| URL: | https://www.drivermax.com/ |
| Full analysis: | https://app.any.run/tasks/0386d6c2-1b75-497f-b30c-8d588ee8abd9 |
| Verdict: | Malicious activity |
| Analysis date: | February 14, 2024, 16:04:51 |
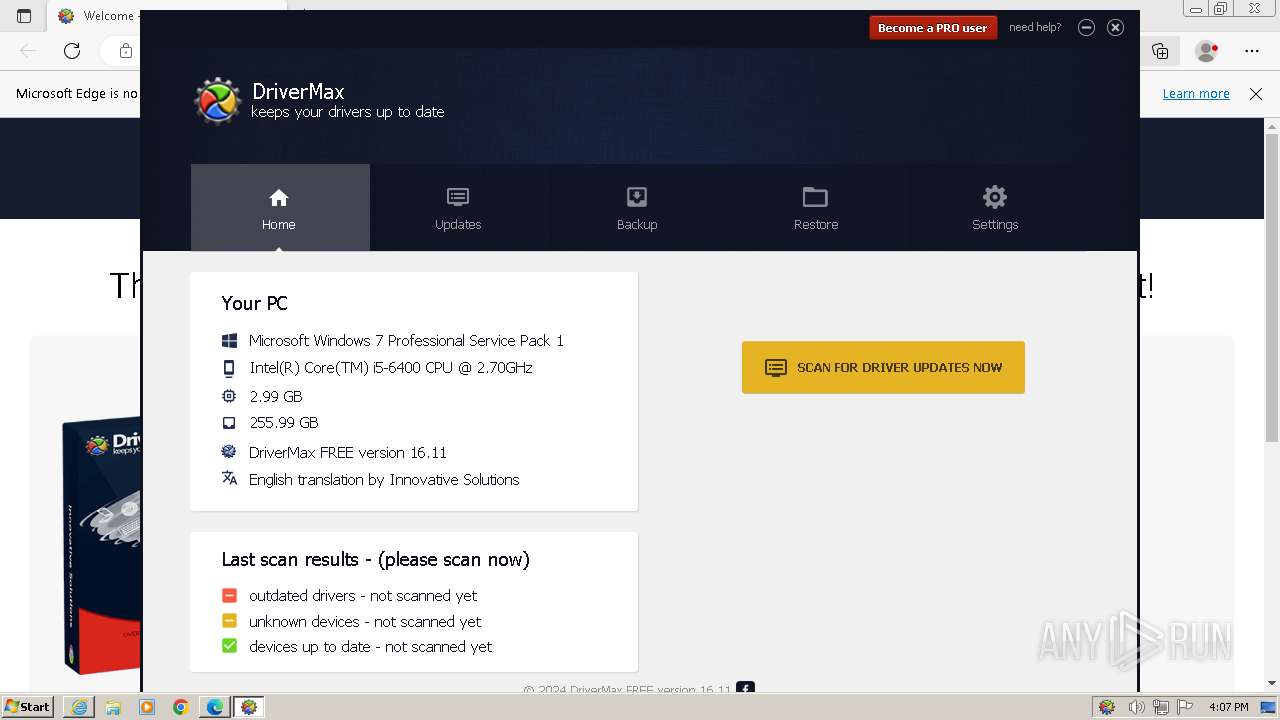
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 724DD1CAEA1A56A80512B96AF3B79D2C |
| SHA1: | 04444109B32B7CA7E7A71DFB9E0AE4924EB000B2 |
| SHA256: | 2F681D492A5A9B9C5A31AAA02EFD68B43C6D2084E1EB3B93D6471DDE7A203EE4 |
| SSDEEP: | 3:N8DSLaWWK3:2OLn3 |
MALICIOUS
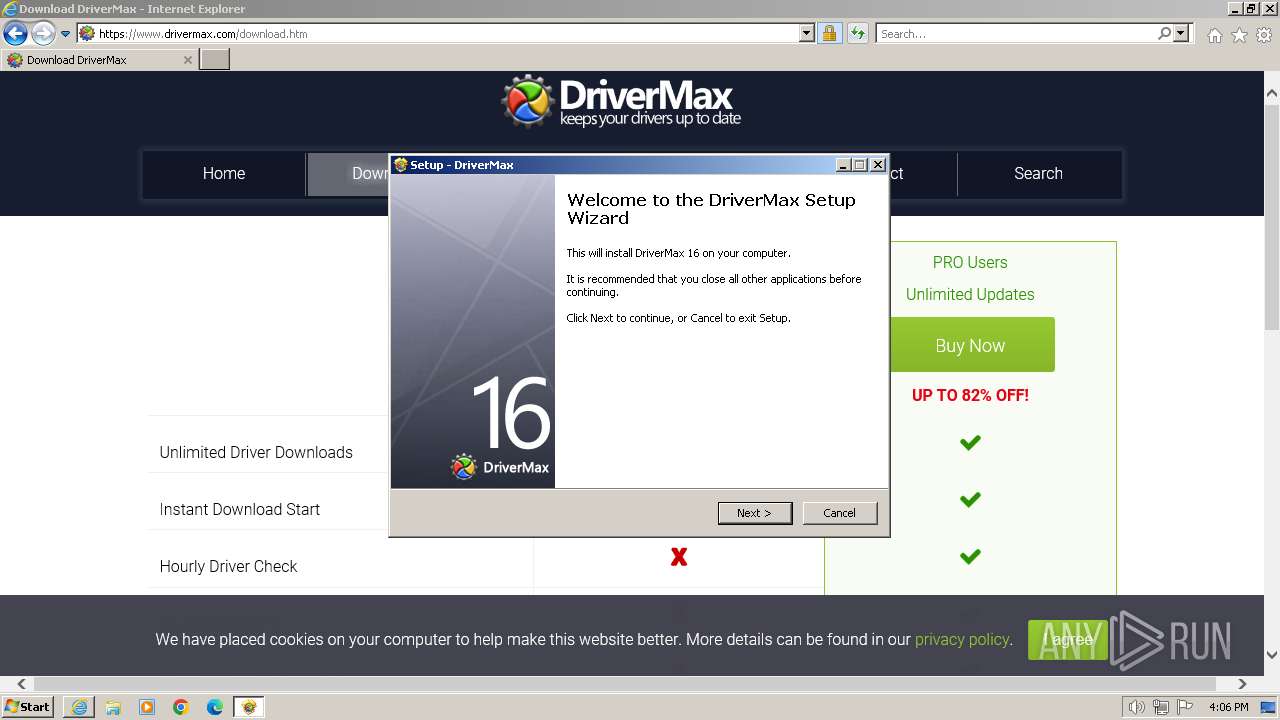
Drops the executable file immediately after the start
- drivermax.exe (PID: 2260)
- drivermax.tmp (PID: 3984)
- drivermax.exe (PID: 3028)
- drivermax.exe (PID: 2624)
- drivermax.exe (PID: 4004)
Connects to the CnC server
- drivermax.tmp (PID: 3984)
Changes the autorun value in the registry
- drivermax.tmp (PID: 3984)
SUSPICIOUS
Executable content was dropped or overwritten
- drivermax.exe (PID: 3028)
- drivermax.tmp (PID: 3984)
- drivermax.exe (PID: 2260)
- drivermax.exe (PID: 2624)
- drivermax.exe (PID: 4004)
Process drops legitimate windows executable
- drivermax.tmp (PID: 3984)
- drivermax.exe (PID: 4004)
Reads security settings of Internet Explorer
- drivermax.tmp (PID: 3984)
- drivermax.exe (PID: 3288)
- drivermax.exe (PID: 2624)
- drivermax.exe (PID: 4004)
- drivermax.exe (PID: 2404)
Reads the Windows owner or organization settings
- drivermax.tmp (PID: 3984)
Reads the Internet Settings
- drivermax.tmp (PID: 3984)
- drivermax.exe (PID: 2624)
- dxdiag.exe (PID: 4072)
Adds/modifies Windows certificates
- drivermax.tmp (PID: 3984)
- drivermax.exe (PID: 3288)
Checks for external IP
- drivermax.tmp (PID: 3984)
- drivermax.exe (PID: 3288)
- drivermax.exe (PID: 2624)
- drivermax.exe (PID: 4004)
- drivermax.exe (PID: 2404)
Reads settings of System Certificates
- drivermax.tmp (PID: 3984)
- drivermax.exe (PID: 3288)
- drivermax.exe (PID: 2624)
- drivermax.exe (PID: 4004)
- dxdiag.exe (PID: 4072)
- drivermax.exe (PID: 2404)
Uses TASKKILL.EXE to kill process
- drivermax.tmp (PID: 3984)
Checks Windows Trust Settings
- drivermax.exe (PID: 3288)
- drivermax.exe (PID: 2624)
- drivermax.exe (PID: 4004)
- drivermax.exe (PID: 2404)
Drops a system driver (possible attempt to evade defenses)
- drivermax.exe (PID: 2624)
- drivermax.exe (PID: 4004)
Searches for installed software
- drivermax.exe (PID: 4004)
Creates/Modifies COM task schedule object
- dxdiag.exe (PID: 4072)
Checks for Java to be installed
- java.exe (PID: 3216)
Starts CMD.EXE for commands execution
- drivermax.exe (PID: 4004)
Application launched itself
- drivermax.exe (PID: 4004)
INFO
Modifies the phishing filter of IE
- iexplore.exe (PID: 4052)
The process uses the downloaded file
- iexplore.exe (PID: 4052)
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 1992)
Application launched itself
- iexplore.exe (PID: 4052)
- msedge.exe (PID: 2856)
- msedge.exe (PID: 1560)
Drops the executable file immediately after the start
- iexplore.exe (PID: 4052)
- iexplore.exe (PID: 2920)
Checks supported languages
- drivermax.exe (PID: 2260)
- drivermax.exe (PID: 3028)
- drivermax.tmp (PID: 3984)
- drivermax.tmp (PID: 2240)
- stop_dmx.exe (PID: 2404)
- drivermax.exe (PID: 3288)
- innostp.exe (PID: 1092)
- drivermax.exe (PID: 2624)
- drivermax.exe (PID: 4004)
- innostp.exe (PID: 948)
- innostp.exe (PID: 1020)
- java.exe (PID: 3216)
- drivermax.exe (PID: 2404)
- wmpnscfg.exe (PID: 2652)
Executable content was dropped or overwritten
- iexplore.exe (PID: 2920)
- iexplore.exe (PID: 4052)
Reads the computer name
- drivermax.tmp (PID: 2240)
- drivermax.tmp (PID: 3984)
- drivermax.exe (PID: 3288)
- innostp.exe (PID: 1092)
- drivermax.exe (PID: 2624)
- drivermax.exe (PID: 4004)
- innostp.exe (PID: 948)
- innostp.exe (PID: 1020)
- wmpnscfg.exe (PID: 2652)
- drivermax.exe (PID: 2404)
Create files in a temporary directory
- drivermax.exe (PID: 2260)
- drivermax.tmp (PID: 3984)
- drivermax.exe (PID: 3028)
- java.exe (PID: 3216)
Checks proxy server information
- drivermax.tmp (PID: 3984)
Creates files or folders in the user directory
- drivermax.tmp (PID: 3984)
- drivermax.exe (PID: 2624)
- drivermax.exe (PID: 4004)
Reads the software policy settings
- drivermax.tmp (PID: 3984)
- drivermax.exe (PID: 3288)
- drivermax.exe (PID: 2624)
- drivermax.exe (PID: 4004)
- dxdiag.exe (PID: 4072)
- drivermax.exe (PID: 2404)
Reads the machine GUID from the registry
- drivermax.tmp (PID: 3984)
- drivermax.exe (PID: 3288)
- innostp.exe (PID: 1092)
- drivermax.exe (PID: 4004)
- innostp.exe (PID: 1020)
- drivermax.exe (PID: 2404)
- drivermax.exe (PID: 2624)
- innostp.exe (PID: 948)
Creates files in the program directory
- drivermax.tmp (PID: 3984)
- drivermax.exe (PID: 3288)
- drivermax.exe (PID: 4004)
- dxdiag.exe (PID: 4072)
- java.exe (PID: 3216)
- cmd.exe (PID: 1832)
Creates a software uninstall entry
- drivermax.tmp (PID: 3984)
Manual execution by a user
- msedge.exe (PID: 1560)
- wmpnscfg.exe (PID: 2652)
Reads security settings of Internet Explorer
- dxdiag.exe (PID: 4072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
116
Monitored processes
56
Malicious processes
10
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=1628 --field-trial-handle=1284,i,15473012119860670403,15368101077620816990,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 548 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=2508 --field-trial-handle=1284,i,15473012119860670403,15368101077620816990,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 572 | "Taskkill.exe" /IM innoupd.exe /F | C:\Windows\System32\taskkill.exe | — | drivermax.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 668 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3912 --field-trial-handle=1284,i,15473012119860670403,15368101077620816990,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 844 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2200 --field-trial-handle=1284,i,15473012119860670403,15368101077620816990,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 908 | "Taskkill.exe" /IM innoupd.exe /F | C:\Windows\System32\taskkill.exe | — | drivermax.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 948 | "C:\Program Files\Innovative Solutions\DriverMax\innostp.exe" -install | C:\Program Files\Innovative Solutions\DriverMax\innostp.exe | — | drivermax.exe | |||||||||||
User: admin Company: Innovative Solutions Integrity Level: HIGH Description: Application Starter Exit code: 0 Version: 1.0.0.9 Modules
| |||||||||||||||
| 1020 | "C:\Program Files\Innovative Solutions\DriverMax\innostp.exe" -install | C:\Program Files\Innovative Solutions\DriverMax\innostp.exe | — | drivermax.exe | |||||||||||
User: admin Company: Innovative Solutions Integrity Level: HIGH Description: Application Starter Exit code: 0 Version: 1.0.0.9 Modules
| |||||||||||||||
| 1092 | "C:\Program Files\Innovative Solutions\DriverMax\innostp.exe" "-install" | C:\Program Files\Innovative Solutions\DriverMax\innostp.exe | — | drivermax.tmp | |||||||||||
User: admin Company: Innovative Solutions Integrity Level: HIGH Description: Application Starter Exit code: 0 Version: 1.0.0.9 Modules
| |||||||||||||||
| 1196 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3700 --field-trial-handle=1284,i,15473012119860670403,15368101077620816990,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
102 594
Read events
100 930
Write events
1 487
Delete events
177
Modification events
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31088479 | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31088479 | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (4052) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
291
Suspicious files
244
Text files
266
Unknown types
116
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2920 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:47B4FB330585AE741EE76F16422EEE75 | SHA256:7A69A2496B285D0790BEA2FCFBE999D4CC8C466E8D3B465DA0E25E6388109356 | |||
| 2920 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:1DC0877972C9B6D51BFE2372A105AC9B | SHA256:230C62F51C389230AB1B4AB1AAF363F63C5CF7FBA4519120410A0D4ADA91218B | |||
| 2920 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\dmax[1].png | image | |
MD5:300E8BA3044534627147A9F1E94E294F | SHA256:B8292C9D40B45903F8CDFBBFF10EB83B9B489DA74EDAA0717B8D4957E6ED0DA0 | |||
| 2920 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\referral[1].js | text | |
MD5:7EDE0F228E352CB1EE954769FCA2CC8C | SHA256:D96763BB18499368F4E79CBBECE0B15390B91518A6D79606ED616538E3936C44 | |||
| 2920 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\addref2[1].js | html | |
MD5:0968421C6B68352236D90F7AF13F6E99 | SHA256:68AADE29D690D8F6A7F4644A92F12FF9E9ABE4D108472E9292526A5BE11D310D | |||
| 2920 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\index[1].css | text | |
MD5:DEBB7BD83824D9D66FE1A5D991600DB0 | SHA256:1A3E56AEA4F92D6E19C4A214F0C568E3E1D996ECD0784378BFB4DC350BB38DCB | |||
| 2920 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\downloadAndRedir[1].js | text | |
MD5:8F84B122C13E8855969B56E41BF0E57A | SHA256:C705E6AB009183E879C0F6C9D63D9B3EBE8F519335C7E255300F41062CF9F19E | |||
| 2920 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\navcollapse[1].js | text | |
MD5:CF8880D3450DDDA95A6A5D7BFAE38C29 | SHA256:3DC1A0EE5E5480866FA9B43778A371E703A61A7213E97DFFF831BA3721E45B2A | |||
| 2920 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\modal[1].js | text | |
MD5:4AA11AAE74D9D6DB7D9CCCF0CD5163D8 | SHA256:638D8DB378EA9B241A0E0541E788B90F23FD990ED6C290BD559A8DB07E7C00AF | |||
| 2920 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\user-animation[1].js | text | |
MD5:6A7759FCEF953380F4C219300155B1F7 | SHA256:32C2EF1F84E5807E7FCDEC4AF2BC54AC2FB136921CCF816ECD42B96F445B8AFB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
63
TCP/UDP connections
167
DNS requests
95
Threats
19
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2920 | iexplore.exe | GET | 200 | 23.192.153.142:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
2920 | iexplore.exe | GET | 304 | 173.222.108.201:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5b0325f31ae0f9b6 | unknown | — | — | unknown |
2920 | iexplore.exe | GET | 200 | 142.250.184.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCG5mYmc5exBwr3zurLpXnC | unknown | binary | 472 b | unknown |
2920 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
2920 | iexplore.exe | GET | 200 | 142.250.184.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
2920 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | unknown | binary | 471 b | unknown |
2920 | iexplore.exe | GET | 200 | 142.250.184.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCSnN9%2FWcCK6QmbjMlxbrBK | unknown | binary | 472 b | unknown |
2920 | iexplore.exe | GET | 200 | 142.250.184.195:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEAch2W18yjrFCctU7xjW0Yc%3D | unknown | binary | 471 b | unknown |
2920 | iexplore.exe | GET | 200 | 142.250.184.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCG5mYmc5exBwr3zurLpXnC | unknown | binary | 472 b | unknown |
2920 | iexplore.exe | GET | 200 | 142.250.184.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCAKlf1nuem1AlkNvBwxf5A | unknown | binary | 472 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2920 | iexplore.exe | 168.119.201.56:443 | www.drivermax.com | Hetzner Online GmbH | UA | unknown |
2920 | iexplore.exe | 173.222.108.201:80 | ctldl.windowsupdate.com | Akamai International B.V. | CH | unknown |
2920 | iexplore.exe | 23.192.153.142:80 | x1.c.lencr.org | AKAMAI-AS | GB | unknown |
2920 | iexplore.exe | 216.58.212.138:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
2920 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2920 | iexplore.exe | 142.250.185.168:443 | www.googletagmanager.com | GOOGLE | US | unknown |
2920 | iexplore.exe | 142.250.184.195:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.drivermax.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
cdn.onesignal.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
ajax.googleapis.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |
2920 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code.jquery .com) |
3984 | drivermax.tmp | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ipinfo.io |
3984 | drivermax.tmp | Misc activity | ET ADWARE_PUP Drivermax Utility Checkin Activity |
3984 | drivermax.tmp | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
3288 | drivermax.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ipinfo.io |
2624 | drivermax.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ipinfo.io |
4004 | drivermax.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ipinfo.io |
1308 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |