (PID: 9872)
- schtasks.exe (PID: 10124)
- schtasks.exe (PID: 10116)
- schtasks.exe (PID: 10136)
- schtasks.exe (PID: 9628)
- schtasks.exe (PID: 9888)
- schtasks.exe (PID: 8964)
- schtasks.exe (PID: 8336)
- schtasks.exe (PID: 7136)
- schtasks.exe (PID: 1640)
- schtasks.exe (PID: 8720)
- schtasks.exe (PID: 7804)
- schtasks.exe (PID: 10088)
- schtasks.exe (PID: 10048)
- schtasks.exe (PID: 10016)
- schtasks.exe (PID: 8068)
- schtasks.exe (PID: 7448)
- schtasks.exe (PID: 9164)
- schtasks.exe (PID: 8840)
- schtasks.exe (PID: 7204)
- schtasks.exe (PID: 7492)
- schtasks.exe (PID: 6548)
- schtasks.exe (PID: 8080)
- schtasks.exe (PID: 7592)
- schtasks.exe (PID: 6040)
- schtasks.exe (PID: 304)
Likely accesses (executes) a file from the Public directory
- schtasks.exe (PID: 8840)
- schtasks.exe (PID: 7204)
- schtasks.exe (PID: 7492)
Connects to FTP
- Hokej.exe (PID: 1492)
- Hokej.exe (PID: 8848)
Crypto Currency Mining Activity Detected
- notepad.exe (PID: 7432)
INFO
Reads security settings of Internet Explorer
- explorer.exe (PID: 4552)
- WMIC.exe (PID: 7996)
- WMIC.exe (PID: 8476)
Disables trace logs
- 4363463463464363463463463.exe (PID: 6556)
- 4363463463464363463463463.exe (PID: 7116)
- powershell.exe (PID: 8336)
- powershell.exe (PID: 8960)
- SearchApp.exe (PID: 7652)
Reads the computer name
- 4363463463464363463463463.exe (PID: 6556)
- sysarddrvs.exe (PID: 6904)
- sysmablsvr.exe (PID: 6932)
- Downaqzh.exe (PID: 1288)
- 2692121105.exe (PID: 2532)
- sysmysldrv.exe (PID: 2608)
- QuizPokemon.exe (PID: 5292)
- tpeinf.exe (PID: 7148)
- DownSysSoft.exe (PID: 3384)
- 15633737.exe (PID: 6924)
- Shopzilla.pif (PID: 6784)
- aaa.exe (PID: 1132)
- npp.exe (PID: 3700)
- pei.exe (PID: 32)
- sylsplvc.exe (PID: 6832)
- build.exe (PID: 5196)
- 309071531.exe (PID: 7184)
- 4363463463464363463463463.exe (PID: 7116)
- poolsdnkjfdbndklsnfgb.exe (PID: 8020)
- TextInputHost.exe (PID: 7816)
- Shopzilla.pif (PID: 7008)
- QQ.exe (PID: 8704)
- hellminer.exe (PID: 8832)
- RegAsm.exe (PID: 8300)
- SrbijaSetupHokej.tmp (PID: 6812)
- RegAsm.exe (PID: 5152)
- random.exe (PID: 8028)
- cmd.exe (PID: 9992)
- %C4%A7%BE%A7.exe (PID: 8664)
- identity_helper.exe (PID: 9820)
- SCP.Desktop.Client.IssueView.exe (PID: 10168)
- adm_atu.exe (PID: 9040)
- 25072023.exe (PID: 9492)
- Botkiller.exe (PID: 8424)
- vbc.exe (PID: 9300)
- Botkiller.exe (PID: 1236)
- loader.exe (PID: 5072)
- rhsgn_protected.exe (PID: 5900)
- NoMoreRansom.exe (PID: 8904)
- ARA.exe (PID: 6816)
- Hokej.exe (PID: 1492)
- Msblockreview.exe (PID: 4100)
- Msblockreview.exe (PID: 8944)
- SearchApp.exe (PID: 7652)
- Hokej.exe (PID: 8848)
- Botkiller.exe (PID: 6236)
- SRBIJA~1.tmp (PID: 9460)
- SrbijaSetupHokej.tmp (PID: 6624)
Reads Environment values
- 4363463463464363463463463.exe (PID: 6556)
- 4363463463464363463463463.exe (PID: 7116)
- cmd.exe (PID: 9992)
- identity_helper.exe (PID: 9820)
- 25072023.exe (PID: 9492)
- Msblockreview.exe (PID: 8944)
- SearchApp.exe (PID: 7652)
- Hokej.exe (PID: 8848)
Checks supported languages
- 4363463463464363463463463.exe (PID: 6556)
- t.exe (PID: 6780)
- a.exe (PID: 6828)
- t2.exe (PID: 6884)
- sysarddrvs.exe (PID: 6904)
- sysmablsvr.exe (PID: 6932)
- Downdd.exe (PID: 5048)
- 1.exe (PID: 4404)
- 2692121105.exe (PID: 2532)
- 532022124.exe (PID: 6200)
- Downaqzh.exe (PID: 1288)
- tdrpload.exe (PID: 4016)
- twztl.exe (PID: 4540)
- r.exe (PID: 232)
