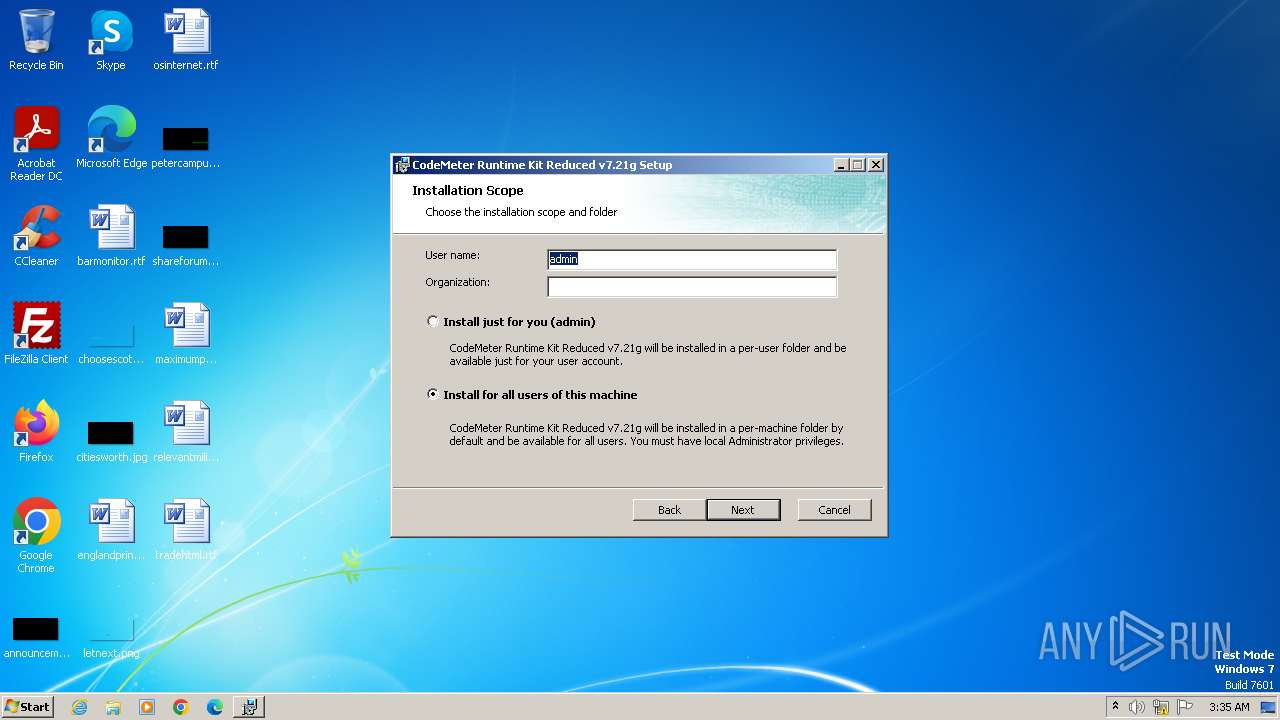
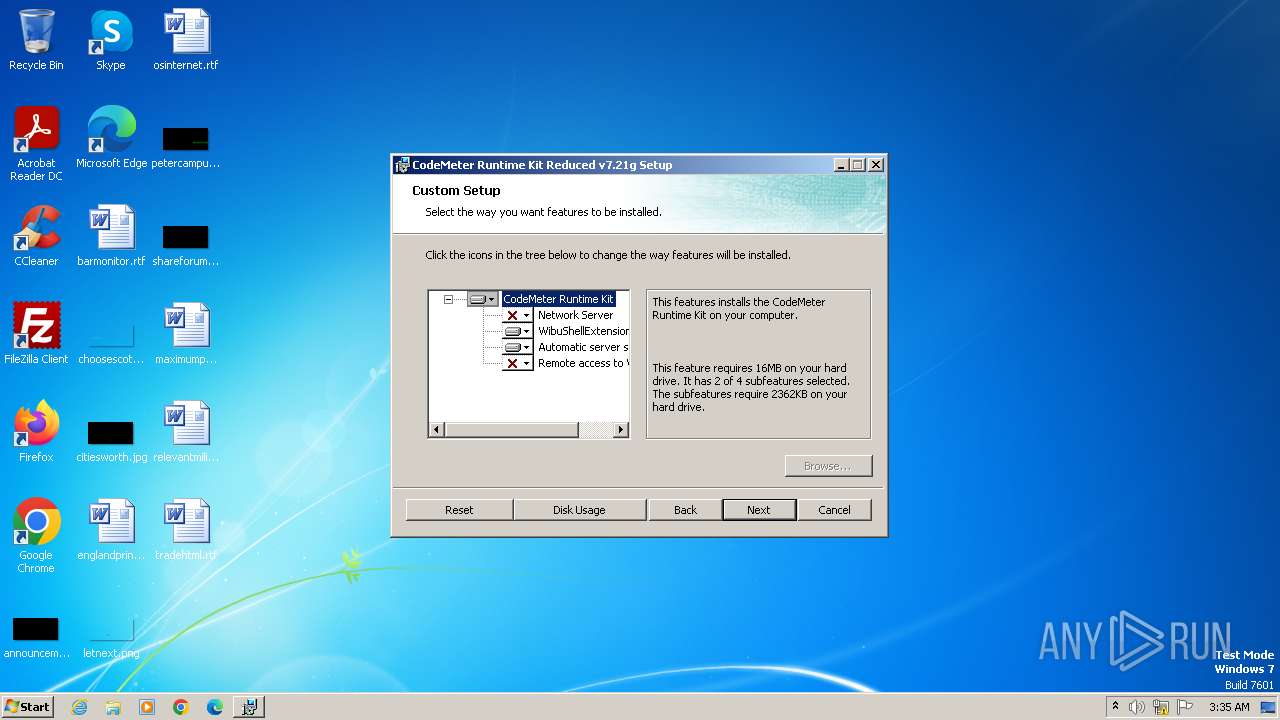
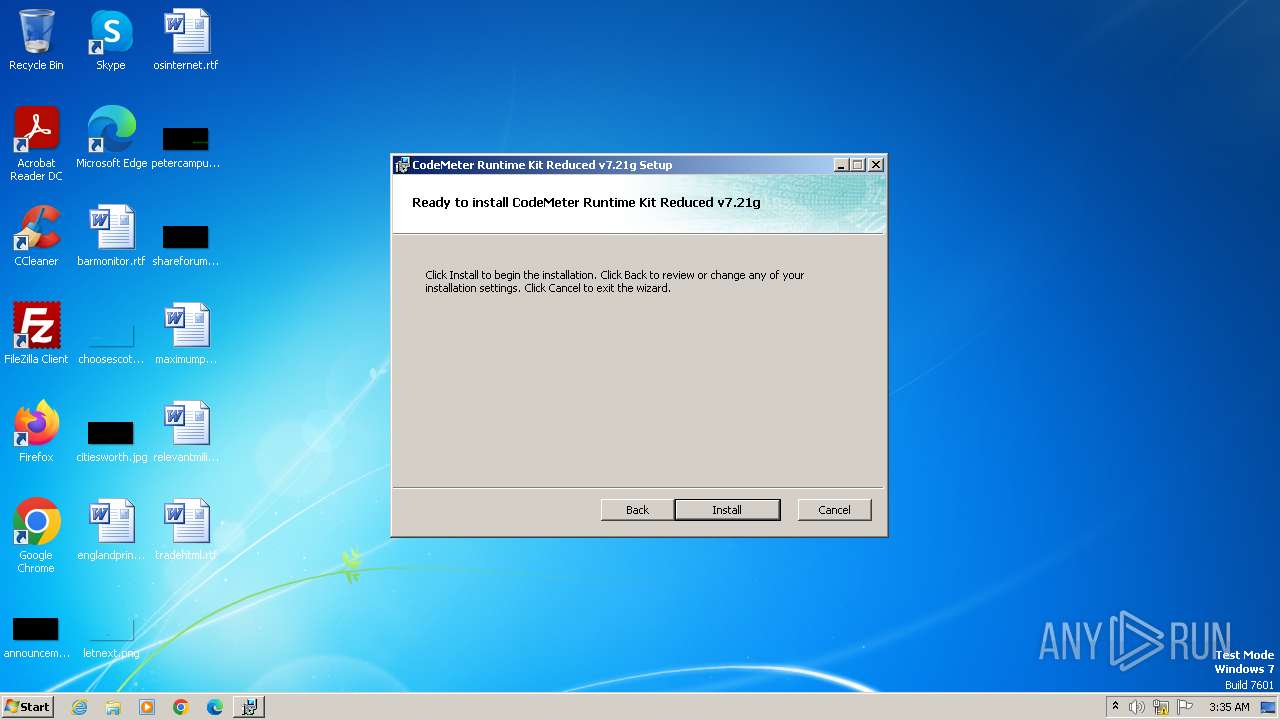
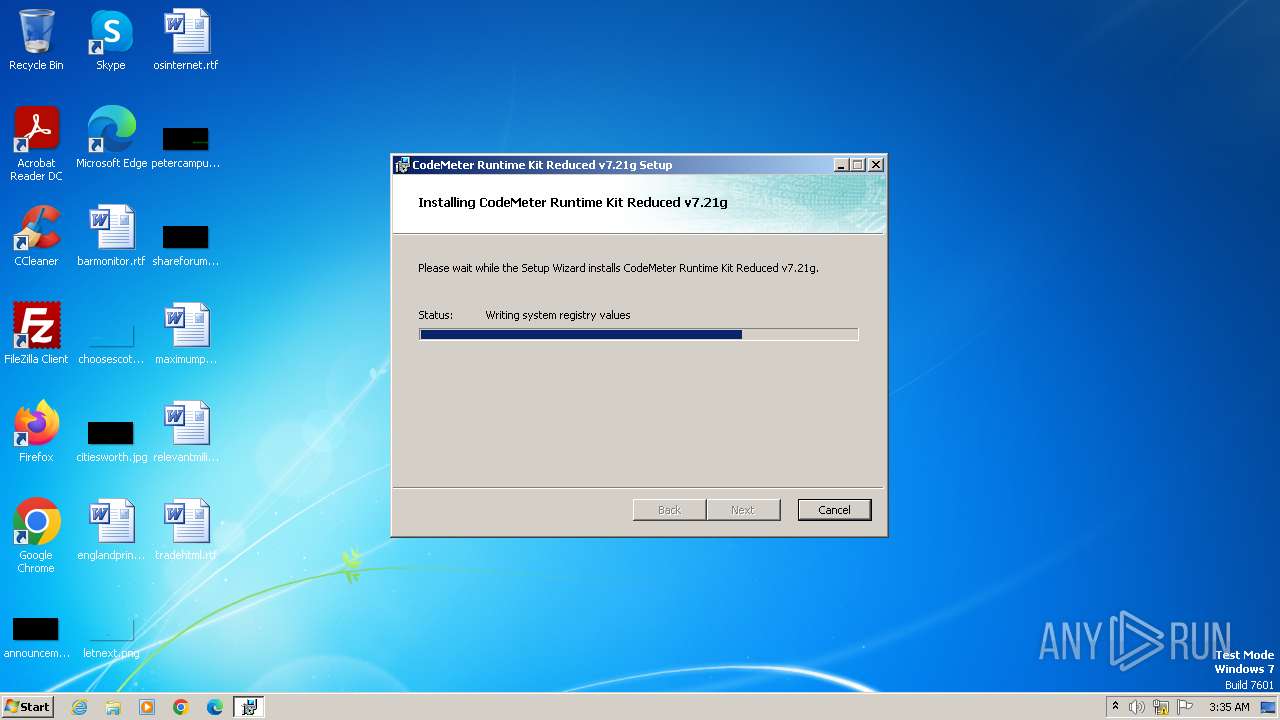
| File name: | CodeMeterRuntimeReduced.exe |
| Full analysis: | https://app.any.run/tasks/cdd824b3-97d1-4a43-8736-940ff735ffa9 |
| Verdict: | Malicious activity |
| Analysis date: | December 01, 2023, 03:34:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | F0C9D4DB2514D6DC655AC1F6776A6A45 |
| SHA1: | AF2C1794AA45150A53A66451F3285DC782E031C9 |
| SHA256: | 2FB295B1DAA9E7B961028E24393920ED52F9DC8A055E00D04757DBCDBAA452A7 |
| SSDEEP: | 98304:X0fQngk7A+RKUdWANUvHPBsVDE8xZDjFcK0zfOxSBbRU8SSHeqS+S+w3qVhRm7i8:lS+LucPMO1zxdj5AhO9 |
MALICIOUS
Drops the executable file immediately after the start
- CodeMeterRuntimeReduced.exe (PID: 3008)
- msiexec.exe (PID: 3100)
Creates a writable file in the system directory
- msiexec.exe (PID: 3100)
Starts NET.EXE for service management
- net.exe (PID: 3116)
- msiexec.exe (PID: 3852)
- net.exe (PID: 3496)
SUSPICIOUS
Adds/modifies Windows certificates
- msiexec.exe (PID: 2308)
Executes as Windows Service
- VSSVC.exe (PID: 3868)
- CodeMeter.exe (PID: 3688)
Checks Windows Trust Settings
- msiexec.exe (PID: 3100)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- msiexec.exe (PID: 3852)
INFO
Create files in a temporary directory
- msiexec.exe (PID: 2308)
- CodeMeterRuntimeReduced.exe (PID: 3008)
- msiexec.exe (PID: 3100)
Checks supported languages
- CodeMeterRuntimeReduced.exe (PID: 3008)
- msiexec.exe (PID: 3100)
- MSI7CC9.tmp (PID: 3296)
- msiexec.exe (PID: 3436)
- msiexec.exe (PID: 3852)
- msiexec.exe (PID: 4052)
- CodeMeter.exe (PID: 3688)
Reads the computer name
- msiexec.exe (PID: 3100)
- msiexec.exe (PID: 3436)
- msiexec.exe (PID: 3852)
- CodeMeter.exe (PID: 3688)
- msiexec.exe (PID: 4052)
Reads the machine GUID from the registry
- msiexec.exe (PID: 3100)
- msiexec.exe (PID: 3436)
- msiexec.exe (PID: 3852)
- CodeMeter.exe (PID: 3688)
- msiexec.exe (PID: 4052)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 2308)
Starts application with an unusual extension
- msiexec.exe (PID: 3100)
Application launched itself
- msiexec.exe (PID: 3100)
