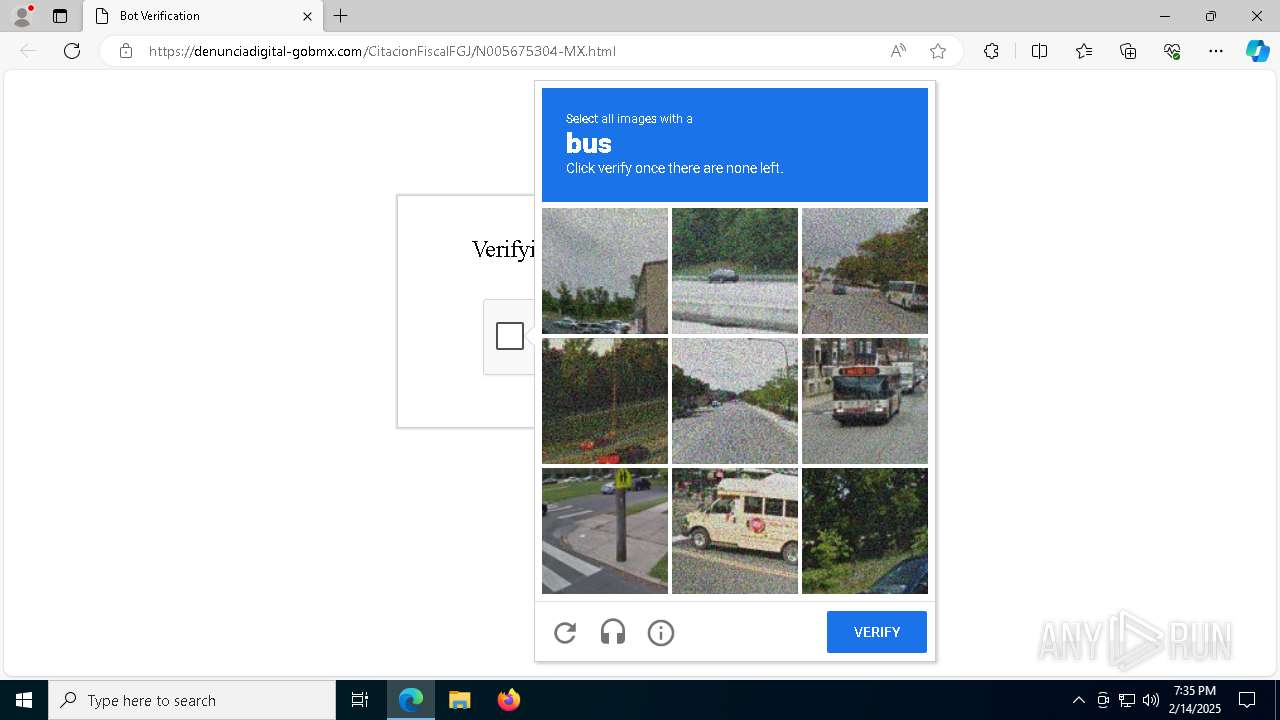
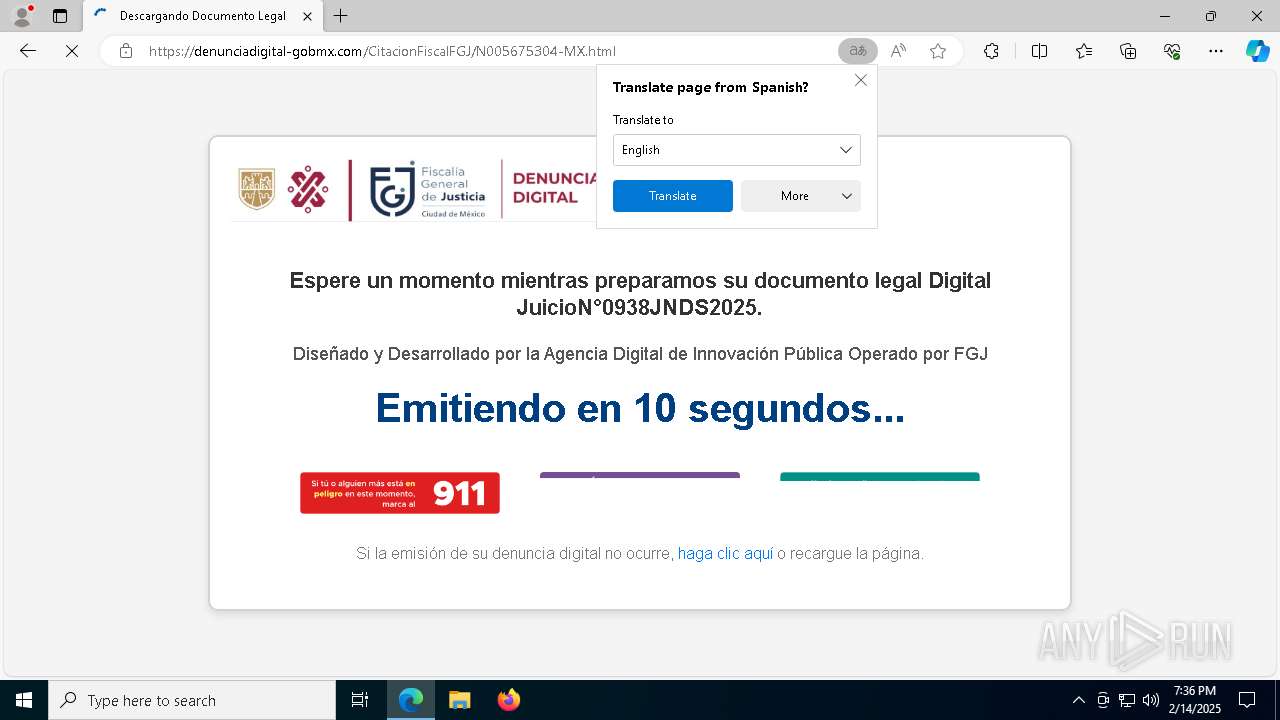
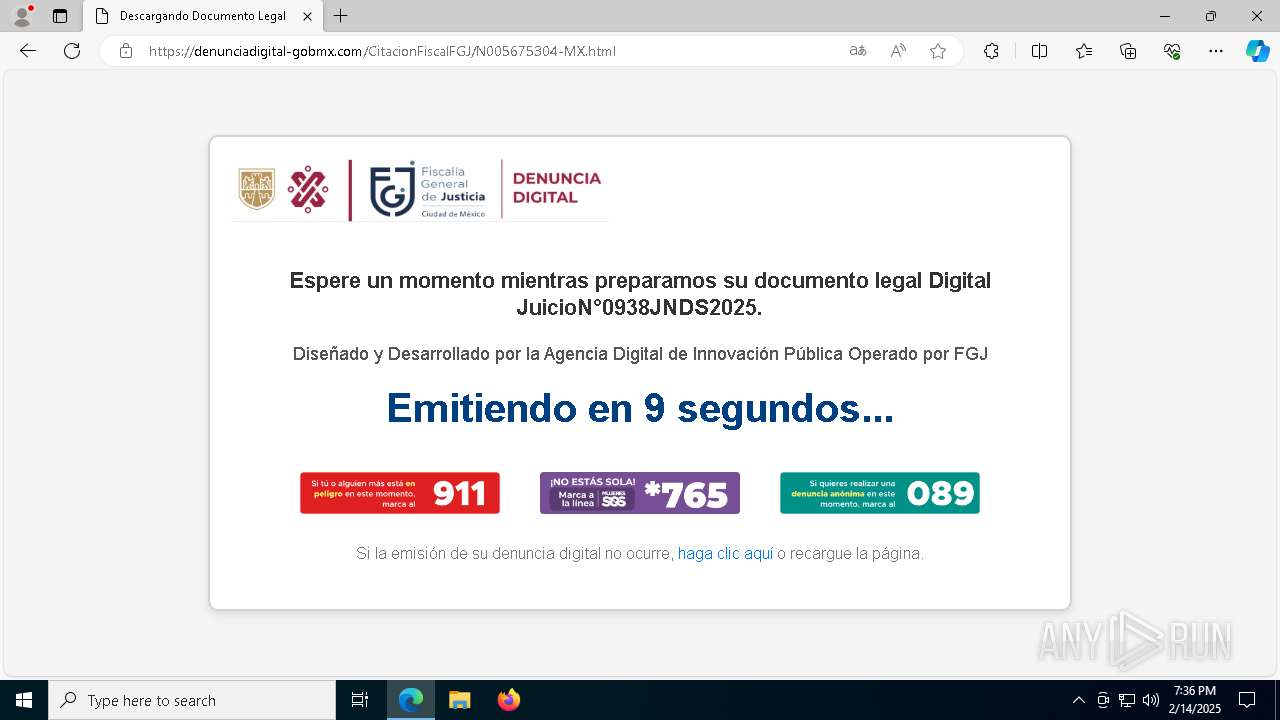
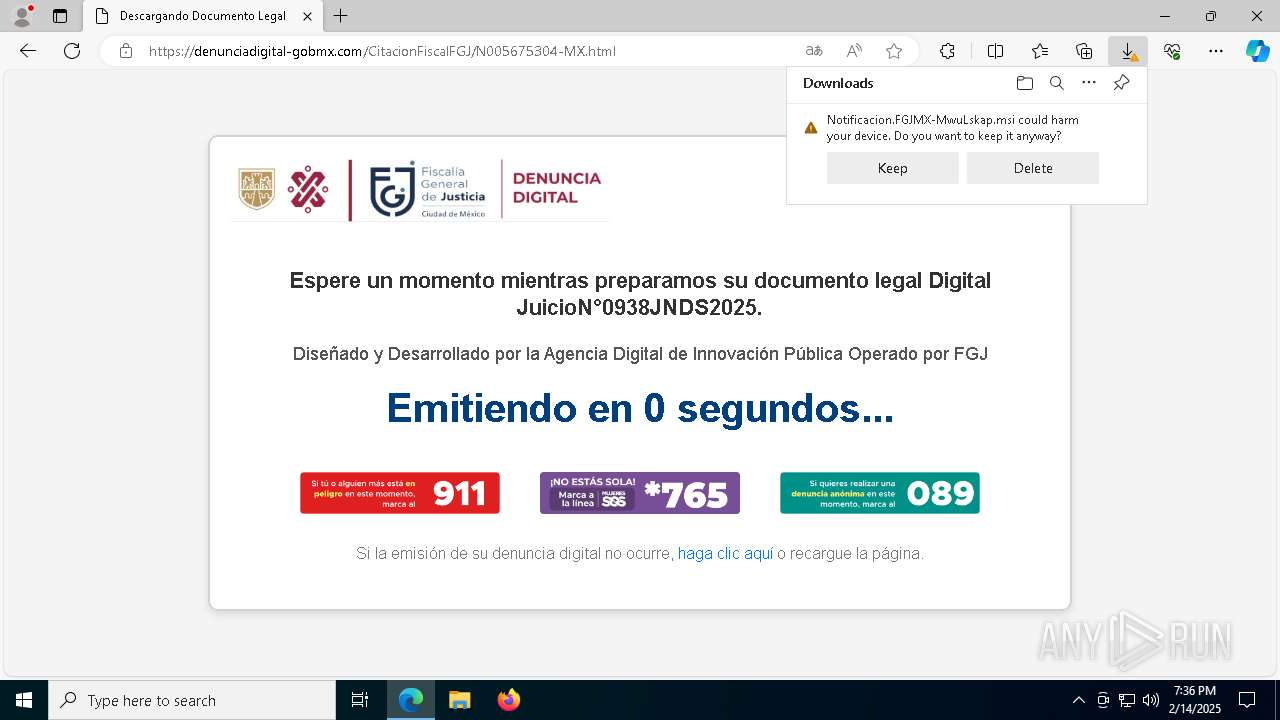
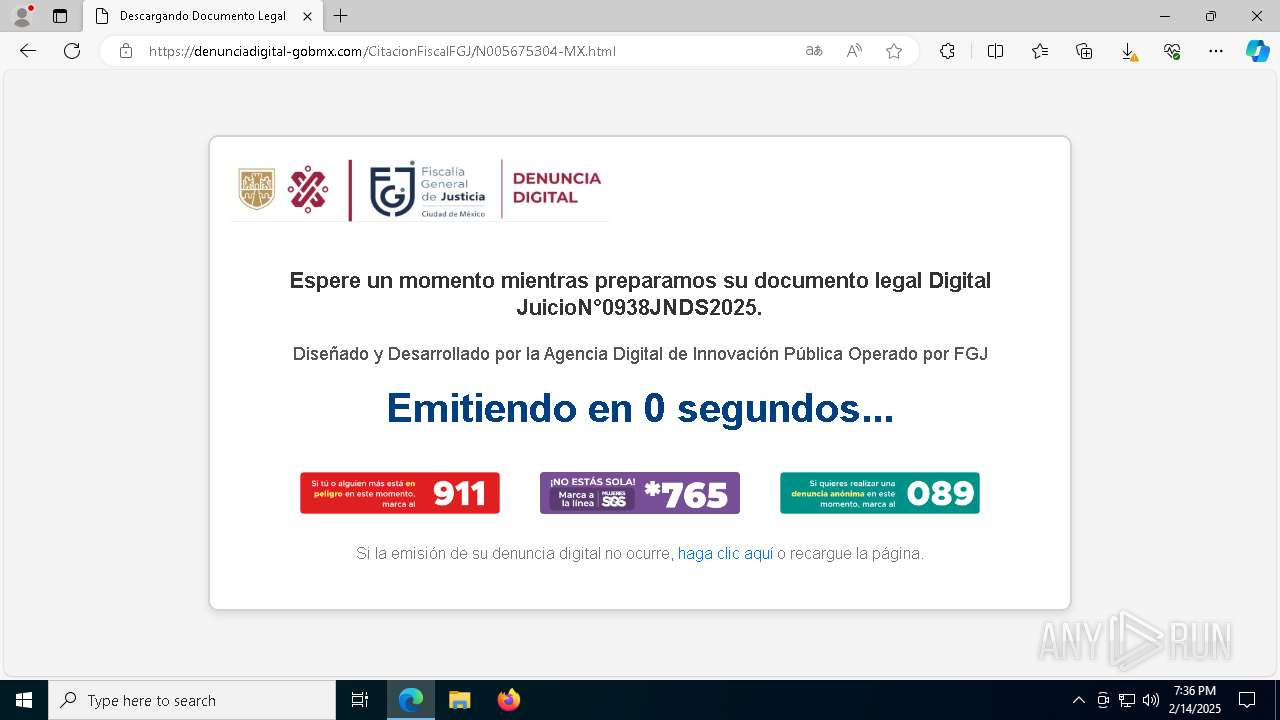
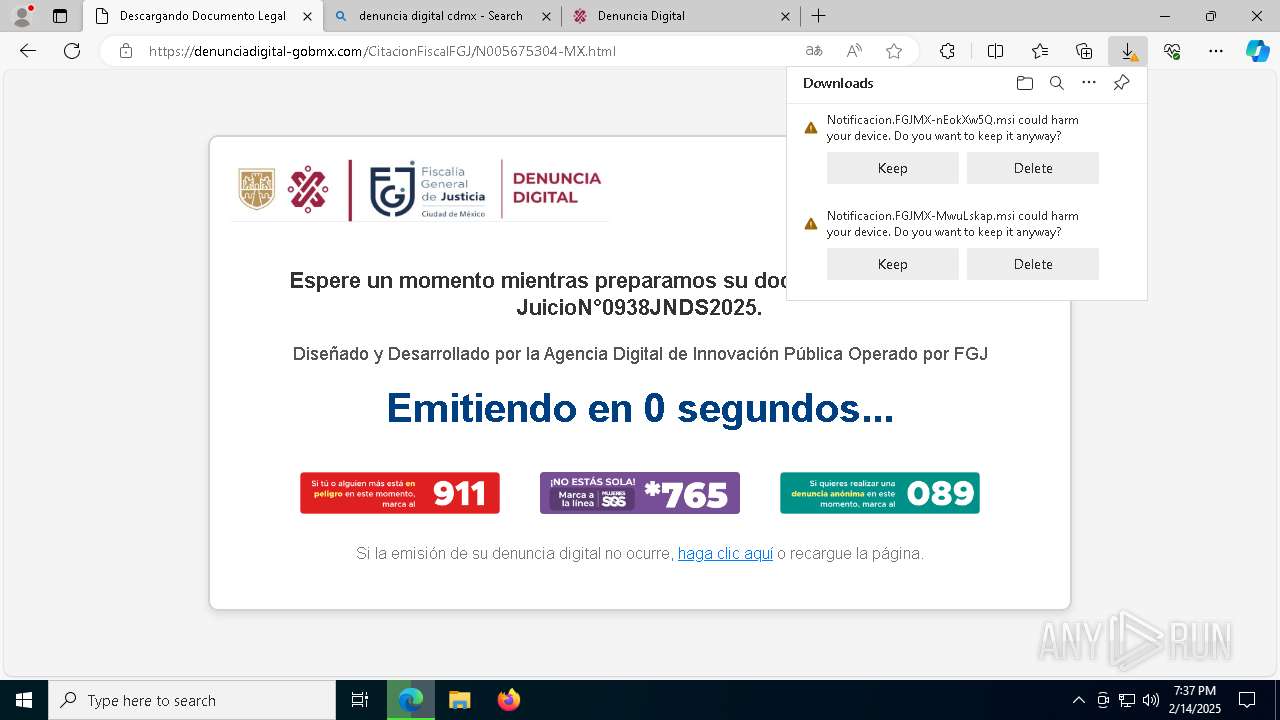
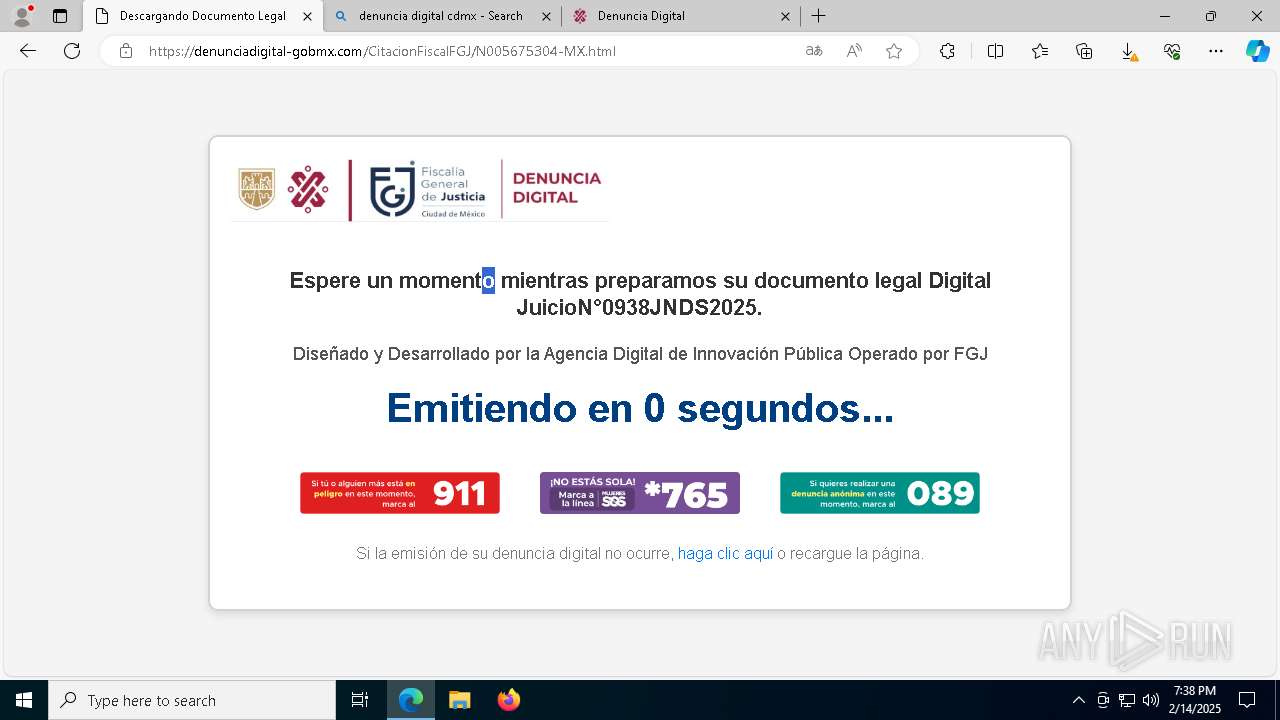
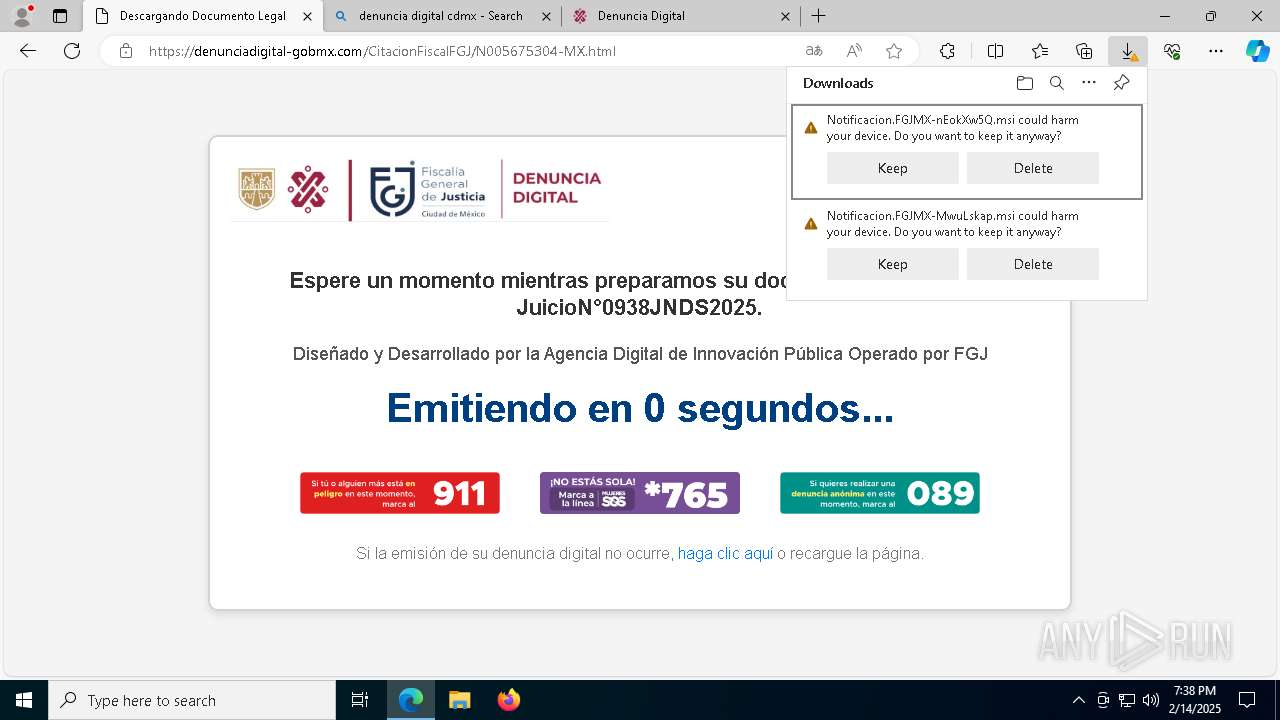
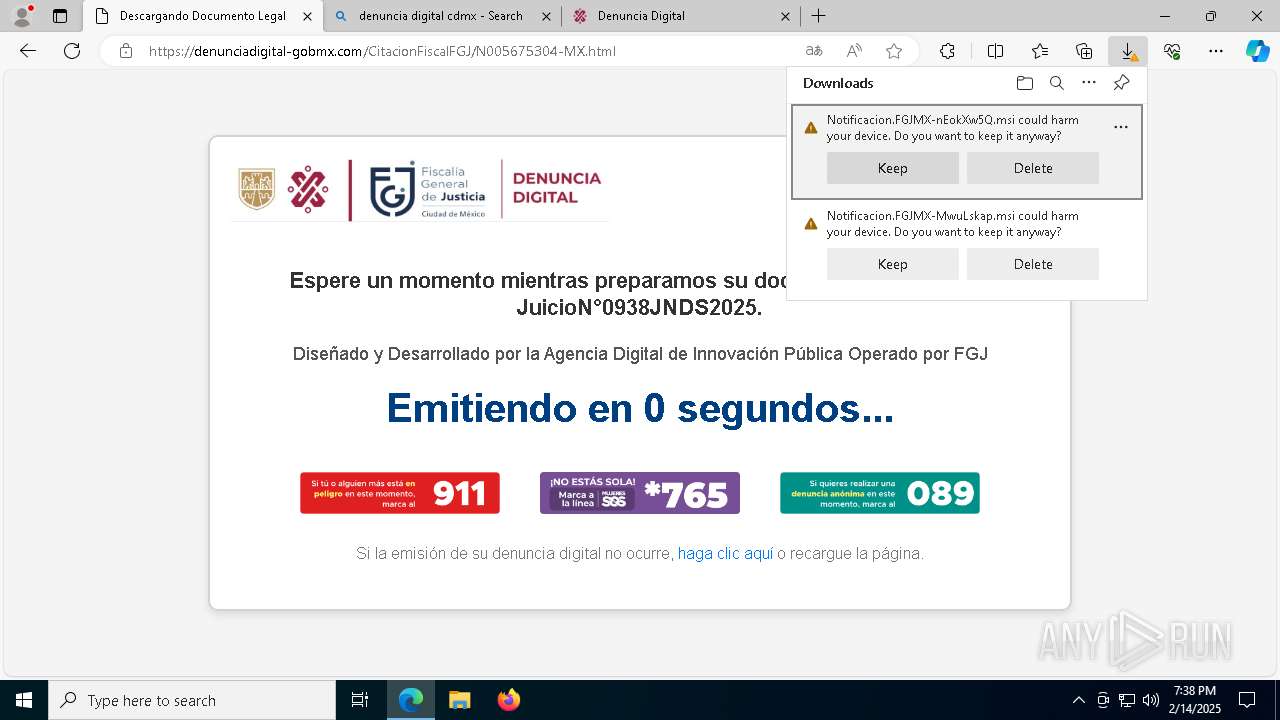
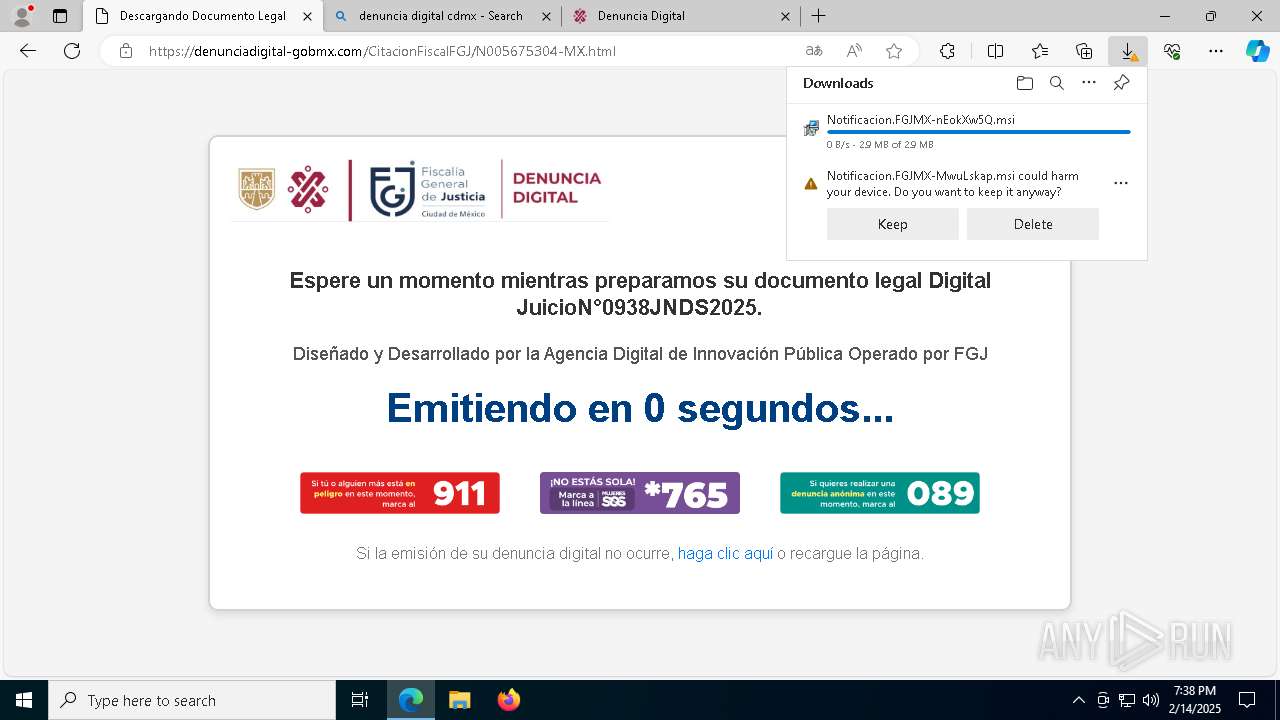
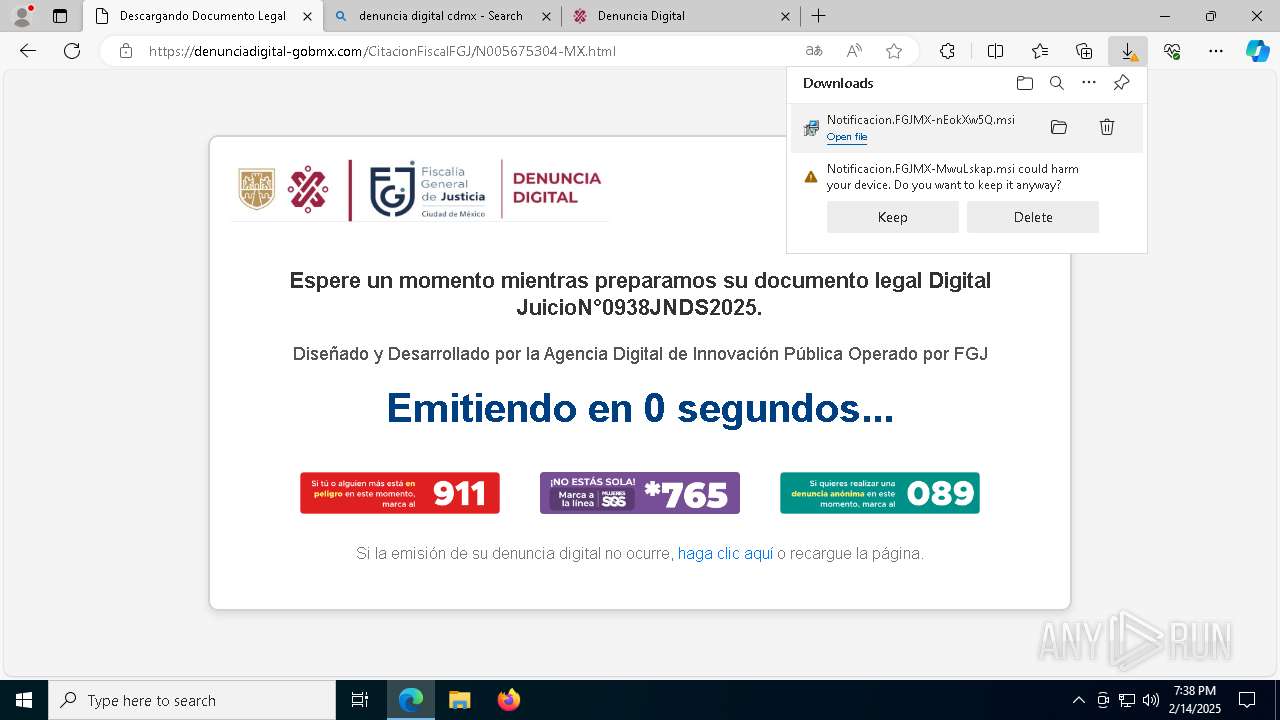
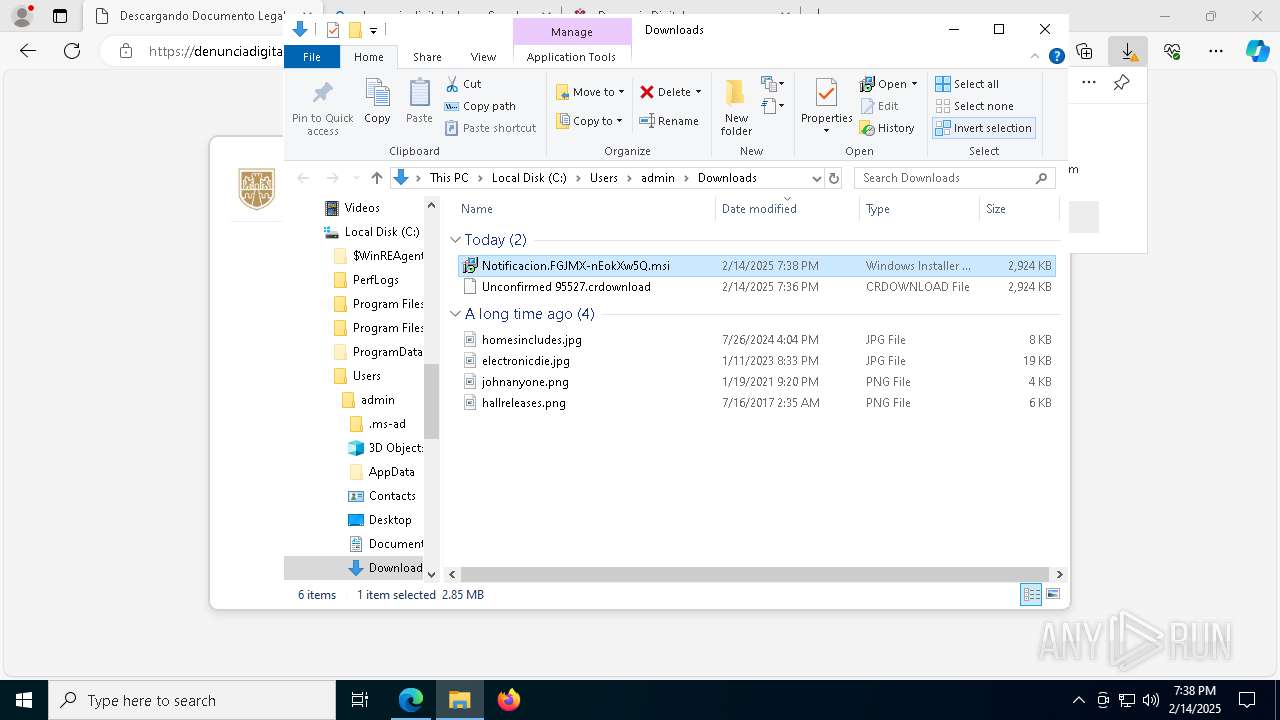
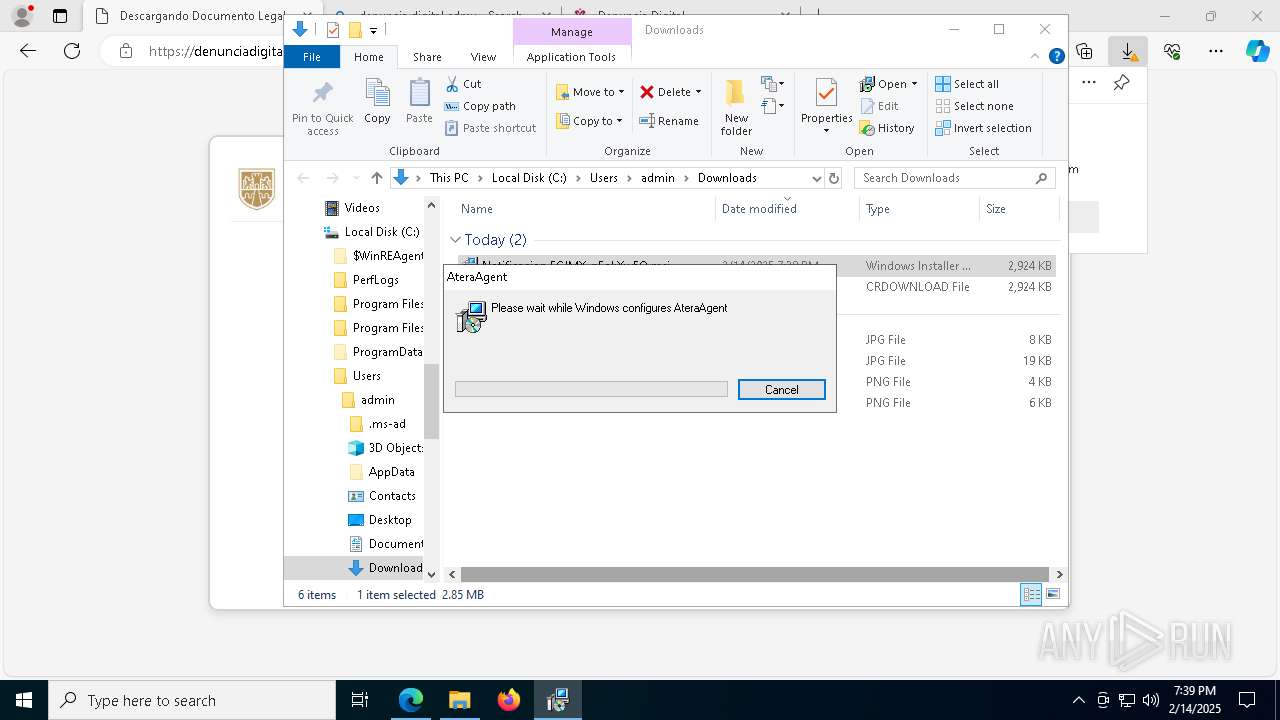
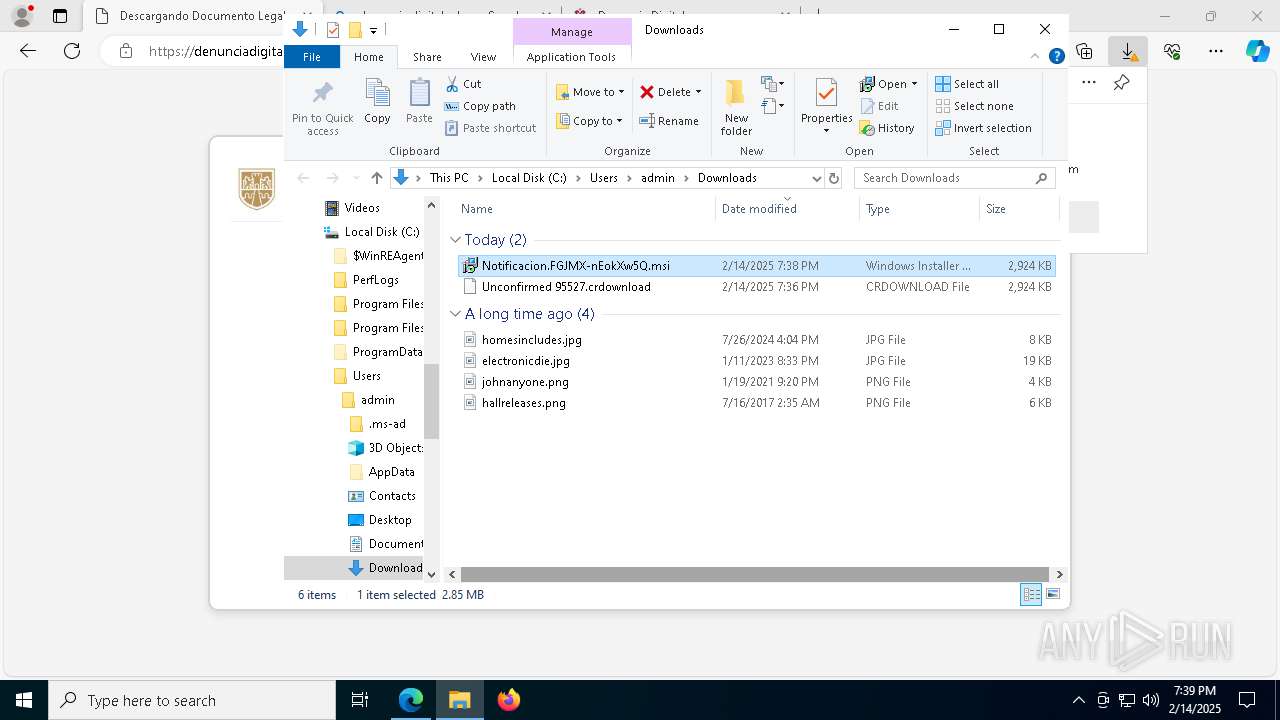
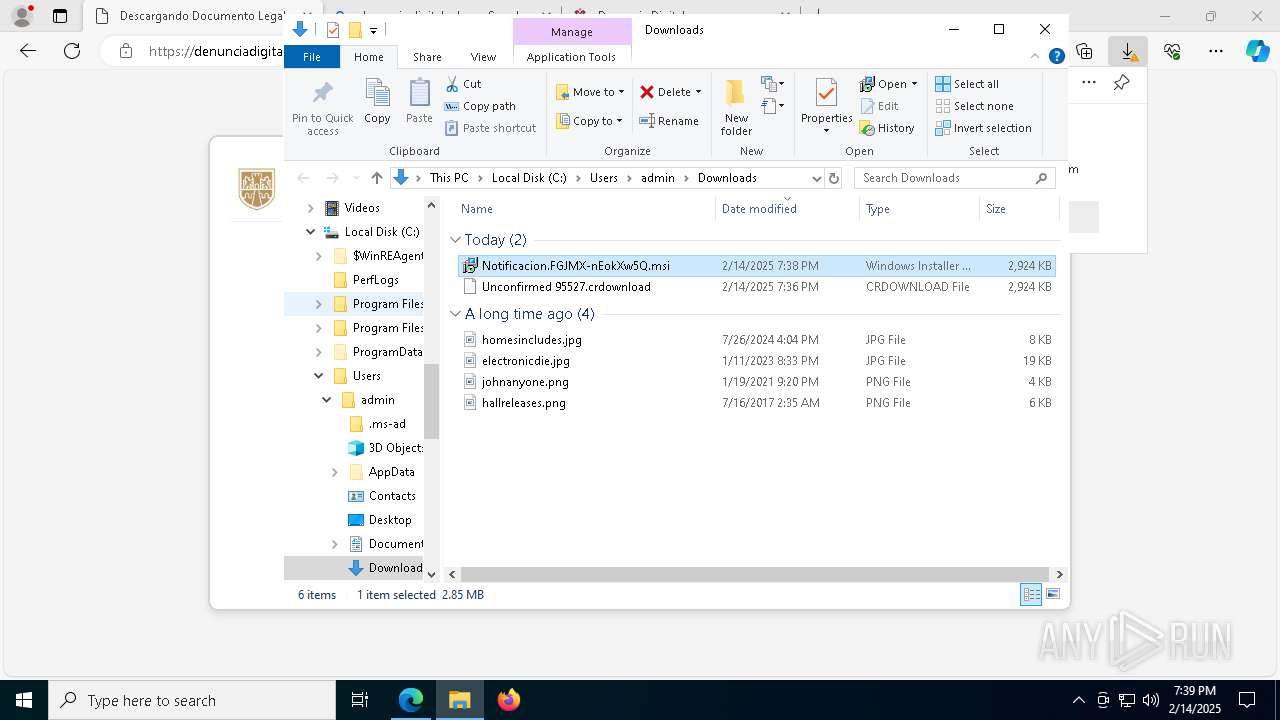
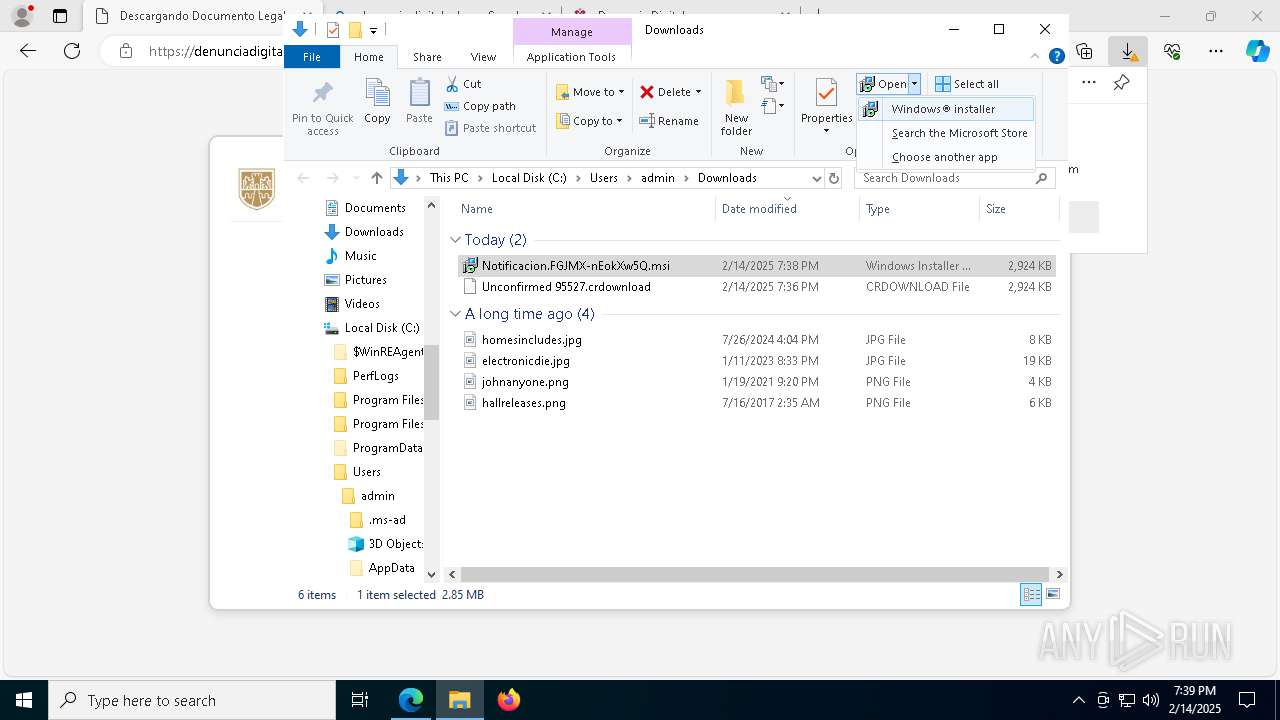
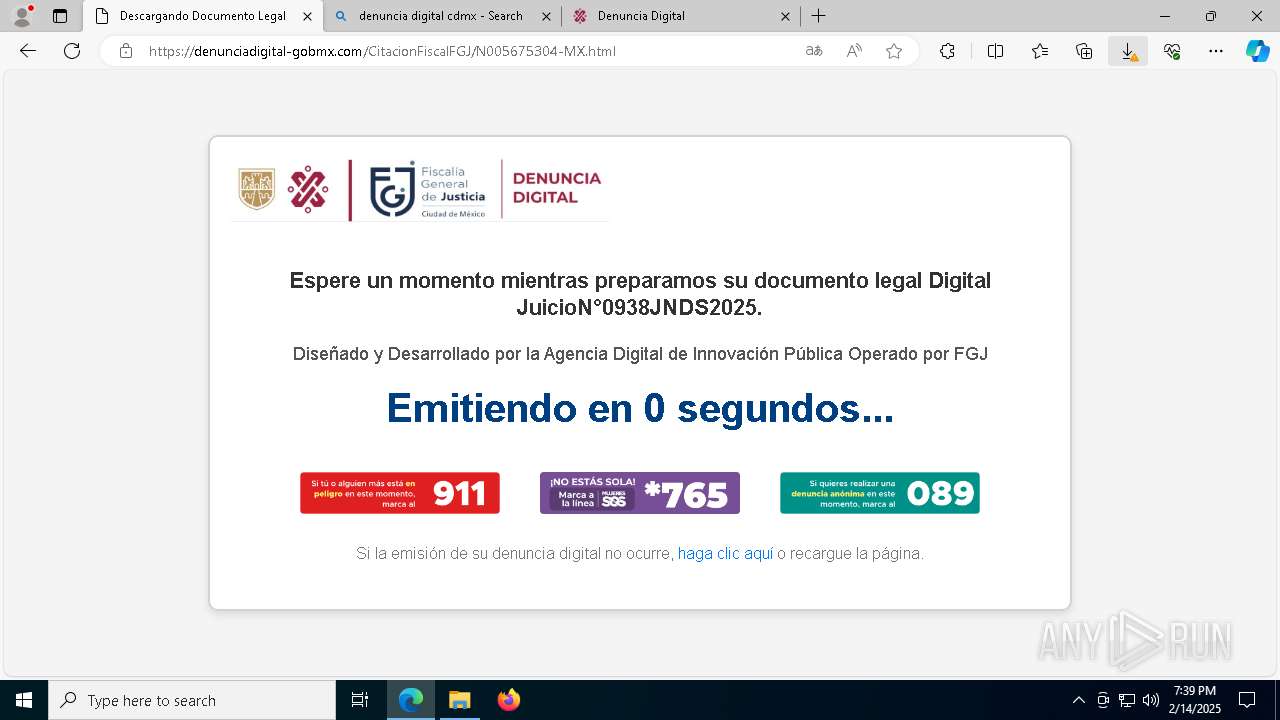
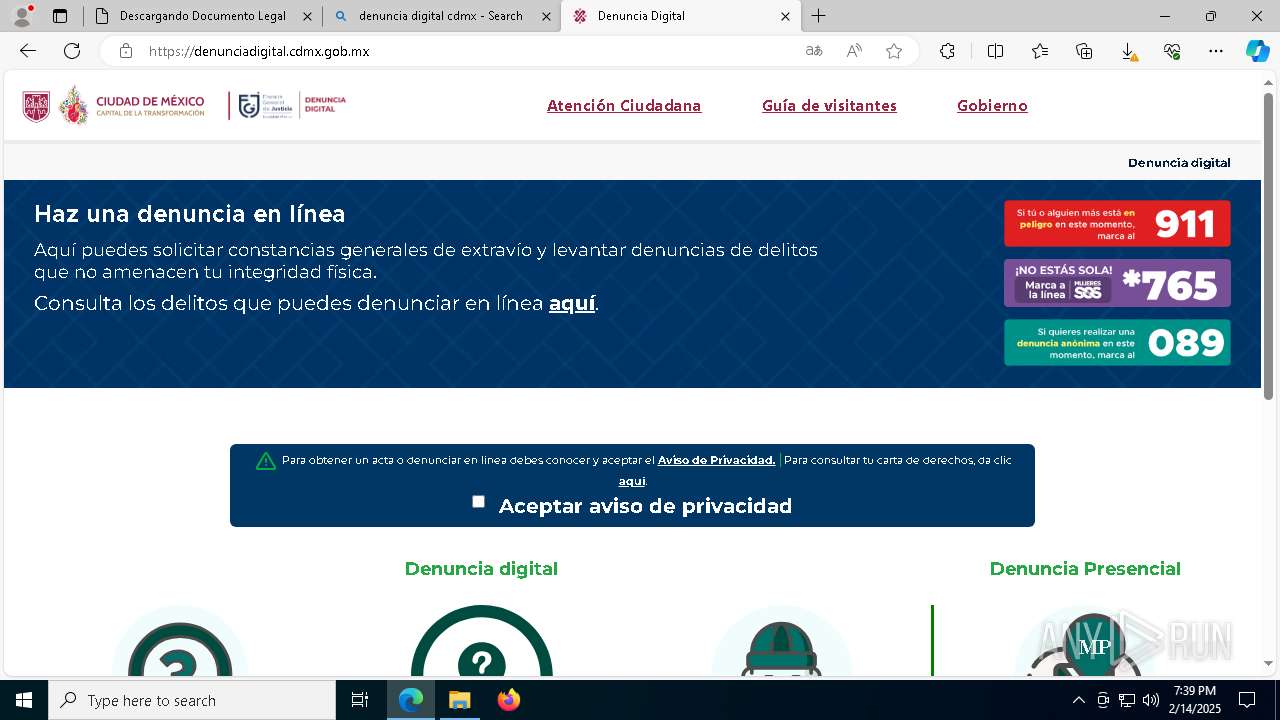
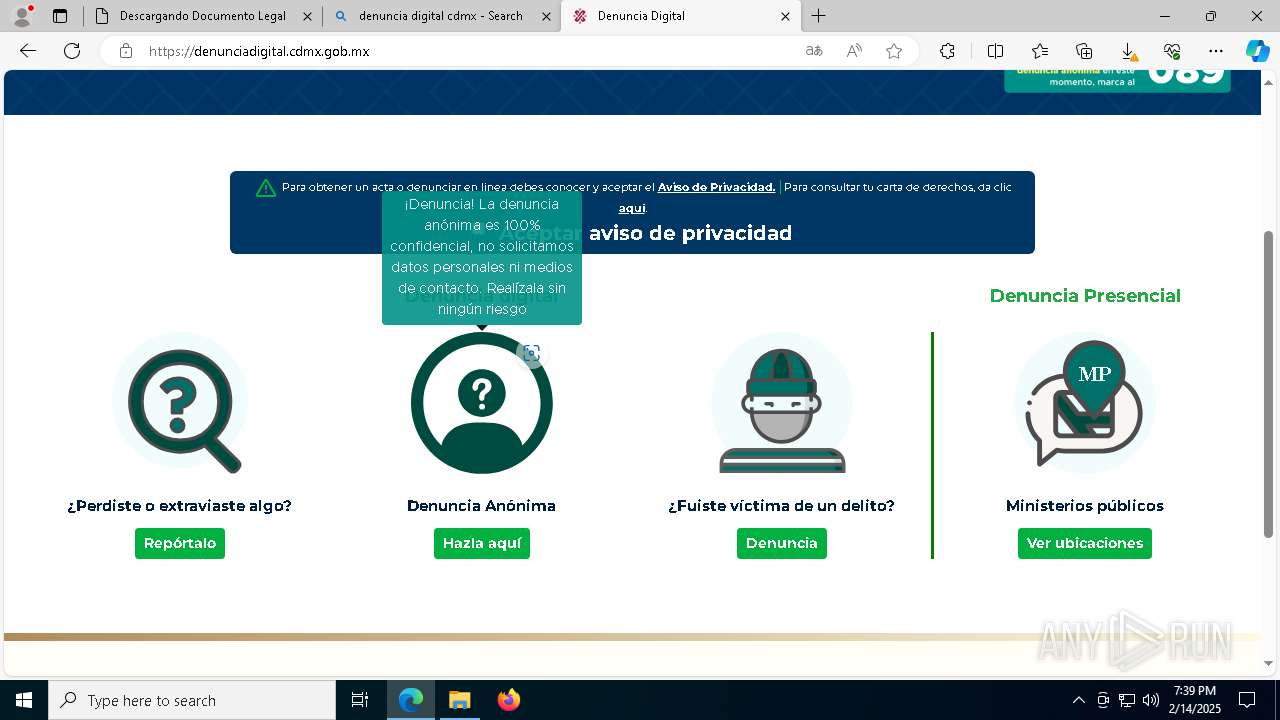
| URL: | https://denunciadigital-gobmx.com/CitacionFiscalFGJ/N005675304-MX.html |
| Full analysis: | https://app.any.run/tasks/2edc7e0b-36b0-48c0-a110-a93ad52ae177 |
| Verdict: | Malicious activity |
| Analysis date: | February 14, 2025, 19:35:13 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 25911098838E285FD897CC3AB0F31922 |
| SHA1: | 9C4DDA1080DC5A4AC14B6D62FDEAC803E8CFCFCA |
| SHA256: | 2FBFBBAC4747C284E915CA61CDEB97BA01674E49A7A9E207A7E35708E3836957 |
| SSDEEP: | 3:N8Y2E6lkIirWVYiSRVpUJn:2Y+BdVJSRVpQn |
MALICIOUS
Starts NET.EXE for service management
- msiexec.exe (PID: 372)
- net.exe (PID: 7516)
Bypass execution policy to execute commands
- powershell.exe (PID: 9040)
Changes powershell execution policy (Bypass)
- AgentPackageAgentInformation.exe (PID: 3888)
SUSPICIOUS
Process drops legitimate windows executable
- msedge.exe (PID: 6464)
- msedge.exe (PID: 5892)
- msiexec.exe (PID: 6280)
- AteraAgent.exe (PID: 904)
- AteraAgent.exe (PID: 7668)
Creates file in the systems drive root
- explorer.exe (PID: 4488)
Executes as Windows Service
- VSSVC.exe (PID: 6244)
- AteraAgent.exe (PID: 904)
- AteraAgent.exe (PID: 7668)
Checks Windows Trust Settings
- msiexec.exe (PID: 6280)
- AteraAgent.exe (PID: 3796)
- msiexec.exe (PID: 2280)
Executable content was dropped or overwritten
- rundll32.exe (PID: 5000)
- rundll32.exe (PID: 7672)
- rundll32.exe (PID: 4132)
- rundll32.exe (PID: 5200)
- AteraAgent.exe (PID: 904)
- csc.exe (PID: 7672)
- SplashtopStreamer.exe (PID: 4864)
- PreVerCheck.exe (PID: 1828)
- AteraAgent.exe (PID: 7668)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6280)