- nxmr.exe (PID: 3520)
- tt.exe (PID: 6740)
- 883712215.exe (PID: 5944)
- build.exe (PID: 5196)
- pi.exe (PID: 2456)
- sysmysldrv.exe (PID: 2608)
- 344212930.exe (PID: 6420)
- 11.exe (PID: 3256)
- 2.exe (PID: 6464)
- peinf.exe (PID: 6900)
- sylsplvc.exe (PID: 6832)
- chromedump.exe (PID: 4192)
- newtpp.exe (PID: 6828)
- QuizPokemon.exe (PID: 5292)
- 15633737.exe (PID: 6924)
- 181884449.exe (PID: 4832)
- tpeinf.exe (PID: 7148)
- DownSysSoft.exe (PID: 3384)
- aaa.exe (PID: 1132)
- t1.exe (PID: 6844)
- wupgrdsv.exe (PID: 3324)
- pp.exe (PID: 4260)
- 3020233042.exe (PID: 3032)
- npp.exe (PID: 3700)
- 2293718278.exe (PID: 6360)
- Shopzilla.pif (PID: 6784)
- 2845718380.exe (PID: 6236)
- m.exe (PID: 6428)
- pei.exe (PID: 32)
- s.exe (PID: 1356)
- 172521378.exe (PID: 4772)
- 37222041.exe (PID: 7196)
- 65873624.exe (PID: 5176)
- 309071531.exe (PID: 7184)
- 45387347.exe (PID: 7372)
- 265799186.exe (PID: 7532)
- 303733371.exe (PID: 7820)
- 2888927522.exe (PID: 7604)
- 259730513.exe (PID: 7792)
- 3342420911.exe (PID: 8152)
- 4363463463464363463463463.exe (PID: 7116)
- wupgrdsv.exe (PID: 8104)
- 530318350.exe (PID: 2388)
- 192901917.exe (PID: 7392)
- poolsdnkjfdbndklsnfgb.exe (PID: 8020)
- Destover.exe (PID: 7212)
- TextInputHost.exe (PID: 7816)
- Shopzilla.pif (PID: 7008)
- o.exe (PID: 3008)
- Installer.exe (PID: 8236)
- QQ.exe (PID: 8704)
- hellminer.exe (PID: 8832)
- hellminer.exe (PID: 9160)
- RambledMime.exe (PID: 9084)
- RegAsm.exe (PID: 8300)
- SrbijaSetupHokej.exe (PID: 6536)
- hellminer.exe (PID: 5072)
- RegAsm.exe (PID: 5152)
- 123.exe (PID: 8012)
- random.exe (PID: 8028)
- SrbijaSetupHokej.tmp (PID: 6812)
- soft.exe (PID: 300)
- %C4%A7%BE%A7.exe (PID: 8664)
- clearkhdyy.exe (PID: 6984)
- soft.exe (PID: 2336)
- cmd.exe (PID: 9992)
- SCP.Desktop.Client.IssueView.exe (PID: 10168)
- identity_helper.exe (PID: 9820)
- windows_update.exe (PID: 7288)
- woc7ckwaexeldh.exe (PID: 7332)
- adm_atu.exe (PID: 9040)
- 25072023.exe (PID: 9492)
- Botkiller.exe (PID: 8424)
- Botkiller.exe (PID: 1236)
- vbc.exe (PID: 9300)
- svchost.com (PID: 8476)
- loader.exe (PID: 5072)
- rhsgn_protected.exe (PID: 5900)
- svchost.com (PID: 5904)
- svchost.com (PID: 8120)
- NoMoreRansom.exe (PID: 8904)
- ARA.exe (PID: 6816)
- svchost.com (PID: 6700)
- Hokej.exe (PID: 1492)
- Msblockreview.exe (PID: 4100)
- svchost.com (PID: 8740)
- Msblockreview.exe (PID: 8944)
- SearchApp.exe (PID: 7652)
- svchost.com (PID: 3256)
- Hokej.exe (PID: 8848)
- svchost.com (PID: 6564)
- Botkiller.exe (PID: 6236)
- SrbijaSetupHokej.exe (PID: 2508)
- svchost.com (PID: 9596)
- SrbijaSetupHokej.exe (PID: 6124)
- SRBIJA~1.tmp (PID: 9460)
- SrbijaSetupHokej.tmp (PID: 6624)
Checks proxy server information
- 4363463463464363463463463.exe (PID: 6556)
- sysarddrvs.exe (PID: 6904)
- sysmablsvr.exe (PID: 6932)
- Downaqzh.exe (PID: 1288)
- 2692121105.exe (PID: 2532)
- sysmysldrv.exe (PID: 2608)
- tpeinf.exe (PID: 7148)
- DownSysSoft.exe (PID: 3384)
- 15633737.exe (PID: 6924)
- npp.exe (PID: 3700)
- pei.exe (PID: 32)
- sylsplvc.exe (PID: 6832)
- 309071531.exe (PID: 7184)
- WerFault.exe (PID: 7300)
- 4363463463464363463463463.exe (PID: 7116)
- explorer.exe (PID: 4552)
- poolsdnkjfdbndklsnfgb.exe (PID: 8020)
- powershell.exe (PID: 8336)
- powershell.exe (PID: 8960)
- WerFault.exe (PID: 6864)
- WerFault.exe (PID: 9424)
- Botkiller.exe (PID: 1236)
- SearchApp.exe (PID: 7652)
- WerFault.exe (PID: 8952)
Process checks computer location settings
- 4363463463464363463463463.exe (PID: 6556)
- sysarddrvs.exe (PID: 6904)
- sysmysldrv.exe (PID: 2608)
- QuizPokemon.exe (PID: 5292)
- 4363463463464363463463463.exe (PID: 7116)
- random.exe (PID: 8028)
- Botkiller.exe (PID: 8424)
- loader.exe (PID: 5072)
- rhsgn_protected.exe (PID: 5900)
- ARA.exe (PID: 6816)
- Msblockreview.exe (PID: 4100)
- Hokej.exe (PID: 1492)
- Msblockreview.exe (PID: 8944)
- Botkiller.exe (PID: 1236)
- SRBIJA~1.tmp (PID: 9460)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 6556)
- sylsplvc.exe (PID: 6832)
- 4363463463464363463463463.exe (PID: 7116)
- sysarddrvs.exe (PID: 6904)
- sysmablsvr.exe (PID: 6932)
- poolsdnkjfdbndklsnfgb.exe (PID: 8020)
- RegAsm.exe (PID: 8300)
- sysmysldrv.exe (PID: 2608)
- RegAsm.exe (PID: 5152)
- cmd.exe (PID: 9992)
- SCP.Desktop.Client.IssueView.exe (PID: 10168)
- 25072023.exe (PID: 9492)
- Botkiller.exe (PID: 1236)
- NoMoreRansom.exe (PID: 8904)
- Msblockreview.exe (PID: 8944)
- SearchApp.exe (PID: 7652)
- Botkiller.exe (PID: 6236)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 6556)
- build.exe (PID: 5196)
- WerFault.exe (PID: 7300)
- 4363463463464363463463463.exe (PID: 7116)
- poolsdnkjfdbndklsnfgb.exe (PID: 8020)
- WerFault.exe (PID: 6864)
- WerFault.exe (PID: 9424)
- Botkiller.exe (PID: 1236)
- WerFault.exe (PID: 8952)
- Botkiller.exe (PID: 6236)
Reads mouse settings
- Downdd.exe (PID: 5048)
- Downaqzh.exe (PID: 1288)
- DownSysSoft.exe (PID: 3384)
- Shopzilla.pif (PID: 6784)
- clearkhdyy.exe (PID: 6984)
Creates files or folders in the user directory
- sysarddrvs.exe (PID: 6904)
- sysmablsvr.exe (PID: 6932)
- Downaqzh.exe (PID: 1288)
- sysmysldrv.exe (PID: 2608)
- tpeinf.exe (PID: 7148)
- 15633737.exe (PID: 6924)
- Shopzilla.pif (PID: 6784)
- DownSysSoft.exe (PID: 3384)
- wupgrdsv.exe (PID: 3324)
- 309071531.exe (PID: 7184)
- WerFault.exe (PID: 7300)
- explorer.exe (PID: 4552)
- WerFault.exe (PID: 6864)
- 25072023.exe (PID: 9492)
- Botkiller.exe (PID: 1236)
- WerFault.exe (PID: 9424)
- ARA.exe (PID: 6816)
- WerFault.exe (PID: 8952)
- Botkiller.exe (PID: 6236)
Create files in a temporary directory
- sysarddrvs.exe (PID: 6904)
- sysmablsvr.exe (PID: 6932)
- 2692121105.exe (PID: 2532)
- Downaqzh.exe (PID: 1288)
- QuizPokemon.exe (PID: 5292)
- sysmysldrv.exe (PID: 2608)
- tpeinf.exe (PID: 7148)
- 15633737.exe (PID: 6924)
- npp.exe (PID: 3700)
- pei.exe (PID: 32)
- sylsplvc.exe (PID: 6832)
- DownSysSoft.exe (PID: 3384)
- wupgrdsv.exe (PID: 3324)
- 309071531.exe (PID: 7184)
- Installer.exe (PID: 8236)
- hellminer.exe (PID: 8832)
- hellminer.exe (PID: 9160)
- SrbijaSetupHokej.exe (PID: 6536)
- hellminer.exe (PID: 5072)
- SrbijaSetupHokej.tmp (PID: 6812)
- random.exe (PID: 8028)
- adm_atu.exe (PID: 9040)
- Botkiller.exe (PID: 8424)
- loader.exe (PID: 5072)
- rhsgn_protected.exe (PID: 5900)
- NoMoreRansom.exe (PID: 8904)
- Msblockreview.exe (PID: 4100)
- SrbijaSetupHokej.exe (PID: 6124)
- SrbijaSetupHokej.exe (PID: 2508)
- SrbijaSetupHokej.tmp (PID: 6624)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 4168)
- powershell.exe (PID: 6696)
- powershell.exe (PID: 4324)
- powershell.exe (PID: 6752)
- powershell.exe (PID: 7880)
- powershell.exe (PID: 4560)
- powershell.exe (PID: 10092)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4168)