Reads Environment values
- CodeMeter.exe (PID: 3688)
Creates files in the program directory
- CodeMeter.exe (PID: 3688)
Reads product name
- CodeMeter.exe (PID: 3688)
Drops the executable file immediately after the start
- msiexec.exe (PID: 2308)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (34.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (25.2) |
| .exe | | | Win64 Executable (generic) (22.3) |
| .scr | | | Windows screen saver (10.6) |
| .exe | | | Win32 Executable (generic) (3.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2014:01:06 20:42:36+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 860160 |
| InitializedDataSize: | 13266944 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x8ee33 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.21.4624.507 |
| ProductVersionNumber: | 7.21.4624.507 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | CodeMeter Installer bootstrapper |
| CompanyName: | WIBU SYSTEMS AG |
| FileDescription: | CodeMeter |
| FileVersion: | 7.21.4624.507 |
| InternalName: | - |
| LegalCopyright: | (c) 2023 WIBU SYSTEMS AG |
| LegalTrademarks: | All Rights Reserved |
| OLESelfRegister: | - |
| OriginalFileName: | - |
| PrivateBuild: | - |
| ProductName: | CodeMeter Installer |
| ProductVersion: | 7.21.4624.507 |
| SpecialBuild: | - |
Total processes
64
Monitored processes
19
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 844 | "C:\Users\admin\AppData\Local\Temp\CodeMeterRuntimeReduced.exe" | C:\Users\admin\AppData\Local\Temp\CodeMeterRuntimeReduced.exe | — | explorer.exe | |||||||||||
User: admin Company: WIBU SYSTEMS AG Integrity Level: MEDIUM Description: CodeMeter Exit code: 3221226540 Version: 7.21.4624.507 Modules
| |||||||||||||||
| 2100 | "netsh" advfirewall firewall delete rule name="CodeMeter Runtime Server" | C:\Windows\System32\netsh.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2308 | msiexec /i "C:\Users\admin\AppData\Local\Temp\CodeMeter_v7.21.4624.507\CodeMeterRuntime32Reduced.msi" /l*v "C:\Users\admin\AppData\Local\Temp\CodeMeter_v7.21.4624.507_{6D132BDD-D54C-4483-98E9-00D391C0B862}_CodeMeterRuntime32Reduced.msi.log" ProductLanguage=1033 | C:\Windows\System32\msiexec.exe | — | CodeMeterRuntimeReduced.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3008 | "C:\Users\admin\AppData\Local\Temp\CodeMeterRuntimeReduced.exe" | C:\Users\admin\AppData\Local\Temp\CodeMeterRuntimeReduced.exe | explorer.exe | ||||||||||||