Potential Corporate Privacy Violation
- rundll32.exe (PID: 7672)
- AteraAgent.exe (PID: 904)
- rundll32.exe (PID: 5200)
- AgentPackageAgentInformation.exe (PID: 6388)
- AgentPackageAgentInformation.exe (PID: 5028)
- AteraAgent.exe (PID: 7668)
- AgentPackageAgentInformation.exe (PID: 3888)
- AgentPackageMonitoring.exe (PID: 7356)
Uses TASKKILL.EXE to kill process
- msiexec.exe (PID: 372)
- cmd.exe (PID: 6908)
- cmd.exe (PID: 8240)
- cmd.exe (PID: 8340)
- cmd.exe (PID: 8464)
- cmd.exe (PID: 8564)
- cmd.exe (PID: 8664)
- cmd.exe (PID: 8864)
- cmd.exe (PID: 8964)
- cmd.exe (PID: 9152)
- cmd.exe (PID: 8764)
Reads security settings of Internet Explorer
- AteraAgent.exe (PID: 3796)
- AteraAgent.exe (PID: 904)
- AteraAgent.exe (PID: 7668)
- AgentPackageAgentInformation.exe (PID: 3888)
- SplashtopStreamer.exe (PID: 4864)
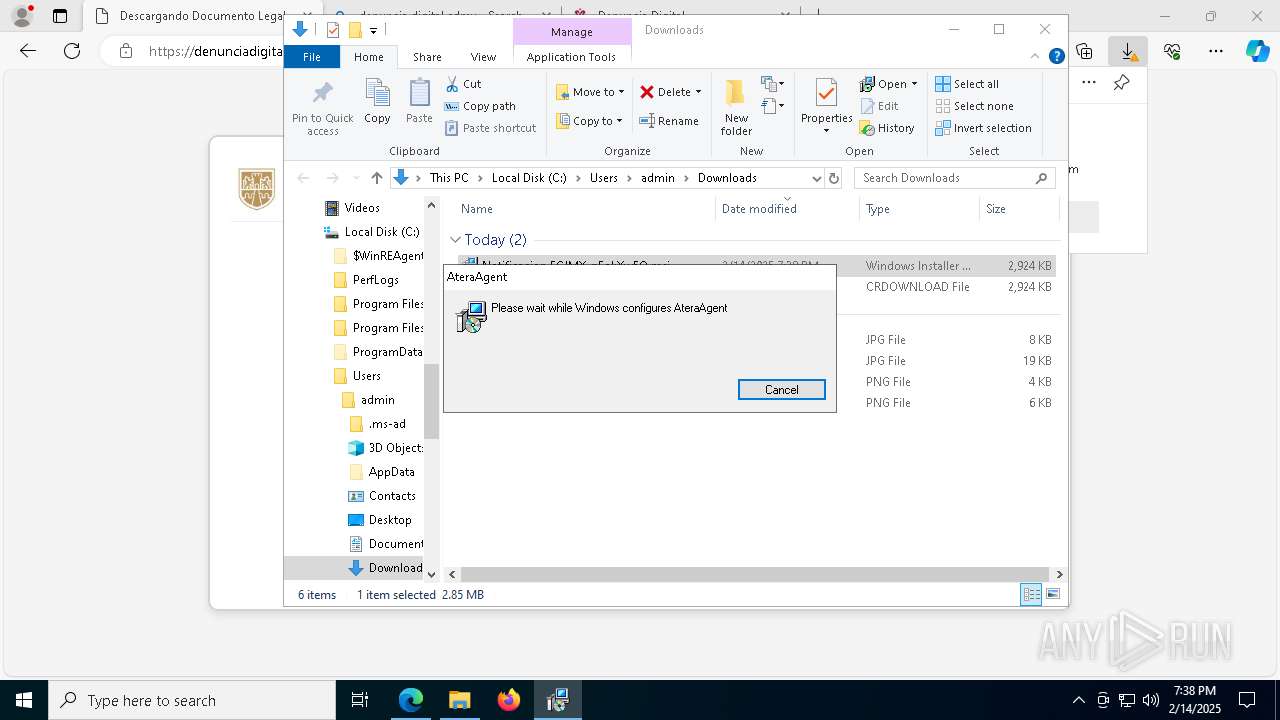
ATERAAGENT has been detected
- AteraAgent.exe (PID: 3796)
- AteraAgent.exe (PID: 904)
- AteraAgent.exe (PID: 7668)
Restarts service on failure
- sc.exe (PID: 7444)
- sc.exe (PID: 4912)
Starts SC.EXE for service management
- AteraAgent.exe (PID: 904)
- AteraAgent.exe (PID: 7668)
Reads the date of Windows installation
- AteraAgent.exe (PID: 904)
- AteraAgent.exe (PID: 7668)
The process executes Powershell scripts
- AgentPackageAgentInformation.exe (PID: 3888)
- cmd.exe (PID: 8476)
The process bypasses the loading of PowerShell profile settings
- AgentPackageAgentInformation.exe (PID: 3888)
Starts POWERSHELL.EXE for commands execution
- AgentPackageAgentInformation.exe (PID: 3888)
- cmd.exe (PID: 8476)
CSC.EXE is used to compile C# code
- csc.exe (PID: 7672)
The process executes VB scripts
- cmd.exe (PID: 8076)
Starts CMD.EXE for commands execution
- AgentPackageAgentInformation.exe (PID: 3888)
- msiexec.exe (PID: 2280)
- SetupUtil.exe (PID: 5540)
Gets the drive type (SCRIPT)
- cscript.exe (PID: 2160)
Gets a collection of all available drive names (SCRIPT)
- cscript.exe (PID: 2160)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 2160)
Accesses computer name via WMI (SCRIPT)
- cscript.exe (PID: 2160)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 2160)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- cscript.exe (PID: 2160)
Executes application which crashes
- cscript.exe (PID: 2160)
The process creates files with name similar to system file names
- WerFault.exe (PID: 7864)
- msiexec.exe (PID: 6280)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 6280)
INFO
Reads Environment values
- identity_helper.exe (PID: 8076)
- AteraAgent.exe (PID: 3796)
- AgentPackageAgentInformation.exe (PID: 6388)
- AgentPackageAgentInformation.exe (PID: 5028)
- AgentPackageAgentInformation.exe (PID: 2012)
- AgentPackageAgentInformation.exe (PID: 3888)
- AteraAgent.exe (PID: 904)
- AgentPackageSTRemote.exe (PID: 1604)
- AteraAgent.exe (PID: 7668)
- AgentPackageMonitoring.exe (PID: 7356)
Checks supported languages
- identity_helper.exe (PID: 8076)
- msiexec.exe (PID: 6280)
- msiexec.exe (PID: 848)
- msiexec.exe (PID: 372)
- AteraAgent.exe (PID: 3796)
- AteraAgent.exe (PID: 904)
- AgentPackageAgentInformation.exe (PID: 6388)
- AgentPackageAgentInformation.exe (PID: 5028)
- AgentPackageAgentInformation.exe (PID: 2012)
- AgentPackageAgentInformation.exe (PID: 3888)
- AteraAgent.exe (PID: 7668)
- AgentPackageSTRemote.exe (PID: 1604)
- AgentPackageMonitoring.exe (PID: 7356)
- csc.exe (PID: 7672)
- cvtres.exe (PID: 7132)
- SplashtopStreamer.exe (PID: 4864)
- PreVerCheck.exe (PID: 1828)
- msiexec.exe (PID: 2280)
- _is3EBE.exe (PID: 6908)
- _is3EBE.exe (PID: 3032)
- _is3EBE.exe (PID: 6908)
- _is3EBE.exe (PID: 7608)
- _is3EBE.exe (PID: 7252)
- _is3EBE.exe (PID: 6936)
- _is3EBE.exe (PID: 7608)
- _is3EBE.exe (PID: 6908)
- _is3EBE.exe (PID: 7608)
- _is48A2.exe (PID: 8232)
- _is48A2.exe (PID: 8252)
- _is48A2.exe (PID: 8300)
- _is48A2.exe (PID: 4764)
- _is48A2.exe (PID: 8296)
- _is48A2.exe (PID: 5456)
- _is48A2.exe (PID: 2148)
- _is48A2.exe (PID: 8440)
- _is665D.exe (PID: 5936)
- _is48A2.exe (PID: 5040)
- _is48A2.exe (PID: 3744)
- SetupUtil.exe (PID: 8328)
- _is3EBE.exe (PID: 6908)
The sample compiled with english language support
- msedge.exe (PID: 2144)
- rundll32.exe (PID: 5000)
- rundll32.exe (PID: 7672)
- rundll32.exe (PID: 4132)
- rundll32.exe (PID: 5200)
- AteraAgent.exe (PID: 904)
- SplashtopStreamer.exe (PID: 4864)
- PreVerCheck.exe (PID: 1828)
- msiexec.exe (PID: 6280)
- msiexec.exe (PID: 2280)
- AteraAgent.exe (PID: 7668)
Reads the computer name
- identity_helper.exe (PID: 8076)
- msiexec.exe (PID: 6280)
- msiexec.exe (PID: 848)
- AteraAgent.exe (PID: 3796)
- msiexec.exe (PID: 372)
- AteraAgent.exe (PID: 904)
- AgentPackageAgentInformation.exe (PID: 5028)
- AgentPackageAgentInformation.exe (PID: 6388)
- AgentPackageAgentInformation.exe (PID: 2012)
- AgentPackageAgentInformation.exe (PID: 3888)
- AgentPackageSTRemote.exe (PID: 1604)
- AteraAgent.exe (PID: 7668)
- AgentPackageMonitoring.exe (PID: 7356)
- SplashtopStreamer.exe (PID: 4864)
- msiexec.exe (PID: 2280)
- _is3EBE.exe (PID: 7252)
- _is3EBE.exe (PID: 6908)
- _is3EBE.exe (PID: 7608)
- _is3EBE.exe (PID: 3032)
- _is3EBE.exe (PID: 6908)
- _is3EBE.exe (PID: 6908)
- _is3EBE.exe (PID: 6936)
- _is3EBE.exe (PID: 7608)
- _is3EBE.exe (PID: 6908)
- _is3EBE.exe (PID: 7608)
- _is48A2.exe (PID: 8232)
- _is48A2.exe (PID: 8252)
- _is48A2.exe (PID: 8296)
- _is48A2.exe (PID: 8300)
- _is48A2.exe (PID: 4764)
- _is48A2.exe (PID: 5456)
- _is48A2.exe (PID: 2148)
- _is48A2.exe (PID: 3744)
- _is48A2.exe (PID: 8440)
- _is48A2.exe (PID: 5040)
- _is665D.exe (PID: 5936)
Executable content was dropped or overwritten
- msedge.exe (PID: 2144)
- msedge.exe (PID: 5892)
- msiexec.exe (PID: 6280)
- msedge.exe (PID: 6464)
- msiexec.exe (PID: 2280)
Application launched itself
- msedge.exe (PID: 5892)
Reads the software policy settings
- msiexec.exe (PID: 7236)
- explorer.exe (PID: 4488)
- msiexec.exe (PID: 6280)
- rundll32.exe (PID: 7672)
- AteraAgent.exe (PID: 3796)
- AteraAgent.exe (PID: 904)
- rundll32.exe (PID: 5200)
- AgentPackageAgentInformation.exe (PID: 6388)
- AgentPackageAgentInformation.exe (PID: 5028)
- AgentPackageSTRemote.exe (PID: 1604)
- AgentPackageMonitoring.exe (PID: 7356)
- cscript.exe (PID: 2160)
- msiexec.exe (PID: 2280)
- WerFault.exe (PID: 7864)
- AteraAgent.exe (PID: 7668)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4488)
- msiexec.exe (PID: 7236)
Creates files or folders in the user directory
- explorer.exe (PID: 4488)
Manages system restore points
- SrTasks.exe (PID: 6912)
Reads the machine GUID from the registry
- msiexec.exe (PID: 6280)
- AteraAgent.exe (PID: 3796)
- AteraAgent.exe (PID: 904)
- AgentPackageAgentInformation.exe (PID: 6388)
- AgentPackageAgentInformation.exe (PID: 5028)
- AgentPackageAgentInformation.exe (PID: 2012)
- AgentPackageAgentInformation.exe (PID: 3888)
- AgentPackageSTRemote.exe (PID: 1604)
- AteraAgent.exe (PID: 7668)
- AgentPackageMonitoring.exe (PID: 7356)
- csc.exe (PID: 7672)
- msiexec.exe (PID: 2280)
Create files in a temporary directory
- rundll32.exe (PID: 7672)
- rundll32.exe (PID: 5000)
- rundll32.exe (PID: 5200)
Disables trace logs
- rundll32.exe (PID: 7672)
- AteraAgent.exe (PID: 904)
- AgentPackageAgentInformation.exe (PID: 6388)
- AgentPackageAgentInformation.exe (PID: 5028)
- AteraAgent.exe (PID: 7668)
- rundll32.exe (PID: 5200)
- AgentPackageSTRemote.exe (PID: 1604)
- AgentPackageMonitoring.exe (PID: 7356)
Reads Microsoft Office registry keys
- explorer.exe (PID: 4488)
Checks proxy server information
- rundll32.exe (PID: 7672)
- explorer.exe (PID: 4488)
- rundll32.exe (PID: 5200)
Creates a software uninstall entry
- msiexec.exe (PID: 6280)
Creates files in the program directory
- AteraAgent.exe (PID: 904)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7304)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
337
Monitored processes
193
Malicious processes
7
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | C:\WINDOWS\TEMP\{CDDD0021-DD18-41F9-B634-44541C28CCFA}\_is665D.exe {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{DA9E5A7E-AE52-44C5-8C8C-4B65F0DAD87A} | C:\Windows\Temp\{CDDD0021-DD18-41F9-B634-44541C28CCFA}\_is665D.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Flexera Integrity Level: SYSTEM Description: InstallShield (R) 64-bit Setup Engine Exit code: 0 Version: 27.0.122 Modules
| |||||||||||||||
| 372 | C:\Windows\syswow64\MsiExec.exe -Embedding C4BFD8AC19C8C259B58B8CB92160ACB8 E Global\MSI0000 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 444 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5780 --field-trial-handle=2300,i,17026543929392605290,5350258612096688138,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 848 | C:\Windows\syswow64\MsiExec.exe -Embedding 0F15651666D1CEDA56E85BC542D4499A | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
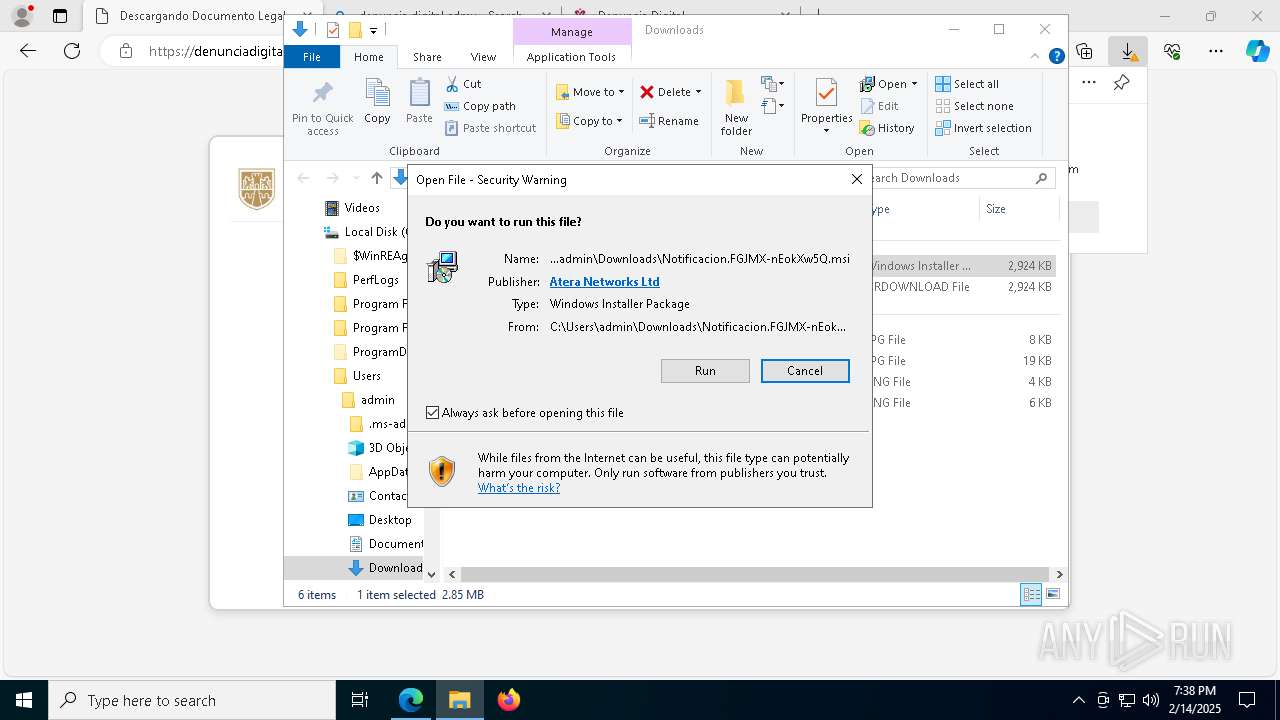
| 904 | "C:\Program Files (x86)\ATERA Networks\AteraAgent\AteraAgent.exe" | C:\Program Files (x86)\ATERA Networks\AteraAgent\AteraAgent.exe | services.exe | ||||||||||||
User: SYSTEM Company: ATERA Networks Ltd. Integrity Level: SYSTEM Description: AteraAgent Exit code: 0 Version: 1.8.7.2 Modules
| |||||||||||||||
| 936 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=8096 --field-trial-handle=2300,i,17026543929392605290,5350258612096688138,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1476 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | AgentPackageSTRemote.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1576 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1604 | "C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\AgentPackageSTRemote\AgentPackageSTRemote.exe" 1f7261bd-117e-4e51-a5db-cca597cc16d2 "797b4217-c2b6-4f36-ac29-956c4ba62eb6" agent-api.atera.com/Production 443 or8ixLi90Mf "install eyJSbW1Db2RlIjoiaFpDREZQaEs3NW1KIiwiUmVxdWVzdFBlcm1pc3Npb25PcHRpb24iOjMsIlJlcXVpcmVQYXNzd29yZE9wdGlvbiI6bnVsbCwiUGFzc3dvcmQiOm51bGx9" 001Q300000QJlPOIA1 | C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\AgentPackageSTRemote\AgentPackageSTRemote.exe | AteraAgent.exe | ||||||||||||
User: SYSTEM Company: Atera Networks Integrity Level: SYSTEM Description: AgentPackageSTRemote Version: 24.4.0.0 Modules
| |||||||||||||||
| 1828 | "C:\Windows\Temp\unpack\PreVerCheck.exe" /s /i sec_opt=0,confirm_d=0,hidewindow=1 | C:\Windows\Temp\unpack\PreVerCheck.exe | SplashtopStreamer.exe | ||||||||||||
User: SYSTEM Company: Splashtop Inc. Integrity Level: SYSTEM Description: Splashtop® Streamer Version: 3.72.4.150 Modules
| |||||||||||||||
Total events
76 343
Read events
75 233
Write events
1 081
Delete events
29
Modification events
| (PID) Process: | (5892) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5892) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5892) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5892) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5892) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: E542CD8EB58C2F00 | |||
| (PID) Process: | (4488) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000602A8 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456A48A294F7A40804AB924005FF030B61F | |||
| (PID) Process: | (4488) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000040294 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456A48A294F7A40804AB924005FF030B61F | |||
| (PID) Process: | (5892) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 3AE2D98EB58C2F00 | |||
| (PID) Process: | (5892) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\393896 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {D3304D1B-56CC-4242-BA8F-8FAAE55AA9C3} | |||
| (PID) Process: | (5892) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\393896 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {EB7DA137-B8B2-4366-8DAA-06A45715B15B} | |||
Executable files
771
Suspicious files
1 237
Text files
323
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5892 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF1350d3.TMP | — | |
MD5:— | SHA256:— | |||
| 5892 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF1350d3.TMP | — | |
MD5:— | SHA256:— | |||
| 5892 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF1350d3.TMP | — | |
MD5:— | SHA256:— | |||
| 5892 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5892 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5892 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF1350d3.TMP | — | |
MD5:— | SHA256:— | |||
| 5892 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5892 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5892 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF1350e2.TMP | — | |
MD5:— | SHA256:— | |||
| 5892 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
71
TCP/UDP connections
249
DNS requests
298
Threats
57
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7164 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4520 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7524 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1739801494&P2=404&P3=2&P4=O4bdXCqXB2pOyIi4qn899WQDNTkiy7QRqWFoye4vR9w5iP6Bf7inE68rmCsPmU%2fni2S5U6xUwnpHxTp1ZewH4g%3d%3d | unknown | — | — | whitelisted |
4520 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7524 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1739801494&P2=404&P3=2&P4=O4bdXCqXB2pOyIi4qn899WQDNTkiy7QRqWFoye4vR9w5iP6Bf7inE68rmCsPmU%2fni2S5U6xUwnpHxTp1ZewH4g%3d%3d | unknown | — | — | whitelisted |
7524 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/5cbc98ff-b69b-4fda-ad94-17ec2f9cf48b?P1=1739805096&P2=404&P3=2&P4=F8U3zEZpwxtfy3UzZDL8Sb%2bn7bvT3iJWuvMe9YFMpEt3emkxM1OwuWGBxIi6EyKNhQdB0EJOwQjW3nCvmXbdRA%3d%3d | unknown | — | — | whitelisted |
7524 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/5cbc98ff-b69b-4fda-ad94-17ec2f9cf48b?P1=1739805096&P2=404&P3=2&P4=F8U3zEZpwxtfy3UzZDL8Sb%2bn7bvT3iJWuvMe9YFMpEt3emkxM1OwuWGBxIi6EyKNhQdB0EJOwQjW3nCvmXbdRA%3d%3d | unknown | — | — | whitelisted |
7524 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/5cbc98ff-b69b-4fda-ad94-17ec2f9cf48b?P1=1739805096&P2=404&P3=2&P4=F8U3zEZpwxtfy3UzZDL8Sb%2bn7bvT3iJWuvMe9YFMpEt3emkxM1OwuWGBxIi6EyKNhQdB0EJOwQjW3nCvmXbdRA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 2.16.204.141:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1480 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6464 | msedge.exe | 52.123.243.95:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | DE | whitelisted |
5892 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6464 | msedge.exe | 13.107.246.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6464 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
denunciadigital-gobmx.com |
| unknown |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
www.recaptcha.net |
| whitelisted |
www.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6464 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
6464 | msedge.exe | Misc activity | SUSPICIOUS [ANY.RUN] Tracking Service (.popin .cc) |
6464 | msedge.exe | Misc activity | SUSPICIOUS [ANY.RUN] Tracking Service (.popin .cc) |
6464 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
7672 | rundll32.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
904 | AteraAgent.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
5200 | rundll32.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
904 | AteraAgent.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
904 | AteraAgent.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
6388 | AgentPackageAgentInformation.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
Process | Message |
|---|---|
AgentPackageMonitoring.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\AgentPackageMonitoring\x64\SQLite.Interop.dll"...
|
SplashtopStreamer.exe | [4864]2025-02-14 19:39:33 [CUnPack::FindHeader] Name:C:\WINDOWS\TEMP\SplashtopStreamer.exe (Last=0) |
SplashtopStreamer.exe | [4864]2025-02-14 19:39:33 [CUnPack::UnPackFiles] FreeSpace:231854350336 FileSize:53075456 (Last=0) |
SplashtopStreamer.exe | [4864]2025-02-14 19:39:33 [CUnPack::UnPackFiles] (1/5)UnPack file name:C:\WINDOWS\TEMP\unpack\setup.msi (53075456) (Last=0) |
SplashtopStreamer.exe | [4864]2025-02-14 19:39:33 [CUnPack::FindHeader] Header offset:434176 (Last=183) |
SplashtopStreamer.exe | [4864]2025-02-14 19:39:33 [CUtility::OSInfo] OS 10.0(19045) x64:1 (Last=0) |
SplashtopStreamer.exe | [4864]2025-02-14 19:39:33 [CUnPack::FindHeader] Sign Size:10240 (Last=0) |
SplashtopStreamer.exe | [4864]2025-02-14 19:39:34 [CUnPack::UnPackFiles] UnPack count:1 len:53075456 File:(null) (Last=0) |
SplashtopStreamer.exe | [4864]2025-02-14 19:39:34 [CUnPack::UnPackFiles] FreeSpace:231801257984 FileSize:15 (Last=183) |
SplashtopStreamer.exe | [4864]2025-02-14 19:39:34 [CUnPack::UnPackFiles] (2/5)UnPack file name:C:\WINDOWS\TEMP\unpack\run.bat (15) (Last=122) |