- powershell.exe (PID: 6696)
Manual execution by a user
- powershell.exe (PID: 4324)
- schtasks.exe (PID: 1108)
- powershell.exe (PID: 6752)
- notepad.exe (PID: 7432)
- powershell.exe (PID: 7880)
- 4363463463464363463463463.exe (PID: 7116)
- schtasks.exe (PID: 8048)
- powershell.exe (PID: 4560)
- firefox.exe (PID: 7100)
Drops the executable file immediately after the start
- explorer.exe (PID: 4552)
Application launched itself
- firefox.exe (PID: 7100)
- firefox.exe (PID: 5984)
- chrome.exe (PID: 7964)
- msedge.exe (PID: 6296)
- firefox.exe (PID: 8636)
- firefox.exe (PID: 7812)
- msedge.exe (PID: 8956)
- msedge.exe (PID: 7260)
Reads Microsoft Office registry keys
- firefox.exe (PID: 5984)
- msedge.exe (PID: 8956)
- chrome.exe (PID: 7964)
- firefox.exe (PID: 7812)
- msedge.exe (PID: 6296)
- msedge.exe (PID: 7260)
Checks operating system version
- hellminer.exe (PID: 9160)
- hellminer.exe (PID: 5072)
Reads CPU info
- hellminer.exe (PID: 9160)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 10092)
Creates files in the program directory
- SrbijaSetupHokej.tmp (PID: 6812)
- NoMoreRansom.exe (PID: 8904)
- Hokej.exe (PID: 1492)
- Msblockreview.exe (PID: 8944)
- Botkiller.exe (PID: 1236)
Creates a software uninstall entry
- SrbijaSetupHokej.tmp (PID: 6812)
UPX packer has been detected
- QQ.exe (PID: 8704)
- windows_update.exe (PID: 7288)
- adm_atu.exe (PID: 9040)
- NoMoreRansom.exe (PID: 8904)
.NET Reactor protector has been detected
- Botkiller.exe (PID: 6236)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RisePro
(PID) Process(7008) Shopzilla.pif
C2 (1)3.36.173.8:50500
Strings (55)\Signal
\OpenVPN Connect\profiles
\tlauncher_profiles.json
\Local Storage
\Microsoft\Skype for Desktop\Local Storage
\GHISLER\wcx_ftp.ini
\config.json
\.purple
\ey_tokens.txt
\Growtopia
\Element\Local Storage
\save.dat
frug?0
\launcher_msa_credentials.bin
\TLauncher
\OpenVPN Connect
\databases
\Games
\accounts.txt
\TotalCommander
UaEt,
VaultCloseVault
\.minecraft\launcher_msa_credentials.bin
\Element
\.lunarclient\settings\games\accounts.txt
\Growtopia\save.dat
\Skype
\FeatherClient
\launcher_accounts.json
C:\program files\steam
\wcx_ftp.ini
logins
C:\program files (x86)\steam
\Steam
\launcher_profiles.json
S,{w_6
\.minecraft\launcher_accounts.json
\Battle.net
\config
\accounts.xml
WSASend
\Messengers
\Session Storage
J~|Hw
\.feather\accounts.json
\LunarClient
APPDATA
\.minecraft\launcher_profiles.json
\accounts.json
VaultOpenVault
VaultGetItem
\Minecraft
\FileZilla
\Pidgin
\ICQ\0001
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
490
Monitored processes
341
Malicious processes
56
Suspicious processes
13
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4 | System | [System Process] | |||||||||||||
User: SYSTEM Integrity Level: SYSTEM | |||||||||||||||
| 32 | "C:\Users\admin\Desktop\Files\pei.exe" | C:\Users\admin\Desktop\Files\pei.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 232 | sc stop wuauserv | C:\Windows\SysWOW64\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1062 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 232 | "C:\Users\admin\Desktop\Files\r.exe" | C:\Users\admin\Desktop\Files\r.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 300 | "C:\Users\admin\Desktop\Files\soft.exe" | C:\Users\admin\Desktop\Files\soft.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 304 | schtasks.exe /create /tn "msedge" /sc ONLOGON /tr "'C:\Program Files (x86)\Common Files\msedge.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 936 | C:\WINDOWS\system32\cmd.exe /c color | C:\Windows\System32\cmd.exe | — | hellminer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1060 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1108 | C:\WINDOWS\System32\schtasks.exe /run /tn "Windows Upgrade Manager" | C:\Windows\System32\schtasks.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | schtasks.exe /create /tn "IdleI" /sc MINUTE /mo 6 /tr "'C:\found.000\dir0001.chk\Idle.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
253 290
Read events
252 165
Write events
1 038
Delete events
87
Modification events
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010015000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C00000019000000000000006100630063006F0075006E00740069006E006700700072006F0062006C0065006D002E007200740066003E0020002000000015000000000000006400690072006500630074007100750061006C006900740079002E0070006E0067003E00200020000000130000000000000064006F00750062006C006500640065006100740068002E0070006E0067003E0020002000000014000000000000006600690078006500640064006900730070006C00610079002E007200740066003E00200020000000120000000000000066006C006F00770065007200730065006E0064002E006A00700067003E0020002000000016000000000000006C006500610072006E00670061006C006C00650072006900650073002E007200740066003E0020002000000010000000000000006F0069006C00620065006C006F0077002E006A00700067003E00200020000000140000000000000070006F006C006900740069006300730074006F006F006B002E007200740066003E002000200000001800000000000000720065007400750072006E00730063006F006D006D0075006E006900740079002E006A00700067003E00200020000000190000000000000073006100740065006C006C0069007400650074007200610069006E0069006E0067002E007200740066003E00200020000000160000000000000073006F006D006500740069006D0065007300700065007400650072002E0070006E0067003E00200020000000130000000000000073006F00750074006800730069006D0070006C0065002E007200740066003E00200020000000210000000000000034003300360033003400360033003400360033003400360034003300360033003400360033003400360033003400360033002E006500780065003E00200020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000001500000000000000000000000000000000000000803F0000004008000000803F0000404009000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E0000000040000040400F0000000040000080401000000000400000A040110000004040000000001200000040400000803F1300000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F0700000080410000A0401400 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconNameVersion |
Value: 1 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010015000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C00000019000000000000006100630063006F0075006E00740069006E006700700072006F0062006C0065006D002E007200740066003E0020002000000015000000000000006400690072006500630074007100750061006C006900740079002E0070006E0067003E00200020000000130000000000000064006F00750062006C006500640065006100740068002E0070006E0067003E0020002000000014000000000000006600690078006500640064006900730070006C00610079002E007200740066003E00200020000000120000000000000066006C006F00770065007200730065006E0064002E006A00700067003E0020002000000016000000000000006C006500610072006E00670061006C006C00650072006900650073002E007200740066003E0020002000000010000000000000006F0069006C00620065006C006F0077002E006A00700067003E00200020000000140000000000000070006F006C006900740069006300730074006F006F006B002E007200740066003E002000200000001800000000000000720065007400750072006E00730063006F006D006D0075006E006900740079002E006A00700067003E00200020000000190000000000000073006100740065006C006C0069007400650074007200610069006E0069006E0067002E007200740066003E00200020000000160000000000000073006F006D006500740069006D0065007300700065007400650072002E0070006E0067003E00200020000000130000000000000073006F00750074006800730069006D0070006C0065002E007200740066003E00200020000000210000000000000034003300360033003400360033003400360033003400360034003300360033003400360033003400360033003400360033002E006500780065003E00200020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000001500000000000000000000000000000000000000803F0000004008000000803F0000404009000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E0000000040000040400F0000000040000080401000000000400000A040110000004040000000001200000040400000803F1300000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F070000004040000000401400 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 21A9AE6600000000 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Security and Maintenance\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 23004100430042006C006F00620000000000000000000000010000000000000074006600 | |||
| (PID) Process: | (6556) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6556) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6556) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6556) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6556) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
Executable files
333
Suspicious files
582
Text files
231
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6556 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\t2.exe | executable | |
MD5:ABABCA6D12D96E8DD2F1D7114B406FAE | SHA256:A992920E64A64763F3DD8C2A431A0F5E56E5B3782A1496DE92BC80EE71CCA5BA | |||
| 4552 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 6556 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\t.exe | executable | |
MD5:E2E3268F813A0C5128FF8347CBAA58C8 | SHA256:D8B83F78ED905A7948E2E1E371F0F905BCAAABBB314C692FEE408A454F8338A3 | |||
| 6556 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\a.exe | executable | |
MD5:ABABCA6D12D96E8DD2F1D7114B406FAE | SHA256:A992920E64A64763F3DD8C2A431A0F5E56E5B3782A1496DE92BC80EE71CCA5BA | |||
| 4168 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_sblpfkft.arj.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6828 | a.exe | C:\Windows\sysmablsvr.exe | executable | |
MD5:ABABCA6D12D96E8DD2F1D7114B406FAE | SHA256:A992920E64A64763F3DD8C2A431A0F5E56E5B3782A1496DE92BC80EE71CCA5BA | |||
| 6556 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\twztl.exe | executable | |
MD5:ABABCA6D12D96E8DD2F1D7114B406FAE | SHA256:A992920E64A64763F3DD8C2A431A0F5E56E5B3782A1496DE92BC80EE71CCA5BA | |||
| 6780 | t.exe | C:\Windows\sysarddrvs.exe | executable | |
MD5:E2E3268F813A0C5128FF8347CBAA58C8 | SHA256:D8B83F78ED905A7948E2E1E371F0F905BCAAABBB314C692FEE408A454F8338A3 | |||
| 6556 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\tdrpload.exe | executable | |
MD5:ABABCA6D12D96E8DD2F1D7114B406FAE | SHA256:A992920E64A64763F3DD8C2A431A0F5E56E5B3782A1496DE92BC80EE71CCA5BA | |||
| 1288 | Downaqzh.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\List[1] | text | |
MD5:FC23051837F44A36F5E703A468766DBE | SHA256:CCE751048E0D0C230C84F9D95537F34E568D68F80358EC747C5F024EE9926627 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
140
TCP/UDP connections
445
DNS requests
283
Threats
278
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6904 | sysarddrvs.exe | GET | 200 | 185.215.113.66:80 | http://185.215.113.66/1 | unknown | — | — | unknown |
6904 | sysarddrvs.exe | GET | 200 | 185.215.113.66:80 | http://185.215.113.66/1 | unknown | — | — | unknown |
2204 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2204 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6572 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6532 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6556 | 4363463463464363463463463.exe | GET | 200 | 185.215.113.66:80 | http://cef331d9-c605-4d06-aa84-b25d5c7662ac.random.fihsifuiiusuiuduf.com/tdrpload.exe | unknown | — | — | malicious |
1288 | Downaqzh.exe | GET | 200 | 58.23.215.23:8765 | http://wieie.cn:8765/Down/List | unknown | — | — | malicious |
2532 | 2692121105.exe | GET | 404 | 185.215.113.66:80 | http://twizt.net/BNTOTSTATS | unknown | — | — | malicious |
6556 | 4363463463464363463463463.exe | GET | 200 | 185.215.113.66:80 | http://faf52996-68c1-46a1-b531-b14d611d20e3.random.aefiabeuodbauobfafoebbf.net/twztl.exe | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4064 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5632 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6556 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
6556 | 4363463463464363463463463.exe | 185.215.113.84:80 | support.tsrv1.ws | 1337team Limited | SC | unknown |
6556 | 4363463463464363463463463.exe | 185.215.113.66:80 | rfddsdaajbs.fihsifuiiusuiuduf.com | 1337team Limited | SC | unknown |
6556 | 4363463463464363463463463.exe | 58.23.215.171:8765 | — | CHINA UNICOM China169 Backbone | CN | unknown |
4064 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
support.tsrv1.ws |
| malicious |
b66c2ee0-f77f-455c-bb30-9b845f1006cb.random.tsrv1.ws |
| malicious |
rfddsdaajbs.fihsifuiiusuiuduf.com |
| unknown |
72ec8d09-fce8-4272-9829-f4a17ae33269.random.tsrv1.ws |
| malicious |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6556 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
6556 | 4363463463464363463463463.exe | A Network Trojan was detected | ET MALWARE Single char EXE direct download likely trojan (multiple families) |
6556 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
6556 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
6556 | 4363463463464363463463463.exe | A Network Trojan was detected | ET MALWARE Single char EXE direct download likely trojan (multiple families) |
6556 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
6556 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
6556 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
6556 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
6556 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
34 ETPRO signatures available at the full report
Process | Message |
|---|---|
4363463463464363463463463.exe | An exception occurred during a WebClient request.
|
4363463463464363463463463.exe | An exception occurred during a WebClient request.
|