| File name: | 1208_37832604.doc |
| Full analysis: | https://app.any.run/tasks/97ee5bcf-3c9f-4207-95aa-e1f94d9294b9 |
| Verdict: | Malicious activity |
| Analysis date: | March 25, 2025, 06:53:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Author: BigAdministrator, Template: Normal.dotm, Last Saved By: win7home, Revision Number: 2, Name of Creating Application: Microsoft Office Word, Create Time/Date: Tue Dec 8 10:58:00 2020, Last Saved Time/Date: Tue Dec 8 10:58:00 2020, Number of Pages: 1, Number of Words: 3, Number of Characters: 19, Security: 0 |
| MD5: | 14450C99698F1725A1933879D104C404 |
| SHA1: | 5FA27C4C455D168BF0EFCED37869B8F840D3DC4D |
| SHA256: | 2FBFF281B9D4D240EF5A800C08CF26D4D4944E73227860A7C4AFEB3B11615238 |
| SSDEEP: | 12288:auE0gXPByytkPiieVC2P3Bd1pJhw5EHkf13VbIkqC0Jo:au3gXPQ2kiie/3BJwskt3VbnqCD |
MALICIOUS
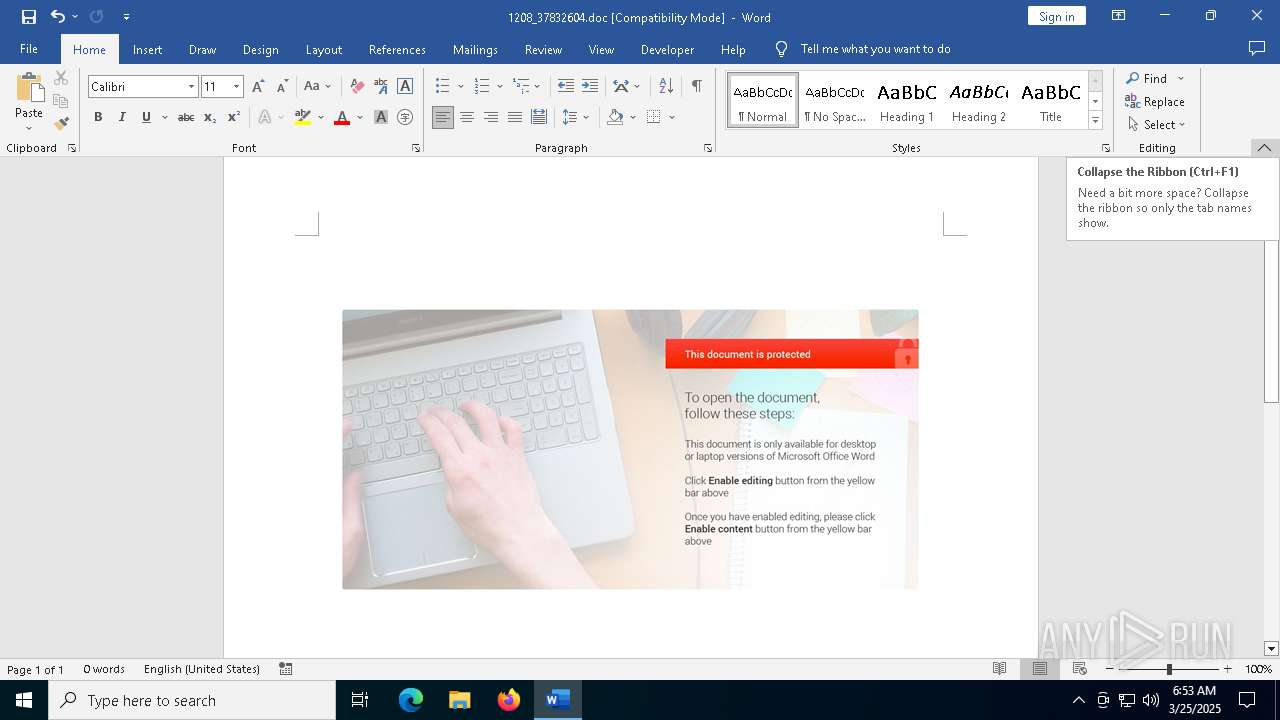
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 7344)
Unusual execution from MS Office
- WINWORD.EXE (PID: 7344)
SUSPICIOUS
Uses RUNDLL32.EXE to load library
- WINWORD.EXE (PID: 7344)
Creates FileSystem object to access computer's file system (SCRIPT)
- WINWORD.EXE (PID: 7344)
Checks for external IP
- rundll32.exe (PID: 7304)
INFO
Reads security settings of Internet Explorer
- splwow64.exe (PID: 8028)
- rundll32.exe (PID: 7304)
The sample compiled with english language support
- WINWORD.EXE (PID: 7344)
Checks proxy server information
- rundll32.exe (PID: 7304)
Reads the software policy settings
- slui.exe (PID: 7792)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | Has picture, 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | - |
| Subject: | - |
| Author: | BigAdministrator |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | win7home |
| Software: | Microsoft Office Word |
| CreateDate: | 2020:12:08 10:58:00 |
| ModifyDate: | 2020:12:08 10:58:00 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| CharCountWithSpaces: | 21 |
| AppVersion: | 15 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 2 |
| TotalEditTime: | - |
| Words: | 3 |
| Characters: | 19 |
| Pages: | 1 |
| Paragraphs: | 1 |
| Lines: | 1 |
Total processes
145
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1096 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2140 | "C:\Windows\System32\rundll32.exe" C:\Users\admin\AppData\Roaming\Microsoft\Templates\W0rd.dll,DllUnregisterServer | C:\Windows\System32\rundll32.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7304 | "C:\Windows\System32\rundll32.exe" C:\Users\admin\AppData\Roaming\Microsoft\Templates\W0rd.dll,DllUnregisterServer | C:\Windows\SysWOW64\rundll32.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7336 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "76DD8CA8-C8CF-4385-81A9-6EBA18917642" "84AC4342-8DDD-4AF7-8435-CB8A45B0EDE3" "7344" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 7344 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n C:\Users\admin\AppData\Local\Temp\1208_37832604.doc /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 7760 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7792 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8028 | C:\WINDOWS\splwow64.exe 8192 | C:\Windows\splwow64.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Print driver host for applications Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 972
Read events
15 580
Write events
368
Delete events
24
Modification events
| (PID) Process: | (7344) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (7344) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\7344 |
| Operation: | write | Name: | 0 |
Value: 0B0E107FDD70D70F991840A54FE0ED85735498230046CACDBAF0A9AAE7ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511B039D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (7344) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (7344) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (7344) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (7344) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (7344) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (7344) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (7344) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (7344) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
35
Suspicious files
124
Text files
17
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7344 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:7407585AE3E302E55697B0FCF885B407 | SHA256:0F7CF40D43C719E71522A47B0A7A7B65ADA9D50FBB4BD361EB95BD4A94B0EE77 | |||
| 7344 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{077A9697-6C65-496D-AB8B-2FA9E905AF54}\{C8A0B81F-765F-453F-9D6F-939868CB45F9}\ya.wav | executable | |
MD5:F8A02665A416F335A420E9033CDBB08F | SHA256:EC1FDA96044F67ABF36E7D3DDBF9FDB06B9FBA9C7D29761487221568746DD05B | |||
| 7344 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\237C294B-1104-4713-9CA1-30A3E619F694 | xml | |
MD5:C0EE2CD063CAC54EFFCD6F464B3352C3 | SHA256:3E17BB51F71E8268B5A13BC7AEE3AE63F4EC6AD931AF837E21578D146475593A | |||
| 7344 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 7344 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | binary | |
MD5:AA73217F15B87241EBBAD2690EDB05CE | SHA256:E4F5942E60EACD12F35A426FA7CD48664262BEE5B8A29B12C0290475369C88FD | |||
| 7344 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:DC7E64A04D2AC09BF4BEACD6C6CCA67F | SHA256:290D13B2254D582AED1A054DD0E2C6EBF14DD4A97282D9088414A9B7A5A3181A | |||
| 7344 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\W0rd.dll | executable | |
MD5:F8A02665A416F335A420E9033CDBB08F | SHA256:EC1FDA96044F67ABF36E7D3DDBF9FDB06B9FBA9C7D29761487221568746DD05B | |||
| 7344 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json | binary | |
MD5:CEB24B7D8C151C05ECD084C21D120F18 | SHA256:271E4ACB18B2CFB185D14CC010C0177679D449F5E9ED5E8228C6E9E3E80345EB | |||
| 7344 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json.tmp | binary | |
MD5:CEB24B7D8C151C05ECD084C21D120F18 | SHA256:271E4ACB18B2CFB185D14CC010C0177679D449F5E9ED5E8228C6E9E3E80345EB | |||
| 7344 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{077A9697-6C65-496D-AB8B-2FA9E905AF54}\{C8A0B81F-765F-453F-9D6F-939868CB45F9}\ya.wav:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
75
DNS requests
33
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7344 | WINWORD.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
8084 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7344 | WINWORD.EXE | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
7344 | WINWORD.EXE | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | whitelisted |
7344 | WINWORD.EXE | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | whitelisted |
7344 | WINWORD.EXE | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
7344 | WINWORD.EXE | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
7344 | WINWORD.EXE | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.16.164.72:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7344 | WINWORD.EXE | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
7344 | WINWORD.EXE | 52.123.130.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7344 | WINWORD.EXE | 2.16.168.119:443 | omex.cdn.office.net | Akamai International B.V. | RU | whitelisted |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.31.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7304 | rundll32.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External IP Lookup by HTTP (api .ipify .org) |
7304 | rundll32.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup api.ipify.org |
— | — | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
7304 | rundll32.exe | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] An IP address was received from the server as a result of an HTTP request |