User: admin Company: WIBU SYSTEMS AG Integrity Level: HIGH Description: CodeMeter Exit code: 0 Version: 7.21.4624.507 Modules
| |||||||||||||||
| 3100 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3116 | "C:\Windows\system32\net.exe" stop CodeMeter.exe /Y | C:\Windows\System32\net.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3296 | "C:\Windows\Installer\MSI7CC9.tmp" /t | C:\Windows\Installer\MSI7CC9.tmp | — | msiexec.exe | |||||||||||
User: admin Company: WIBU-SYSTEMS AG Integrity Level: HIGH Description: CleanUp Exit code: 0 Version: Version 7.21g of 2023-Aug-28(Build 4624) Modules
| |||||||||||||||
| 3340 | "netsh" advfirewall firewall delete rule name="CodeMeterFWEx1" | C:\Windows\System32\netsh.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3424 | C:\Windows\system32\net1 start CodeMeter.exe /Y | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3436 | C:\Windows\system32\MsiExec.exe -Embedding 49AD99205CAAC78E38D0178986FCC42F | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
36 394
Read events
35 780
Write events
547
Delete events
67
Modification events
| (PID) Process: | (2308) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2308) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\3679CA35668772304D30A5FB873B0FA77BB70D54 |
| Operation: | write | Name: | Blob |
Value: 090000000100000034000000303206082B0601050507030206082B0601050507030306082B0601050507030406082B0601050507030106082B06010505070308190000000100000010000000AD6D6FF31B24013151F279E26A8C33240B000000010000006000000056006500720069005300690067006E00200055006E006900760065007200730061006C00200052006F006F0074002000430065007200740069006600690063006100740069006F006E00200041007500740068006F00720069007400790000006200000001000000200000002399561127A57125DE8CEFEA610DDF2FA078B5C8067F4E828290BFB860E84B3C140000000100000014000000B677FA6948479F5312D5C2EA07327607D19707191D0000000100000010000000439B4D52906DF7A01771D729528723B37F000000010000000C000000300A06082B060105050703017E00000001000000080000000040D0D1B0FFD4010300000001000000140000003679CA35668772304D30A5FB873B0FA77BB70D540F000000010000002000000017FE16F394EC70A5BB0C6784CAB40B1E61025AE9D50ECAA0531D6B4D997BBC5953000000010000004200000030403021060B6086480186F8450107170630123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C02000000001000000BD040000308204B9308203A1A0030201020210401AC46421B31321030EBBE4121AC51D300D06092A864886F70D01010B05003081BD310B300906035504061302555331173015060355040A130E566572695369676E2C20496E632E311F301D060355040B1316566572695369676E205472757374204E6574776F726B313A3038060355040B1331286329203230303820566572695369676E2C20496E632E202D20466F7220617574686F72697A656420757365206F6E6C79313830360603550403132F566572695369676E20556E6976657273616C20526F6F742043657274696669636174696F6E20417574686F72697479301E170D3038303430323030303030305A170D3337313230313233353935395A3081BD310B300906035504061302555331173015060355040A130E566572695369676E2C20496E632E311F301D060355040B1316566572695369676E205472757374204E6574776F726B313A3038060355040B1331286329203230303820566572695369676E2C20496E632E202D20466F7220617574686F72697A656420757365206F6E6C79313830360603550403132F566572695369676E20556E6976657273616C20526F6F742043657274696669636174696F6E20417574686F7269747930820122300D06092A864886F70D01010105000382010F003082010A0282010100C761375EB10134DB62D7159BFF585A8C2323D6608E91D79098837AE65819388CC5F6E56485B4A271FBEDBDB9DACD4D00B4C82D73A5C76971951F393CB244079CE80EFA4D4AC421DF29618F32226182C5871F6E8C7C5F16205144D1704F57EAE31CE3CC79EE58D80EC2B34593C02CE79A172B7B00377A413378E133E2F3101A7F872CBEF6F5F742E2E5BF8762895F004BDFC5DDE4754432413A1E716E69CB0B754608D1CAD22B95D0CFFBB9406B648C574DFC13117984ED5E54F6349F0801F3102506174ADAF11D7A666B986066A4D9EFD22E82F1F0EF09EA44C9156AE2036E33D3AC9F5500C7F6086A94B95FDCE033F18460F95B2711B4FC16F2BB566A80258D0203010001A381B23081AF300F0603551D130101FF040530030101FF300E0603551D0F0101FF040403020106306D06082B0601050507010C0461305FA15DA05B3059305730551609696D6167652F6769663021301F300706052B0E03021A04148FE5D31A86AC8D8E6BC3CF806AD448182C7B192E30251623687474703A2F2F6C6F676F2E766572697369676E2E636F6D2F76736C6F676F2E676966301D0603551D0E04160414B677FA6948479F5312D5C2EA07327607D1970719300D06092A864886F70D01010B050003820101004AF8F8B003E62C677BE4947763CC6E4CF97D0E0DDCC8B935B9704F63FA24FA6C838C479D3B63F39AF976329591B177BCAC9ABEB1E43121C68195565A0EB1C2D4B1A659ACF163CBB84C1D59904AEF9016281F5AAE10FB8150380C6CCCF13DC3F563E3B3E321C92439E9FD156646F41B11D04D73A37D46F93DEDA85F62D4F13FF8E074572B189D81B4C428DA9497A570EBAC1DBE0711F0D5DBDDE58CF0D532B083E657E28FBFBEA1AABF3D1DB5D438EAD7B05C3A4F6A3F8FC0666C63AAE9D9A416F481D195140E7DCD9534D9D28F7073817B9C7EBD9861D845879890C5EB8630C635BFF0FFC35588834BEF05920671F2B89893B7ECCD8261F138E64F97982A5A8D | |||
| (PID) Process: | (2308) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\3679CA35668772304D30A5FB873B0FA77BB70D54 |
| Operation: | write | Name: | Blob |
Value: 0400000001000000100000008EADB501AA4D81E48C1DD1E11400951953000000010000004200000030403021060B6086480186F8450107170630123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C00F000000010000002000000017FE16F394EC70A5BB0C6784CAB40B1E61025AE9D50ECAA0531D6B4D997BBC590300000001000000140000003679CA35668772304D30A5FB873B0FA77BB70D547E00000001000000080000000040D0D1B0FFD4017F000000010000000C000000300A06082B060105050703011D0000000100000010000000439B4D52906DF7A01771D729528723B3140000000100000014000000B677FA6948479F5312D5C2EA07327607D19707196200000001000000200000002399561127A57125DE8CEFEA610DDF2FA078B5C8067F4E828290BFB860E84B3C0B000000010000006000000056006500720069005300690067006E00200055006E006900760065007200730061006C00200052006F006F0074002000430065007200740069006600690063006100740069006F006E00200041007500740068006F0072006900740079000000190000000100000010000000AD6D6FF31B24013151F279E26A8C3324090000000100000034000000303206082B0601050507030206082B0601050507030306082B0601050507030406082B0601050507030106082B060105050703082000000001000000BD040000308204B9308203A1A0030201020210401AC46421B31321030EBBE4121AC51D300D06092A864886F70D01010B05003081BD310B300906035504061302555331173015060355040A130E566572695369676E2C20496E632E311F301D060355040B1316566572695369676E205472757374204E6574776F726B313A3038060355040B1331286329203230303820566572695369676E2C20496E632E202D20466F7220617574686F72697A656420757365206F6E6C79313830360603550403132F566572695369676E20556E6976657273616C20526F6F742043657274696669636174696F6E20417574686F72697479301E170D3038303430323030303030305A170D3337313230313233353935395A3081BD310B300906035504061302555331173015060355040A130E566572695369676E2C20496E632E311F301D060355040B1316566572695369676E205472757374204E6574776F726B313A3038060355040B1331286329203230303820566572695369676E2C20496E632E202D20466F7220617574686F72697A656420757365206F6E6C79313830360603550403132F566572695369676E20556E6976657273616C20526F6F742043657274696669636174696F6E20417574686F7269747930820122300D06092A864886F70D01010105000382010F003082010A0282010100C761375EB10134DB62D7159BFF585A8C2323D6608E91D79098837AE65819388CC5F6E56485B4A271FBEDBDB9DACD4D00B4C82D73A5C76971951F393CB244079CE80EFA4D4AC421DF29618F32226182C5871F6E8C7C5F16205144D1704F57EAE31CE3CC79EE58D80EC2B34593C02CE79A172B7B00377A413378E133E2F3101A7F872CBEF6F5F742E2E5BF8762895F004BDFC5DDE4754432413A1E716E69CB0B754608D1CAD22B95D0CFFBB9406B648C574DFC13117984ED5E54F6349F0801F3102506174ADAF11D7A666B986066A4D9EFD22E82F1F0EF09EA44C9156AE2036E33D3AC9F5500C7F6086A94B95FDCE033F18460F95B2711B4FC16F2BB566A80258D0203010001A381B23081AF300F0603551D130101FF040530030101FF300E0603551D0F0101FF040403020106306D06082B0601050507010C0461305FA15DA05B3059305730551609696D6167652F6769663021301F300706052B0E03021A04148FE5D31A86AC8D8E6BC3CF806AD448182C7B192E30251623687474703A2F2F6C6F676F2E766572697369676E2E636F6D2F76736C6F676F2E676966301D0603551D0E04160414B677FA6948479F5312D5C2EA07327607D1970719300D06092A864886F70D01010B050003820101004AF8F8B003E62C677BE4947763CC6E4CF97D0E0DDCC8B935B9704F63FA24FA6C838C479D3B63F39AF976329591B177BCAC9ABEB1E43121C68195565A0EB1C2D4B1A659ACF163CBB84C1D59904AEF9016281F5AAE10FB8150380C6CCCF13DC3F563E3B3E321C92439E9FD156646F41B11D04D73A37D46F93DEDA85F62D4F13FF8E074572B189D81B4C428DA9497A570EBAC1DBE0711F0D5DBDDE58CF0D532B083E657E28FBFBEA1AABF3D1DB5D438EAD7B05C3A4F6A3F8FC0666C63AAE9D9A416F481D195140E7DCD9534D9D28F7073817B9C7EBD9861D845879890C5EB8630C635BFF0FFC35588834BEF05920671F2B89893B7ECCD8261F138E64F97982A5A8D | |||
| (PID) Process: | (3100) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000F2B487BA16B0D901C80700002C0A0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3100) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000F2B487BA16B0D901C80700002C0A0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3100) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 72 | |||
| (PID) Process: | (3100) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 40000000000000008C62D6BA16B0D901C80700002C0A0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3100) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Leave) |
Value: 400000000000000064514ABC16B0D901C80700002C0A0000D3070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3100) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppAddInterestingComponents (Enter) |
Value: 400000000000000064514ABC16B0D901C80700002C0A0000D4070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3100) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppAddInterestingComponents (Leave) |
Value: 400000000000000034645DBC16B0D901C80700002C0A0000D4070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
276
Suspicious files
11
Text files
212
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3008 | CodeMeterRuntimeReduced.exe | C:\Users\admin\AppData\Local\Temp\CodeMeter_v7.21.4624.507\CodeMeterRuntime32Reduced.msi | executable | |
MD5:46B6810ADE2AF8E8376D3E432A691785 | SHA256:30CD92B1A545BAC3D43D6A85211774DB86CD3698B3AD14AF4FA03492575232BB | |||
| 3008 | CodeMeterRuntimeReduced.exe | C:\Users\admin\AppData\Local\Temp\CodeMeter_v7.21.4624.507\Global Assembly Cache Folder\WibuCmNET.resources\7.21.4624.507_nl_01D86E1EB0C69C23\WibuCmNET.resources.dll | executable | |
MD5:826A91E7CDA736F6B36A8FE0F00DB574 | SHA256:7FEE8AF2FFC4D9298033A028BA3A9A24C8C507C741FF41C5B1D218438A5B7FE3 | |||
| 3008 | CodeMeterRuntimeReduced.exe | C:\Users\admin\AppData\Local\Temp\CodeMeter_v7.21.4624.507\Global Assembly Cache Folder\WibuCmNET.resources\7.21.4624.507_zh-Hans_01D86E1EB0C69C23\WibuCmNET.resources.dll | executable | |
MD5:7F233029DCAAA4B789C556A84563A540 | SHA256:092A0C3254B1C5C92C2C5E64741166F665C454FAD560F2A474996BBC6490CC57 | |||
| 3008 | CodeMeterRuntimeReduced.exe | C:\Users\admin\AppData\Local\Temp\CodeMeter_v7.21.4624.507\Global Assembly Cache Folder\WibuCmNET.resources\7.21.4624.507_ru_01D86E1EB0C69C23\WibuCmNET.resources.dll | executable | |
MD5:D9DC9C4A1067EBFC760C661CC47DD0C2 | SHA256:475CEBE79BD9CE328A3D9F988D17DF60F279A5EEE4CC09ACFD9F0CA95BB0D087 | |||
| 3008 | CodeMeterRuntimeReduced.exe | C:\Users\admin\AppData\Local\Temp\DVE00C.tmp | image | |
MD5:FD173D37EEC670297E7F6F30C3F31D81 | SHA256:50EEE916A9C37CBAB2D8281B49107080783DE073F13DDB808012B3CE2D34C0E6 | |||
| 3008 | CodeMeterRuntimeReduced.exe | C:\Users\admin\AppData\Local\Temp\CodeMeter_v7.21.4624.507\Global Assembly Cache Folder\WibuCmNET.resources\7.21.4624.507_fr_01D86E1EB0C69C23\WibuCmNET.resources.dll | executable | |
MD5:92780FA61FC4C43CFAE272C08338FE6C | SHA256:59F2DFD561B9B94A55B75DBD0DA9A8E2F773856F76A02E8306B1E71AAFEF4642 | |||
| 3008 | CodeMeterRuntimeReduced.exe | C:\Users\admin\AppData\Local\Temp\CodeMeter_v7.21.4624.507\Global Assembly Cache Folder\WibuCmNET.resources\6.40.228.501_fr_01D86E1EB0C69C23\WibuCmNET.resources.dll | executable | |
MD5:2F2CF54A5E5961CD187FBD08B88F23F3 | SHA256:E30F7A591939A26921B02F4BCA34E303C2F48E11E43BC7CE91C290DDB75FC2DA | |||
| 3008 | CodeMeterRuntimeReduced.exe | C:\Users\admin\AppData\Local\Temp\CodeMeter_v7.21.4624.507\Global Assembly Cache Folder\WibuCmNET.resources\7.21.4624.507_it_01D86E1EB0C69C23\WibuCmNET.resources.dll | executable | |
MD5:E91F5D9CB1CAA1E6C40320136CC069ED | SHA256:4219665BE0DBF258B6C5A3B3AEFF97CE3F1B111262004C27C8D35993693094A2 | |||
| 3008 | CodeMeterRuntimeReduced.exe | C:\Users\admin\AppData\Local\Temp\CodeMeter_v7.21.4624.507\Global Assembly Cache Folder\WibuCmNET.resources\7.21.4624.507_ja_01D86E1EB0C69C23\WibuCmNET.resources.dll | executable | |
MD5:7D765DD23B701030BBEB017EA9AC0CC7 | SHA256:9F0E233A0EF18470A601F012EB27E0443605048A98F51EB6608D62F4335C8ACC | |||
| 3008 | CodeMeterRuntimeReduced.exe | C:\Users\admin\AppData\Local\Temp\CodeMeter_v7.21.4624.507\Global Assembly Cache Folder\WibuCmNET.resources\6.40.228.501_zh-CHS_01D86E1EB0C69C23\WibuCmNET.resources.dll | executable | |
MD5:8B55394EF97D3244811FD8C31CA5D83C | SHA256:EA7EA6C9425A2E909B33D5936998E90363B4E6CCD3576A004AFDF53CEADAA4BC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |